An Agent-Based System for Location Privacy Protection in Location-Based Services
Abstract
1. Introduction
1.1. Motivation
1.2. Contributions
- We introduce a novel agent-based LBS privacy protection architecture that is compatible with heterogeneous platforms and has good performance quality attributes.
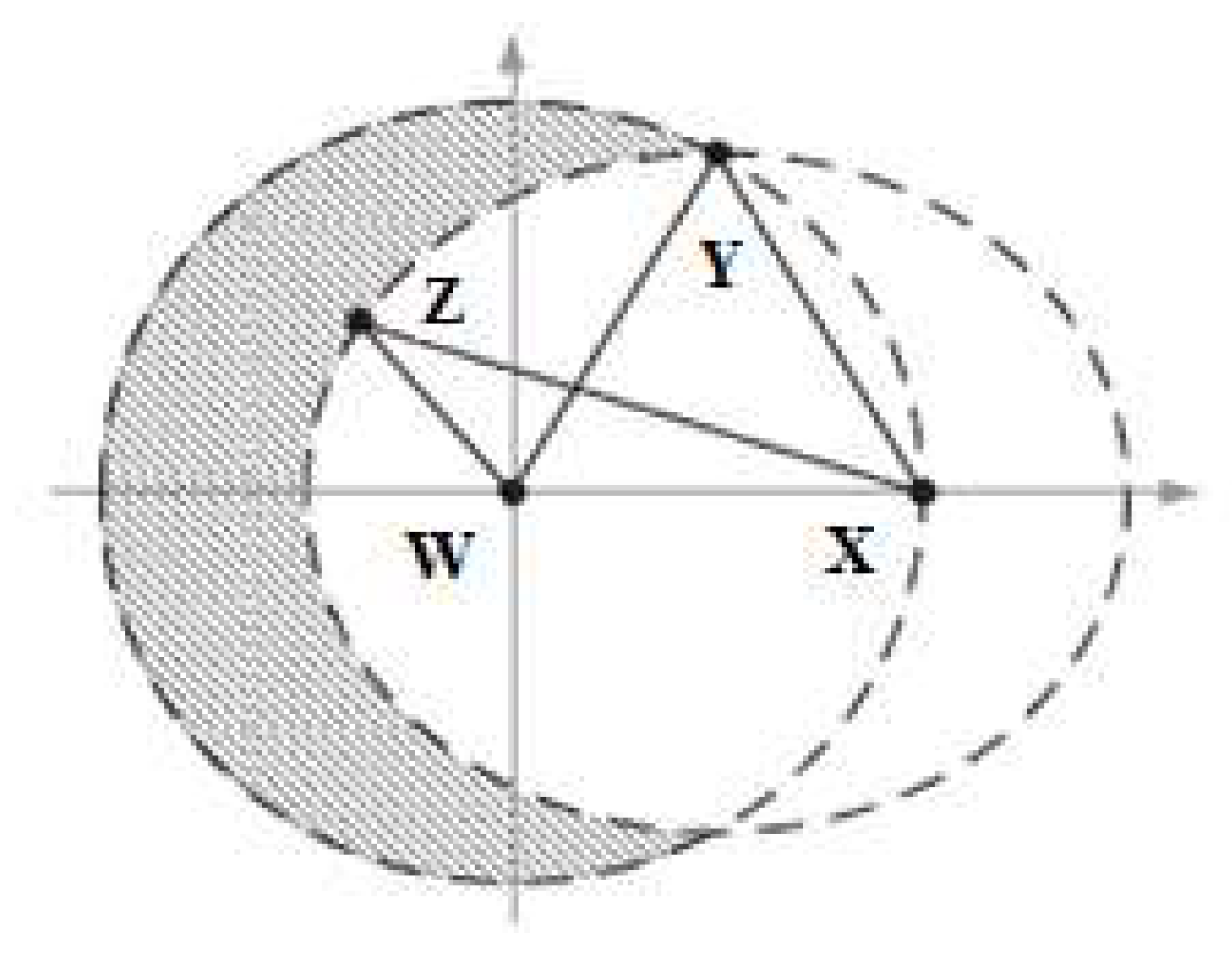
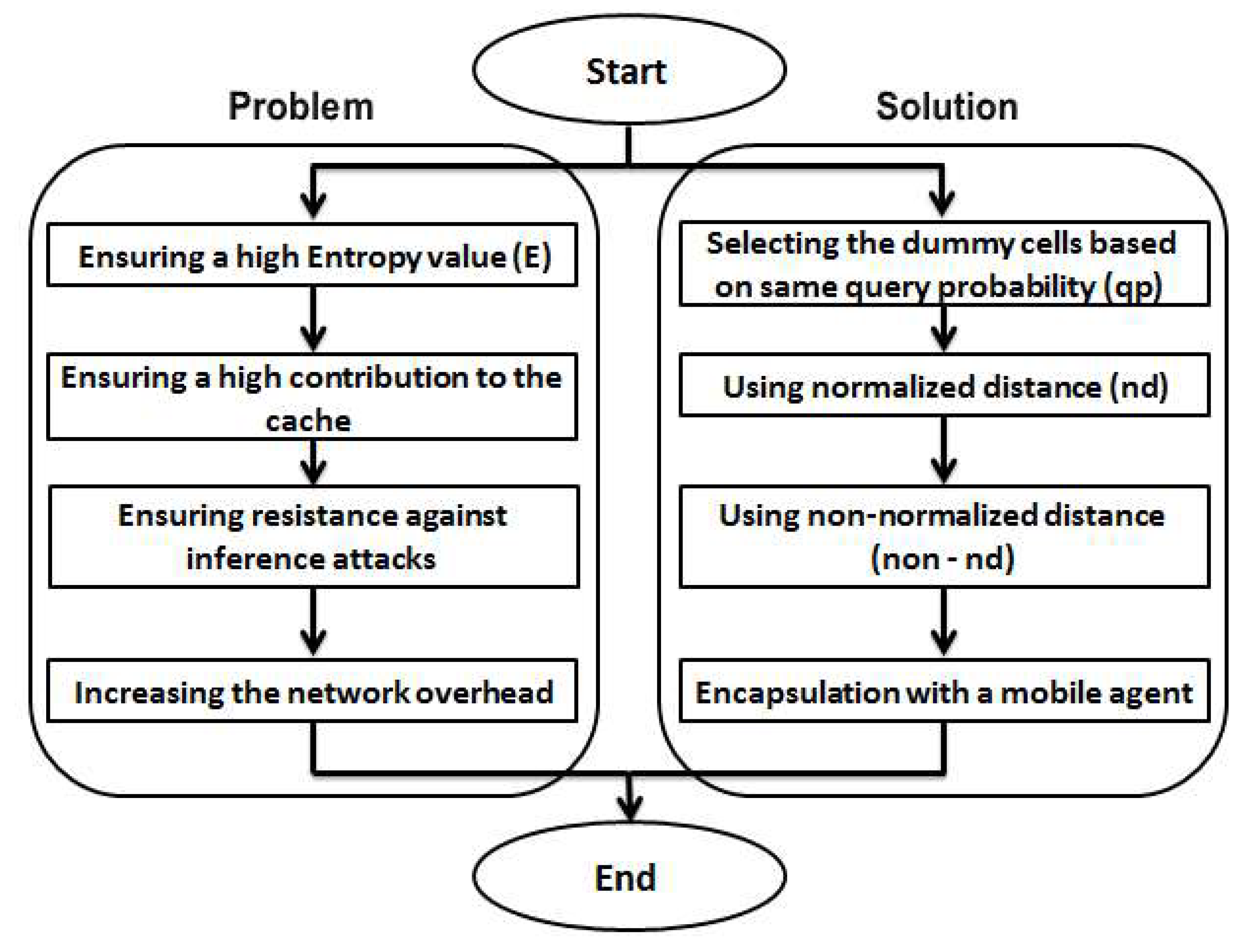
- We propose the Caching-Aware Double-Dummy Selection (CaDDSL) algorithm to generate/select strong location dummies for location privacy protection purposes. Our proposed CaDDSL algorithm employs normalized distance to achieve two objectives: generating/selecting the dummies that have the highest contributions to the cache for answering the future queries, and decreasing the number of connections with the LBS server (a malicious party).
- Considering resistance against inference attacks, we enhance the CaDDSL algorithm to obtain the Caching-Aware Overhead-Aware Dummy Selection (CaOaDSL) algorithm. Our CaOaDSL algorithm ensures resistance against homogeneity location attack and semantic location attack based on generating/selecting the dummies using non-normalized distance. In addition, it guarantees a high privacy protection level with minimal network overhead.
- We introduce a novel privacy metric to estimate the compromised privacy of the LBS user. Our privacy metric mainly depends on the entropy metric, and it is used to alert LBS users to situations in which they are vulnerable to privacy, a feature that has not been offered previously, to the best of our knowledge.
1.3. Structure of Paper
2. Related Works
2.1. Server-Based Approaches
2.2. User-Based Approaches
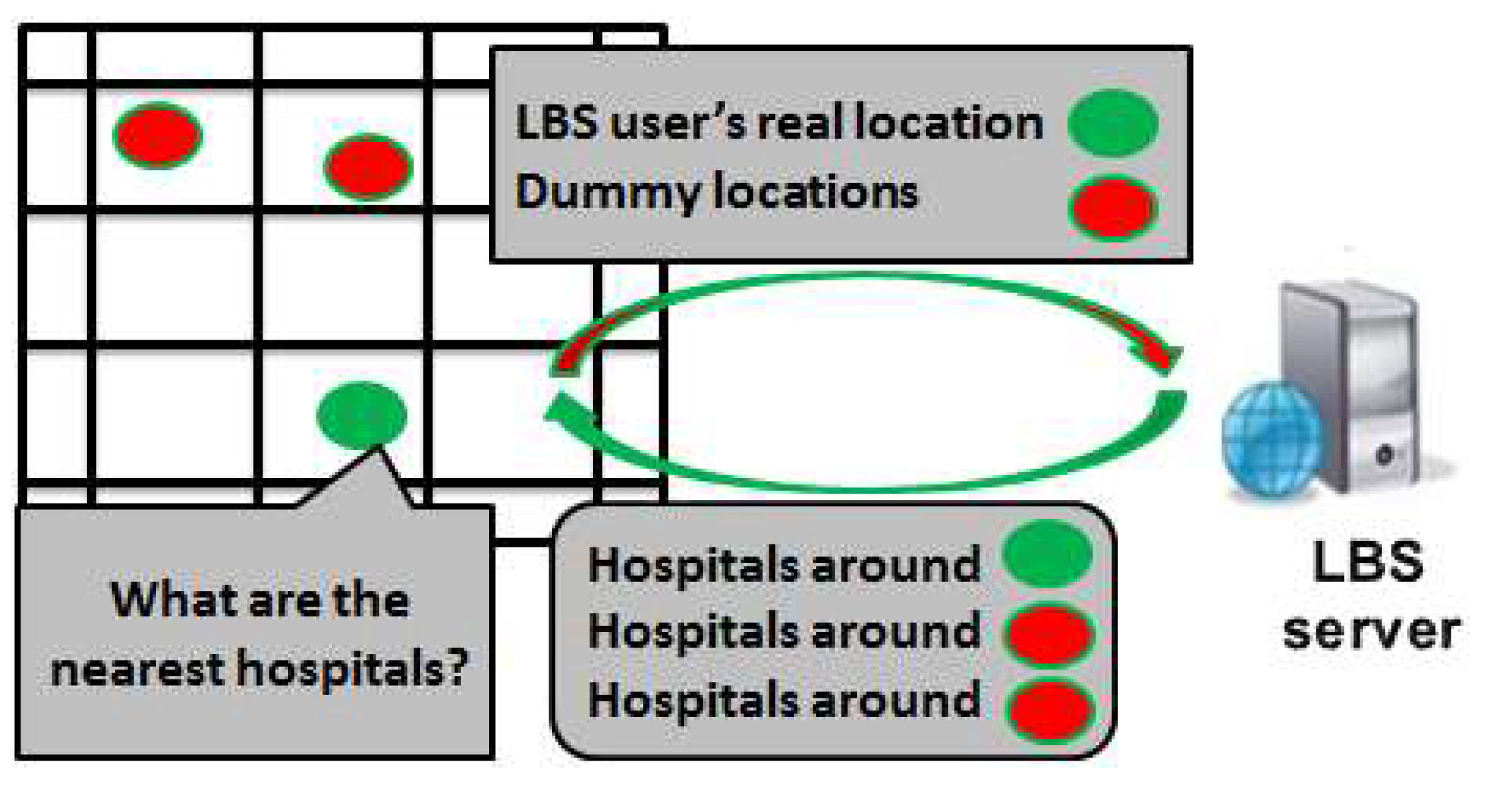
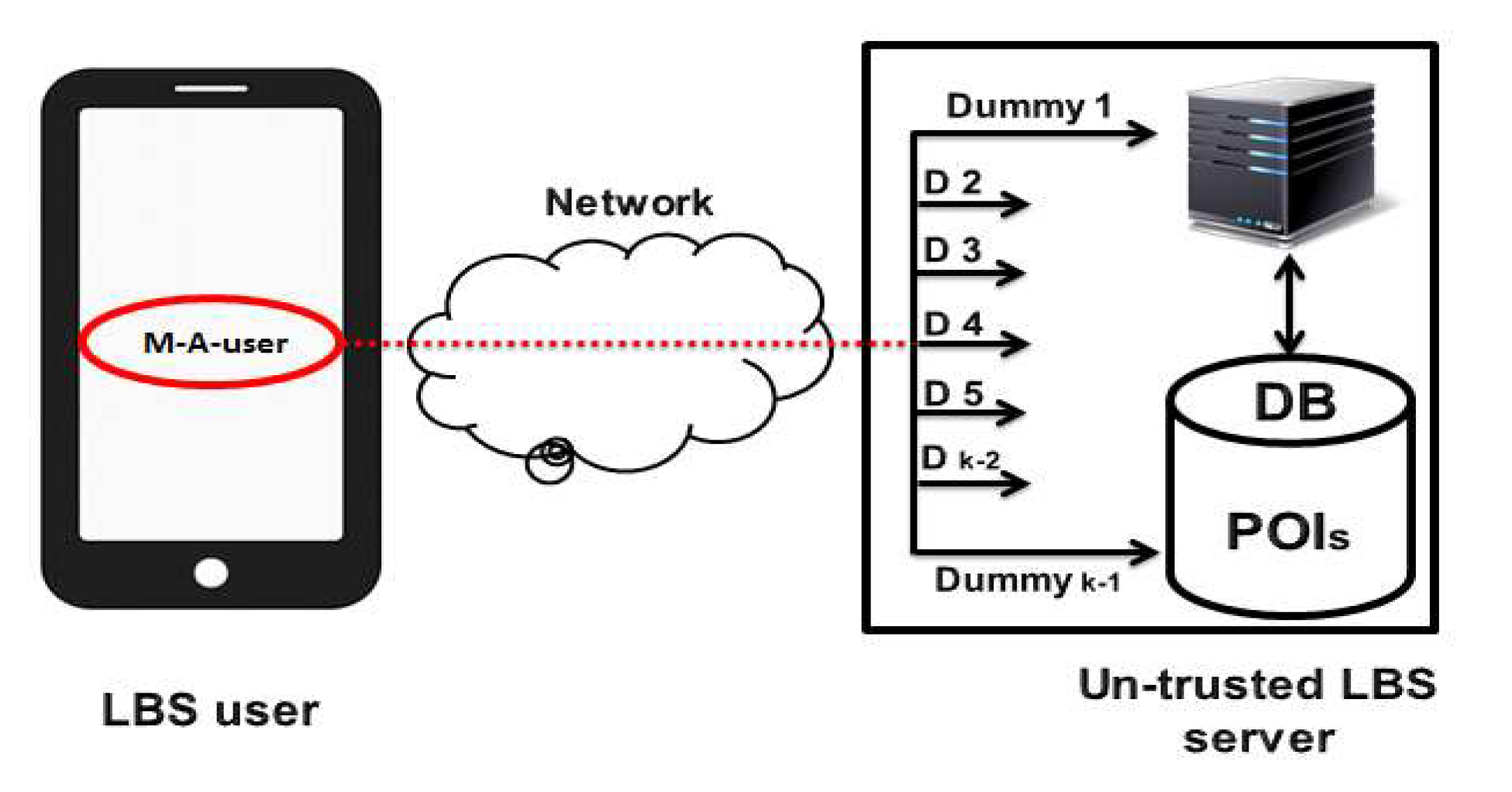
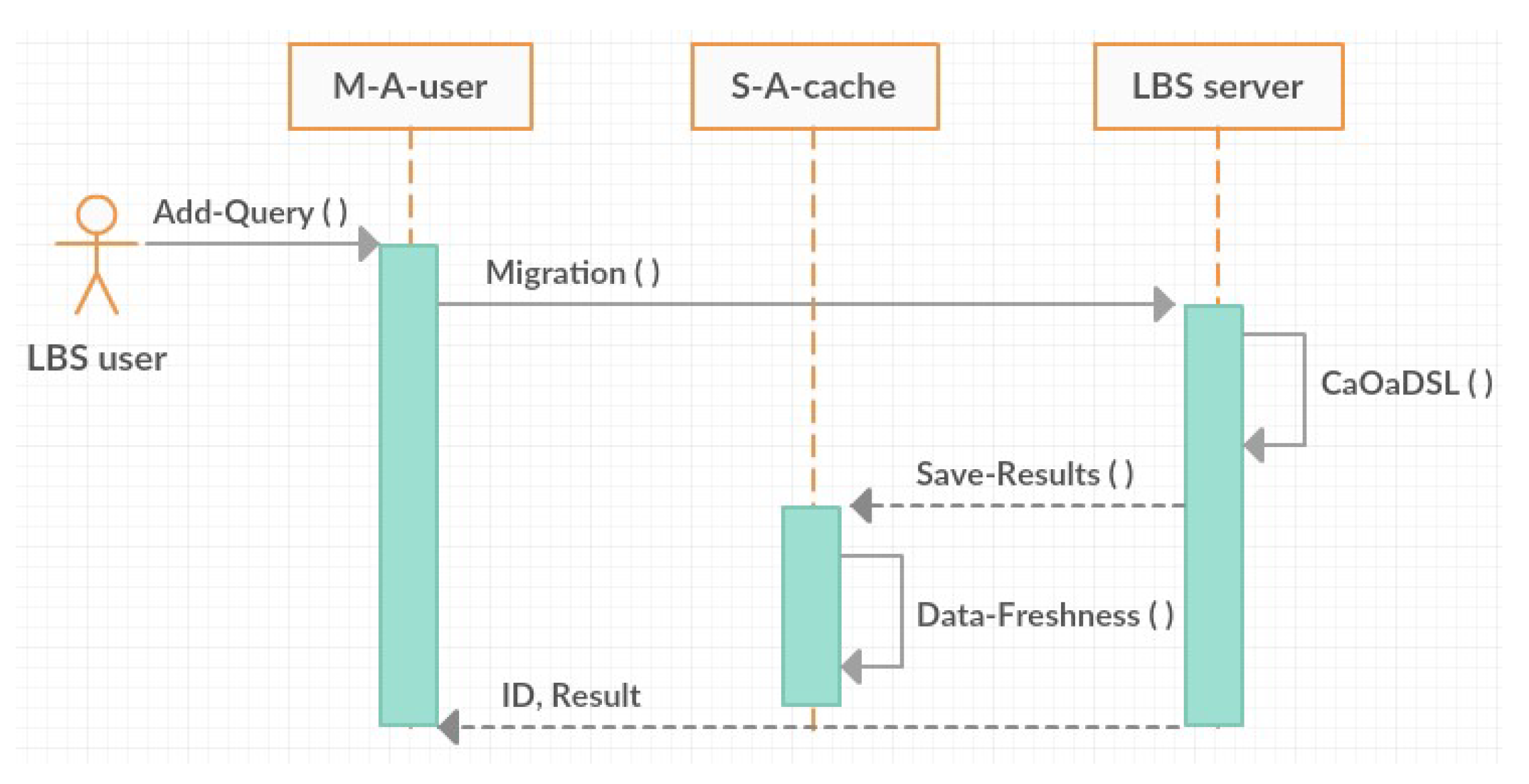
3. Proposed Privacy Protection Architecture
3.1. System Model
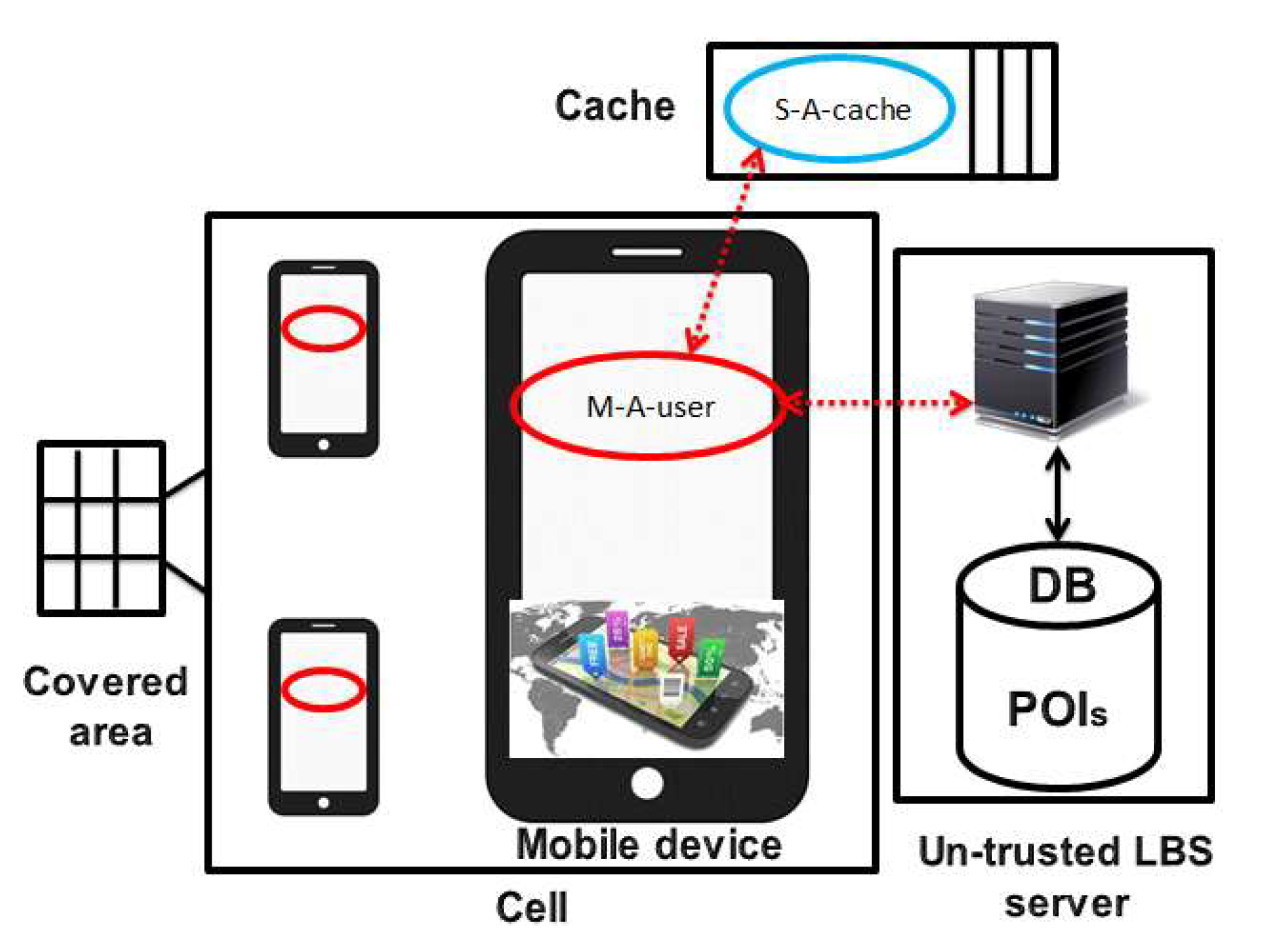
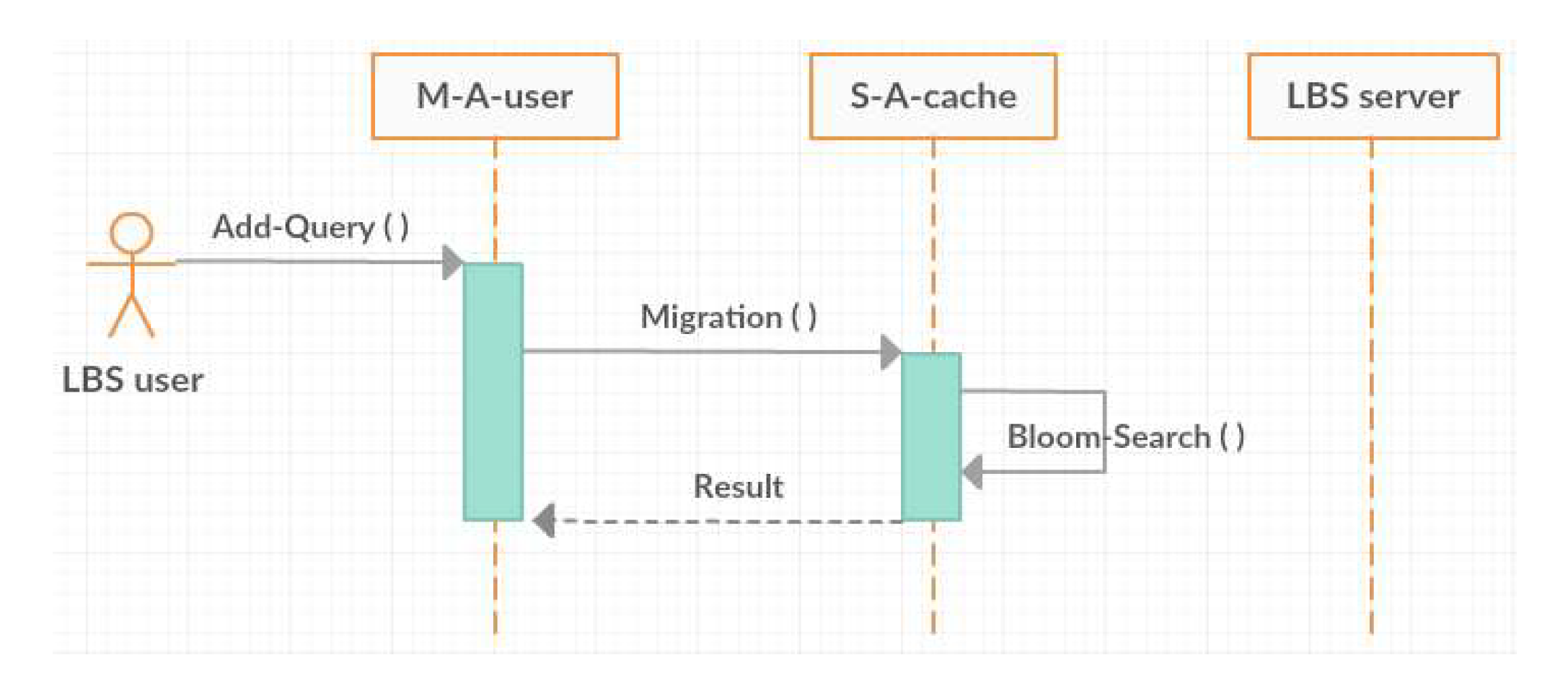
3.2. Agent-Based Location Privacy Protection Architecture
3.3. Roles of the Agents
| Algorithm 1: Caching-Aware Double-Dummy Selection (CaDDSL) Algorithm |
 |
| Algorithm 2: Caching-Aware Overhead-Aware Dummy Selection (CaOaDSL) |
| Input: (query probability of each cell), (the real location of the LBS user), (a system parameter. |
| Output: . |
| 1: ; (create M-A-user agent); |
| 2: ; (create an itinerary); |
| 3: , |
| where the lines 1–18 of Algorithm 1 are performed. |
| 4: , |
| where is a method that contains the retrieved POIs. |
| 5: Output , where . |
| Algorithm 3: Data freshness task |
| Input: (query probability of each cell), , (specific period of time that can be updated). |
| Output: . |
| 1: While , do |
| 2: Begin |
| 3: If , then |
| 4: Delete it from the cache; |
| 5: Else |
| 6: If and , then |
| 7: Delete it from the cache; |
| 8: Else |
| 9: ; |
| 10: End while |
| 11: Output: . |
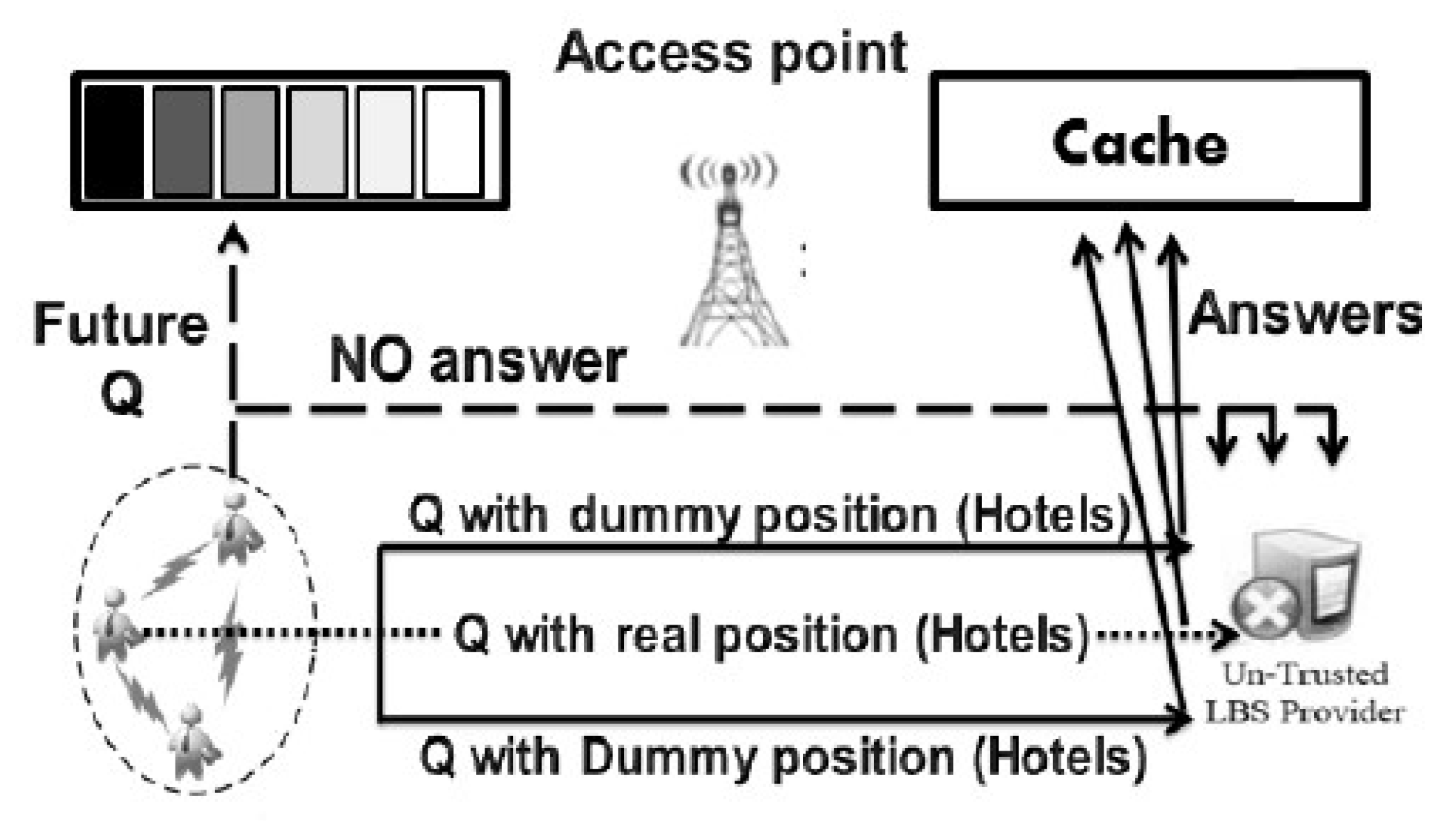
3.4. Proposed Architecture Details
4. Security Analysis
4.1. Security of Agents
4.2. Security Against Inference Attacks
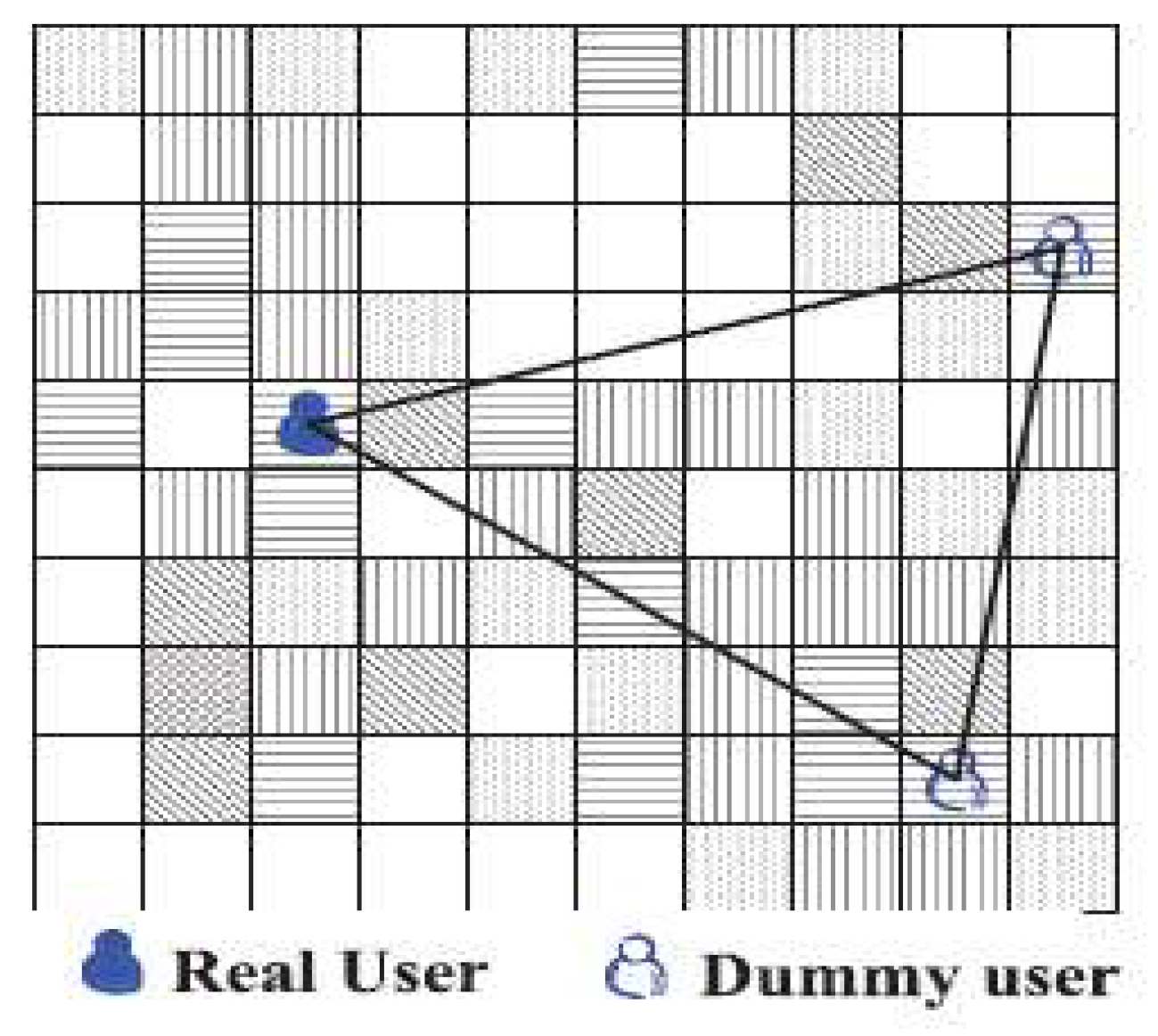
5. Used Metrics
5.1. Privacy Metrics
5.2. Performance Metrics
6. Experimental Results and Evaluations
6.1. Simulation Setup
- Assigning weights to POIs based on expected popularity (e.g., hospitals = 0.3, restaurants = 0.5, and metro stations = 0.2).
- Using normal distribution probability to model query rates.
- Randomizing frequencies per POI.
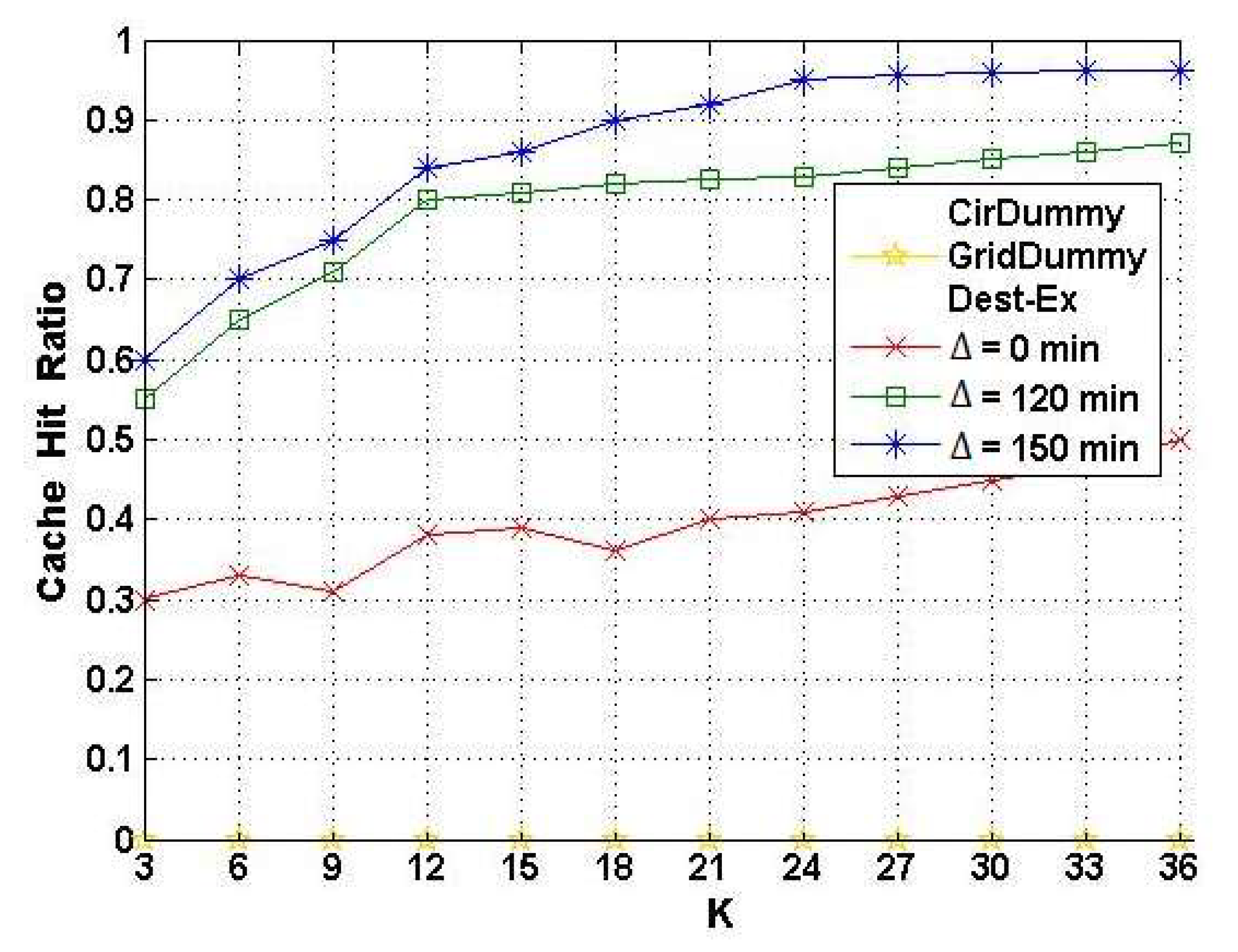
6.2. Evaluation of Cache Hit Ratio Results
6.3. Evaluation of Results on Resistance Against Inferences Attacks
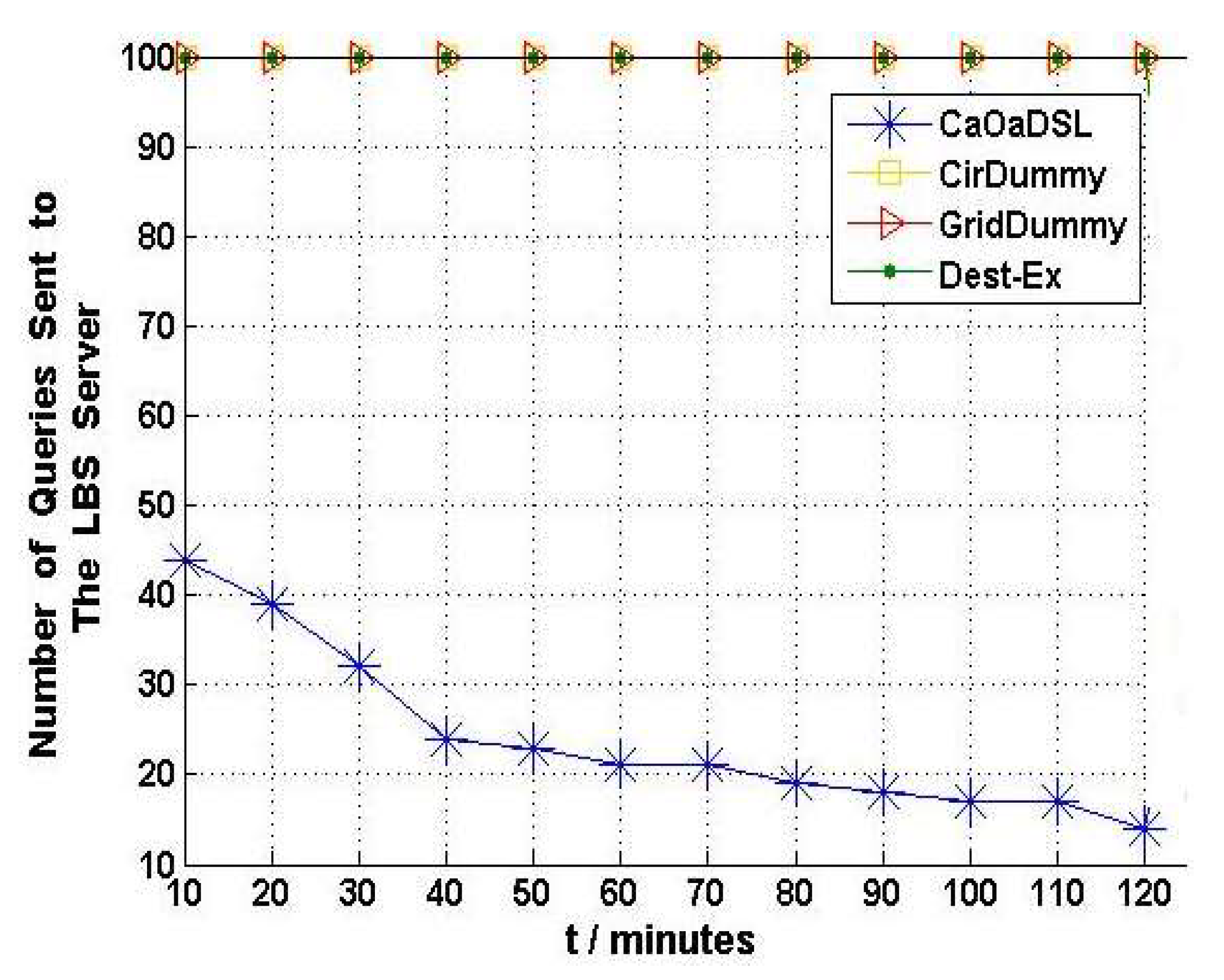
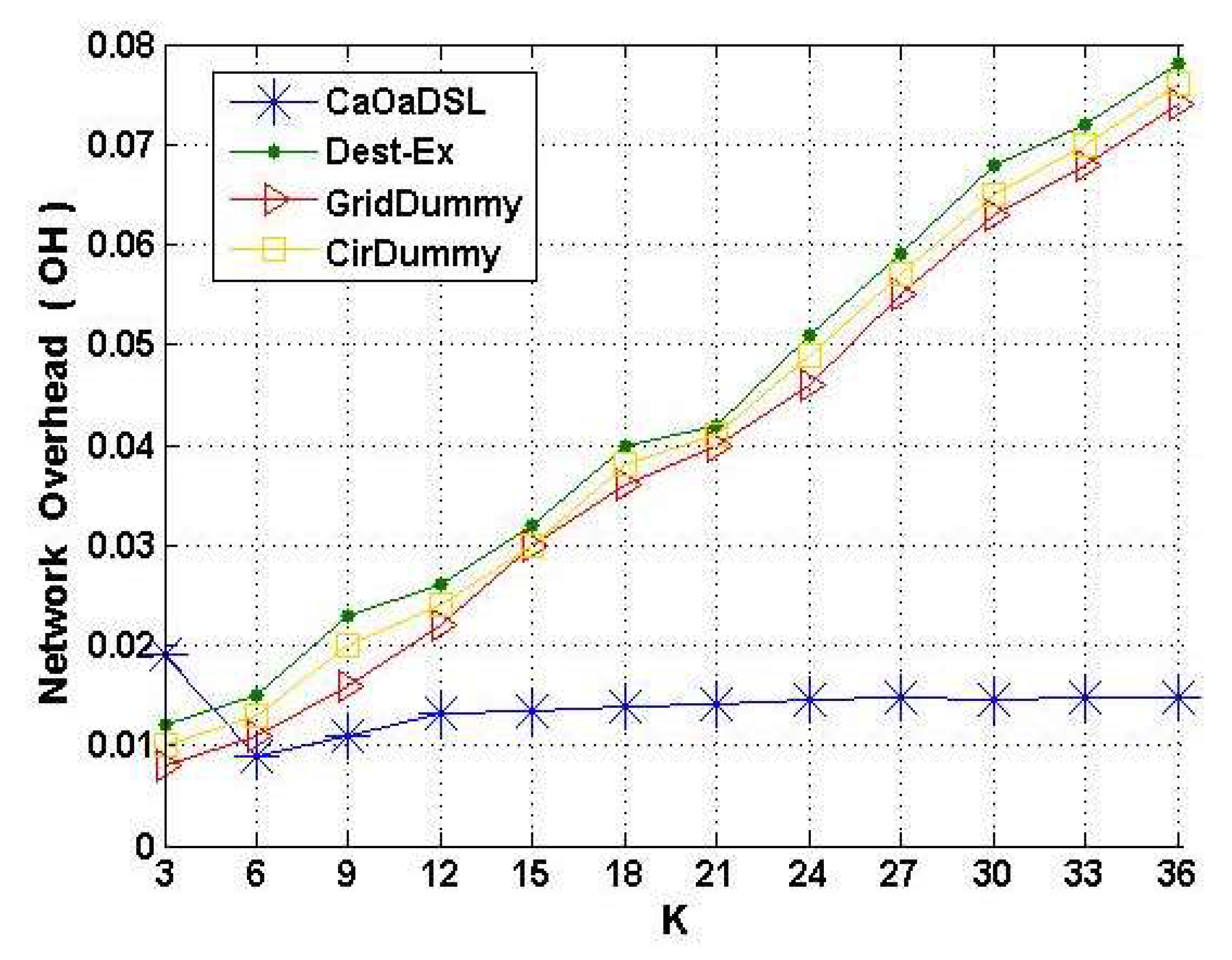
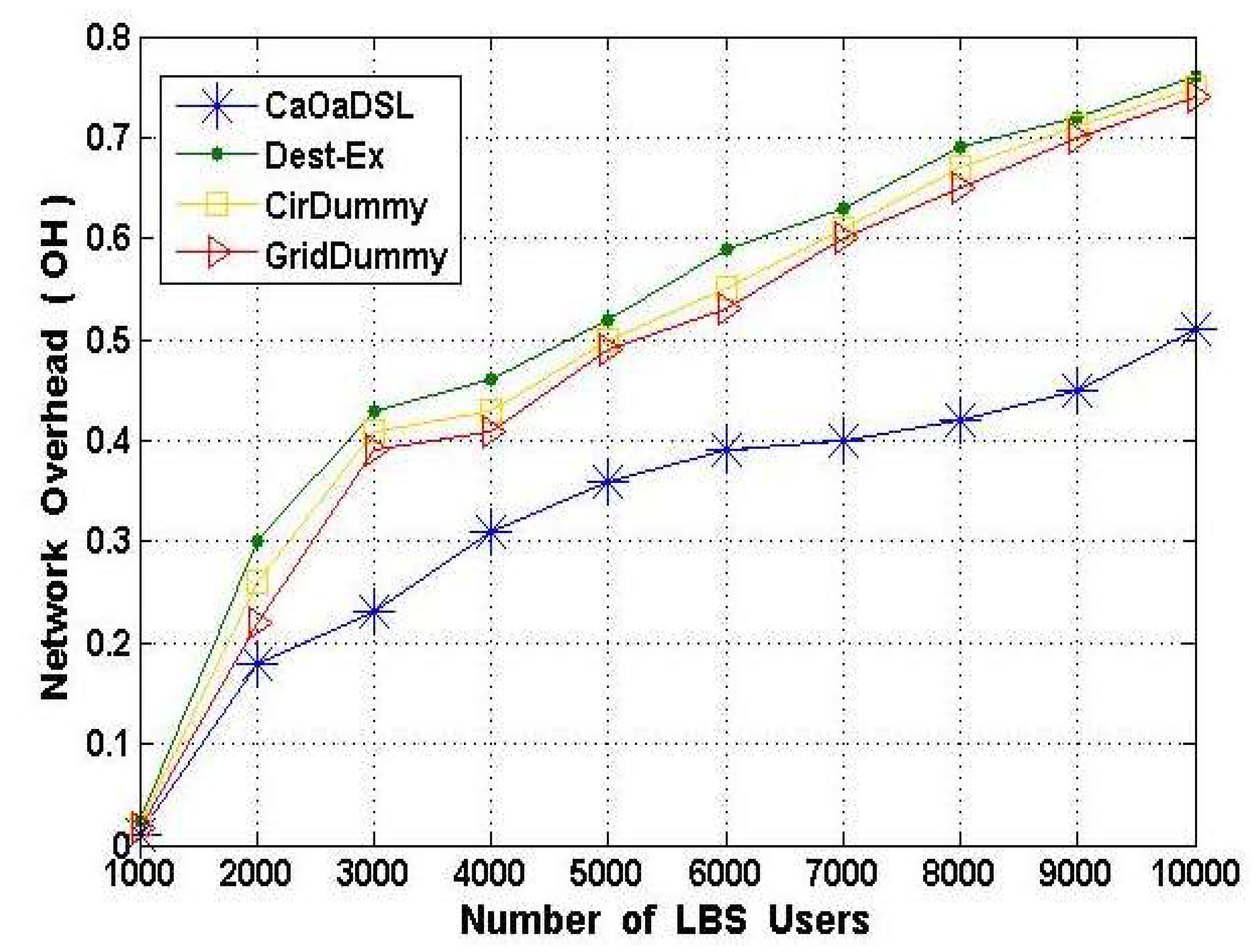
6.4. Scalability and Network Overhead Results Evaluation
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Albouq, S.S.; Sen, A.A.A.; Namoun, A.; Bahbouh, N.M.; Alkhodre, A.B.; Alshanqiti, A. A double obfuscation approach for protecting the privacy of IoT location based applications. IEEE Access 2020, 8, 129415–129431. [Google Scholar] [CrossRef]
- Giovanni, P.; Pilloni, V.; Martalò, M. Trustworthy Localization in IoT Networks: A Survey of Localization Techniques, Threats, and Mitigation. Sensors 2024, 24, 2214. [Google Scholar] [CrossRef]
- Basmh, A.; Mahgoub, I. Location privacy-preserving scheme in iobt networks using deception-based techniques. Sensors 2023, 23, 3142. [Google Scholar]
- Liu, T.; Liu, J.; Wang, J.; Zhang, H.; Zhang, B.; Ma, Y.; Sun, M.; Lv, Z.; Xu, G. Pseudolites to support location services in smart cities: Review and prospects. Smart Cities 2023, 6, 2081–2105. [Google Scholar] [CrossRef]
- Qi, L.; Liu, Y.; Yu, Y.; Chen, L.; Chen, R. Current Status and Future Trends of Meter-Level Indoor Positioning Technology: A Review. Remote Sens. 2024, 16, 398. [Google Scholar] [CrossRef]
- Jo, H.G.; Son, T.Y.; Jeong, S.Y.; Kang, S.J. Proximity-based asynchronous messaging platform for location-based Internet of Things service. ISPRS Int. J. Geo Inf. 2016, 5, 116. [Google Scholar] [CrossRef]
- Liu, Q.; Ma, Y.; Alhussein, M.; Zhang, Y.; Peng, L. Green data center with IoT sensing and cloud-assisted smart temperature control system. Comput. Netw. 2016, 101, 104–112. [Google Scholar]
- Hidetoshi, K.; Yanagisawa, Y.; Satoh, T. An anonymous communication technique using dummies for location-based services. In Proceedings of the ICPS’05 International Conference on Pervasive Services, Santorini, Greece, 11–14 July 2005. [Google Scholar]
- Lu, H.; Jensen, C.S.; Yiu, M.L. Pad: Privacy-area aware, dummy-based location privacy in mobile services. In Proceedings of the Seventh ACM International Workshop on Data Engineering for Wireless and Mobile Access, Vancouver, BC, Canada, 13 June 2008. [Google Scholar]
- Hara, T.; Suzuki, A.; Iwata, M.; Arase, Y.; Xie, X. Dummy-Based User Location Anonymization Under Real-World Constraints. IEEE Access 2016, 4, 673–687. [Google Scholar] [CrossRef]
- Yin, C.; Xi, J.; Sun, R. Location Privacy Protection Based on Improved-Value Method in Augmented Reality on Mobile Devices. Mob. Inf. Syst. 2017, 2017, 7251395. [Google Scholar]
- Chen, M.; Li, W.; Chen, X.; Li, Z.; Lu, S.; Chen, D. LPPS: A Distributed Cache Pushing Based K-Anonymity Location Privacy Preserving Scheme. Mob. Inf. Syst. 2016, 2016, 7164126. [Google Scholar] [CrossRef]
- Zhang, S.; Li, M.; Liang, W.; Sandor, V.K.A.; Li, X. A survey of dummy-based location privacy protection techniques for location-based services. Sensors 2022, 22, 6141. [Google Scholar] [CrossRef]
- Alrahhal, H.; Alrahhal, M.S.; Jamous, R.; Jambi, K. A symbiotic relationship based leader approach for privacy protection in location based services. ISPRS Int. J. Geo Inf. 2020, 9, 408. [Google Scholar] [CrossRef]
- Shady, M.; Khemakhem, M.; Jambi, K. Agent-based system for efficient kNN Query processing with comprehensive privacy protection. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 52–66. [Google Scholar] [CrossRef]
- Alrahhal, M.S.; Khemakhem, M.; Jambi, K. A survey on privacy of location-based services: Classification, inference attacks, and challenges. J. Theor. Appl. Inf. Technol. 2017, 95, 6719–6740. [Google Scholar]
- Gupta, A.K.; Shanker, U. Location Privacy Preservation for Location Based Service Applications: Taxonomies, Issues and Future Research Directions. Wirel. Pers. Commun. 2024, 134, 1617–1639. [Google Scholar] [CrossRef]
- Horvath, K.; Kimovski, D. Efficient Location-Based Service Discovery for IoT and Edge Computing in the 6G Era. arXiv 2025, arXiv:2504.00743. [Google Scholar]
- Wang, B.; Li, H.; Ren, X.; Guo, Y. An efficient differential privacy-based method for location privacy protection in location-based services. Sensors 2023, 23, 5219. [Google Scholar] [CrossRef]
- Saravanan, P.; Ramani, S.; Reddy, V.R.; Farhaoui, Y. A novel approach of privacy protection of mobile users while using location-based services applications. Ad Hoc Netw. 2023, 149, 103253. [Google Scholar] [CrossRef]
- Siddiqie, S.; Reddy, P.K.; Annappalli, S.R. Location and Intent Privacy Preservation for Spatial Range Queries in a Mobile Network. IEEE Access 2025, 13, 45998–46013. [Google Scholar] [CrossRef]
- Sun, S.; Qian, Y.; Zhang, R.; Wang, Y.; Li, X. An improved chinese string comparator for Bloom filter based privacy-preserving record linkage. Entropy 2021, 23, 1091. [Google Scholar] [CrossRef]
- Alluhaybi, B.; Alrahhal, M.S.; Alzahrani, A.; Thayananthan, V. Dummy-based approach for protecting mobile agents against malicious destination machines. IEEE Access 2020, 8, 129320–129337. [Google Scholar] [CrossRef]






| Symbol | <X, Y> | POI | R | ID |
|---|---|---|---|---|
| Description | The coordinates of the exact location of the LBS user. | The queried interest. | The queried range. | The identity of the LBS user. |
| Property | Technical Problems | Privacy-Level Degree | Resistance Against Inference Attacks | |||
|---|---|---|---|---|---|---|
| Approach | Heterogeneous Platforms | Network Overhead | K-Anonymity Level | Homogeneity Attack | Semantic Location Attack | |
| CirDummy [9] | × | × | Low | × | × | |
| GridDummy [9] | × | × | Low | × | × | |
| Dest-Ex [10] | × | × | Low | × | × | |
| Ours | √ | √ | High | √ | √ | |
| Agent Name | Type | Location |
|---|---|---|
| M-A-user | Mobile | Each mobile device |
| S-A-cache | Stationary | Access point |
| Cap. No. | Description |
|---|---|
| 1 | Can monitor the current queries that are sent by the LBS users and access/obtain all stored information. |
| 2 | Knows the CaOaDSL algorithm. |
| Term | Number of LBS Users that Exceeded the Threshold | Percentage of Encroachment | |
|---|---|---|---|
| Approach | |||
| CaOaDSL | 2 | 0.1 | |
| Dest-Ex | 12 | 0.6 | |
| CirDummy | 15 | 0.75 | |
| GridDummy | 20 | 100 | |
| Try No. | No. of LBS Users | Percentage of Encroachment | |||||
|---|---|---|---|---|---|---|---|
| CaOaDSL | Dest | Cir | Grid | ||||
| 1 | 40 | 130 | 0.75 | 0.12 | 0.51 | 0.64 | 100 |
| 2 | 60 | 140 | 0.7 | 0.14 | 0.53 | 0.8 | 100 |
| 3 | 80 | 150 | 0.65 | 0.21 | 0.4 | 0.68 | 100 |
| 4 | 100 | 160 | 0.6 | 0.18 | 0.43 | 0.56 | 100 |
| 5 | 120 | 170 | 0.55 | 0.13 | 0.38 | 0.54 | 100 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the International Society for Photogrammetry and Remote Sensing. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aloufi, O.F.; Alfakeeh, A.S.; Alotaibi, F.M. An Agent-Based System for Location Privacy Protection in Location-Based Services. ISPRS Int. J. Geo-Inf. 2025, 14, 433. https://doi.org/10.3390/ijgi14110433
Aloufi OF, Alfakeeh AS, Alotaibi FM. An Agent-Based System for Location Privacy Protection in Location-Based Services. ISPRS International Journal of Geo-Information. 2025; 14(11):433. https://doi.org/10.3390/ijgi14110433
Chicago/Turabian StyleAloufi, Omar F., Ahmed S. Alfakeeh, and Fahad M. Alotaibi. 2025. "An Agent-Based System for Location Privacy Protection in Location-Based Services" ISPRS International Journal of Geo-Information 14, no. 11: 433. https://doi.org/10.3390/ijgi14110433
APA StyleAloufi, O. F., Alfakeeh, A. S., & Alotaibi, F. M. (2025). An Agent-Based System for Location Privacy Protection in Location-Based Services. ISPRS International Journal of Geo-Information, 14(11), 433. https://doi.org/10.3390/ijgi14110433






