A Review of Research on Privacy Protection of Internet of Vehicles Based on Blockchain
Abstract
1. Introduction
- We classify the most recent study on blockchain-based privacy protection in the IoV according to the types of privacy to be safeguarded.
- A categorization of the mentioned blockchain-based privacy protection schemes for IoV is provided, considering the type of blockchain adopted by the scheme and the blockchain framework used at the bottom.
- We summarize the shortcomings and research challenges in prior solutions and envision potential research directions for future work.
2. Research Methodology
2.1. The Research Method
OR “Cooperative and Intelligent Transport Systems”
AND blockchain AND privacy) AND(LIMIT-TO(SUBJAREA, “COMP”))
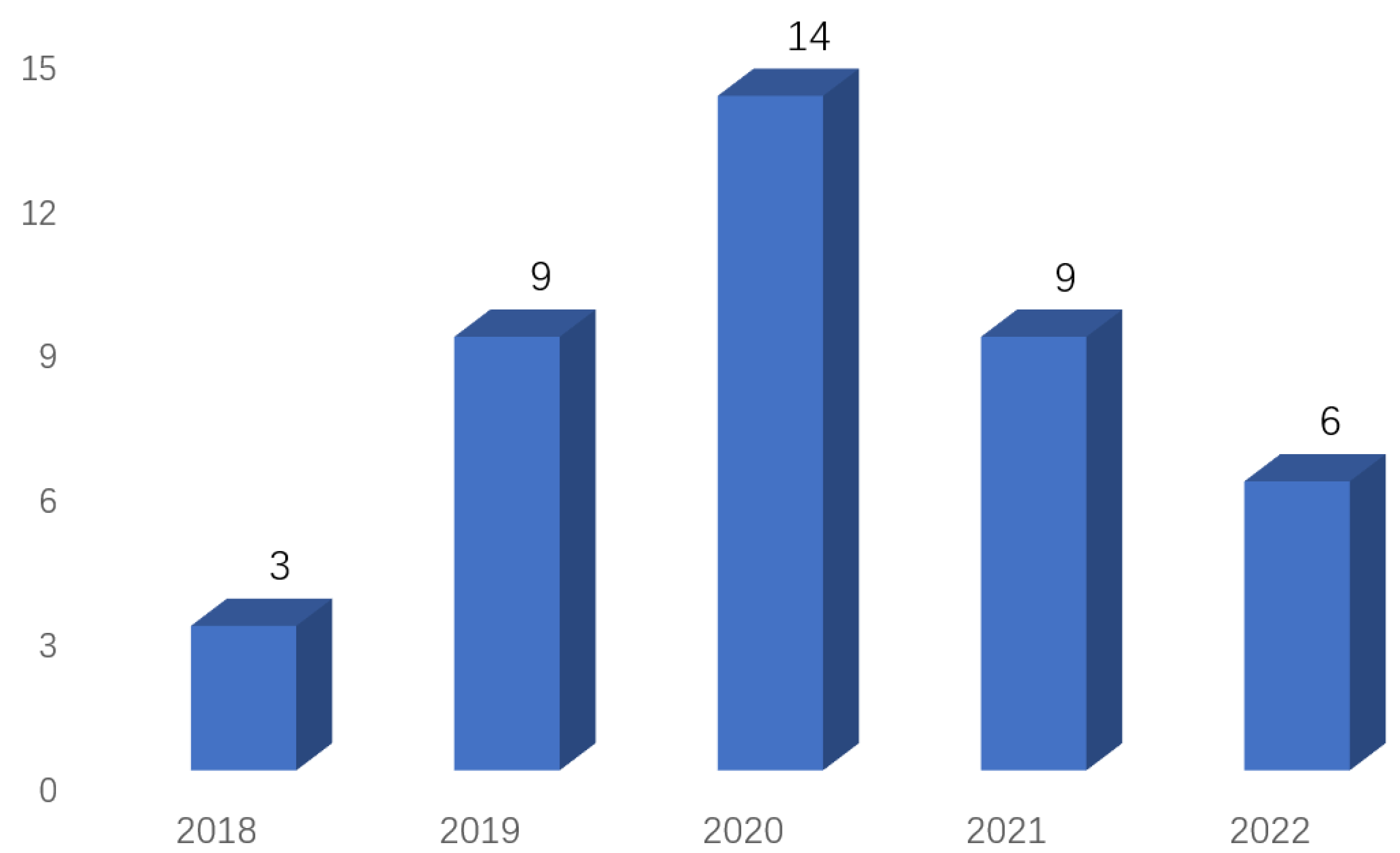
2.2. Analysis of Results
3. Background
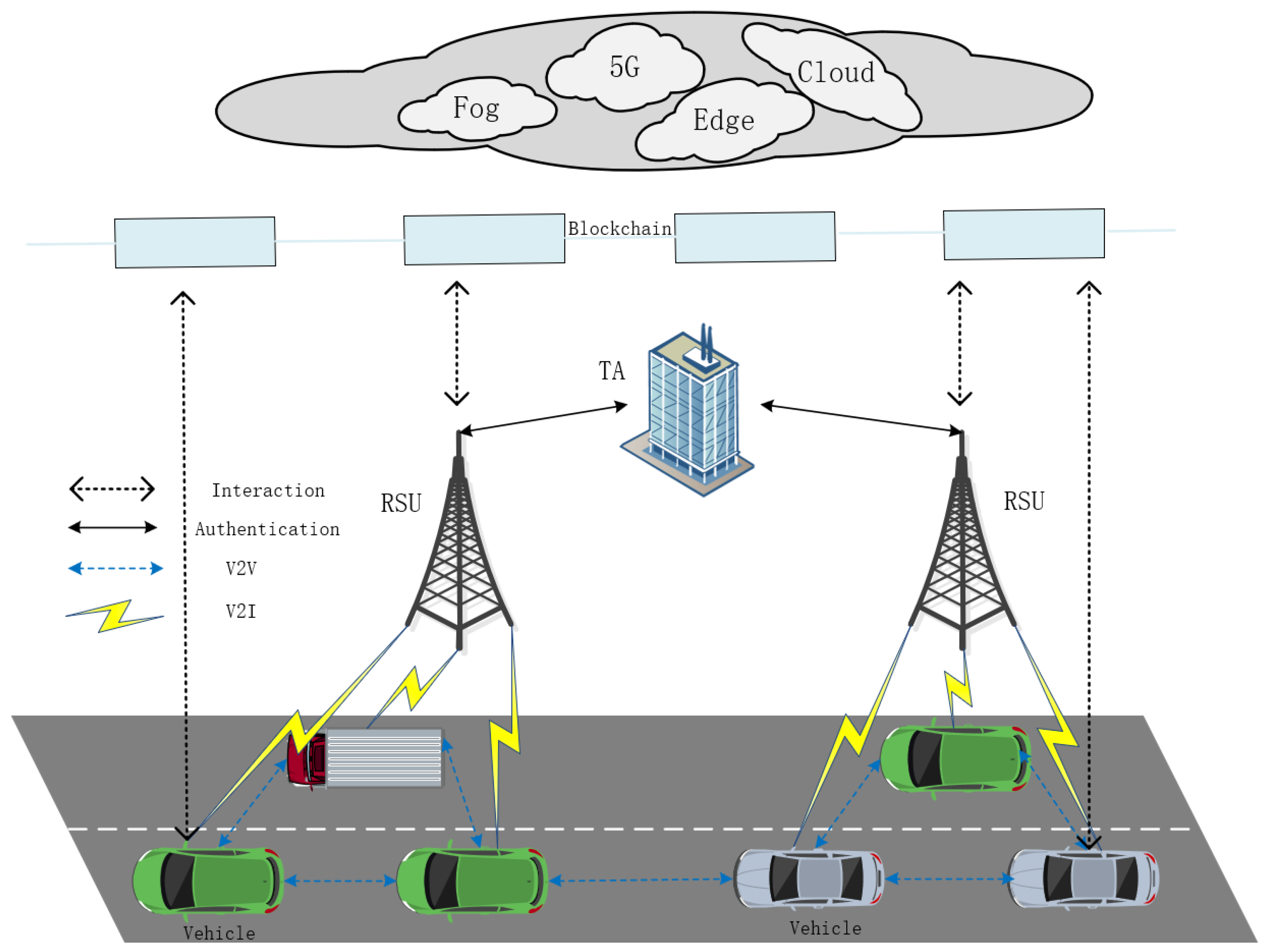
3.1. Internet of Vehicles
- Trusted authority (TA): The city’s vehicle registration and management center is a trusted third party. It is responsible for vehicle registration and the revocation of malicious vehicles, such as those reported by certain vehicles after being identified, to send false information about roads, traffic, or the environment. Additionally, it provides deployment and maintenance of smart contracts for vehicle registration and cancellation. TA is an entity with strong computational and communication capabilities and is totally trusted by the system. It is the sole entity that knows the true identity of the vehicle.
- RSU: RSUs can communicate directly with vehicles in radio range and transmit messages to TAs or central servers. The RSU is responsible for verifying the legitimacy of the vehicle and assigning regional secrets to verified vehicles. The RSU is semi-trustworthy, meaning that it would follow the specified interaction protocol, but may want to know the private information about the vehicles due to curiosity or being attacked (e.g., once an adversary attacks the RSU, it can access the vehicle’s authentication information).
- Vehicle: The vehicle’s on-board unit (OBU) is installed, which also has a communication and computing unit. In IoV, vehicles must be authenticated before communicating with other vehicles or posting messages. Otherwise, the messages sent are regarded as invalid and discarded.
- Blockchain: The blockchain is a decentralized and trustworthy platform that ensures the integrity of data. Registration data will be uploaded on the blockchain so that users and RSUs can quickly search the recorded data. Transaction information is connected to secure the authenticity, validity, and immutability of shared multimedia material.
3.2. Blockchain
3.2.1. Introduction to Blockchain
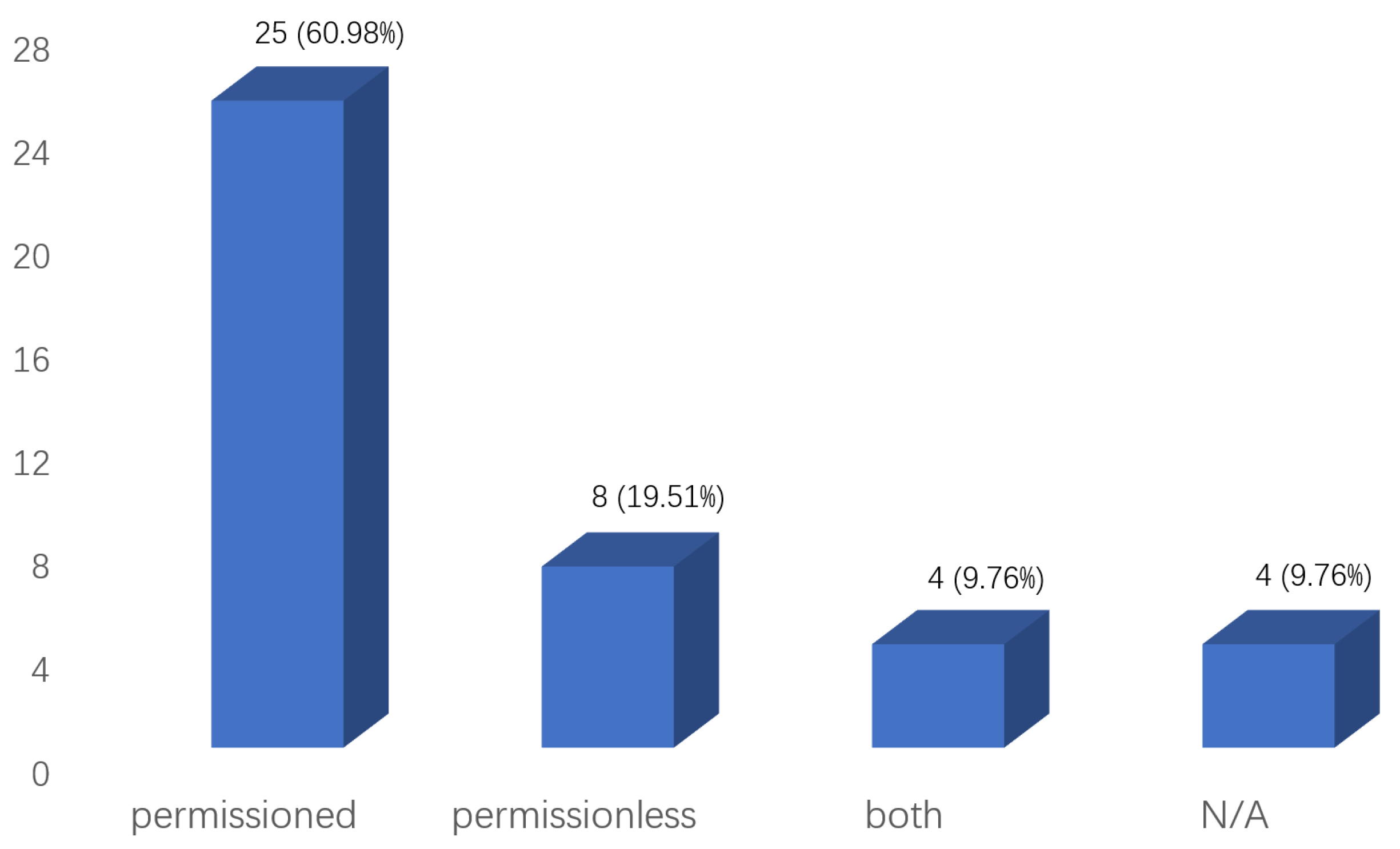
- Public chain: No complex requirements exist for the participation authority of the public chain, and any individual or organization can join and leave freely. All data records on the public chain are open and transparent, and anybody may participate in the consensus procedure. The public chain is an institution-free blockchain that is entirely decentralized. The most typical representative of the public chain is the Bitcoin system. The system is open to everyone, and the information in the Bitcoin system is completely open and transparent.
- Private chain: Also known as an internal chain, it is a non-public “chain” that usually requires authorization to join the nodes and has a shallow degree of openness. Access to write and modify data is only in the hands of insiders, and it is a single central network of private organizations. Many large groups of companies are currently developing their private chains, which can be used for corporate management, financial auditing, bank clearing, settlement, etc.
- Consortium chain: It is jointly participated by multiple organizations and has an excellent cooperative relationship with each other. The degree of openness of the consortium chain is between the public and private chains, and the writing and modification rights are still in the hands of multiple organizations. It is regarded as a partially decentralized blockchain. The participants of the consortium chain have a high degree of mutual trust, where the verification efficiency is fast, the transaction cost is significantly reduced compared with the public chain, and part of the data privacy can be well-protected. Consortium members can only share the information and resources on the consortium chain. The well-known consortium chain includes the R3 blockchain [20] and Hyperledger Fabric [21]. In a blockchain, a consensus result is reached between multiple nodes for a particular state mainly through a consensus algorithm.
3.2.2. The Reason Why Blockchain Can Be Combined with the IoV
- Data integrity—guaranteeing that messages exchanged are protected from alteration or modification by attackers;
- Vehicle authentication—recognizing valid vehicles and making sure they are what they claim to be;
- Vehicle privacy and anonymity—guaranteeing that the vehicle’s private information is not leaked and cannot be traced by attackers;
- Access control—granting access to data and services of various entities in the network.
- Decentralization: BC is a distributed system without a centralized authority that is able to offer a secure solution.
- Cryptocurrency: Many BC ledgers offer cryptocurrency exchange services. Vehicle cooperation can be effectively facilitated by developing efficient, secure, and automated incentives.
- Transparency: All nodes in the BC network have access to the contents of the BC ledger.
- Pseudonymity: Each BC user is associated with an anonymous address. This method enables the deployment of privacy protection services.
- Availability: As a result of the BC decentralization, there is no single failure point. This significantly increases the system’s availability and dependability.
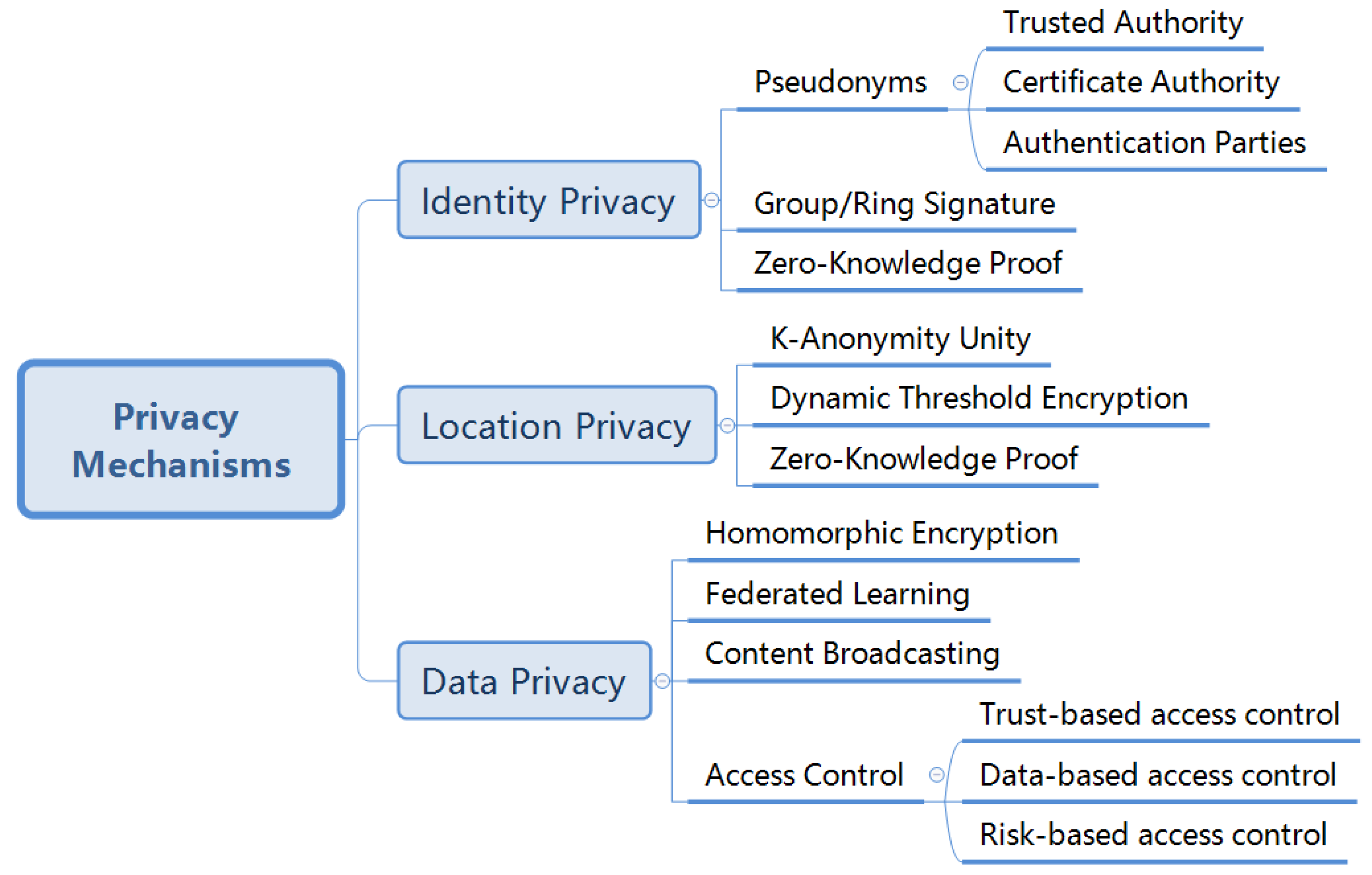
4. Privacy Protection Scheme for IoV on Blockchain
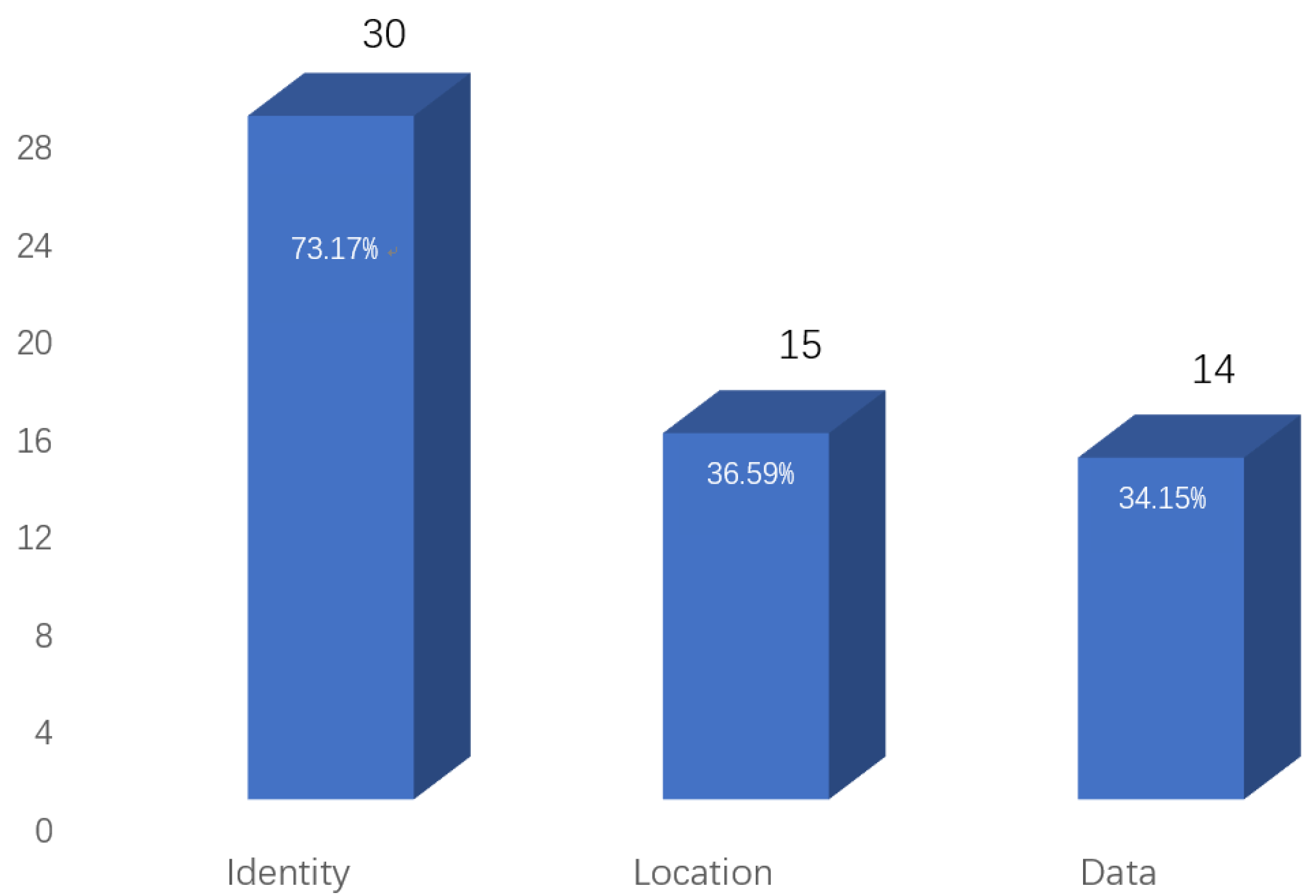
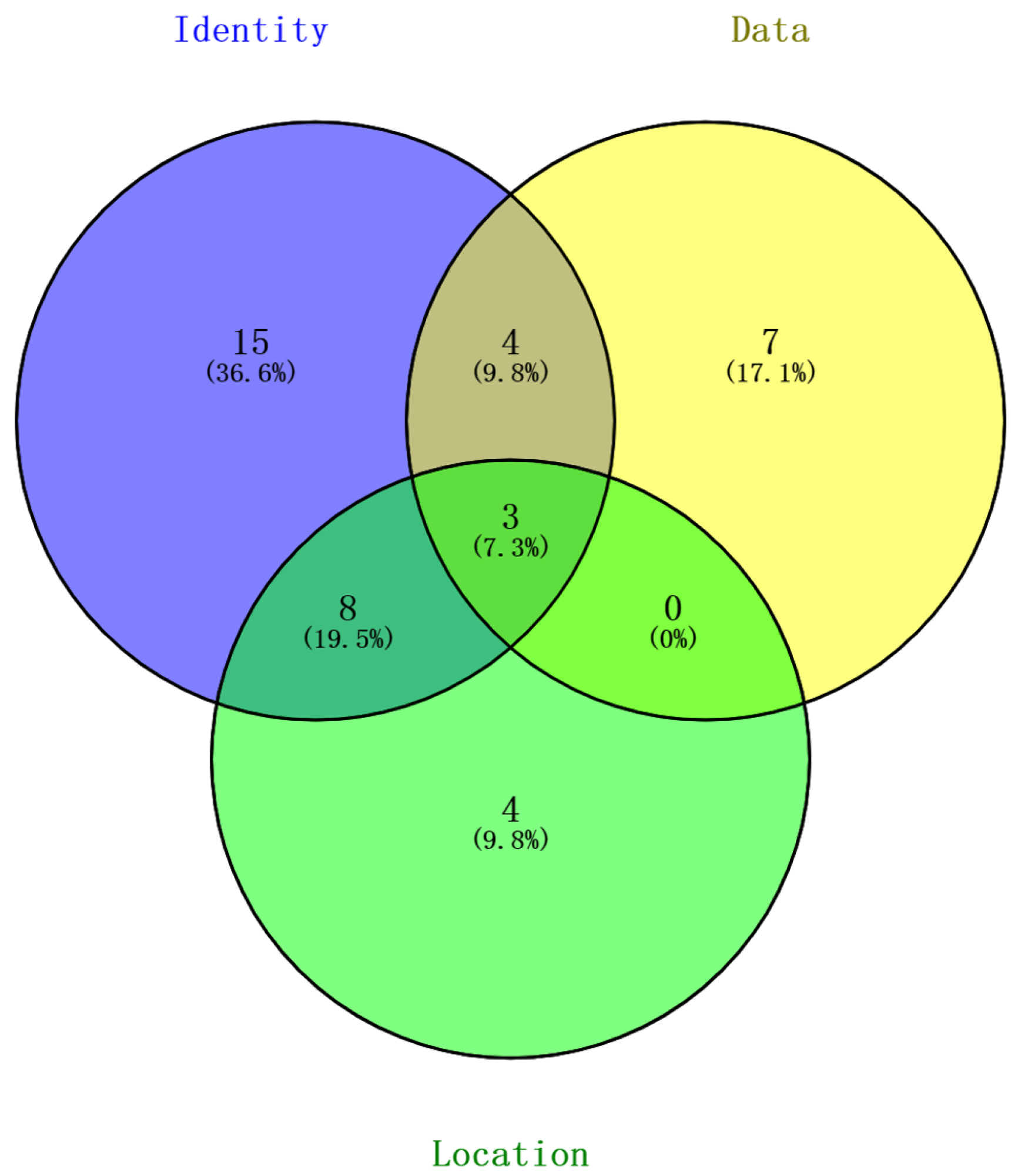
- Identity privacy: It protects the user’s true identity from disclosure, mainly through using pseudonyms during in-vehicle system communications.
- Location privacy: It safeguards the user’s location information, often using camouflage and clustering techniques.
- Data privacy: It secures personal user data, such as vehicle trajectories, speeds, and temporary messages among vehicles. For data privacy, encryption techniques, such as homomorphic encryption, are utilized.
4.1. Identity Privacy
4.2. Location Privacy
4.3. Data Privacy
5. Research Challenges
- Many of the above proposed solutions are still based on simulations and simple experiments and rely on limited hardware equipment, which makes it difficult to apply the existing solutions in practice. In addition, it is a question of how to better integrate blockchain technology into the existing infrastructure while considering the cost. To do this, we need to further optimize the hardware and software requirements.
- Blockchain is effective in decentralization and security, but its system throughput is very limited and throughput is a quantitative indicator of the scalability of blockchain systems, which is one of the difficulties to be overcome by current blockchain technology. For this reason, we need to improve the scalability of blockchain, for example, by improving the read performance of blockchain, using more efficient sharing techniques, designing secure directed acyclic graphs (DAGs), and reducing the storage volume by employing the coding theories. Moreover, there is a need for developing a scalable blockchain-based approach for authentication and access control for new IoV architectures, such as the software-defined vehicular networks.
- As the number of vehicles increases, data transmission becomes more widespread and the amount of data becomes more massive. It is a great challenge to provide low-latency IoV services in such a large volume. In the future, we have to develop higher speed communication networks to reduce the transmission latency between data and optimize the communication architecture.
- The one-wayness of cryptographic hashing provides blockchain immutability as its core advantage. With the emergence of quantum computing, the immutability may be compromised. However, it also offers opportunity. In the future years, quantum computing will have widespread application sources [69], for which we can combine quantum computing with new technologies. Additionally, edge computing can be applied in blockchain to enhance data analysis performance, which can be incorporated with anti-quantum security protocols to improve the security of vehicle nodes. Moreover, deep learning and reinforcement learning may be integrated with blockchain technology to enhance system security.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zeadally, S.; Hunt, R.; Chen, Y.S.; Irwin, A.; Hassan, A. Vehicular ad hoc networks (VANETS): Status, results, and challenges. Telecommun. Syst. 2012, 50, 217–241. [Google Scholar] [CrossRef]
- Al-Sultan, S.; Al-Doori, M.M.; Al-Bayatti, A.H.; Zedan, H. A comprehensive survey on vehicular ad hoc network. J. Netw. Comput. Appl. 2014, 37, 380–392. [Google Scholar] [CrossRef]
- Tangade, S.S.; Manvi, S.S. A survey on attacks, security and trust management solutions in VANETs. In Proceedings of the 2013 Fourth International Conference on Computing, Communications and Networking Technologies (ICCCNT), Tiruchengode, India, 4–6 July 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Garg, T.; Kagalwalla, N.; Churi, P.; Pawar, A.; Deshmukh, S. A survey on security and privacy issues in IoV. Int. J. Electr. Comput. Eng. 2020, 10, 5409–5419. [Google Scholar] [CrossRef]
- Luckshetty, A.; Dontal, S.; Tangade, S.; Manvi, S.S. A survey: Comparative study of applications, attacks, security and privacy in VANETs. In Proceedings of the 2016 International Conference on Communication and Signal Processing (ICCSP), Melmaruvathur, India, 6–8 April 2016; pp. 1594–1598. [Google Scholar] [CrossRef]
- Sağlam, E.T.; Bahtiyar, S. A Survey: Security and Privacy in 5G Vehicular Networks. In Proceedings of the 2019 4th International Conference on Computer Science and Engineering (UBMK), Samsun, Turkey, 11–15 September 2019; pp. 108–112. [Google Scholar] [CrossRef]
- Mathew, D.; Roy, H.A. A survey on different privacy-preserving authentication schemes in VANET. IOP Conf. Ser. Mater. Sci. Eng. 2018, 396, 012033. [Google Scholar] [CrossRef]
- Lu, Z.; Qu, G.; Liu, Z. A Survey on Recent Advances in Vehicular Network Security, Trust, and Privacy. IEEE Trans. Intell. Transp. Syst. 2019, 20, 760–776. [Google Scholar] [CrossRef]
- Talat, H.; Nomani, T.; Mohsin, M.; Sattar, S. A Survey on Location Privacy Techniques Deployed in Vehicular Networks. In Proceedings of the 2019 16th International Bhurban Conference on Applied Sciences and Technology (IBCAST), Islamabad, Pakistan, 8–12 January 2019; pp. 604–613. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. Security and privacy in vehicular ad hoc network and vehicle cloud computing: A survey. Wirel. Commun. Mob. Comput. 2020, 2020, 5129620. [Google Scholar] [CrossRef]
- Mendiboure, L.; Chalouf, M.A.; Krief, F. Survey on blockchain-based applications in internet of vehicles. Comput. Electr. Eng. 2020, 84, 106646. [Google Scholar] [CrossRef]
- Kaltakis, K.; Polyzi, P.; Drosatos, G.; Rantos, K. Privacy-Preserving Solutions in Blockchain-Enabled Internet of Vehicles. Appl. Sci. 2021, 11, 9792. [Google Scholar] [CrossRef]
- Yaga, D.; Mell, P.; Roby, N.; Scarfone, K. Blockchain technology overview. arXiv 2019, arXiv:1906.11078. [Google Scholar]
- Kaiwartya, O.; Abdullah, A.H.; Cao, Y.; Altameem, A.; Prasad, M.; Lin, C.T.; Liu, X. Internet of Vehicles: Motivation, Layered Architecture, Network Model, Challenges, and Future Aspects. IEEE Access 2016, 4, 5356–5373. [Google Scholar] [CrossRef]
- Manivannan, D.; Moni, S.S.; Zeadally, S. Secure authentication and privacy-preserving techniques in Vehicular Ad-hoc NETworks (VANETs). Veh. Commun. 2020, 25, 100247. [Google Scholar] [CrossRef]
- Mundhe, P.; Verma, S.; Venkatesan, S. A comprehensive survey on authentication and privacy-preserving schemes in VANETs. Comput. Sci. Rev. 2021, 41, 100411. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System; Decentralized Business Review. 2008, p. 21260. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 16 October 2022).
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Buterin. On Public and Private Blockchains. 2015. Available online: https://blog.ethereum.org/2015/08/07/on-public-and-private-blockchains (accessed on 16 October 2022).
- Brown, R.G. The corda platform: An introduction. Retrieved 2018, 27, 2018. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; 26 April 2018; pp. 1–15. [Google Scholar]
- Abassi, R. VANET security and forensics: Challenges and opportunities. Wiley Interdiscip. Rev. Forensic Sci. 2019, 1, e1324. [Google Scholar] [CrossRef]
- Sun, G.; Chang, V.; Ramachandran, M.; Sun, Z.; Li, G.; Yu, H.; Liao, D. Efficient location privacy algorithm for Internet of Things (IoT) services and applications. J. Netw. Comput. Appl. 2017, 89, 3–13. [Google Scholar] [CrossRef]
- Sun, G.; Xie, Y.; Liao, D.; Yu, H.; Chang, V. User-defined privacy location-sharing system in mobile online social networks. J. Netw. Comput. Appl. 2017, 86, 34–45. [Google Scholar] [CrossRef]
- Kalaiarasy, C.; Sreenath, N.; Amuthan, A. Location privacy preservation in VANET using mix zones—A survey. In Proceedings of the 2019 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 23–25 January 2019; pp. 1–5. [Google Scholar]
- Contreras-Castillo, J.; Zeadally, S.; Guerrero-Ibañez, J.A. Internet of Vehicles: Architecture, Protocols, and Security. IEEE Internet Things J. 2018, 5, 3701–3709. [Google Scholar] [CrossRef]
- Liu, Y.N.; Lv, S.Z.; Xie, M.; Chen, Z.B.; Wang, P. Dynamic anonymous identity authentication (DAIA) scheme for VANET. Int. J. Commun. Syst. 2019, 32, e3892. [Google Scholar] [CrossRef]
- Guehguih, B.; Lu, H. Blockchain-based privacy-preserving authentication and message dissemination scheme for vanet. In Proceedings of the 2019 5th International Conference on Systems, Control and Communications, Wuhan, China, 21–23 December 2019; pp. 16–21. [Google Scholar]
- Shi, K.; Zhu, L.; Zhang, C.; Xu, L.; Gao, F. Blockchain-based multimedia sharing in vehicular social networks with privacy protection. Multimed. Tools Appl. 2020, 79, 8085–8105. [Google Scholar] [CrossRef]
- Yang, H.; Li, Y. A Blockchain-Based Anonymous Authentication Scheme for Internet of Vehicles. Procedia Comput. Sci. 2022, 201, 413–420. [Google Scholar] [CrossRef]
- Sharma, R.; Chakraborty, S. BlockAPP: Using Blockchain for Authentication and Privacy Preservation in IoV. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Moussaoui, D.; Kadri, B.; Feham, M.; Ammar Bensaber, B. A Distributed Blockchain Based PKI (BCPKI) architecture to enhance privacy in VANET. In Proceedings of the 2020 2nd International Workshop on Human-Centric Smart Environments for Health and Well-being (IHSH), Boumerdes, Algeria, 9–10 February 2021; pp. 75–79. [Google Scholar] [CrossRef]
- Bao, S.; Lei, A.; Cruickshank, H.; Sun, Z.; Asuquo, P.; Hathal, W. A Pseudonym Certificate Management Scheme Based on Blockchain for Internet of Vehicles. In Proceedings of the 2019 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Fukuoka, Japan, 5–8 August 2019; pp. 28–35. [Google Scholar] [CrossRef]
- Akhter, A.S.; Ahmed, M.; Shah, A.S.; Anwar, A.; Zengin, A. A secured privacy-preserving multi-level blockchain framework for cluster based VANET. Sustainability 2021, 13, 400. [Google Scholar] [CrossRef]
- Mei, Q.; Xiong, H.; Zhao, Y.; Yeh, K.H. Toward Blockchain-Enabled IoV with Edge Computing: Efficient and Privacy-Preserving Vehicular Communication and Dynamic Updating. In Proceedings of the 2021 IEEE Conference on Dependable and Secure Computing (DSC), Aizuwakamatsu, Japan, 30 January–2 February 2021; pp. 1–8. [Google Scholar] [CrossRef]
- Akhter, A.S.; Ahmed, M.; Shah, A.S.; Anwar, A.; Kayes, A.; Zengin, A. A blockchain-based authentication protocol for cooperative vehicular ad hoc network. Sensors 2021, 21, 1273. [Google Scholar] [CrossRef] [PubMed]
- Li, L.; Liu, J.; Cheng, L.; Qiu, S.; Wang, W.; Zhang, X.; Zhang, Z. Creditcoin: A privacy-preserving blockchain-based incentive announcement network for communications of smart vehicles. IEEE Trans. Intell. Transp. Syst. 2018, 19, 2204–2220. [Google Scholar] [CrossRef]
- Lee, J.; Lee, J.; Park, H. A Privacy Preserving Blockchain-based Reward Solution for Vehicular Networks. In Proceedings of the 2020 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 4–6 January 2020; pp. 1–4. [Google Scholar] [CrossRef]
- George, S.A.; Jaekel, A.; Saini, I. Secure Identity Management Framework for Vehicular Ad-hoc Network using Blockchain. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Shrivastava, A.L.; Dwivedi, R.K. A Secure Design of the Smart Vehicular IoT System using Blockchain Technology. In Proceedings of the 2022 9th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 23–25 March 2022; pp. 616–620. [Google Scholar]
- Zheng, D.; Jing, C.; Guo, R.; Gao, S.; Wang, L. A traceable blockchain-based access authentication system with privacy preservation in VANETs. IEEE Access 2019, 7, 117716–117726. [Google Scholar] [CrossRef]
- Zhang, J.; Yang, F.; Ma, Z.; Wang, Z.; Liu, X.; Ma, J. A Decentralized Location Privacy-Preserving Spatial Crowdsourcing for Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 22, 2299–2313. [Google Scholar] [CrossRef]
- Su, T.; Shao, S.; Guo, S.; Lei, M. Blockchain-based internet of vehicles privacy protection system. Wirel. Commun. Mob. Comput. 2020, 2020, 8870438. [Google Scholar] [CrossRef]
- Li, B.; Liang, R.; Zhu, D.; Chen, W.; Lin, Q. Blockchain-Based Trust Management Model for Location Privacy Preserving in VANET. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3765–3775. [Google Scholar] [CrossRef]
- Chaudhary, B.; Singh, K. A Blockchain enabled location-privacy preserving scheme for vehicular ad-hoc networks. Peer-to-Peer Netw. Appl. 2021, 14, 3198–3212. [Google Scholar] [CrossRef]
- Liang, R.; Li, B.; Song, X. Blockchain-based privacy preserving trust management model in VANET. In Proceedings of the International Conference on Advanced Data Mining and Applications, Foshan, China, 12–14 November 2020; pp. 465–479. [Google Scholar]
- Li, H.; Pei, L.; Liao, D.; Sun, G.; Xu, D. Blockchain meets VANET: An architecture for identity and location privacy protection in VANET. Peer-to-Peer Netw. Appl. 2019, 12, 1178–1193. [Google Scholar] [CrossRef]
- Li, B.; Liang, R.; Zhou, W.; Yin, H.; Gao, H.; Cai, K. LBS meets blockchain: An efficient method with security preserving trust in SAGIN. IEEE Internet Things J. 2021, 9, 5932–5942. [Google Scholar] [CrossRef]
- Feng, J.; Wang, Y.; Wang, J.; Ren, F. Blockchain-Based Data Management and Edge-Assisted Trusted Cloaking Area Construction for Location Privacy Protection in Vehicular Networks. IEEE Internet Things J. 2021, 8, 2087–2101. [Google Scholar] [CrossRef]
- Gabay, D.; Akkaya, K.; Cebe, M. Privacy-Preserving Authentication Scheme for Connected Electric Vehicles Using Blockchain and Zero Knowledge Proofs. IEEE Trans. Veh. Technol. 2020, 69, 5760–5772. [Google Scholar] [CrossRef]
- Li, M.; Weng, J.; Yang, A.; Liu, J.N.; Lin, X. Toward blockchain-based fair and anonymous ad dissemination in vehicular networks. IEEE Trans. Veh. Technol. 2019, 68, 11248–11259. [Google Scholar] [CrossRef]
- Li, H.; Li, J.; Zhao, H.; He, S.; Hu, T. Blockchain-Based Incentive Mechanism for Spectrum Sharing in IoV. Wirel. Commun. Mob. Comput. 2022, 2022, 6807257. [Google Scholar] [CrossRef]
- Wang, H.; Wang, C.; Shen, Z.; Liu, K.; Liu, P.; Lin, D. A MADM Location Privacy Protection Method Based on Blockchain. IEEE Access 2021, 9, 27802–27812. [Google Scholar] [CrossRef]
- Chen, X.; Ding, J.; Lu, Z. A Decentralized Trust Management System for Intelligent Transportation Environments. IEEE Trans. Intell. Transp. Syst. 2022, 23, 558–571. [Google Scholar] [CrossRef]
- Yao, Y.; Chen, W.; Chen, X.; Ding, J.; Pan, S. A Blockchain-based Privacy Preserving Scheme for Vehicular Trust Management Systems. In Proceedings of the 2020 International Conference on Internet of Things and Intelligent Applications (ITIA), Zhenjiang, China, 27–29 November 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Cheng, L.; Liu, J.; Xu, G.; Zhang, Z.; Wang, H.; Dai, H.N.; Wu, Y.; Wang, W. SCTSC: A Semicentralized Traffic Signal Control Mode With Attribute-Based Blockchain in IoVs. IEEE Trans. Comput. Soc. Syst. 2019, 6, 1373–1385. [Google Scholar] [CrossRef]
- Ma, Z.; Wang, L.; Zhao, W. Blockchain-Driven Trusted Data Sharing With Privacy Protection in IoT Sensor Network. IEEE Sens. J. 2021, 21, 25472–25479. [Google Scholar] [CrossRef]
- Li, H.; Pei, L.; Liao, D.; Chen, S.; Zhang, M.; Xu, D. FADB: A Fine-Grained Access Control Scheme for VANET Data Based on Blockchain. IEEE Access 2020, 8, 85190–85203. [Google Scholar] [CrossRef]
- Li, W.; Guo, H.; Nejad, M.; Shen, C.C. Privacy-Preserving Traffic Management: A Blockchain and Zero-Knowledge Proof Inspired Approach. IEEE Access 2020, 8, 181733–181743. [Google Scholar] [CrossRef]
- Ma, X.; Ge, C.; Liu, Z. Blockchain-enabled privacy-preserving Internet of vehicles: Decentralized and reputation-based network architecture. In Proceedings of the International Conference on Network and System Security, Sapporo, Japan, 15–18 December 2019; pp. 336–351. [Google Scholar]
- Patel, A.; Shah, N.; Limbasiya, T.; Das, D. Vehiclechain: Blockchain-based vehicular data transmission scheme for smart city. In Proceedings of the 2019 IEEE International Conference on Systems, Man and Cybernetics (SMC), Bari, Italy, 6–9 October 2019; pp. 661–667. [Google Scholar]
- Wang, J.; Huang, J.; Kong, L.; Chen, G.; Zhou, D.; Rodrigues, J.J.C. A Privacy-Preserving Vehicular Data Sharing Framework atop Multi-Sharding Blockchain. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, G.; Sun, R.; Du, X.; Guizani, M. A Blockchain-based Conditional Privacy-Preserving Traffic Data Sharing in Cloud. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Zhao, Y.; Wang, Y.; Wang, P.; Yu, H. PBTM: A Privacy-Preserving Announcement Protocol With Blockchain-Based Trust Management for IoV. IEEE Syst. J. 2022, 16, 3422–3432. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Shahzad, L.; Abdelmaboud, A.; Elfadil Eisa, T.A.; Alamri, B.; Javed, I.T.; Al-Dhaqm, A.; Crespi, N. A Blockchain-Based Efficient, Secure and Anonymous Conditional Privacy-Preserving and Authentication Scheme for the Internet of Vehicles. Appl. Sci. 2022, 12, 476. [Google Scholar] [CrossRef]
- Zhang, Q.; Li, Y.; Wang, R.; Li, J.; Gan, Y.; Zhang, Y.; Yu, X. Blockchain-based asymmetric group key agreement protocol for internet of vehicles. Comput. Electr. Eng. 2020, 86, 106713. [Google Scholar] [CrossRef]
- Qian, Y.; Jiang, Y.; Hu, L.; Hossain, M.S.; Alrashoud, M.; Al-Hammadi, M. Blockchain-Based Privacy-Aware Content Caching in Cognitive Internet of Vehicles. IEEE Netw. 2020, 34, 46–51. [Google Scholar] [CrossRef]
- Qi, Y.; Hossain, M.S.; Nie, J.; Li, X. Privacy-preserving blockchain-based federated learning for traffic flow prediction. Future Gener. Comput. Syst. 2021, 117, 328–337. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Goyal, A.; Kanhere, S.S.; Guizani, N. Forthcoming applications of quantum computing: Peeking into the future. IET Quantum Commun. 2020, 1, 35–41. [Google Scholar] [CrossRef]
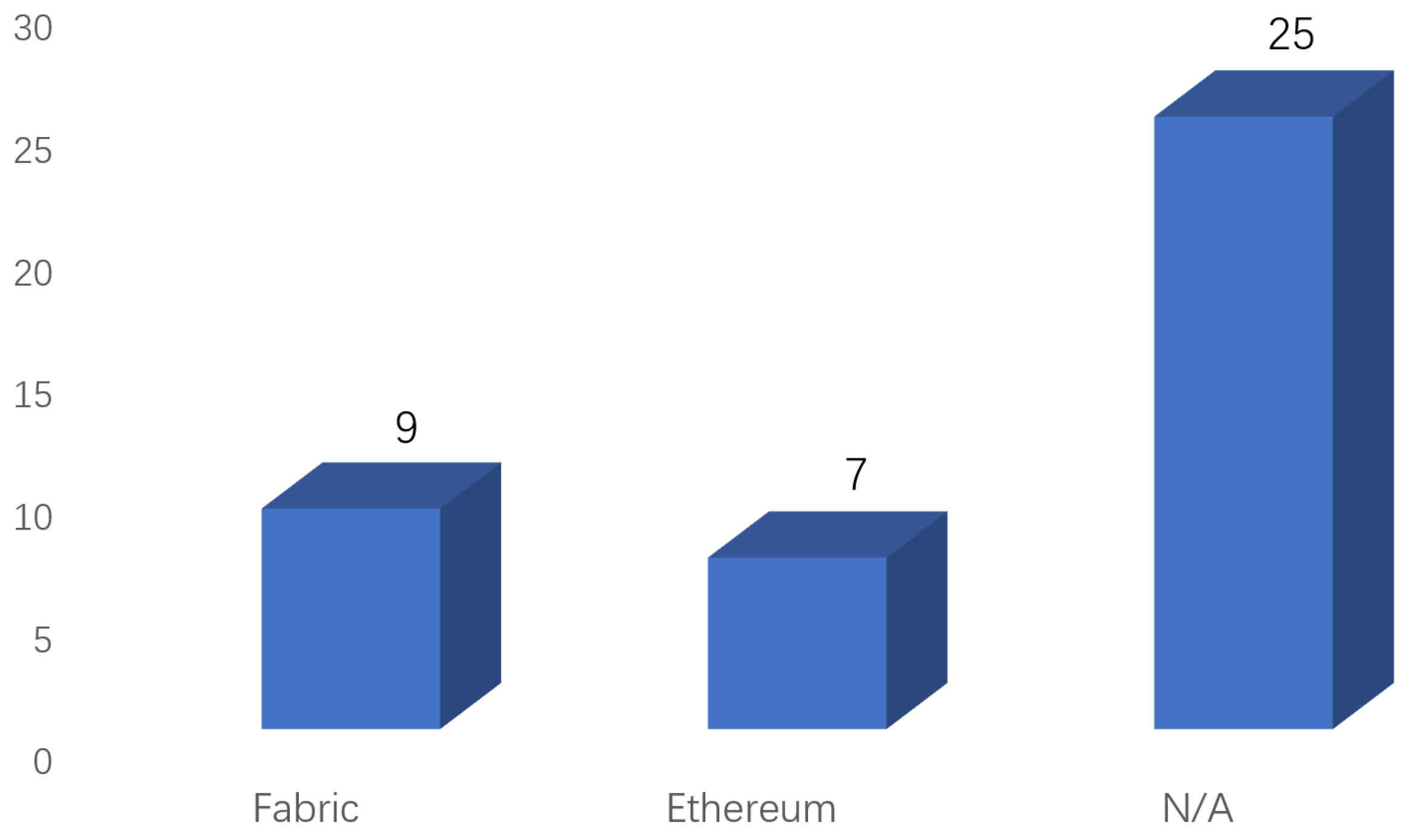
| Literature | Underlying Privacy Protection Mechanism | Blockchain Characteristic |
|---|---|---|
| [27] | Dynamic Pseudonyms (using TPD) | Permissioned |
| [28] | Pseudonyms (using Certificate Authority) | Permissioned, Permissionless |
| [29] | Pseudonyms (using Trusted Authority) | Permissionless |
| [30] | Anonymous Authentication | Permissioned |
| [31] | Pseudonyms | Permissioned |
| [32] | Pseudonyms (using Certificate Authority) | Permissionless |
| [33] | Pseudonyms Shuffling | Permissioned |
| [34] | Cluster-based Medium Access Control, Pseudonyms | Permissioned |
| [35] | Multiple One-Time Pseudonyms | Permissioned |
| [36] | Digital Signature Algorithm | Permissioned |
| [37] | Threshold Ring Signature, Combined-Public Keys | Permissioned |
| [38] | Access Control | Permissioned |
| [39] | Pseudonyms (using Certificate Authority) | Permissioned |
| [40] | Access Control | Permissioned |
| [41] | Pseudonyms (using Service Provider) | Permissionless |
| Literature | Underlying Privacy Protection Mechanism | Blockchain Characteristic |
|---|---|---|
| [42] | Additively Homomorphic Encryption | Permissioned |
| [43] | Pseudonyms (using Public Keys) | Permissionless |
| [44] | Anonymous Cloaking Regions, Pseudonyms | Permissionless |
| [45] | Pseudonyms, Random Encryption Period | Permissioned |
| [46] | Pseudonym update | Permissioned |
| [47] | K-anonymous | Permissioned |
| [48] | Digital Certificate | Permissioned |
| [49] | Dynamic threshold encryption | Permissioned |
| [50] | K-anonymous | Permissionless |
| [51] | Zero-Knowledge Proof of Knowledge | Permissioned |
| [52] | Edge calculation | Permissioned |
| [53] | Multiple-attribute decision making | Permissioned |
| Literature | Underlying Privacy Protection Mechanism | Blockchain Characteristic |
|---|---|---|
| [54,55] | Homomorphic encryption, Pseudonym update | Permissioned |
| [56] | Ciphertext-policy attribute-based encryption | Permissioned |
| [57] | Homomorphic Encryption, Zero-Knowledge Proof | Permissioned |
| [58] | CP-ABE | Permissioned |
| [59] | Zero-knowledge proof | Permissioned |
| [60] | Access control | Permissioned |
| [61] | Elliptic-curve cryptography | Permissioned |
| [62] | Zero-knowledge proof | Permissioned |
| [63] | Aggregation signature | Permissioned |
| [64] | Group signature | Permissioned |
| [65] | Anonymous Authentication | Permissioned |
| [66] | Group key | Permissioned |
| [67] | Deep learning | Permissioned |
| [68] | Federated learning | Permissioned |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, W.; Wu, H.; Chen, X.; Chen, J. A Review of Research on Privacy Protection of Internet of Vehicles Based on Blockchain. J. Sens. Actuator Netw. 2022, 11, 86. https://doi.org/10.3390/jsan11040086
Chen W, Wu H, Chen X, Chen J. A Review of Research on Privacy Protection of Internet of Vehicles Based on Blockchain. Journal of Sensor and Actuator Networks. 2022; 11(4):86. https://doi.org/10.3390/jsan11040086
Chicago/Turabian StyleChen, Wendong, Haiqin Wu, Xiao Chen, and Jinfu Chen. 2022. "A Review of Research on Privacy Protection of Internet of Vehicles Based on Blockchain" Journal of Sensor and Actuator Networks 11, no. 4: 86. https://doi.org/10.3390/jsan11040086
APA StyleChen, W., Wu, H., Chen, X., & Chen, J. (2022). A Review of Research on Privacy Protection of Internet of Vehicles Based on Blockchain. Journal of Sensor and Actuator Networks, 11(4), 86. https://doi.org/10.3390/jsan11040086











