1. Introduction
The increasing requirements for telecommunication systems have led to the research of Multiple-Input, Multiple-Output (MIMO) techniques, due to their large capacity gains over traditional single antenna system techniques [
1]. In fact, these techniques have already been employed in recent standards, such as Wi-Fi [
2] and LTE [
3], and will be integrated in 5G systems [
4].
In traditional Orthogonal Multiple Access (OMA) systems, radio resources are allocated to users in an orthogonal fashion (OFDMA, orthogonal CDMA, etc.), that is the uncoded messages meant for different users are never superimposed in the time and frequency domains. These systems, ideally, have no inter-user interference and require no additional processing for separating user’s at the receiver. However, due to new demands to further increase spectrum efficiency, Non-Orthogonal Multiple Access (NOMA) schemes are quickly surging as solutions due to their higher spectrum efficiency [
5,
6], even for mmWave systems [
7]. In a NOMA scheme, two or more users’ messages are superimposed in the time and frequency domains, and user separation can be made in the power domain, leading to the so-called power domain NOMA [
8]. It is also possible to allocate users among clusters [
9]; however, in this work, we assume only two users, which can be approximated as a single cluster scenario [
10]. The detection of the different users usually resorts to Successive Interference Cancellation (SIC) techniques.
Although there is a great benefit in adopting NOMA schemes, the security requirements are higher than the ones of traditional OMA schemes. This is explained by the fact that, when performing the SIC process, a user may decode messages meant for other users. Therefore, NOMA schemes can greatly benefit from Physical Layer Security (PLS) schemes [
11,
12,
13,
14], which can be combined with upper layer security techniques to ensure the confidentiality of a user’s message [
15].
For this purpose, we chose to analyze the PLS characteristics of a Single Carrier (SC) NOMA-MIMO system employing Frequency Domain Equalization (FDE). Although there are many published works on PLS techniques, most of them focus on Orthogonal Frequency Division Multiplexing (OFDM) [
16], and few are dedicated to SC systems. In [
17], an SC system is analyzed, however, it does not consider a NOMA scenario, which poses additional security concerns. As is widely known, SC-FDE systems are appealing due to their lower Peak-to-Average Power Ratio (PAPR) when compared to multicarrier schemes. Moreover, when combined with non-linear iterative equalization techniques to mitigate Inter-Symbol Interference (ISI), such as Iterative Block-Decision Feedback Equalization (IB-DFE), they can achieve excellent performance, making this technique appealing for applications where there are strict energy efficiency requirements, as well as highly frequency selective channels. The security potential can be analyzed under various scenarios, such as in [
18], where a friendly jammer and an eavesdropper were considered, or in [
19], where a jammer and an eavesdropper worked together in an attempt to eavesdrop the system, or even through the use of artificial noise sequences at the transmitter [
20]. This makes a direct comparison between these scenarios a challenging task. As such, in this work, we consider a simpler scenario with two independent eavesdroppers, which attempt to eavesdrop two different users.
In this work, we consider a novel Singular Value Decomposition (SVD) technique for separating user streams in MIMO-NOMA SC-FDE systems. More concretely, we analyze the security potential of this scheme in a scenario with an eavesdropper located near each user. Even in LOS scenarios, it is shown that the secrecy rate of the MIMO-NOMA system can be kept high if the multipath component’s power is relatively high.
This paper is organized as follows: In
Section 2, we characterize the MIMO-NOMA system with its intended receivers, B and C, and eavesdropper E, with varying positions and targets.
Section 3 concerns the system capacity and presents secrecy rate calculations.
Section 4 shows the simulated Bit Error Rate (BER) and secrecy rate for all transmitter-receiver sets. Lastly,
Section 5 concludes this paper.
2. Materials and Methods
2.1. System Characterization
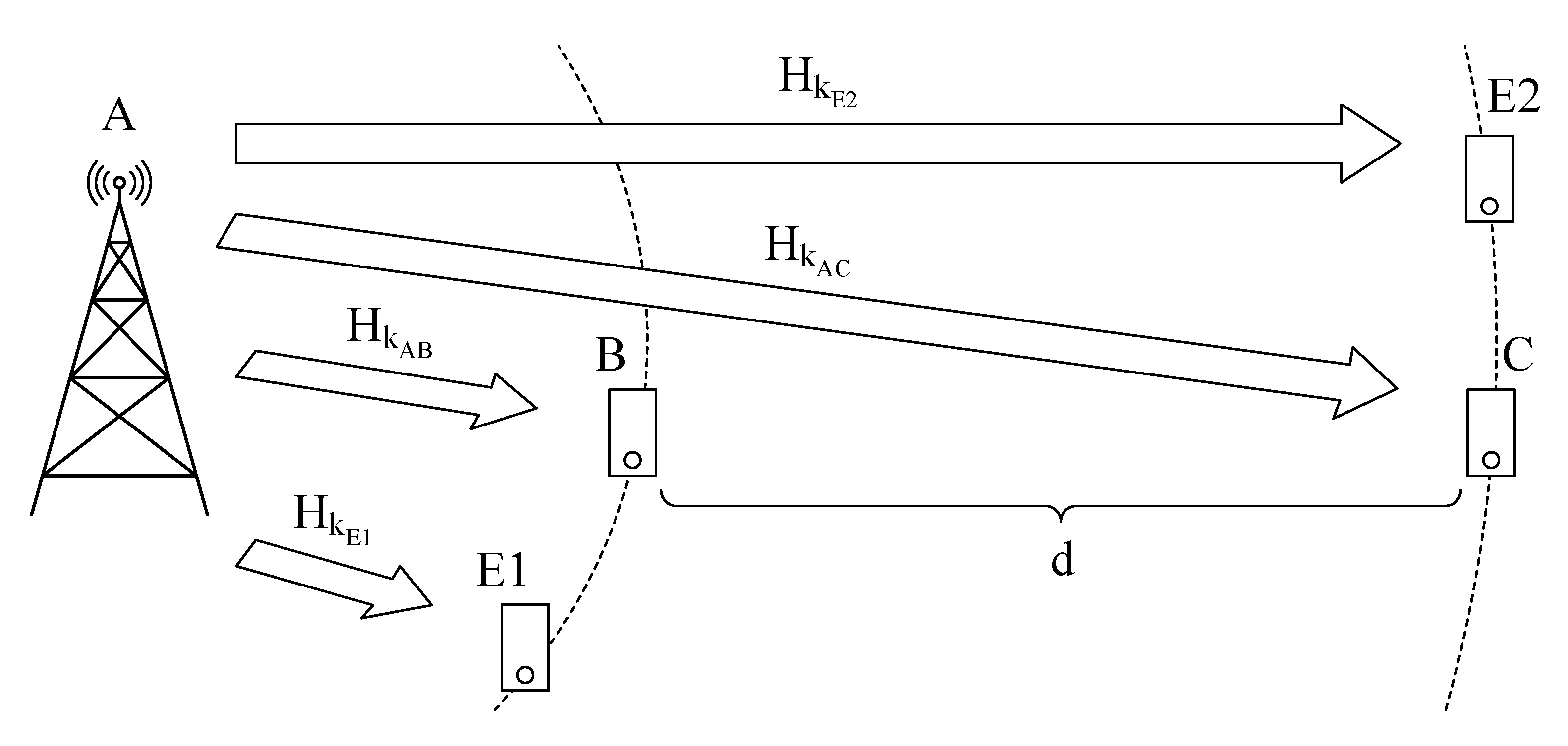
In this paper, we consider a three user system, where one user, the transmitter A, attempts to communicate with the other two users, receivers B and C. The receivers are separated by a large distance,
d, with one receiver, B, being close to the transmitter, while C is placed far from the transmitter. The transmitter employs a power based NOMA scheme and transmits both users’ signals at the same time. In addition, there is an eavesdropper near each user, attempting to listen to the messages being transmitted. A diagram summarizing this scenario can be seen in
Figure 1. Although the transmitter’s position may vary, it is assumed that the distance to all other users is always much greater than the wavelength of the transmitted signal. The transmitter employs
T antennas, while the receivers and eavesdropper employ
R antennas. In order to handle the highly frequency selective channel, we employ an SC-FDE technique, combined with an appropriate Cyclic Prefix (CP) larger than the maximum overall channel impulse response.
The transmitter sends
C data blocks, with
, and each data block is composed by the sum of two blocks of
N Quadrature Phase Shift Keying (QPSK) symbols with differing power (the generalization to other constellations is straightforward [
21]). Contrary to the single user system studied in [
17], fir the power domain NOMA scenario of this work, we must define the symbols to be transmitted to both users. The data symbols transmitted for user B are denoted by the
matrix
, with each data stream defined as an
vector
. In that context,
represents the QPSK symbol at the
time instant of the
data stream. The frequency domain counterpart of the data to be transmitted is denoted by
. The group of symbols associated with the
subcarrier are defined as
. The symbols for User C are defined identically to the symbols for User B and denoted by
,
,
, and
, respectively. Under these conditions, the transmitted data at
time instant are defined as:
with a frequency domain counterpart defined as:
Since we are considering two receivers that are not co-located, we can define two channels, one from A to B and another from A to C. The frequency response for the
subcarrier of the channel from A to B is defined as:
and the frequency response for the
subcarrier of the channel from A to C is defined as:
In any MIMO system, the different channels must be separated, so as to avoid cross-channel interference. In this work, we employ a technique that combines precoding and decoding, which is based on the SVD in [
22]. Calculating the SVD of the channel matrix requires Channel State Information (CSI) at both receivers and at the transmitter. This CSI can be obtained through the exchange of pilot sequences at the start of the transmission. In a Time Division Duplexing (TDD) system, this process is greatly simplified due to the reciprocity of the channel.
The SVD of each channel matrix is defined as:
and:
For simplicity’s sake, we omit the channel identifier (i.e., AB or AC) when we are referring to any channel. We denote as the decoding matrix, as the precoding matrix, and as an diagonal matrix composed by the singular values of , which are sorted in descending order according to their power.
2.2. Transmission
In a power domain NOMA scheme, the data meant for each user are sent at the same time and over the same channel, with differing transmitting power. In this work, we define the ratio between the power of and as .
It is widely known that the performance of a given stream in an SVD system depends on the singular value power of that stream. A simple scheme for averaging the performance of all streams was proposed in [
23], which consisted of interleaving the data symbols before applying the precoding technique. The interleaving scheme can be different for each user, as it only affects the data symbols. Therefore, we define the interleaved symbols for Users B and C as
and
, respectively.
Before transmitting data, there is an initial training sequence exchange between all users, so as to obtain the channel matrices with which to compute the SVD. The exchange begins with the farthest user, C, sending a training sequence meant for the transmitter, which is ignored by B. In the next step, B sends a training sequence meant for the transmitter as well. Lastly, the transmitter sends a training sequence, followed by the precoded data to all users. In all steps, there is an eavesdropper that listens to all of the exchanged sequences and computes its own channel estimates.
As described in [
24], the channel matrices associated with the
subcarrier can be defined as:
and:
where
and
are the channel estimates used by the transmitter,
and
are correlation factors with the true channels, and
is the error associated with the channel estimation process (our analysis can be easily extended to other models for the channel estimation errors). This error
is characterized as a complex variable with a Gaussian distribution and variance
, where
is the noise variance for a specific Signal-to-Noise Ratio (SNR) value and
is a scaling factor. For
and
, there is a perfect channel estimation, i.e.,
and
. We define the SVD of the channel estimates as:
and:
Using the result of SVD, the transmitter performs the precoding operation defined as:
where
is the signal to be transmitted and
is the ratio between the power transmitted meant for User C and the power transmitted meant for User B. Since the precoding operation only utilizes the channel estimate of the close user, additional information must be sent to allow the far user to complete the SVD process. The transmitter sends a partial key
, which is defined as:
Since
is a unitary matrix, then for the case of a system with
, this matrix can be written as:
where
a and
b are complex coefficients such that
, and the determinant of this matrix is given by:
Under this decomposition, the transmitter must send four parameters that allow for the reconstruction of the original matrix. These parameters are , , , and , which are all real valued quantities that can be quantized with a low resolution, so as to reduce the overhead associated with the transmission of the partial key.
2.3. Reception
The received signal at User B can be defined as:
while the received signal at User C is defined as:
Before decoding the symbols, both receivers employ the Iterative Block-Decision Feedback Equalization (IB-DFE) technique [
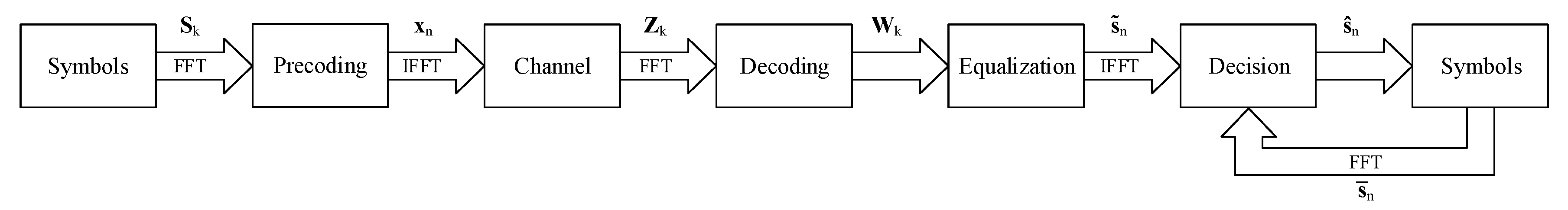
25] with soft decisions. This technique utilizes feedback from the soft decided symbols to improve the equalization and mitigate the intersymbol interference in frequency selective channels.
Figure 2 shows a simplified diagram of this system. However, it should be noted that this 2userscheme must be slightly changed for our power domain NOMA scenario, mainly due to the SIC and partial key requirements at each receiver.
2.4. Receiver B
As described earlier, User B also computes a channel estimation, with the training sequence transmitted by A. We can express the channel as:
where
is a correlation factor with the true channel. It is not unreasonable to assume that there is a high correlation between the estimate of the receiver B and the transmitter; therefore, we can assume
. For simplicity, we assume that the error distribution of the channel estimate is the same for both A and B, though the generalization to other cases is straightforward. The SVD of the channel estimate at User B is written as:
with
,
, and
being the corresponding estimates of the matrices defined in (
5).
As in conventional SVD techniques, the decoding is performed by multiplying the signal by the decoding matrix
, which is computed as:
where
is a
column vector with the interleaved, decoded symbols. This operation can be expanded as:
with
corresponding to an estimate of the diagonal matrix composed by the singular values of the channel. Before performing equalization, however, the receiver must perform deinterleaving, to restore the original symbol order, yielding:
After the deinterleaving, each stream is affected by a frequency selective channel made up of the different singular values.
Before User B can detect its intended symbols, it must perform the SIC reception on the symbols intended for User C. In order to do so, it first performs detection on the stronger signal, which has a much higher Signal-to-Noise Ratio (SNR) than the wanted signal, making the detection simple.
The equalized signal is obtained by computing:
where the equalization factor
is defined according to Minimum Mean Squared Error (MMSE) criterion as:
Subsequently, the receiver computes hard decisions of the transmitted symbols as:
with
being a hard decided estimate of the transmitted symbols meant for User C. Using this estimate, the receiver can perform detection on the intended symbols.
In the scenario where there is a nearby eavesdropper, E, attempting to listen to the message being sent to B, then it must attempt to estimate the channel between A and B. Since an eavesdropper cannot attempt to estimate this channel, it estimates two different channels, defined as:
and:
where
is the channel between A and E,
is the channel between B and E,
and
are correlation coefficients with the true channels, and
is an appropriate Gaussian distributed error term with variance
, where
is a scaling factor. Since the eavesdropper does not know the channel, we can assume that
. For simplicity’s sake, we assume that
. In order to increase the accuracy of the channel estimate, the receiver can compute the average of both intermediate channels, i.e.,
Iterative Equalization
To reduce the ISI, the receiver and eavesdropper employ an iterative frequency domain equalization scheme based on the IB-DFE [
25] and MMSE criterion, which performs both feedforward and feedback equalization at a subcarrier level. This equalization process can be repeated up to
L times, which we fixed at
for this work.
The equalized symbols at the
subcarrier and
iteration are computed by:
where
is the feedforward factor,
is the feedback factor, and
are the soft decided symbols of the previous iteration (for
, this is simply a null vector). The feedforward factor matrix is defined as:
where
denotes the block-wise reliability associated with the data estimated in the
iteration (when
, we have
). The feedback factor matrix, on the other hand, is defined as:
2.5. Receiver C
The detection at User C is significantly different from the detection scheme employed in [
17]. This is explained by the modifications required for the interleaving scheme and by the use of a partial key. As described earlier, User C also computes a channel estimation, with the training sequence transmitted by A. We can express the channel as:
where
is a correlation factor with the true channel. It is not unreasonable to assume that there is a high correlation between the estimate of the receiver C and the transmitter; therefore, we can assume
. For simplicity, we assume that the error distribution of the channel estimate is the same for both A and C, though the generalization to other cases is straightforward. The SVD of the channel estimate at User C is written as:
with
,
and
being the corresponding estimates of the matrices defined in (
6).
As in conventional SVD techniques, the decoding is performed by multiplying the signal by the decoding matrix
, which is computed as:
where
is a
column vector with the interleaved, decoded symbols. This operation can be expanded as:
with
corresponding to an estimate of the diagonal matrix composed by the singular values of the channel. The received signal is then deinterleaved, so as to split the singular values amongst the streams, yielding:
As was the case with Receiver B, this receiver performs the same iterative equalization, with the exception that it does not need to perform an initial first detection. The equalization is defined as:
where
is the equalized received signal at the
subcarrier and
iteration and
is the equalized signal estimate of the previous iteration (for
, it is set to 0). However, unlike Receiver B, this receiver cannot complete the SVD on its own. Therefore, it makes use of the partial key
, which is computed from the received parameters as:
where
,
,
, and
are the finite resolution quantized values transmitted by A and
is obtained from
. Prior to applying the partial key, the equalized signal is interleaved, in order to match the SVD matrices. The equalized symbols estimates are expressed as:
which are then deinterleaved into the equalized symbol estimates
.
In the scenario where there is a nearby eavesdropper, E, attempting to listen to the message being sent to C, then it must attempt to estimate the channel between A and C. Since an eavesdropper cannot attempt to estimate this channel, it estimates two different channels, defined as:
and:
where
is the channel between A and E,
is the channel between B and E, and
and
are correlation coefficients with the true channels. Since the eavesdropper does not know the channel, we can assume that
. Once again, for simplicity’s sake, we assume that
. In order to increase the accuracy of the channel estimate, the receiver can compute the average of both intermediate channels, i.e.,
2.6. Line-of-Sight Link Scenario
An additional scenario where there is LOS between the transmitter and all other users can be considered. In these conditions, the channel is defined as the sum of an LOS component (without fading effects) and several multipath rays (which are uncorrelated and have fading). In the worst case scenario, the eavesdropper can estimate the LOS component, albeit with a certain error; however, that is not feasible for the remaining multipath rays [
26]. In this case, we define the channels as:
and:
where
and
are the low fading, highly correlated LOS components and
and
are the high fading multipath components of the respective channels. We then substitute these channels in (
7), (
8), (
17), and (
31) as:
The receivers’ and transmitter’s remaining operations are calculated as described previously.
The eavesdropper, however, cannot estimate the multipath component of the channel and must instead rely on the estimate of the LOS component. We define this component for the eavesdropper estimating the closest user as:
where:
and:
Likewise, the component for the eavesdropper estimating the farthest user is defined as:
where:
and:
In this scenario, the channel estimates
and
, likewise with the channel estimates
and
, only concern the LOS component between A and E and B and E or between A and E, and A and C, respectively. The difference between these estimates and the real channels will be proportional to the power of the multipath component. We define the ray power coefficient for both scenarios as:
where
and
are the powers of the LOS and multipath components, respectively. Clearly, if
, the channel is only composed by the LOS component, whereas at
, the channel is composed of only the multipath component.
2.7. Decision Feedback
The definitions in this section, unless otherwise stated, apply to all receivers. As is known, employing soft decisions in the feedback equalization greatly reduces the level of ISI. These soft decisions can be calculated through the log likelihood ratios (LLR) of the equalized signal, obtained by:
and:
where:
After obtaining the LLR for each bit, we can calculate the soft decision of a given data symbol as:
The estimated data symbols are obtained through the hard decision of the equalized symbols. For Receiver C, there is an additional step, which consists of, once again, interleaving the soft decided symbols and multiplying by the Hermitian of the partial key matrix, written as:
The resulting matrix is then deinterleaved and applied in (
36).
3. Secrecy Rate
To measure the security potential of this system, we utilize a figure of merit referred to as the secrecy rate [
27]. The secrecy rate is expressed as the difference between the capacity of the proper channel, from A to B or A to C, and the eavesdropper channel, from A to E. For simplicity’s sake, we use
and
as placeholders for the signals in either receiver. The total capacity of the system is defined as the sum of the capacity of each sub-carrier, i.e.,
where
denotes the capacity of a single sub-carrier, defined according to [
28]:
where
is the mutual information between the transmitted signal and the received signal, which can be computed as:
where
is the
singular value of the corresponding channel.
Let us divide the analysis into two parts, the first being the proper transmitter/receiver pair, while the second is the transmitter/eavesdropper pair. For the scenario with A and B, we define the capacity as:
where
and
are the variances of
and
, respectively, and
is the power of the interference associated with the imperfect channel estimation, given by:
with
denoting a matrix comprised of the interference in the receiver, which can be computed as:
Likewise, the capacity of the system with the link from A to C is given by:
where
is the power of the interference associated with the imperfect channel estimation, given by:
with
denoting a matrix comprised of the interference in the receiver, which can be computed as:
Similarly, we can define the capacity of the eavesdropper as:
where
is a simplification defined as
and
is the interference power due to the imperfect channel estimation, which is larger than
, and is computed as:
Likewise,
is the interference matrix computed as:
With (
63) and (
69), we are able to obtain the total capacity by using (
60). Moreover, we are also able to compute the secrecy rate, defined by the difference between the intended receiver’s capacity and the eavesdropper’s capacity, i.e., for the link between and A and B, we have:
while for the link between A and C, we have:
4. Results and Discussion
This system was simulated under a variety of conditions utilizing Monte Carlo simulations. The frequency selective channel was characterized by 16 multipath rays with uncorrelated Rayleigh fading. Our analysis focused on the achievable secrecy rate for various levels and sources of channel errors and different system considerations, as well as on the BER at the users B and C. Unless otherwise mentioned,
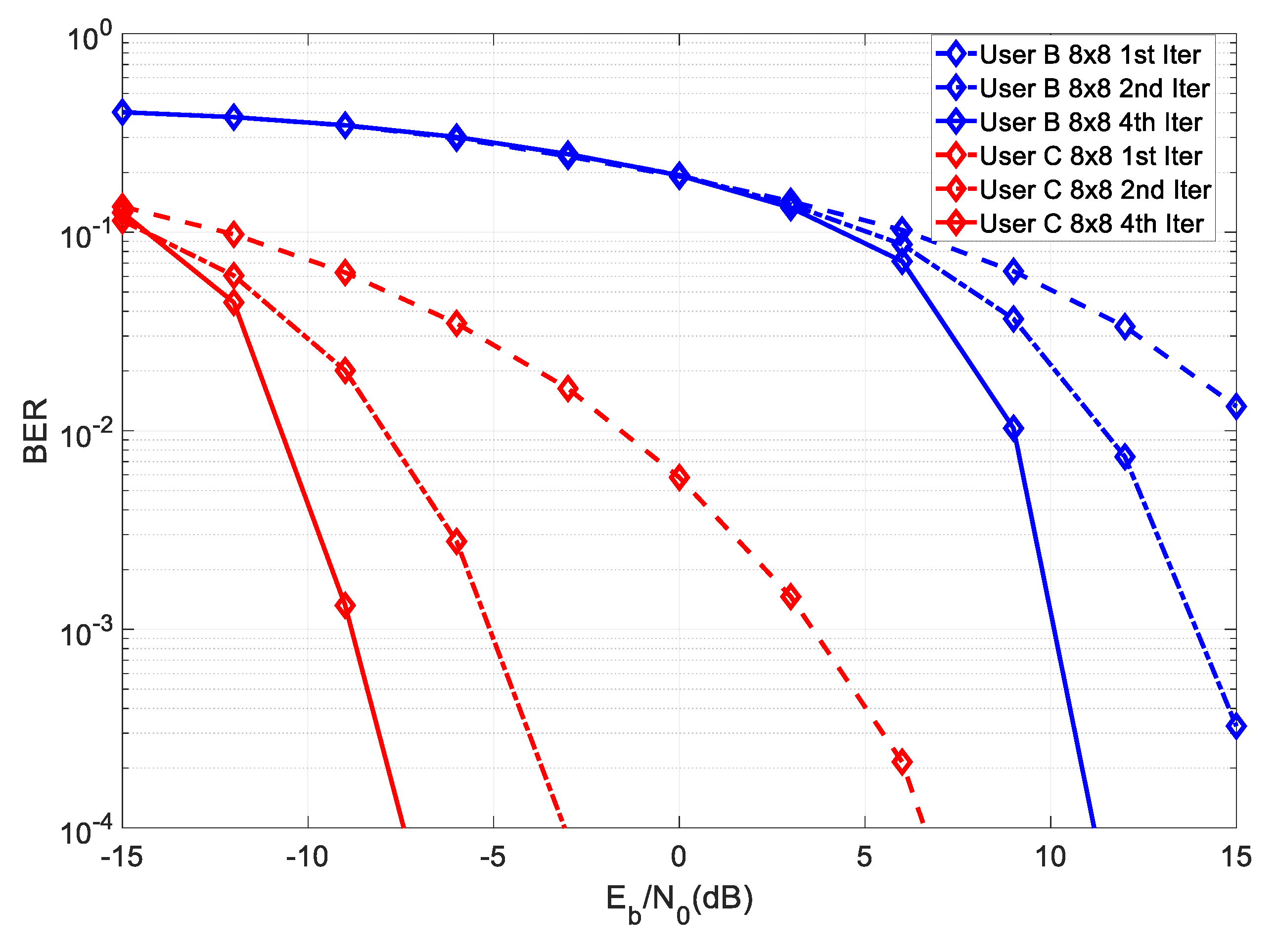
dB. Let us start with
Figure 3, which shows the BER of the proposed system considering an
system with perfect CSI.
From the figure, it can be seen that User C required an SNR of about 18 dB lower than User B, in order to achieve the same BER in the first iteration, which corresponded to the gain due to the higher transmit power. As mentioned before, the partial key
must be quantized using a finite resolution, before being transmitted.
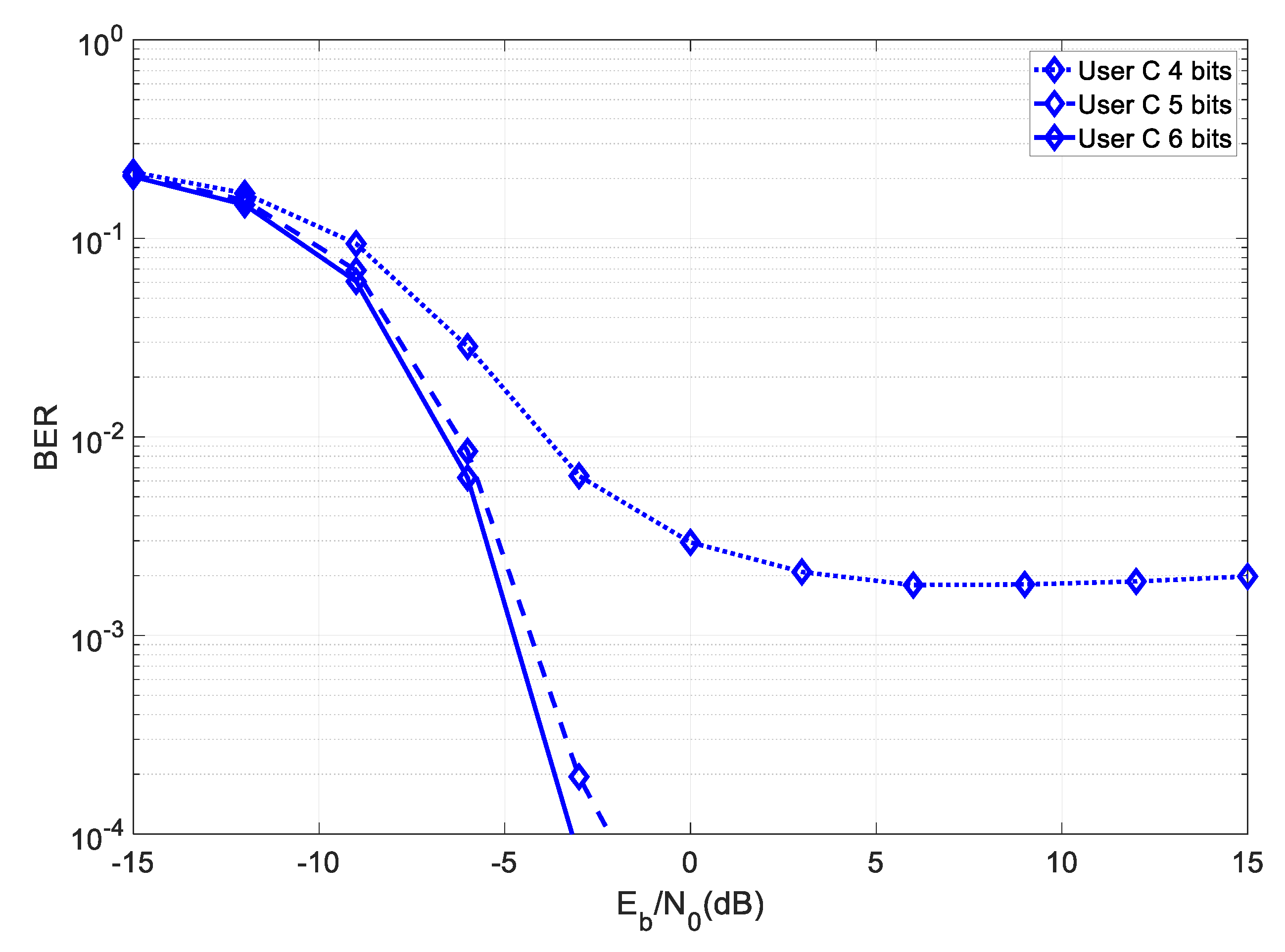
Figure 4 shows the achievable BER results for a
system at User C for different quantization resolutions.
From the figure, it can be seen that this system required at least five bits of quantization to reach a target BER of . Since the matrix could be reconstructed based on four parameters, then the total overhead associated with the transmission of the partial key had a length of 20 bits.
4.1. Secrecy Rate Results
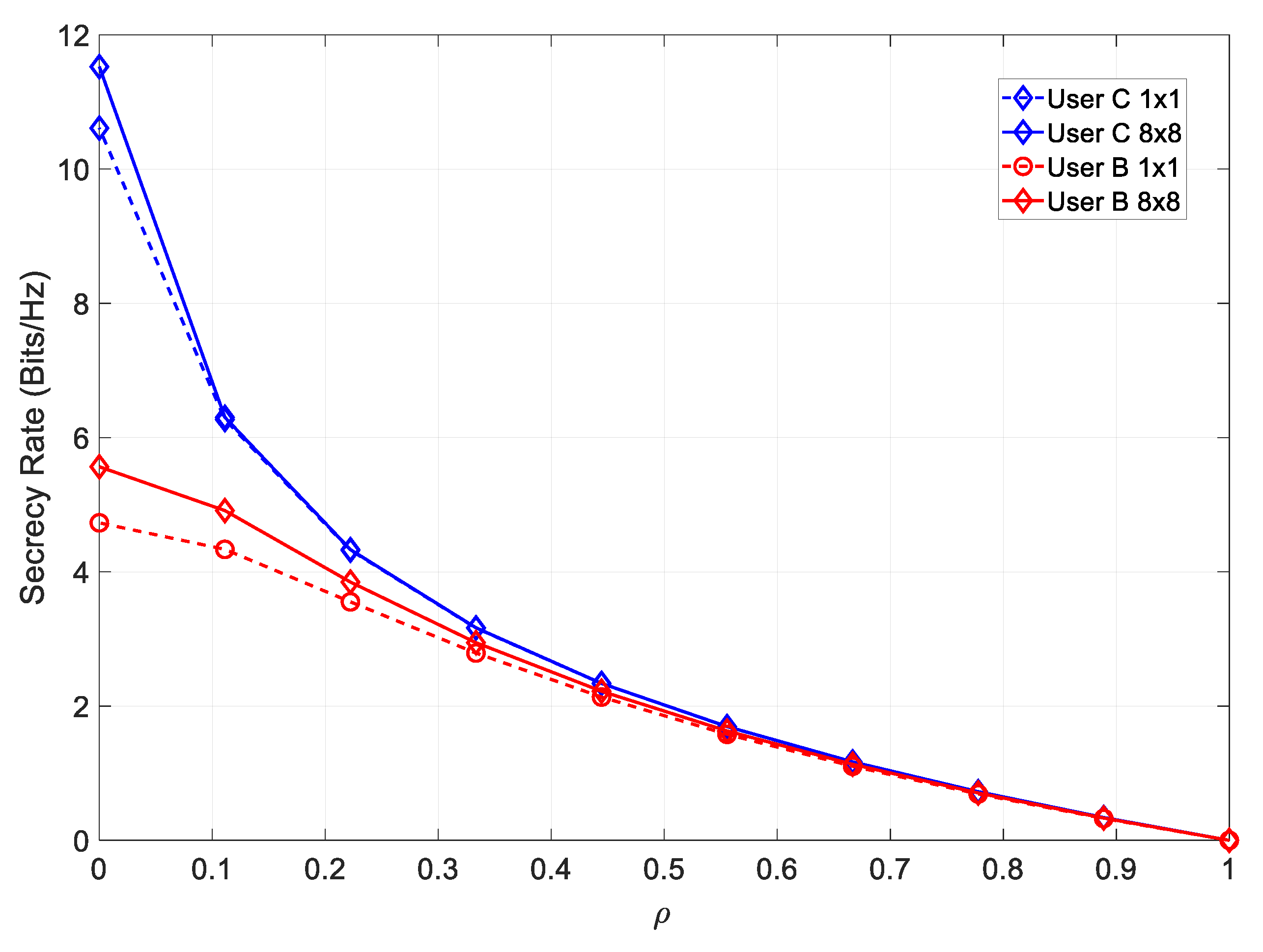
Figure 5 shows a comparison of the secrecy rate for both channels considering both a SISO and MIMO configuration.
From the figure, it could be concluded that employing MIMO led to a higher achievable secrecy rate at lower values of and .
4.1.1. User B Results
Let us analyze the secrecy rate of the nearest user, beginning with
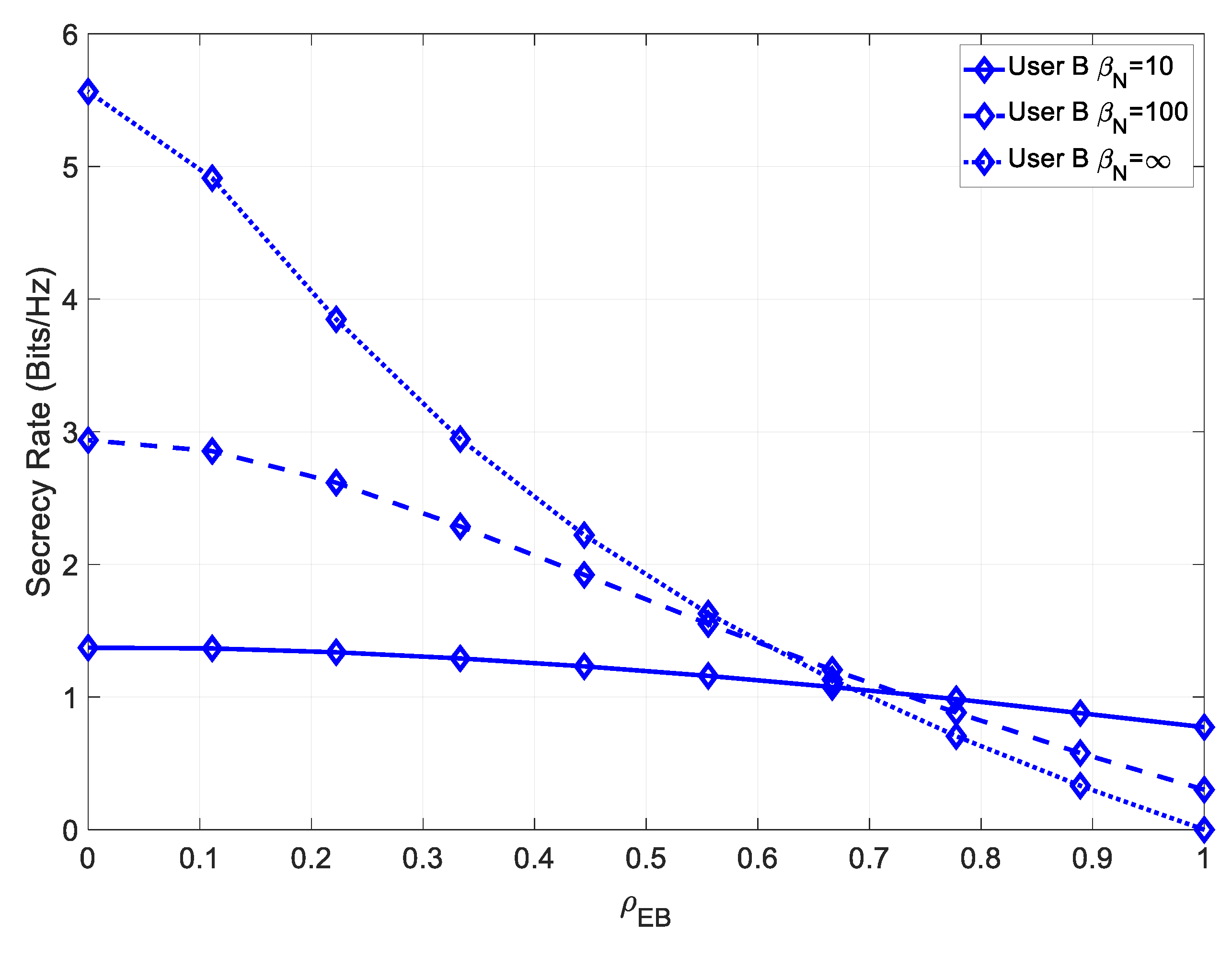
Figure 6, which depicts the secrecy rate of User B under various channel estimation errors.
It can be seen that minimizing the channel estimation error in the receiver was crucial to ensuring a high secrecy rate. For low values of
, this receiver achieved significant levels of the secrecy rate. In
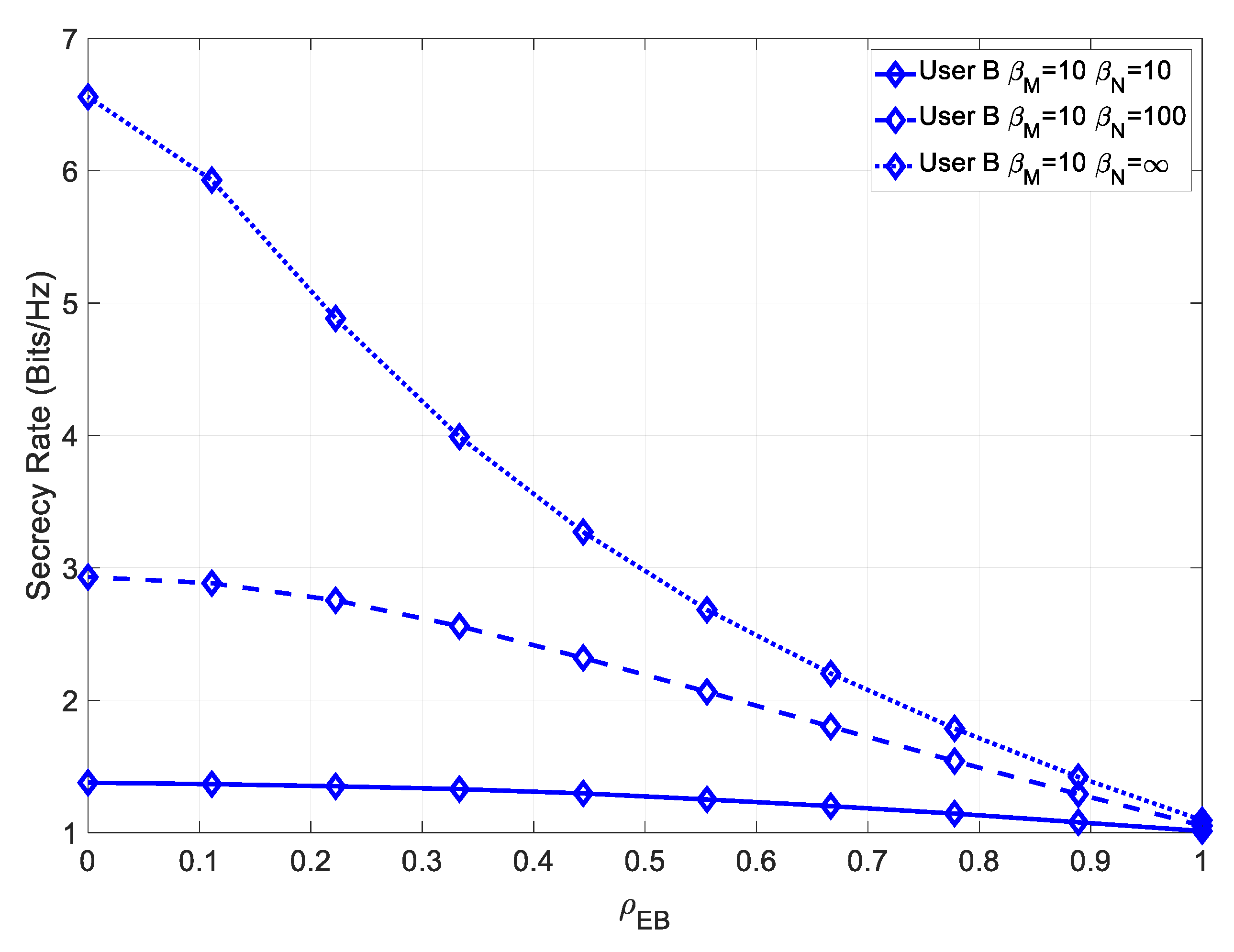
Figure 7, we introduce a channel mismatch error.
It was observed that maximum achievable secrecy rate, for low values of , increased as the channel estimation error decreased. It should be noted that in this scenario, since the channel mismatch error did not affect the intended receiver, the secrecy rate for high values of was also higher and could not be compensated by decreasing the channel estimation error.
4.1.2. Line-of-Sight at User B
In this scenario, there was an LOS with all users; therefore, we analyzed the impact of the power ratio
on the attainable secrecy rate. In
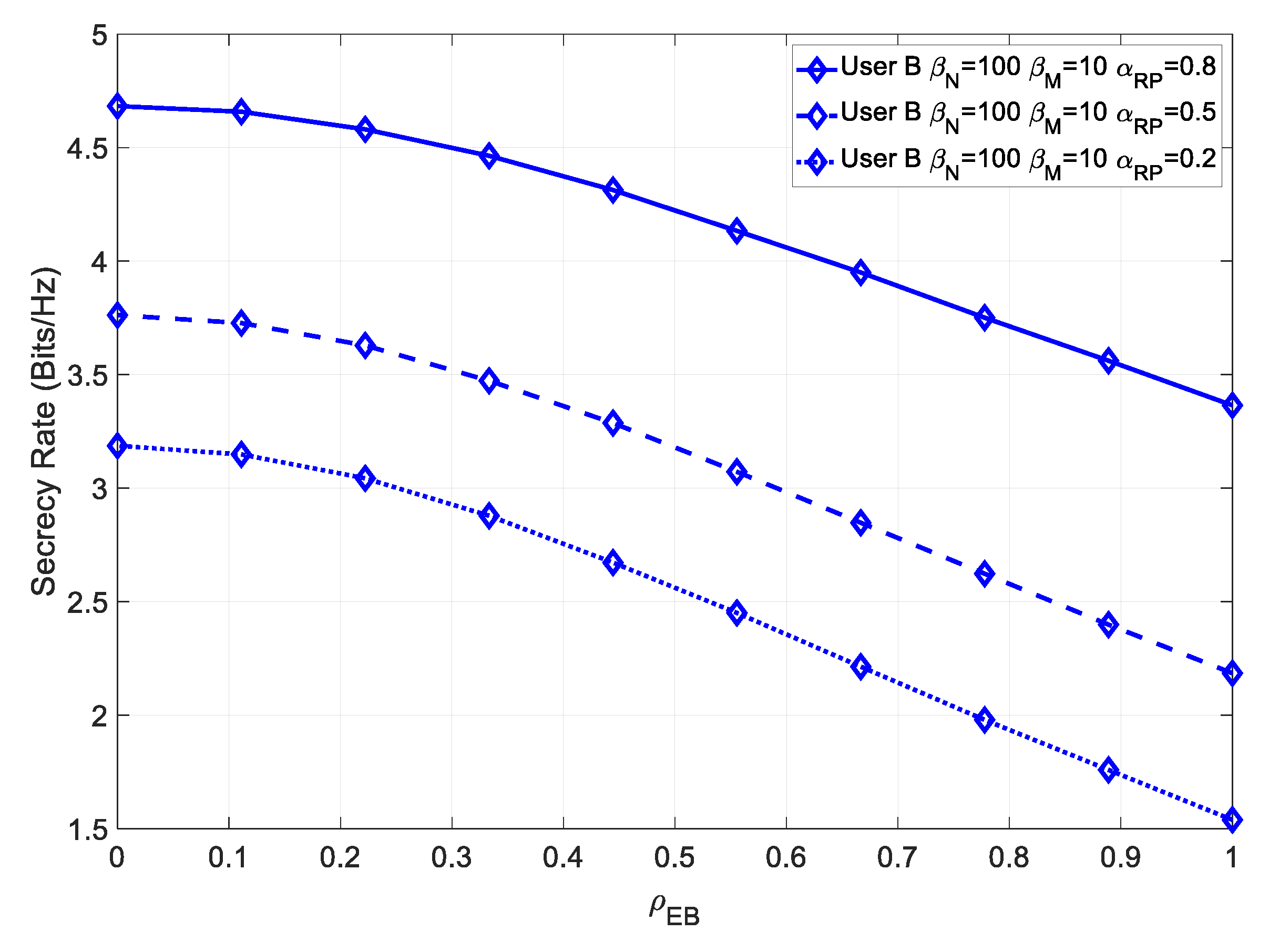
Figure 8, the secrecy rate for various values of
is shown for User B.
As expected, since the eavesdropper could not estimate the multipath component, the greater the value of
, the more secure the system could be.
Figure 9 shows the secrecy rate in a scenario where there was imperfect channel estimation.
It could be observed that the channel estimation severely degraded our secrecy rate; however, even for high values of
and
, the secrecy rate remained high, when compared with the non-LOS scenario, due to the multipath component.
Figure 10 shows the impact of a channel mismatch error on the secrecy rate.
It could be concluded that the permanent channel mismatch error increased the secrecy rate for high values of , albeit the increase was relatively small, when compared with the non-LOS scenario. Since the lack of a multipath estimation produced a much more significant effect on the secrecy rate, then a further channel mismatch error had a smaller impact on the secrecy rate.
4.1.3. User C Results
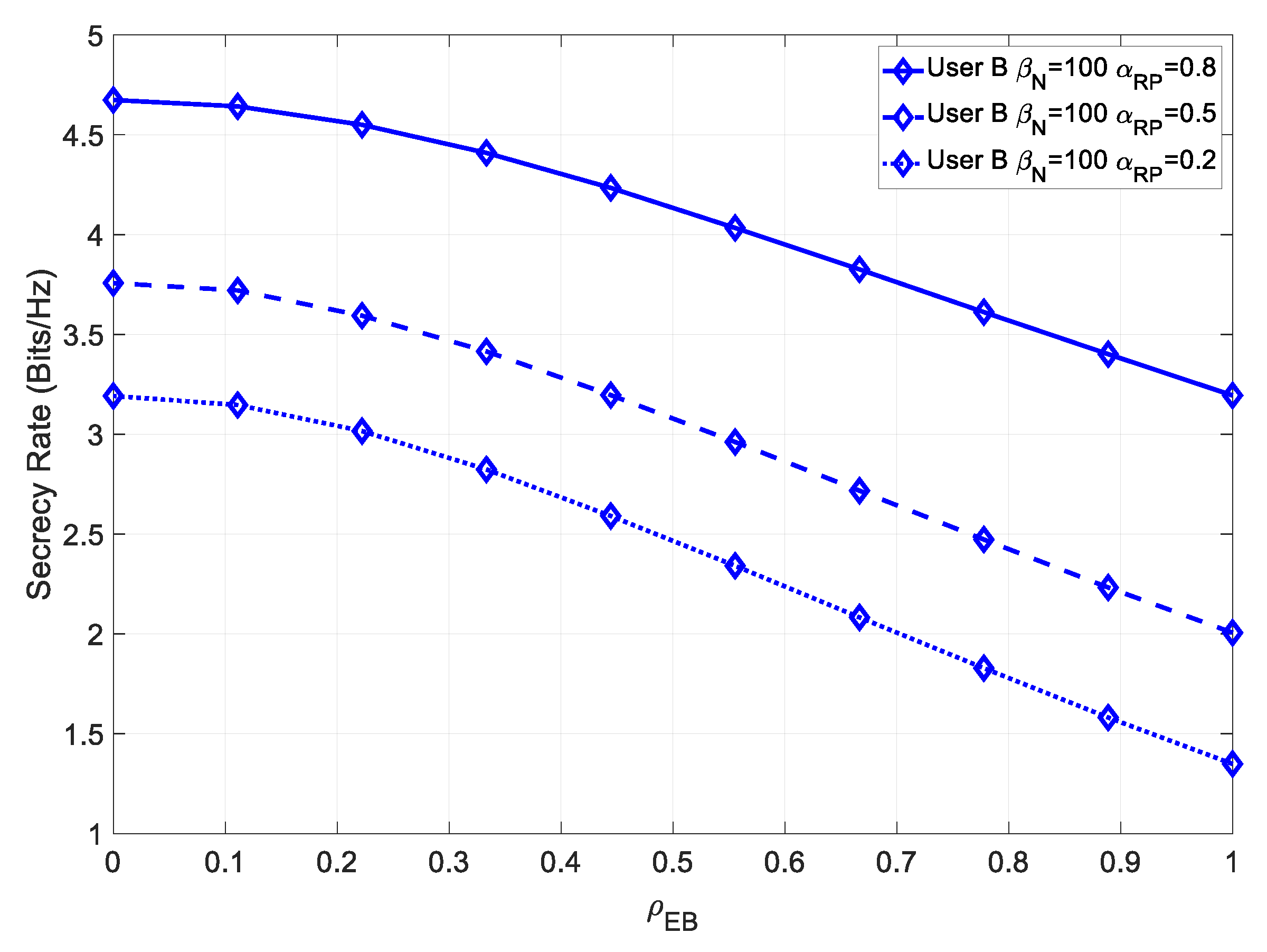
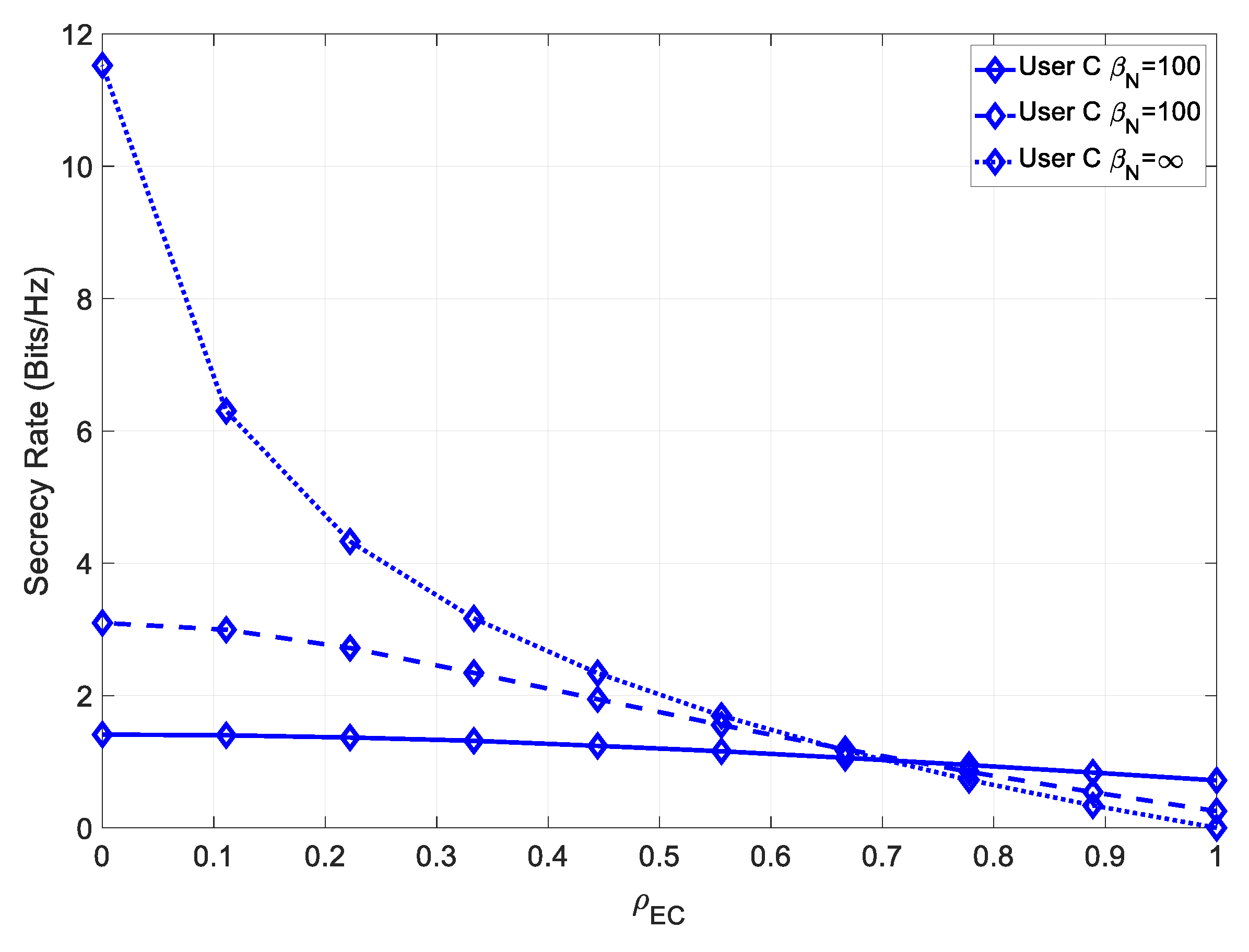
Let us analyze the secrecy rate at the farthest user. In
Figure 11, we compare the secrecy rate of User C under different levels of channel estimation error.
In this case, the maximum achievable secrecy rate was higher than the one of User B, due to the increased capacity of the channel with a higher transmit power. The effect of minimizing the channel estimation error of the receiver was significantly more noticeable in this scenario, at low values of
. In
Figure 12, the secrecy rate of User C is simulated under imperfect channel estimation, as well as a channel mismatch error at the eavesdropper.
It could be seen that, similarly to User B, this system achieved a higher maximum secrecy rate, at low values of , and a higher secrecy rate, even for high values .
4.1.4. Line-of-Sight at User C
In the LOS scenario, we analyzed the impact of the power ratio
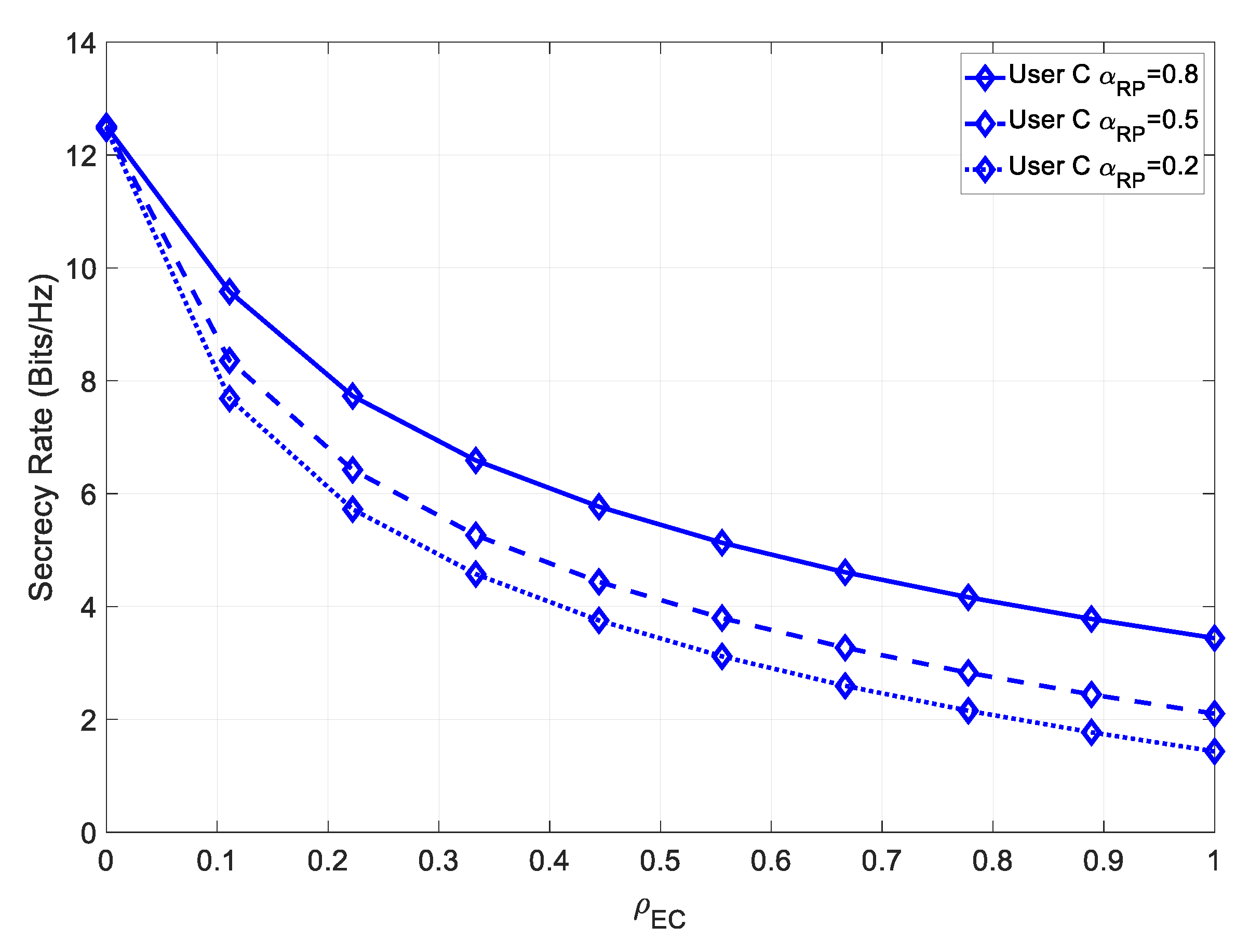
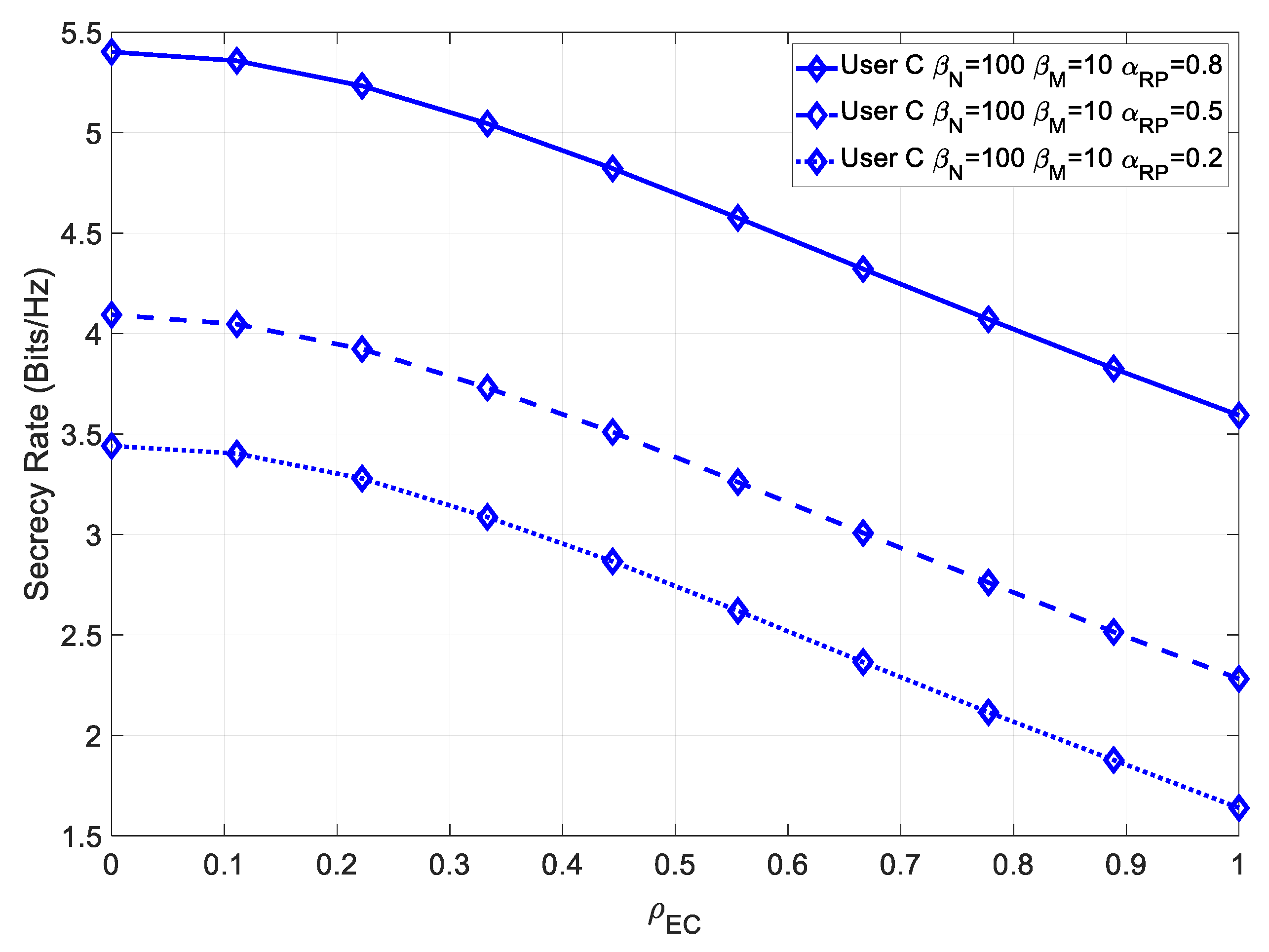
on the attainable secrecy rate for user C. In
Figure 13, the secrecy rate for various values of
is shown.
Similarly, for a higher contribution of the multipath component, the achievable secrecy increased. Since in this case, there was perfect channel estimation, then User C achieved a much higher maximum secrecy rate than User B, due to its higher channel capacity.
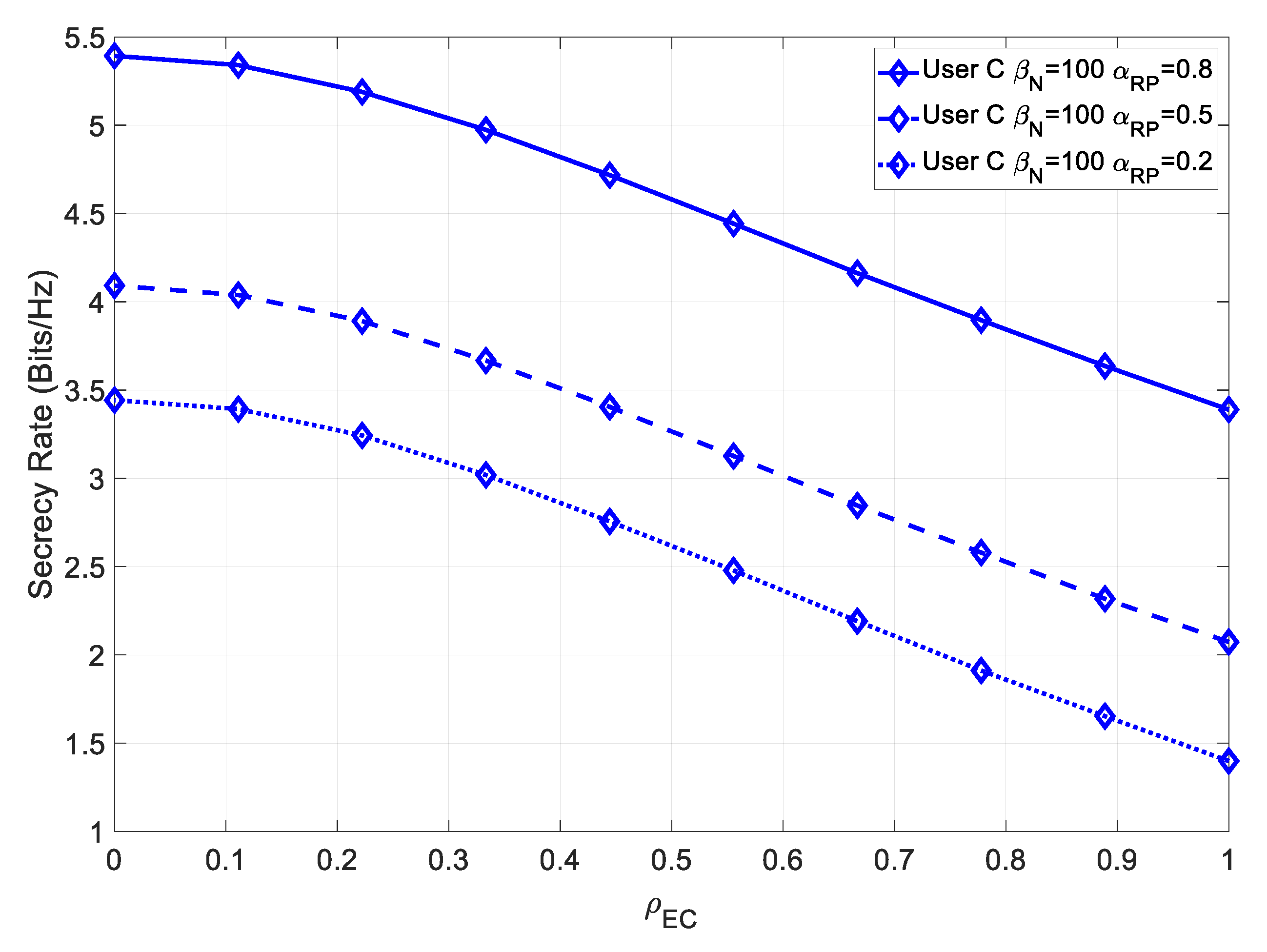
Figure 14 shows the secrecy rate for various values of
, in the presence of channel estimation errors.
In this case, the channel estimation error lowered the overall secrecy rate; however, the degradation was less severe for higher power multipath components. Moreover, it should be noted that User C’s secrecy rate was degraded much more than User B’s, as User C required very precise channel estimation.
Figure 15 shows the secrecy rate for various values of
and various sources of channel estimation errors.
As is the case for User B, the increase in the secrecy rate at high was relatively small, compared to the NLOS scenario, as the LOS component contributed less in this scenario.