Copyright Protection Based on Zero Watermarking and Blockchain for Vector Maps
Abstract
:1. Introduction
2. Basic Idea and Preliminaries
2.1. Zero Watermarking
2.2. Blockchain
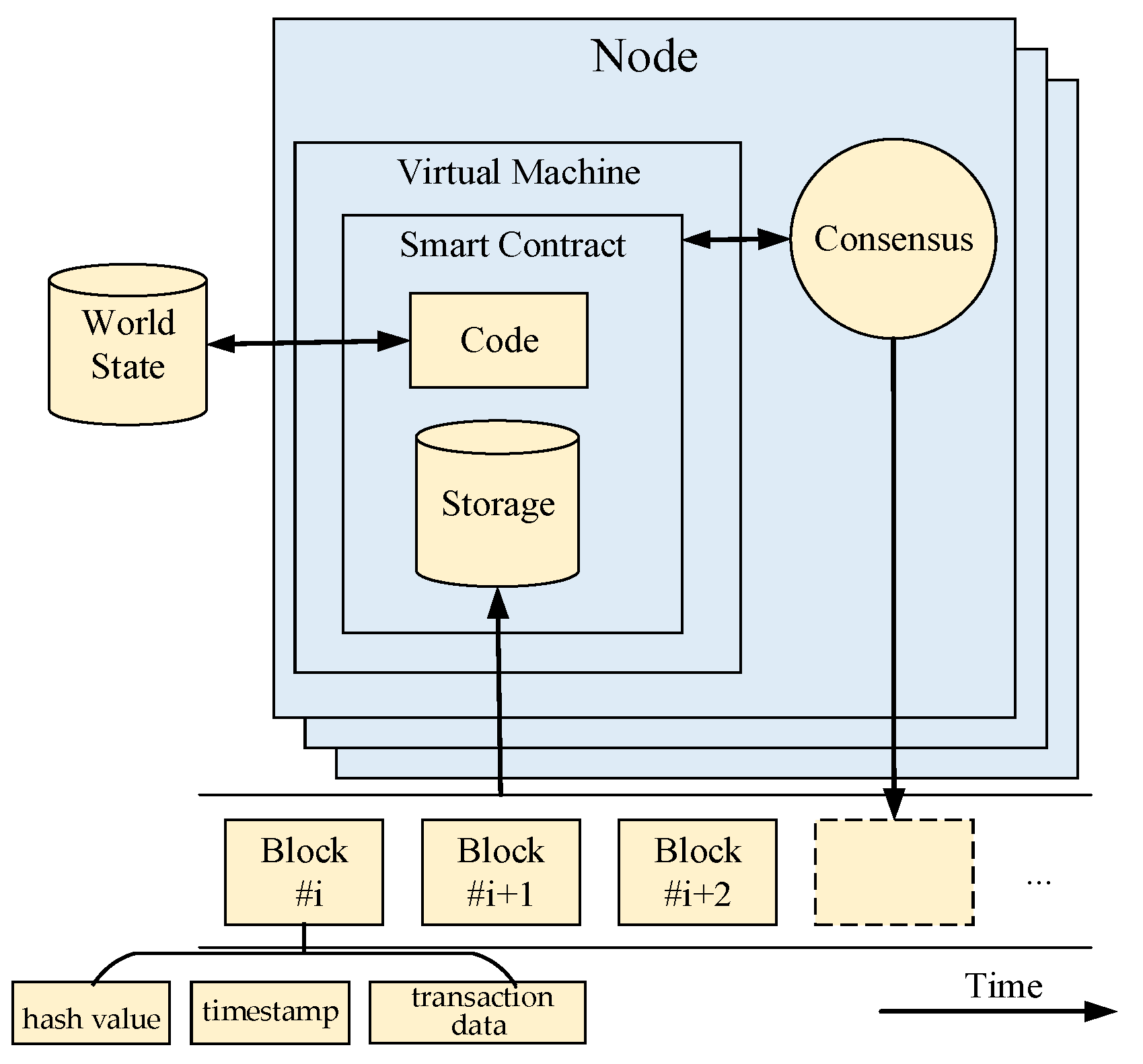
2.2.1. Blockchain Technology
2.2.2. Ant Blockchain Open Alliance
- Smart contract
- Gas
- Virtual machine
- World state
- Consensus algorithm
3. Methods
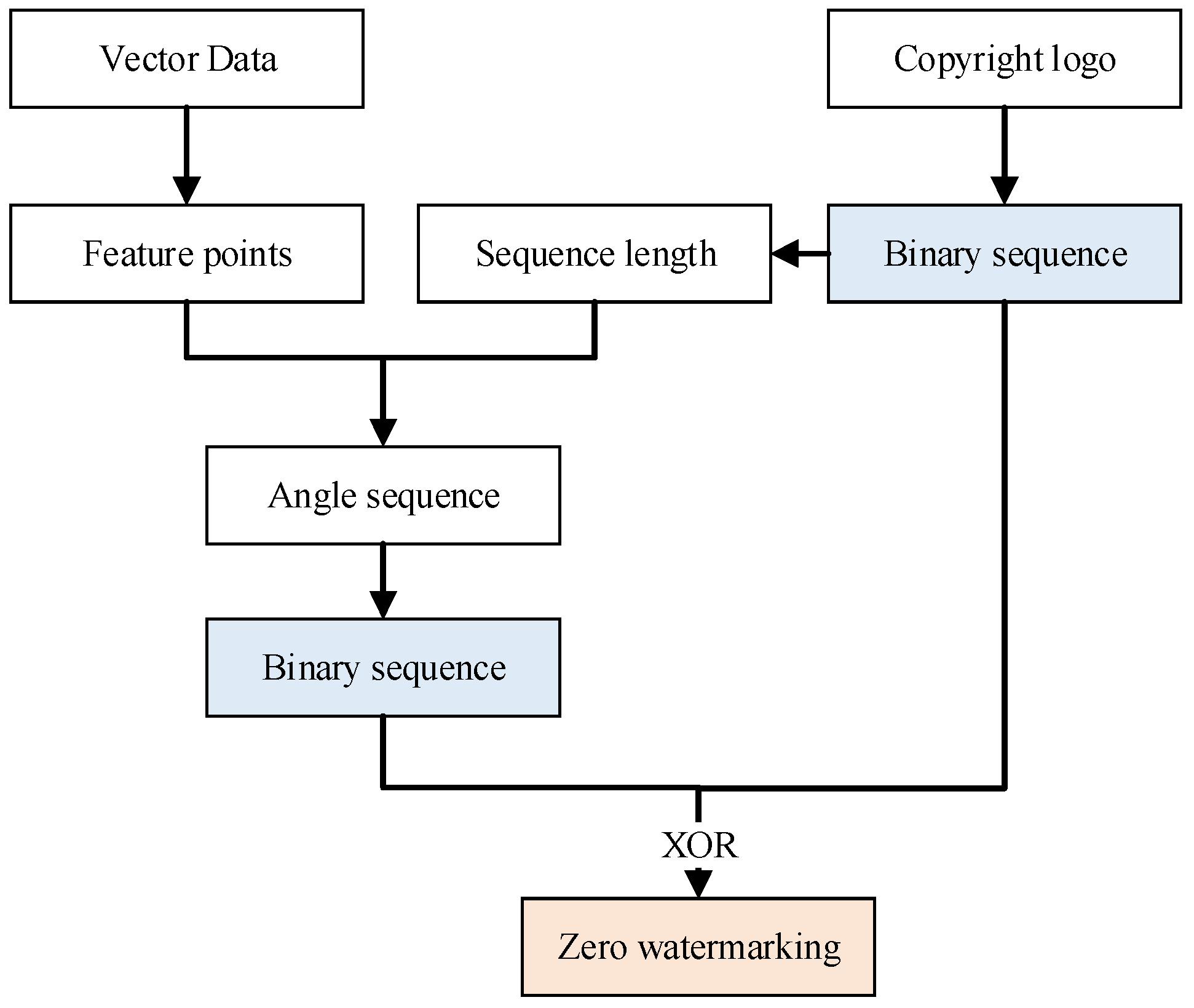
3.1. Zero Watermarking Algorithm
3.1.1. Feature Point Extraction
3.1.2. Angle Calculation
3.1.3. Construction of a Zero Watermark
3.1.4. Extraction of the Zero Watermark
3.1.5. Zero Watermarking Forensics
3.2. Smart Contract and Storage System Design
3.2.1. Smart Contract Design
- initContractData: only the DU can execute the interface, whose function is to compose the block with the DU_AD, RU_AD and ZW, and the return value is CONTRACT_BC;
- searchContract: both the DU and RU can execute this interface. Its function is to return the information of the contract. If it is not initialized, it will return null;
- dataDistribution: only the DU can execute the interface. Its function is to return the THX of the uploaded block.
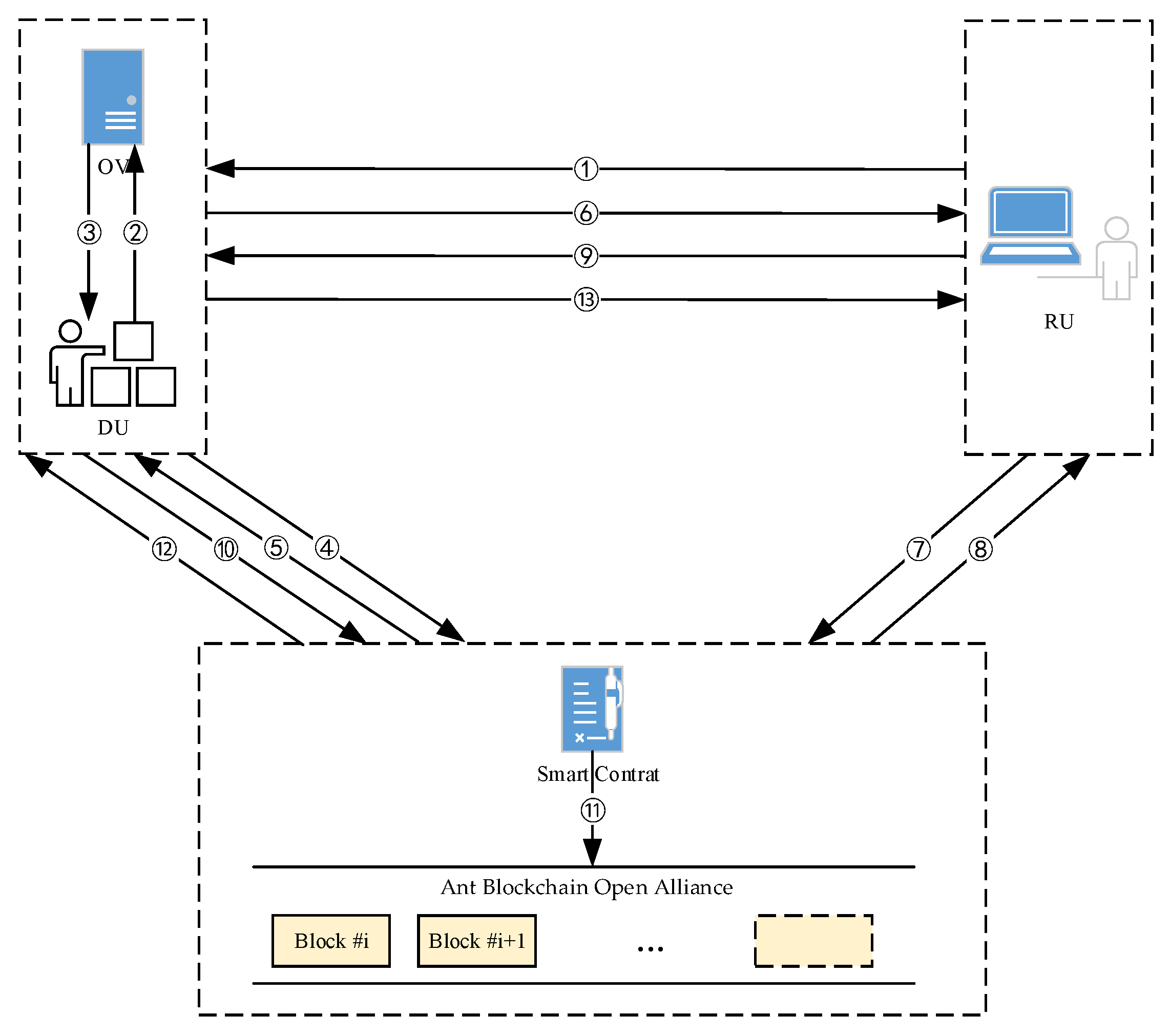
3.2.2. Zero Watermarking Storage System Design
- RU sends RU_AD and the request for OV to the DU.
- After confirming the identity of the RU, the DU will use the proposed algorithm to extract the ZW of OV in SERVER.
- SERVER returns the extracted ZW to the DU.
- DU deploys the ZW, DU_AD, and RU_AD to the smart contract.
- The smart contract constructs information into the BLOCK and returns CONTRACT_BC to the DU.
- DU sends the CONTRACT_BC to the RU.
- RU uses the CONTRACT_BC to access the smart contract.
- The smart contract returns the ZW, DU_AD, and RU_AD to the RU.
- After confirming the RU_AD is correct, the RU returns the confirmation information to the DU.
- The DU sends the confirmation information to the smart contract.
- The smart contract uploads the BLOCK to the blockchain.
- The smart contract returns the THX to the DU.
4. Experiments and Results
4.1. Zero Watermarking Experiment and Results
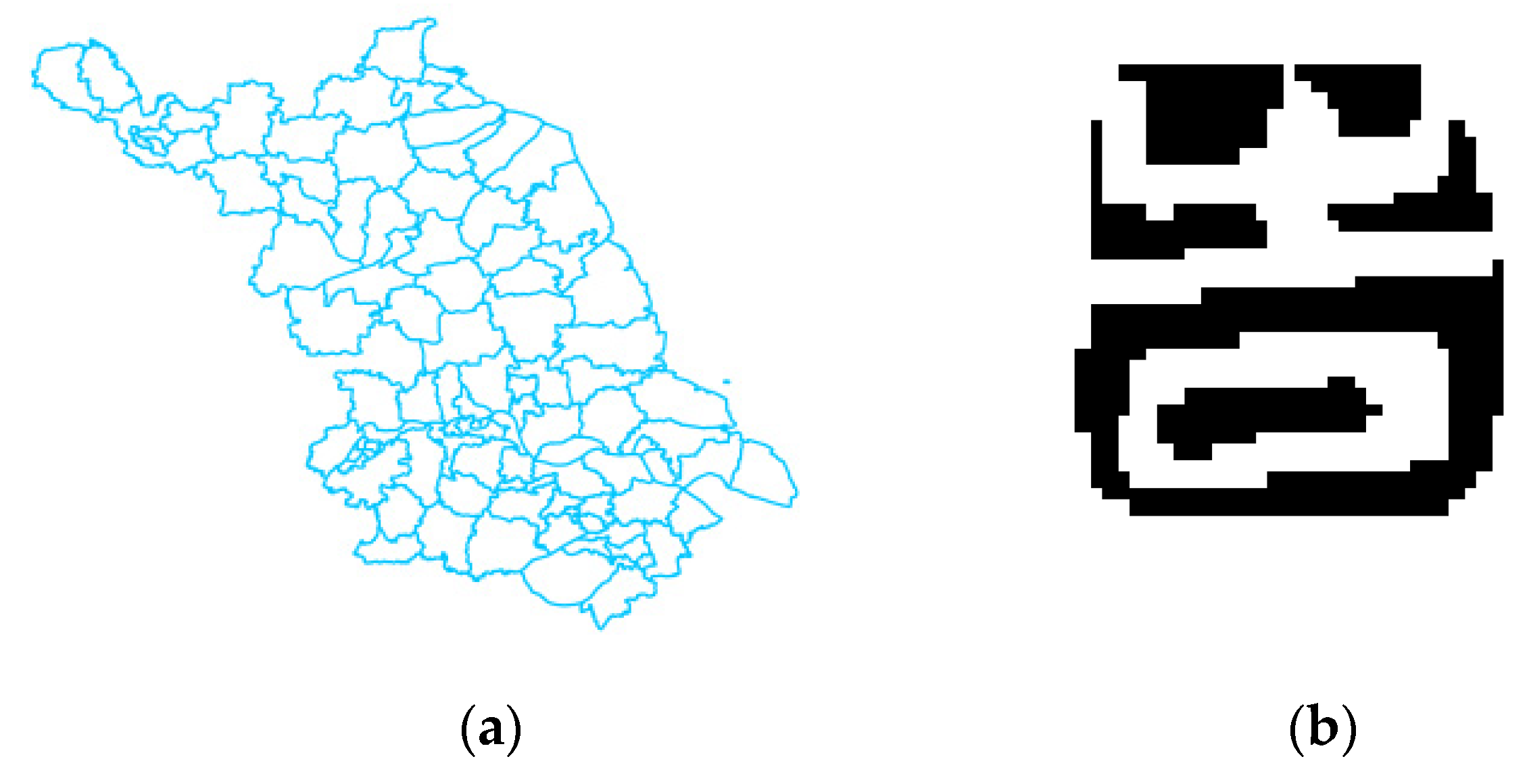
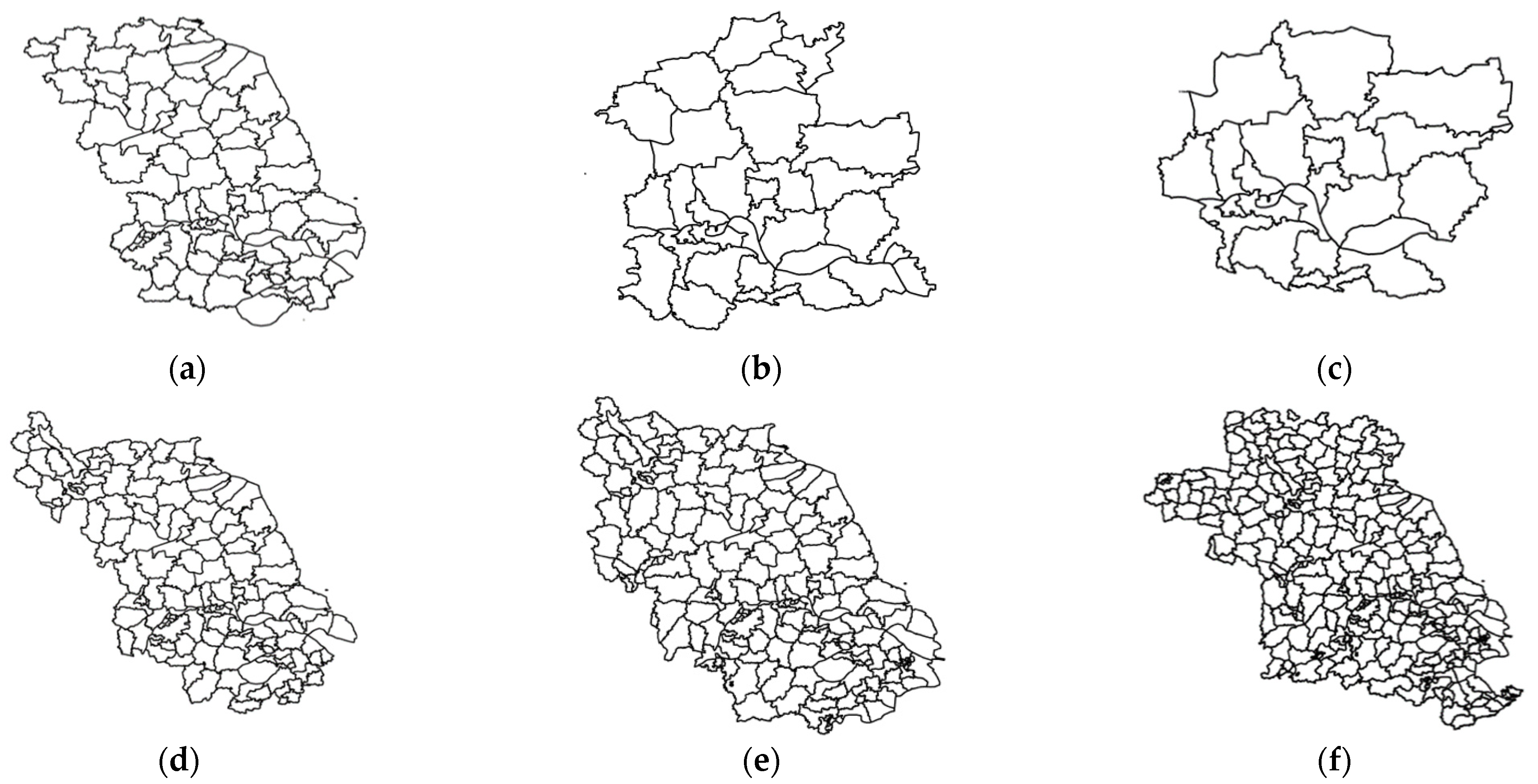
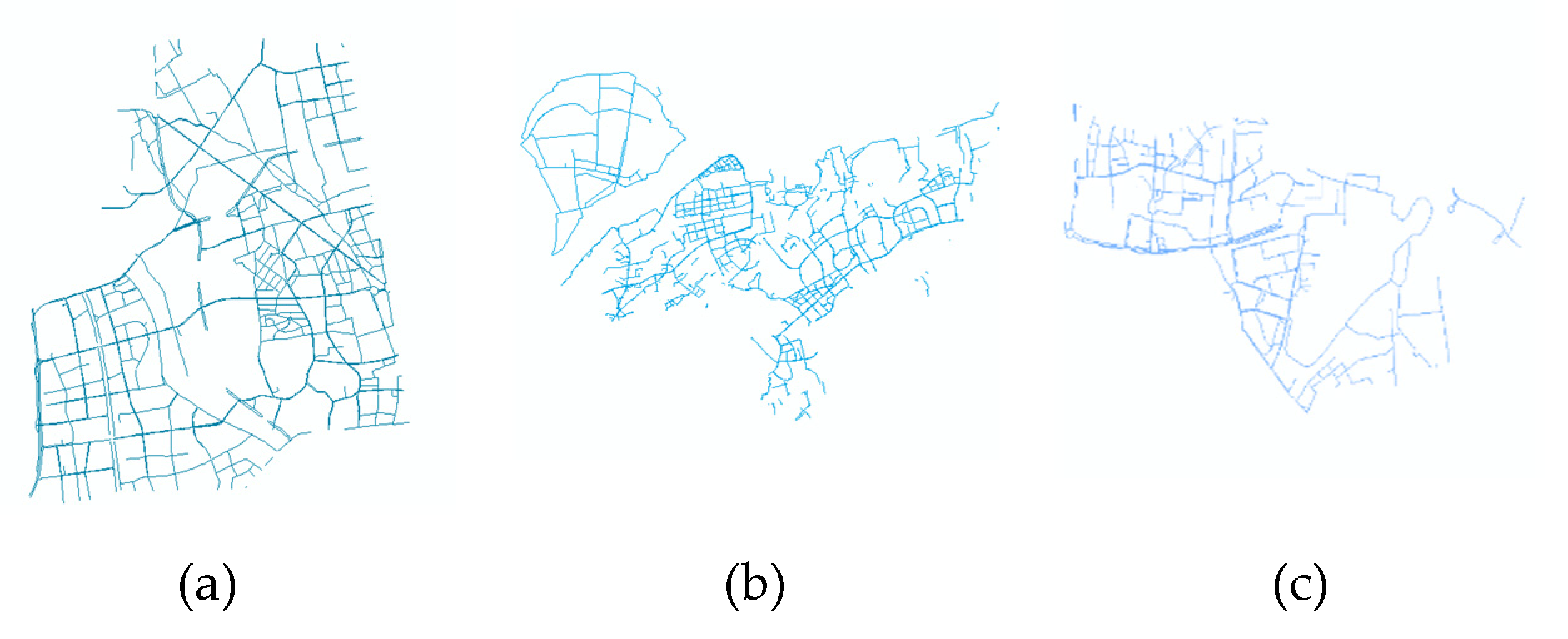
4.1.1. Experimental Data and Parameter Settings
4.1.2. Geometrical Attacks
4.1.3. Cropping and Adding
4.1.4. Compression Attacks
4.2. Blockchain Experiment and Results
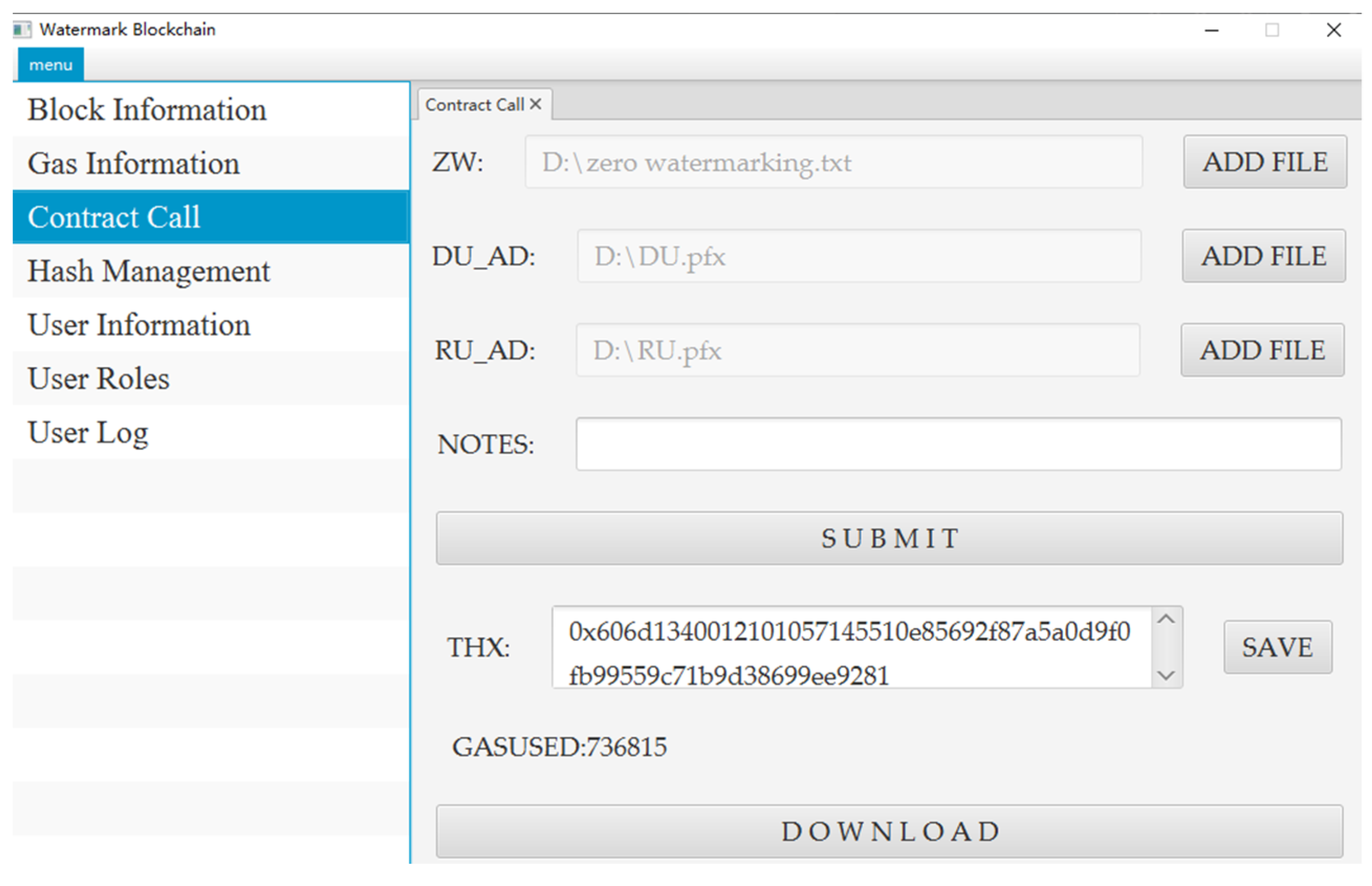
4.2.1. System Implementation
4.2.2. Gas Cost
5. Discussion
5.1. Comparison with Other Algorithms
5.1.1. Uniqueness Verification
5.1.2. Robustness Comparison
5.2. Comparison between the Blockchain Framework and the Traditional IPR Framework
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Lee, S.H.; Kwon, K.R. Vector watermarking scheme for GIS vector map management. Multimed. Tools Appl. 2013, 63, 757–790. [Google Scholar] [CrossRef]
- Wang, Y.Y.; Yang, C.S.; Zhu, C.Q.; Ding, K.M. An Efficient Robust Multiple Watermarking Algorithm for Vector Geographic Data. Information 2018, 9, 296. [Google Scholar] [CrossRef] [Green Version]
- Yan, H.W.; Zhang, L.M.; Yang, W.F. A normalization-based watermarking scheme for 2D vector map data. Earth Sci. Inf. 2017, 10, 471–481. [Google Scholar] [CrossRef]
- Tong, D.; Zhu, C.; Ren, N. Watermarking Algorithm Applying to Small Amount of Vector Geographical Data. Acta Geod. Et Cartogr. Sin. 2018, 47, 1518–1525. [Google Scholar]
- Xu, D.; Zhu, C.; Wang, Q. Blind Watermarking Model of Vector Spatial Data Based on DFT of QIM. Geomat. Inf. Sci. Wuhan Univ. 2010, 35, 1100–1103. [Google Scholar]
- Zhang, L.; Yan, H.; Lv, W. A Blind Watermarking Algorithm Robust to Projection Attacks for Vector Data. Remote Sens. Inf. 2017, 32, 175–180. [Google Scholar]
- Cao, L.J.; Men, C.G.; Gao, Y. A recursive embedding algorithm towards lossless 2D vector map watermarking. Digit. Signal Process. 2013, 23, 912–918. [Google Scholar] [CrossRef]
- Wang, X.; Shao, C.; Xu, X.; Niu, X. Reversible data-hiding scheme for 2-d vector maps based on difference expansion. IEEE Trans. Inf. Sec. 2007, 2, 311–320. [Google Scholar] [CrossRef]
- Chengyong, S.; Xiaotong, W.; Xiaogang, X.U.; Xiamu, N.I.U. Study on Lossless Data Hiding Algorithm for Digital Vector Maps. J. Image Graph. 2007, 12, 206–211. [Google Scholar]
- Peng, F.; Jiang, W.-Y.; Qi, Y.; Lin, Z.-X.; Long, M. Separable Robust Reversible Watermarking in Encrypted 2D Vector Graphics. IEEE Trans. Circuits Syst. Video Technol. 2020, 30, 2391–2405. [Google Scholar] [CrossRef]
- Sun, J.; Zhang, G.; Yao, A.; Wu, J. Lossless Digital Watermarking Technology for Vector Maps. Acta Electron. Sin. 2010, 38, 2786–2790. [Google Scholar] [CrossRef]
- Zhou, Q.; Ren, N.; Zhu, C.; Tong, D. Storage Feature-Based Watermarking Algorithm with Coordinate Values Preservation for Vector Line Data. Ksii Trans. Internet Inf. Syst. 2018, 12, 3475–3496. [Google Scholar] [CrossRef] [Green Version]
- Ren, N.; Zhou, Q.; Zhu, C.; Zhu, A.X.; Chen, W. A Lossless Watermarking Algorithm Based on Line Pairs for Vector Data. Ieee Access 2020, 8, 156727–156739. [Google Scholar] [CrossRef]
- Wen, Q.; Sun, T.; Wang, S. Concept and Application of Zero-Watermark. Acta Electron. Sin. 2003, 31, 214–216. [Google Scholar]
- Sun, Y.; Li, D. Vector Map Zero-Watermark Algorithm Based on Node Feature. Geogr. Geo Inf. Sci. 2017, 33, 17–21. [Google Scholar]
- Zhao, H.; Du, S.; Zhang, D. Zero-Watermark Scheme for 2D Vector Drawings Based on Mapping. In Proceedings of the 2011 IEEE 12th International Conference on Computer-Aided Industrial Design & Conceptual Design, Vols 1 and 2: New Engines for Industrial Design: Intelligence-Interaction-Services, New York, NY, USA, 27–29 November 2011; pp. 366–370. [Google Scholar]
- Lyu, W.; Zhang, L. A DFT-Based Zero-Watermarking Agorithm for Vector Geodata. J. Geomat. Sci. Technol. 2018, 35, 94–98, 104. [Google Scholar]
- Zeng, W.; Xiong, X. Robust Zero Watermarking Algorithm Based on Integer Wavelet Transform. Microelectron. Comput. 2016, 33, 97–101, 107. [Google Scholar]
- Li, W.; Yan, H.; Wang, Z.; Zhang, L. A Zero-Watermarking Algorithm for Vector Linear Feature Data. J. Geomat. Sci. Technol. 2016, 33, 94–98. [Google Scholar]
- Lyu, W.; Zhang, L. A zero-watermark algorithm for vector data based on distribution center. Eng. Surv. Mapp. 2017, 26, 50–53, 61. [Google Scholar]
- Liang, W.; Zhang, X.; Xi, X.; Zhang, P. A multiple watermarking algorithm for vector geographic data based on zero-watermarking and fragile watermarking. Acta Sci. Nat. Univ. Sunyatseni 2018, 57, 1–8. [Google Scholar]
- Xin, Y.; Ting, Y. A Practical Scheme of Defeating Interpretation Attack of Digital Watermarking. In Proceedings of the 2009 International Conference on Image Analysis and Signal Processing 2009, Taizhou, China, 11–12 April 2009; pp. 91–93. [Google Scholar]
- Nakamoto, S. A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 10 April 2021).
- Zheng, Z.B.; Xie, S.A.; Dai, H.N.; Chen, X.P.; Wang, H.M. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. IEEE Int. Congr. Big 2017, 557–564. [Google Scholar] [CrossRef]
- Atzei, N.; Bartoletti, M.; Cimoli, T. A Survey of Attacks on Ethereum Smart Contracts (SoK). Lect. Notes Comput. Sci. 2017, 10204, 164–186. [Google Scholar] [CrossRef]
- Xu, C.; Li, X. Data Privacy Protection Method of Block Chain Transaction. Comput. Sci. 2020, 47, 281–286. [Google Scholar]
- Savelyev, A. Copyright in the blockchain era: Promises and challenges. Comput. Law Secur. Rev. 2018, 34, 550–561. [Google Scholar] [CrossRef] [Green Version]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3690–3700. [Google Scholar] [CrossRef] [Green Version]
- Zhang, A.; Lin, X. Towards Secure and Privacy-Preserving Data Sharing in e-Health Systems via Consortium Blockchain. J. Med Syst. 2018, 42. [Google Scholar] [CrossRef] [PubMed]
- Buy Open Alliance Chain Fuel. Available online: https://product.cloud.alipay.com/common-buy?productCode=GAS&tenantName=FPANPSDP (accessed on 22 April 2021).
- Zuo-li, Z.; Shu-sen, S.U.N.; Ya-ming, W.; Ke-biao, Z. Zero-watermarking algorithm for 2D vector map. Comput. Eng. Des. 2009, 30, 1474–1479. [Google Scholar]
- Xun, W.; Huang, D.; Zhang, Z. A robust zero-watermarking algorithm for vector digital maps based on statistical characteristics. Softw. Appl. Econ. Anal. Bus. Manag. 2012, 7, 2349. [Google Scholar]
- Li, A.-B.; Zhu, A.X. Copyright authentication of digital vector maps based on spatial autocorrelation indices. Earth Sci. Inf. 2019, 12, 629–639. [Google Scholar] [CrossRef]
- Peng, W.; Yi, L.; Fang, L.; XinHua, D.; Ping, C. Secure and Traceable Copyright Management System Based on Blockchain. In Proceedings of the 2019 IEEE 5th International Conference on Computer and Communications (ICCC), Chengdu, China, 6–9 December 2019; pp. 1243–1247. [Google Scholar]
- Xu, R.Z.; Zhang, L.; Zhao, H.W.; Peng, Y. Design of Network Media’s Digital Rights Management Scheme Based on Blockchain Technology. In Proceedings of the 2017 Ieee 13th International Symposium on Autonomous Decentralized Systems (Isads 2017), Bangkok, Thailand, 22–24 March 2017; pp. 128–133. [Google Scholar] [CrossRef]
- Zhao, C.; Liu, M.; Yang, Y.; Zhao, F.; Chen, S. Toward a Blockchain Based Image Network Copyright Transaction Protection Approach. In Advances in Intelligent Systems and Computing; Yang, C.N., Peng, S.L., Jain, L.C., Eds.; Springer International Publishing Ag: Cham, Switzerland, 2020; Volume 895, pp. 17–28. [Google Scholar]





| Abbreviation | Description |
|---|---|
| DU | Distribution Unit, the owner of data, responsible for the distribution of data |
| RU | Receiving Unit, the receiver of data |
| DU_AD | Account address of distribution unit |
| RU_AD | Account address of receiving unit |
| CONTRACT_BC | The byte code of the smart contract |
| BLOCK | The block constructed of ZW, DU_AD, and RU_AD |
| SERVER | The server is used to store vector geographic data and extract the zero watermarking algorithm |
| OV | Original vector map data |
| ZW | Zero watermarking extracted from the original vector map data |
| THX | The unique hash value generated after a successful transaction on the blockchain |
| Attack Type | Attack Degree or Mode | Extraction Result | NC |
|---|---|---|---|
| Translation | Translation 5 meter |  | 1.000 |
| Translation 10 meter |  | 1.000 | |
| Translation 20 meter |  | 1.000 | |
| Scaling | Scaling 0.5 |  | 1.000 |
| Scaling 2 |  | 1.000 | |
| Scaling 5 |  | 1.000 | |
| Rotating | Rotate |  | 1.000 |
| Rotate |  | 1.000 | |
| Rotate |  | 1.000 |
| Attack Type | Attack Degree or Mode | Extraction Result | NC |
|---|---|---|---|
| Cropping | Cut 10% |  | 1.000 |
| Cut 70% |  | 1.000 | |
| Cut 80% |  | 0.532 | |
| Adding | Add 10% |  | 1.000 |
| Add 50% |  | 1.000 | |
| Add 100% |  | 1.000 |
| Attack Type | Attack Degree or Mode | Extraction Result | NC |
|---|---|---|---|
| Compression | Compressed 10% |  | 1.000 |
| Compressed 50% |  | 1.000 | |
| Compressed 90% |  | 1.000 |
| Vector Data | NC | ||||
|---|---|---|---|---|---|
| Proposed | [20] | [31] | [32] | [33] | |
| Gulou District | 1.000 | 1.000 | 1.000 | 1.000 | 1.000 |
| Qinhuai District | 0.523 | 0.972 | 0.480 | 0.828 | 0.671 |
| Xuanwu District | 0.541 | 0.981 | 0.454 | 0.831 | 0.557 |
| Evaluation Indicator | Blockchain Framework | Traditional IPR Framework |
|---|---|---|
| credibility | strong | common |
| audit cycle | not needed | long |
| cost | negligible | expensive |
| interpretation attack | can resist | unable to resist |
| traceability | yes | no |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ren, N.; Zhao, Y.; Zhu, C.; Zhou, Q.; Xu, D. Copyright Protection Based on Zero Watermarking and Blockchain for Vector Maps. ISPRS Int. J. Geo-Inf. 2021, 10, 294. https://doi.org/10.3390/ijgi10050294
Ren N, Zhao Y, Zhu C, Zhou Q, Xu D. Copyright Protection Based on Zero Watermarking and Blockchain for Vector Maps. ISPRS International Journal of Geo-Information. 2021; 10(5):294. https://doi.org/10.3390/ijgi10050294
Chicago/Turabian StyleRen, Na, Yazhou Zhao, Changqing Zhu, Qifei Zhou, and Dingjie Xu. 2021. "Copyright Protection Based on Zero Watermarking and Blockchain for Vector Maps" ISPRS International Journal of Geo-Information 10, no. 5: 294. https://doi.org/10.3390/ijgi10050294
APA StyleRen, N., Zhao, Y., Zhu, C., Zhou, Q., & Xu, D. (2021). Copyright Protection Based on Zero Watermarking and Blockchain for Vector Maps. ISPRS International Journal of Geo-Information, 10(5), 294. https://doi.org/10.3390/ijgi10050294






