The Design of Compact SM4 Encryption and Decryption Circuits That Are Resistant to Bypass Attack
Abstract
1. Introduction
1.1. Masking Method
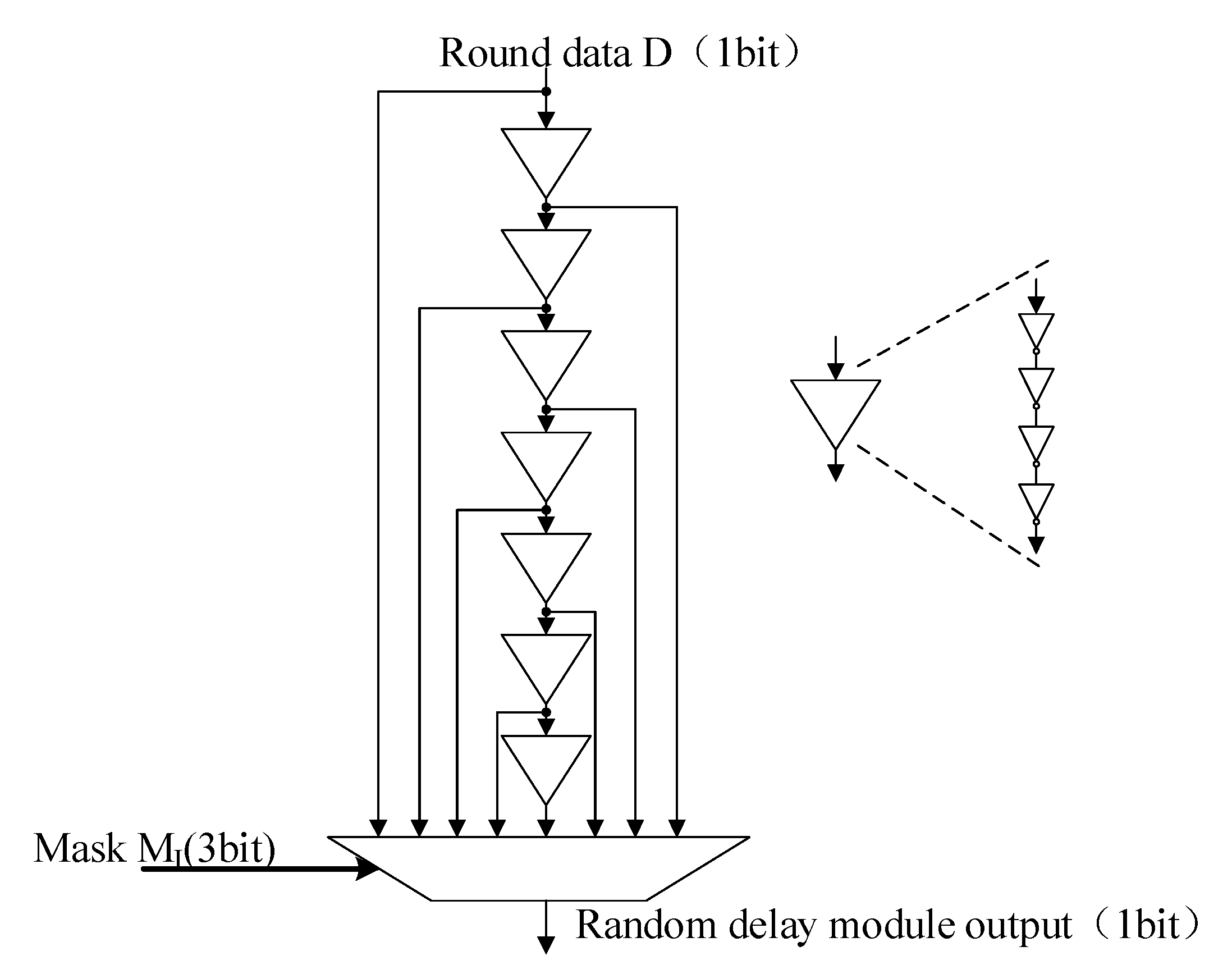
1.2. Randomization Method
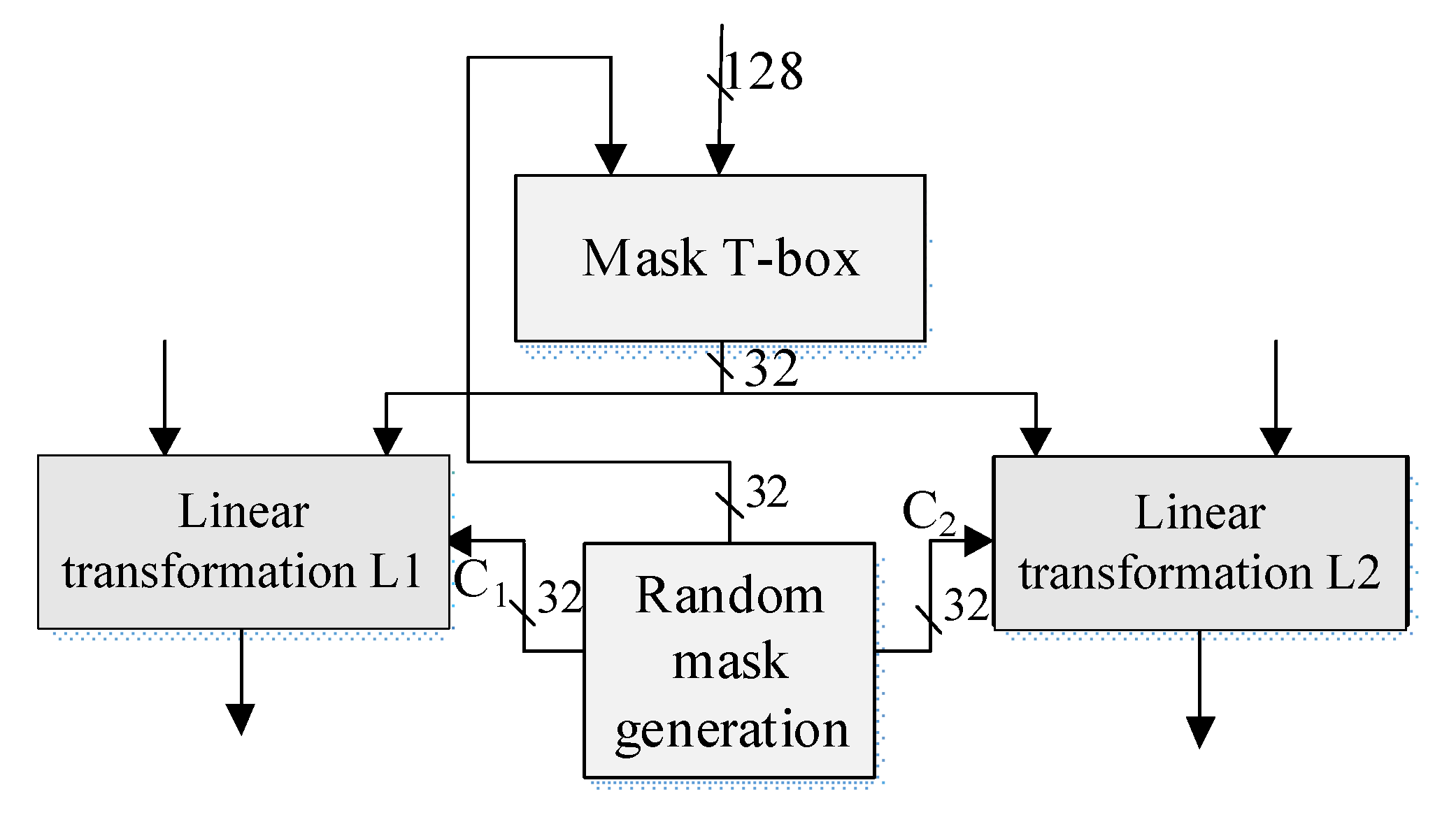
2. Overall Structure Design
3. Sub-Module Design
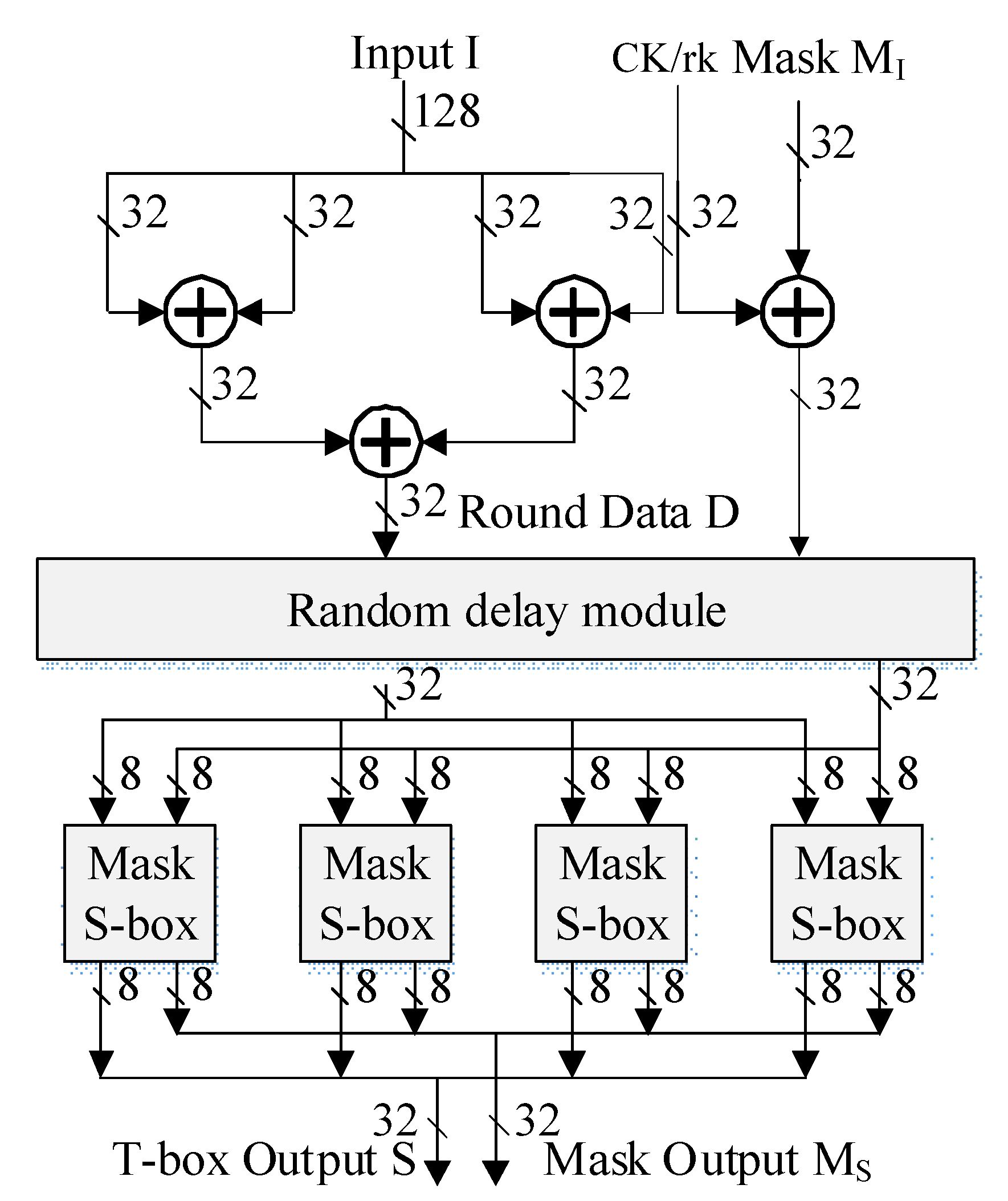
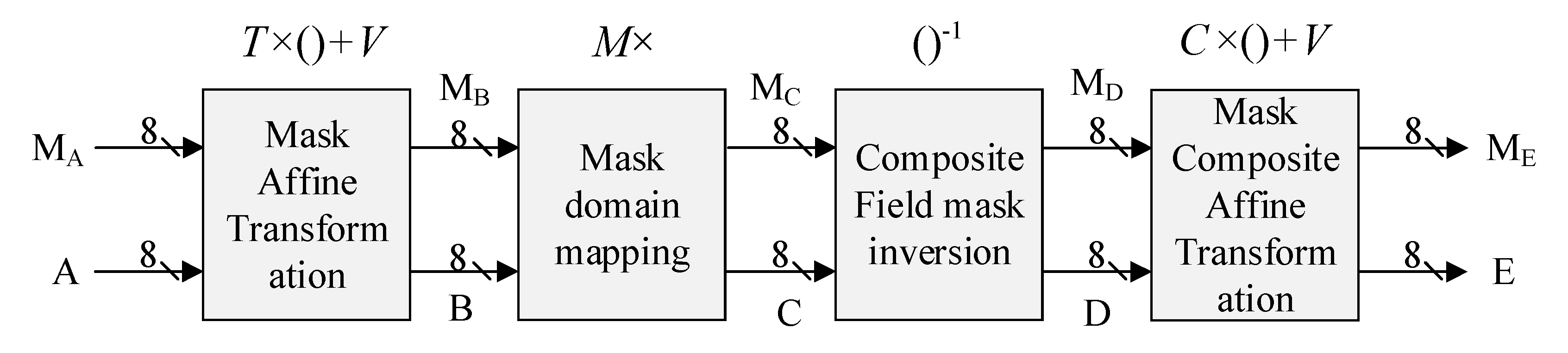
3.1. Design of the Mask T-Box
3.1.1. Optimization Design of Mask Affine Transformation Module
3.1.2. Optimized Design of Mask Field Mapping Module
3.1.3. Optimized Design of Mask Composite Affine Transformation Module
3.1.4. Optimal Design of the Inverse Operation of the Mask GF((24)2)
- (a)
- Mask GF(24) Add Operation
- (b)
- Mask GF(24) Multiplication
- (c)
- Mask GF(24) Squared Constant Operation
- (d)
- Mask GF(24) Inversion Operation
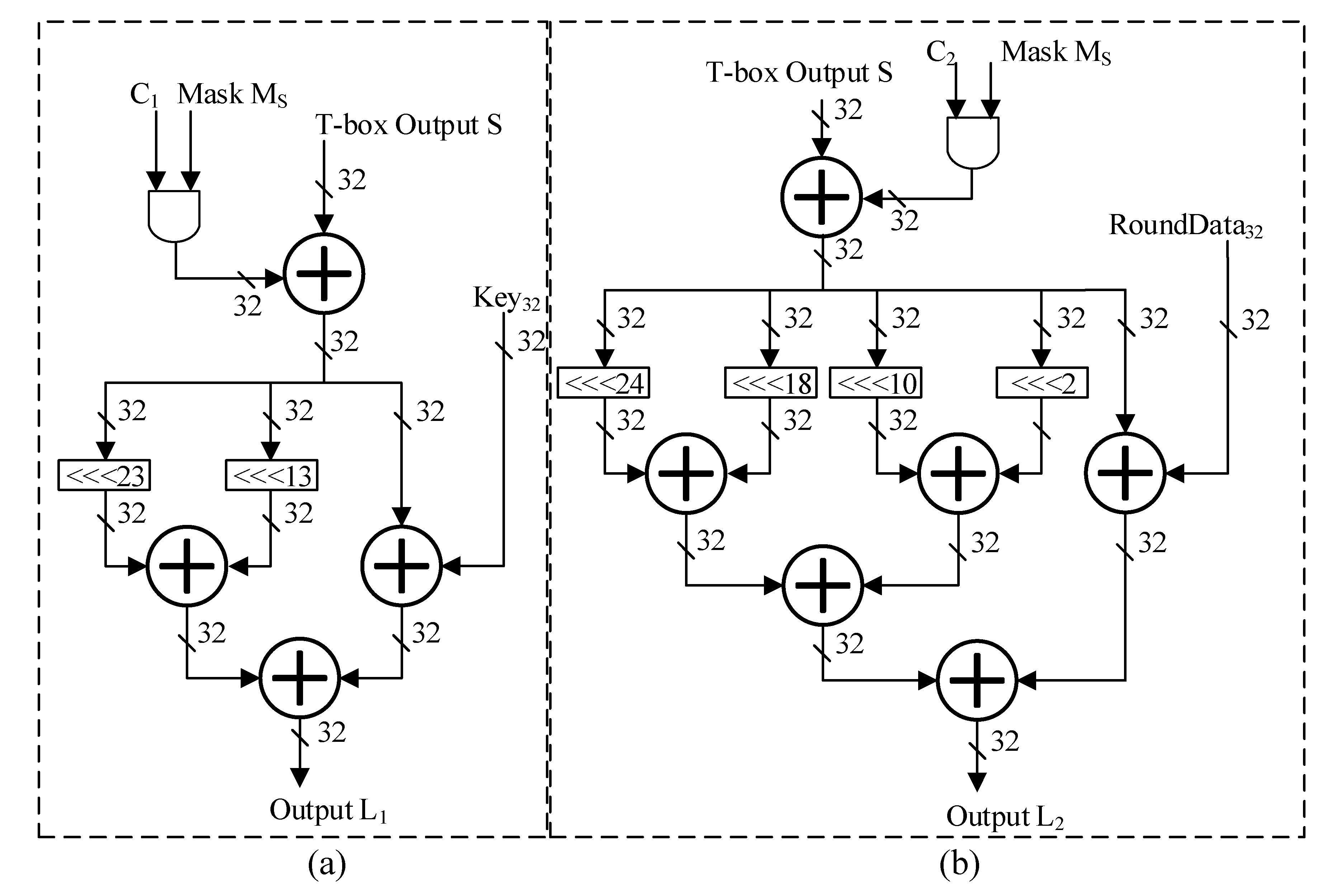
3.2. Design of Random Linear Transformation
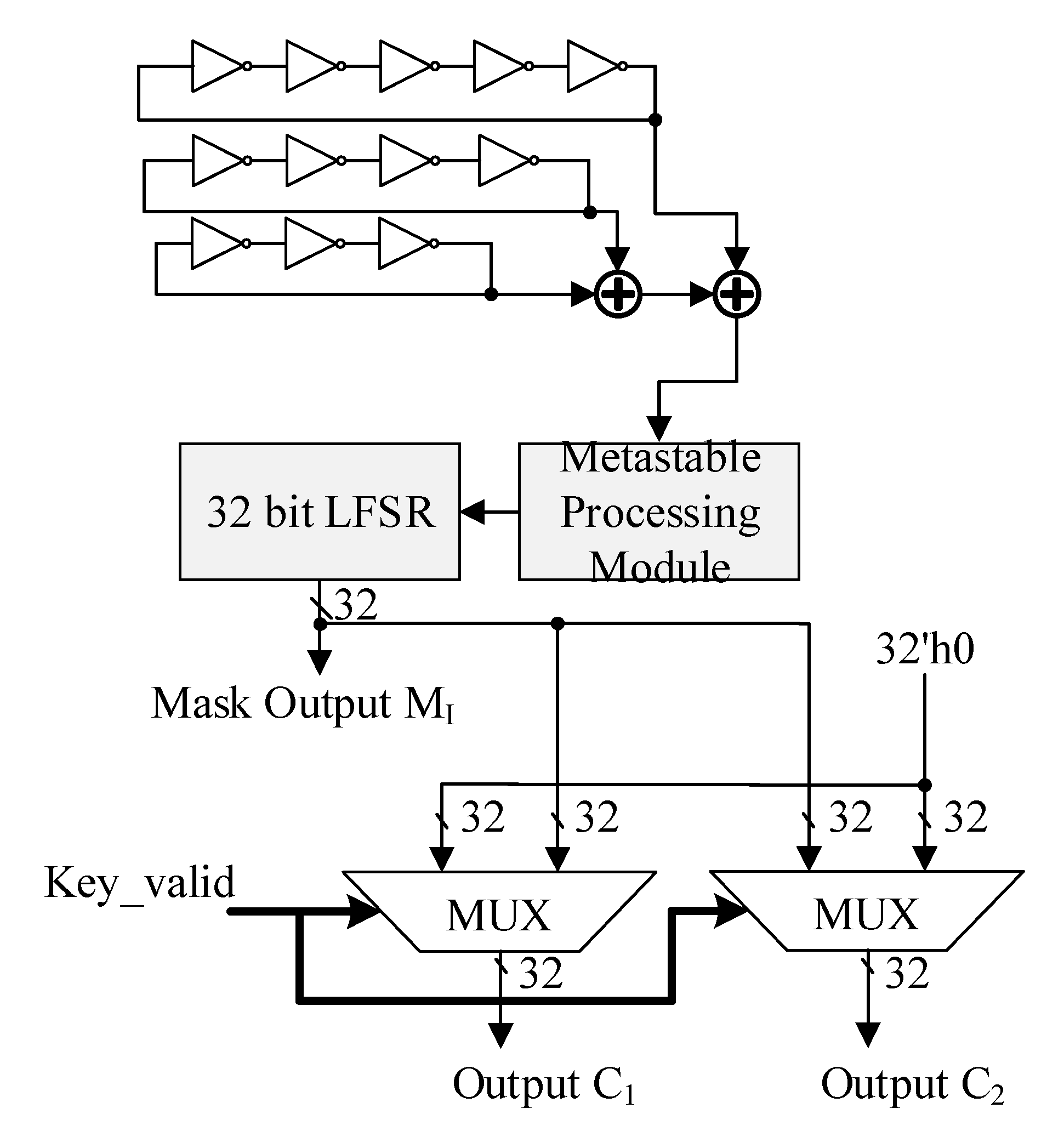
3.3. Design of Random Mask Generation Module
4. Security Analysis
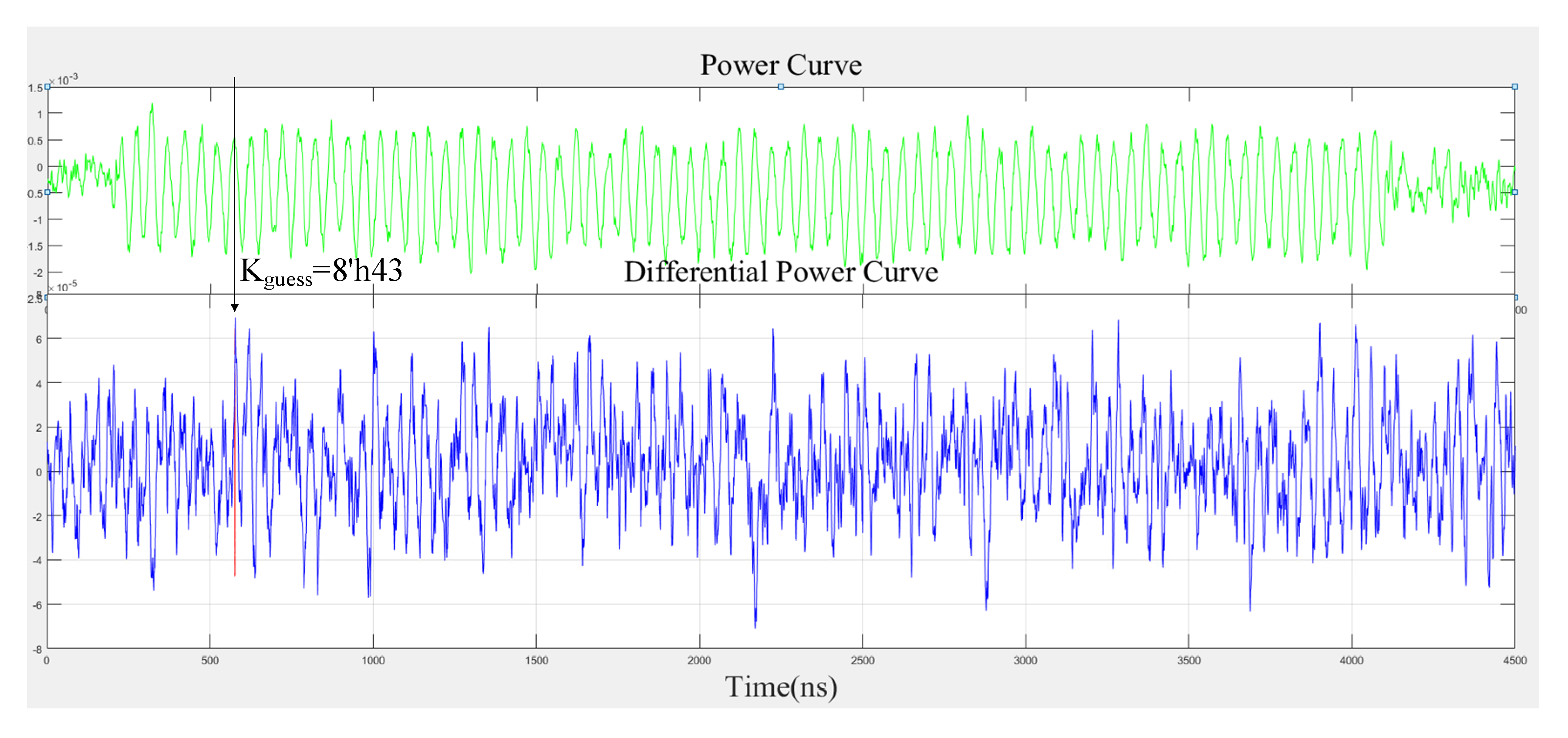
4.1. Security Analysis of Random Delay Mask S-box
4.2. Security Analysis of SM4 Encryption and Decryption Circuit
5. Synthesize Results
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Chao, P.E.I. A Method of masking SM4 and analysis against DPA attacks. J. Cryptol. Res. 2016, 3, 79–90. [Google Scholar]
- Di, W.; Wu, L.; Zhang, X. Key-leakage hardware Trojan with super concealment based on the fault injection for block cipher of SM4. Electron. Lett. 2018, 54, 810–812. [Google Scholar]
- Niu, Y.; Jiang, A. The low power design of SM4 cipher with resistance to differential power analysis. In Proceedings of the International Symposium on Quality Electronic Design, Santa Clara, CA, USA, 2–4 March 2015. [Google Scholar]
- Yuanman, T. Research on Key Techniques of Design and Implementation of Power Analysis. Ph.D. Thesis, National University of Defense Technology, Changsha, China, 2008. [Google Scholar]
- Feng, H.; Lin, W.; Shang, W.; Cao, J.; Huang, W. MLP and CNN-based Classification of Points of Interest in Side-channel Attacks. Int. J. Networked Distrib. Comput. 2020, 8, 108–117. [Google Scholar] [CrossRef]
- Wang, Z.; Zhang, W.; Ma, P.; Wang, X.A. Power consumption attack based on improved principal component analysis. In Proceedings of the 2019 International Conference on Broadband and Wireless Computing, Communication and Applications, Antwerp, Belgium, 7–9 November 2019. [Google Scholar]
- Bae, D.; Nam, S.; Ha, J. Side channel attack on block cipher SM4 and analysis of masking-based countermeasure. J. Korea Inst. Inf. Secur. Cryptol. 2020, 30, 39–49. [Google Scholar]
- Liling, D. The Optimization and Research for AES Cipher Chips with Power Attack Resistance. Master’s Thesis, Nanjing University of Aeronautics and Astronautics, Nanjing, China, 2016. [Google Scholar]
- Akkar, M.-L.; Giraud, C. An implementation of DES and AES, secure against some attacks. In Proceedings of the Cryptographic Hardware and Embedded Systems (CHES 2001), Nara, Japan, 28 September–1 October 2001. [Google Scholar]
- Ruineng, T.; Yuanyuan, L.; Jiaoling, T. SM4 multi-path multiplicative masking method against side-channel attack. Comput. Eng. 2014, 40, 103–108. [Google Scholar]
- Courtois, N.T.; Goubin, L. An algebraic masking method to Prltect AES against power attacks. In Proceedings of the ICISC, Seoul, Korea, 1–2 December 2005. [Google Scholar]
- Herbst, C.; Oswald, E.; Mangard, S. An AES smart card implementation resistant to power analysis attacks. In Proceedings of the ACNS, Singapore, 6–9 June 2006. [Google Scholar]
- Mangard, S.; Pramstaller, N.; Oswald, E. Successfully attacking masked AES hardware implementations. In Proceedings of the CHES 2005, Edinburgh, UK, 29 August–1 September 2005. [Google Scholar]
- Liang, H.; Wu, L.; Zhang, X.; Wang, J. Design of a masked S-box for SM4 Based on composite field. In Proceedings of the 2014 Tenth International Conference on Computational Intelligence and Security, Kunming, China, 15–16 November 2014. [Google Scholar]
- Jing, L. Side-Channel Analysis and Implementation of FPGA based Cryptographic Algorithms. Master’s Thesis, Hunan University, Changsha, China, 2011. [Google Scholar]
- Kocher, P.; Jaffe, J. Using Unpredictable Information to Minimize Leakage from Smartcards and Other Cryptosystems. U.S. Patent 6,327,661, 4 December 2001. [Google Scholar]
- Zhang, Y.; Wu, N.; Zhou, F.; Zhang, J.; Yahya, M.R. A Countermeasure against DPA on SIMON with an Area-Efficient Structure. Electronics 2019, 8, 240. [Google Scholar] [CrossRef]

| - | AND | XOR | XNOR | Value | ||
|---|---|---|---|---|---|---|
| Mask addition *2 | Before optimization | Area | - | 8 | - | 212.88 μm2 |
| Delay | - | 1 | - | 0.21 ns | ||
| After optimization | Area | - | 8 | - | 212.88 μm2 | |
| Delay | - | 1 | - | 0.21 ns | ||
| Mask multiplication *3 | Before optimization | Area | 64 | 68 | - | 2661.32 μm2 |
| Delay | 1 | 5 | - | 1.21 ns | ||
| After optimization | Area | 32 | 46 | - | 1649.98 μm2 | |
| Delay | 1 | 5 | - | 1.21 ns | ||
| Mask squared constant | Before optimization | Area | 50 | 42 | - | 1783.12 μm2 |
| Delay | 1 | 3 | - | 0.79 ns | ||
| After optimization | Area | - | - | - | 0 | |
| Delay | - | - | - | 0 | ||
| Mask inversion | Before optimization | Area | 80 | 152 | - | 5109.52 μm2 |
| Delay | 2 | 9 | - | 2.21 ns | ||
| After optimization | Area | 63 | 77 | 1 | 2914.11 μm2 | |
| Delay | 2 | 7 | 0 | 1.79 ns | ||
| Total | Before optimization | Area | 322 | 414 | - | 15,302.36 μm2 |
| Delay | 4 | 21 | - | 5.05 ns | ||
| After optimization | Area | 159 | 231 | 1 | 8289.81 μm2 | |
| Delay | 4 | 19 | 0 | 4.63 ns | ||
| Module | AND | XOR | XNOR | Total | ||
|---|---|---|---|---|---|---|
| Mask Affine Transformation | Before optimization | Area | - | 69 | - | 1836.09 μm2 |
| Delay | - | 3 | - | 0.63 ns | ||
| After optimization | Area | - | 39 | 4 | 1144.23 μm2 | |
| Delay | - | 3 | 0 | 0.63 ns | ||
| Mask field mapping | Before optimization | Area | - | 48 | - | 1277.28 μm2 |
| Delay | - | 3 | - | 0.63 ns | ||
| After optimization | Area | - | 28 | - | 745.08 μm2 | |
| Delay | - | 2 | - | 0.42 ns | ||
| Mask composite field inversion | Before optimization | Area | 322 | 414 | - | 15302.36 μm2 |
| Delay | 4 | 21 | - | 5.05 ns | ||
| After optimization | Area | 159 | 231 | 1 | 8289.81 μm2 | |
| Delay | 4 | 19 | 0 | 4.63 ns | ||
| Mask Composite Affine Transformation | Before optimization | Area | - | 49 | - | 1303.89 μm2 |
| Delay | - | 3 | - | 0.63 ns | ||
| After optimization | Area | - | 24 | 2 | 691.86 μm2 | |
| Delay | - | 3 | 0 | 0.63 ns | ||
| Total | Before optimization | Area | 322 | 580 | - | 19719.62 μm2 |
| Delay | 4 | 30 | - | 6.94 ns | ||
| After optimization | Area | 159 | 322 | 7 | 10870.98 μm2 | |
| Delay | 4 | 27 | 0 | 6.10 ns | ||
| SboxIn | 0xff | 0xaa | 0x44 | 0x56 | |
|---|---|---|---|---|---|
| MaskIn | |||||
| 0xedcba9 | 35 | 33 | 30 | 26 | |
| 0xff24dc | 33 | 39 | 31 | 32 | |
| 0x156894 | 29 | 32 | 21 | 31 | |
| 0xffffff | 22 | 24 | 26 | 29 | |
| 0x002456 | 34 | 29 | 23 | 26 | |
| 0x380cd9 | 42 | 32 | 28 | 48 | |
| 0x6ad0c3 | 31 | 24 | 28 | 29 | |
| Type | Name | Value |
|---|---|---|
| Resource overhead | LUT (Look up table) | 968/53,200 (1.82%) |
| FF (Register) | 536/106,400 (0.38%) | |
| Performance evaluation | Maximum clock frequency | 60.67 MHz |
| Critical path delay | 16.482 ns | |
| Throughput | 99.56 MHz/s |
| Parameter | This Article | [1] | [10] |
|---|---|---|---|
| Process | SMIC 0.18 μm | SMIC 0.13 μm | SMIC 0.18 μm |
| Clock frequency (MHz) | 110.1 | 50 | 50 |
| Area (μm2) | 82,734 | - | - |
| Equivalent gate (gate) | 8290 | 16,000 | 36,000 |
| Throughput (Mb/s) | 207 | 200 | 200 |
| Throughput/gate (Mb·s-1·kgate-1) | 24.97 | 12.5 | 5.56 |
| Attack cost (number of curves) | 100,000+ | 500,000+ | 500,000+ |
| Circuit characteristics | Resistant to DPA (including Glitch Attack), support encryption and decryption | Resistant to DPA, only support encryption | Resists DPA, only supports encryption |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, F.; Zhang, B.; Wu, N.; Bu, X. The Design of Compact SM4 Encryption and Decryption Circuits That Are Resistant to Bypass Attack. Electronics 2020, 9, 1102. https://doi.org/10.3390/electronics9071102
Zhou F, Zhang B, Wu N, Bu X. The Design of Compact SM4 Encryption and Decryption Circuits That Are Resistant to Bypass Attack. Electronics. 2020; 9(7):1102. https://doi.org/10.3390/electronics9071102
Chicago/Turabian StyleZhou, Fang, Benjun Zhang, Ning Wu, and Xiangli Bu. 2020. "The Design of Compact SM4 Encryption and Decryption Circuits That Are Resistant to Bypass Attack" Electronics 9, no. 7: 1102. https://doi.org/10.3390/electronics9071102
APA StyleZhou, F., Zhang, B., Wu, N., & Bu, X. (2020). The Design of Compact SM4 Encryption and Decryption Circuits That Are Resistant to Bypass Attack. Electronics, 9(7), 1102. https://doi.org/10.3390/electronics9071102





