1. Introduction
Wireless networks are the principal mechanisms for establishing computer networks through wireless connections among the nodes of a network [
1]. Therefore, wireless networking eliminates the costs of cables. Furthermore, wireless networking is implemented in the physical layer of open systems interconnection (OSI) model networks [
2]. Source to destination communications are possible with OSI models. The data are divided into data packets and are distributed by the internet protocol (IP), based on the packet header IP addresses [
3]. IP version 4 (IPv4) is the most commonly used IP adaptation. Moreover, IP version 6 (IPv6) is being rendered compatible for these applications. IPv6 supports longer addresses, thereby connecting greater number of internet users. Furthermore, IPv6 integrates IPv4. Therefore, a specific IP is required for mobile devices. The permanent IP addresses must be maintained when moving between different networks [
4]. Since mobile IPs (MIPs) are host-based, every movement results in delay, data loss, and signal overload. Therefore, dynamic IPs have been introduced in mobile IP technology. Functionality of this IP is updated by the system responsible for tracking the host’s developments and launching the required versatile named tag [
5].
The demand for high quality mobile computing service, known as "always and everywhere", will increase in the future. Additionally, the expectation and demand for different types of novel applications and several specific Quality of Services (QoS) mobile computing environments will likely increase. The rapid increase in demand for high-speed "anytime, anywhere" internet-access has become a concern for network operators [
6]. Generally, the tendency of central networks is to accommodate the requirements of all mobile IP networks. IP mobile networks, which transmit media (telecommunications) and use internet, organize networks emphatically. Networks, wherein IP operates from a mobile user to access point (AP), link wireless systems to the internet. Mobility management is a principal challenge for next-generation networks [
7]. Communication between different devices, through the internet is known as internet of things (IoT) [
8]. In simple terms, we discuss the mechanisms of a machine sending and receiving data. Due to advancements in the IoT, the number of communications devices is steadily increasing [
9] with the usage and number of devices becoming greater than the world’s population. The limit might increase, as human existence on other planets is not confirmed. Therefore, by 2020, as the use of devices increases with people, devises connecting the Web universe will also increase. This has not existed before. Therefore, by 2020, the IoT will likely exceed 50 billion linked gadgets [
9].
In 2018, the advent of high-end communication technology and user-friendly devices saw the development of wireless body networks (WBANs) and a dedicated human body network that monitored, directed, and communicated various vital functions, including blood pressure, temperature, and electrocardiogram (ECG), etc. Several sensors were connected to a patient’s body and clothing so as to monitor their vital functions. WBANs have a huge range of novel applications, including computer-assisted rehabilitation, an emergency medical response system (EMRS), ubiquitous health monitoring (UHM), and healthy life-style promotion [
10]. In general, WBAN in UHM helps in reducing hospital visits. As regular hospital visits are difficult for the general public, the said automation reduces dependency on the specialized health sector workforce. Therefore, this system is recommended in countries with inadequate medical infrastructure and medical personnel, enabling a quicker establishment of a cost-effective health care system. The WBAN is a communication network that integrates human system and computational interface, through portable devices. The common sensor node in a WBAN ensures in identifying correct signals, capturing weak sensor signals, and wirelessly processing these signals at a local processing unit. A special protocol, called a constrained application protocol (CoAP) [
9], has been introduced to remotely control WBAN. CoAP is a limited application protocol that transports data in packets from the client to the server. Furthermore, low-weight CoAP devices can be used in small-sized devices with a lower processing capacity and memory. CoAP devices use the user datagram protocol (UDP), which is light, compared to other protocols that support the simultaneous forwarding of messages to different recipients. Among mobile nodes (MNs), mobile access gateway (MAG) and local mobility anchor (LMA), MN moves among networks to facilitate the smooth running of sessions, reduce packet loss, and avoid handover delays in mobility management significance. After entering a new sensor node network domain, from MAG
A to MAG
B, MN changes the point of attachments. MAG
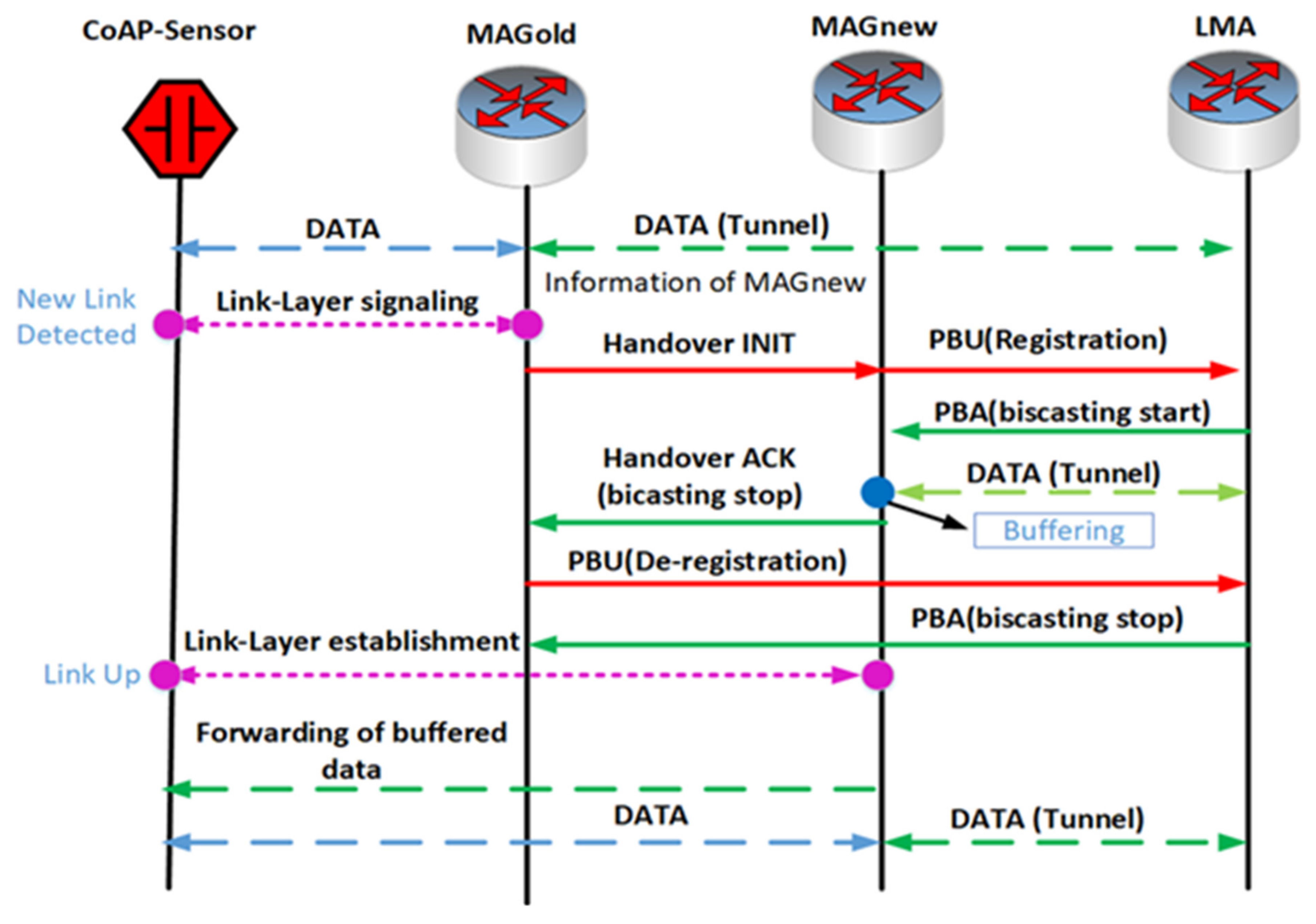
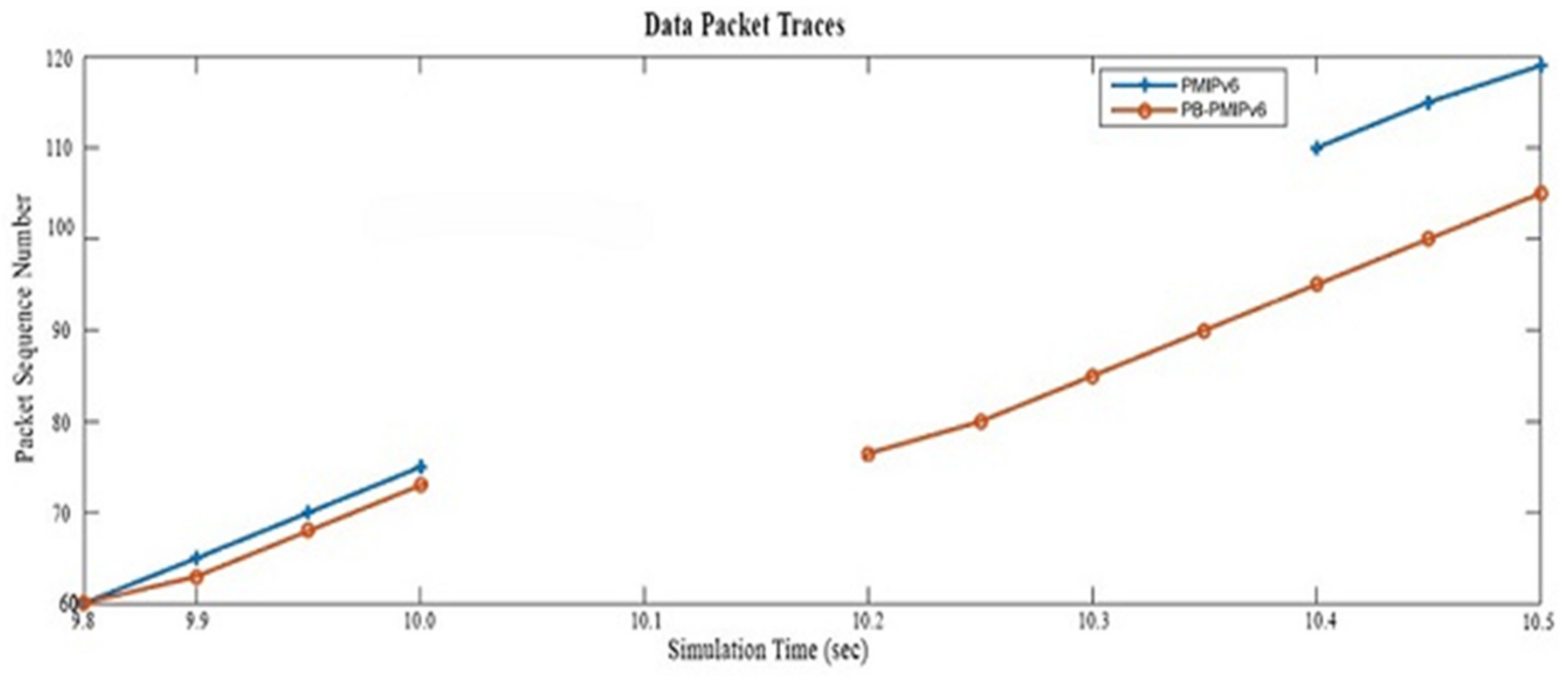
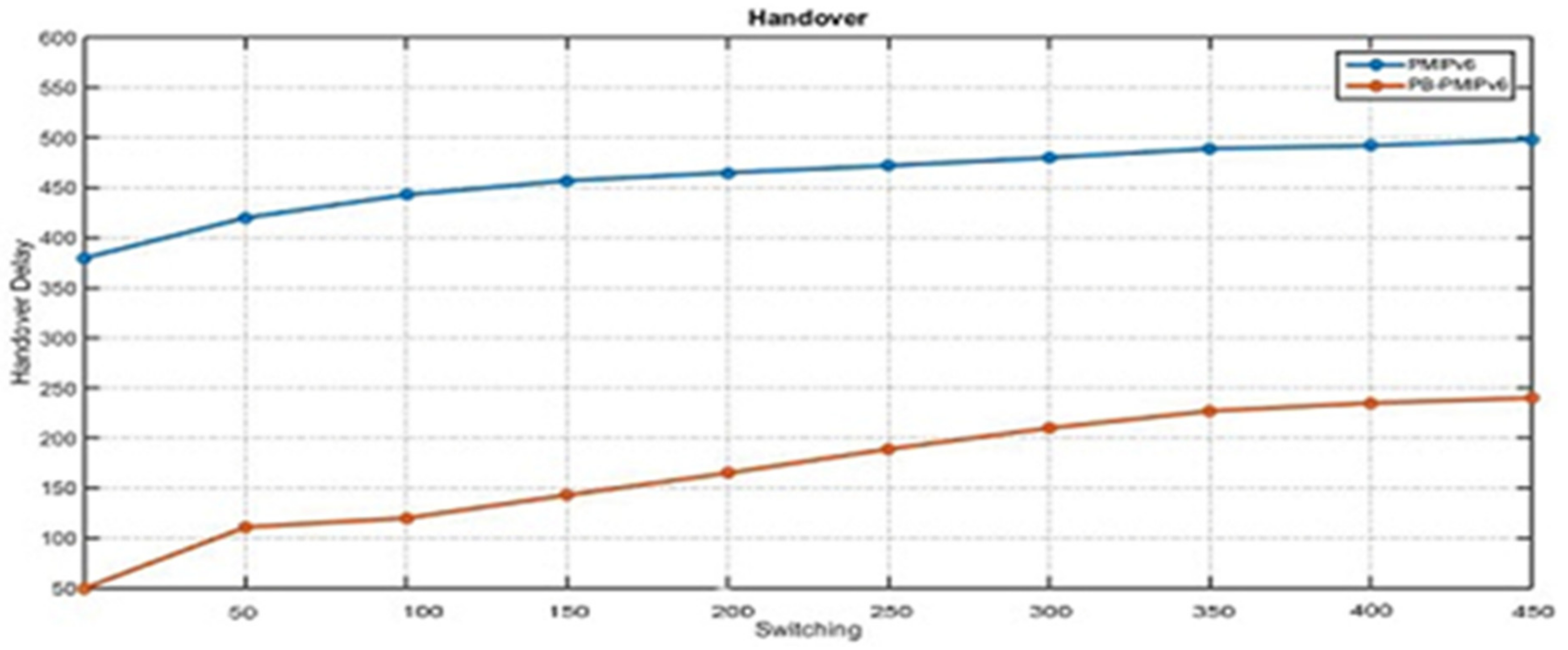
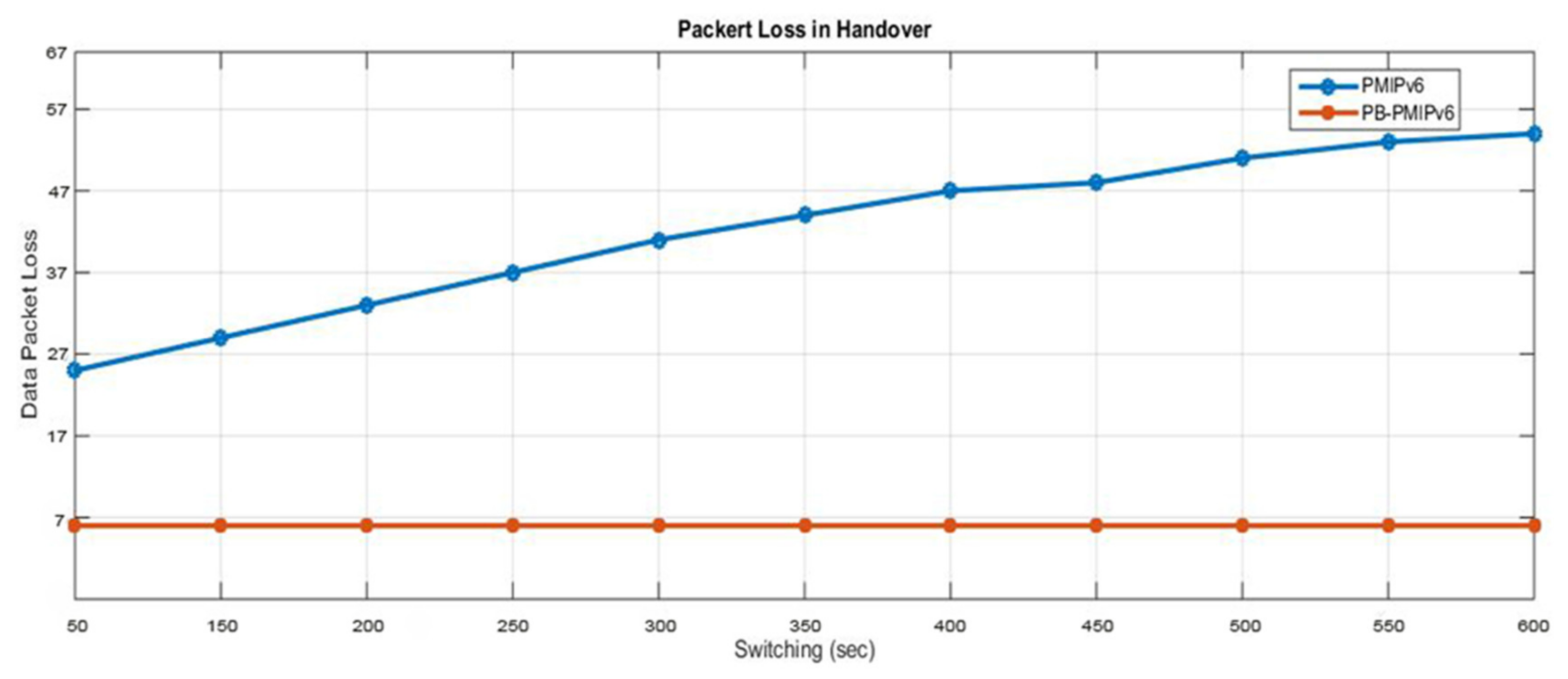
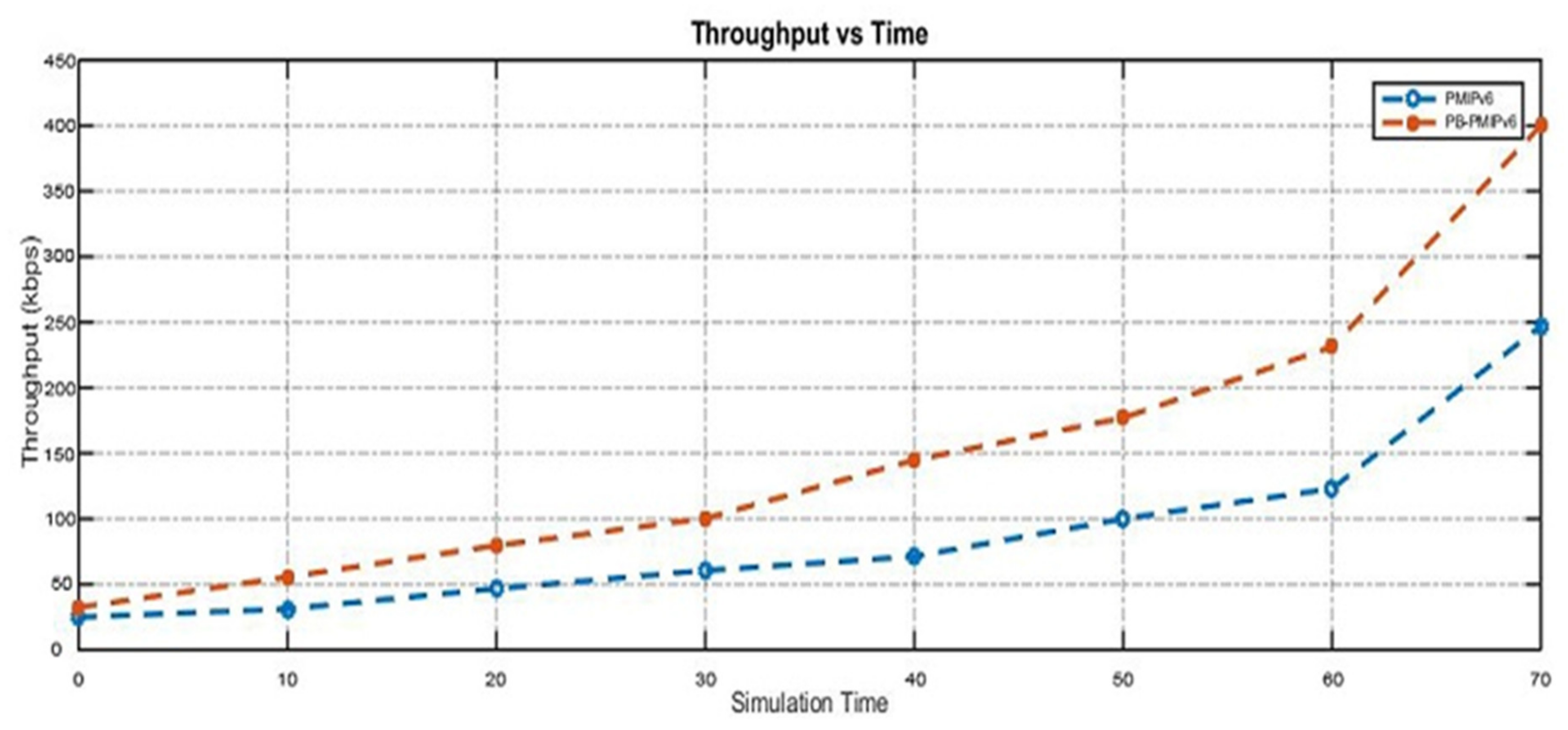
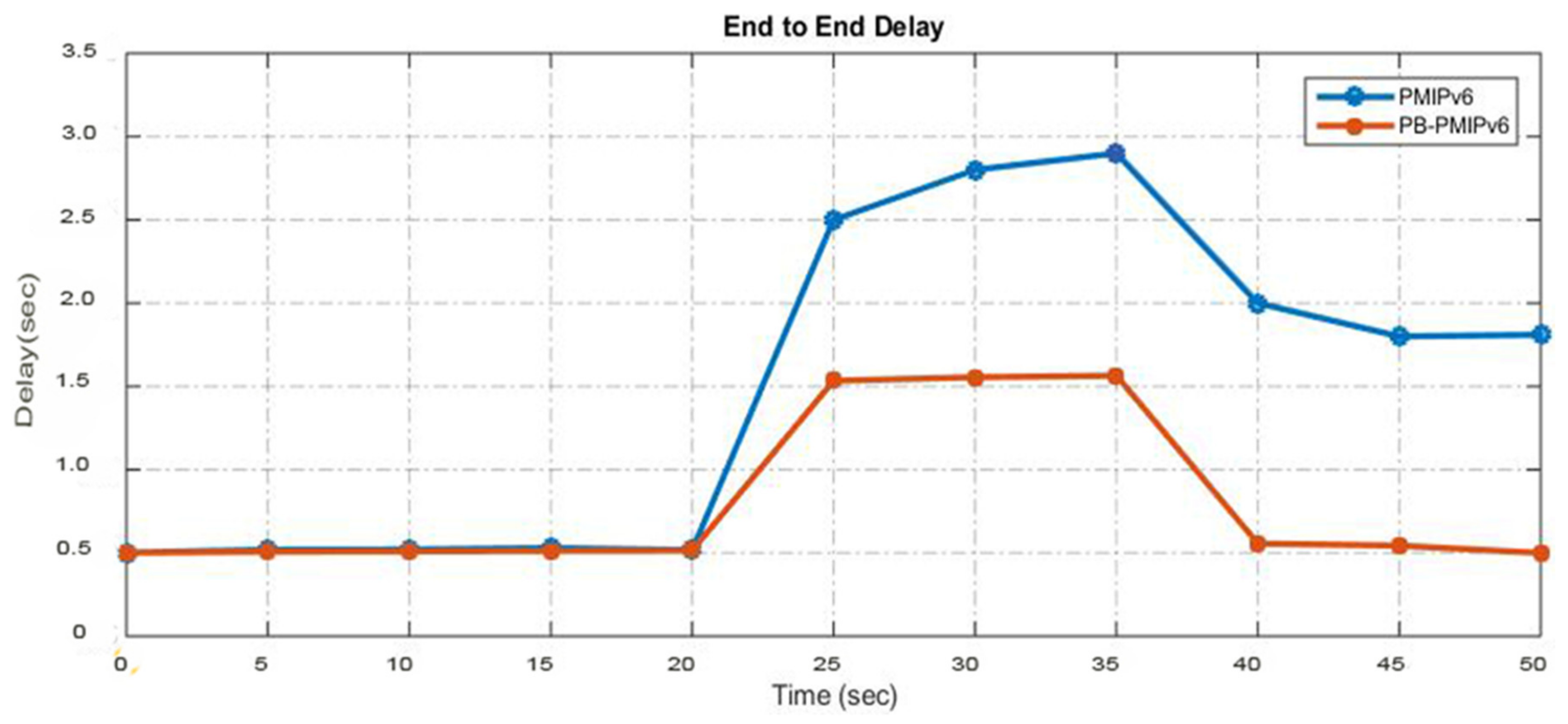
B senses the mobile node detachment and ensues the proxy binding update (PBU) functions, with a local mobility anchor to remove the binding state. This is further linked with the mobile node simultaneously, thereby, resulting in handover delay and packet loss. The research findings can be broadly divided into two phases. The first phase describes the implementation of existing CoAP IoT-based network mobility and the second phase is based on the implementation of partial bicasting with buffering for the IoT scheme. The proposed scheme is compared with the existing scheme by ns-3 simulations. We demonstrate that the proposed scheme could reduce handover delays, packet losses, end-to-end delay, throughput, and energy consumption, compared to the existing scheme.
2. Related Work
The requirement of faster “anywhere, anytime, and anyway” internet has been increasing due to the rapid increase in the number of mobile phone users and the development of portable communication devices, such as cellular phones, smartphones, laptops, and other modern technologies systems [
7]. With recent developments in wireless technologies, such as WCDMA and IEEE 802.16d, IETF, ITU-T, and third-generation partnership project (3GPP), the ubiquitous computing environments have been realized. However, achieving the goals of communication technologies is challenging. Compared to the regular internet, the general communication devices in IoT are turned into smarter devices and modern communication systems are turned into highly informative systems, as IoT possesses intelligent processing. However, IoT communication is through middleware and fundamental protocols [
11,
12]. Moreover, a functioning connection is important for IoT. The communication between the endpoints should be energy and time efficient. Therefore, IoT procedures must identify the best communication protocol and the CoAP is the principally employed protocol in IoT. CoAP is specified in RFC 7252 and is an open IETF standard compliant. This is a web transmission protocol used in either nodes or restricted networks, such as IoT, Wireless Sensor Network (WSN), etc. The protocol is designed for the resource-constrained IoT, which has lower memory and power consumption. CoAP is also referred to as the "web of things protocol" [
13], as it is designed for web applications. It can be used to transport data from a few to thousand bytes in web applications. Principally, CoAP is an efficient RESTful protocol for an integrated web app transfer (CoAP://). The methods used in CoAP are GET, POST, PUT, and DELETE [
14,
15]. CoAP uses a simple and small 4-byte header. For secure message transmission, CoAP employs certified protection protocols. Additionally, confirmable and non-confirmable messages are used for reliability. The port number used for secure CoAP is 5683 [
9]. The message queue telemetry transport (MQTT), an ISO standard method (IEC/ISO PRF 20922) reported in 1999, uses the publish-subscribe based message pattern. MQTT is considered for smaller M2M communications. Although MQTT was established by IBM, it is an open source package. MQTT uses Transmission Control Protocol (TCP) for message transport. The port numbers for MQTT are 1883 and 8883. MQTT works over TCP/IP and provides communication pattern flexibility. MQTT uses a topic-based publish-subscribe architecture [
16]. This architecture is based on three components:
Publishers: Publishers act as sensors in IoT and communicate with subscribers through brokers. Importantly, publishers can bring the system to sleep-mode, as needed;
Brokers: Brokers bridge between publishers and subscribers. The broker is responsible for the categorization of all the information collected from publishers. Further, the brokers transmit sensor data to the subscribers;
Subscribers: Subscribers are the application end-users, on whom brokers are interested when the publishers transfer new data to the broker [
17].
The secure MQTT (SMQTT) [
18] is the improved form of MQTT. Although all the characteristic features in this log work are similar to MQTT, additional security functionality was added to improve the properties of MQTT. This algorithm uses four parts: (a) Set-up, (b) encryption, (c) publication, and (d) decryption. The brokers communicate with subscribers and publishers and receive a passkey. The publishers will encrypt the data to be published. Subscribers receive broker information. Subscribers with the same passkey could, therefore, decrypt the data. Notably, the key generation algorithm is dynamic.
The advanced message queuing protocol (AMQP) is specifically used in the financial sector and works additionally as a MQTT protocol. This publish-subscribe model-based [
19] protocol employs a telecommunication protocol. The key components are (1) queues and (2) exchange.
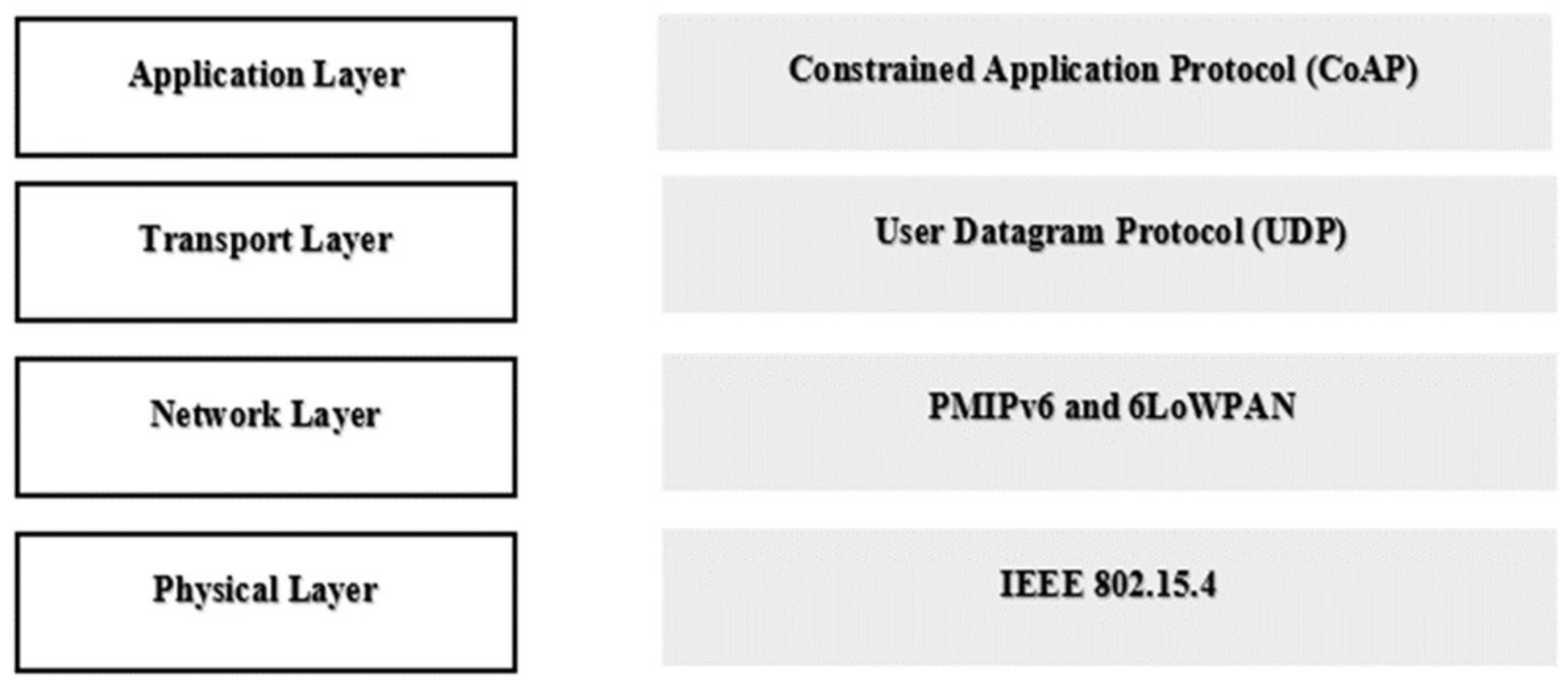
Furthermore, IoT interconnects physical gadgets and users for implementing specific tasks and sharing data. As IoT hosts separate protocols for communication at different levels and we employed similar protocols. We employed CoAP, as it is the best IoT protocol and employed UDP for the transport layer. As the signal sensors need to be attached on the patients’ body, we employed Proxy Mobile IPv6 (PMIPv6) for the network layer, and inserted 6LoWPAN into the network’s abstraction layer, which works in conjunction with PMIPv6. Recently, the IETF approved the CoAP as an open source package for investigating M2M and IoT interaction [
9]. Upon clients’ request on the server, CoAP employed four methods, PUT, POST, GET, and DELETE, which is similar to HTTP. However, unlike HTTP, CoAP employed UDP as a transport layer protocol to avoid message congestion and TCP-based extended resource requirement. Reliability was ensured through confirmation messages. The client might choose to acknowledge a message. CoAP is a simple and cost-effective protocol developed for low-end microcontrollers and high-bandwidth, high-error-burdened networks, such as 6LowPANs. Furthermore, CoAP is defined by the open standard IETF RFC 7252 and is the default protocol for UDP. Additionally, CoAP can be implemented in other channels, such as TCP or DTLS. The CoAP is based on the request-response communication model and includes support for resource identification, improved reliability, Uniform Resource Identifiers (URIs), etc. Although the protocol was originally developed for M2M, it has been adapted for gateway-supported IoTs, high-end servers, and business integration. Although CoAP behaves similarly to HTTP in the REST model, with GET, POST, PUT and DELETE commands, it should not be considered as compressed HTTP. For URI, response codes, MIME types, etc., CoAP, however, can easily be connected to HTTP proxy mechanisms, where HTTP clients can communicate with CoAP servers, enabling better web service integration whilst meeting IoT requirements.
The TCP server forwards information to the server and conveys the message to the subscribers, immediately. TCP also executes an error checksum. In UDP, the sender constantly sends information to the receiver, without ensuring its purposeful receipt. For example, live video streaming continues if the next packet is sent via UDP. Although the video transmission is blocked at the particular time, it will accurately resume within milliseconds.
PMIPv6, an IETF-designed network-based mobility management protocol, is defined in RFC 5213. PMIPv6 supports a proxy role for the network game operator for the mobile node in IP mobility reporting. The system’s mobility substances follow the mobility signal, the MN movement, and the configuration of the requested routing status. The most important functional units are the MAGs and LMAs. MAG carries out mobility management. The MAG exists on the access link where the mobile node is anchored. LMA maintains the reachability status of the mobile node and is the topological anchor of the IP address of the mobile node. The Cisco wireless LAN controller (WLC) implements the MAG feature. The key objective of this protocol is to provide mobility support for each IPv6 host within the localized and topologically limited network, without the host’s participation in mobility signaling. Significant PMIPv6 capabilities are supported for unmodified IPv4 and IPv6 MNs, which efficiently use wireless network resources, are independent interconnected technology, and improve crossover performance. A method was proposed to reduce transmission delays in CoAP [
11].
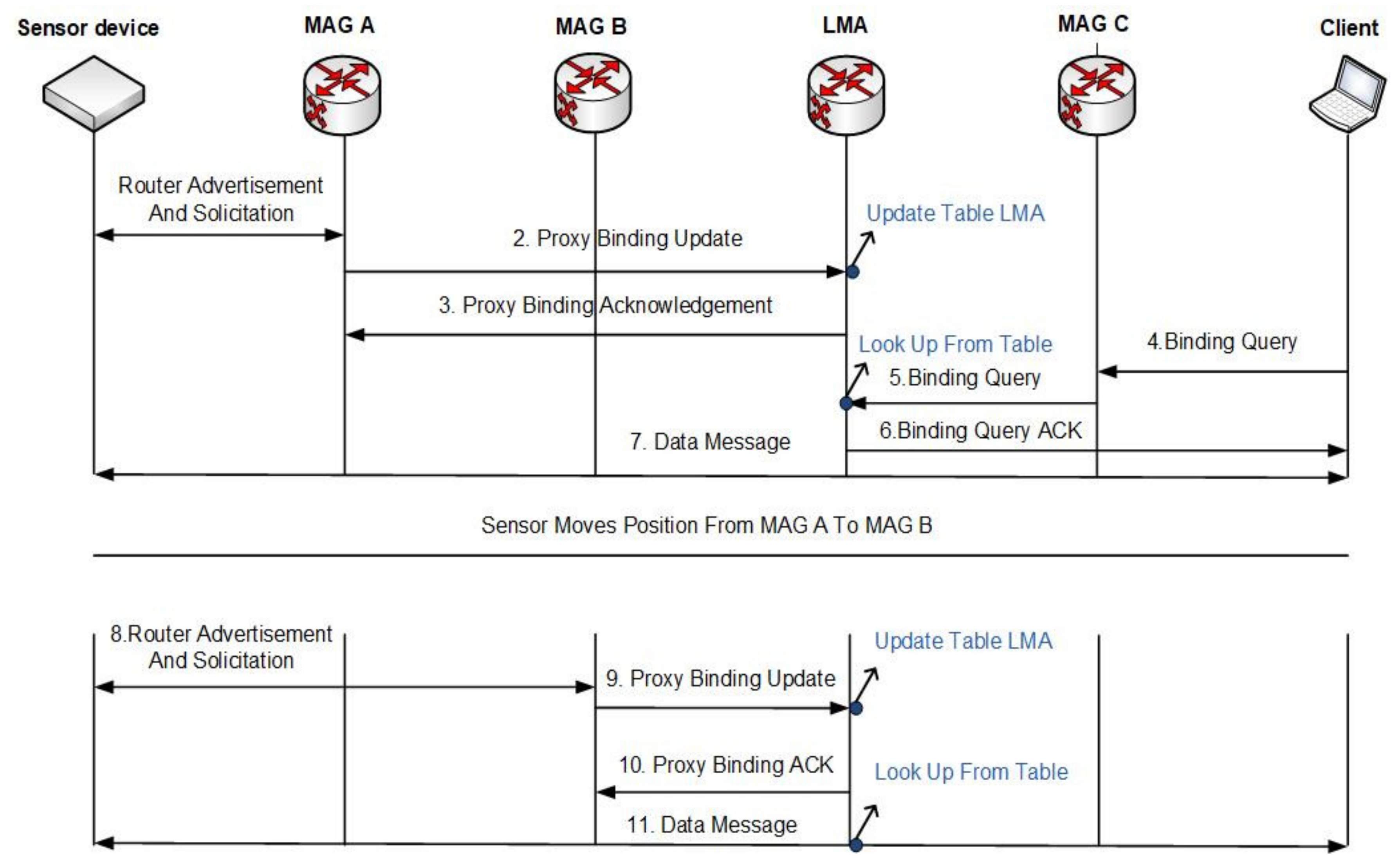
Figure 1 illustrates the “CoAP-PMIP” scheme [
11]. The sensor was connected to MAG
A, which sent the PBU to LMA. LMA registered the IP address of the sensor and sent a confirmation as a proxy binding acknowledgement (PBA) to MAG
A (Steps 1, 2, and 3). To convey a communication request, the client sent a binding query to MAG
C, and MAG
C sent the binding query to LMA. Since LMA bears the IP address and other sensor-specific values, it receives a binding query and PBA (Steps 4, 5, and 6). Therefore, to resume a new handover, the first sensor was connected to new MAG
B and its address updated in the LMA table, after handover. After the update, LMA sent the PBA to MAG
B (Steps 8, 9, and 10). Therefore, to communicate with the sensor, the client conveyed a binding acknowledgment query to the LMA with MAG
C. The LMA could communicate, as it contained a new sensor device value (Step 11).