Malicious PowerShell Detection Using Attention against Adversarial Attacks
Abstract
1. Introduction
2. Related Work
3. Adversarial Attacks on Deep Learning-Based Malicious PowerShell Detection
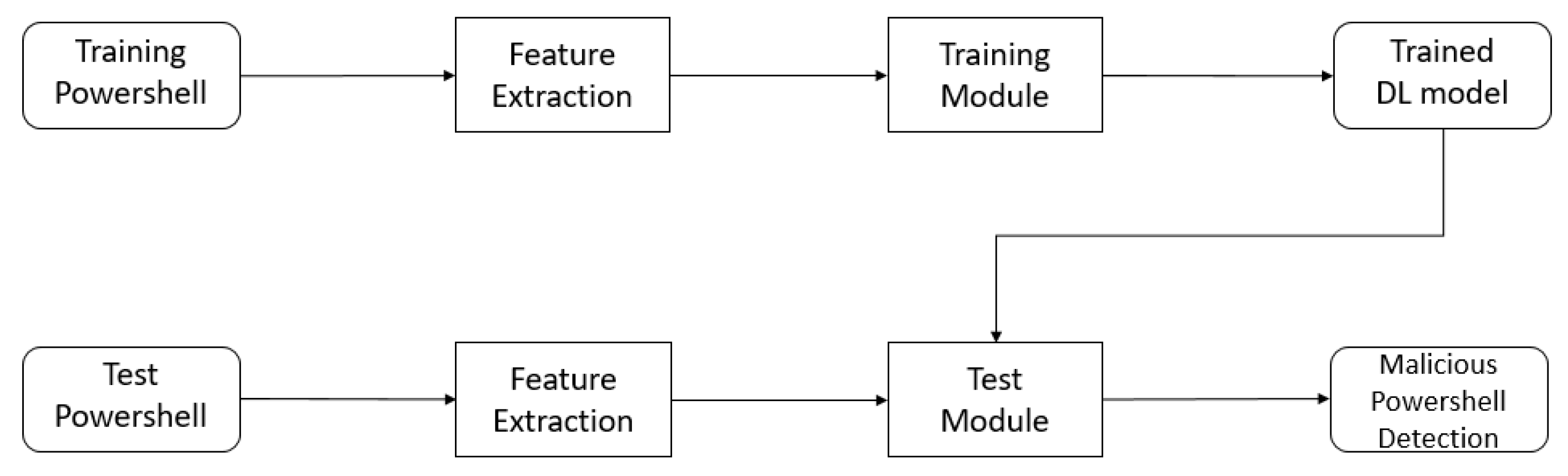
3.1. Deep Learning-Based Malicious PowerShell Detection
{Attribute, Command, CommandArgument, CommandParameter, Comment, GroupEnd, GroupStart, Keyword, LineContinuation, LoopLabel, Member, NewLine, Number, Operator, Position, StatementSeparator, String, Type, Unknown, Variable}
{Command, CommandArgument, CommandParameter, Keyword, Member, Variable}
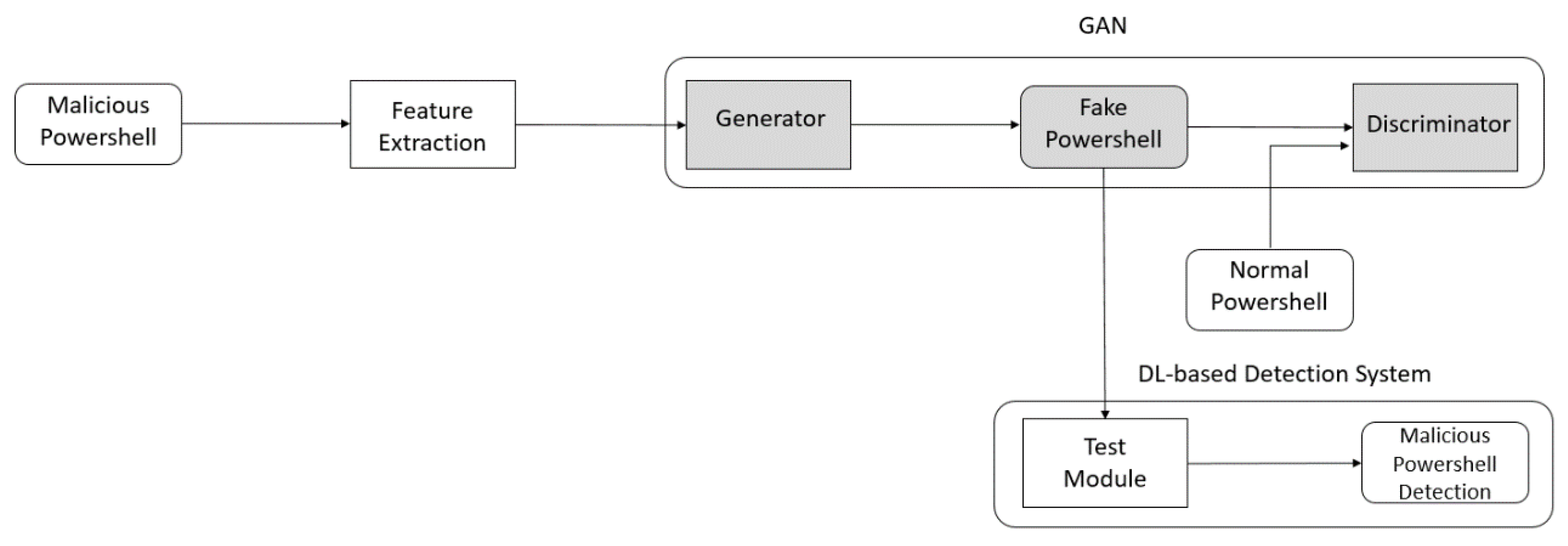
3.2. Adversarial Attack
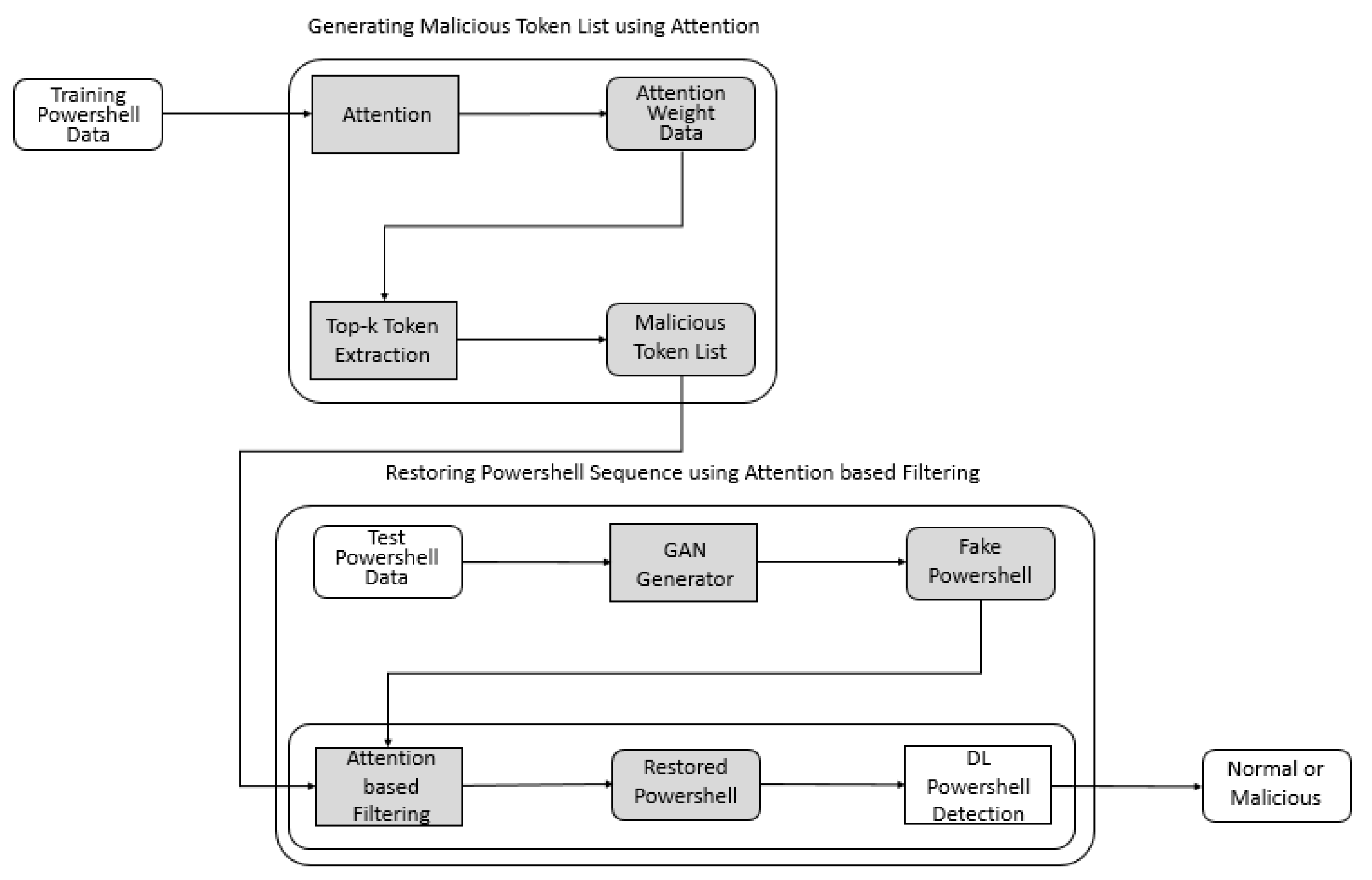
4. Malicious PowerShell Detection Using Attention against Adversarial Attacks
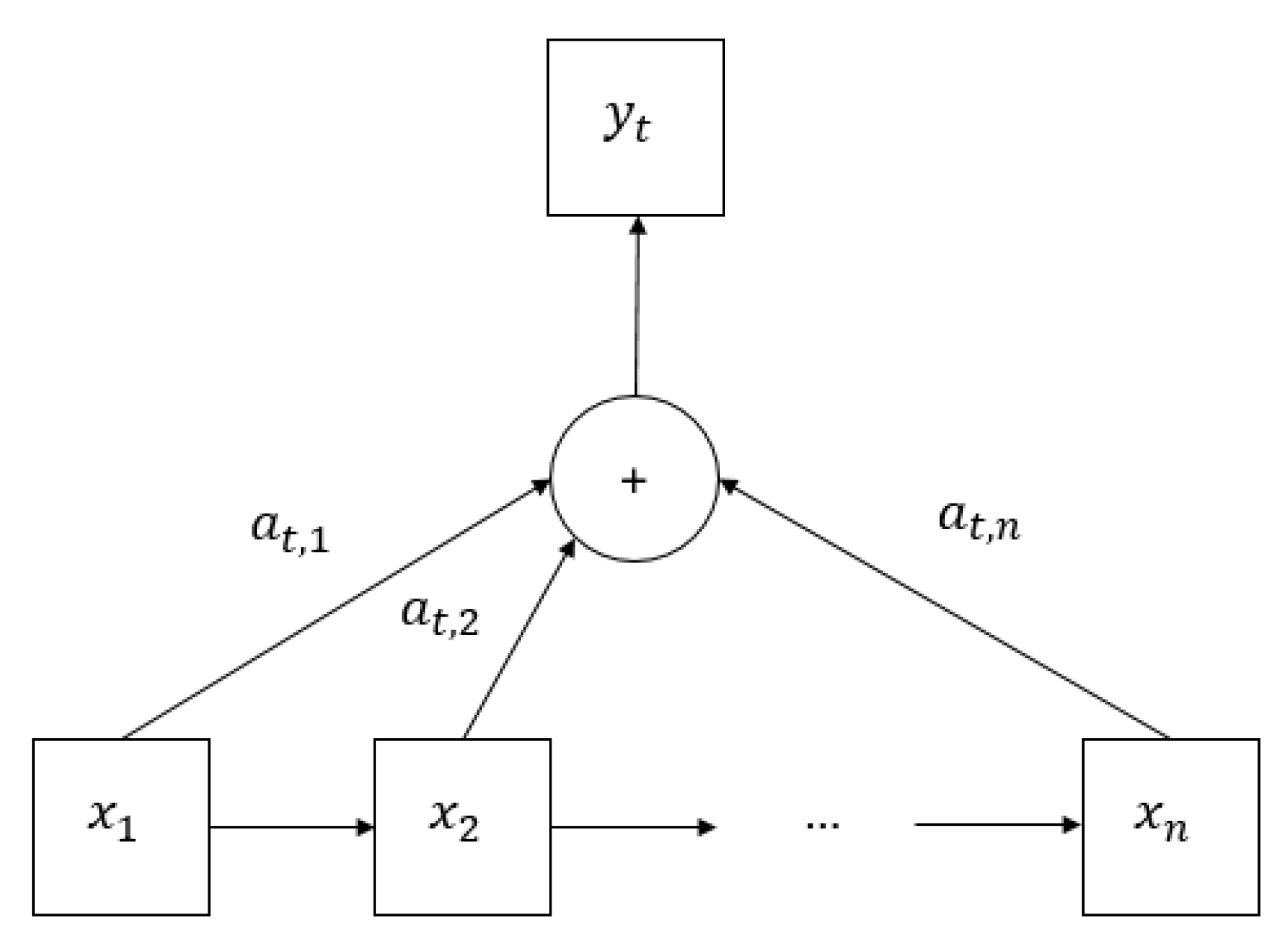
4.1. Attention
Russian defense minister Ivanov, called Sunday for the creation of a joint front to combat global terrorism
Russia called for a joint front for terrorism
4.2. Malicious PowerShell Detection Using Attention
{Normal_token_list, Malicious_token_list}
{Normal_only_token_list, Malicious_only_token_list, Common_token_list}
5. Experimental Results
5.1. Setup
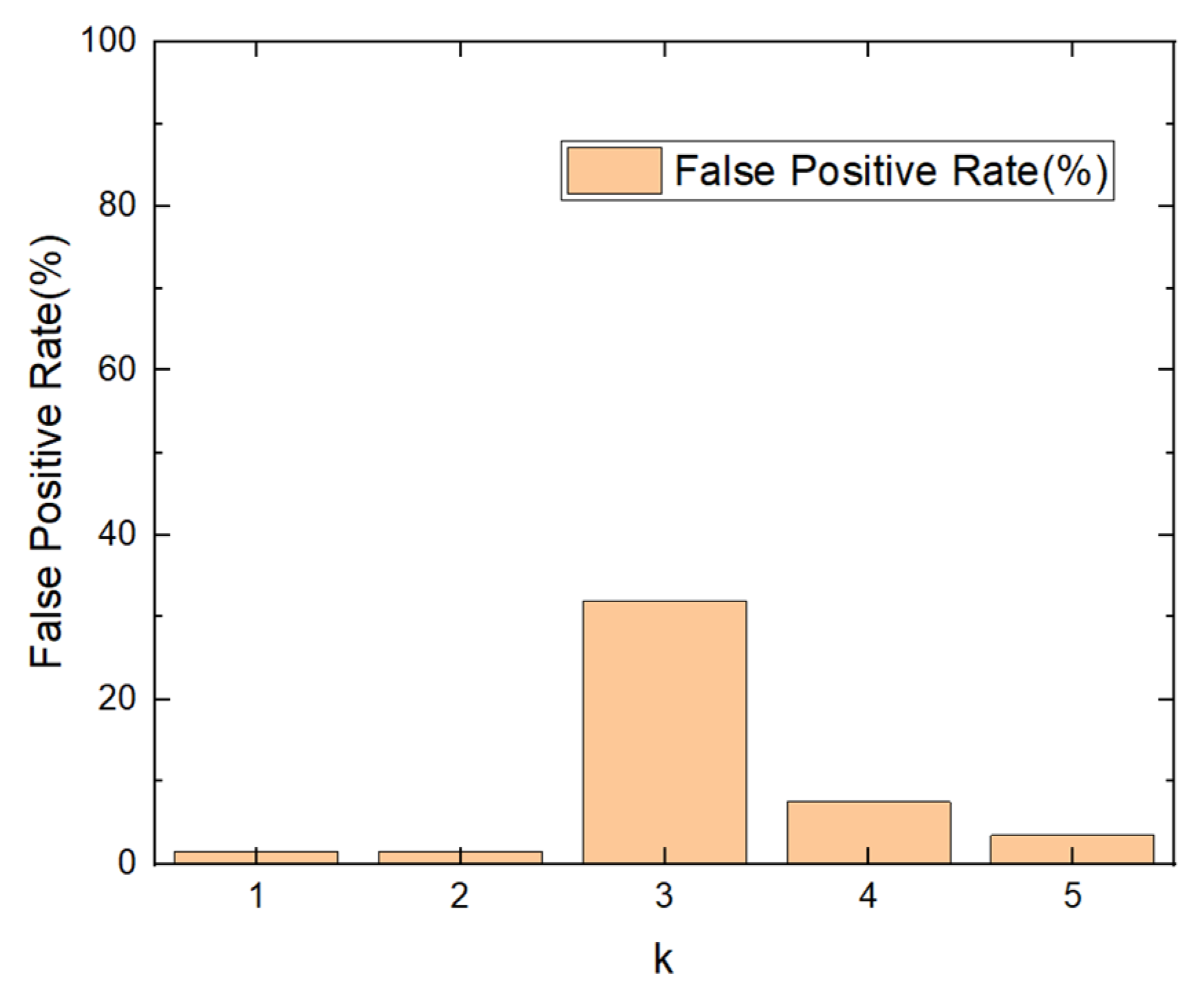
5.2. Performance Metric
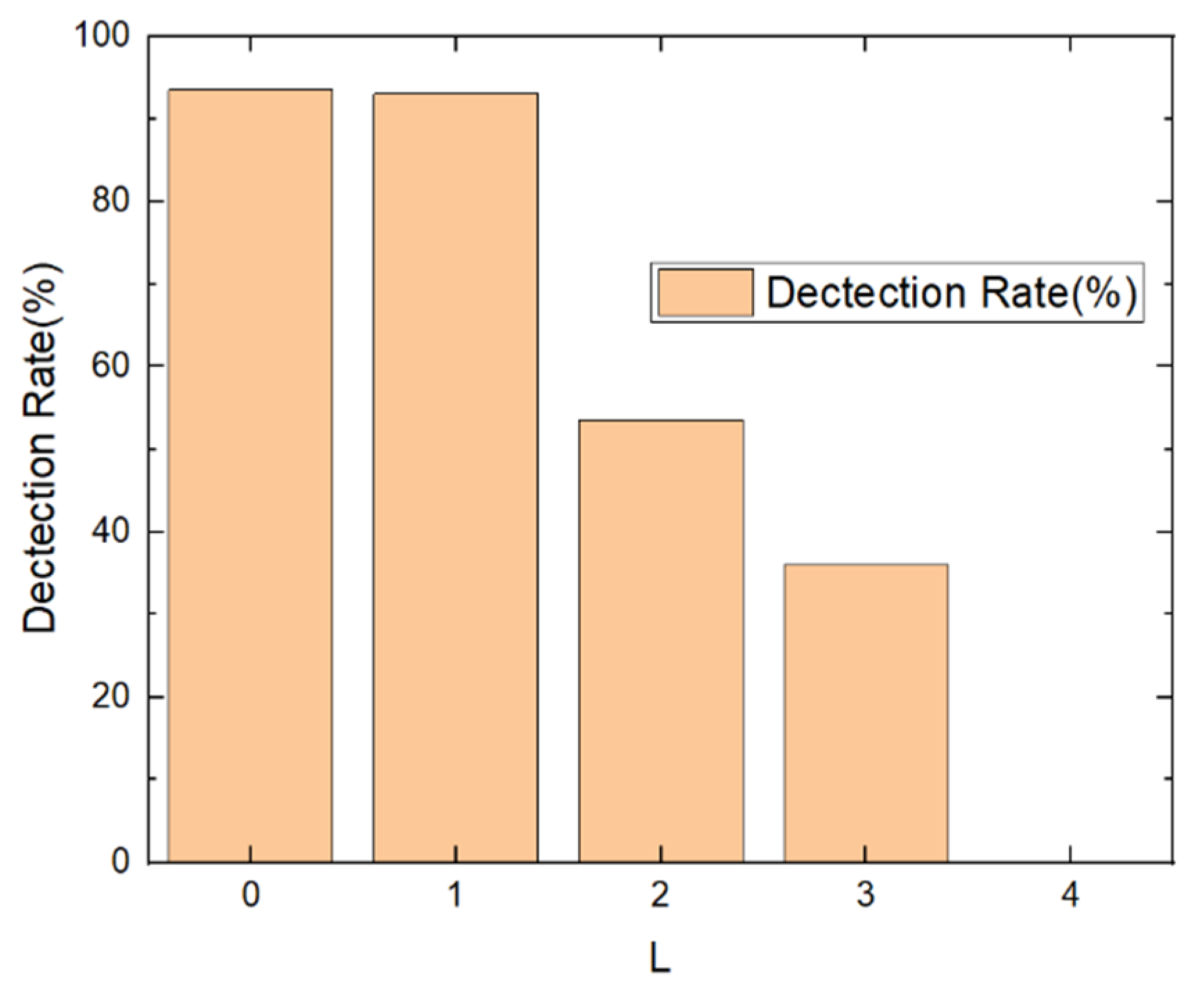
5.3. Adversarial Attack
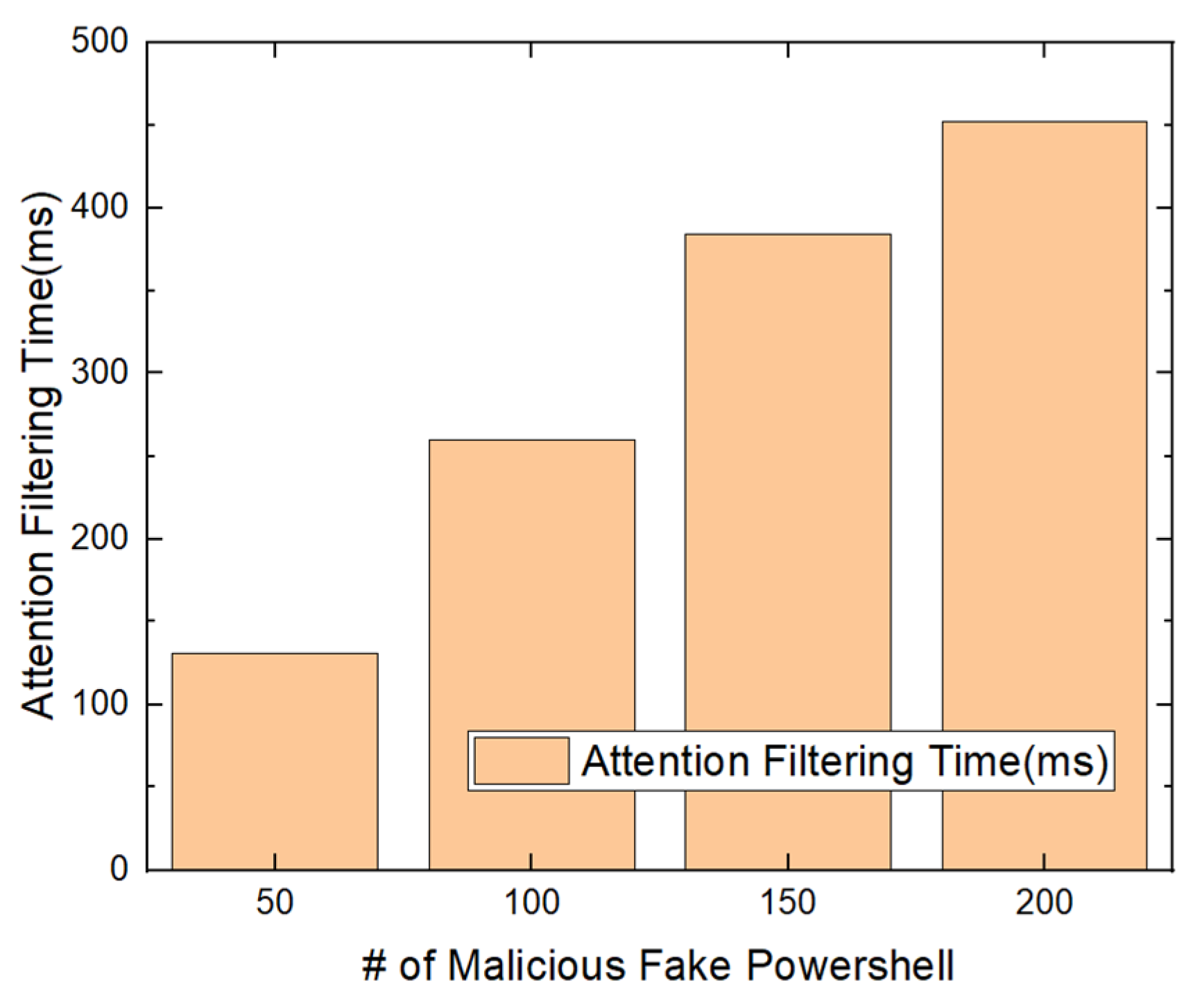
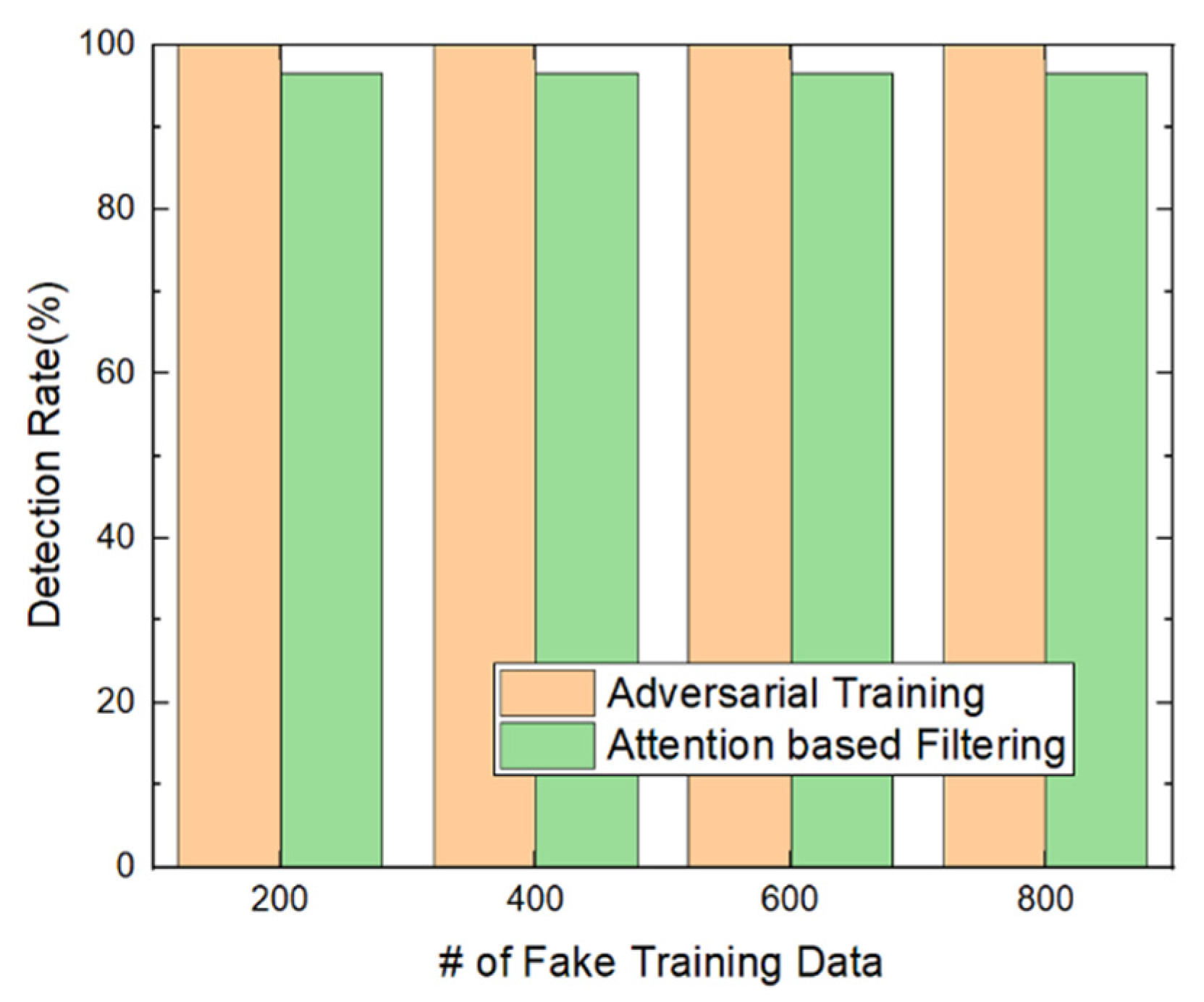
5.4. Malicious PowerShell Detection Using Attention against Adversarial Attack
6. Discussion
Funding
Conflicts of Interest
References
- AV-TEST. Available online: https://www.av-test.org (accessed on 9 September 2020).
- Gavrilut, D.; Cimpoesu, M.; Anton, D.; Ciortuz, L. Malware Detection Using Machine Learning. In Proceedings of the International Multiconference on Computer Science and Information Technology, Mragowo, Poland, 12–14 October 2009. [Google Scholar]
- Saxe, J.; Berlin, K. Deep Neural Network Based Malware Detection Using Two Dimensional Binary Program Features. In Proceedings of the International Conference on Malicious and Unwanted Software (MALWARE), Fajardo, PR, USA, 20–22 October 2015. [Google Scholar]
- Gibert, D. Convolutional Neural Networks for Malware Classification. Master’s Thesis, Universitat de Barcelona, Barcelona, Spain, 2016. [Google Scholar]
- Dahl, G.E.; Stokes, J.W.; Deng, L.; Yu, D. Large-Scale Malware Classification Using Random Projections and Neural Networks. In Proceedings of the International Conference on Acoustics, Speech and Signal Processing (ICASSP), Vancouver, BC, Canada, 26–31 May 2013. [Google Scholar]
- Pascanu, R.; Stokes, J.W.; Sanossian, H.; Marinescu, M.; Thomas, A. Malware Classification With Recurrent Networks. In Proceedings of the International Conference on Acoustics, Speech and Signal Processing (ICASSP), Brisbane, QLD, Australia, 19–24 April 2015. [Google Scholar]
- Huang, W.; Stokes, J.W. MtNet: A Multi-Task Neural Networks for Dynamic Malware Classification. In Proceedings of the International Conference on Detection of Intrusions and Malware and Vulnerability Assessment (DIMVA), San Sebastian, Spain, 7–8 July 2016. [Google Scholar]
- Ki, Y.; Kim, E.; Kim, H.K. A Novel approach to detect malware based on API call sequence analysis. Int. J. Distrib. Sens. Netw. 2015, 11, 659101. [Google Scholar] [CrossRef]
- Bae, J.; Lee, C.; Choi, S.; Kim, J. Malware Detection model with skip-connected LSTM RNN. J. Korean Inst. Inf. Sci. Eng. 2018, 45, 1233–1239. [Google Scholar] [CrossRef]
- Choi, S.; Bae, J.; Lee, C.; Kim, Y.; Kim, J. Attention-based automated feature extraction for malware analysis. Sensors 2020, 20, 2893. [Google Scholar] [CrossRef] [PubMed]
- Choi, S. Combined kNN Classification and hierarchical similarity hash for fast malware detection. Appl. Sci. 2020, 10, 5173. [Google Scholar] [CrossRef]
- Song, J.; Kim, J.; Choi, S.; Kim, J.; Kim, I. Implementation of a Static Powershell Analysis Based on the Cnn-Lstm Model With Token Optimizations. In Proceedings of the WISA Workshop, Jeju, Korea, 21–24 August 2019. [Google Scholar]
- Hendler, D.; Kels, S.; Rubin, A. Detecting Malicious Powershell Commands Using Deep Neural Networks. In Proceedings of the ACM ASIACCS, Incheon, Korea, 4–8 June 2018. [Google Scholar]
- Trendmicro. Emotet Uses Coronavirus Scare in Latest Campaign, Targets Japan. Available online: http://trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-thrests (accessed on 9 September 2020).
- Tokenizing PowerShell Scripts. Available online: http://powershell.one/powershell-internals/parsing-and-tokenization/simple-tokenizer (accessed on 8 September 2020).
- Goodfellow, I.J.; Abadie, J.P.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative Adversarial Nets. In Proceedings of the 28th Annual Conference on Neural Information Processing Systems NIPS, Montreal, QC, Canada, 8–13 December 2014. [Google Scholar]
- Grosse, K.; Papernot, N.; Manoharan, P.; Backes, M.; McDaniel, P. Adversarial Examples for Malware Detection. In Proceedings of the 22nd European Symposium on Research in Computer Security ESORICS, Oslo, Norway, 11–13 September 2017. [Google Scholar]
- Hu, W.; Tan, Y. Black-box attacks against RNN Based Malware Detection Algorithms. In Proceedings of the Workshops of the Thirty-Second AAAI Conference on Artificial Intelligence, New Orleans, LA, USA, 2–7 February 2018. [Google Scholar]
- Rush, A.M.; Harvard, S.E.A.S.; Chopra, S.; Weston, J. A neural Attention Model for Sentence Summarization. In Proceedings of the Conference on Empirical Methods in Natural Language Processing EMNLP, Lisbon, Portugal, 17–21 September 2015. [Google Scholar]
- Kendall, K.; McMillan, C. Practical Malware Analysis; BlackHat: Las Vegas, NV, USA, 2007. [Google Scholar]
- Moser, A.; Kruegel, C.; Kirda, E. Limits of Static Analysis for Malware Detection. In Proceedings of the 23rd IEEE International Conference on Computer Security and Applications, Miami Beach, FL, USA, 10–14 December 2007; pp. 421–430. [Google Scholar]
- Goodfellow, I.J.; Shlens, J.; Szegedy, C. Explaining and Harnessing Adversarial Examples. In Proceedings of the 3rd International Conference on Learning Representations ICLR, San Diego, CA, USA, 7–9 May 2015. [Google Scholar]
- Papernot, N.; McDaniel, P.; Wu, X.; Jha, S.; Swami, A. Distillation As a Defense to Adversarial Perturbations Against Deep Neural Networks. In Proceedings of the IEEE Symposium on Security and Privacy Workshop, San Jose, CA, USA, 23–25 May 2016. [Google Scholar]
- Samangouei, P.; Kabkab, M.; Chellappa, R. DEFENSE-GAN: Protecting Classifiers Against Adversarial Attacks Using Generative Models. In Proceedings of the 6th International Conference on Learning Representations ICLR, Vancouver, BC, Canada, 30 April–3 May 2018. [Google Scholar]
- Krizhevsky, A.; Sutskever, I.; Hinton, G. ImageNet Classification With Deep Convolutional Neural Networks. In Proceedings of the International Conference on Neural Information Processing Systems, Lake Tahoe, CA, USA, 3–6 December 2012. [Google Scholar]
- Jones, K. GANGogh: Creating Art with GANS. Available online: http://towardsdatascience.com/gangogh-creating-art-with-gans-8d087d8f74a1 (accessed on 9 September 2020).
- Engel, J. GANSynth: Making Music with GANS. Available online: http://magenta.tensorflow.org/gansynth (accessed on 1 November 2020).
- Understanding LSTM Networks. Available online: https://colah.github.io/posts/2015-08-Understanding-LSTMs/ (accessed on 27 July 2020).
- Bahdanau, D.; Cho, K.; Bengio, Y. Neural Machine Translation by Jointly Learning to Align and Translate. In Proceedings of the 6th International Conference on Learning Representations, San Diego, CA, USA, 7–9 May 2015. [Google Scholar]
- Information Security Research Division, Electronics and Telecommunications Research Institute (ETRI). Available online: http://etri.re.kr (accessed on 9 September 2020).
- N-fold Cross Validation. Available online: https://en.wikipedia.org/wiki/Cross-validation_(statistics) (accessed on 9 September 2020).
- Keras. Available online: http://keras.io (accessed on 9 September 2020).
- Antivirus Performance Comparisons. Available online: http://sharedit.co.kr/posts/424 (accessed on 5 October 2020).
- Lin, Z.; Xue, Z.; Shi, Y. IDSGAN: Generative adversarial networks for attack generation against intrusion detection. arXiv 2018, arXiv:1809.02077. [Google Scholar]





| Reference | File Type | Feature Extraction | Malware Detection | Year |
|---|---|---|---|---|
| [3] | PE | Static | DNN | 2015 |
| [4] | PE | Static | CNN | 2016 |
| [5] | PE | Dynamic | DNN | 2013 |
| [6] | PE | Dynamic | RNN | 2015 |
| [7] | PE | Dynamic | DNN | 2016 |
| [8] | PE | Dynamic | LCS | 2015 |
| [9] | PE | Static | SC-LSTM | 2018 |
| [10] | PE | Static | Attention | 2020 |
| [11] | PE | Static | TLSH + LSTM | 2020 |
| [12] | PowerShell | Static | CNN + LSTM | 2019 |
| [13] | PowerShell | Static | CNN | 2018 |
| Name | Specification |
|---|---|
| OS | Windows 10 Pro |
| CPU | Intel i7 2.2 GHz |
| RAM | 16 GB |
| GPU | GeForce RTX 2060 |
| Cuda | 8.0 |
| - | Malware | Normal File |
|---|---|---|
| Predicted Malware | TP | FP |
| Predicted Normal File | FN | TN |
| Top-1 | Top-2 | Top-3 | Top-4 | Top-5 | |
|---|---|---|---|---|---|
| Size of Malicious Only Token List | 93 | 165 | 183 | 213 | 233 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Choi, S. Malicious PowerShell Detection Using Attention against Adversarial Attacks. Electronics 2020, 9, 1817. https://doi.org/10.3390/electronics9111817
Choi S. Malicious PowerShell Detection Using Attention against Adversarial Attacks. Electronics. 2020; 9(11):1817. https://doi.org/10.3390/electronics9111817
Chicago/Turabian StyleChoi, Sunoh. 2020. "Malicious PowerShell Detection Using Attention against Adversarial Attacks" Electronics 9, no. 11: 1817. https://doi.org/10.3390/electronics9111817
APA StyleChoi, S. (2020). Malicious PowerShell Detection Using Attention against Adversarial Attacks. Electronics, 9(11), 1817. https://doi.org/10.3390/electronics9111817




