SMS: A Secure Healthcare Model for Smart Cities
Abstract
1. Introduction
1.1. Paper Organization
1.2. Main Contributions
- Identifying the limitations of classical healthcare systems and their inapplicability in smart cities ecosystems.
- Identifying the need for transitioning from the cloud to edge and the role of mobile edge computing in providing real-time healthcare services.
- Identifying security vulnerabilities in MEC and the possible solutions.
- Proposing a smart healthcare model for smart cities based on MEC, IoT, and blockchain consensus mechanisms for the reliable, faster, secured, and transparent interconnection of participating entities of the healthcare system.
2. Need for Transition from Cloud to Edge in a Smart City Ecosystem
2.1. Mobile Edge Computing (MEC)
- The large amount of data generated at the edges of the network (sensors, devices, etc.) requires, in a cloud architecture, the transmission of a large amount of data across the network, which is the origin of the bottleneck that is currently seen in the cloud paradigm. If we use the example of a Boeing 787, which is estimated to generate 5 gigabytes of data per second, it is easy to conclude that a system using the cloud paradigm will not scale to support such or similar situations [16].
- Data producers in an IoT solution (such as sensors, mobile devices, traffic lights, lights, appliances, etc.) will grow exponentially and reach billions in the coming years. In a cloud computing architecture, data consumers obtain the information they want after requesting it to the cloud, which will no longer be possible considering the amount and increasing number of data producers.
- In today’s scenarios with the proliferation of mobile devices and even other wearables, data consumers will also act as producers of data (uploading and sharing multimedia contents) and hence the cloud paradigm will not be enough. In addition, the data being produced on the edges tend to be more personal (photos, videos, etc.), raising privacy issues that will be more easily addressed by maintaining edge processing.
2.2. Security Vulnerabilities in Mobile Edge Computing
- Insecure IoT Devices: The efficiency and reliability of edge computing are highly dependent on the “security” and “privacy” features of the smart devices. The IoT devices and the data generated by them are always at a high risk. Any compromised device might lead to a bad decision. Most of the IoT device manufacturers are mainly concerned about the working of the device and its functionality. There are hardly any inherent security features included within the IoT devices as it is of the least concern [10,11,17,18,19,20].
- Identification of Usable Data: Although processing data at the device level helps to improve the latency and response time, it might lead to incomplete data at the main information repository. Due to the limited processing and storage capabilities at the edge, there are chances that an important portion of the data may be of greater usage if left out [10,11,17,18,19,20,21].
- Lack of Unified Security Standards: The different IoT devices are mostly of different make and follow their specific syntax, semantics, and operating standards. Up until now, there is no unified security standard available that is universally applicable across all categories of IoT devices. Furthermore, the weakly coupled edge devices on the network are vulnerable to physical and cyber-attacks, making privacy preservation a difficult task [10,11,17,18,19,20,21].
- Distributed Denial of Service (DDoS) Attacks: DDOS attacks constitute the most widely reported security threats to mobile edge computing. The attackers flood the devices with data packets through compromised devices, which then deny the services to the legitimate users. In addition, a compromised edge device may restrict the normal services by targeting the edge server with a DOS attack [10,11,17,18,19,20,21].
- Side Channel Attacks: The user’s general data and information patterns can be accessed and collected overtime. This information may not be sensitive and private but, over time, it can be used to profile the user and get ahold of the user’s private data by linking it through side channels [10,11,17,18,19,20,21].
3. Related Works
Research Gaps and Motivations
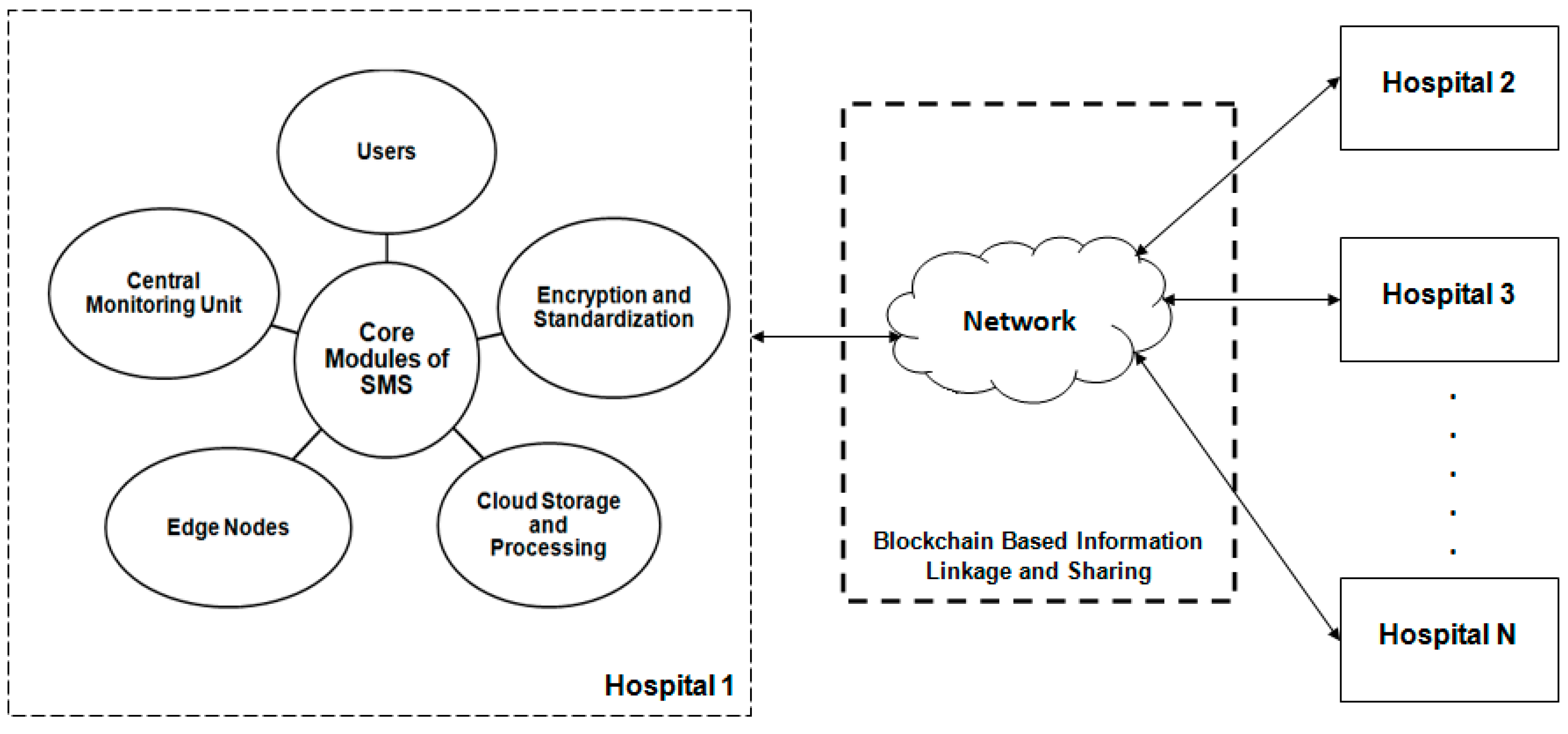
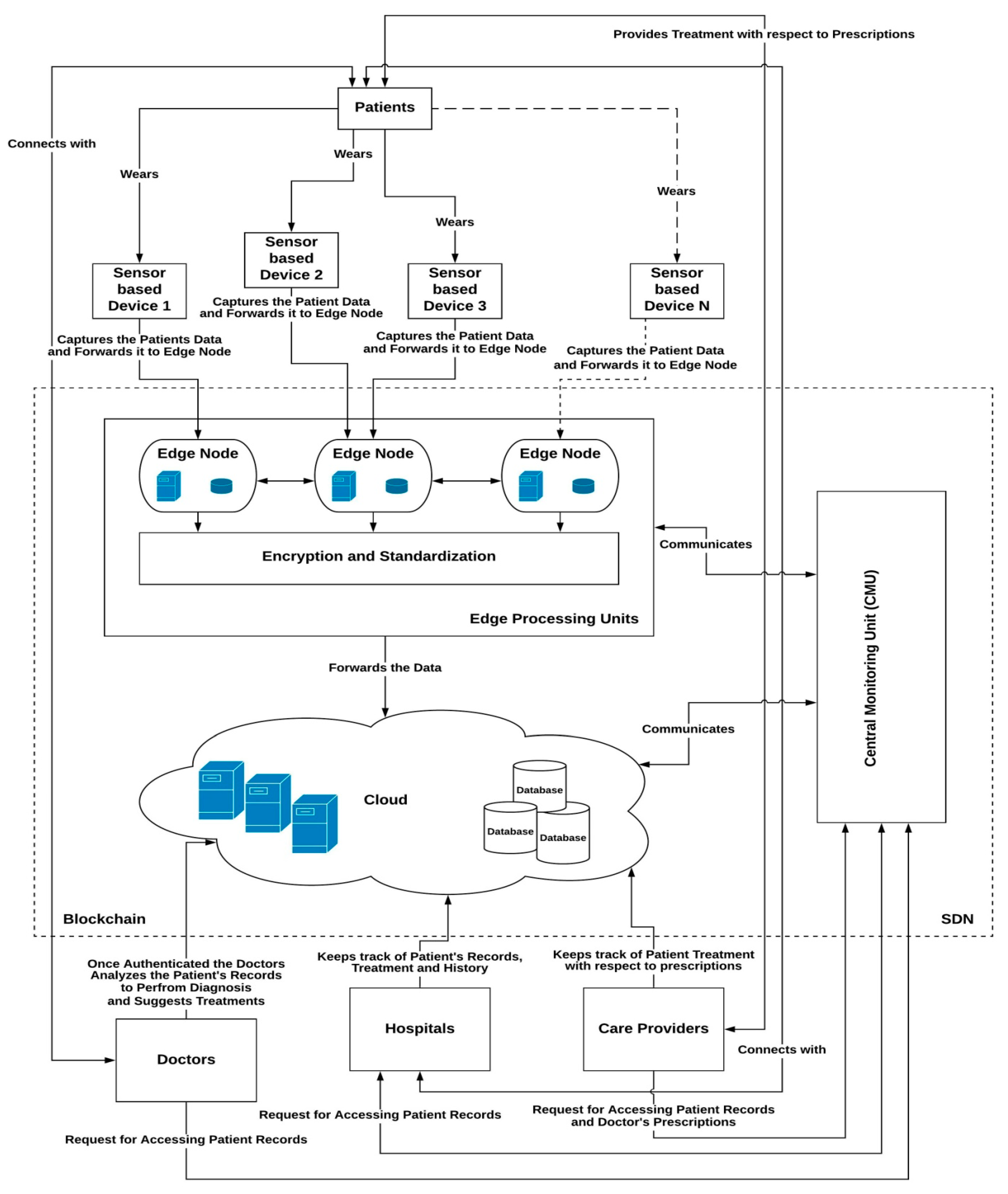
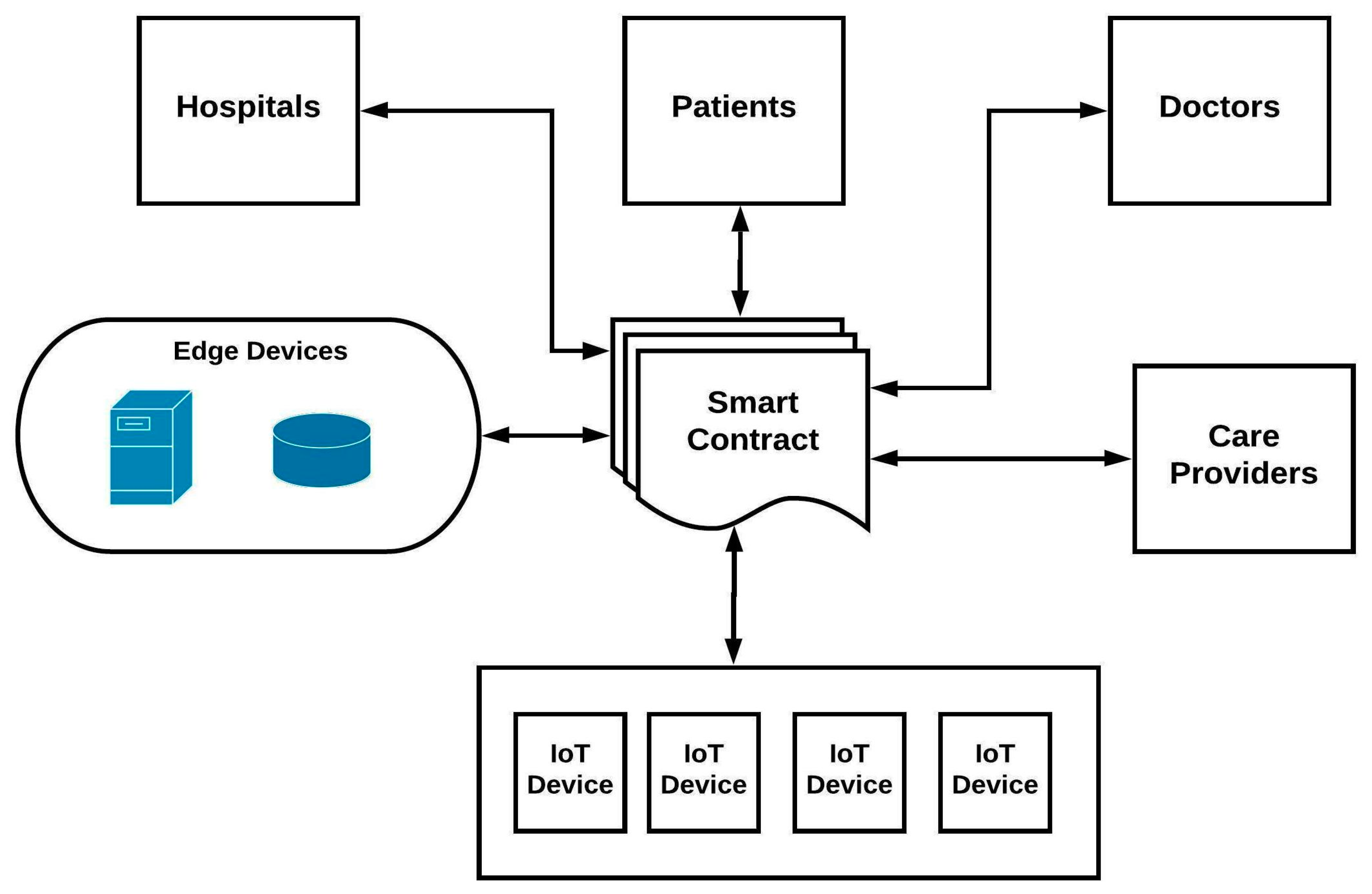
4. Proposed SMS Framework
4.1. Overview and Architecture
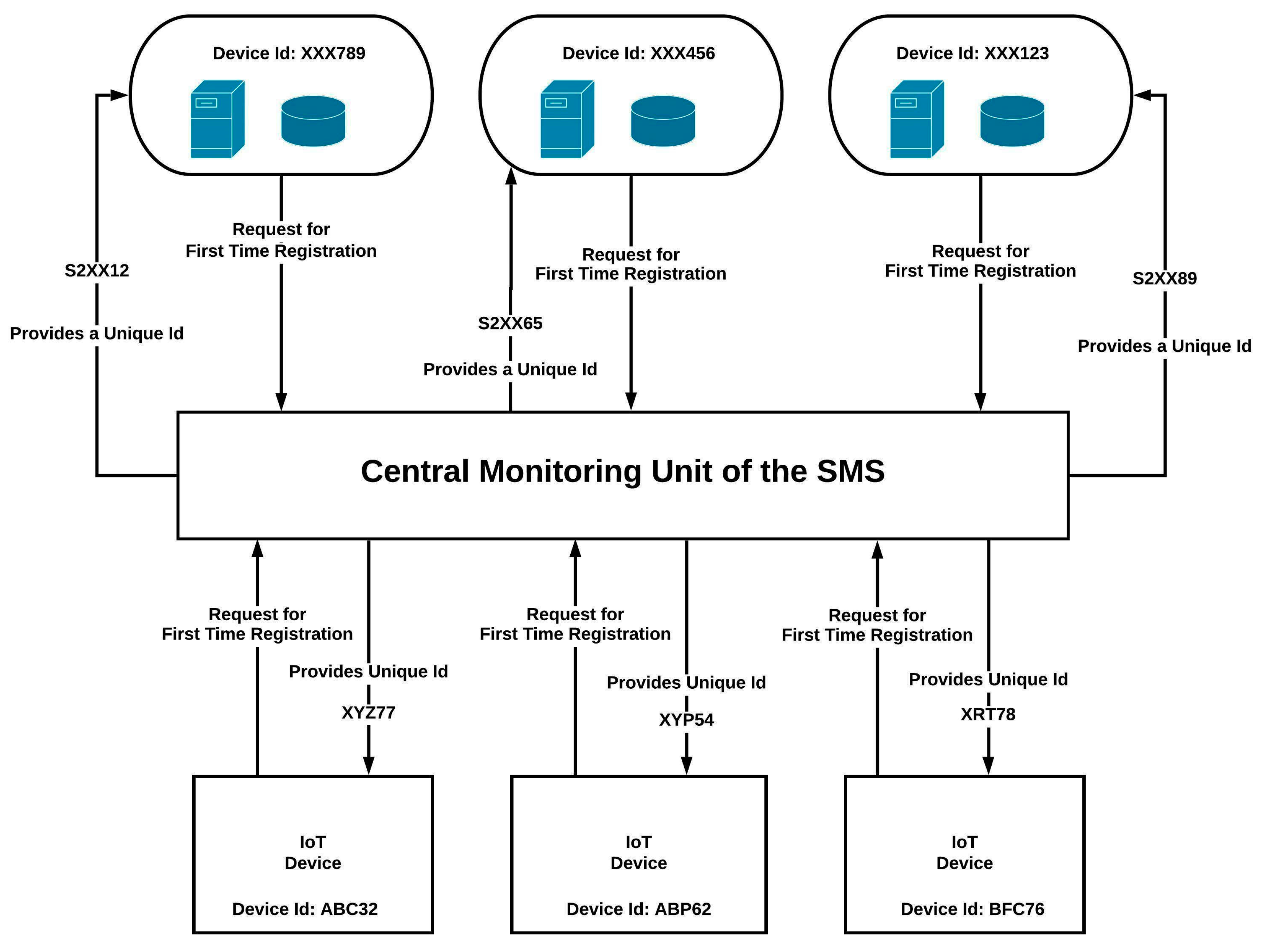
4.2. Components of SMS
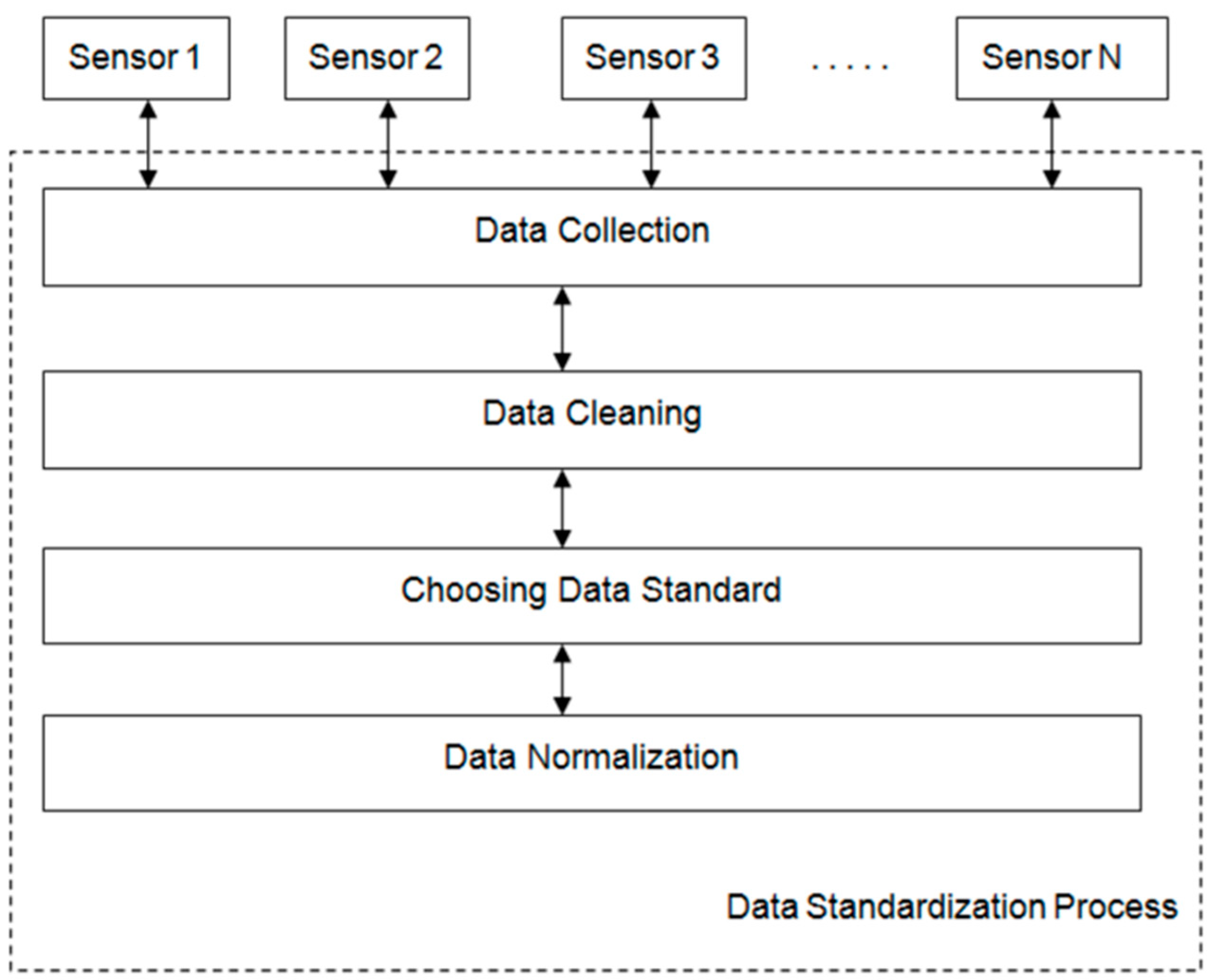
4.3. Three Stages of the Proposed Approach
- Phase 1-Data collection
- Phase 2-Data Encryption and Standardization
- Phase 3-Data Storage
4.4. Role of IoT in SMS
- MQTT: This is a very lightweight protocol responsible for sharing information between two devices. It supports “machine-to-machine (M2M)” communication and works on the principle of the “publish-subscribe” communication pattern usually using TCP/IP [67].
- OMA-DM: This is a device management protocol responsible for managing the devices connected in an IoT network. It works in the client server model. OMA-DM works in sessions. A typical session comprises two phases. The first phase is known as the “setup,” while the second phase is known as the “management” phase. The setup phase contains authentication and device information, while in the management phase, the commands issued by DM server are executed by DM clients [67].
- 6LowPAN: This provides a low-power wireless connection over IPv6. It is used to provide end-to-end connectivity for the transfer of data in a WSN. It has an inbuilt encryption and compression mechanism that takes care of the security and speed of the data transferred [67].
- CoAP: CoAP is primarily used for low-resourced devices like sensors nodes. They can provide multicast support, minimal overhead, and ease of usage [67].
- XMPP: This stands for “Extensible Messaging and Presence Protocol’. It is mainly used in “real-time communication” like “instant messaging,” “voice and video calls,” chatting, etc.
- ZigBee: This is a protocol that uses the IEEE 82.15.4 standard and is used for low-powered sensor devices. They are highly cost-effective and perform very well in several varieties of applications like home automation, personal health monitoring, etc. [67].
4.5. Data Analytics in SMS
5. Role of MEC in the Proposed SMS
Blockchain in SMS
- Medical data safety
- Interoperability
- Loans and payments
- Health insurance
- Research and development
- Social Service/Philanthropic activities
| Algorithm 1 Request Handling in SMS |
| 1: Request→Ri 2: Request Type (RT)→{Urgent, Normal}; 3: For ∀ Ri ∈ RT 4: If (Ri = = Urgent) 5: Forward the Data/Request to Edge Nodes 6: Process the Data/Request 7: Return the results to the User 8: Else 9: Forward the data/Request to the Cloud 10: Process the Data 11: Return the data to the user |
6. Conclusions and Future Scope
Author Contributions
Funding
Conflicts of Interest
References
- Ashton, K. That ‘internet of things’ thing. RFID J. 2009, 22, 97–114. [Google Scholar]
- Ahad, M.A.; Paiva, S.; Tripathi, G.; Feroz, N. Enabling Technologies and Sustainable Smart Cities. Sustain. Cities Soc. 2020, 61, 102301. [Google Scholar] [CrossRef]
- Ahad, M.A.; Tripathi, G.; Agarwal, P. Learning analytics for IoE based educational model using deep learning techniques: Architecture, challenges and applications. Smart Learn. Environ. 2018, 5, 1–16. [Google Scholar] [CrossRef]
- Ahad, M.A.; Biswas, R. Dynamic merging based small file storage (DM-SFS) architecture for efficiently storing small size files in hadoop. Procedia Comput. Sci. 2018, 132, 1626–1635. [Google Scholar] [CrossRef]
- Ahad, M.A.; Biswas, R. Request-based, secured and energy-efficient (RBSEE) architecture for handling IoT big data. J. Inf. Sci. 2019, 45, 227–238. [Google Scholar] [CrossRef]
- Madaan, N.; Ahad, M.A.; Sastry, S.M. Data integration in IoT ecosystem: Information linkage as a privacy threat. Comput. Law Secur. Rev. 2018, 34, 125–133. [Google Scholar] [CrossRef]
- Tripathi, G.; Ahad, M.A. IoT in Education: An Integration of Educator Community to Promote Holistic Teaching and Learning. In Soft Computing in Data Analytics; Springer: Singapore, 2019. [Google Scholar]
- Yu, W.; Liang, F.; He, X.; Hatcher, W.G.; Lu, C.; Lin, J.; Yang, X. A survey on the edge computing for the Internet of Things. IEEE Access 2017, 6, 6900–6919. [Google Scholar] [CrossRef]
- Satyanarayanan, M. The emergence of edge computing. Computer 2017, 50, 30–39. [Google Scholar] [CrossRef]
- Sittón-Candanedo, I.; Corchado Rodríguez, J. An Edge Computing Tutorial. Orient. J. Comput. Sci. Technol. 2019, 12, 34–38. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Sajid, A.; Abbas, H. Data privacy in cloud-assisted healthcare systems: State of the art and future challenges. J. Med. Syst. 2016, 40, 155. [Google Scholar] [CrossRef] [PubMed]
- Khattak HA, K.; Abbass, H.; Naeem, A.; Saleem, K.; Iqbal, W. Security concerns of cloud-based healthcare systems: A perspective of moving from single-cloud to a multi-cloud infrastructure. In Proceedings of the 2015 17th International Conference on E-health Networking, Boston, MA, USA, 14–17 October 2015. [Google Scholar]
- Mahmud, R.; Koch, F.L.; Buyya, R. Cloud-fog Interoperability in IoT-enabled Healthcare Solutions. In Proceedings of the 19th International Conference on Distributed Computing and Networking. Available online: https://dl.acm.org/doi/10.1145/3154273.3154347 (accessed on 8 June 2020).
- Evans, D. The Internet of Things: How the next evolution of the Internet is changing everything. Cisco White Pap. 2011, 1, 1–11. [Google Scholar]
- Mark, v.R. Boeing 787s to Create Half a Terabyte of Data Per Flight. Available online: https://datafloq.com/read/self-driving-cars-create-2-petabytes-data-annually/172 (accessed on 7 December 2016).
- Chen, M.; Li, W.; Hao, Y.; Qian, Y.; Humar, I. Edge cognitive computing based smart healthcare system. Future Gener. Comput. Syst. 2018, 86, 403–411. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Luo, Z.; Sangaiah, A.K.; Baik, S.W. Mobile edge computing based QoS optimization in medical healthcare applications. Int. J. Inf. Manag. 2019, 45, 308–318. [Google Scholar] [CrossRef]
- Oueida, S.; Kotb, Y.; Aloqaily, M.; Jararweh, Y.; Baker, T. An edge computing based smart healthcare framework for resource management. Sensors 2018, 18, 4307. [Google Scholar] [CrossRef] [PubMed]
- Shi, W.; Dustdar, S. The promise of edge computing. Computer 2016, 49, 78–81. [Google Scholar] [CrossRef]
- Xiao, Y.; Jia, Y.; Liu, C.; Cheng, X.; Yu, J.; Lv, W. Edge Computing Security: State of the Art and Challenges. Proc. IEEE 2019, 107, 1608–1631. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. BSN-Care: A secure IoT-based modern healthcare system using body sensor network. IEEE Sens. J. 2016, 16, 1368–1376. [Google Scholar] [CrossRef]
- Moosavi, S.R.; Gia, T.N.; Rahmani, A.M.; Nigussie, E.; Virtanen, S.; Isoaho, J.; Tenhunen, H. SEA: A secure and efficient authentication and authorization architecture for IoT-based healthcare using smart gateways. Procedia Comput. Sci. 2015, 52, 452–459. [Google Scholar] [CrossRef]
- Kulkarni, A.; Sathe, S. Healthcare applications of the Internet of Things: A Review. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 6229–6232. [Google Scholar]
- Rohokale, V.M.; Prasad, N.R.; Prasad, R. A cooperative Internet of Things (IoT) for rural healthcare monitoring and control. In Proceedings of the Wireless Communication, Vehicular Technology, Information Theory and Aerospace & Electronics Systems Technology (Wireless VITAE), Chennai, India,, 28 February–3 March 2011; pp. 1–6. [Google Scholar]
- Amendola, S.; Lodato, R.; Manzari, S.; Occhiuzzi, C.; Marrocco, G. RFID technology for IoT- based personal healthcare in smart spaces. IEEE Internet Things J. 2014, 1, 144–152. [Google Scholar] [CrossRef]
- Doukas, C.; Maglogiannis, I. Bringing IoT and cloud computing towards pervasive healthcare. In Proceedings of the Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Palermo, Italy, 4–6 July 2012; pp. 922–926. [Google Scholar]
- Hou, J.L.; Yeh, K.H. Novel authentication schemes for IoT based healthcare systems. Int. J. Distrib. Sens. Netw. 2015, 11, 183659. [Google Scholar] [CrossRef]
- Catarinucci, L.; De Donno, D.; Mainetti, L.; Palano, L.; Patrono, L.; Stefanizzi, M.L.; Tarricone, L. An IoT-aware architecture for smart healthcare systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Fan, Y.J.; Yin, Y.H.; Da Xu, L.; Zeng, Y.; Wu, F. IoT-based smart rehabilitation system. IEEE Trans. Ind. Inform. 2014, 10, 1568–1577. [Google Scholar]
- Talpur, M.S.H. The appliance pervasive of internet of things in healthcare systems. arXiv 2013, arXiv:1306.3953. [Google Scholar]
- Xu, B.; Da Xu, L.; Cai, H.; Xie, C.; Hu, J.; Bu, F. Ubiquitous data accessing method in IoT-based information system for emergency medical services. IEEE Trans. Ind. Inform. 2014, 10, 1578–1586. [Google Scholar]
- Ray, P.P. Home Health Hub Internet of Things (H 3 IoT): An architectural framework for monitoring health of elderly people. In Proceedings of the Science Engineering and Management Research (ICSEMR), Chennai, India, 27–29 November 2014; pp. 1–3. [Google Scholar]
- Lee, I.; Lee, K. The Internet of Things (IoT): Applications, investments, and challenges for enterprises. Bus. Horiz. 2015, 58, 431–440. [Google Scholar] [CrossRef]
- Luo, E.; Bhuiyan MZ, A.; Wang, G.; Rahman, M.A.; Wu, J.; Atiquzzaman, M. Privacy Protector: Privacy-Protected Patient Data Collection in IoT-Based Healthcare Systems. IEEE Commun. Mag. 2018, 56, 163–168. [Google Scholar] [CrossRef]
- Yang, Y.; Zheng, X.; Guo, W.; Liu, X.; Chang, V. Privacy-preserving smart IoT-based healthcare big data storage and self-adaptive access control system. Inf. Sci. 2018, 479, 567–592. [Google Scholar] [CrossRef]
- Firouzi, F.; Rahmani, A.M.; Mankodiya, K.; Badaroglu, M.; Merrett, G.V.; Wong, P.; Farahani, B. Internet-of-Things and big data for smarter healthcare: From device to architecture, applications and analytics. Future Gener. Comput. Syst. 2018, 78, 583–586. [Google Scholar]
- Salunke, P.; Nerkar, R. IoT Driven Healthcare System for Remote Monitoring of Patients. J. Mod. Trends Sci. Technol. 2017, 3, 100–103. [Google Scholar]
- Muhammad, G.; Alhamid, M.F.; Alsulaiman, M.; Gupta, B. Edge computing with cloud for voice disorder assessment and treatment. IEEE Commun. Mag. 2018, 56, 60–65. [Google Scholar] [CrossRef]
- Pang, H.; Tan, K.L. Authenticating query results in edge computing. In Proceedings of the 20th International Conference on Data Engineering, Boston, MA, USA, 2 April 2004; pp. 560–571. [Google Scholar]
- Tripathi, G.; Ahad, M.A.; Paiva, S. S2HS-A Blockchain based Approach for Smart Healthcare System. Available online: https://doi.org/10.1016/j.hjdsi.2019.100391 (accessed on 10 July 2020).
- Swapnaja; Hiray, R.; Bhramaramba, R. Health Care in Smart Cities: A Survey based on IoT Data Analytics. Available online: https://xueshu.baidu.com/usercenter/paper/show?paperid=1a6906j0m95f0gn09d6m0cx0f7025367&site=xueshu_se (accessed on 10 July 2020).
- Cook, Diane & Duncan, Glen & Sprint, Gina & Fritz, Roschelle. Using Smart City Technology to Make Healthcare Smarter. Proc. IEEE 2018, 106, 708–722. [Google Scholar] [CrossRef]
- Pacheco Rocha, N.; Dias, A.; Santinha, G.; Rodrigues, M.; Queirós, A.; Rodrigues, C. Smart Cities and Healthcare: A Systematic Review. Technologies 2019, 7, 58. [Google Scholar] [CrossRef]
- Al-Azzam, M.; Alazam, M. Smart City and Smart-Health Framework, Challenges and Opportunities. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 171–176. [Google Scholar] [CrossRef]
- Baker, S.B.; Xiang, W.; Atkinson, I. Internet of things for smart healthcare: Technologies, challenges, and opportunities. IEEE Access 2017, 5, 26521–26544. [Google Scholar] [CrossRef]
- Elhoseny, M.; Ramírez-González, G.; Abu-Elnasr, O.M.; Shawkat, S.A.; Arunkumar, N.; Farouk, A. Secure Medical Data Transmission Model for IoT-based Healthcare Systems. IEEE Access 2018, 6, 20596–20608. [Google Scholar] [CrossRef]
- Gong, T.; Huang, H.; Li, P.; Zhang, K.; Jiang, H. A medical healthcare system for privacy protection based on IoT. In Proceedings of the 2015 Seventh International Symposium on Parallel Architectures, Algorithms and Programming (PAAP), Nanjing, China, 12–14 December 2015; pp. 217–222. [Google Scholar]
- He, D.; Ye, R.; Chan, S.; Guizani, M.; Xu, Y. Privacy in the Internet of Things for smart healthcare. IEEE Commun. Mag. 2018, 56, 38–44. [Google Scholar] [CrossRef]
- Manogaran, G.; Varatharajan, R.; Lopez, D.; Kumar, P.M.; Sundarasekar, R.; Thota, C. A new architecture of Internet of Things and big data ecosystem for secured smart healthcare monitoring and alerting system. Future Gener. Comput. Syst. 2018, 82, 375–387. [Google Scholar] [CrossRef]
- Ng, H.S.; Sim, M.L.; Tan, C.M. Security issues of wireless sensor networks in healthcare applications. BT Technol. J. 2006, 24, 138–144. [Google Scholar] [CrossRef]
- Pramanik, M.I.; Lau, R.Y.; Demirkan, H.; Azad MA, K. Smart health: Big data enabled health paradigm within smart cities. Expert Syst. Appl. 2017, 87, 370–383. [Google Scholar] [CrossRef]
- Tarouco LM, R.; Bertholdo, L.M.; Granville, L.Z.; Arbiza LM, R.; Carbone, F.; Marotta, M.; De Santanna, J.J.C. Internet of Things in healthcare: Interoperatibility and security issues. In Proceedings of the 2012 IEEE international conference on communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; pp. 6121–6125. [Google Scholar]
- Uddin, M.Z. A wearable sensor-based activity prediction system to facilitate edge computing in smart healthcare system. J. Parallel Distrib. Comput. 2019, 123, 46–53. [Google Scholar] [CrossRef]
- Zhang, Y.; Gravina, R.; Lu, H.; Villari, M.; Fortino, G. PEA: Parallel electrocardiogram-based authentication for smart healthcare systems. J. Netw. Comput. Appl. 2018, 117, 10–16. [Google Scholar] [CrossRef]
- Kakria, P.; Tripathi, N.K.; Kitipawang, P. A real-time health monitoring system for remote cardiac patients using smartphone and wearable sensors. Int. J. Telemed. Appl. 2015, 2015, 373474. [Google Scholar] [CrossRef] [PubMed]
- Zhao, X.H.; Ma, S.N.; Long, H.; Yuan, H.; Tang, C.Y.; Cheng, P.K.; Tsang, Y.H. Multifunctional sensor based on porous carbon derived from metal–organic frameworks for real time health monitoring. ACS Appl. Mater. Interfaces 2018, 10, 3986–3993. [Google Scholar] [CrossRef]
- Esposito, C.; De Santis, A.; Tortora, G.; Chang, H.; Choo, K.K.R. Blockchain: A panacea for healthcare cloud-based data security and privacy? IEEE Cloud Comput. 2018, 5, 31–37. [Google Scholar] [CrossRef]
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y.; Ma, M.; He, J. Blochie: A blockchain-based platform for healthcare information exchange. In Proceedings of the 2018 IEEE International Conference on Smart Computing (Smartcomp), Taormina, Italy, 18–20 June 2018; pp. 49–56. [Google Scholar]
- Griggs, K.N.; Ossipova, O.; Kohlios, C.P.; Baccarini, A.N.; Howson, E.A.; Hayajneh, T. Healthcare blockchain system using smart contracts for secure automated remote patient monitoring. J. Med. Syst. 2018, 42, 130. [Google Scholar] [CrossRef]
- Jones, M.; Hardt, D. The Oauth 2.0 Authorization Framework: Bearer Token Usage. No. RFC 6750. Internet Engineering Task Force (IETF). Available online: https://tools.ietf.org/pdf/rfc6750.pdf (accessed on 2 June 2020).
- Boyd, R. Getting Started with OAuth 2.0.; O’Reilly Media publication, Inc.: Sebastopol, CA, USA, 2012. [Google Scholar]
- Schneier, B.; Kelsey, J.; Whiting, D.; Wagner, D.; Hall, C.; Ferguson, N. The Twofish Encryption Algorithm: A 128-Bit Block Cipher. Available online: https://xueshu.baidu.com/usercenter/paper/show?paperid=af1baf2b83ca69305a23bddb548eab0a&site=xueshu_se (accessed on 2 June 2020).
- Bhanot, R.; Hans, R. A review and comparative analysis of various encryption algorithms. Int. J. Secur. Appl. 2015, 9, 289–306. [Google Scholar] [CrossRef]
- McKeown, N. Software-defined networking. INFO- COM Keynote Talk 2009, 17, 30–32. [Google Scholar]
- Kirkpatrick, K. Software-defined networking. Commun. ACM 2013, 56, 16–19. [Google Scholar] [CrossRef]
- Trevor, H. IoT Standards and Protocols. Available online: https://www.postscapes.com/internet-of-things-protocols/ (accessed on 30 June 2020).
- Bhushan, B.; Sahoo, G. Routing Protocols in Wireless Sensor Networks. In Computational Intelligence in Sensor Networks Studies in Computational Intelligence; Springer: Berlin/Heidelberg, Germany, 2018; pp. 215–248. [Google Scholar] [CrossRef]
- Sharma, M.; Tandon, A.; Narayan, S.; Bhushan, B. Classification and analysis of security attacks in WSNs and IEEE 802.15.4 standards: A survey. In Proceedings of the 2017 3rd International Conference on Advances in Computing, Communication & Automation (ICACCA), Dehradun, India, 15–16 September 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Sinha, P.; Jha, V.K.; Rai, A.K.; Bhushan, B. Security vulnerabilities, attacks and countermeasures in wireless sensor networks at various layers of OSI reference model: A survey. In Proceedings of the 2017 International Conference on Signal Processing and Communication (ICSPC), Coimbatore, India, 28–29 July 2017; pp. 288–293. [Google Scholar] [CrossRef]
- Hölbl, M.; Kompara, M.; Kamišalić, A.; Nemec Zlatolas, L. A systematic review of the use of blockchain in healthcare. Symmetry 2018, 10, 470. [Google Scholar] [CrossRef]
- Zubaydi, H.D.; Chong, Y.W.; Ko, K.; Hanshi, S.M.; Karuppayah, S. A review on the role of blockchain technology in the healthcare domain. Electronics 2019, 8, 679. [Google Scholar] [CrossRef]
- Kombe, C.; Ally, M.; Sam, A. A review on healthcare information systems and consensus protocols in blockchain technology. Int. J. Adv. Technol. Eng. Explor. 2018, 5, 2394–7454. [Google Scholar] [CrossRef]
| Stakeholders | Impact of Data Analytics |
|---|---|
| Healthcare practitioners |
|
| Government |
|
| Healthcare providers |
|
| Pharmaceutical companies |
|
| Patients |
|
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tripathi, G.; Abdul Ahad, M.; Paiva, S. SMS: A Secure Healthcare Model for Smart Cities. Electronics 2020, 9, 1135. https://doi.org/10.3390/electronics9071135
Tripathi G, Abdul Ahad M, Paiva S. SMS: A Secure Healthcare Model for Smart Cities. Electronics. 2020; 9(7):1135. https://doi.org/10.3390/electronics9071135
Chicago/Turabian StyleTripathi, Gautami, Mohd Abdul Ahad, and Sara Paiva. 2020. "SMS: A Secure Healthcare Model for Smart Cities" Electronics 9, no. 7: 1135. https://doi.org/10.3390/electronics9071135
APA StyleTripathi, G., Abdul Ahad, M., & Paiva, S. (2020). SMS: A Secure Healthcare Model for Smart Cities. Electronics, 9(7), 1135. https://doi.org/10.3390/electronics9071135






