Verification Method of Safety Properties of Embedded Assembly Program by Combining SMT-Based Bounded Model Checking and Reduction of Interrupt Handler Executions
Abstract
1. Introduction
1.1. Background
- All errors (e.g., stack overflows, arithmetic overflows, interrupt handling errors, and writing reserved registers) introduced during the complete development process are consequently included in assembly program outcome, but by analyzing only the assembly program it is not possible to find and detect the roots of the assembly outcome.
- Assembly language usually has a clean and well-documented semantics. Vendors of microcontrollers provide documentation describing the semantics of the provided assembly constructs.
- Recently, bounded model checking of software using SMT solvers attracts attention [9]. SMT Solvers check the satisfiability of first-order formulas containing operations from various theories such as the Booleans, bit-vectors, arithmetic, arrays, and recursive datatypes. When model checking assembly program using SMT, the model checker does not have to exploit the compiler behavior, hardware-dependent constructs can be handled, and the source code (C code) of the software is not required. Hence, even programs that use libraries not available in source code can be analyzed. On the other hand, L.C. Cordeiro et al. have developed bounded model checking of C program using SMT [10], but bounded model checking of the assembly program using SMT has not existed.
- Programs consisting of components written in different programming languages can be verified. When model checking the source code, only single components can be verified, and for each programming language used, a specific model checker has to be utilized.
1.2. Outline of This Paper
1.3. Related Work
- B. Schlich studied a new approach to model checking software for microcontrollers, which verifies the assembly code of the software [1]. The state space is built using a tailored simulator based on static analysis, which abstracts from time, handles nondeterminism, and creates an overapproximation of the behavior shown by the real microcontroller. On the other hand, we have developed model checker by both static analysis and dynamic program analysis such as undefined values [13].This paper and Reference [1] use different approaches as follows:
- (a)
- In Reference [1], if the model checker requests successors of a state which are not created yet, the state space uses the simulator to create the successors on-the-fly.
- (b)
- On the other hand, in this paper, the verification system completes the state transition system and passes it to the SMT solver. By using SMT’s background theory such as bit vector, bit-level assembly instructions can be easily expressed as functions of background theory and can be directly input to the SMT solver for verification.
- L.C. Cordeiro et al. studied SMT-Based Bounded Model Checking of embedded ANSI-C program [10]. On the other hand, we study SMT-Based Bounded Model Checking of embedded assembly program. The background theory of the bit vector is effective for assembly program. Similar to model checking of C program, the background theory of the bit vector is expected to be effective in model checking of assembly program. In this study, we use the background theory of the bit vector for the assembly program, and construct the state space by representing register as a data type of a fixed length bit vector and representing the address space as a function of fixed bit vector mapping from address to value.
- Recently, L. Lihao et al. proposed effective verification of low-level embedded C software with nested interrupts based on both partial-order encoding and symbolic execution [15]. On the other hand, in this paper, we merge basic blocks generated by interrupt processings based on reducing the number of interrupt handlers by IHER, and verify assembly program based on SMT Bounded model checking. If the method of Lihao Liang et al. is adopted, nested interrupts can be effectively handled in our paper as well.
1.4. The History of Model Checking
- First, the evolution from (1) to (2) is in Reference [16]. The system is encoded in BDD without implementing the system directly in the adjacency list and so forth, realizing the verification of the large scale system.
- Second, the evolution from (2) to (3) is in Reference [17]. We avoid the exponential state explosion of BDD, and encode the system into propositional logic rather than BDD to realize SAT verification with bounded model checking.
- Finally, the evolution from (3) to (4) is in Reference [9]. SMT model checking is realized by expanding the scope of the verification by using the background theory by encoding the system into the predicate logic expression without the quantification symbol, not the propositional logic. Furthermore, SMT model checking can use a general-purpose SMT solver [18], and there is also future development. Our study is based on SMT model checking.
1.5. Structure of This Paper
2. Introduction to SMT-Based Bounded Model Checking
2.1. Overview
2.2. Program Verification by SMT-Based Bounded Model Checking
3. Proposal of Modeling Assembly Codes
3.1. Defining States of Assembly Codes
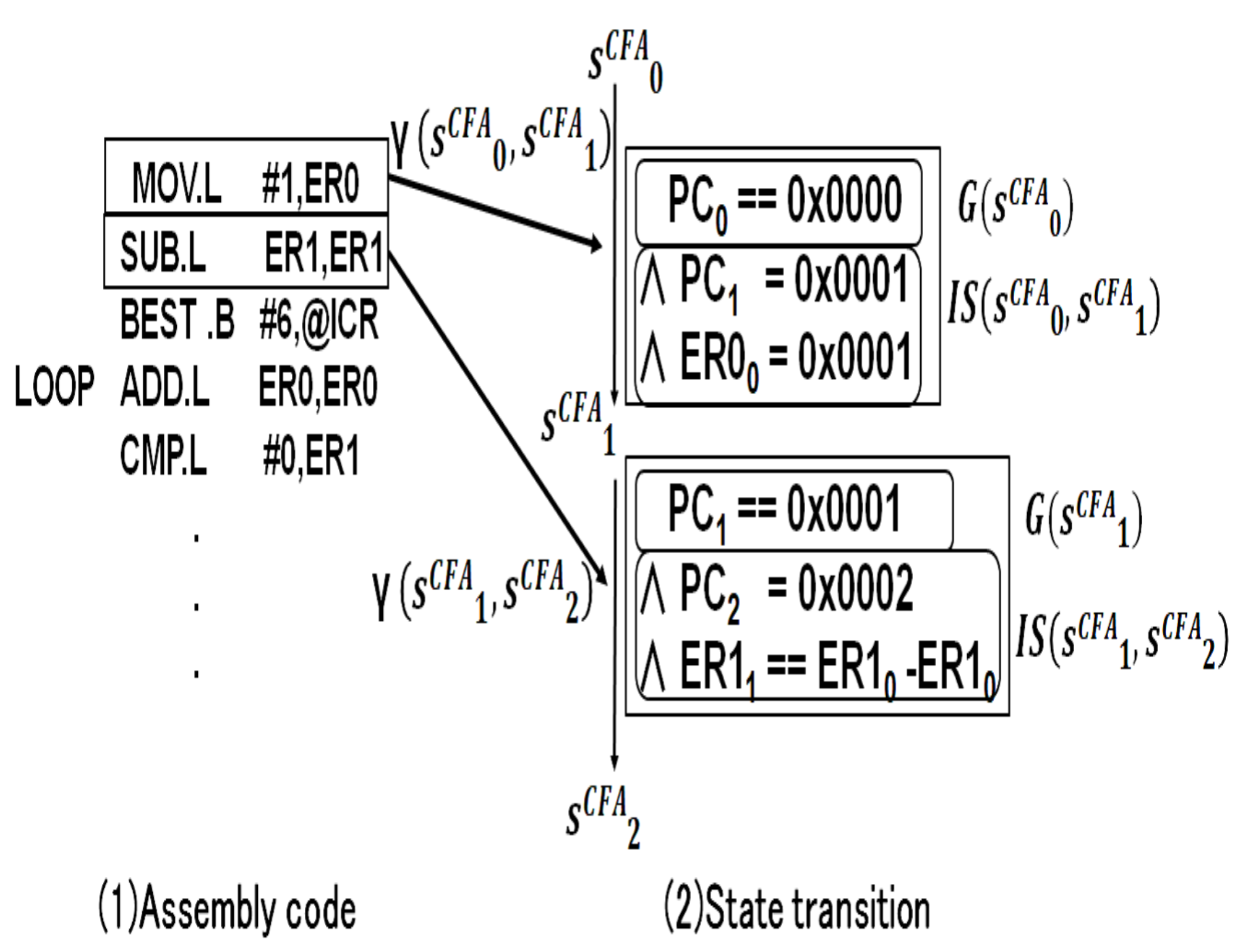
3.2. Defining State Transitions of Assembly Codes
- First a transition condition is the equation using (Program Counter). For , if the is , this means that the instructions of the Static Single Assignment form (SSA) format are executed. means to assign to .
- Next after executing assembly codes at , the transition from to occurs. The next state is defined by a instruction constraint . CFA is constructed from assembly codes. Each node consists of assembly code, and each edge is caused by a instruction constraint . An instruction constraint is represented by predicate formulas. There are instructions such as data transfer, arithmetic operation, extraction and concatenation [24]. The logical formula of state transition is represented by a instruction constraint . All instructions can be transformed into .
- The instruction constraint of data transfer instruction is represented by the equation between and as follows.where represents the value of at , and represents the value of at .
- The instruction constraint of Fixed-Size Bit-Vector operation, for example is represented by the equation between an operation result and a destination register. The following Equation (3) represents adding and , and storing it in using .
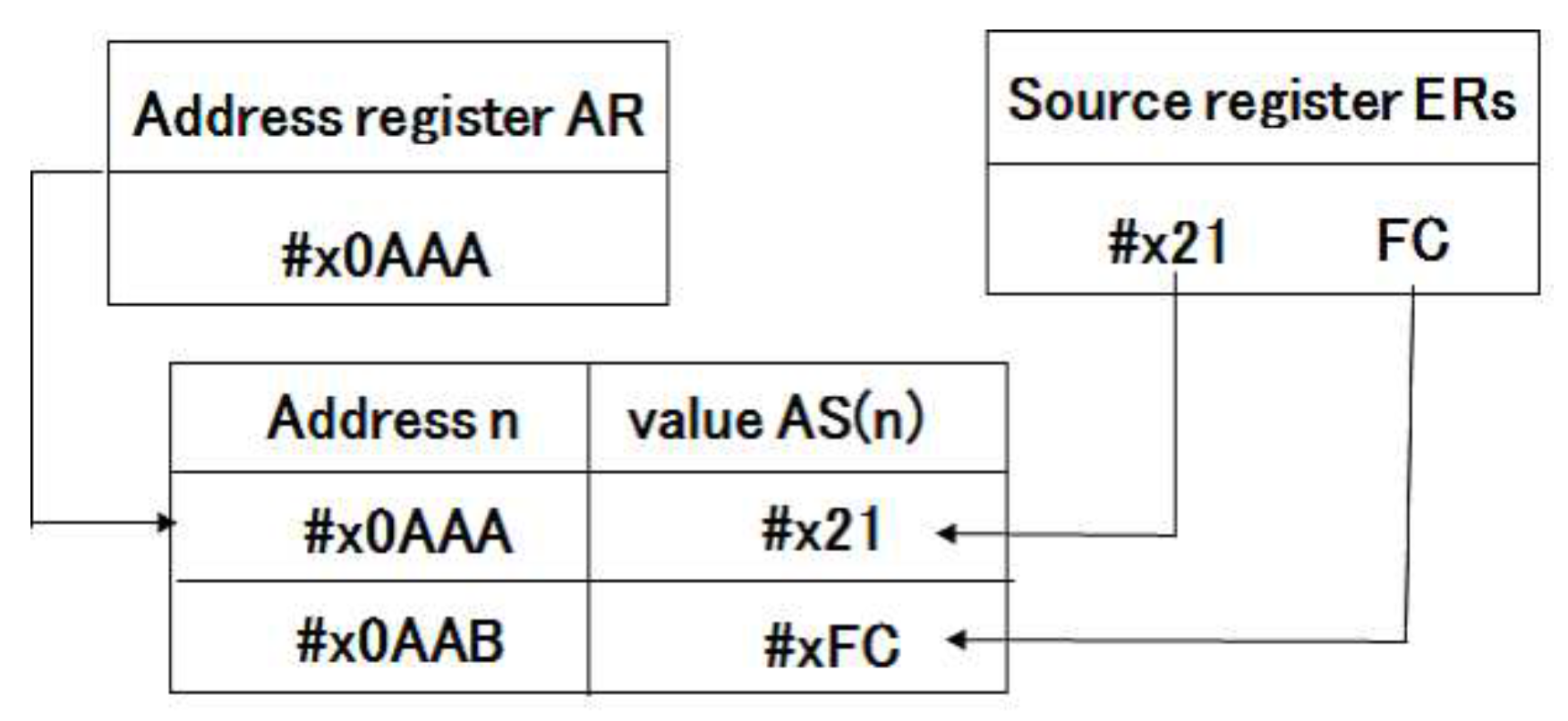
- The instructions (a) and (b) are represented by functions and of bits as follows. Here ⓐ denotes register indirect addressing. Access to address space is defined by a function AS and the argument of the function is indirect address.
- (a)
- (b)
4. Introduction to Interrupt Handler Execution Reduction (IHER)
- Detect Dependencies between IHs:IH depend on each other, if one of the following conditions holds:
- one enables or disables the other,
- one writes a memory location accessed by the other, or
- one writes a memory location. Writing a memory location or a register is an atomic proposition, where an atomic proposition is appeared in temporal logic formulas. In other words, writing a value to a variable is used as the atomic proposition in a temporal logic formula that describes a property to be verified.
- Detect Dependencies between Program and IHs:To detect the dependencies between the program and the IHs, we mark specific program locations with the following two labels: and . The label implies that there exists a dependency between the preceding program location and an IH, and thus, this IH needs to be executed eventually. The label denotes that there exists a dependency between that program location and an IH, and therefore, this IH needs to be executed before the instruction at that location is executed.Let program location k be a direct predecessor of program location l.
- Label :For each IH, l is labeled with if one of the following conditions is satisfied:
- –
- k enables or disables i,
- –
- k writes a memory location that is accessed by i, or
- –
- k writes a memory location that is used in an atomic proposition.
- Label :For each IH, a program location l is labeled with if one of the following conditions holds:
- –
- i writes a memory location that is accessed by l,
- –
- l enables or disables i,
- –
- l writes a memory location that is accessed by i, or
- –
- l writes a memory location that is used in an atomic proposition.
- Refine Labelings:In the refinement step, we try to reduce state spaces further by moving labels until their execution is actually required. We move labels forward until one of the following conditions holds:
- a program location labeled with is reached,
- a loop entry is found, or
- a loop exit is found.
- Label Blocking Locations:In the last step, all program locations are labeled with IHs that can be blocked at the corresponding program location. An IH can be blocked at a program location if its execution is not required. Thus, a program location is labeled with if it is not labeled with .
5. Proposal of Assembly Code Block (ACB) of CFG Using IHER (in Other Words, Combining SMT-Based Bounded Model Checking and Reduction of Interrupt Handler Executions)
5.1. Introduction to ACB
- A start node of program
- A branch destination node
- An node
- An end node of program, which has return instruction
- A node, which has branch instruction
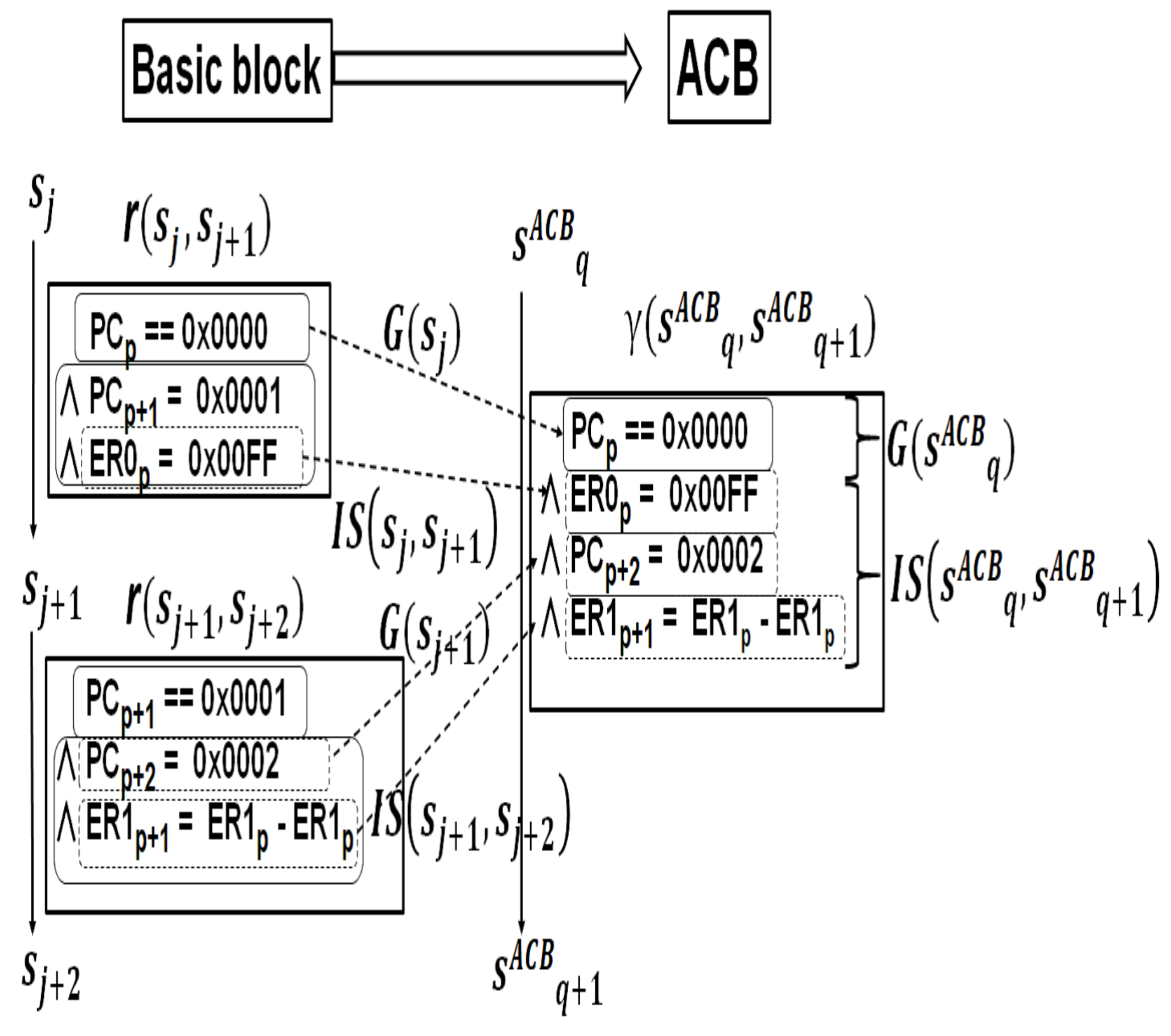
5.2. ACB (Assembly Code Block)
- is the conditional statement using value of the first instruction.
- is the conjunction of logical formulas representing update of registers and locations by executing instructions. As shown in Figure 5, the number of logical formulas of ACB is smaller than the number of logical formulas of basic block.
- (1)
- Since the first instruction of ACB is a guard instruction, a predicate logical expression with a conditional expression == is generated.
- (2)
- Since the instruction after the first is an assignment statement to a register or a memory, a logical expression is generated in the usual SSA format [7].
- (3)
- Repeat (2) to generate these logical products.
- (4)
- Finally generate a logical product of (1) and (3).
| Algorithm 1: Algorithm to generate from CFA to ACB |
|
5.3. Program Verification Based on ACB
- When instructions included in one are few, the effect of reducing state spaces is not provided enough.
- As the length of logical formula is long, verification time is long by SMT solver.
5.4. Comparison of Usual CFG, CFG of IHER, CFG of ACB
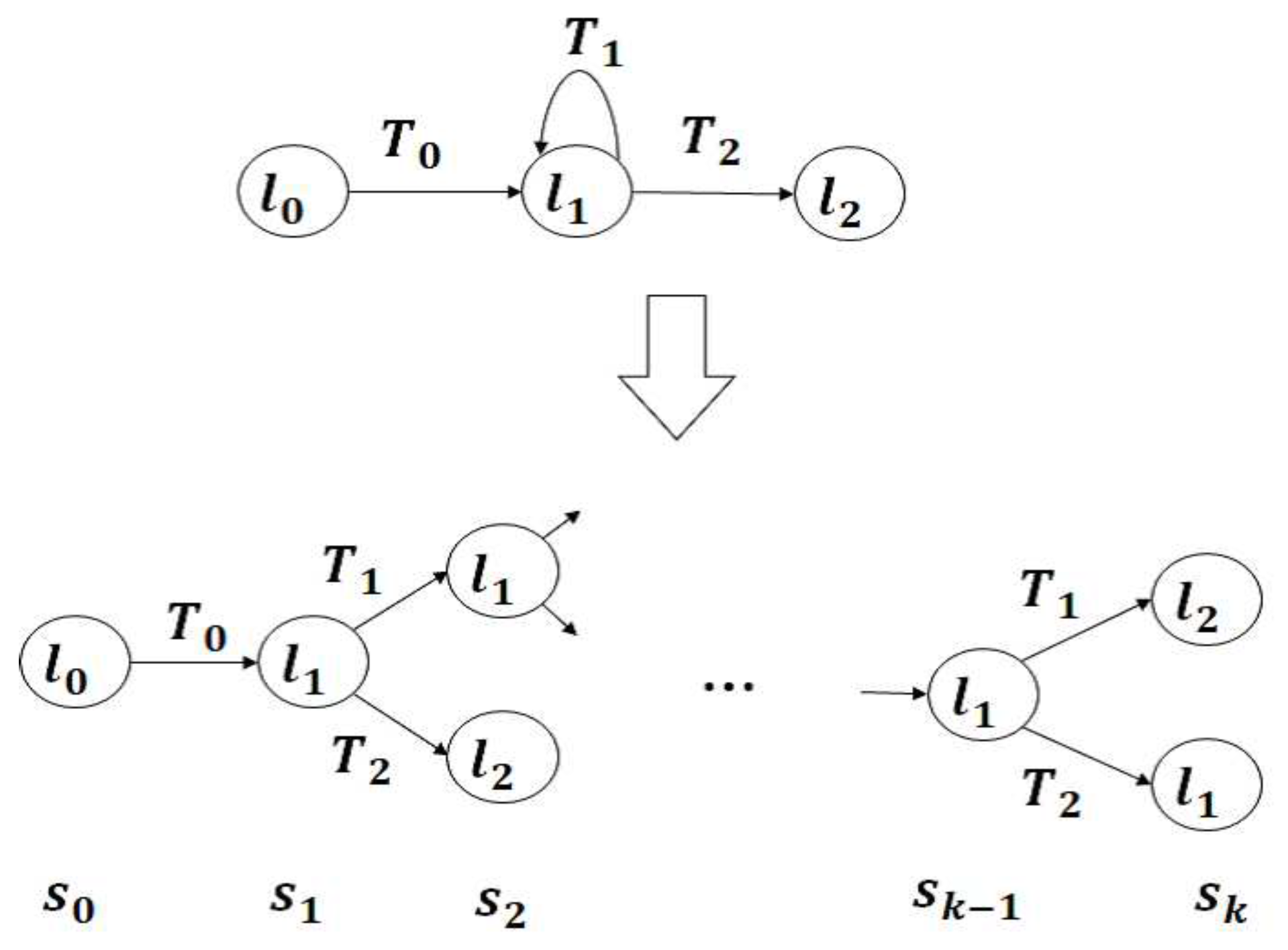
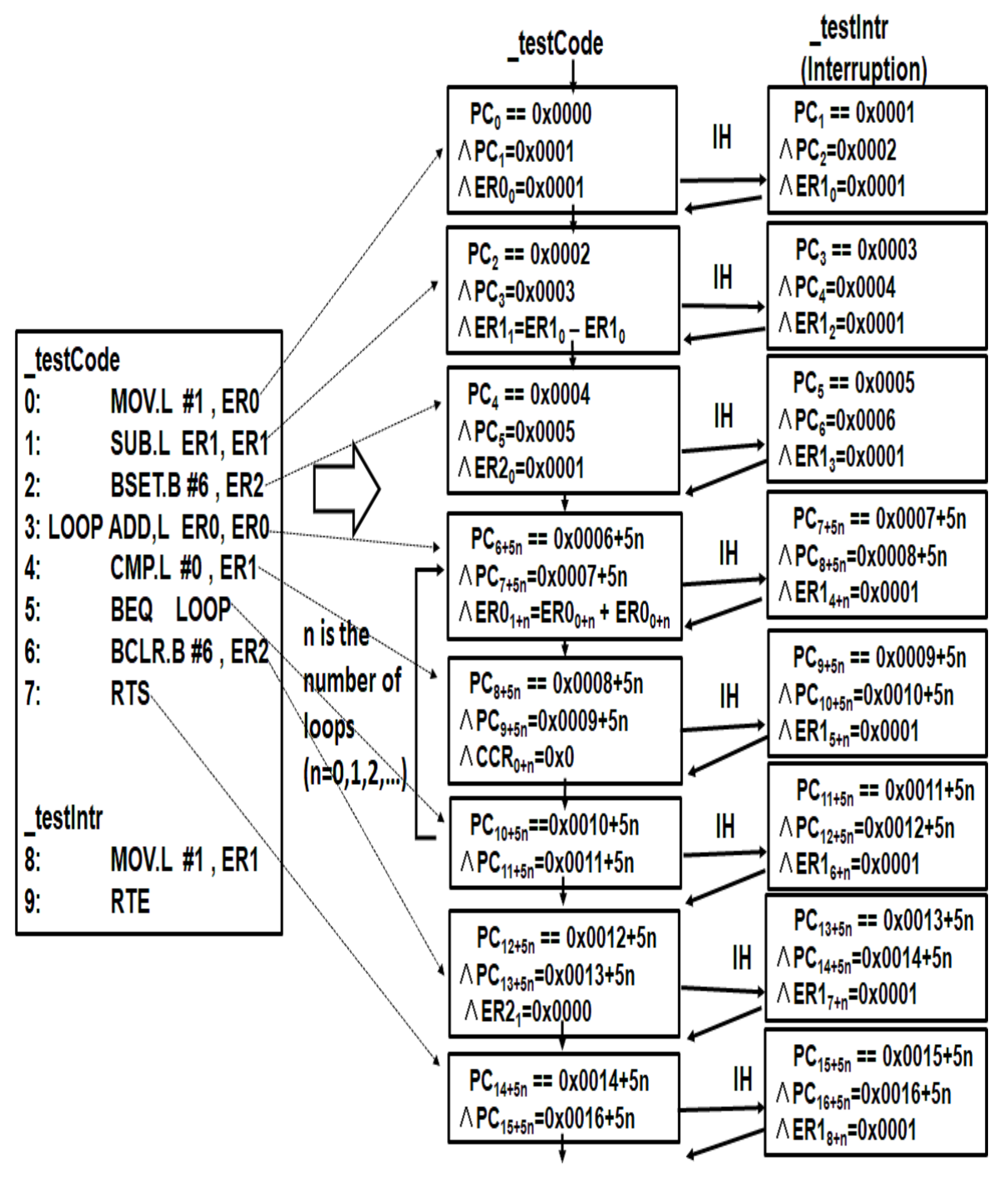
- CFG of IHER is developed by B. Schlich et al. [8]. IHER reduces the number of Interrupt Handler executions by blocking Interrupt Handlers at program locations where there is no dependency between certain Interrupt Handlers and the program [8]. Therefore CFG of IHER is shown in Figure 7.For example, in Figure 7, since the value of ER1 after executing SUB.L instruction is the same regardless of the presence or absence of the interrupt routine, the transition to the interrupt routine is decreasing because there is no dependency. As explained in Section 4, IHER and our proposed method analyze even such complex dependencies.
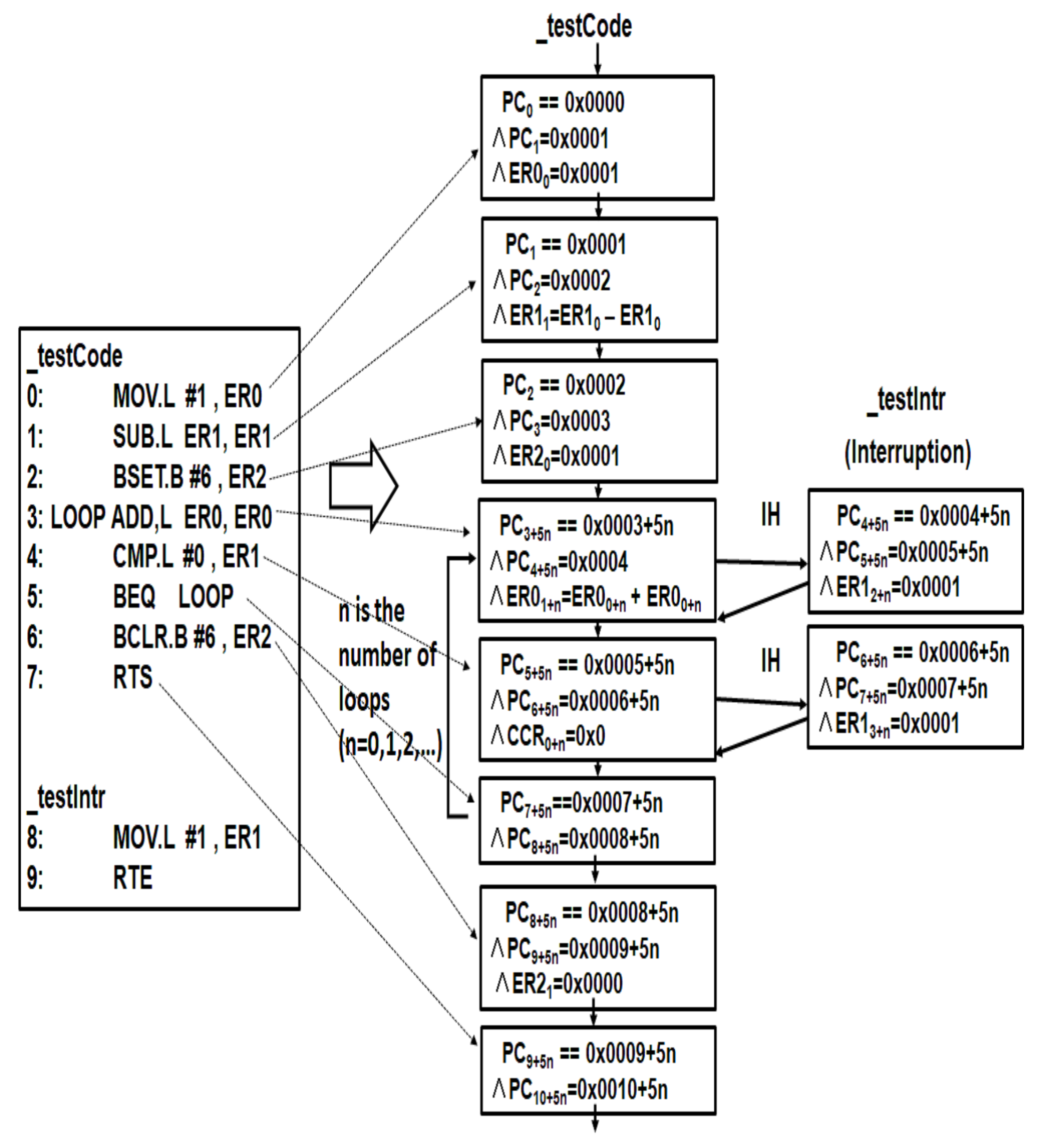
- We propose CFG of ACB in this paper. We propose ACB by extending Basic block of CFG [6,7] using IHER [8] in order to reduce the state spaces. In order to reduce the number of blocks, we propose the method of making the block of codes, at which interruptions do not occur. Therefore CFG of ACB is shown in Figure 8. Here for example, we show , , in Figure 8 as follows:
- (a)
- (b)
- The following is repeated with a loop count of lines 3–5 of the program:
- (c)
- Here, the on the sixth line of the program is , and the on the seventh line is .
However, changes depending on k of bounded model check k-bound. The larger k is, the larger n is.
6. Prototype Model Checker
6.1. Verification Example
6.2. Example of Modeling Assembly Instructions
- The data transfer instruction is represented by the equation between source register and destination register .
- is represented by the equation between an operation result and a destination register using , and .
- ⓐ denotes register indirect addressing. stores the low 8 bits of a source operand into the address that the value in a destination register points. Access to address space (AS) is defined by a function, and the argument of the function is indirect address.
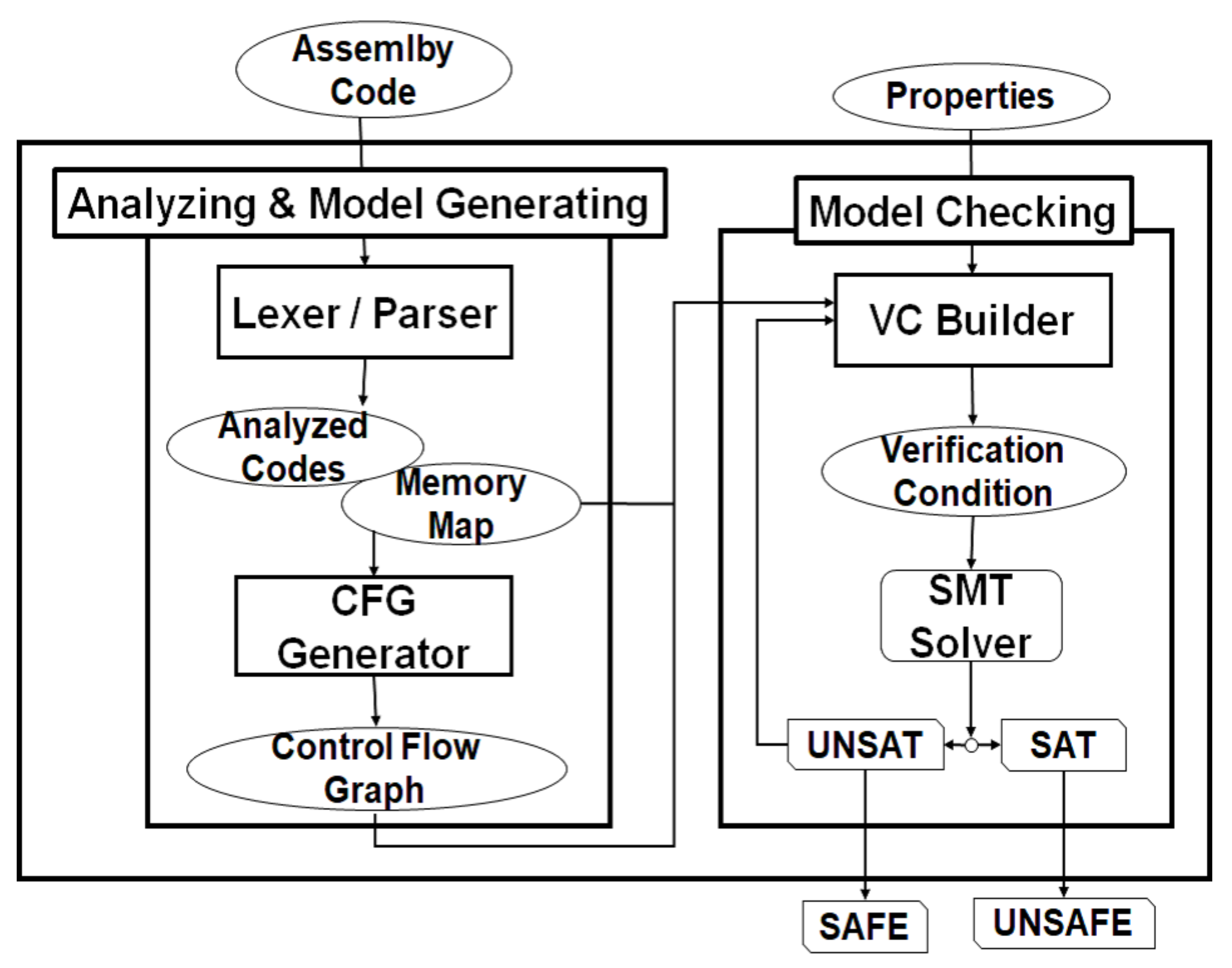
6.3. Configuration of Prototype Model Checker
- Lexer and Parser:
- CFG generator:CFG generator constructs CFG from syntax tree. First CFG generator composes interrupts. After that it constructs CFG using IHER. CFG consists of both ACBs and the transitions between ACBs.
- VC builder:VC builder generates verification conditions. VC builder generates logical formulas of an initial condition and transition relations from CFG. Given a property and a bound k, the verification condition is gnerated such as Equation (6).
7. Verification Experiments
7.1. Overview of Verification Experiments
- : Program reaches RTS instruction.
- : The value of stack pointer after reaching RTS is equal to the value of stack pointer before executing the routine.
- : The value of after executing RTS is equal to return address.
- : The initial value of is set.
- : The initial value of stack pointer is equal to the value of stack pointer before calling this routine.
- : The return address is stored in the stack at the time of the routine start.
- When the initial value of is set to and the return destination address is set to in program 1, the set of initial states is defined as follows:, where , , .Here is an expression defining the initial value of the program counter (corresponding to the initial condition 1), is an expression defining that the initial value of stack pointer is equal to the value of stack pointer before calling this routine (corresponding to the initial condition 2), and is an expression defining that the return address is stored in the stack at the time of the routine start.
- When the address of ReTurn from Subroutine (RTS) instruction is , the return destination address is , and the stack pointer register is in program 1, the verification property is defined, where and as follows:, where , , .As shown in Figure 8, a verifier specify including and using the correspondence between the assembly program and the CFG with dotted arrows, where n is the number of loops of program.Here is an expression defining that Program reaches RTS instruction (corresponding to the property 1), is an expression defining that the value of stack pointer after reaching RTS is equal to the value of stack pointer before executing the routine (corresponding to the property 2), and is an expression defining that the value of after executing RTS is equal to return address (corresponding to the property 3).
- The verification property that the stack pointer before the function call is equal to the stack pointer immediately after returning from the called function can be verified only by the assembly program. By this verification property we verify whether the stack is not destroyed.
- The verification property that the return address saved before the function call is equal to the address after execution of the RTS instruction of the called function can be verified only by the assembly program. By this verification property we verify whether the stack is not destroyed, too.
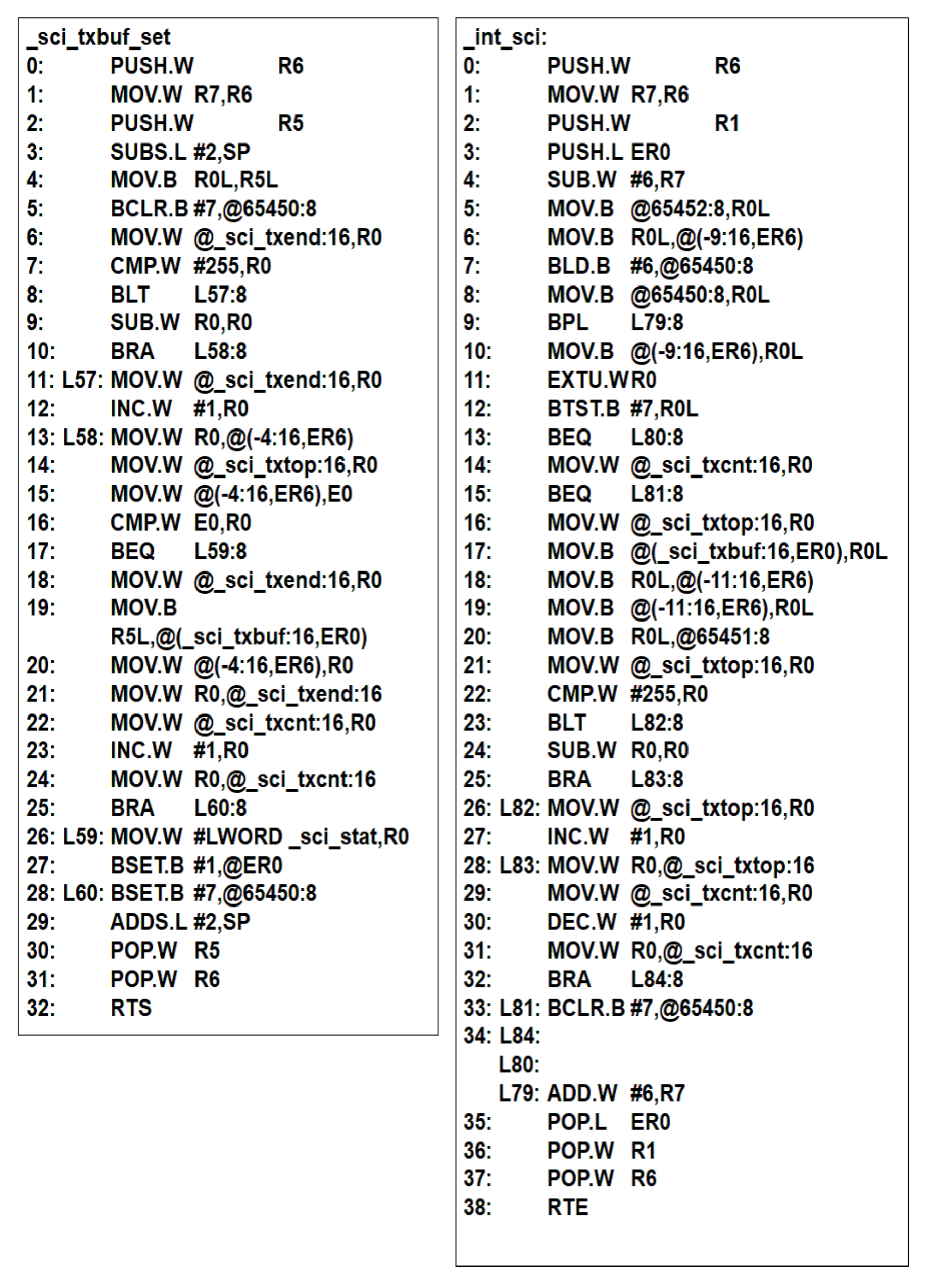
7.2. Which Programs Are Verified ?
7.3. Results of Experiments
7.3.1. Verification Results of Program 1
7.3.2. Verification Results of Program 2
7.4. Comparison with Classical Model Checking
7.4.1. Comparison with the Classical Model Checker SPIN
- partial order reduction
- bitstate hashing
- minimised automaton encoding of states (not in a hashtable)
- state vector compression
- dataflow analysis
- slicing algorithm
7.4.2. Examples That Can Not Be Verified by Classical Model Checking
8. Conclusions and Future Works
Author Contributions
Funding
Conflicts of Interest
References
- Schlich, B. Model Checking of Software for Microcontrollers. ACM Trans. Embed. Comput. Syst. 2010, 9, 1–27. [Google Scholar] [CrossRef]
- Kanellos, M. Software Glitch Stalls Some Toyota Hybrids. Available online: https://www.cnet.com/roadshow/news/software-glitch-stalls-some-toyota-hybrids/ (accessed on 28 May 2020).
- International Electrotechnical Commission. Functional Safety for Electrical/Electronic/Programmable Electronic Safety-Related Systems; IEC: Geneva, Switzerland, 2010. [Google Scholar]
- Clarke, E.M., Jr.; Grumberg, O.; Kroening, D.; Peled, D.; Veith, H. Model Checking; Cyber Physical Systems Series; MIT Press: Cambridge, MA, USA, 2018. [Google Scholar]
- Schlich, B.; Kowalewski, S. Model checking C source code for embedded systems. Int. J. Softw. Tools Technol. Transf. 2009, 11, 187–202. [Google Scholar] [CrossRef]
- Muchnick, S. Advanced Compiler Design and Implementation; Morgan Kaufmann Publishers Inc.: Burlington, MA, USA, 1997. [Google Scholar]
- Aho, A.V.; Sethi, R.; Ullman, J.D. Compilers: Principles, Techniques and Tools, 2 Revised ed of International ed.; Pearson: London, UK, 2006. [Google Scholar]
- Schlich, B.; Noll, T.; Brauer, J.; Brutschy, L. Reduction of interrupt handler executions for model checking embedded software. In HVC 2009: Hardware and Software: Verification and Testing; Springer: Berlin/Heidelberg, Germany, 2011; pp. 5–20. [Google Scholar]
- Armando, A.; Mantovani, J.; Platania, L. Bounded model checking of software using SMT solvers instead of SAT solvers. Int. J. Softw. Tools Technol. Transf. 2009, 11, 69–83. [Google Scholar] [CrossRef]
- Cordeiro, L.; Fischer, B.; Marques-Silva, J. SMT-Based Bounded Model Checking for Embedded ANSI-C Software. IEEE Trans. Softw. Eng. 2012, 38, 957–974. [Google Scholar] [CrossRef]
- Takeshita, A.; Kobashi, J.; Yamane, S. Verification of embedded software in assembly code by SMT Solver. In ESS2012; Information Processing Society of Japan: Tokyo, Japan, 2012; pp. 197–202. [Google Scholar]
- Kobashi, J.; Yamane, S.; Takeshita, A. Development of SMT-Based Bounded Model Checker for embedded assembly program. In Proceedings of the 2014 IEEE 3rd Global Conference on Consumer Electronics (GCCE), Tokyo, Japan, 7–10 October 2014. [Google Scholar]
- Yamane, S.; Konoshita, R.; Kato, T. Model checking of embedded assembly program based on simulation. IEICE Trans. Inf. Syst. 2017, 100, 1819–1826. [Google Scholar] [CrossRef]
- Schlich, B.; Brauer, J.; Kowalewski, S. Application of static analyses for state-space reduction to the microcontroller binary code. Sci. Comput. Program 2011, 76, 100–118. [Google Scholar] [CrossRef][Green Version]
- Liang, L.; Melham, T.; Kroening, D.; Schrammel, P.; Tautschnig, M. Effective Verification for Low-Level Software with Competing Interrupts. ACM Trans. Embed. Comput. Syst. 2018, 17, 36:1–36:26. [Google Scholar] [CrossRef]
- Burch, J.R.; Clarke, E.M.; McMillan, K.L.; Dill, D.L.; Hwang, L.J. Symbolic Model Checking: 1020 States and Beyond. Inf. Comput. 1992, 98, 142–170. [Google Scholar] [CrossRef]
- Biere, A.; Cimatti, A.; Clarke, E.M.; Fujita, M.; Zhu, Y. Symbolic Model Checking Using SAT Procedures instead of BDDs. In Proceedings of the 36th Annual ACM/IEEE Design Automation Conference, New Orleans, LA, USA, 21–25 June 1999; pp. 317–320. [Google Scholar]
- Barrett, C.; Sebastiani, R.; Seshia, S.A.; Tinelli, C. Satisfability Modulo Theories. In Handbook of Satisfability; Springer: Cham, Switzerland, 2018; pp. 305–343. [Google Scholar]
- Biere, A.; Cimatti, A.; Clarke, E.; Zhu, Y. Symbolic model checking without BDDs. In International Conference on Tools and Algorithms for the Construction and Analysis of Systems; Springer: Berlin/Heidelberg, Germany, 1999; pp. 193–207. [Google Scholar]
- Barrett, C.; Stump, A.; Tinelli, C. The SMT-LIB Standard: Version 2.0; SMT-LIB.org; Department of Computer Science, The University of Iowa: Iowa City, IA, USA, 2010. [Google Scholar]
- Cok, D.R. The SMT-LIB v2 Language and Tools: A Tutorial. Available online: https://smtlib.github.io/jSMTLIB/SMTLIBTutorial.pdf (accessed on 28 May 2020).
- Henzinger, T.A.; Jhala, R.; Majumdar, R.; Sutre, G. Lazy abstraction. In Proceedings of the 29th ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, Portland, OR, USA, 16–18 January 2002; pp. 58–70. [Google Scholar]
- Beyer, D.; Henzinger, T.A.; Jhala, R.; Majumdar, R. The software model checker Blast. Int. J. Softw. Tools Technol. Transf. 2007, 9, 505–525. [Google Scholar] [CrossRef]
- Nadel, A. Handling Bit-Propagating Operations in Bit-Vector Reasoning. In Proceedings of the Workshop on Satisfiability Modulo Theories, Helsinki, Finland, 8–9 July 2013. [Google Scholar]
- Browne, M.C.; Clarke, E.M.; Grumberg, O. Characterizing Finite Kripke Structures in Propositional Temporal Logic. Theor. Comput. Sci. 1988, 59, 115–131. [Google Scholar] [CrossRef]
- H8/3687 Group Hardware Manual—RS Components International, Renesas. 2005. Available online: https://docs-emea.rs-online.com/webdocs/0862/0900766b80862532.pdf (accessed on 28 May 2020).
- H8S, H8/300 Series C/C++ Compiler Package, Renesas. 2010. Available online: https://www.renesas.com/en-us/doc/products/tool/apn/rej05b0464_h8s.pdf (accessed on 28 May 2020).
- JFlex—The Fast Scanner Generator for Java. 2015. Available online: http://jflex.de/ (accessed on 28 May 2020).
- BYACC/J Java Extension. 2013. Available online: http://byaccj.sourceforge.net/ (accessed on 28 May 2020).
- De Moura, L.; Bjørner, N. Z3: An Efficient SMT Solver. In International Conference on Tools and Algorithms for the Construction and Analysis of Systems; Springer: Berlin/Heidelberg, Germany, 2008; pp. 337–340. [Google Scholar]
- ZMP Inc. Nuvo R WHEEL. 2010. Available online: https://robot.watch.impress.co.jp/cda/news/2006/07/12/81.html (accessed on 12 October 2019).
- Holzmann, G.J. The model checker SPIN. IEEE Trans. Softw. Eng. 1997, 23, 279–295. [Google Scholar] [CrossRef]







| Item | Instruction | Operation | Formula |
|---|---|---|---|
| 1. | MOV.L ERs, ERd | ERs32 → ERd32 | |
| 2. | ADD.W Rs, Rd | Rd16 + Rs16 → Rd16 | |
| 3. | MOV.B RsL, @ERd | Rs8 → @ERd | |
| and | |||
| CPU | Windows 7 Professional 64 bit |
| OS | Core i7-3770 CPU @3.40 GHz |
| Memory | 16 GB |
| SMT solver | Microsoft Z3 v4.3.0 [30] |
| Java | Ver. 1.7.0_45 |
| Prototype | 8400 lines |
| Model | Nodes | Result | Time (s) | k-Bound | Assembly [Lines] |
|---|---|---|---|---|---|
| IHER | 10 | UNSAT | 3673 | 57 | 3536 |
| ACB | 5 | UNSAT | 4075 | 52 | 4682 |
| Model | Nodes | Result | Time (s) | k-Bound | Assembly [Lines] |
|---|---|---|---|---|---|
| IHER | 73 | UNSAT | 43,656 | 33 | 4485 |
| ACB | 43 | UNSAT | 43,789 | 22 | 9704 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yamane, S.; Kobashi, J.; Uemura, K. Verification Method of Safety Properties of Embedded Assembly Program by Combining SMT-Based Bounded Model Checking and Reduction of Interrupt Handler Executions. Electronics 2020, 9, 1060. https://doi.org/10.3390/electronics9071060
Yamane S, Kobashi J, Uemura K. Verification Method of Safety Properties of Embedded Assembly Program by Combining SMT-Based Bounded Model Checking and Reduction of Interrupt Handler Executions. Electronics. 2020; 9(7):1060. https://doi.org/10.3390/electronics9071060
Chicago/Turabian StyleYamane, Satoshi, Junpei Kobashi, and Kosuke Uemura. 2020. "Verification Method of Safety Properties of Embedded Assembly Program by Combining SMT-Based Bounded Model Checking and Reduction of Interrupt Handler Executions" Electronics 9, no. 7: 1060. https://doi.org/10.3390/electronics9071060
APA StyleYamane, S., Kobashi, J., & Uemura, K. (2020). Verification Method of Safety Properties of Embedded Assembly Program by Combining SMT-Based Bounded Model Checking and Reduction of Interrupt Handler Executions. Electronics, 9(7), 1060. https://doi.org/10.3390/electronics9071060




