Simulating Spatio-Temporal Patterns of Terrorism Incidents on the Indochina Peninsula with GIS and the Random Forest Method
Abstract
:1. Introduction
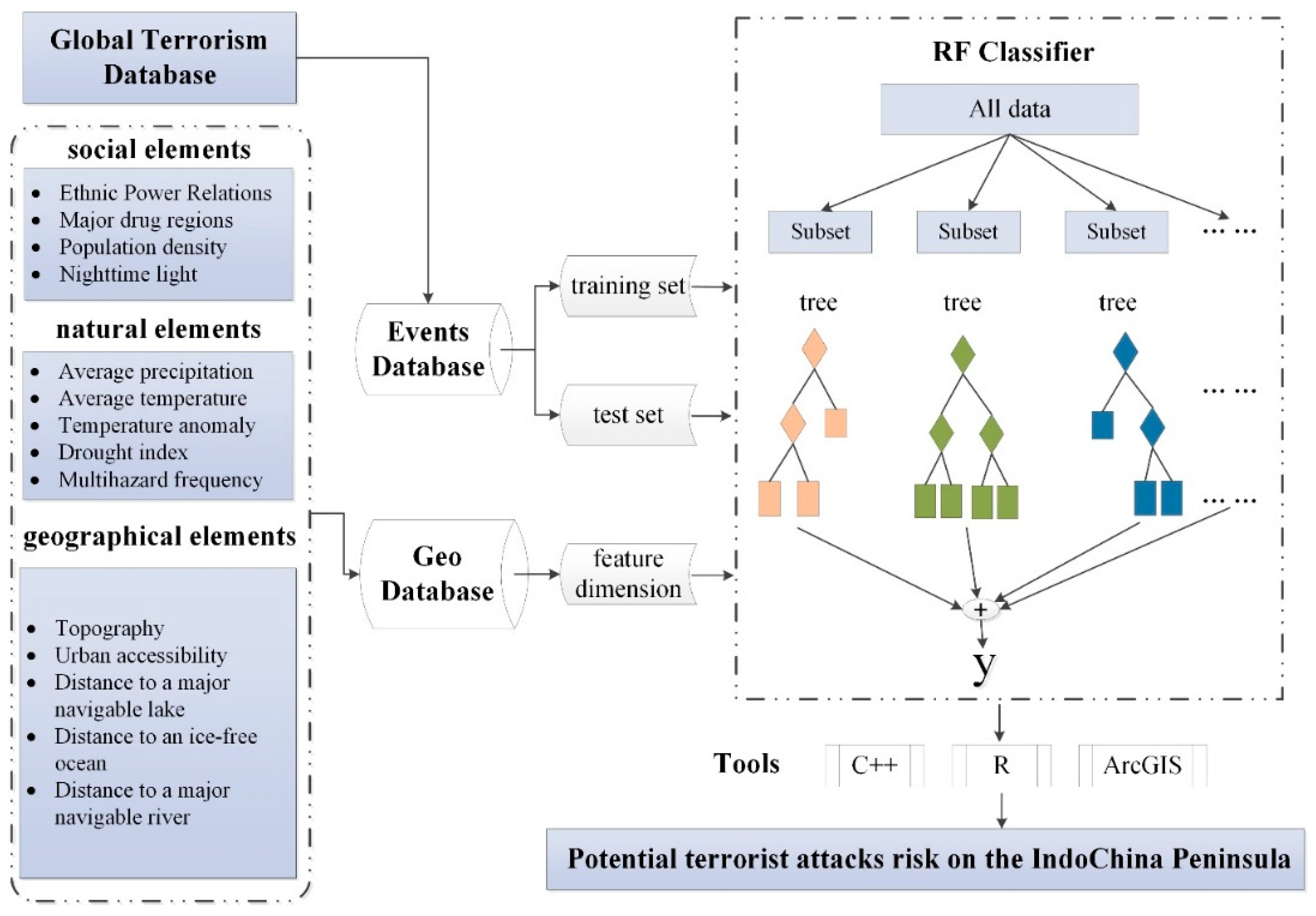
2. Materials and Methods
2.1. Feature Selection
2.2. The Events Dataset (GTD)
2.3. Kernel Density Estimation
2.4. RF Algorithm
3. Results
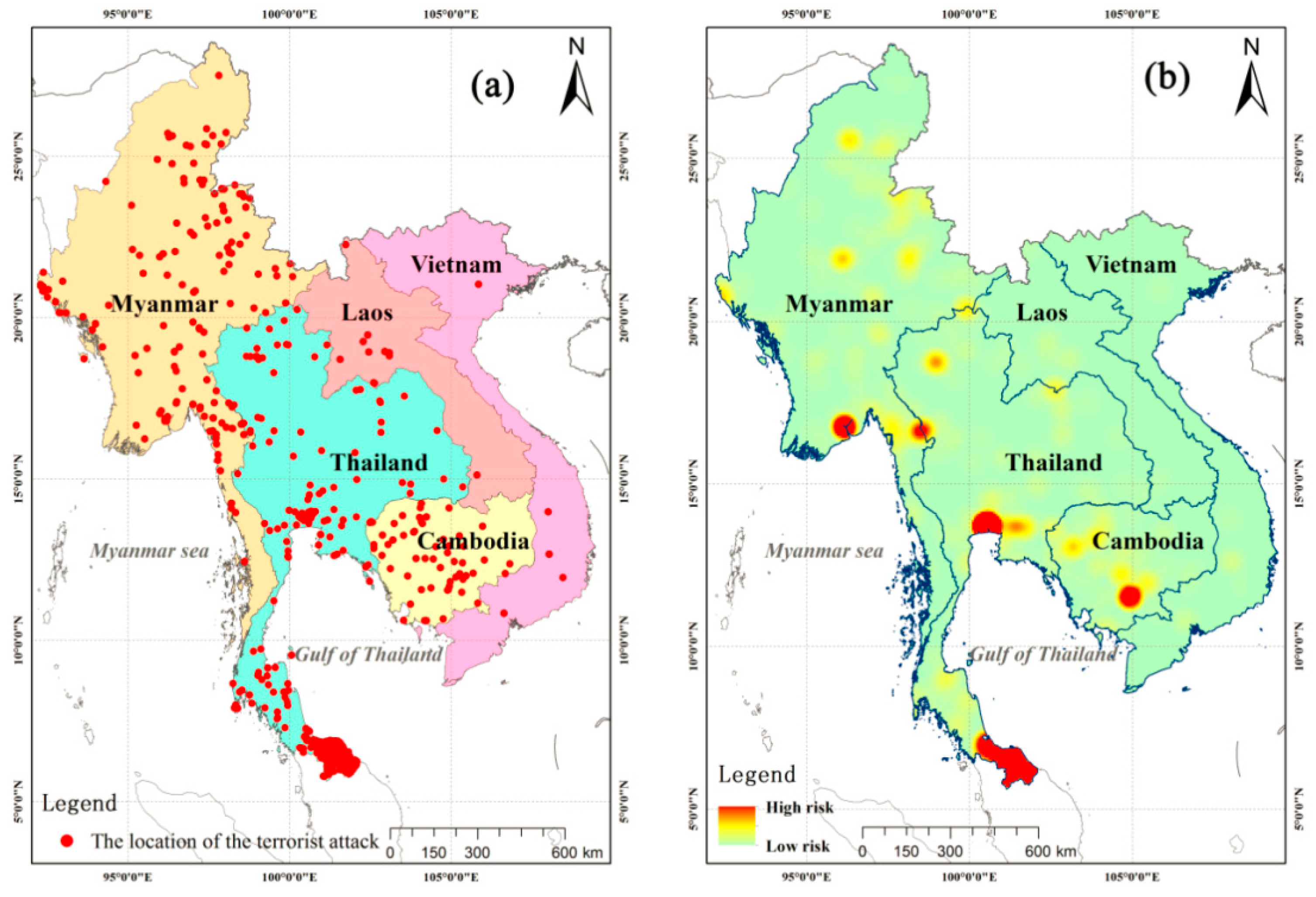
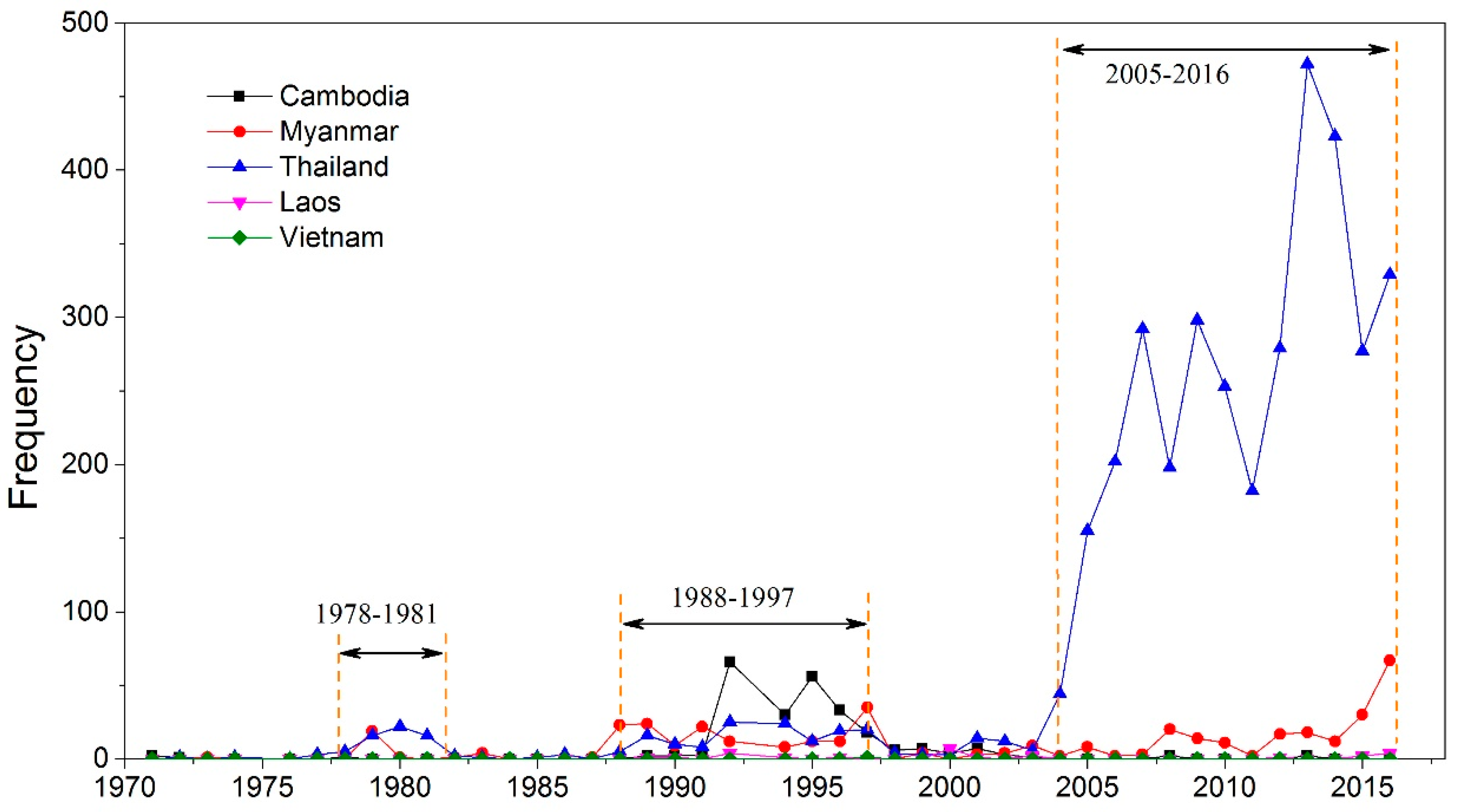
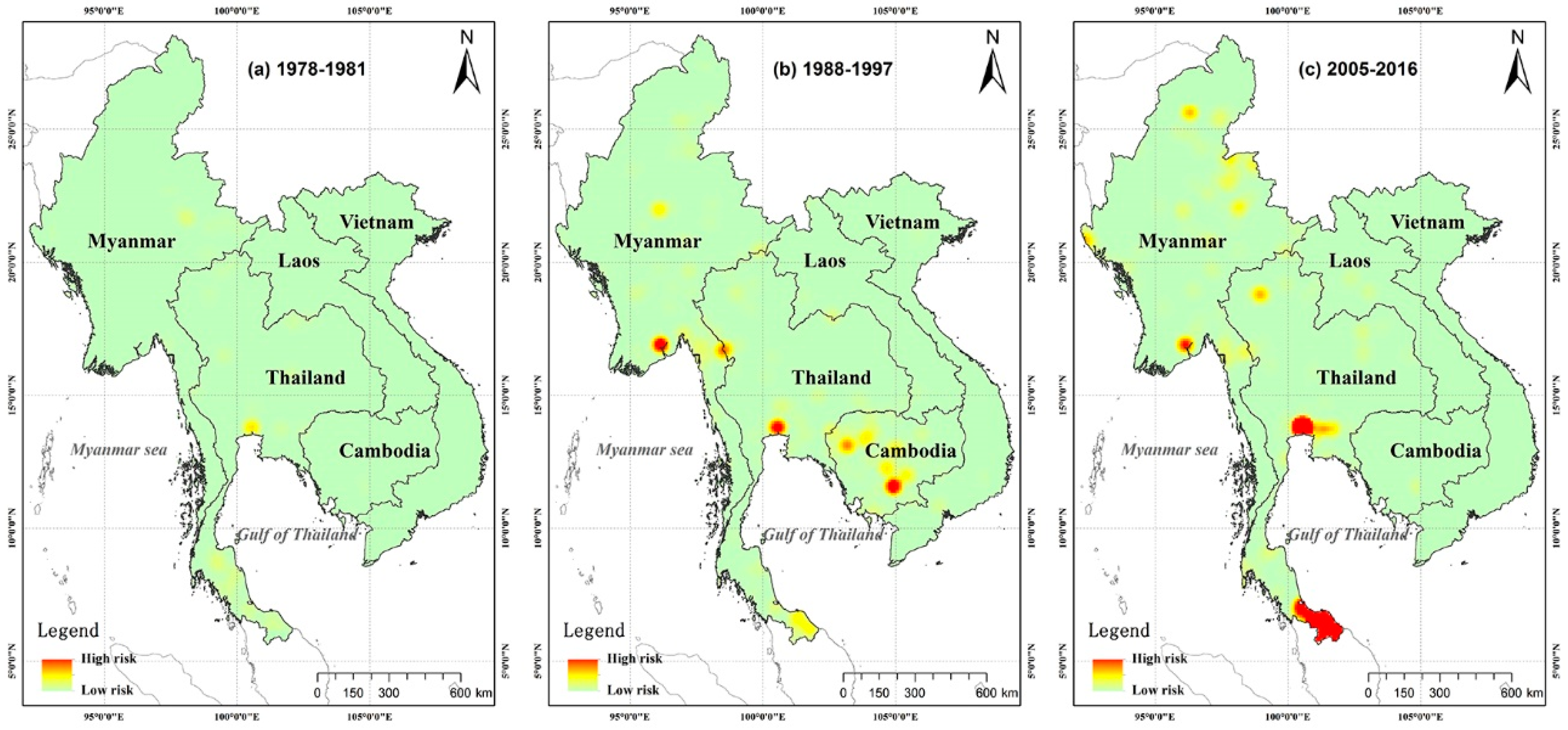
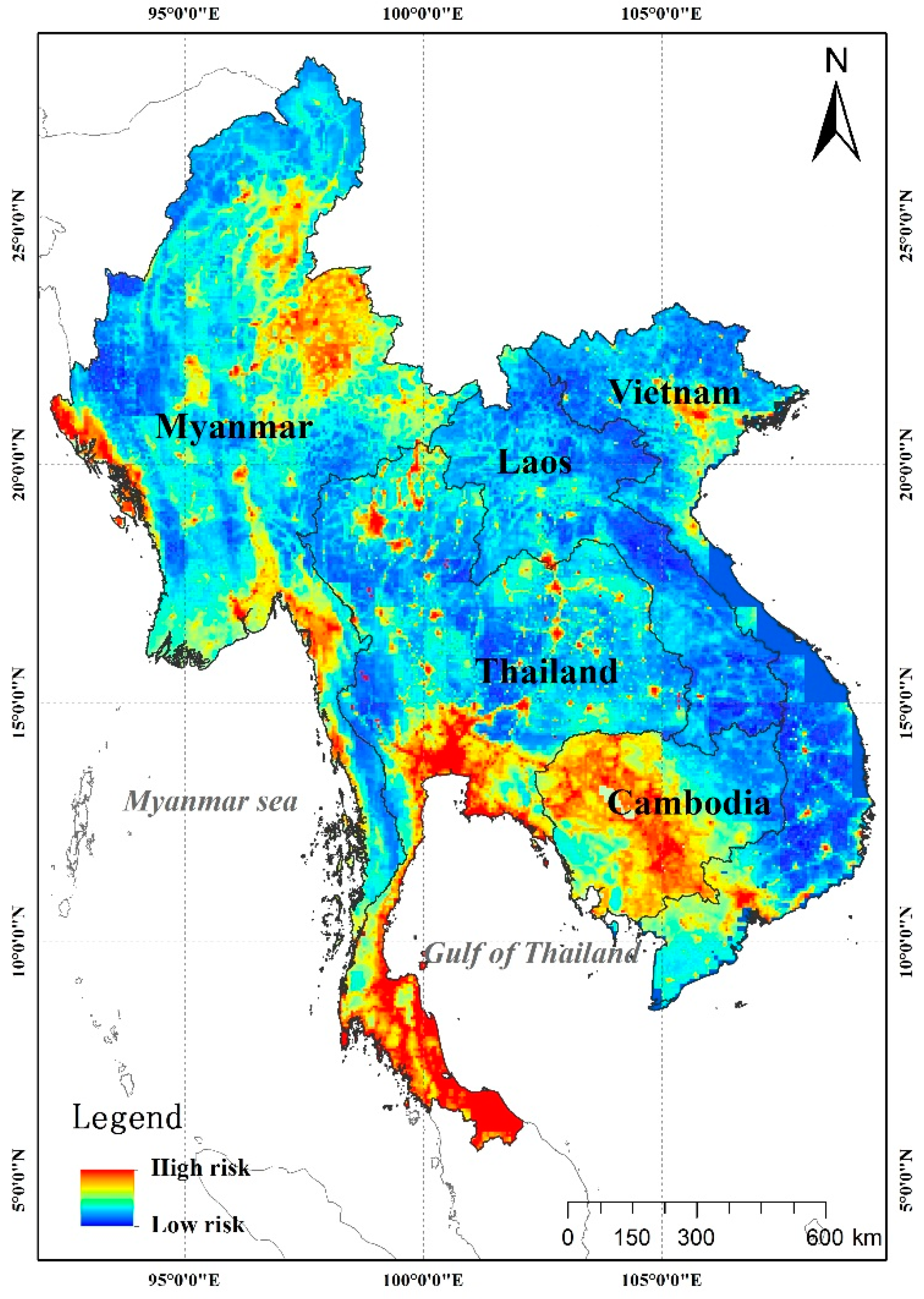
3.1. Spatio-Temporal Variation of Terrorist Attacks on the Indochina Peninsula
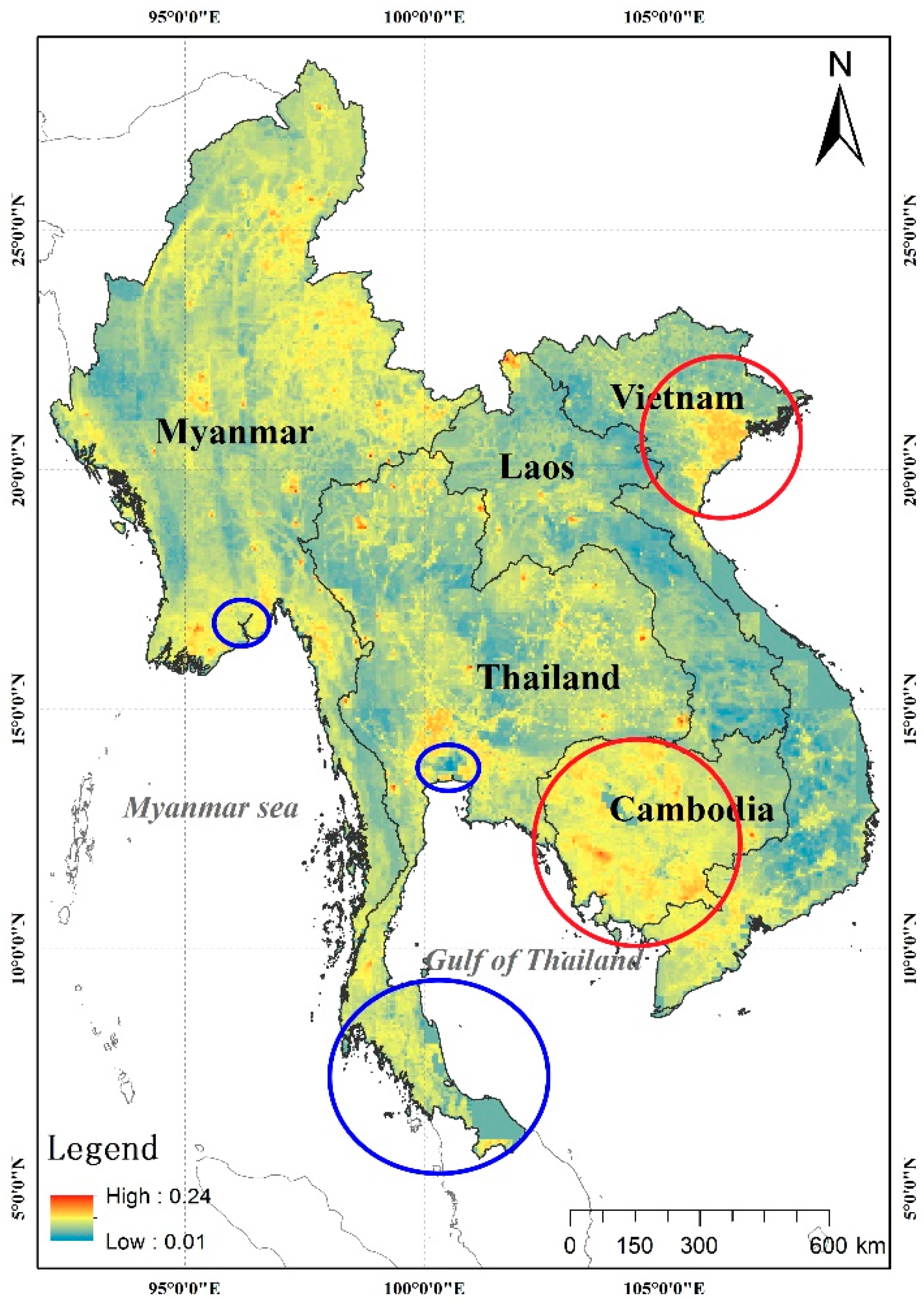
3.2. Predicting Potential Risk Areas for Terrorist Attacks in Indochina Peninsula
4. Discussion
4.1. Uncertainty Analysis
4.2. Feature Analysis
4.3. Comparison with Related Research
4.4. Limitation Analysis
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Schleussner, C.F.; Donges, J.F.; Donner, R.V.; Schellnhuber, H.J. Armed-conflict risks enhanced by climate-related disasters in ethnically fractionalized countries. Proc. Natl. Acad. Sci. USA 2016, 113, 9216–9221. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Barnes, V.A.; Treiber, F.A.; Ludwig, D.A. African-American adolescents’ stress responses after the 9/11/01 terrorist attacks. J. Adolesc. Health 2005, 36, 201–207. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Martens, A.; Sainudiin, R.; Sibley, C.G.; Schimel, J.; Webber, D. Terrorist attacks escalate in frequency and fatalities preceding highly lethal attacks. PLoS ONE 2014, 9, e93732. [Google Scholar] [CrossRef] [PubMed]
- START. Global Terrorism Database. 2016. Available online: https://www.start.umd.edu/gtd (accessed on 7 June 2018).
- Swahn, M.H.; Mahendra, R.R.; Paulozzi, L.J.; Winston, R.L.; Shelley, G.A.; Taliano, J.; Frazier, L.; Saul, J.R. Violent attacks on Middle Easterners in the United States during the month following the September 11, 2001 terrorist attacks. Inj. Prev. J. Int. Soc. Child Adolesc. Inj. Prev. 2003, 9, 187. [Google Scholar] [CrossRef]
- Li, Z.; Sun, D.; Chen, H.; Huang, S.Y. Identifying the socio-spatial dynamics of terrorist attacks in the Middle East. In Proceedings of the 2016 IEEE Conference on Intelligence and Security Informatics (ISI), Tucson, AZ, USA, 28–30 September 2016. [Google Scholar]
- Kang, W.; Julak, L.; Yongtae, C. Attack Patterns and Trajectories of Terrorist Groups in East and South Asia. Korean J. Def. Anal. 2014, 26, 209–224. [Google Scholar]
- Jones, S. Briefing for the New President: The Terrorist Threat in Indonesia and Southeast Asia. Ann. Am. Acad. Political Soc. Sci. 2008, 618, 69–78. [Google Scholar] [CrossRef]
- Febrica, S. Securitizing Terrorism in Southeast Asia: Accounting for the Varying Responses of Singapore and Indonesia. Asian Surv. 2010, 50, 569–590. [Google Scholar] [CrossRef]
- Gunaratna, R. Terrorism in South-East Asia. Available online: https://www.researchgate.net/publication/266355761_Terrorism_in_South-East_Asia (accessed on 12 July 2018).
- Bertram, S. Sub Saharan African Terrorist Groups’ use of the Internet. Discret. Math. Appl. 2014, 5, 1167–1175. [Google Scholar] [CrossRef]
- Price, G.; Elu, J. Do Remittances Finance Terrorism in Sub-Saharan Africa? Social Science Electronic Publishing: Rochester, NY, USA, 2011. [Google Scholar]
- Shiraishi, M. East-West Economic Corridor: Lao Bao—Dansavanh Border; Palgrave Macmillan: Hampshire, UK, 2013. [Google Scholar]
- Mandel, D.R. Are risk assessments of a terrorist attack coherent? J. Exp. Psychol. Appl. 2005, 11, 277–288. [Google Scholar] [CrossRef] [PubMed]
- Braithwaite, A.; Li, Q. Transnational Terrorism Hot Spots: Identification and Impact Evaluation. Confl. Manag. Peace Sci. 2007, 24, 281–296. [Google Scholar] [CrossRef]
- Guo, D. Early Detection of Terrorism Outbreaks Using Prospective Space–Time Scan Statistics. Prof. Geogr. 2013, 65, 676–691. [Google Scholar] [CrossRef]
- Li, S.; Zhuang, J.; Shen, S. Dynamic forecasting conditional probability of bombing attacks based on time-series and intervention analysis. Risk Anal. 2016, 37, 1287–1297. [Google Scholar] [CrossRef] [PubMed]
- Sachan, A.; Roy, D. TGPM: Terrorist Group Prediction Model for Counter Terrorism. Int. J. Comput. Appl. 2012, 44, 49–52. [Google Scholar] [CrossRef]
- Cederman, L.E.; Weidmann, N.B. Predicting armed conflict: Time to adjust our expectations? Science 2017, 355, 474. [Google Scholar] [CrossRef] [PubMed]
- Mo, H.; Meng, X.; Li, J.; Zhao, S. Terrorist event prediction based on revealing data. In Proceedings of the 2017 IEEE 2nd International Conference on Big Data Analysis (ICBDA), Beijing, China, 10–12 March 2017. [Google Scholar]
- Zhou, B.; Shi, A.; Cai, F.; Zhang, Y. Wavelet Neural Networks for Nonlinear Time Series Analysis. Int. J. Knowl. Manag. 2004, 10, 430–435. [Google Scholar]
- Muhammad, H.; Kazi, H. Use of Predictive Modeling for Prediction of Future Terrorist Attacks in Pakistan. Int. J. Comput. Appl. 2016, 179, 8–16. [Google Scholar] [CrossRef]
- Brandt, P.; Freeman, J.R.; Schrodt, P.A. Real Time, Time Series Forecasting of Inter- and Intra-State Political Conflict. Confl. Manag. Peace Sci. 2011, 28, 41–63. [Google Scholar] [CrossRef]
- Dong, Q. Machine Learning and Conflict Prediction: A Cross-Disciplinary Approach. World Econ. Politics 2017, 2, 56. [Google Scholar]
- Hartman, A.; Blair, R.; Blattman, C. Predicting Local Violence: Evidence from a Panel Survey in Liberia. Soc. Sci. Electron. Publ. 2017, 54, 298–312. [Google Scholar]
- Weidmann, N.B.; Ward, M.D. Predicting Conflict in Space and Time. J. Confl. Resolut. 2010, 54, 883–900. [Google Scholar] [CrossRef]
- Ding, F.; Ge, Q.; Jiang, D.; Fu, J.; Hao, M. Understanding the dynamics of terrorism events with multiple-discipline datasets and machine learning approach. PLoS ONE 2017, 12, e0179057. [Google Scholar] [CrossRef] [PubMed]
- Scheffran, J.; Brzoska, M.; Kominek, J.; Link, P.M.; Schilling, J. Climate change and violent conflict. Science 2012, 336, 869–871. [Google Scholar] [CrossRef] [PubMed]
- Hauge, W.; Ellingsen, T. Beyond Environmental Scarcity: Causal Pathways to Conflict. J. Peace Res. 1998, 35, 299–317. [Google Scholar] [CrossRef]
- Binningsbø, H.M.; Soysa, I.D.; Gleditsch, N.P. Green giant or straw man? Environmental pressure and civil conflict, 1961–1999. Popul. Environ. 2007, 28, 337–353. [Google Scholar] [CrossRef]
- Buhaug, H.; Rød, J.K. Local Determinants of African Civil Wars 1970–2001. Political Geogr. 2006, 25, 315–335. [Google Scholar] [CrossRef]
- Urdal, H. People vs. Malthus: Population Pressure, Environmental Degradation, and Armed Conflict Revisited. J. Peace Res. 2005, 42, 417–434. [Google Scholar] [CrossRef]
- Raleigh, C.; Urdal, H. Climate change, environmental degradation and armed conflict. Political Geogr. 2007, 26, 674–694. [Google Scholar] [CrossRef]
- Hendrix, C.S.; Glaser, S.M. Trends and Triggers: Climate Change and Civil Conflict in Sub-Saharan Africa. Political Geogr. 2007, 26, 695–715. [Google Scholar] [CrossRef]
- Theisen, O.M. Blood and Soil? Resource Scarcity and Internal Armed Conflict Revisited. J. Peace Res. 2008, 45, 801–818. [Google Scholar] [CrossRef]
- Lujala, P. The spoils of nature: Armed civil conflict and rebel access to natural resources. J. Peace Res. 2010, 47, 15–28. [Google Scholar] [CrossRef]
- Gizelis, T.I.; Wooden, A.E. Water resources, institutions, & intrastate conflict. Political Geogr. 2010, 29, 444–453. [Google Scholar]
- Østby, G.; Urdal, H.; Tadjoeddin, M.Z.; Murshed, S.M.; Strand, H. Population Pressure, Horizontal Inequality and Political Violence: A Disaggregated Study of Indonesian Provinces, 1990–2003. J. Dev. Stud. 2011, 47, 377–398. [Google Scholar] [CrossRef]
- Sekhri, S.; Storeygard, A. Dowry Deaths: Consumption Smoothing in Response to Climate Variability in India. Va. Econ. Online Papers 2012, 407, 131. [Google Scholar]
- Mares, D. Climate change and crime: Monthly temperature and precipitation anomalies and crime rates in St. Louis, MO 1990–2009. Crime Law Soc. Chang. 2013, 59, 185–208. [Google Scholar] [CrossRef]
- Blakeslee, D.S.; Fishman, R. Rainfall Shocks and Property Crimes in Agrarian Societies: Evidence from India; Social Science Electronic Publishing: Rochester, NY, USA, 2013. [Google Scholar]
- Kawsar, R. Spatio-Temporal Analyses of the Relationship between Armed Conflict and Climate Change in the Eastern Africa. Master’s Thesis, Westfälische Wilhelms-Universität, Münster, Germany, 28 February 2013. [Google Scholar]
- Hsiang, S.M.; Marshall, B.; Edward, M. Quantifying the influence of climate on human conflict. Science 2013, 341, 1212. [Google Scholar] [CrossRef] [PubMed]
- Linke, A.M.; Witmer, F.D.W.; Holland, E.C.; O’Loughlin, J. Mountainous Terrain and Civil Wars: Geospatial Analysis of Conflict Dynamics in the Post-Soviet Caucasus. Ann. Assoc. Am. Geogr. 2016, 107, 520–535. [Google Scholar] [CrossRef]
- Brochmann, M.; Hensel, P.R. Peaceful Management of International River Claims. Int. Negot. 2009, 14, 393–418. [Google Scholar] [CrossRef] [Green Version]
- Yue, H. Development trend of geopolitics on Indochina Peninsula. Soc. Sci. Yunnan 2008, 2, 27–30. [Google Scholar]
- Wimmer, A.; Cederman, L.-E.; Min, B. Ethnic Politics and Armed Conflict: A Configurational Analysis of a New Global Data Set. Am. Sociol. Rev. 2009, 74, 316–337. [Google Scholar] [CrossRef] [Green Version]
- Manuel, C.; Torres, M.R.; Ramon, H.; Fowler, J.H. Violent extremist group ecologies under stress. Sci. Rep. 2013, 3, 1544. [Google Scholar]
- Sheather, S.J.; Jones, M.C. A Reliable Data-Based Bandwidth Selection Method for Kernel Density Estimation. J. R. Stat. Soc. 1991, 53, 683–690. [Google Scholar] [CrossRef]
- Silverman, B.W. Density Estimation for Statistics and Data Analysis; Chapman and Hall: London, UK, 1986. [Google Scholar]
- Dehnad, K. Density Estimation for Statistics and Data Analysis. Technometrics 1986, 29, 495. [Google Scholar] [CrossRef]
- Breiman, L. Random Forest. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Parmar, C.; Grossmann, P.; Bussink, J.; Lambin, P.; Aerts, H.J.W.L. Machine Learning methods for Quantitative Radiomic Biomarkers. Sci. Rep. 2015, 5, 13087. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Palmer, D.; O’Boyle, N.M.; Glen, R.; Mitchell, J.B.O. Random Forest Models To Predict Aqueous Solubility. J. Chem. Inf. Model. 2007, 47, 150. [Google Scholar] [CrossRef] [PubMed]
- Vincenzi, S.; Zucchetta, M.; Franzoi, P.; Pellizzato, M.; Pranovi, F.; Leo, G.A.D.; Torricelli, P. Application of a Random Forest algorithm to predict spatial distribution of the potential yield of Ruditapes philippinarum in the Venice lagoon, Italy. Ecol. Model. 2011, 222, 1471–1478. [Google Scholar] [CrossRef]
- Hyslop, D.; Morgan, T. Measuring Terrorism with the Global Terrorism Index. Contrib. Confl. Manag. Peace Econ. Dev. 2014, 22, 97–114. [Google Scholar]
- Conlon, K.T. Ethnic Violence in Southern Thailand: The Anomaly of Satun; Monterey California Naval Postgraduate School: Monterey, CA, USA, 2012. [Google Scholar]
| References | Study Area and Time Span | The Model or Method | The Main Findings |
|---|---|---|---|
| The social elements | |||
| Hauge and Ellingsen [29] | Global; 1980–1992 | Logit | Population growth, water scarcity and deforestation all increase the probability of conflicts. Economic and political influences on conflicts outweigh other factors. |
| Binningsbø et al. [30] | Global; 1961–1999 | Logit | Consumption reduces the risk of conflicts. |
| Buhaug and Rød [31] | Africa; 1970–2001 | Logit | Population density has an impact on internal conflicts. |
| Urdal [32] | Global; 1950–2000 | Logit | Population pressure and land pressure will increase the probability of conflicts. |
| Raleigh and Urdal [33] | Global; 1990–2004 | Logit | The interaction of factors such as population density increase; soil degradation and water shortage will increase the risk of conflicts, but the impact will be small in underdeveloped countries. |
| The natural elements | |||
| Hendrix and Glaser [34] | Sub-Saharan Africa; 1981–1999 | Logit | Drought increases conflicts risk. |
| Theisen [35] | Global; 1979–2001 | Logit | Land degradation increases risk; water shortages and drought have an impact on conflicts. |
| Lujala [36] | Global; 1946–2003 | Kaplan–Meier Survival Estimates | Natural resources have an impact on the duration of conflicts. When armed conflicts occur in resource-rich areas, the duration of conflict will be doubled. |
| Gizelis and Wooden [37] | 98 countries; 1981–2000 | Simultaneous equation model | Water shortages increase the risk of conflicts. |
| Østby et al. [38] | Indonesia; 1990–2003 | Logit | There is a negative correlation between land resources and conflicts. |
| Sekhri and Storeygard [39] | India; 2002–2007 | Regression analysis | Less rain will increase violence in the country. |
| Mares [40] | The United States; 1990–2009 | Regression analysis | Temperature anomalies increase the frequency of conflicts. |
| Blakeslee and Fishman [41] | India; 1971–2000 | Parallel regressions and Poisson regression | Abnormal rainfall increases violence and crime. |
| Kawsar [42] | East Africa; 1991–2000 | Point process models and Spatial Autoregressive (SAR) | Climate change increases the risk of armed conflict. |
| Schleussner et al. [1] | Global; 1980–2010 | ECA | Climate change, especially climate-related natural disasters, increases the risk of conflict in ethnically divided countries. |
| Scheffran et al. [28] | ----- | Perspective in “Science” | Climate variability may have been more associated with low-level violence. |
| Hsiang et al. [43] | ------- | Rsearch article summary in “Sciences” | There is a clear link between climate and conflict. |
| The geographical elements | |||
| Linke el al. [44] | Caucasus; 1990–2012 | Spatial analysis | Topography can influence conflict behaviour. |
| Brochmann and Hensel [45] | Americas, Western Europe, and the Middle East; 1900–2001 | Probit | Conflicts over shared river systems have been associated with low-level violence. |
| Feature | Source | Publisher | The Meaning of the Feature |
|---|---|---|---|
| The social elements | |||
| Fragile States Index | Global Fragile States Index | The Fund for Peace (http://www.fundforpeace.org/fsi/) | The index aims to assess states’ vulnerability to conflict or collapse. |
| Ethnic distribution | GeoEPR, the Ethnic Power Relations dataset | Center for Comparative and International Studies (CIS), International Conflict Research (https://icr.ethz.ch/data/epr/geoepr/) | The GeoEPR dataset provides geo-spatial information about every politically relevant ethnic group. It includes a coding of type of ethnic marker distinguishing group members based on religion, language, race, etc. It reflects ethnic distribution and religious background [47]. |
| Major drug regions | World drug report | Division for Policy Analysis and Public Affairs, United Nations Office on Drugs and Crime (https://www.unov.org/unov/en/unodc.html) | These data reflect the degree of social stability. |
| Population density | Adjusted population density, V4.10 | NASA Socioeconomic Data and Applications Center (SEDAC) (https://neo.sci.gsfc.nasa.gov/view.php?datasetId=SEDAC_POP) | These data reflect the degree of population concentration and the pressure of population on land. |
| Night-time light | Version 4 DMSP-OLS night-time lights time series | The Earth Observation Group, NOAA (http://ngdc.noaa.gov/eog/index.html) | The night-time light data reflects the region’s economic development. |
| The natural elements | |||
| Average precipitation | G-Econ 4.0 | Yale University (http://gecon.yale.edu/) | These data reflect spatial differences in climate (precipitation and temperature). |
| Average temperature | |||
| Temperature anomaly | Land surface temperature anomaly | NASA Earth Observations (NEO) (https://earthobservatory.nasa.gov/global-maps/MOD_LSTAD_M) | These data can reflect weather anomalies. |
| Drought index | Drought index of the world | Numerical Terradynamic Simulation Group, University of Montana (http://files.ntsg.umt.edu/) | It can reflect the drought conditions in the region, and it can also reflect abnormal precipitation. |
| Multi-hazard frequency | Global Multi-hazard Frequency and Distribution, v1 | NASA Socioeconomic Data and Applications Center (SEDAC) (http://sedac.ciesin.columbia.edu/data/set/ndh-multihazard-frequency-distribution) | These data provide insight into the frequency and distribution of multi-hazard events, which include cyclones, droughts, earthquakes, floods, landslides, and volcanoes. |
| The geographical elements | |||
| topography | ASTER Global DEM | NASA Earth Observations (NEO) (https://gdex.cr.usgs.gov/gdex/) | It reflects the spatial difference of topography. |
| Urban accessibility | Global urbanisation and accessibility map | Joint Research Centre, European Commission (https://ec.europa.eu/info/departments/joint-research-centre_en) | It reflects the accessibility and sophistication of a region. |
| distance to a major navigable lake | G-Econ 4.0 | Yale University (http://gecon.yale.edu/) | These data reflect the abundance of water resources in a region and in the surrounding water network. |
| distance to an ice-free ocean | |||
| distance to a major navigable lake | |||
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hao, M.; Jiang, D.; Ding, F.; Fu, J.; Chen, S. Simulating Spatio-Temporal Patterns of Terrorism Incidents on the Indochina Peninsula with GIS and the Random Forest Method. ISPRS Int. J. Geo-Inf. 2019, 8, 133. https://doi.org/10.3390/ijgi8030133
Hao M, Jiang D, Ding F, Fu J, Chen S. Simulating Spatio-Temporal Patterns of Terrorism Incidents on the Indochina Peninsula with GIS and the Random Forest Method. ISPRS International Journal of Geo-Information. 2019; 8(3):133. https://doi.org/10.3390/ijgi8030133
Chicago/Turabian StyleHao, Mengmeng, Dong Jiang, Fangyu Ding, Jingying Fu, and Shuai Chen. 2019. "Simulating Spatio-Temporal Patterns of Terrorism Incidents on the Indochina Peninsula with GIS and the Random Forest Method" ISPRS International Journal of Geo-Information 8, no. 3: 133. https://doi.org/10.3390/ijgi8030133
APA StyleHao, M., Jiang, D., Ding, F., Fu, J., & Chen, S. (2019). Simulating Spatio-Temporal Patterns of Terrorism Incidents on the Indochina Peninsula with GIS and the Random Forest Method. ISPRS International Journal of Geo-Information, 8(3), 133. https://doi.org/10.3390/ijgi8030133







