Abstract
This paper studies an approach for detecting cyber attacks against networked cooperative systems (NCS) that are assumed to be working in a cyber-physical environment. NCS are prone to anomalies both due to cyber and physical attacks and faults. Cyber-attacks being more hazardous given the cooperative nature of the NCS may lead to disastrous consequences and thus need to be detected as soon as they occur by all systems in the network. Our approach deals with two types of malicious attacks aimed at compromising the stability of the NCS: intrusion attacks/local malfunctions on individual systems and deception/cyber-attacks on the communication between the systems. In order to detect and identify such attacks under switching communication topologies, this paper proposes a new distributed methodology that solves global state estimation of the NCS where the aim is identifying anomalies in the networked system using residuals generated by monitoring agents such that coverage of the entire network is assured. A cascade of predefined-time sliding mode switched observers is introduced for each agent to achieve a fast estimate of the global state whereby the settling time is an a priori defined parameter independently of the initial conditions. Then, using the conventional consensus algorithm, a set of residuals are generated by the agents that is capable of detecting and isolating local intrusion attacks and communication cyber-attacks in the network using only locally exchanged information. In order to prove the effectiveness of the proposed method, the framework is tested for a velocity synchronization seeking network of mobile robots.
1. Introduction
Networked Control Systems are control systems where the control loops are closed through a communication network whereby necessary signals for the control mission are exchanged among the system components through a network, namely wireless. Indeed, one of the main advantages of such systems is the capability of connecting their cyberspace to their physical space thus enabling the execution of several tasks from long distance. Figure 1 represents an example of a NCS, its environment and basic components. These systems, sometimes referred to as cyber-physical systems (CFS) [1,2] or multi-agent systems (MAS) in the literature [3], have attracted a lot of research interest in recent years due to their numerous potential use in various applications and industries ranging from flocking of mobile vehicles, terrestrial exploration, manufacturing plant monitoring, formation control in spacecraft flights to unmanned aerial vehicles and autonomous underwater vehicles, just to mention a few (see [4,5,6,7,8,9]).
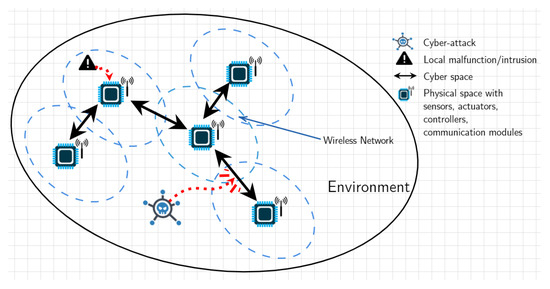
Figure 1.
An illustration of a networked control system, basic components, cyber-physical layers and possible attack types.
However, the nature of NCS makes them extremely vulnerable to external malicious attacks while sharing information through a wireless network, which may compromise the efficiency of cooperative control algorithms and can lead to heavily degraded performances of the overall system and possibly to catastrophic effects. Consequently, the issue of cyber security in such systems has been attracting considerable attention in the literature [10,11].
Some of the research works have focused on local physical component faults, namely actuator and sensor faults (e.g., [12,13,14,15,16]). A relatively recent survey of different approaches to fault diagnosis in swarm systems was presented in [17], where the advantages of distributed designs in contrast with centralized and decentralized ones have been highlighted.
System security plays an increasingly enhanced role in the reliability of NCS as it allows for maintaining unbiased user defined coordination between the agents by detecting violating and malicious information. A few potential ways to violate security measures are deception or cyber-attacks. Indeed, these types of attacks are usually more difficult to identify as they can be coordinated. They typically include false data injection attacks (FDIA) [18], denial of service (DoS) [19], replay attacks [20], amongst others. Indeed, such types of attacks are aimed at destabilising the network by injecting control structures with deceptive information. A number of instances have been outlined in the past [21]. Detecting them has thus become a central focus for system security and control.
2. Related Work and Contribution
When it comes to cyber security in NCS, some of the works in literature has tackled problems such as false data injection in state estimation [18], secure computations in networked systems [22], to name a few. One way to increase resilience of MAS with respect to these faults is to design a robust control algorithm that is resilient to the effects of certain faults and attacks [23]. Another way, as pointed out in [24], is to develop monitoring schemes to detect failures in the MAS caused by attacks and faults.
On the other hand, [25] has provided an exhaustive literature review on model-based techniques in fault detection and isolation where observer-based techniques have proven to be powerful software-based tools in fault diagnosis due to their efficiency and online implementation capability. Such techniques have been used for instance in [26,27,28,29,30,31,32,33,34,35] for cyber-attack detection in NCS.
However, most of the works on observer-based attack detection of control systems consider centralized architectures, second order systems or do not consider the case of a possibly dynamic communication topologies. Unfortunately, the study of global fault detection for NCS with switching topologies subject to cyber-attacks is still in its infancy.
Motivated by all of the above and the recent works in [36] where a novel approach called predefined-time stability has been proposed, this paper introduces a new approach to identify faults and deception attacks in a cooperating networked system with a switching topology. The objective in this work is to deal with these non-cooperative and malicious activities. The proposed protocol makes an agent act as a central node monitoring the whole system activities in a distributed fashion. Compared to the existing works in the literature, our main contributions are:
- (1)
- The design of a bank of distributed predefined-time sliding mode observers (SMO) for global state estimation for a multi-agent system with integrator dynamics whereby the convergence time is an a priori user defined parameter, in order to overcome the problem of attack detection under switching topologies.
- (2)
- A residual based approach is proposed where the equivalent control concept is used to detect different faults and attacks that might occur anywhere in the system (i.e., an intrusion attack reflective of a local malfunction in agent or a cyber-attack affecting a communication link between two agents) in a distributed way based on the topological properties of the network. This allows detection and identification of multiple simultaneous attacks and intrusions.
The rest of the manuscript is organized as follows: Section 2 provides a brief background on graph theory. Section 3 introduces some important definitions, lemmas and the problem formulation of the global fault detection and identification issue. Section 4 presents the main results, namely the design of banks of distributed predefined-time sliding mode observers for state estimation and residual generation based on local information. Section 5 presents numerical simulation results, where our approach is applied in the context of a practical application to consensus seeking fleet of mobile robots, in order to show the efficacy of our approach. Finally, Section 6 draws the main conclusions of this work and present future scopes for research on the considered topic.
Notations: The superscript T stands for the matrix transpose and we denote by I the identity matrix and by 1 the vector with all elements one, both with appropriate dimensions. The set of real-valued matrices is given by . represents the smallest non-zero eigenvalue of a square matrix . and denote the 1- and 2- norms, respectively. refers to the equivalent control value of and refers to the upper right-hand Dini derivative of . For the sake of simplicity, the time argument is omitted when it is not required for clarity. Table 1 presents a list of the employed acronyms:

Table 1.
List of acronyms.
3. Graph Theory
In this paper, we are going to refer to networked systems as multi-agent systems and given that networked multi-agent systems need to exchange information amongst them, it is natural to model them using graph theory. In general, a communication topology composed of N systems is represented by whereby is the node set consisting of N nodes/vertices each representing an agent, and is the edge set representing the communication links between two agents. Here, we shall assume that is connected, undirected and is a non-empty subset of agents that agent i can interact with. In this work, we shall further assume that the communication topology is time-varying. As a result, we denote by set of all possible known topologies and by the set of indices corresponding to these topologies. More precisely, the communication topology is characterised by a switching graph where is piecewise constant switching signal and determines the communication topology with being the switching instants of . Furthermore, it is assumed that satisfies the minimum dwell time condition [37], and with a known constant. Therefore, when , the topology is activated. For the rest of this paper, we refer to the active mode using the superscript . The adjacency matrix is defined by when the agent can receive information from the agent and otherwise. The diagonal of matrix is null since self-connections are not allowed. Let be the in-degree diagonal matrix with entries . Then, the Laplacian matrix is defined as:
Let us denote by the Laplacian matrix defined without agent i, and by:
the associated diagonal matrix defining the interconnections between agent i and the remaining agents under the active topology , if information of agent i is accessible by the agent; otherwise .
4. Preliminaries and Problem Statement
Before stating the main results, a brief overview of the techniques employed in our work are presented hereafter.
4.1. Definitions and Useful Lemmas
Consider the following nonlinear system:
where is the state and where is the system parameters considered to be constant (). is assumed to be a nonlinear function with its origin as an equilibrium point, i.e., .
Definition 1
Definition 2
Definition 3
Let us recall some lemmas concerning predefined-time stability.
Lemma 1
([40]). Consider the system
with . The parameters of the system are real numbers satisfying the constraints , . Let be the parameter vector, then its origin is fixed-time stable and the settling time function satisfies , where:
and is the well known Gamma function defined as .
Remark 1.
The concept of predefined-time stability is introduced where a settling time bound is set in advance as a function of system parameters ϕ, i.e., , and a strong notion of this class of stability is given when , i.e., is the least upper bound of the settling time.
Lemma 2
([40]). Let us consider the nonlinear system (1) with as the initial condition, where is the state and with , is the system parameters considered to be constant. is assumed to be a nonlinear function with its origin as an equilibrium point. Suppose there exists a continuous radially unbounded candidate Lyapunov function such that
and its derivative along the trajectories of (1) satisfies
with , p, q, , , , is given in (2) and is the upper right-hand Dini derivative of . Then, the origin is predefined-time stable with predefined time .
Now, let us recall some complementary key lemmas that will be used throughout this paper.
Lemma 3.
Let . If is a sequence of positive numbers, then the following inequality is satisfied:
for with and .
Lemma 4.
Let f be the function defined as
for with and . Then, is monotonically increasing for all .
Lemma 5
([41]). Let and
Then, : .
4.2. Problem Statement
Consider a homogeneous multi-agent system composed of N agents labelled by , and described by the following -order dynamics
where is agent i’s state variable with , is a process fault affecting the dynamics of the agent which could be exogenous and might correspond to an internal malfunction, local intrusion attack, etc, is the control input and is agent i’s internal measurement. Note that there is a multitude of practical applications of such systems, namely robotic systems, power systems, etc. Research on cyber-attack identification for such systems is of both practical and theoretical significance.
Furthermore, it is considered that agents have access to their control inputs, but they do not receive their neighbours’ inputs. If needed, they have to reconstruct them using state estimates from exchanged information which are possibly corrupted. The exchanged information is expressed as
where is agent i’s output signal sent to agent k with , and is agent j’s estimate of agent i’s output which is sent to agent k, the term will be defined in the next Section. Both pieces of information are subject to an edge fault denoted and , respectively. Note that, these types of faults may affect all broadcasted information of an agent to another. This might include DoS, FDIA, deception attacks, cyber-attacks, etc. In this paper, a solution to the following questions is investigated:
- How can we detect a cyber-attack anywhere in the MAS while keeping a distributed approach of the detection scheme?
- How can we distinguish said attacks from local malfunctions/intrusions?
The conceptual idea in this work is that information locally produced by the sensors is considered to be secure, while the one sent over the communication network/cyber layer of the system is vulnerable to external attacks. The next section lays out our main results.
5. Proposed Methodology
The proposed distributed bank of predefined-time observers for output and state estimation and global cyber-attack detection scheme is laid out in this section.
5.1. Global Output and State Estimation
Let us define the ’monitored’ agent i as the agent to be diagnosed by a ‘monitoring’ agent k. First, let us consider the case of a fixed communication topology, where no cyber-attack exists in the system (i.e., ). Denote by , agent k’s estimate of the state variable of agent i and by , agent k’s estimate of agent i’s output. The proposed distributed switched observer takes the following structure:
with ,
The auxiliary state variables are defined as
where the subscript denotes the equivalent value of sign function. In the following, it is assumed that the effect of the filter dynamics is negligible w.r.t. those of the observer. Let us define the errors as
Differentiating them yields the following error dynamics:
where can be expressed in terms of the output estimation errors as . Putting (8) in compact form, the following is obtained:
where for each agent and , the estimation errors, the state estimates and the auxiliary variables are concatenated in the vectors: , , . Let us denote . The terms are expressed as
Assumption 1.
For every agent, the state variables, the control and fault signals are bounded, and their maximum values are known, i.e., for , and : , , .
Theorem 1.
Given Assumption 1, for a fixed communication topology and in the absence of cyber-attack, for each agent, the observation errors (9) converge towards zero in a predefined time independently of initial conditions, with the observer gains:
with
and
where and . is defined in Equation (2), represents the observer switches and is the settling-time for each dynamic which is an user-defined parameter, considered to be the same for all of the dynamics of the agents for notational convenience.
Proof of Theorem 1.
The proof is done step by step by taking advantage of the switching conditions. Indeed, due to this, at each step, only a one-dimensional, corresponding sub-dynamical system is studied.
Step 1: Initially, , the error dynamics are expressed as
Consider the following Lyapunov function associated with the concatenated first error dynamics of the agents
Differentiating it results in
By setting , one obtains
Then, it follows that
with
Considering Lemma 3, and taking into account the fact that and , the term can be expressed as
Using Lemma 5, it can be shown that
By expressing as a linear combination of the eigenvectors of , the term can be bounded as
Thus, using Lemma 4, one has
On the other hand, from the second term , the following can be deduced
Therefore, in accordance with Lemma 2, converges towards the origin with the settling time (i.e., ). As a result, at (), we have
Hence, one gets . At this point, one can go to the next step.
Step 2: At , the error dynamics become
Selecting the Lyapunov function and by following the same reasoning as before, one gets
with . Then, it is straightforward to show that . Consequently, converges towards the origin with the settling time (i.e., ). Therefore, at and .
Step n: Now, fast forward to the step, at , the error dynamics become
Taking as the Lyapunov function and by setting , and following the same procedure as before, the following inequalities are obtained for the terms and
The proof is thus concluded at the step. □
Now, let us consider the presence of a possible cyber-attack in the network. Due to the presence of these attacks, the output estimation errors is expressed as
In this case, the following theorem can be stated.
Theorem 2.
Given Assumption 1 and in the presence of one or multiple cyber attacks incident to agent k, in the case of fixed communication topology, the observation errors converge towards zero in a predefined time independently of initial conditions, and the gains are given as
with
where corresponds to the time derivative of and is the corresponding upper bound. The gains and the observer switches remain the same as in Theorem 1.
Proof of Theorem 2.
When cyber-attacks are considered, (6) becomes
The rest of the proof straightforwardly follows the same reasoning as Theorem 1 and is thus omitted for brevity. □
Note that the use of the predefined-time concept is very useful when dealing with switching topologies. Indeed, using our proposed scheme, one can immediately derive the following proposition:
Proposition 1.
Remark 2.
The global fault estimation protocol proposed in this paper, is a distributed one. Each neighbouring agent can only exchange local information during the fault estimation process. Furthermore, provided that all of the possible topologies are known to all agents, constants and therefore can be computed a priori. If all are the same (i.e., ), with .
5.2. Residual Definition and Cyber-Attack Identification
The idea is to compute the difference between the actual input of an agent and the estimated input effort. The difference should indeed be null in the case of no attacks or faults. The next step is to identify the source and type of faults, specifically deception attacks and thus trigger the appropriate alarms and further corrective measures. Note that, for Theorems 1 and 2, the upper bounds of the control inputs are used in Assumption 1 to design the predefined-time distributed observers. In this section, we will show through a residual based approach how one can detect process or communication faults/cyber-attacks with a global approach using input estimates if the control structure is known. In the following, let us consider the following typical linear higher-order consensus control algorithm [42,43], used with the available information
where , and are the consensus gains. It can be noticed that communication faults spread in the MAS through , and thus need to be detected as they occur. In the absence of edge faults, consensus is achieved provided a suitable selection of , and due to the fixed-time stability property of the proposed distributed observers [44].
Proposition 2.
Define agent k as the monitoring agent, agent i as the monitored agent, agents as agent k’s neighbours and agents as agent i’s neighbours, where agent i may or may not be a direct neighbour of k and . Using protocol (29), an agent k can detect a deception attack on a communication link incident to agent k or i and local malfunctions/intrusions anywhere in the fleet, given one type fault happens at a time, using the following residual signal:
where
is agent i’s reconstructed input by agent k with .
Proof of Proposition 2.
After the convergence of errors, the actual applied control input for each agent becomes
Furthermore, the reconstructed input generated by the monitoring agent k is expressed as
Note that, when the control efforts are known to other agents in the network, the term in Equation (31) disappears. In this case, the residual signals become
where . As a result, the defined residual signals (30) generated by the monitoring agent k are able to detect the presence of a cyber-attack or a local malfunction. □
Residual evaluation: Once the residual signals are generated, it is important to be able to interpret them in order to find the root of the fault and thus make corrective measures accordingly. Indeed, from Equation (30), it can be noticed that, when a cyber-attack incident to agent k or i occurs while there is no local malfunction, agent k’s generated residual signal for itself is and for all regardless of whether or not agent i is a neighbour of k. On the other hand, when there is no cyber-attack, the residuals provide explicit estimations of the local malfunctions/intrusions, with and . is thus used to identify a cyber-attack in the system as it is only sensitive to local malfunctions/intrusions. The proposed cyber-attack identification scheme is thus summarized in the following Algorithm 1:
| Algorithm 1: Observer Design and Decision Logic |
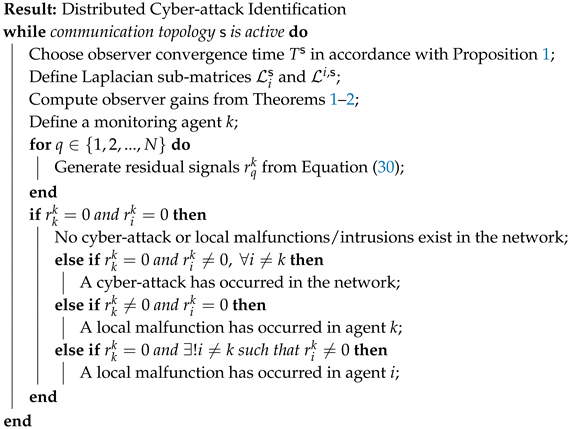 |
Remark 3.
Note that our approach does not present limitation with respect to the number of detectable attacks in the system, contrary to some existing works, for instance in [26]. Indeed, Proposition 2 can be used to detect simultaneous local malfunctions/intrusions and cyber-attacks, and discern them from each other thus achieving the cyber-attack identification objective. Moreover, the predefined-time stability principle is useful to design fast converging switched observers to solve the problem of switching communication topologies as pointed out in Proposition 1. This allows for avoiding false alarms and achieving fast convergence of the estimation errors before the next topology switching instant. Furthermore, it is worth mentioning that our proposed approach can also be used when sudden communication breaks occur or when communication attacks on the communication weights and sudden abnormal quality drops of the exchanged information (i.e., attacks on communication parameters defined in Section 2) are considered. Indeed, these types of attacks manifest themselves in the generated residuals as exponentially decaying signals.
6. Practical Example
Cyber-Attack Identification in Cooperative Multi-Robot Systems
In this section, an illustrative numerical example is given for a practical application in order to show the effectiveness of the proposed global cyber-attack identification protocol. For this, let us consider a team of omnidirectional wheeled mobile robots (WMR) that are labelled with numbers 1 through 5 and are moving in a two-dimensional plane (see Figure 2). In this example, the robots have to cooperate in order to render the steady state axial jerk null and thus achieve constant linear acceleration synchronization of the network of WMR.
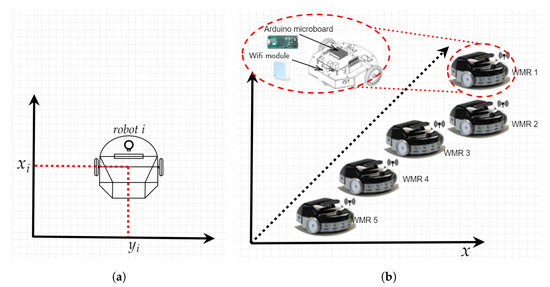
Figure 2.
The setup of the studied problem where: (a) represents the upper perspective view of a WMR on the x-y 2D plane and (b) represents an illustration of the setup of the five mobile robots.
Here, we assume non-slipping and pure rolling conditions and since our aim is to achieve linear acceleration synchronization, only the dynamics along the x-direction are considered. In this case, each robot can be modelled with the following simplified triple integrator dynamics which is a special case of system (3):
where , , and are the x-position, the linear velocity on the x-axis, the linear acceleration on the x-axis and an internal fault affecting the local jerk of a robot. The proposed residual observer-based cyber-attack identification algorithm can be implemented on the on-board micro-controllers as depicted in Figure 2. Furthermore, the robots are assumed to be equipped with WiFi modules and broadcast their information through a wireless network described by the graph topologies illustrated in Figure 3 and Figure 4 respectively, which are characterised by the Laplacian matrices:
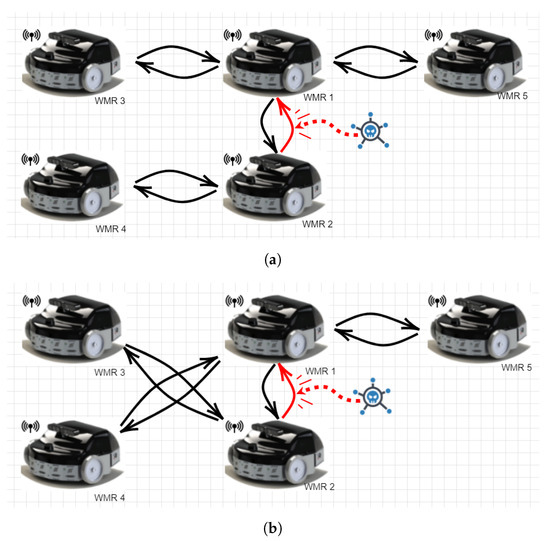
Figure 3.
An illustration of the interaction between the robots: (a) in the first 12 s and (b) after 12 s, where an arrow indicates the direction of information flow amongst two designated robots.
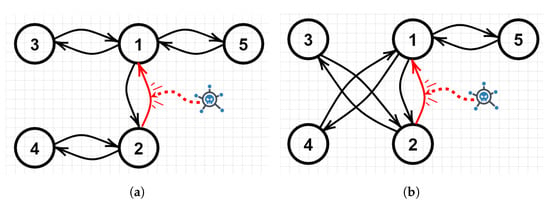
Figure 4.
The corresponding graph topology models, where: (a) corresponds to and (b) to .
The communication topology is assumed to switch from to at s. In this example, in order to achieve acceleration consensus, the following cooperative control is used for each robot
where , , , and are the consensus gains set to 5, 4, 3, and, 2.5, respectively, for both possible communication topology modes , and 1 m s is the reference acceleration. Hence, , the exchanged signals between agents are given as
where , and are noise due to some communication uncertainties.
The initial positions of the five agents on the x-axis are given as m, m, m, m and m respectively, while the initial velocities and acceleration are set to 0. For each of the mobile robots, the distributed observers are designed to estimate the global state in the desired predefined time s with s which satisfies the conditions of Proposition 1. The observer parameters are chosen as
used for each corresponding topology. On the other hand, to obtain the equivalent values, first-order low pass filters are used with cut-off frequency of 100 s for the first dynamics and 10 s for the second and third dynamics. In order to verify the performance of the proposed scheme, the following two simulation scenarios are carried out on MATLAB.
First Scenario: In the 1st scenario, an intrusion occurs in robot 3 causing an out of control situation that affects its local jerk simulated by the following function :
This fault only represents a local malfunction in the robot 3 and thus needs to be distinguished from a cyber-attack. It can be clearly seen from Figure 5 corresponding to the 1st scenario that the residuals generated by the monitoring agents for the monitored agent 3, i.e., , , and respectively, provide an explicit estimation of .
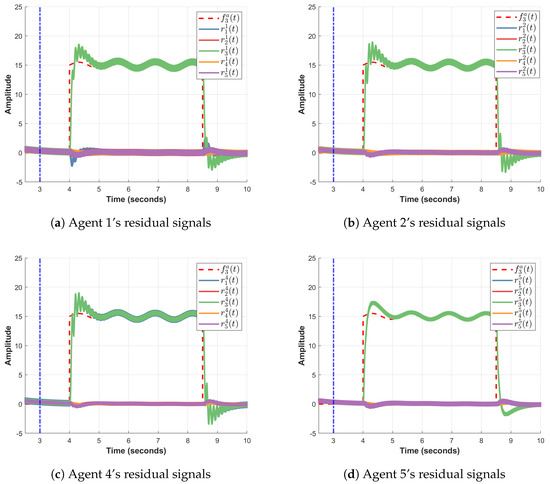
Figure 5.
Residuals in scenario 1 by agents 1, 2, 4, and 5, shown in sub-figures (a–d) respectively. The vertical dashed blue line represents the convergence time.
Second Scenario: In the 2nd scenario, a communication fault occurs in exchanges flowing from robots 1 to 2 at s, for the first topology such that
Note that the topology switches at s and remains throughout the topology change (see Figure 4). Therefore, the gains are computed from Theorem 2 and Remark 2 as
It should be recalled that these gains are valid for both scenarios. Figure 6 corresponding to the 2nd scenario shows that a cyber-attack in the form of the simulated functions and , incident to agent 1 in both topologies, can be distinguished even in the presence of some reasonable communication noise. Indeed, the residual signals , , , and stay around 0 after the cyber-attack appears in the system and throughout the topology change.
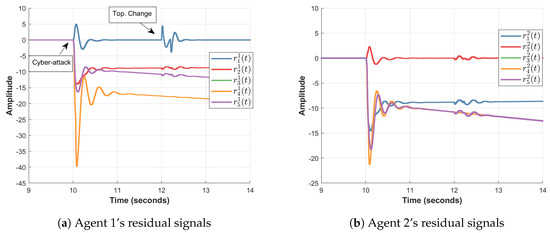
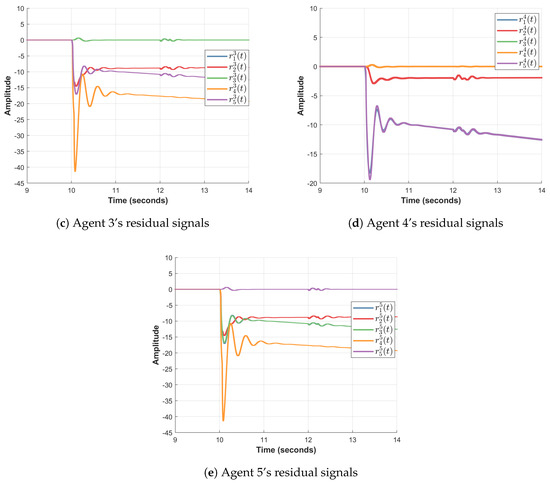
Figure 6.
Residuals generated by all agents in scenario 2.
Consequently, according to Proposition 2, one can distinguish and identify a cyber-attack in the networked system.
7. Conclusions and Future Work
In this paper, a novel distributed cyber-attack identification scheme was proposed for NCS with switching topologies subject to cyber-attacks, where any agent/node can act as a monitor to the whole system behavior and can thus detect and identify intrusion and cyber attacks. This is done by employing a bank of distributed predefined-time observers to estimate the global system state through auxiliary states whereby the settling time is an a priori user defined parameter, independently of the initial conditions. Numerical simulation results have been carried out by implementing the proposed scheme on a synchronization seeking network of mobile robots. Future works will include the design of a control reconfiguration algorithm based on the estimated faults from our FDI scheme.
Author Contributions
Conceptualization, A.T.; methodology, A.T.; validation, M.D. (Michael Defoort), K.B., M.D. (Mohamed Djemai); formal analysis, M.D. (Michael Defoort), K.B.; investigation, M.D. (Michael Defoort), K.B.; resources, M.D. (Michael Defoort), K.B., M.D. (Mohamed Djemai), A.T.; writing—original draft preparation, A.T.; writing—review and editing, A.T., M.D. (Michael Defoort), K.B., M.D. (Mohamed Djemai); supervision, M.D. (Michael Defoort), K.B., M.D. (Mohamed Djemai); Funding Acquisition, L.D.; All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, or in the decision to publish the results.
References
- Baheti, R.; Gill, H. Cyber-physical systems. Impact Control Technol. 2011, 12, 161–166. [Google Scholar]
- Wu, C.; Hu, Z.; Liu, J.; Wu, L. Secure estimation for cyber-physical systems via sliding mode. IEEE Trans. Cybern. 2018, 48, 3420–3431. [Google Scholar] [CrossRef]
- Shamma, J. Cooperative Control of Distributed Multi-Agent Systems; John Wiley & Sons: Hoboken, NJ, USA, 2008. [Google Scholar]
- Cao, Y.; Yu, W.; Ren, W.; Chen, G. An overview of recent progress in the study of distributed multi-agent coordination. IEEE Trans. Ind. Inform. 2012, 9, 427–438. [Google Scholar] [CrossRef]
- Yang, Z.; Zhang, Q.; Chen, Z. Flocking of multi-agents with nonlinear inner-coupling functions. Nonlinear Dyn. 2010, 60, 255–264. [Google Scholar] [CrossRef]
- Olfati-Saber, R. Flocking for multi-agent dynamic systems: Algorithms and theory. IEEE Trans. Autom. Control 2006, 51, 401–420. [Google Scholar] [CrossRef]
- Oh, K.K.; Park, M.C.; Ahn, H.S. A survey of multi-agent formation control. Automatica 2015, 53, 424–440. [Google Scholar] [CrossRef]
- Su, H.; Chen, M.Z.; Wang, X. Global coordinated tracking of multi-agent systems with disturbance uncertainties via bounded control inputs. Nonlinear Dyn. 2015, 82, 2059–2068. [Google Scholar] [CrossRef]
- Ren, W.; Beard, R.W. Distributed Consensus in Multi-Vehicle Cooperative Control; Springer: Berlin/Heidelberg, Germany, 2008; Volume 27. [Google Scholar]
- Cárdenas, A.A.; Amin, S.; Sastry, S. Research Challenges for the Security of Control Systems. In Proceedings of the 3rd Conference on Hot Topics in Security, HOTSEC’08, Berkeley, CA, USA, 29 July 2008. [Google Scholar]
- Guo, M.; Dimarogonas, D.V.; Johansson, K.H. Distributed real-time fault detection and isolation for cooperative multi-agent systems. In Proceedings of the IEEE 2012 American Control Conference (ACC), Montreal, QC, Canada, 27–29 June 2012; pp. 5270–5275. [Google Scholar]
- Shames, I.; Teixeira, A.M.; Sandberg, H.; Johansson, K.H. Distributed fault detection for interconnected second-order systems. Automatica 2011, 47, 2757–2764. [Google Scholar] [CrossRef]
- Taoufik, A.; Busawon, K.; Defoort, M.; Djemai, M. An output observer approach to actuator fault detection in multi-agent systems with linear dynamics. In Proceedings of the 2020 28th Mediterranean Conference on Control and Automation (MED), Saint-Raphaël, France, 15–18 September 2020; pp. 562–567. [Google Scholar]
- Chadli, M.; Davoodi, M.; Meskin, N. Distributed state estimation, fault detection and isolation filter design for heterogeneous multi-agent linear parameter-varying systems. IET Control Theory Appl. 2016, 11, 254–262. [Google Scholar] [CrossRef]
- Meskin, N.; Khorasani, K. Actuator fault detection and isolation for a network of unmanned vehicles. IEEE Trans. Autom. Control 2009, 54, 835–840. [Google Scholar] [CrossRef]
- Taoufik, A.; Michael, D.; Djemai, M.; Busawon, K.; Sánchez-Torres, J.D. Distributed global actuator fault-detection scheme for a class of linear multi-agent systems with disturbances. In Proceedings of the IFAC World Congress, Berlin, Germany, 12–17 July 2020. [Google Scholar]
- Qin, L.; He, X.; Zhou, D. A survey of fault diagnosis for swarm systems. Syst. Sci. Control Eng. Open Access J. 2014, 2, 13–23. [Google Scholar] [CrossRef]
- Liu, Y.; Ning, P.; Reiter, M.K. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. (TISSEC) 2011, 14, 1–33. [Google Scholar] [CrossRef]
- Liang, G.; Zhao, J.; Luo, F.; Weller, S.R.; Dong, Z.Y. A review of false data injection attacks against modern power systems. IEEE Trans. Smart Grid 2016, 8, 1630–1638. [Google Scholar] [CrossRef]
- Pasqualetti, F.; Dörfler, F.; Bullo, F. Attack detection and identification in cyber-physical systems. IEEE Trans. Autom. Control 2013, 58, 2715–2729. [Google Scholar] [CrossRef]
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A survey on cyber security for smart grid communications. IEEE Commun. Surv. Tutorials 2012, 14, 998–1010. [Google Scholar] [CrossRef]
- Pasqualetti, F.; Bicchi, A.; Bullo, F. Distributed intrusion detection for secure consensus computations. In Proceedings of the 2007 46th IEEE Conference on Decision and Control, New Orleans, LA, USA, 12–14 December 2007; pp. 5594–5599. [Google Scholar]
- Pasqualetti, F.; Bicchi, A.; Bullo, F. Consensus computation in unreliable networks: A system theoretic approach. IEEE Trans. Autom. Control 2011, 57, 90–104. [Google Scholar] [CrossRef]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. Distributed fault detection and isolation resilient to network model uncertainties. IEEE Trans. Cybern. 2014, 44, 2024–2037. [Google Scholar] [CrossRef]
- Ding, S.X. Model-Based Fault Diagnosis Techniques: Design Schemes, Algorithms, and Tools; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Teixeira, A.; Sandberg, H.; Johansson, K.H. Networked control systems under cyber attacks with applications to power networks. In Proceedings of the 2010 American Control Conference, Baltimore, MD, USA, 30 June–2 July 2010; pp. 3690–3696. [Google Scholar]
- Pasqualetti, F. Secure Control Systems: A Control-Theoretic Approach to Cyber-Physical Security. 2012. Available online: http://www.fabiopas.it/PhD_Dissertation.pdf (accessed on 21 September 2020).
- Smith, R.S. Covert misappropriation of networked control systems: Presenting a feedback structure. IEEE Control Syst. Mag. 2015, 35, 82–92. [Google Scholar]
- Boem, F.; Gallo, A.J.; Ferrari-Trecate, G.; Parisini, T. A distributed attack detection method for multi-agent systems governed by consensus-based control. In Proceedings of the 2017 IEEE 56th Annual Conference on Decision and Control (CDC), Melbourne, Australia, 12–15 December 2017; pp. 5961–5966. [Google Scholar]
- Khan, A.S.; Khan, A.Q.; Iqbal, N.; Sarwar, M.; Mahmood, A.; Shoaib, M.A. Distributed fault detection and isolation in second order networked systems in a cyber-physical environment. ISA Trans. 2020, 103, 131–142. [Google Scholar] [CrossRef]
- Luo, X.; Yao, Q.; Wang, X.; Guan, X. Observer-based cyber attack detection and isolation in smart grids. Int. J. Electr. Power Energy Syst. 2018, 101, 127–138. [Google Scholar] [CrossRef]
- Jahanshahi, N.; Ferrari, R.M. Attack detection and estimation in cooperative vehicles platoons: A sliding mode observer approach. IFAC-PapersOnLine 2018, 51, 212–217. [Google Scholar] [CrossRef]
- Lemma, L.N.; Kim, S.H.; Choi, H.L. An unknown-input-observer based approach for cyber attack detection in formation flying UAVs. In Proceedings of the AIAA Infotech@ Aerospace, San Diego, CA, USA, 4–8 January 2016; p. 0916. [Google Scholar]
- Lv, M.; Yu, W.; Lv, Y.; Cao, J.; Huang, W. An integral sliding mode observer for CPS cyber security attack detection. Chaos Interdiscip. J. Nonlinear Sci. 2019, 29, 043120. [Google Scholar] [CrossRef]
- Sahoo, S.; Mishra, S.; Peng, J.C.H.; Dragičević, T. A Stealth Cyber-Attack Detection Strategy for DC Microgrids. IEEE Trans. Power Electron. 2018, 34, 8162–8174. [Google Scholar] [CrossRef]
- Sánchez-Torres, J.D.; Gómez-Gutiérrez, D.; López, E.; Loukianov, A.G. A class of predefined-time stable dynamical systems. IMA J. Math. Control Inf. 2018, 35, i1–i29. [Google Scholar] [CrossRef]
- Jadbabaie, A.; Lin, J.; Morse, A.S. Coordination of groups of mobile autonomous agents using nearest neighbor rules. IEEE Trans. Autom. Control 2003, 48, 988–1001. [Google Scholar] [CrossRef]
- Bhat, S.P.; Bernstein, D.S. Finite-time stability of continuous autonomous systems. SIAM J. Control Optim. 2000, 38, 751–766. [Google Scholar] [CrossRef]
- Polyakov, A. Nonlinear feedback design for fixed-time stabilization of linear control systems. IEEE Trans. Autom. Control 2011, 57, 2106–2110. [Google Scholar] [CrossRef]
- Aldana-López, R.; Gómez-Gutiérrez, D.; Jiménez-Rodríguez, E.; Sánchez-Torres, J.D.; Defoort, M. Enhancing the settling time estimation of a class of fixed-time stable systems. Int. J. Robust Nonlinear Control 2019, 29, 4135–4148. [Google Scholar] [CrossRef]
- Basile, G.; Marro, G. Controlled and Conditioned Invariants in Linear System Theory; Prentice Hall: Englewood Cliffs, NJ, USA, 1992. [Google Scholar]
- Ren, W.; Moore, K.L.; Chen, Y. High-order and model reference consensus algorithms in cooperative control of multivehicle systems. J. Dyn. Syst. Meas. Control 2007, 129, 678–688. [Google Scholar] [CrossRef]
- Ren, W.; Atkins, E. Distributed multi-vehicle coordinated control via local information exchange. Int. J. Robust Nonlinear Control 2007, 17, 1002–1033. [Google Scholar] [CrossRef]
- Jiang, F.; Wang, L. Consensus seeking of high-order dynamic multi-agent systems with fixed and switching topologies. Int. J. Control 2010, 83, 404–420. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).