A Zero-Trust Multi-Processor Reporter-Verifier Design of Edge Devices for Firmware Authenticity in Internet of Things and Blockchain Applications
Abstract
1. Introduction
2. Related Work
2.1. Blockchain in Internet of Things
2.1.1. Blockchain-IoT Applications
- Enhanced Security: Blockchain’s decentralized nature and cryptographic techniques provide robust security for IoT devices and data. Each transaction or data exchange is recorded in an immutable ledger, reducing the risk of unauthorized access and data breaches.
- Data Integrity and Immutability: Blockchain ensures that the data recorded from IoT devices are tamper-proof and verifiable. This immutability is crucial for applications in which data accuracy and trust are paramount.
- Transparency and Traceability: Blockchain’s transparent ledger allows all participants in the IoT ecosystem to verify transactions and data exchanges. This transparency enhances trust and accountability, particularly in supply chain and logistics applications.
- Decentralization: By eliminating the need for a central authority, blockchain reduces single points of failure and enhances the resilience of IoT networks.
2.1.2. Shortcomings with Regard to Firmware Authenticity
2.1.3. Zero Trust Security Model
2.2. Internet of Things Edge Devices
2.2.1. Detecting Security Threats in IoT Edge
- Unexpected Device Behavior: If the device starts acting strangely, such as turning on or off without user input, changing settings spontaneously, or performing tasks outside its normal function, it might be compromised [25].
- Increased Bandwidth Usage: A sudden spike in bandwidth usage can indicate that the device is being used as part of a botnet or for other malicious activities [26].
- Unexplained Data Traffic: Monitoring network traffic for unusual data being sent to unfamiliar network addresses can help identify compromised devices [26].
- Slow Device Performance: Compromised devices often exhibit poor performance, such as responding slowly or freezing frequently [27].
- Unusual Account Activity: Check for unauthorized login attempts, password changes, or unknown devices accessing accounts linked to the IoT device [28].
- Disabled Security Features: If security features like firewalls or antivirus software are disabled without explanation, it could be a sign of a hack [29].
- New and Unknown Software Installations: Unrecognized software on the device can indicate malware or unauthorized applications [29].
2.2.2. Authenticity of Edge Firmware
- Digital Signatures: The manufacturer digitally signs the firmware. This cryptographic signature verifies that the firmware has not been tampered with and is from a trusted source.
- Secure Boot: Implementing a secure boot process can verify the integrity of the firmware before the device boots up. This ensures that only authorized firmware runs on the device.
- End-to-end Encryption: Ensuring that firmware updates are delivered through encrypted channels to prevent tampering during transmission.
- Multi-Factor Authentication (MFA): MFA is used for firmware updates to add an additional layer of security, ensuring that only authorized personnel can update the firmware.
- Trusted Supply Chain: Establish a trusted supply chain to ensure that the firmware is authentic from the point of manufacture to deployment.
- Regular Audits: Regular and thorough code reviews by independent human teams can help identify malicious code or vulnerabilities introduced by developers.
- Segregation of Duties: Implementing segregation of duties ensures that no single developer has control over the entire development and deployment process.
- Transparency and Accountability: Maintain transparency in the development process and hold developers accountable for their work through logging and monitoring.
- Security Training: Provide regular security training to developers to ensure they understand the importance of secure coding practices and the potential consequences of introducing vulnerabilities.
2.2.3. Secure Bootloader
2.2.4. Software Authenticity and Signatures
- Codes must be manually checked, which is time-consuming and challenging. One stakeholder generates IoT edge data, but it is relevant to multiple other stakeholders. Each one wants the data to be actual. However, the owner can put any malicious code in the device, misreporting the data even with a perfect digital signature and secure boot loading.
- IoT Edge often reports only numeric or smaller data. Observing any deviation from normal behavior is already challenging, as the only thing coming from the device is a set of numbers or characters. It is even more complicated if the device reports normal data when the actual data are bad. There is usually no other interface that can be observed for performances.
- They work in retrospect, i.e., if a problem occurs, it can be traced back to the source of the fault. However, again, false normal data are more challenging to detect digitally. They can only be detected when the actual environments or products face actual damage when it is too late.
- They are focused on the network transfer but not on the actual code’s execution.
2.3. Embedded Systems Memory and Data Protocols
2.3.1. Flash Memory
2.3.2. In-Circuit Serial Programming
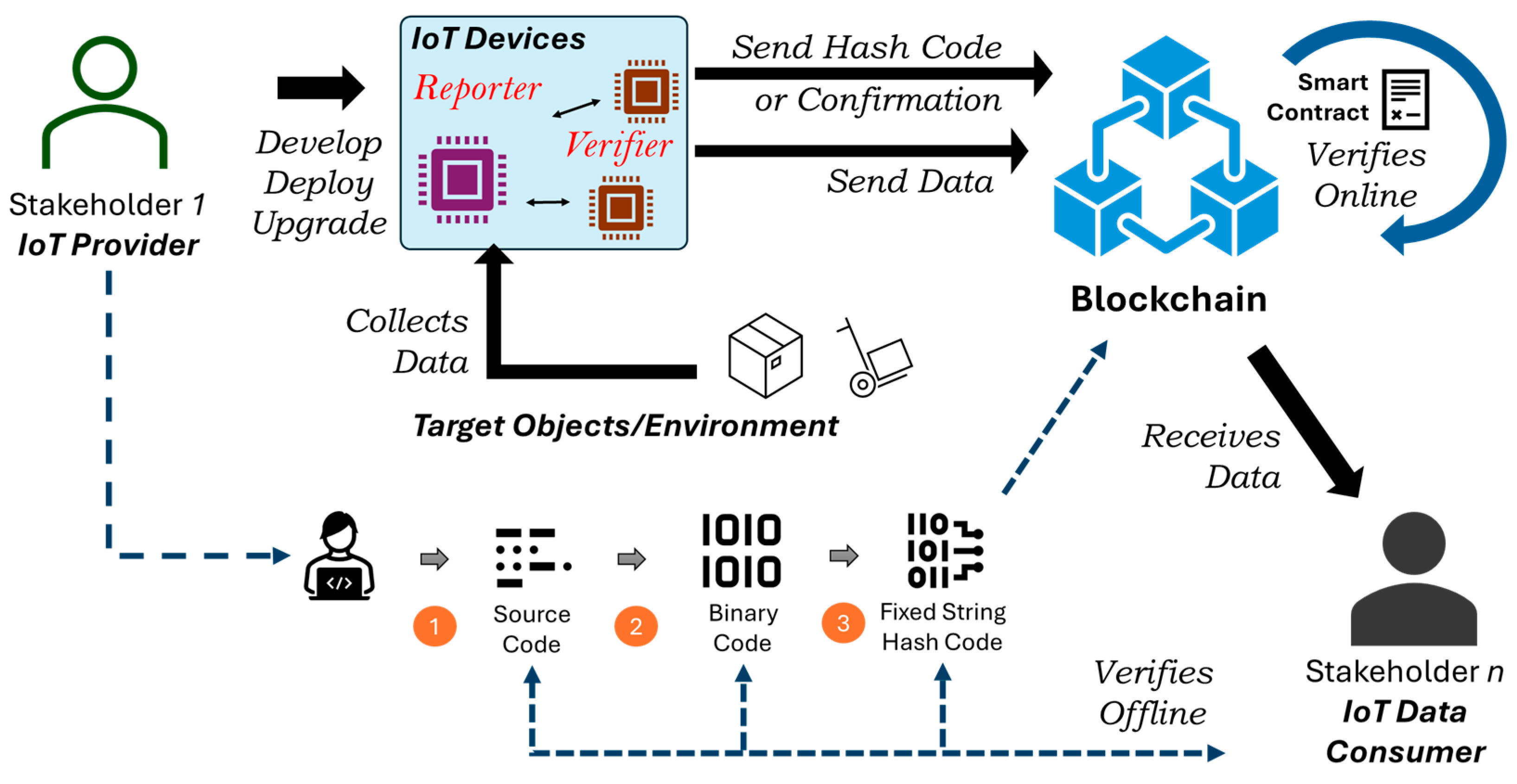
3. Proposed Firmware Validation Architecture with Multi-Processor Method
3.1. Firmware Validation Architecture
- (1)
- When the device is created, its source code is also formed to serve the application requirements. All stakeholders agree upon these requirements in the IoT-blockchain application.
- (2)
- The binary code is generated from the source code using a compiler.
- (3)
- The corresponding binary code hash(es) is generated in parallel with the device’s deployment or upgrade.
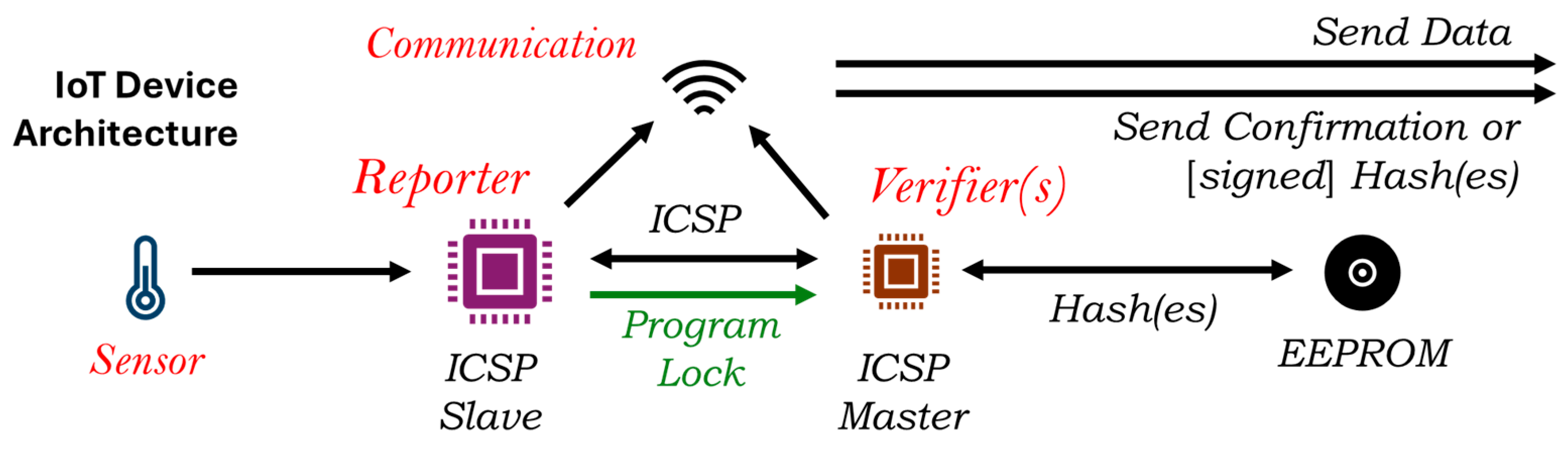
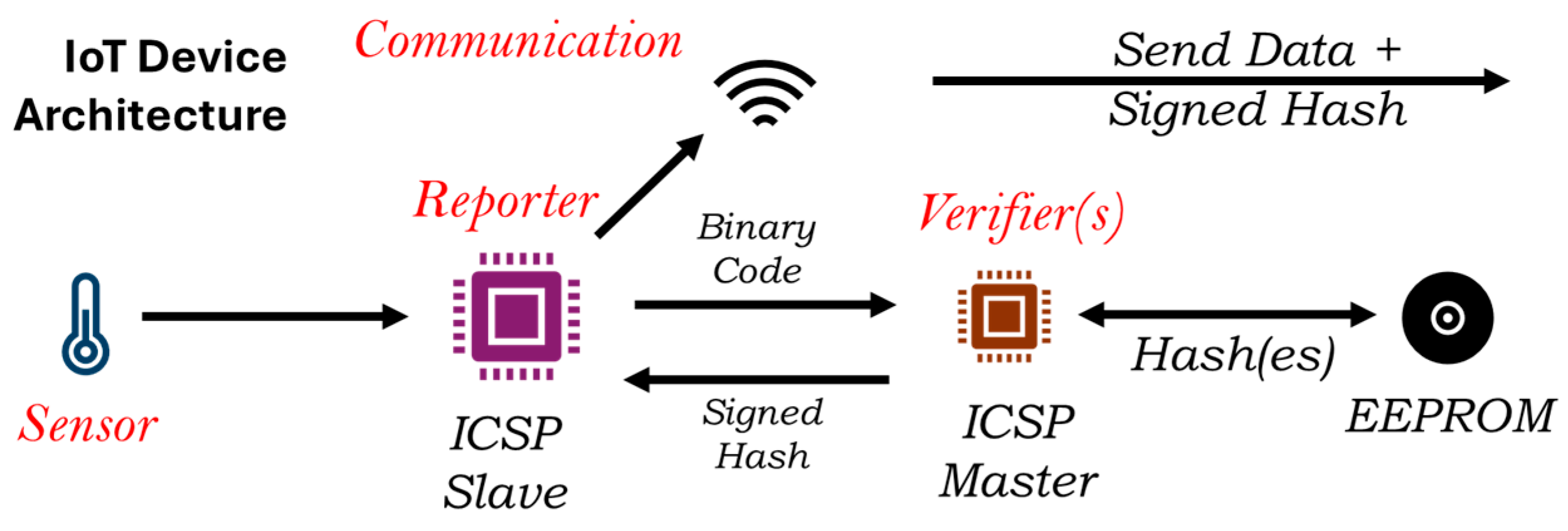
3.2. Reporter-Verifier Model
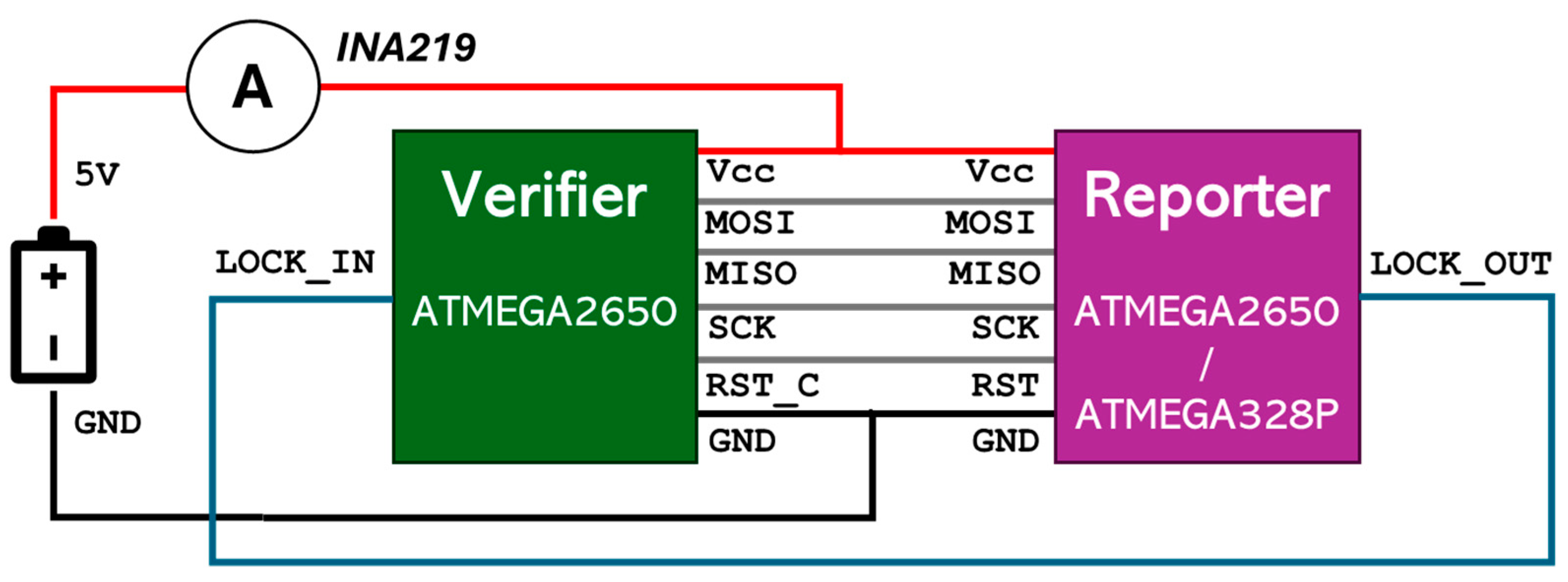
3.2.1. Active Verifier Design
- Local Hash and Match Mode (LHM): In this, the verifier aims to perform all the tasks on the device—binary code extraction, hashing, and matching—before sending a confirmation. The fundamental drawback with this approach is that the verifier cannot be too strong, i.e., have large RAM or processing power. Most low-power microprocessors would have a minimum speed of 1 MHz, which is sufficient for performing hashes. Assuming the processing power is constant, the major limitation is memory. Different hashing techniques generate a hash of different fixed-size strings ranging from 128 to 1024 bits. However, the compiled code can be in several KBs. For example, the Arduino ATMEGA2560 processor has a flash memory size of 256 KB and a RAM of 8 KB. This means the code written can be much larger than the RAM available in a typical microprocessor. The size of the reporter flash memory is denoted as α and the RAM of the verifier as β. In order to verify the program, the verifier needs to divide the reporter code into blocks with a block size of at most 8 KB, and the number of blocks n can be:The verifier reads the code from the reporter byte by byte so it can partition the code into blocks and then run the hashing on each block. This is shown in Figure 3.The verifier stores the expected n hash(es) in an EEPROM. When a new code is loaded into the reporter in a secure medium with the knowledge of all stakeholders, the verifier creates the hashes and stores them in a dedicated EEPROM. EEPROM can be low-cost and available in larger sizes than the reporter flash size α. The verifier can detect any further changes in the reporter code by matching the hashes with the hashes in EEPROM.The verifier only sends confirmation of matching to the blockchain, which requires much less memory. This is the most secure approach for protecting the device code, as nothing leaves the device. It can also keep verifying even when there is no network connection for a period of time and send the confirmations when the network becomes available.
- Local Hash Remote Match Mode (LHRM): In a more untrusted but likely environment, the verifier does not match the hashes locally. It creates the n hashes and sends them to the blockchain, where smart contracts match the hash(es) on the blockchain. It may not need an EEPROM for this, but the size of the blocks is determined by the size of the buffer available on the verifier for transmissions.This is a zero-trust model and the most likely implementation. However, the verifier may need to send many batches of hashed data, which requires a lot more transmissions.
- Remote Hash and Match Mode (RHM): If no hashing is implemented on the verifier, then the verifier can send segments of the code back to the blockchain, where it can be hashed and matched. This is very insecure, as the code, even though it is in a binary form, has to be regularly transmitted over a network. Even if this is encrypted, there is a possibility of a leak.
- The verifier resets the reporter. To address this, the lock pin may be used, where the reporter can set the lock pin to logically high to prevent the verifier from initiating a read. As most edge devices sleep after operating for a while, the reset of the reporter should not matter in its operations.
- The verifier needs to sleep as well and synchronize with the reporter to stay awake and perform the check at the right time. This can be achieved easily with the proper hardware design. Also, if the verifier does not send the hash or confirmation in time, the blockchain can start an alert notification.
3.2.2. Verifier as a Module Design
3.2.3. Authenticity of the Verifier Code
3.3. Unique Identification of an Embedded Program in Flash Memory
3.3.1. Binary Code—Hexadecimal Representation
- Preprocessing: The compiler adds necessary function prototypes and includes core libraries.
- Compilation: The preprocessed code is compiled into object files, such as the avr-gcc compiler for AVR processors. This compiler is different for each type of board.
- Linking and Conversion: The object files are linked together to create a single binary file, such as an Arduino board .elf file. The binary file is then converted into the final machine code, which is in the hexadecimal format. In the case of Arduino boards, it is a .hex file.
3.3.2. Reconstructing Source Code
3.3.3. Duplicate Binary Files
- Dead Code Elimination: If both programs contain code that does not affect the program’s output or behavior, the compiler might remove this “dead code”, resulting in identical .hex files. Optimized code for an IoT device will not contain dead code. An eventual upgrade to the code would always add new features and corresponding function codes.
- Identical Functionality: If two programs perform the same operations in the same way, even if their source code looks different, the compiler might produce the same machine code for both. This is also nearly impossible for commercial IoT devices, as the upgrade would use the same libraries and only add to the original code.
- Minimal Programs: Very simple programs, such as those that only initialize variables or contain empty loops, might compile to the same .hex file because there is not much code to differentiate them. Commercial IoT devices should definitely have complex code.
- Compiler Settings: Using the same compiler settings and libraries can also lead to identical hex files for different programs. The developer can set this to ensure that no two codes generate the same binary file.
3.3.4. Hashing
3.4. Role of Blockchain and Version Control
- LHM smart contract: For this, the smart contract only needs to record a successful confirmation message from the verifier along with its identification details in definite time periods. These confirmations are then written in the blockchain.
- LHRM smart contracts: For this, the smart contract receives the reporter’s hash and identification details. It then matches the hash with the expected hash of the device based on the identification details. This requires some additional calculations but nothing significant for a cloud-based blockchain. If there is a match, then confirmation is stored in the blockchain.
- RHM smart contract: The smart contract receives the device’s hexadecimal/binary code along with the identification. It then has to look up the corresponding hashing and, optionally, any decryption mechanism corresponding to the device and perform the operations to obtain the binary code’s hash. Then, it matches the hash with the expected hash and stores the results in the blockchain.
4. Results
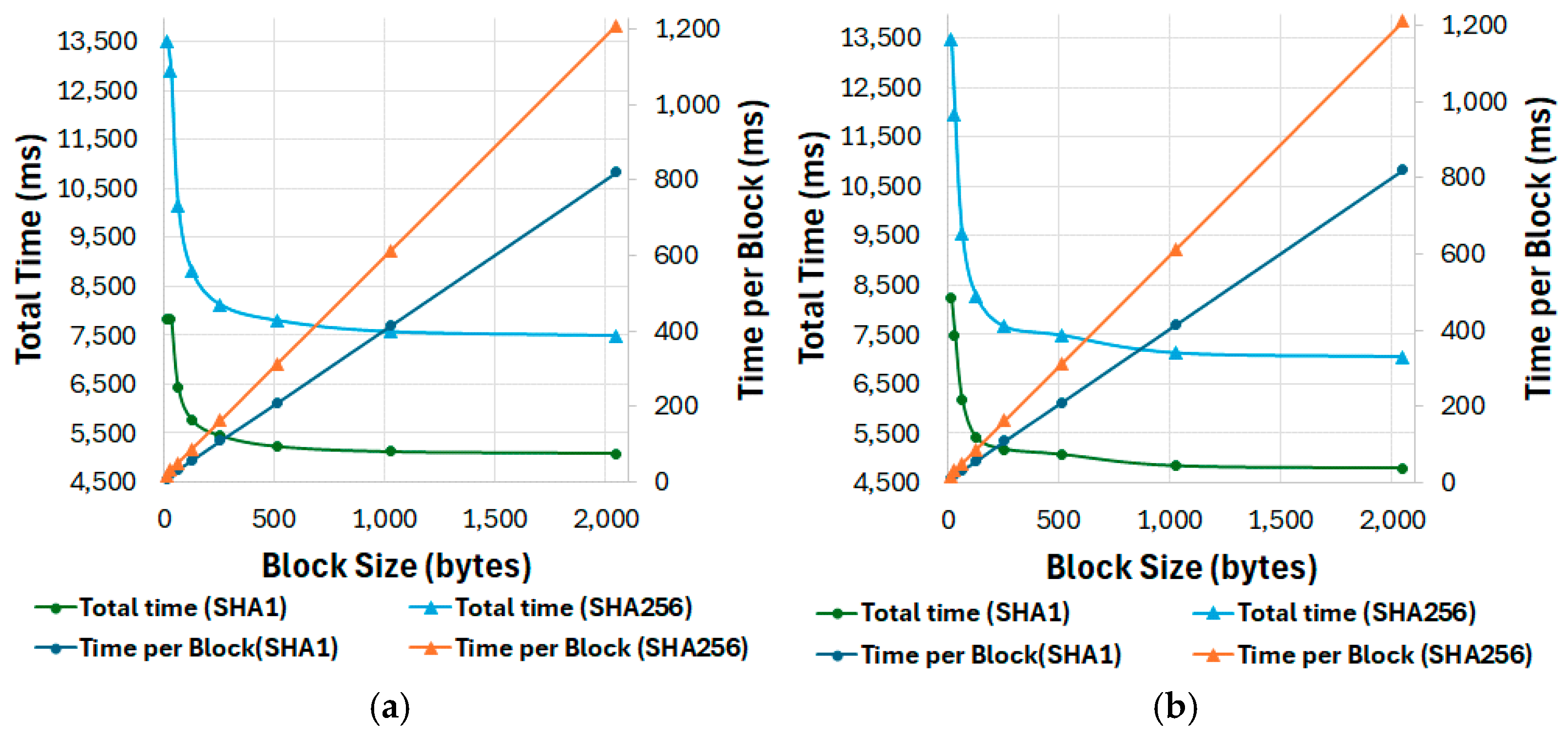
4.1. Time Consumption Analysis
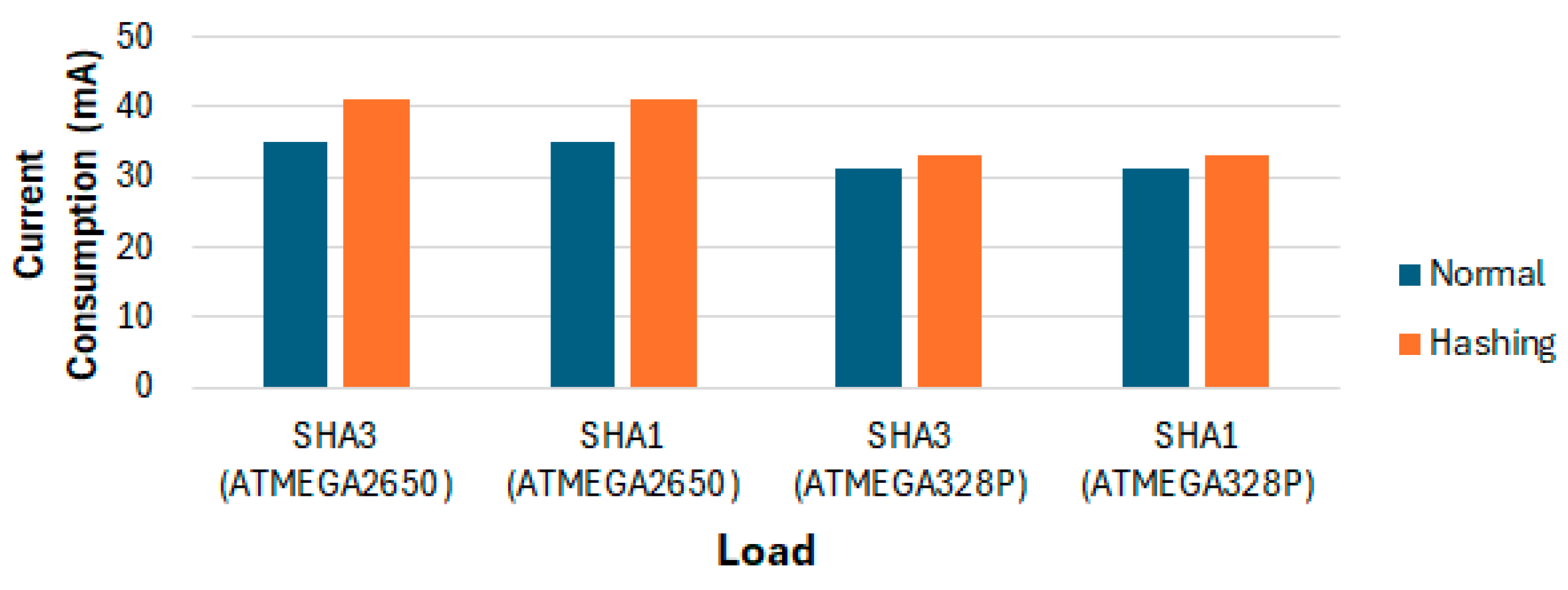
4.2. Power Consumption Analysis
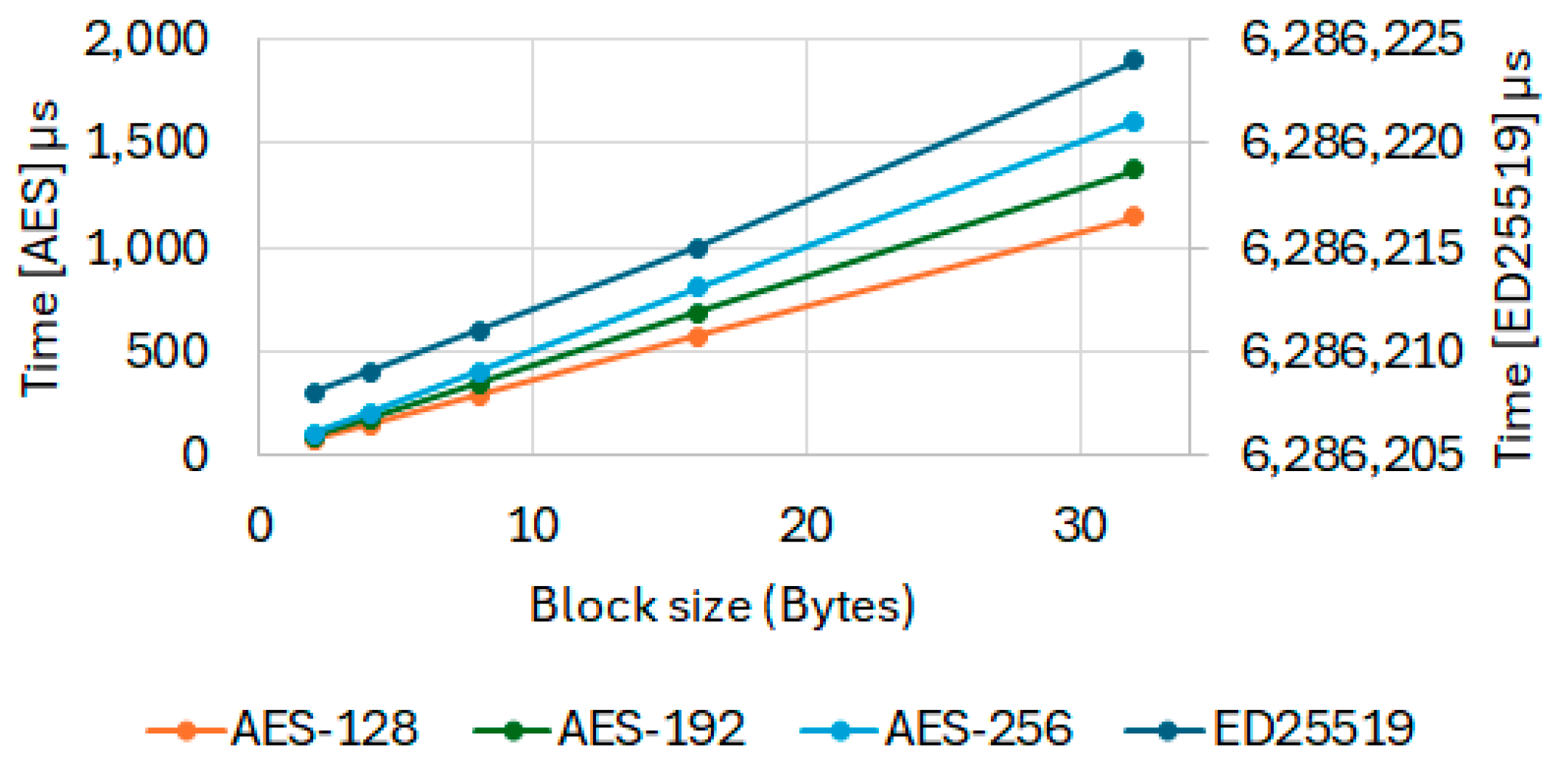
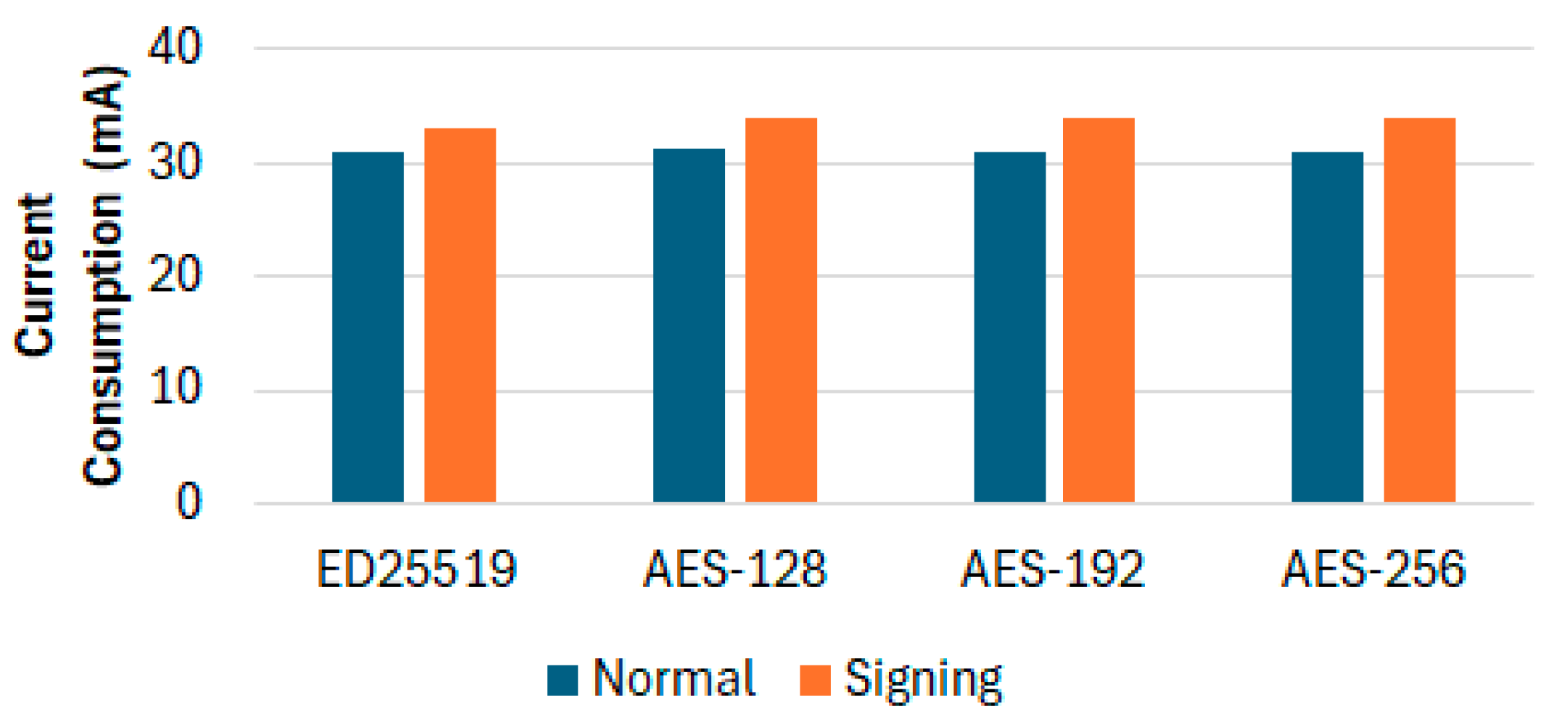
4.3. Encryption Time and Power Analysis
5. Discussion
5.1. IoT Reliability in the Era of Edge AI
5.2. Limitations and Challenges
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Chen, Z. Security of Esoteric Firmware and Trusted Execution Environments. Ph.D. Thesis, University of Birmingham, Birmingham, UK, 2023. [Google Scholar]
- Wu, Y.; Wang, J.; Wang, Y.; Zhai, S.; Li, Z.; He, Y.; Sun, K.; Li, Q.; Zhang, N. Your firmware has arrived: A study of firmware update vulnerabilities. In Proceedings of the 33rd USENIX Security Symposium (USENIX Security 24), Philadelphia, PA, USA, 14–16 August 2024; pp. 5627–5644. [Google Scholar]
- Akkaoui, R.; Stefanov, A.; Palensky, P.; Epema, D.H.J. Resilient, Auditable, and Secure IoT-Enabled Smart Inverter Firmware Amendments with Blockchain. IEEE Internet Things J. 2024, 11, 8945–8960. [Google Scholar] [CrossRef]
- Singh, R.; Gill, S.S. Edge AI: A survey. Internet Things Cyber-Phys. Syst. 2023, 3, 71–92. [Google Scholar]
- Abbassi, Y.; Benlahmer, H. IoT and Blockchain combined: For decentralized security. Procedia Comput. Sci. 2021, 191, 337–342. [Google Scholar] [CrossRef]
- Obaidat, M.A.; Rawashdeh, M.; Alja’afreh, M.; Abouali, M.; Thakur, K.; Karime, A. Exploring IoT and Blockchain: A Comprehensive Survey on Security, Integration Strategies, Applications and Future Research Directions. Big Data Cogn. Comput. 2024, 8, 174. [Google Scholar] [CrossRef]
- Rejeb, A.; Rejeb, K.; Appolloni, A.; Jagtap, S.; Iranmanesh, M.; Alghamdi, S.; Alhasawi, Y.; Kayikci, Y. Unleashing the power of internet of things and blockchain: A comprehensive analysis and future directions. Internet Things Cyber-Phys. Syst. 2024, 4, 1–18. [Google Scholar] [CrossRef]
- Allouche, M.; Frikha, T.; Mitrea, M.; Memmi, G.; Chaabane, F. Lightweight Blockchain Processing. Case Study: Scanned Document Tracking on Tezos Blockchain. Appl. Sci. 2021, 11, 7169. [Google Scholar] [CrossRef]
- Anagnostakis, A.G.; Giannakeas, N.; Tsipouras, M.G.; Glavas, E.; Tzallas, A.T. IoT Micro-Blockchain Fundamentals. Sensors 2021, 21, 2784. [Google Scholar] [CrossRef]
- Anderson, J.S.; Ravindran, B.; Jensen, E.D. Consensus-Driven Distributable Thread Scheduling in Networked Embedded Systems. In Proceedings of the International Conference on Embedded and Ubiquitous Computing, Taipei, Taiwan, 17–20 December 2007; Kuo, T.-W., Sha, E., Guo, M., Yang, L.T., Shao, Z., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; pp. 247–260. [Google Scholar]
- Dorri, A.; Jurdak, R. Tree-Chain: A Lightweight Consensus Algorithm for IoT-based Blockchains. In Proceedings of the 2021 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Sydney, Australia, 3–6 May 2021; pp. 1–9. [Google Scholar] [CrossRef]
- Frikha, T.; Chaabane, F.; Aouinti, N.; Cheikhrouhou, O.; Ben Amor, N.; Kerrouche, A. Implementation of Blockchain Consensus Algorithm on Embedded Architecture. Secur. Commun. Netw. 2021, 2021, 9918697. [Google Scholar] [CrossRef]
- Kolaric, P.; Chen, C.; Dalal, A.; Lewis, F.L. Consensus controller for multi-UAV navigation. Control Theory Technol. 2018, 16, 110–121. [Google Scholar] [CrossRef]
- Ktari, J.; Frikha, T.; Chaabane, F.; Hamdi, M.; Hamam, H. Agricultural Lightweight Embedded Blockchain System: A Case Study in Olive Oil. Electronics 2022, 11, 3394. [Google Scholar] [CrossRef]
- Ktari, J.; Frikha, T.; Hamdi, M.; Hamam, H. Enhancing Blockchain Consensus with FPGA: Accelerating Implementation for Efficiency. IEEE Access 2024, 12, 44773–44785. [Google Scholar] [CrossRef]
- Ktari, J.; Frikha, T.; Yousfi, M.A.; Belghith, M.K.; Sanei, N. Embedded Keccak implementation on FPGA. In Proceedings of the 2022 IEEE International Conference on Design & Test of Integrated Micro & Nano-Systems (DTS), Cairo, Egypt, 6–9 June 2022; pp. 1–5. [Google Scholar]
- Mahmoud, M.A.; Gurunathan, M.; Ramli, R.; Babatunde, K.A.; Faisal, F.H. Review and Development of a Scalable Lightweight Blockchain Integrated Model (LightBlock) for IoT Applications. Electronics 2023, 12, 1025. [Google Scholar] [CrossRef]
- Andola, N.; Venkatesan, S.; Verma, S. PoEWAL: A lightweight consensus mechanism for blockchain in IoT. Pervasive Mob. Comput. 2020, 69, 101291. [Google Scholar] [CrossRef]
- Rao, N.M.; Veer, M.S.; Jayachandra, K.; Santosh, C.V.; Goud, B.M.; Naidu, P.R. Blockchain Over Low Power Microcontrollers. In Proceedings of the 2022 Third International Conference on Intelligent Computing Instrumentation and Control Technologies (ICICICT), Kannur, India, 11–12 August 2022; pp. 735–739. [Google Scholar] [CrossRef]
- Tanjung, W.; Fat, J.; Hugeng, H. Blockchain Technology Implementation on Simple Microcontroller Based Ballots System. Int. J. Appl. Sci. Technol. Eng. 2023, 1, 770–777. [Google Scholar] [CrossRef]
- Xu, W. Hybrid Fault Tolerant Consensus in Wireless Embedded Systems. Ph.D. Thesis, Technische Universität Braunschweig, Braunschweig, Germany, 2021. [Google Scholar]
- Zhang, W.; Wu, Z.; Han, G.; Feng, Y.; Shu, L. LDC: A lightweight dada consensus algorithm based on the blockchain for the industrial Internet of Things for smart city applications. Future Gener. Comput. Syst. 2020, 108, 574–582. [Google Scholar] [CrossRef]
- He, Y.; Huang, D.; Chen, L.; Ni, Y.; Ma, X. A survey on zero trust architecture: Challenges and future trends. Wirel. Commun. Mob. Comput. 2022, 2022, 6476274. [Google Scholar]
- Xiao, Y.; Jia, Y.; Liu, C.; Cheng, X.; Yu, J.; Lv, W. Edge Computing Security: State of the Art and Challenges. Proc. IEEE 2019, 107, 1608–1631. [Google Scholar] [CrossRef]
- Mahadevappa, P.; Al-amri, R.; Alkawsi, G.; Alkahtani, A.A.; Alghenaim, M.F.; Alsamman, M. Analyzing Threats and Attacks in Edge Data Analytics within IoT Environments. IoT 2024, 5, 123–154. [Google Scholar] [CrossRef]
- Zhao, Y.; Cheng, G.; Duan, Y.; Gu, Z.; Zhou, Y.; Tang, L. Secure IoT edge: Threat situation awareness based on network traffic. Comput. Netw. 2021, 201, 108525. [Google Scholar] [CrossRef]
- Abawajy, J.; Huda, S.; Sharmeen, S.; Hassan, M.M.; Almogren, A. Identifying cyber threats to mobile-IoT applications in edge computing paradigm. Future Gener. Comput. Syst. 2018, 89, 525–538. [Google Scholar] [CrossRef]
- Ficco, M.; Granata, D.; Rak, M.; Salzillo, G. Threat Modeling of Edge-Based IoT Applications. In Proceedings of the International Conference on the Quality of Information and Communications Technology, Algarve, Portugal, 8–11 September 2021; Springer: Cham, Switzerland, 2021; pp. 282–296. [Google Scholar]
- Aldaej, A.; Ullah, I.; Ahanger, T.A.; Atiquzzaman, M. Ensemble technique of intrusion detection for IoT-edge platform. Sci. Rep. 2024, 14, 11703. [Google Scholar] [CrossRef]
- Guin, U.; Cui, P.; Skjellum, A. Ensuring Proof-of-Authenticity of IoT Edge Devices Using Blockchain Technology. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1042–1049. [Google Scholar] [CrossRef]
- Guin, U.; Singh, A.; Alam, M.; Canedo, J.; Skjellum, A. A secure low-cost edge device authentication scheme for the internet of things. In Proceedings of the 2018 31st International Conference on VLSI Design and 2018 17th International Conference on Embedded Systems (VLSID), Pune, India, 6–10 January 2018; IEEE: New York, NY, USA, 2018; pp. 85–90. [Google Scholar]
- Lee, B.; Lee, J.-H. Blockchain-based secure firmware update for embedded devices in an Internet of Things environment. J. Supercomput. 2017, 73, 1152–1167. [Google Scholar] [CrossRef]
- Nadir, I.; Mahmood, H.; Asadullah, G. A taxonomy of IoT firmware security and principal firmware analysis techniques. Int. J. Crit. Infrastruct. Prot. 2022, 38, 21. [Google Scholar] [CrossRef]
- Verderame, L.; Ruggia, A.; Merlo, A. PARIOT: Anti-repackaging for IoT firmware integrity. J. Netw. Comput. Appl. 2023, 217, 18. [Google Scholar] [CrossRef]
- Yeasmin, S.; Haque, A.; Sayegh, A. A novel and failsafe blockchain framework for secure OTA updates in connected autonomous vehicles. Veh. Commun. 2023, 43, 12. [Google Scholar] [CrossRef]
- Bruschi, F.; Zanghieri, M.; Terziani, M.; Sciuto, D. Decentralized Updates of IoT and Edge Devices. In Proceedings of the International Conference on Advanced Information Networking and Applications, Kitakyushu, Japan, 17–19 April 2024; Springer: Cham, Switzerland, 2024; pp. 161–170. [Google Scholar]
- Bakhshi, T.; Ghita, B.; Kuzminykh, I. A Review of IoT Firmware Vulnerabilities and Auditing Techniques. Sensors 2024, 24, 708. [Google Scholar] [CrossRef]
- Rashmi, R.; Karthikeyan, A. Secure boot of embedded applications-a review. In Proceedings of the 2018 Second International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 29–31 March 2018; pp. 291–298. [Google Scholar]
- Alanzi, T. A review of mobile applications available in the app and google play stores used during the COVID-19 outbreak. J. Multidiscip. Healthc. 2021, 14, 45–57. [Google Scholar] [CrossRef]
- Meza, J.; Wu, Q.; Kumar, S.; Mutlu, O. A large-scale study of flash memory failures in the field. ACM SIGMETRICS Perform. Eval. Rev. 2015, 43, 177–190. [Google Scholar] [CrossRef]
- Ahmed, A.I.; Sharobim, B.K.; Fetteha, M.A.; Said, L.A.; Eltawil, A.M.; Madian, A.H. A Design of Rechargeable In-Circuit Serial Programmer for Industrial Embedded Systems. In Proceedings of the 2024 International Conference on Microelectronics (ICM), Doha, Qatar, 14–17 December 2024; pp. 1–5. [Google Scholar]
- Ahmed, A.; Sharf, S.; Badawy, W.; Madian, A.; Abdelhamied, R.; Mekky, M.; Abdelhamied, M. Wireless ATMEL AVR In-Circuit Serial Programmer based on Wi-Fi and ZigBee. In Proceedings of the 2020 16th International Computer Engineering Conference (ICENCO), Cairo, Egypt, 29–30 December 2020; pp. 187–190. [Google Scholar]
- Ajanovic, J. PCI express 3.0 overview. In Proceedings of the 2009 IEEE Hot Chips 21 Symposium (HCS), Stanford, CA, USA, 23–25 August 2009; pp. 1–61. [Google Scholar]
- Amestica, O.E.; Melin, P.E.; Duran-Faundez, C.R.; Lagos, G.R. An Experimental Comparison of Arduino IDE Compatible Platforms for Digital Control and Data Acquisition Applications. In Proceedings of the 2019 IEEE CHILEAN Conference on Electrical, Electronics Engineering, Information and Communication Technologies (CHILECON), Valparaiso, Chile, 13–27 November 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Bulgakov, A.L.; Aleshina, A.V.; Smirnov, S.D.; Demidov, A.D.; Milyutin, M.A.; Xin, Y. Scalability and Security in Blockchain Networks: Evaluation of Sharding Algorithms and Prospects for Decentralized Data Storage. Mathematics 2024, 12, 3860. [Google Scholar] [CrossRef]
- Haque, E.U.; Abbasi, W.; Almogren, A.; Choi, J.; Altameem, A.; Rehman, A.U.; Hamam, H. Performance enhancement in blockchain based IoT data sharing using lightweight consensus algorithm. Sci. Rep. 2024, 14, 26561. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Maiti, A.; Kist, A.A. A Zero-Trust Multi-Processor Reporter-Verifier Design of Edge Devices for Firmware Authenticity in Internet of Things and Blockchain Applications. J. Sens. Actuator Netw. 2025, 14, 35. https://doi.org/10.3390/jsan14020035
Maiti A, Kist AA. A Zero-Trust Multi-Processor Reporter-Verifier Design of Edge Devices for Firmware Authenticity in Internet of Things and Blockchain Applications. Journal of Sensor and Actuator Networks. 2025; 14(2):35. https://doi.org/10.3390/jsan14020035
Chicago/Turabian StyleMaiti, Ananda, and Alexander A. Kist. 2025. "A Zero-Trust Multi-Processor Reporter-Verifier Design of Edge Devices for Firmware Authenticity in Internet of Things and Blockchain Applications" Journal of Sensor and Actuator Networks 14, no. 2: 35. https://doi.org/10.3390/jsan14020035
APA StyleMaiti, A., & Kist, A. A. (2025). A Zero-Trust Multi-Processor Reporter-Verifier Design of Edge Devices for Firmware Authenticity in Internet of Things and Blockchain Applications. Journal of Sensor and Actuator Networks, 14(2), 35. https://doi.org/10.3390/jsan14020035






