1. Introduction
Internet of Things, also referred to as IoT, has become one of the most eye-catching technologies in recent years. In the immediate future, in 2025, more than 24.9 billion IoT connections are forecasted [
1]. IoT brings huge innovation space and business value to many application fields, such as environmental monitoring, smart homes, smart cities, and so on. [
2,
3,
4,
5,
6]. As the Internet of things technology is used more and more widely, security issues have also started to attract widespread attention. According to the report from Gartner, 20% of companies or organizations have experienced at least one IoT-based attack in the past three years [
7].
Most IoT devices are vulnerable to malicious attacks, and the attack surfaces mainly include hardware, software, and protocols. The first is attack on the hardware. Because of the simple structure and low cost of the IoT device, it is relatively easy to be imitated and replaced. In addition, some devices are placed in unmanned areas, such as sensor nodes, which are vulnerable to physical damage. The second is attack on the software. An attacker can gain control of the terminal by hacking the operating system of the device or injecting malicious code, and illegally read user data stored on the device [
8,
9,
10]. Once control of the IoT device is obtained, the device can be used as a springboard to further invade the back-end service system [
11]. The last attack surface is attacking the protocol. Due to the limited capabilities of computing, storage, and communication, most IoT devices adopt lightweight designed communication protocols and identity authentication protocols. Because the key and encryption algorithm are too simple, the data is vulnerable to eavesdropping and tampering during transmission, and the confidentiality and integrity of the data are difficult to guarantee. Because of the huge number of IoT devices and the wide attack surface, once IoT devices are maliciously controlled, a large-scale denial of service attack could be constituted, such as the Dyn event in 2016 [
12].
Through the above analysis, it can be found that the IoT device is the key to achieving IoT security. Usually, to prevent unauthorized users from accessing the system, most IoT terminals use password-based authentication. Facts have shown that this approach has huge security risks. Taking the city camera as an example, due to the large number of cameras, it is difficult for the staff to set the passwords one by one, and most of them use the default initial password. Once the password of a single camera is cracked, it will cause other cameras to lose control [
13]. Therefore, identity authentication for IoT terminal is considered a key issue to ensure the security of IoT systems [
14].
With the continuous enrichment of IoT application, it is inevitable that there will be requirement for cross-domain access, value exchange and collaborative control among different application systems. Since different application systems have their own user space and autonomy, these requirements of cross-domain access caused cross-domain authentication issue. For example, the smart bracelet of the smart medical system needs to be connected to the smart home system to obtain the environmental parameters of the patient’s living in order to provide reference data for the doctor’s diagnosis. Since the bracelet needs to access smart home system and smart medical system at the same time, Cross-domain authentication is needed. The issue of cross-domain authentication is described as follows. Assume that there are multiple security domains in a network, and each domain has its own users and certificate authority. The goal of cross-domain authentication is to integrate these security domains so that the same user identity can log in to different domains and access resources and services in it.
The traditional identity authentication protocol based on the public key infrastructure, also known as PKI, is considered to be the most secure identity authentication method, but this type of scheme is not suitable for IoT terminals [
15]. Firstly, most IoT terminals have limited resources in terms of energy, memory and processing capacity, the calculation, storage, and communication costs generated by this type of identity authentication protocol are too high to resource constrained IoT terminals [
16,
17]. Secondly, the traditional PKI based authentication model is a centralized authentication model, which has a single point of failure risk and is difficult to resist DOS / DDoS attacks [
18,
19]. Additionally, in the mMtc application scenario of 5G, the authentication peak caused by massive terminal accesses may also cause the authentication system to be paralyzed. Finally, due to political, economic and many other reasons, it is difficult to require all application systems to believe in a unified third-party organization. Compared with the centralized authentication model, the decentralized authentication model has no single point of failure, and has good scalability, which is considered as the development trend of the Internet of things authentication technology. Blockchain technology is regarded as an effective means to realize decentralized authentication [
20].
In this paper, we propose an identity-based cross-domain authentication scheme for the Internet of Things. For convenience, our algorithm is called IRBA, which is consisted by the first letter of the four words Identity, Recognize, Blockchain, and Algorithm. IRBA explored the cross-domain access control problems caused by multiple IoT applications and proposed a novel solution with low cost, fast response, and anti-attack function, while eliminating the security risks brought by trusted third parties.
Compared with the previous research works, the innovations and contributions of IRBA are as follows:
Proposed a cross-domain access control oriented authentication method based on IBC (Identity-Based Cryptograph) algorithm.
IRBA decomposes the cross-domain access control into two stages: identity authentication and access authorization. In the identity authentication stage, IRBA uses the identity of the IoT terminal to replace digital certificates issued by third parties and implements a decentralized identity authentication. Since every application domain can verify the authenticity of its identity through the identity of terminal, it does not need to rely on a third-party authentication server during the authentication stage. Our method avoids the problem that IoT terminals need to maintain multiple digital certificates for different application domains.
Proposed a cross-domain joint authorization method based on threshold cryptographic algorithm.
Using threshold cryptography algorithm, IRBA has designed a joint authorization method for cross-domain access. With this method, authentication servers in different application domains can jointly calculate the authorization signature and can independently verify the authorization signature. Therefore, the authorization process does not rely on trusted third parties. IRBA implements the authorization process through smart contracts to ensure the credibility of the authorization process. At the same time, the Blockchain is used to save the authorization results to ensure the authenticity of the authorization results. Through the above mechanism, IRBA achieves decentralized storage of access authorization results.
Proposed an implementation scheme and evaluated the effectiveness through the prototype system
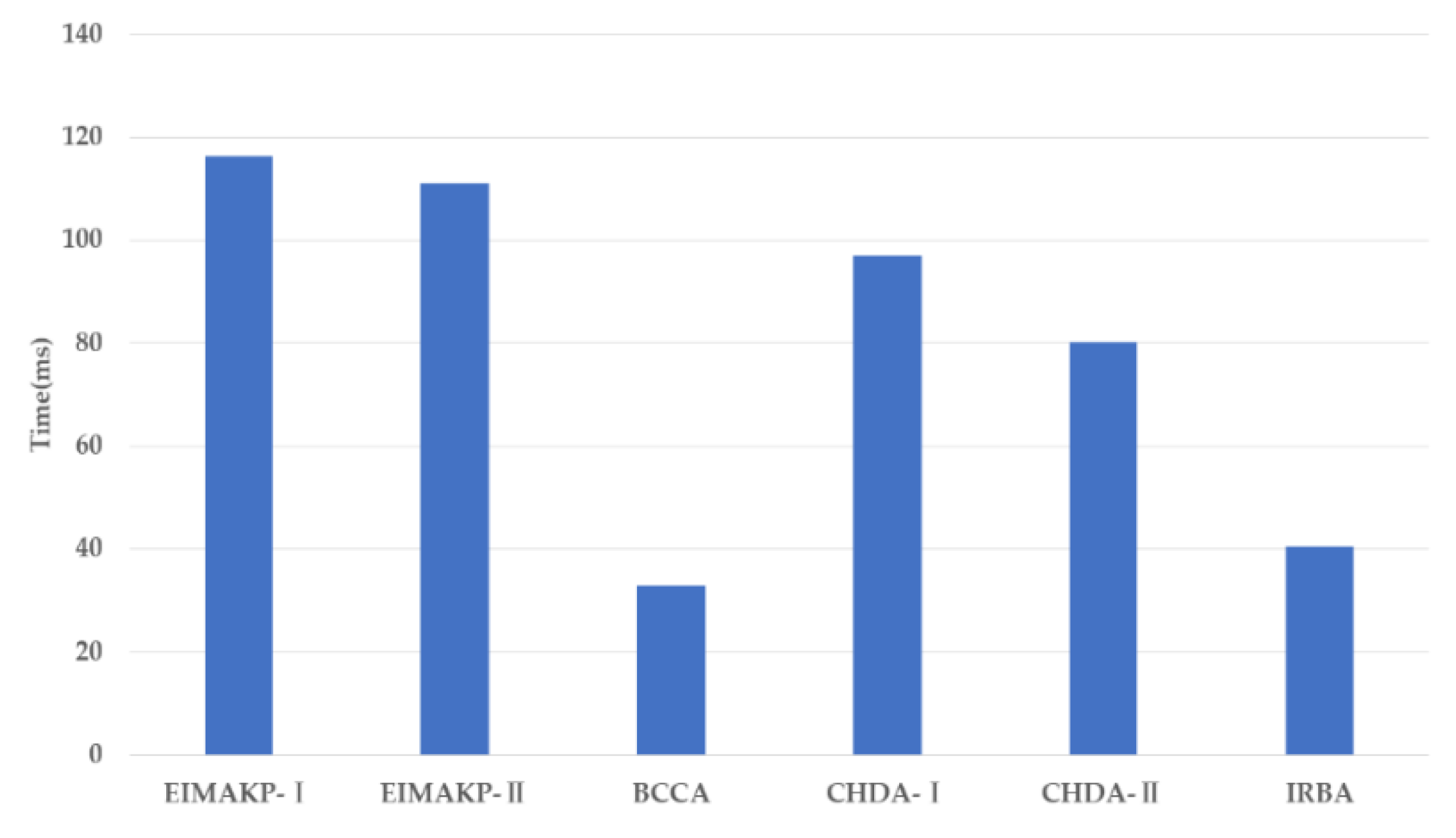
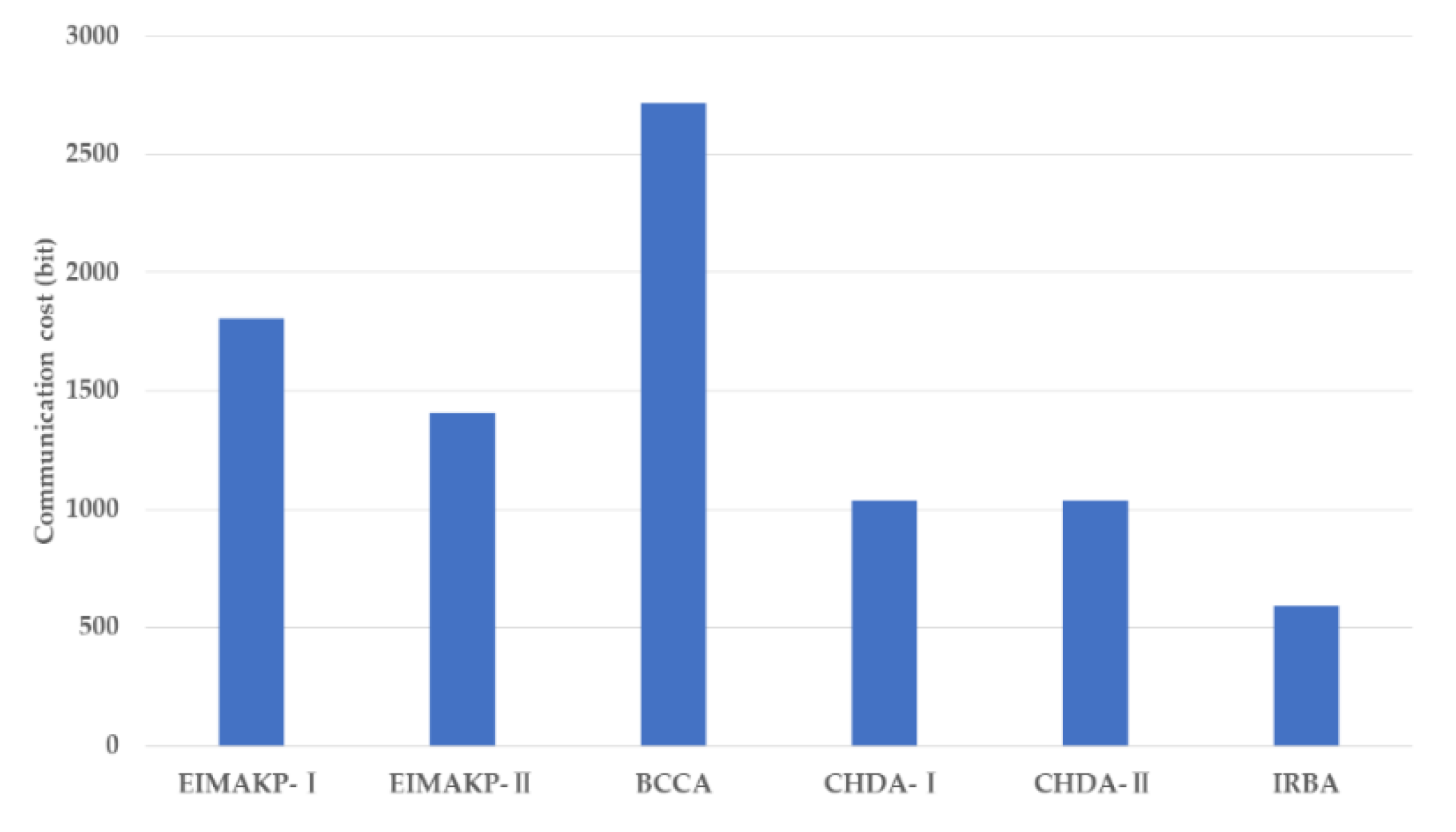
We implemented a prototype system of IRBA based on two open source projects, which are Hyperledger Fabric and YH-RADIUS. Furthermore, we performed a performance evaluation of the core mechanism of IRBA. The experimental results show that IRBA has good processing performance and low computing overhead, which is very suitable for solving the cross-domain authentication problem of IoT.
The remainder of this article is organized as follows.
Section 2 introduces the existing research and related work.
Section 3 presents the motivation and our objectives.
Section 4 gives a detail description of IRBA.
Section 5 introduces the technical implementation of IRBA.
Section 6 gives the results of performance evaluation.
Section 7 summarizes of this article.
3. Motivation and Objectives
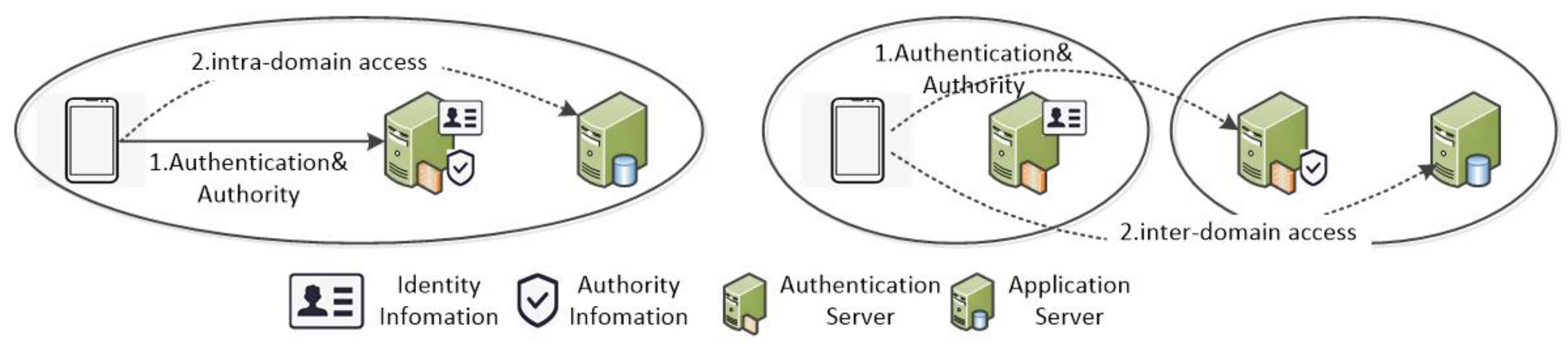
Considering the vulnerability of IoT terminals in terms of security, most IoT application systems use identity authentication mechanisms to prevent malicious access by illegal terminals. When an IoT terminal needs to access the background services, it must first authenticate its identity through an authentication server. After confirming the authenticity of the terminal, the authentication server also needs to check the network access authorization result of the terminal. Only authorized users can be allowed to access. This process is often referred to as network access control. Access control not only occurs in a single application system, but also access control problems between different application systems. The problem of access control not only occurs in case of single application system, but also exists between different application systems. For example, with the popularity of wearable devices, people began to use these devices to replace wallets and ID cards. When users use wearable devices as identity cards or wallets to consume or enjoy services in different chain stores or supermarkets, cross-domain authentication problems exist. Because different application systems have their own user space and security policies, they are independent security autonomous domains. When customers in store A need to access the system of store B, cross-authentication requirement arise.
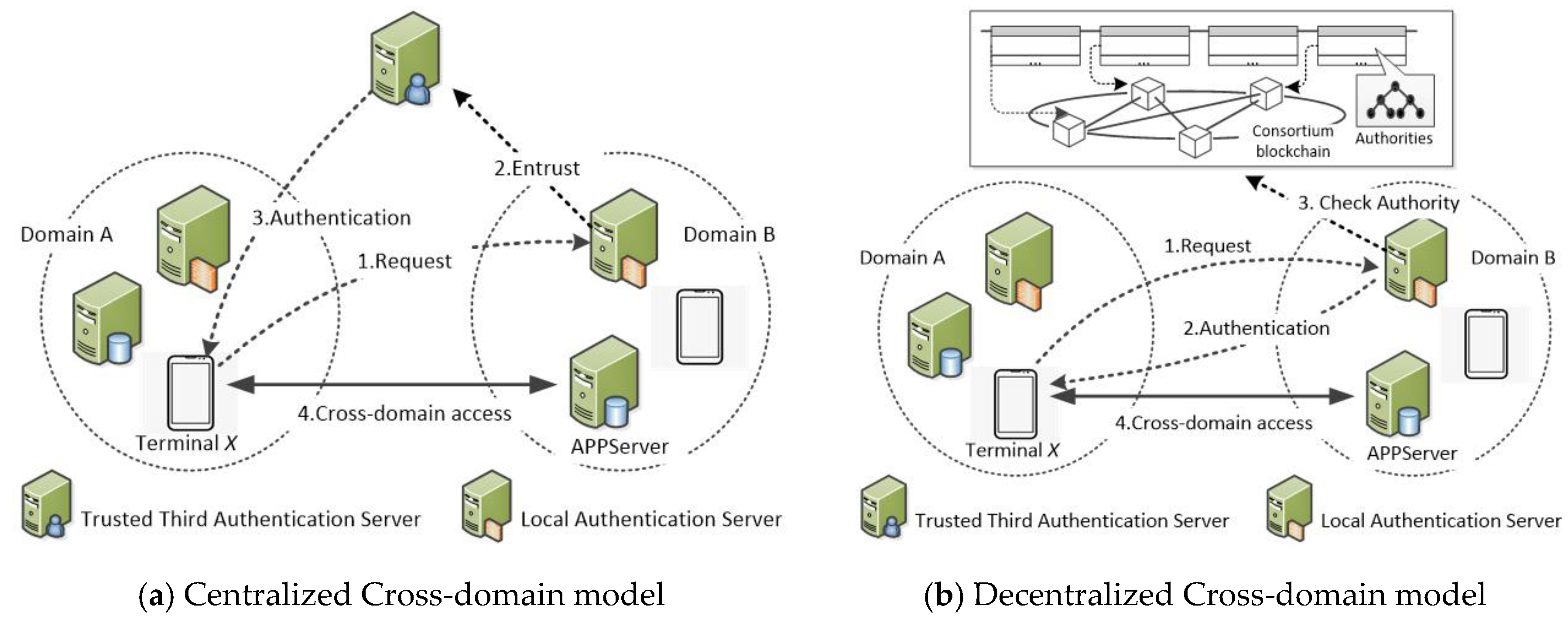
In order to solve the problem of cross-domain authentication, the traditional solution uses a centralized authentication model based on PKI. The authentication process is shown in
Figure 1a. For convenience, we define an application system with a unified Certificate Authority (CA) and secure access control policies as a security domain. In
Figure 1a, terminal
X represents a user of security domain
A. When
X needs to access the service of security domain
B, it has to pass the authentication and authorization checks from the authentication server of domain
B. Since there is no direct trust relationship between domain
A and domain
B, Domain
B entrusts
C, which is a trusted third party, to authenticate terminal
X and perform an authorization check before allowing
X to access. The centralized authentication model destroys the autonomy and independence of the application system, and there are hidden dangers of single points and unilateral control problems.
For eliminating the disadvantages of the centralized authentication model, we hope to implement a decentralized authentication model, which is shown in
Figure 1b. In
Figure 1b, domain A and domain B establish a federal relationship and generate a user authorization list that allows cross-domain access, then jointly calculate the digital signature for the authorization list. After that, the authorization result is submitted to Blockchain to prevent repudiation and tampering. When terminal
X accesses domain
B, it uses a self-authentication identity authentication method instead of RSA authentication, so that
B can complete the authentication of
X identity without introducing a trusted third party. Next, the authentication server of domain
B checks whether the authorization result stored on the Blockchain contains the terminal
X. If it does, authentication succeeds otherwise fails. Compared with the centralized authentication model, decentralized authentication can guarantee the autonomy and initiative of the security domain. It does not need to rely on a third party to dynamically adjust the mutual trust relationship.
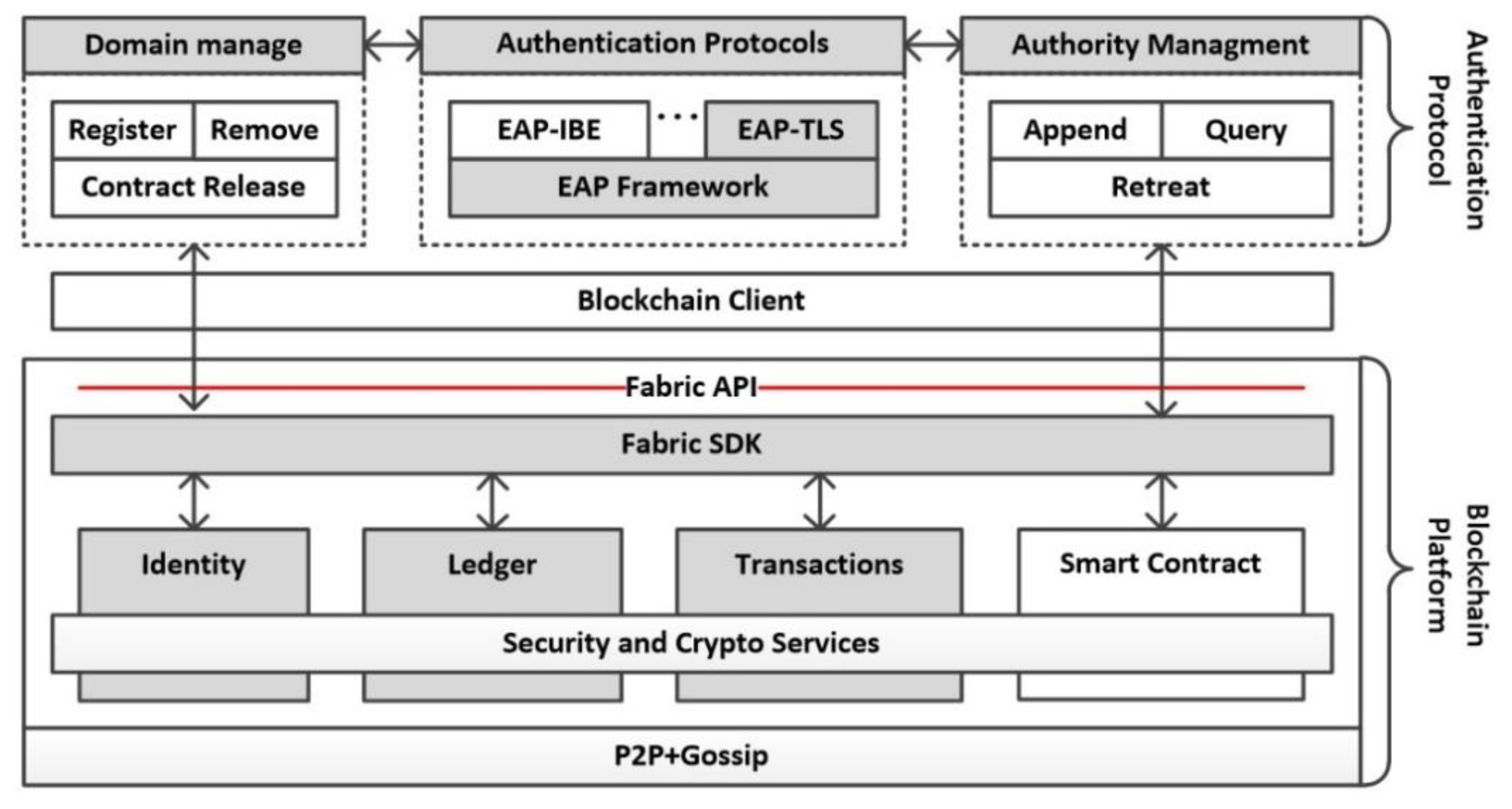
5. System Implementation
We develop a prototype system of IRBA with Go language. For convenience, we still use IRBA to represent the prototype system in this article. The IRBA consists of three parts. The first is the Blockchain platform. We adopt Hyperledger Fabric v1.0 [
46] in IRBA. Since IRBA does not need to change the underlying mechanism of the Blockchain, not only Hyperledger Fabric, but other Blockchain platforms that support smart contracts can also be selected. The second part is smart contract, which is called chain-code in Hyperledger Fabric. IRBA implements threshold cryptographic algorithms based on smart contracts. When the security domain wishes to establish a cross-domain trust relationship with other domains, it issues smart contracts through transactions. The third part is the authentication protocol. As we all know, Remote Authentication Dial In User Service (RADIUS) [
47] is often used to build AAA servers, also known as Authenticate, Authority and Audit server. Therefore, we choose the open source project-YH-RADIUS [
48]. This project implements an extensible development framework of RADIUS. The composition of the entire prototype system is shown in
Figure 5.
Given that near-field communication protocols such as Bluetooth cannot support remote access, in our prototype system, only the case of TCP / IP-based networks is considered for the time being.
In the
Figure 5, Extensible Authentication Protocol (EAP) is a universal authentication protocol standard framework running on TCP / IP networks [
49]. This framework implements different authentication processes by encapsulating different protocol plug-ins. By using an identity-based signature algorithm, we implement the EAP-IBE protocol in IRBA. The module of domain management in
Figure 5 is responsible for member registration, member removing, cross-domain request processing and smart contract release. When different security domains need to access each other, they release smart contracts through the domain management module, which is used to calculate joint authorization signatures of permission for cross-domain access. The model of authority management provides functions of appending, querying and retreating for cross-domain access authority. Because the Blockchain does not allow deletion of records that have been stored, both appending and retreating function will generate a new record with timestamp. When querying authorization results, the record with latest timestamp must prevail.
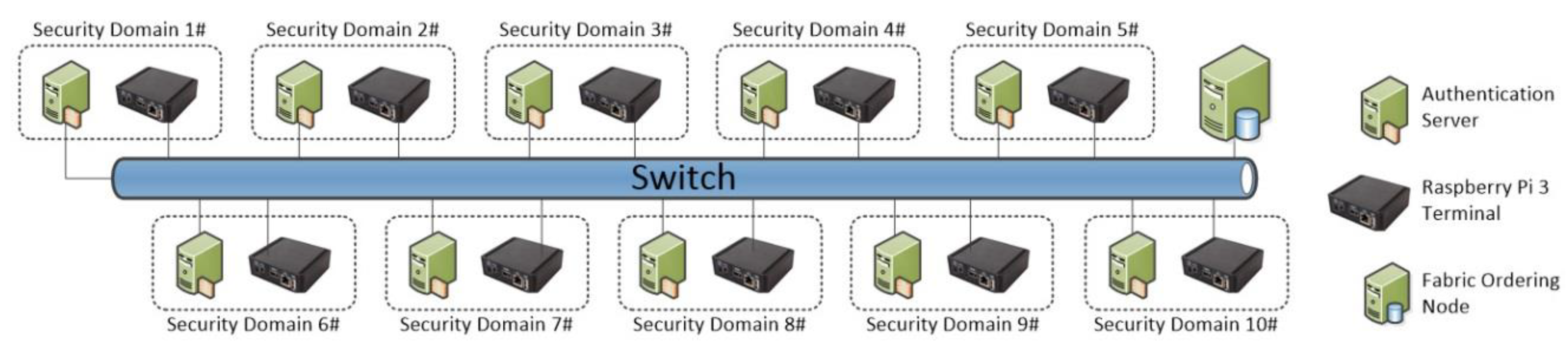
IRBA is installed on all authentication servers, providing full identity authentication and cross-domain access authentication capabilities. All IRBA-certified servers form a Fabric-based permission Blockchain [
50]. Every authentication server can be configured as endorsement node, confirmation node and CA node. Each authentication server locally saves the identity information of members in the domain, and also maintained the distributed ledger and chain code. In order to ensure the reliability of the Blockchain system, the deployment of the sequencing service adopts the Kafka model of Fabric, which can prevent single points of failure of the sequencing nodes.
Figure 6 presents a conceptual deployment scenario.
IRBA is composed of two subsystems which are authentication and access authorization. In the traditional AAA system implementation, the identity authentication subsystem interacts with the authorization subsystem through the RADIUS protocol. However, in IRBA, due to the special nature of smart contracts, the identity authentication subsystem calls the smart contract through the API of fabric SDK to complete the interaction.