Abstract
Wireless Sensor Networks (WSN) have experienced an important revitalization, particularly with the arrival of Internet of Things applications. In a general sense, a WSN can be composed of different classes of nodes, having different characteristics or requirements (heterogeneity). Duty-cycling is a popular technique used in WSN, that allows nodes to sleep and wake up periodically in order to save energy. We believe that the modeling and performance evaluation of heterogeneous WSN with priorities operating in duty-cycling, being of capital importance for their correct design and successful deployment, have not been sufficiently explored. The present work presents a performance evaluation study of a WSN with these features. For a scenario with two classes of nodes composing the network, each with a different channel access priority, an approximate analytical model is developed with a pair of two-dimensional discrete-time Markov chains. Note that the same modeling approach can be used to analyze networks with a larger number of classes. Performance parameters such as average packet delay, throughput and average energy consumption are obtained. Analytical results are validated by simulation, showing accurate results. Furthermore, a new procedure to determine the energy consumption of nodes is proposed that significantly improves the accuracy of previous proposals. We provide quantitative evidence showing that the energy consumption accuracy improvement can be up to two orders of magnitude.
1. Introduction
A Wireless Sensor Network (WSN) is a collection of nodes, considered energy-constrained devices as they are powered by batteries, that cooperatively perform data collection, processing and communication activities. Some areas of application for WSN are in medical, industrial, agricultural and environmental monitoring. The technological evolution of sensors promise to facilitate the integration of WSN with the Internet of Things (IoT) and, therefore, improve applications such as the distribution of intelligent services (smart grid, smart water), intelligent transport systems (ITS) and smart homes [1,2,3,4,5]. However, efficient energy deployment is a crucial issue in WSN. Among the operations performed by nodes, the medium access coordinated by the Medium Access Control (MAC) protocol, and the consequent data transmission, consume a significant amount of energy [6,7].
Some recent WSN MAC protocol developments employ duty-cycling (DC) to save energy and maximize the WSN lifetime. In WSN MAC protocols operating with DC, idle nodes stay in the sleep mode in order to save energy. Nodes wake up only during packet exchange periods. Medium access in WSN is based on contention deploying a Carrier Sense Multiple Access and Collision Avoidance (CSMA/CA) mechanism, and the Request-to-send/Clear-to-send/DATA/Acknowledgment (RTS/CTS/DATA/ACK) handshake [8,9]. S-MAC (Sensor-MAC) was the first WSN MAC protocol that implemented DC and remains one of the most popular [10].
A certain degree of heterogeneity is typically present in many WSN [11,12,13,14,15]. A common modeling approach for heterogeneous WSN is to define different classes of nodes, and with different traffic patterns [16]. In our study, in addition, different node classes have different channel access priorities. For example, WSN deployments in emergency scenarios, such as fires, earthquakes or some medical applications, require that nodes send data towards a control center as soon as events occur. Therefore, nodes sending emergency data need to have medium access priority over other network nodes.
The modeling and performance evaluation of heterogeneous WSN with priorities operating in DC, being of capital importance for their correct design and successful deployment, have not been sufficiently explored. Most MAC protocols that deploy CSMA/CA are analytically modeled using Markov chains. Models in [17,18] are based on a discrete-time Markov chain (DTMC), allowing the characterization of the evolution of the state of the network along time. These models are relatively simple and accurate enough, but they cannot be directly applied to the performance evaluation of synchronous MAC protocols that use DC.
In [19,20,21,22], we found recent examples of the application of DTMC to the modeling and performance evaluation of homogeneous WSN scenarios operating in DC without priorities. The models proposed in [19,20] assume that the state of nodes is mutually independent, even though there is a certain degree of dependency between them in practice [21]. All these models were designed considering homogeneous scenarios, where nodes behave in the same way in terms of load. Therefore, these models do not consider the possibility of different loads or different channel access priorities.
Markov-based models for heterogeneous scenarios were presented in [23,24]. In [23], different classes of nodes are considered, including the assignment of different packet arrival rates for each class, but all nodes have the same access priority. In [24], priority schemes, including different classes of nodes, are considered but without the possibility of different arrival rates or different number of nodes per class. Although these models evaluate heterogeneous scenarios for WSN, they cannot be directly applied to WSN using a DC mechanism.
In [25], a preliminary performance evaluation model for WSN operating in DC that supports multiple classes of nodes was presented. For each class, the model allows to independently configure access priority, number of nodes per class, and packet arrival rate to nodes of the class (load). For clarity, we will refer to the MAC protocol proposed in [25] as Priority Sink Access MAC (PSA-MAC).
Previous schemes for energy consumption computation were based on procedures that did not fully exploit the system stationary distribution. Different intermediate terms were defined that lead to a less intuitive, less systematic, and less accurate procedure for energy consumption computation. See, for example, [19,20,21,22,25]. However, in this paper, we propose a novel computation method that is simple and accurate, as discussed later.
There are two main contributions of this paper. First, the analytical modeling and performance evaluation of a WSN where nodes deploy a MAC protocol that uses CSMA/CA, a DC mechanism such as the one used in PSA-MAC, and support different loads and access priorities. For a scenario with two classes of nodes composing the network, each with a different access priority, an approximate analytical model is developed with a pair of two-dimensional DTMC (2D-DTMC). Note that the same modeling approach can be used to analyze networks with a larger number of classes, as described in Section 3.3. This model extends the capability of the models presented in [21] in order to allow the modeling of different classes of nodes with different access priority assignments in heterogeneous network scenarios.
Second, the proposal of a new method to determine the energy consumption of a node that is more intuitive and systematic than those considered before. In addition, this method substantially outperforms previous ones in terms of accuracy when results are compared with those obtained by simulation.
The rest of the article is organized as follows. In Section 2, the network scenario is presented, and the model assumptions are defined. The mathematical model of the system is presented in Section 3. The analysis to determine the performance parameters is developed in Section 4. The results and their discussion is presented in Section 5. Finally, the conclusions are presented in Section 6.
2. Network Scenario
2.1. PSA-MAC Protocol
As in most MAC protocols operating in DC, in PSA-MAC, the time is divided into cycles of equal duration T, and each cycle consists of an active and sleep period, as in Figure 1. The active period is subdivided in two parts: the sync period of fixed duration , where SYNC packets are exchanged; and the data period, where DATA packets are exchanged.
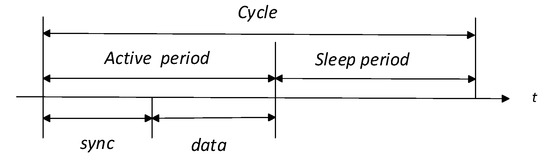
Figure 1.
An operation cycle with the active and sleep periods.
During a sync period, nodes choose a sleep–awake schedule and exchange it with their neighbors using SYNC packets. These packets include the transmitter node address and the start time of their next active period. With this information, nodes coordinate to wake up simultaneously at the beginning of each sync period. SYNC and DATA packets are transmitted using the CSMA/CA contention mechanism in order to access the channel. In CSMA/CA active nodes generate a random backoff time and perform a channel carrier sensing procedure. A node is considered active when it has packets to transmit. If the channel is idle when the backoff timer expires, then nodes transmit a packet using the RTS/CTS/DATA/ACK handshake. When a winning node receives a CTS in response to its previous RTS, it transmits the SYNC or DATA packet and waits for the ACK.
During the data period, nodes transmit DATA packets. Active nodes generate a new backoff time at each data period initiation and perform carrier sensing before accessing the channel. In PSA-MAC, during the data period a node goes to sleep mode until the beginning of the next sync or data period when: (i) it loses the contention (hears a busy medium before its backoff time expires); (ii) it encounters a RTS collision; (iii) after a successful transmission (only one packet per cycle is transmitted).
2.2. Network Operation and Assumptions
We consider a heterogeneous WSN with N nodes of different classes, where all nodes listen to each other and send packets to a common sink node, as, for example, in Figure 2.
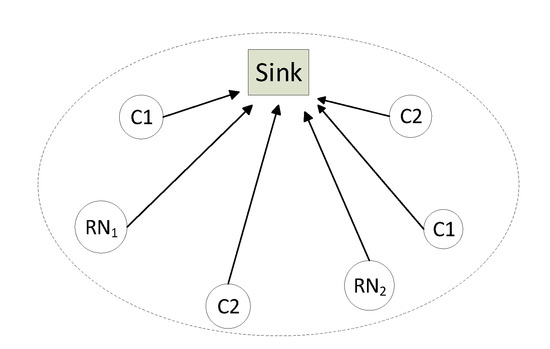
Figure 2.
Heterogeneous Wireless Sensor Network (WSN) with two classes of nodes. Class 1 nodes (C1) have channel access priority over class 2 nodes (C2). One reference node (RN) per class is defined.
The scenario consists of a single cell cluster, but multiple clusters together may configure a larger network. In this work, the scenario of a single cluster is studied. Two classes of nodes are considered, and we assume that class 1 nodes have medium access priority over class 2 nodes. Other assumptions considered in this study are: (i) the sink node only receives packets, never transmits; (ii) for realistic scenarios, it has been shown that one or two retransmissions are enough to transmit a packet successfully [21]. Then, for simplicity, we consider an infinite retransmissions model, as a simpler modeling alternative to the more complex model of finite retransmissions; (iii) from the MAC perspective, the channel is ideal (error-free); (iv) packets arrive to the buffer (queue) of a node following a renewal process, and the number of packets that arrive in each cycle is characterized by independent and identically distributed random variables.
In the evaluated scenario, as expected, the sink responds to each received data packet with the corresponding CTS and ACK. In some scenarios, the sink might also send data to nodes, either configuration or data packets. However, in most applications, the desired information is typically collected by the sensor nodes and aggregated at the sink before being forwarded upstream. For example, health monitoring applications [26]. As the load of configuration traffic, if present, should be typically small and sporadic, we have not included it in the model. Nevertheless, sink traffic can be included in the network, associating it to one or both of the two considered classes. For scenarios where the traffic offered by the sink to the nodes of a class is similar to the one offered by the rest of nodes of the same class (homogeneous load case), please refer to [21]. There, a single class is considered, the sink is considered as another class member node, and all class member nodes exchange packets among themselves.
The modeling approach can also be extended to scenarios with a non-ideal channel. For example, in [27], a DTMC model is proposed to investigate the impact of channel impairments on the performance of a single class WSN with no priorities, where the packet error probability depends on the packet length. The model in [27] can be readily adapted to a scenario with priorities as the one studied in this paper. Please refer to Section 3.3 for further details.
Each node has a finite buffer with a storage capacity of Q packets that are served according to a FIFO discipline. For simplicity, we assume that the number of packets arriving to a buffer per cycle follows a discrete Poisson distribution of mean , where is the packet arrival rate, and T is the cycle duration. However, the proposed analytical model is generic enough to support any other distribution. For class 1 nodes, the nodes with the highest channel access priority, we consider low traffic loads, since in realistic application, for instance, emergencies, the high priority information to transmit is small and sporadic. Nerveless, the proposed model supports any load for class 1 nodes.
2.3. Assignment of Medium Access Priorities
A way to prioritize the medium access for class 1 nodes over the class 2 nodes is to assure that class 1 devices complete the medium access procedure before class 2 devices. Figure 3 shows the medium access procedure for both classes along time, where the sync period for both classes of nodes has been omitted.
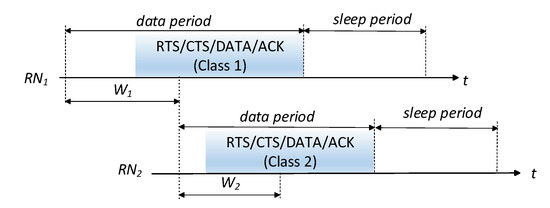
Figure 3.
Operation of the Medium Access Control (MAC) protocol for both classes of nodes.
In the proposed WSN operation, the medium access priority is granted to class 1 nodes by following the next access procedure. At the beginning of a cycle, only active class 1 nodes trigger the medium access and contend for medium access among themselves. Active class 2 nodes wake up just after the class 1 contention window () has ended, and if they detect an idle medium, they will proceed to transmit, activating their own contention mechanism. If class 2 nodes detect the medium occupied at that instant, they return to sleep mode and wake up again at the next cycle. We assume that the duration of a packet transmitted by a class 1 node is longer than .
3. System Model
The expressions developed in Section 3 and Section 4 are equally applicable to both classes of nodes. We use a generic notation to define the model parameters associated with any of the two node classes, unless otherwise specified. For description convenience, one node of each class is selected arbitrarily as reference node, and .
3.1. Access to the Medium
Active nodes generate random backoff times selected from the interval . When the RN is active, it transmits a packet successfully if the other contending nodes choose backoff times larger than the one chosen by the RN. The packet transmitted by the RN will collide (fail) when the RN and one or more of the other contending nodes choose the same backoff time, and this backoff time is the smallest of those generated in the current cycle. If the backoff time generated by the RN is not the smallest one, two outcomes are possible: (i) another node is able to transmit successfully; (ii) other nodes will collide when transmitting. Nodes that lose the contention (because they hear a busy medium before their backoff time expires), or find an RTS packet collision, go to sleep mode and remain in that mode until the active period of the next cycle.
For notation simplicity, N denotes the number of nodes of a given class. Considering a cycle where the RN is active, k denotes the number of nodes that are also active in the same cycle, besides the RN, .
Let , and , be the probabilities that the RN transmits a packet successfully, transmits a packet (successfully or with collision), and transmits with failure (collision), respectively, when the RN contends with other k nodes. Then,
Note that is the probability that the RN chooses a backoff value from the interval , and the other k nodes choose a larger value. Probabilities and can be described in similar terms.
Conditioned on a successful or unsuccessful packet transmission by the RN, when contending with other k nodes, the average backoff times are given by,
3.2. System with Two Classes and Priorities
In this subsection, we model the time evolution of the number of packets in the queue of and , and the number of active nodes in the network, by a pair of 2D-DTMC, one chain for each node class. The state of each node class is represented by the tuple , where i, , is the number of packets in the queue of the RN, and m, , is the number of active nodes of the corresponding class other than the RN.
Let be the transition probability from state to state . The first 2D-DTMC is adapted from [21], and is proposed to describe the time evolution of the state of class 1 nodes. The second 2D-DTMC is taken from [25] and is proposed to describe the time evolution of the state of class 2 nodes. For clarity and paper length limitations, the transition probabilities of both 2D-DTMC are presented in detail in [28].
Note that the representation of the network state is an approximation. For each class, the state of the set of nodes other than the RN is approximated using only the m parameter [21,22]. As it will be justified later, this approximation provides very accurate results.
3.3. Solution of the Pair of 2D-DTMC
The solution of each of these 2D-DTMC can be obtained by solving the following system of linear equations,
where is the stationary distribution, P is the transition probability matrix, the elements of which are defined in [28] (the referred technical report includes two tables: Table 1 for class 1 nodes, and Table 2 for class 2 nodes), and e is a column vector of ones.
The probability that the RN transmits a packet successfully in a random cycle, conditioned on the RN being active in that cycle, is given by,
As observed in [28], to determine the stationary distribution, is required, i.e., the stationary distribution is a function of , . By solving the set of Equation (6), can be determined for a given . Then, a new can be obtained from Equation (7). We follow a fixed-point iteration procedure and denote its solution by .
To determine the solution of the second 2D-DTMC, the solution of the first 2D-DTMC is required. In particular, one of the parameters of the second 2D-DTMC is the fraction of time (cycles) that the channel remains idle due to the inactivity of the high priority nodes (class 1 nodes), , where is the stationary distribution of the first 2D-DTMC.
For a system with a larger number of priorities, the solution of the stationary distribution of any priority class would previously require the solution of stationary distributions of all higher priority classes. Please refer to [28] for additional details.
4. Performance Parameters
In this section, we define different expressions to determine the throughput, average packet delay and average energy consumption per cycle. The following expressions are applicable to both classes of nodes.
4.1. Throughput
The node throughput is defined as the average number of packets successfully transmitted by a node in a cycle, and it is determined by,
In a network of N nodes, the aggregated throughput, , expressed in packets per cycle is obtained as,
4.2. Average Packet Delay
Let D be the average delay (in cycles) that a packet experiences from its arrival until its successful transmission. Then, D can be determined by applying Little’s law,
Note that is the stationary probability of finding i packets in the queue of the RN, and is the average number of packets in the RN queue.
4.3. New Improved Method to Determine the Average Energy Consumption
As observed in Figure 1, the active period of a cycle is subdivided into sync and data periods. The energy consumed during the active period represents the most significant contribution to the total energy consumption. In this section, we compute the average energy consumed by the RN in the data period. Note that only the energy consumed by the radio frequency transceiver is considered. The energy consumed by sensor nodes due to events related to specific sensing tasks is dependent on the specific application. Then, as it does not depend on the MAC, it is not included in this study.
Let , and , be the average energy consumption per cycle terms, when the RN transmits successfully, it transmits with failure (collision), and when it overhears other node transmissions, respectively. Then, the average energy consumed by the RN per cycle is given by,
is obtained as,
where , , and , are the transmission times for the RTS, DATA, CTS and ACK packets, respectively. and are the transmission and reception power levels, and is the one-way propagation delay. The term is determined by,
Finally, is obtained by,
where is the probability that two or more of the other k nodes differ from the RN chosen with the smallest backoff value and, therefore, smaller than the backoff value chosen by the RN. In this case, the RN will lose the contention, and the other two or more k nodes will transmit with collision.
In summary, an active RN overhears the channel when: (i) one of the other k nodes transmits successfully (with probability ); or (ii) two or more of the other k nodes collide (with probability ). Note that if the RN is not active, it will not listen to the channel, as we assume that the sink only receives and never transmits.
For class 2 nodes, the same expressions are applied to obtain the energy consumed during the active period . However, an additional term must be added to account for the energy consumed by class 2 nodes to sense the channel when they wake up but they sense a busy channel. We denote this term as , where is the duration of one time slot.
Let and be the average energy consumed by class 1 and class 2 nodes per cycle, respectively. The final expressions to determine the energy consumption for both classes of nodes are given by,
where is the stationary probability of finding no active class 1 nodes in a cycle (fraction of cycles where all class 1 nodes are inactive). As , we approximate .
The proposed model to determine the energy consumed by a node allows to accurately predict the lifetime of a node of any priority class in the network. When nodes start operating with different battery levels, as nodes deplete their batteries, they can be removed from the network, and then a new stationary distribution must be computed.
Performance Evaluation of the Improved Method to Determine Energy Consumption
The new procedure to determine the energy consumed by a node per cycle was described in Section 4.3. In this subsection, we highlight its advantage in terms of accuracy improvement, particularly for class 2 nodes, with respect to the energy consumption computation method proposed in [19,20,21,22,25].
As a summary, we will say that previous procedures required the computation of additional intermediate terms (see Section IV.C, from [25]), in addition to the stationary distribution . However, the new procedure described by Equations (14)–(20), only requires .
As an example, Table 1 shows the relative error of the energy consumption of class 2 nodes computed into two specific scenarios defined in Section 5. To highlight the difference with the previous computation method in [25], we have chosen two operating points where the worst accuracy is obtained. Note that relative values are obtained as , where x is the value obtained by the corresponding analytical computation procedure, and y is the value obtained by simulation.

Table 1.
Relative errors for the two energy computation methods.
As shown, on average, the new computation method considerably outperforms the previous one, by up to two orders of magnitude. In addition, it is more systematic and intuitive than the previous one, as it uses the stationary probability distribution more efficiently in the computation process.
5. Numerical Results
5.1. 2D-DTMC Model Validation
Results obtained from the proposed 2D-DTMC analytical model are validated by simulation. We have developed a discrete event simulator in C language that implements the physical transmission scheme and describes the time evolution of the sensor network state. At each cycle, each sensor receives packets according to a given discrete distribution. If a sensor has packets in its buffer, it contends with other nodes for channel access, and if it wins, it then transmits a DATA packet according to the described transmission scheme.
Simulation results are completely independent of those obtained by the analytical model. That is, the computation of the performance metrics by simulation does not use the system state representation, nor its stationary distribution, nor the mathematical expressions developed for the analytical model. The simulation results presented later are average values of measurements carried out along cycles. We have obtained confidence intervals with a 95% confidence level. However, as they are very small, for clarity they have been mostly omitted. For illustration purposes and as examples, confidence intervals are drawn for the top curves of Figure 4 and Figures 7–9.
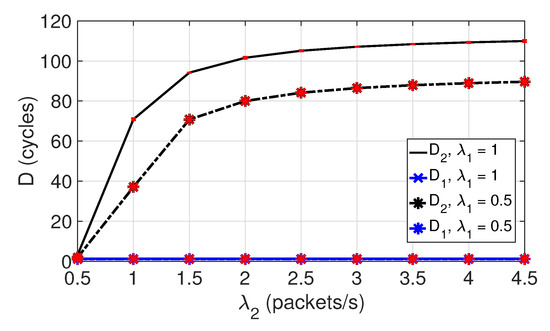
Figure 4.
Average packet delay for both classes in SC1.
In the following subsections, we show performance results obtained by the analytical model and by simulation. Simulation results are represented with red confidence intervals or red markers. Analytical results are represented with lines, or lines and markers. In many cases, the markers of analytical and simulation results totally overlap, and they are difficult to distinguish. In particular, red markers (simulation results) overlap and hide markers depicted with other colors (analytical results), which are the ones shown in the legends of the corresponding figures. As an example, in Figure 4, the average delay of the successfully transmitted packets is shown for both classes of nodes. Clearly, analytical and simulation results perfectly match, confirming that the analytical model is very accurate.
5.2. Scenarios and Parameter Configuration
In this section, the performance of a WSN, such as the one illustrated in Figure 2, is evaluated. We have considered two classes of nodes (1 and 2), with and populations. We have studied two scenarios (SC1 and SC2) with different configurations for each class of nodes, in terms of load and population. Configuration parameters are summarized in Table 2 [29]. The performance parameters of interest are: average packet delay, throughput and average energy consumption.

Table 2.
Parameter configuration.
For simplicity, in the evaluation scenario defined in this section, we have considered that nodes have sufficient energy so that the stationary regime is achieved before the battery of any node is depleted. When appropriately configured, the stationary regime is achieved after a small number of cycles. When nodes do not have the same initial energy, nodes that deplete their batteries stop operating, and, for modeling purposes, can be removed from the network. The proposed energy consumption procedure allows to predict with excellent accuracy the lifetime of a node with a given initial energy. Once the population of nodes of each class is readjusted, the model can be solved again until the next node stops operating.
5.3. Average Packet Delay
Figure 4 shows the average packet delay expressed in cycles, for both classes of nodes in SC1, and for two packet arrival rates for class 1 nodes ().
We denote by and the average delay of packets transmitted successfully by nodes of class 1 and class 2, respectively. Observe in Figure 4 that is constant for the load range studied, as class 1 packets have access priority, and and are both constant. In addition, it takes a very low value as we study realistic scenarios where class 1 nodes generate a small and sporadic load.
However, for nodes of class 2, the packet arrival rate takes values in the range . Note that the fraction of class 2 packets that collide increases with . As the number of retransmissions increase, also increases. Note also that as class 1 traffic load increases, class 2 nodes perceive the channel as busy for longer periods. Therefore, class 2 nodes take longer to transmit their packets, and their delay increases.
Note that does not increase when increases from 0.5 to 1 packets/s, as for both load values, the queues of class 1 nodes remain almost empty most of the time, i.e., nodes remain idle and access the channel rarely. Then, when a packet arrives, it is transmitted immediately, without neither delay nor collision.
Figure 5 shows the evolution of the average delay for class 2 nodes with in both scenarios, and with different values. Note that for SC1, , and for SC2, . Curves show that increases rapidly with , until approximately . For higher loads, increases slowly. As expected in SC2, where the number of nodes is larger, takes values higher than in SC1. When the number of nodes increases, contention also increases, and it takes longer to access the channel. Therefore, packets wait longer in the queue before being transmitted. In addition, more collisions and, hence, more retransmissions occur. Observe also that increases with . This can be explained in the same terms as those used to explain the results of Figure 4.
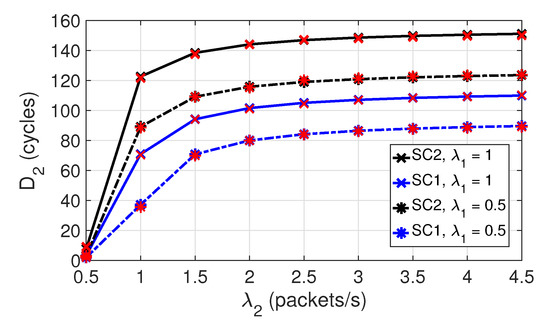
Figure 5.
Average packet delay for class 2 in SC1 and SC2.
Figure 6 shows the evolution of the average delay for class 2 nodes with with different contention window sizes in SC1. Results for Figure 6 (and Figure 10, shown later) have been obtained with the following configuration changes: and . Note that in our model, the priority assignment is not affected by the contention window size, as explained in Section 2.3. The changes for and do not modify the defined priority but influence the delay. has been chosen because being small, the collision probability does not significantly change for the larger values. Recall that the collision probability was defined in Equation (3). In addition, it has been observed that does not significantly change when .
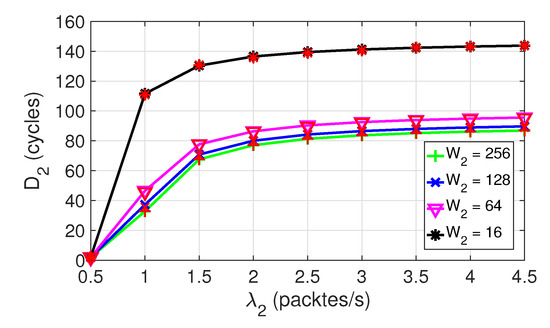
Figure 6.
Average packet delay for class 2 in SC1, , .
However, for class 2 nodes, there is a significant impact when the value of changes. The probability that two or more backoff timer values for class 2 nodes coincide increases as decreases. Figure 6 clearly shows the effect of in . For a fixed load, when increases, the probability of collision decreases and, therefore, decreases.
5.4. Throughput
Figure 7 shows the throughput per class 2 node for both scenarios. In both scenarios, reaches the saturation level for loads of approximately , observing a relatively constant behavior for higher loads. In addition, note that is higher in SC1 than in SC2. This is because in SC1 the number of nodes is smaller and, therefore, there is less channel contention.
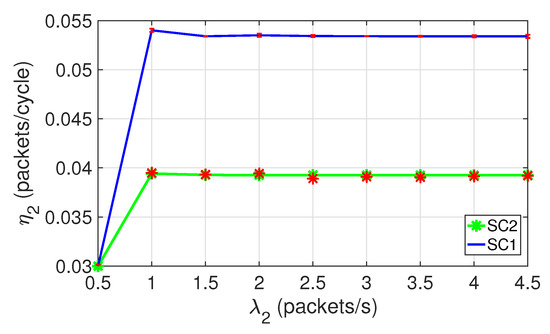
Figure 7.
Throughput per node for class 2. SC1 and SC2, .
Figure 8 shows the aggregated throughput for both classes of nodes as a function of . Results are obtained with the following general configuration changes: , . Observe that reaches a maximum for , and for higher values, it decreases gradually. Clearly, decreases because as increases, the contention increases, collisions increase, retransmissions increase, and the average packet delay increases. However, remains constant as is kept constant, and class 2 nodes have no influence on the perception that class 1 nodes have of the state of the channel.
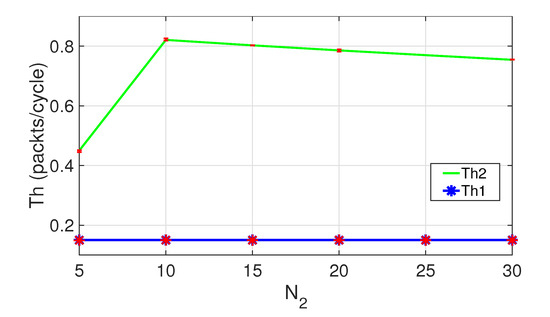
Figure 8.
Aggregated throughput for both classes. ,, .
5.5. Average Energy Consumption
Figure 9 shows the average energy consumption per node and per cycle for both classes of nodes, expressed in millijoules (mJ). Note that the energy consumption of class 2 nodes is higher in SC1 than in SC2. This scenario of higher energy consumption corresponds to the scenario where a higher throughput per node is achieved (Figure 7). Larger throughput values imply that more transmissions occur, leading to a higher activity of nodes and, therefore, to a greater energy consumption.
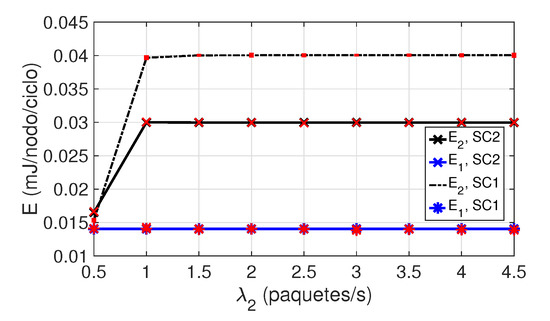
Figure 9.
Average energy consumption for both classes. SC1, SC2, .
Figure 9 also shows that is lower than , and constant with . This is due to the fact that class 1 nodes have priority over class 2 nodes. For class 2 nodes, the packet arrival rate takes values in the interval , and the number of nodes in the network is different for each scenario. Observe in Figure 9 an initial linear increase of the energy consumption for class 2 nodes in both scenarios. At approximately packets/s, the saturation load is reached and the activity of nodes, as well as their energy consumption, also reaches its limit.
Figure 10 shows the average energy consumption for class 2 nodes in SC1, when and . Note that increases with . As the contention window increases, the collision probability decreases, and increases. With larger window sizes, on average, the carrier sense mechanism remains active longer listening to the channel, the throughput of nodes increases and the energy consumption increases. On the other hand, if decreases, the energy consumption per node also decreases. However, when decreases, increases, as discussed in Figure 6.
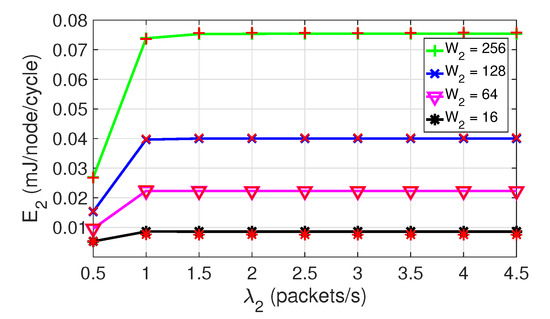
Figure 10.
Average energy consumption for class 2. SC1, , .
As an example, note that the proposed model can be used to appropriately set . As observed, might be a good compromise, as the energy consumption increases moderately when compared to (by a factor of two), and the delay is almost halved, as shown in Figure 6. However, by increasing beyond 64, the delay decreases only slightly, but the energy consumption drastically increases.
6. Conclusions
We have developed a novel approximate analytical model to evaluate the performance of a wireless sensor network that operates with a synchronous duty-cycle mechanism. The network is composed of different node classes with different traffic requirements and channel access priorities.
As an example, for a scenario with two classes of nodes, each with a different access priority, the analytical model is based on two two-dimensional DTMC, and it is solved for different scenarios. Multiple performance parameters are obtained such as the average packet delay, throughput and average energy consumption.
The model is quite flexible and can be extended to a number of different scenarios. For example, when more than two priorities are deployed, when the channel is error-prone, when the sink not only receives data packets but also transmits, or when the battery level of nodes is not equal.
A novel procedure has been proposed to determine the average energy consumed by the network nodes. Its most remarkable features are that it is simpler and more systematic than other alternative methods found in literature. In addition, results obtained with the new energy computation procedure are more accurate than those obtained by previous proposals. We provide evidence showing that the accuracy improvement can be between one and two orders of magnitude.
The results of the study show the impact that the incorporation of priorities has on the performance parameters. As expected, for two node classes, the performance of nodes with channel access priority is not affected by the low priority traffic load. In addition, for moderately low loads of high priority traffic, the delay obtained by the high priority packets is negligible. The obtained results confirm the suitability of the proposed model for the performance evaluation of WSN deployed in emergency scenarios.
Author Contributions
Conceptualization, C.P. and J.M.-B.; methodology, C.P. and J.M.B.; software, C.P. and J.M.-B.; validation, C.P.; formal analysis, C.P., J.M.-B., V.P. and V.C.-G.; investigation, C.P.; resources, J.M.-B., V.P. and V.C.-G.; writing—original draft preparation, C.P., J.M.-B.; supervision, J.M.-B., V.P. and V.C.-G.; funding acquisition, J.M.-B., V.P. and V.C.-G. All authors have read and agreed to the published version of the manuscript.
Funding
This work is part of the project PGC2018-094151-B-I00, which is financed by the Ministerio de Ciencia, Innovación y Universidades (MCIU), Agencia Estatal de Investigación (AEI) and Fondo Europeo de Desarrollo Regional (FEDER) (MCIU/AEI/FEDER.UE). C. Portillo acknowledges the funding received from the European Union under the program Erasmus Mundus Partnerships, project EuroinkaNet, GRANT AGREEMENT NUMBER - 2014 -0870/001/001, and the support received from SEP-SES (DSA/103.5/15/6629).
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| ACK | Acknowledgement |
| CSMA/CA | Carrier Sense Multiple Access/Collision Avoidance |
| CTS | Clear to Send |
| DC | Duty Cycling |
| DTMC | Discrete Time Markov Chain |
| FIFO | First in, First out |
| IoT | Internet of Things |
| ITS | Intelligent Transport System |
| MAC | Medium Access Control |
| RN | Reference Node |
| RTS | Request to Send |
| S-MAC | Sensor Medium Access Control |
| WSN | Wireless Sensor Networks |
| 2D-DTMC | two-Dimensional DTMC |
References
- Yinbiao, S.; Lee, K.; Lanctot, P.; Jianbin, F.; Hao, H.; Chow, B.; Desbenoit, J.P. Internet of things: Wireless sensor networks. In White Paper; International Electrotechnical Commission: Geneva, Switzerland, 2014. [Google Scholar]
- Gomes, D.A.; Bianchini, D. Interconnecting Wireless Sensor Networks with the Internet Using Web Services. IEEE Latinam. Trans. 2016, 14, 1937–1942. [Google Scholar] [CrossRef]
- Libo, Z.; Tian, H.; Chunyun, G. Wireless multimedia sensor network for rape disease detections. EURASIP J. Wirel. Commun. 2019, 2019, 159. [Google Scholar] [CrossRef]
- Shi, X.; An, X.; Zhao, Q.; Liu, H.; Xia, L.; Sun, X.; Guo, Y. State-of-the-Art Internet of Things in Protected Agriculture. Sensors 2019, 19, 1833. [Google Scholar] [CrossRef] [PubMed]
- Khalil, N.; Abid, M.R.; Benhaddou, D.; Gerndt, M. Wireless sensors networks for Internet of Things. In Proceedings of the 2014 IEEE Ninth International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), Singapore, 21–24 April 2014; pp. 1–6. [Google Scholar]
- Rajandekar, A.; Sikdar, B. A survey of MAC layer issues and protocols for machine-to-machine communications. IEEE Internet Things J. 2015, 2, 175–186. [Google Scholar] [CrossRef]
- Dai, H.N.; Ng, K.W.; Wu, M.Y. On busy-tone based MAC protocol for wireless networks with directional antennas. Wirel. Pers. Commun. 2013, 73, 611–636. [Google Scholar] [CrossRef]
- Ye, W.; Heidemann, J.; Estrin, D. An energy-efficient MAC protocol for wireless sensor networks. In Proceedings of the Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies, New York, NY, USA, 23–27 June 2002; Volume 3, pp. 1567–1576. [Google Scholar]
- Padilla, P.; Padilla, J.L.; Valenzuela-Valdés, J.F.; Serrán-González, J.V.; López-Gordo, M.A. Performance Analysis of Different Link Layer Protocols in Wireless Sensor Networks (WSN). Wirel. Pers. Commun. 2015, 84, 3075–3089. [Google Scholar] [CrossRef]
- Ye, W.; Heidemann, J.; Estrin, D. Medium access control with coordinated adaptive sleeping for wireless sensor networks. IEEE/ACM Trans. Netw. 2004, 12, 493–506. [Google Scholar] [CrossRef]
- Yarvis, M.; Kushalnagar, N.; Singh, H.; Rangarajan, A.; Liu, Y.; Singh, S. Exploiting heterogeneity in sensor networks. In Proceedings of the IEEE 24th Annual Joint Conference of the IEEE Computer and Communications Societies, Miami, FL, USA, 13–17 March 2005; Volume 2, pp. 878–890. [Google Scholar]
- Yıldırım, G.; Tatar, Y. On WSN heterogeneity in IoT and CPSs. In Proceedings of the 2017 International Conference on Computer Science and Engineering (UBMK), Antalya, Turkey, 5–7 October 2017; pp. 1020–1024. [Google Scholar]
- Alam, M.; Kim, Y.C. Efficient MAC Protocol for Hybrid Wireless Network with Heterogeneous Sensor Nodes. J. Sens. 2016, 2016, 7951965. [Google Scholar] [CrossRef]
- Kuo, Y.W.; Li, C.L.; Jhang, J.H.; Lin, S. Design of a wireless sensor network-based IoT platform for wide area and heterogeneous applications. IEEE Sens. J. 2018, 18, 5187–5197. [Google Scholar] [CrossRef]
- He, X.; Liu, S.; Yang, G.; Xiong, N. Achieving Efficient Data Collection in Heterogeneous Sensing WSNs. IEEE Access 2018, 6, 63187–63199. [Google Scholar] [CrossRef]
- Ortín, J.; Cesana, M.; Redondi, A.E.; Canales, M.; Gállego, J.R. Analysis of unslotted IEEE 802.15.4 networks with heterogeneous traffic classes. IEEE Wirel. Commun. Lett. 2019, 8, 380–383. [Google Scholar] [CrossRef]
- Bianchi, G. Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun 2000, 18, 535–547. [Google Scholar] [CrossRef]
- Liu, R.P.; Sutton, G.J.; Collings, I.B. A new queueing model for QoS analysis of IEEE 802.11 DCF with finite buffer and load. IEEE Trans. Wirel. Commun. 2010, 9, 2664–2675. [Google Scholar] [CrossRef]
- Yang, O.; Heinzelman, W. Modeling and throughput analysis for SMAC with a finite queue capacity. In Proceedings of the 2009 International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), Melbourne, Australia, 7–10 December 2009; pp. 409–414. [Google Scholar]
- Yang, O.; Heinzelman, W. Modeling and performance analysis for duty-cycled MAC protocols with applications to S-MAC and X-MAC. IEEE Trans. Mob. Comput. 2012, 11, 905–921. [Google Scholar] [CrossRef]
- Martinez-Bauset, J.; Guntupalli, L.; Li, F.Y. Performance analysis of synchronous duty-cycled MAC protocols. IEEE Wirel. Commun. Lett. 2015, 4, 469–472. [Google Scholar] [CrossRef]
- Guntupalli, L.; Martinez-Bauset, J.; Li, F.Y.; Weitnauer, M.A. Aggregated packet transmission in duty-cycled WSNs: Modeling and performance evaluation. IEEE Trans. Veh. Technol. 2016, 66, 563–579. [Google Scholar] [CrossRef]
- Lv, C.; Zhu, J. A new analysis model for IEEE 802.15.4 MAC with heterogeneous unsaturated conditions. In Proceedings of the 2012 International Conference on Measurement, Information and Control, Harbin, China, 18–20 May 2012; Volume 1, pp. 92–97. [Google Scholar]
- Kim, M. Performance analysis of service differentiation for IEEE 802.15.4 slotted CSMA/CA. In Proceedings of the 9th Asia-Pacific Network Operations and Management Symposium (APNOMS 2006), Busan, Korea, 27–29 September 2006; pp. 11–22. [Google Scholar]
- Portillo, C.; Martinez-Bauset, J.; Pla, V. Modelling of S-MAC for Heterogeneous WSN. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–6. [Google Scholar]
- Zhang, R.; Moungla, H.; Yu, J.; Mehaoua, A. Medium access for concurrent traffic in wireless body area networks: Protocol design and analysis. IEEE Trans. Veh. Technol. 2016, 66, 2586–2599. [Google Scholar] [CrossRef]
- Guntupalli, L.; Martinez-Bauset, J.; Li, F.Y. Performance of frame transmissions and event-triggered sleeping in duty-cycled WSNs with error-prone wireless links. Comput. Netw. 2018, 134, 215–227. [Google Scholar] [CrossRef]
- Portillo, C.; Martinez-Bauset, J.; Casares-Giner, V.; Pla, V. (July, 2019). The State Transition Probabilities of the Two 2D-DTMC. Technical Report. Available online: http://personales.upv.es/jmartine/public/2DDTMC.pdf (accessed on 1 December 2019).
- MICA Data Sheet. Crossbow Technology Incorporated, San Jose, CA, USA. Available online: http://www.openautomation.net/uploadsproductos/micaz-datasheet.pdf (accessed on 19 January 2020).
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).