Slicing the Core Network and Radio Access Network Domains through Intent-Based Networking for 5G Networks
Abstract
1. Introduction
- An intent-driven approach for the automated E2E slice configuration and the resource orchestration is the main contribution of our system. It induces a generic mechanism that can orchestrate resources at multiple domains. Additionally, it abstracts the underlying platforms and enables the configuration of different vendor-specific platforms. A few of the example platforms are CORD, OSM, and FlexRAN. Additionally, The best thing about this mechanism is that it eliminates the manual effort of work for creating, updating, and deleting network slices. Hence, it completely automates the lifecycle management of network services while keeping the IETF standard-based intent lifecycle mechanism.
- For the lifecycle management of intents, continuous monitoring is essential. Hence, while having been limited to open-source platforms this system introduced the monitoring and management of both the access and core network resources.
- The standards for network automation insist on introducing intelligence into different domains of the networks. Hence, AI-driven slice resource assurance is achieved by using the GAN deep learning model.
2. Related Work
2.1. Intent-Based Networking (IBN)
2.2. End-to-End Network Slicing
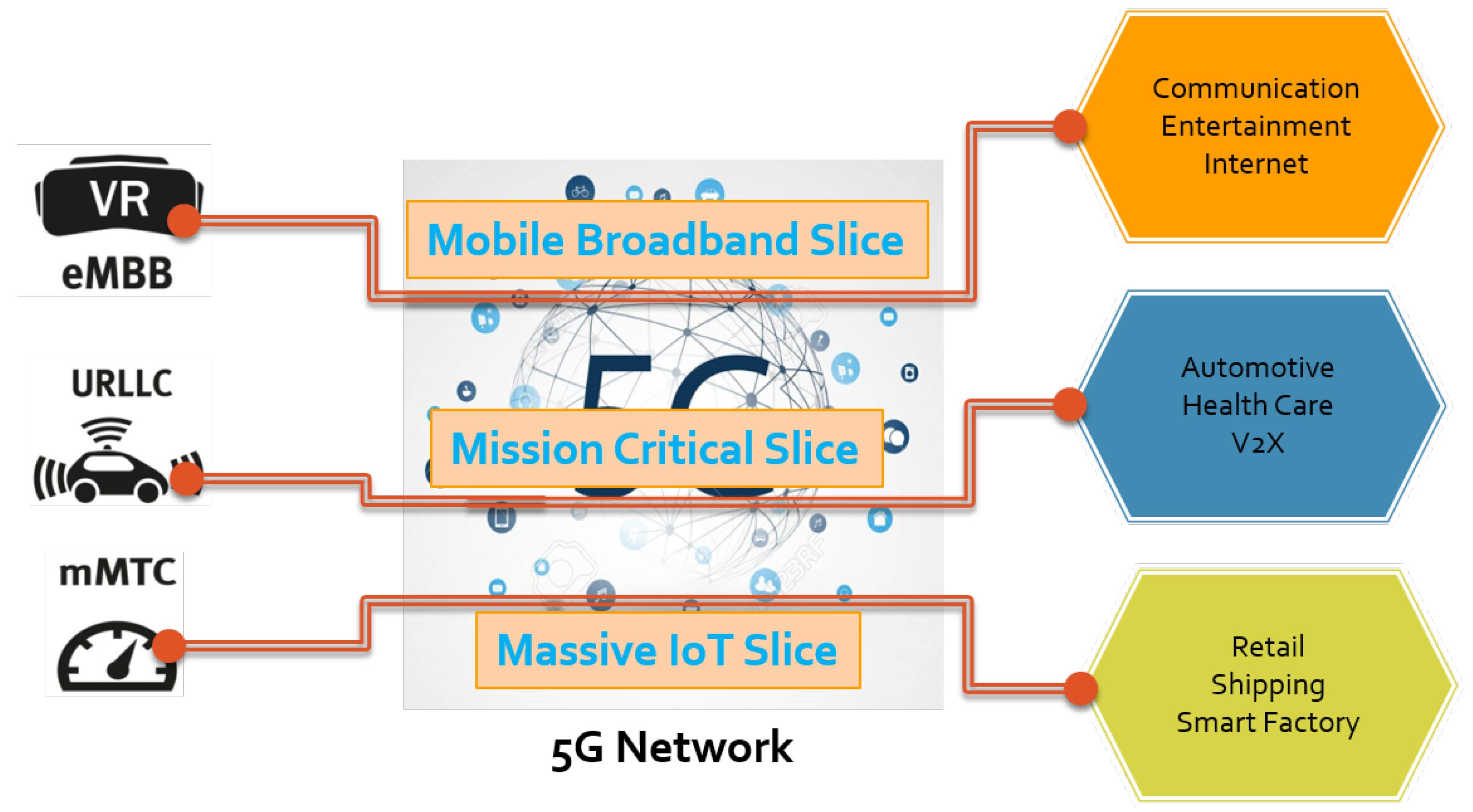
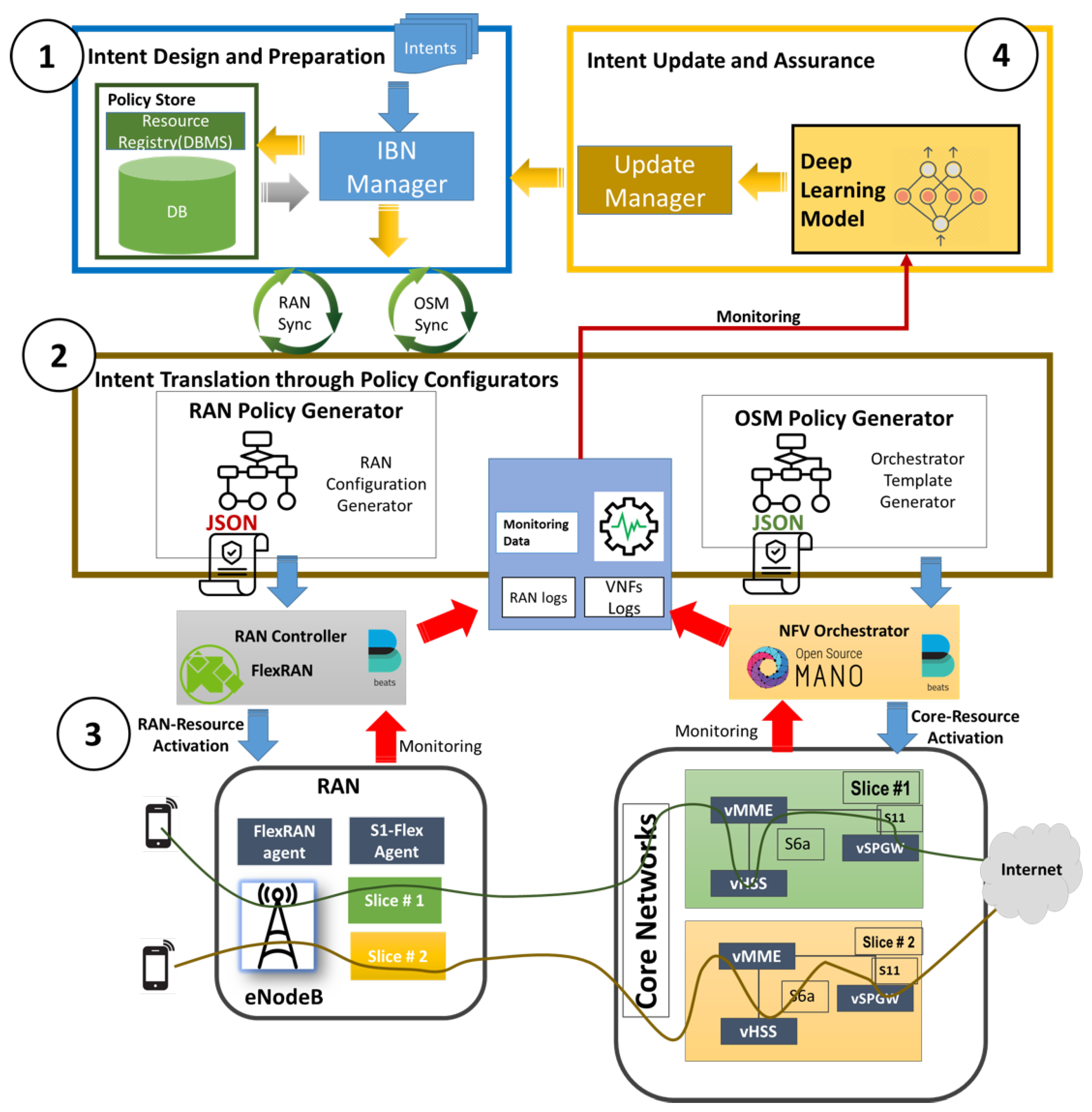
3. Design and Architecture of the Network Slicing System
4. Major Components of Network Slicing System
4.1. Open Source Mano (OSM)
4.2. Intent-Based Networking (IBN) Tool
4.2.1. User Intents/Contract Design
4.2.2. Intent Manager
4.2.3. Policy Store
4.2.4. OSM Policy Configurator
4.2.5. RAN Policy Configurator
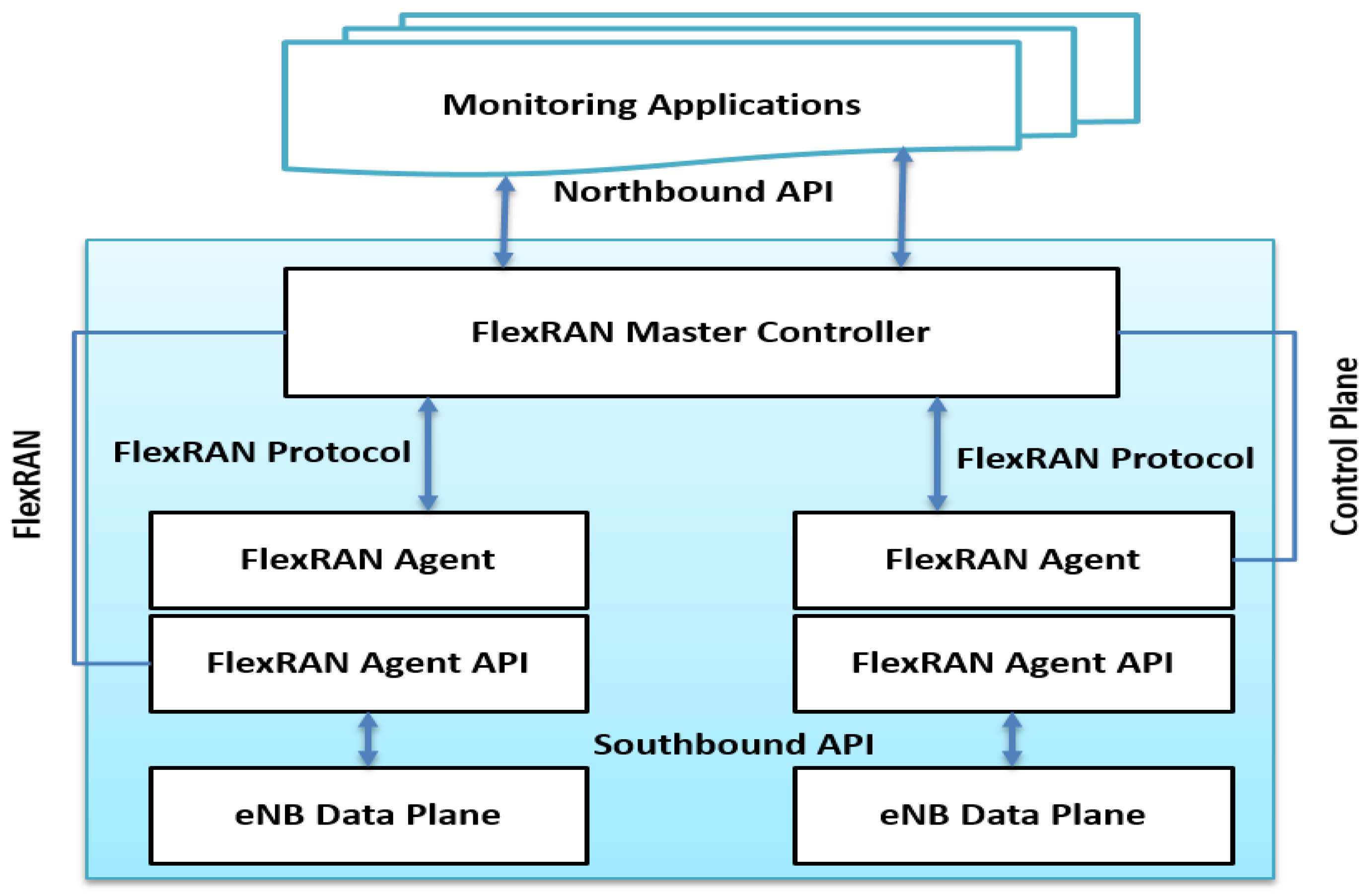
4.3. SDN Controller FLEXRAN for Ran Slicing
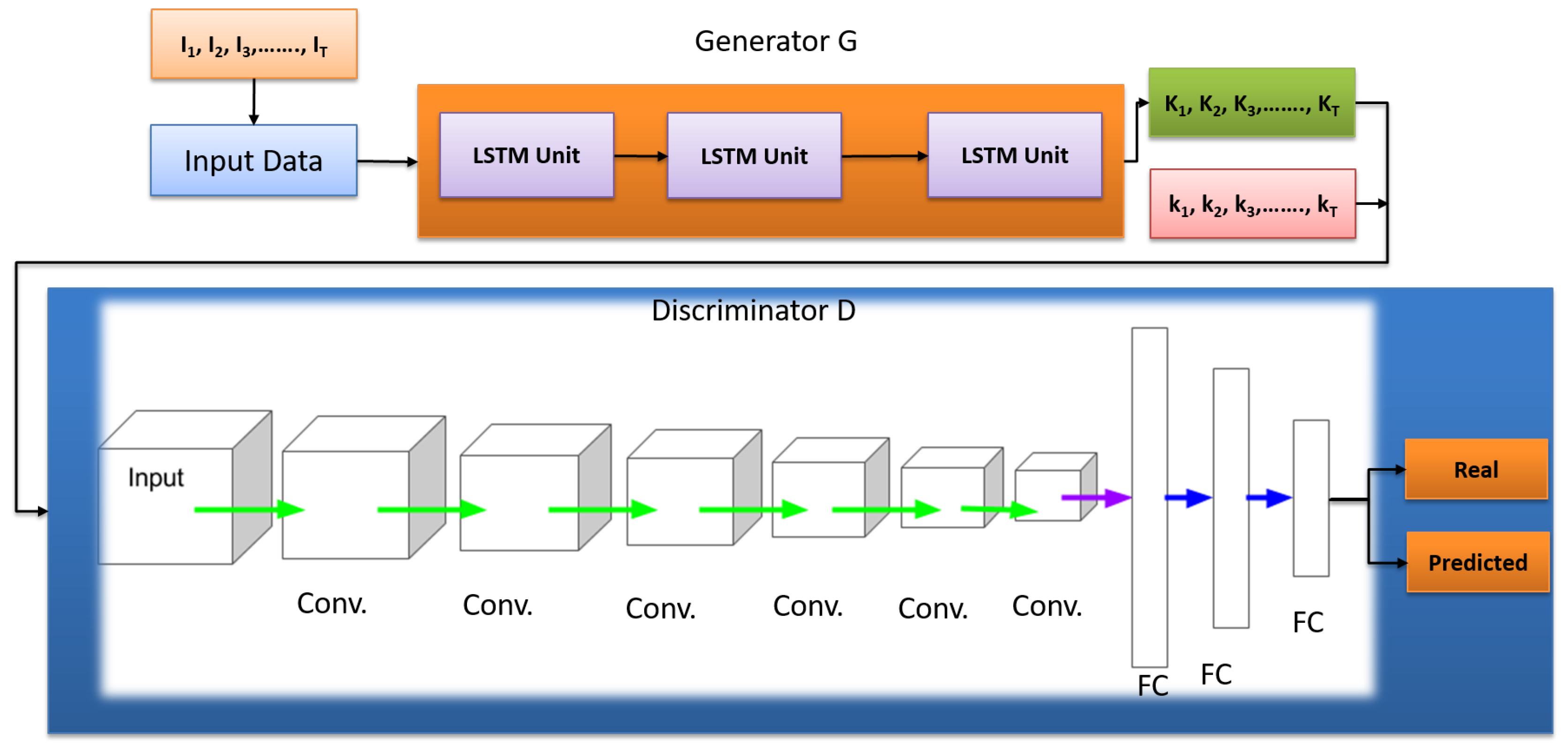
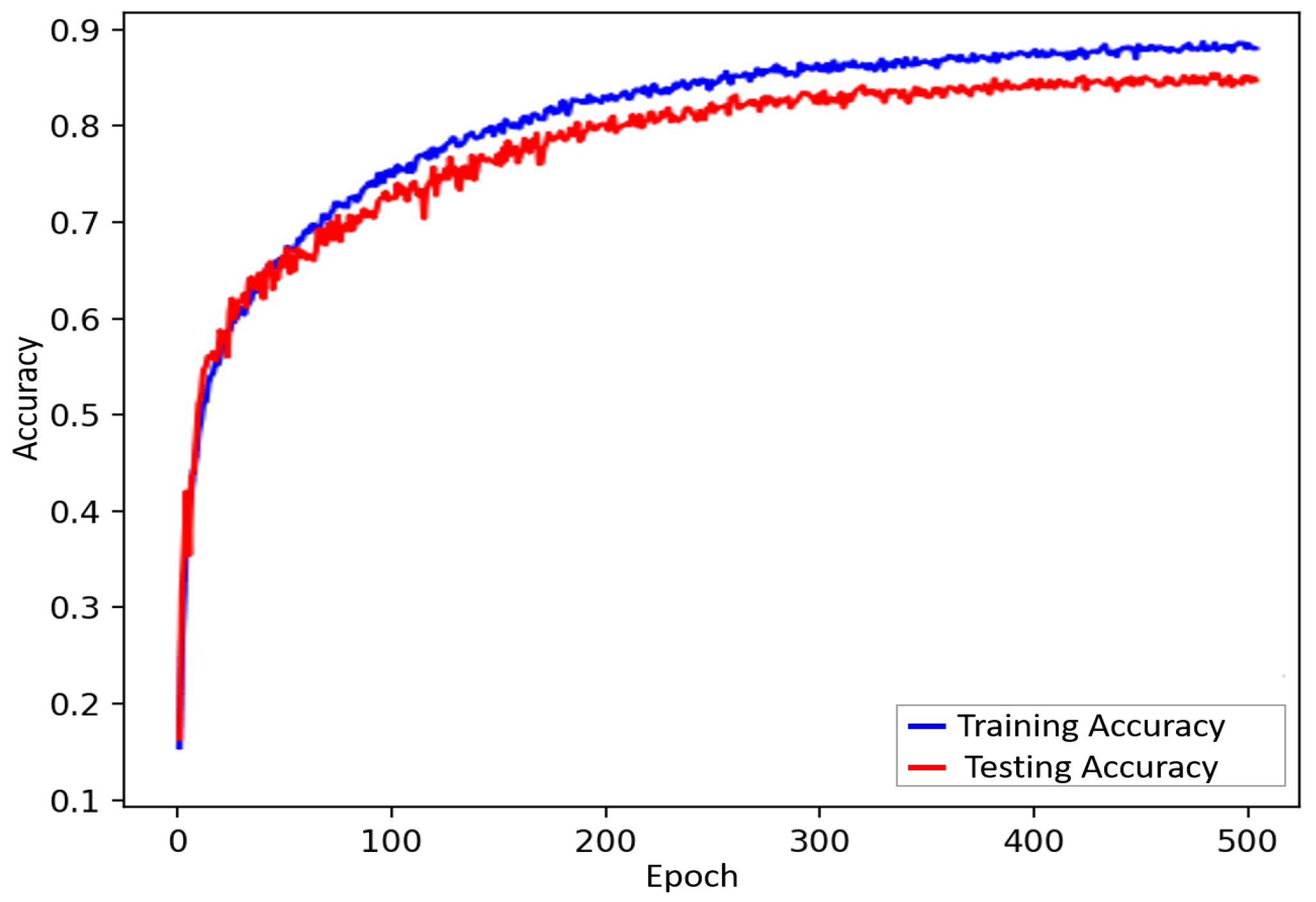
4.4. Advanced Deep Learning Module
| Algorithm 1 Pseudo-code for the generative adversarial network (GAN) model. |
|
| Algorithm 2 Pseudo-code for the training of Generator and Discriminator. |
|
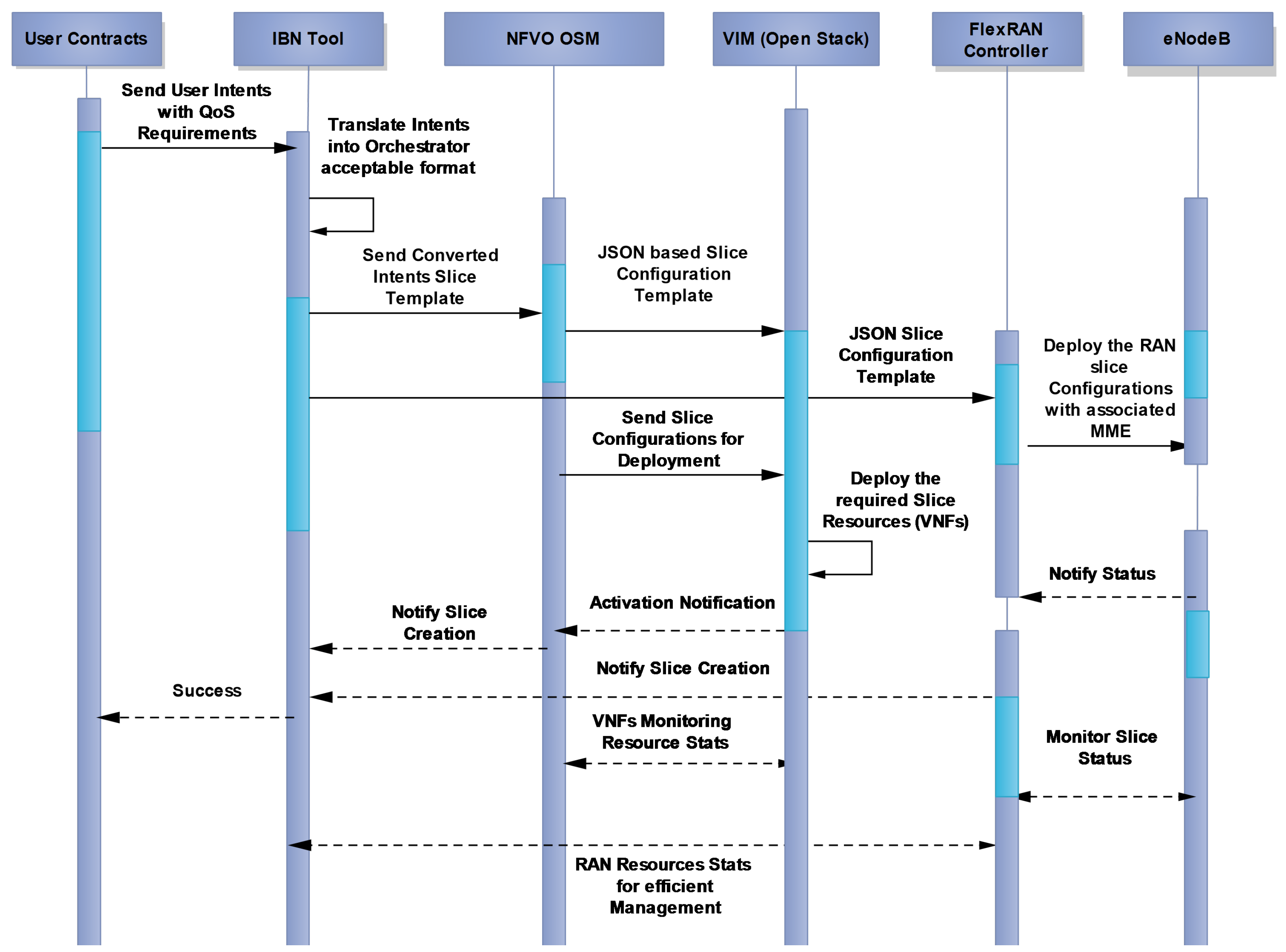
5. Radio Access Network Slice Instantiation Process
6. Experimental Test-Bed Implementation
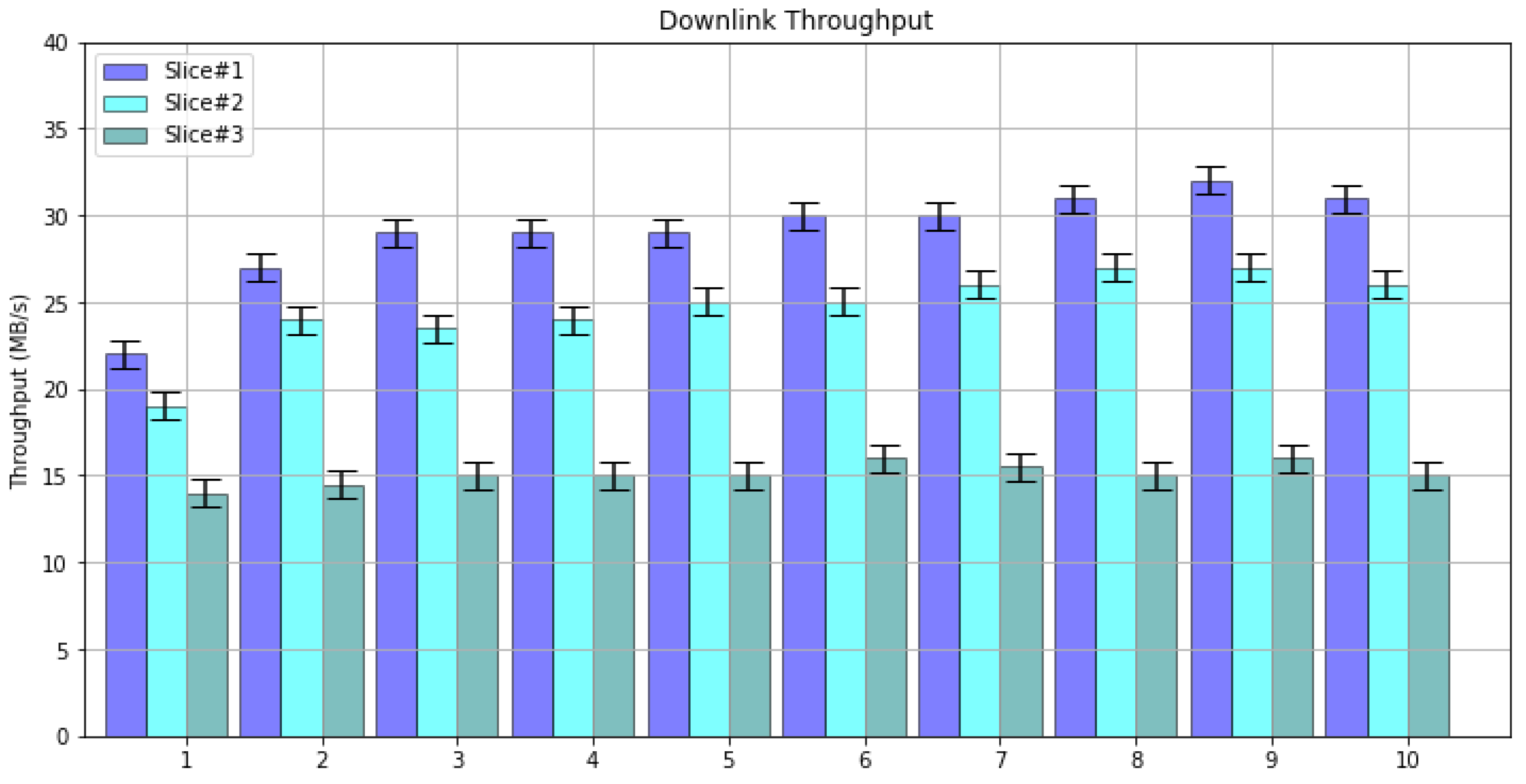
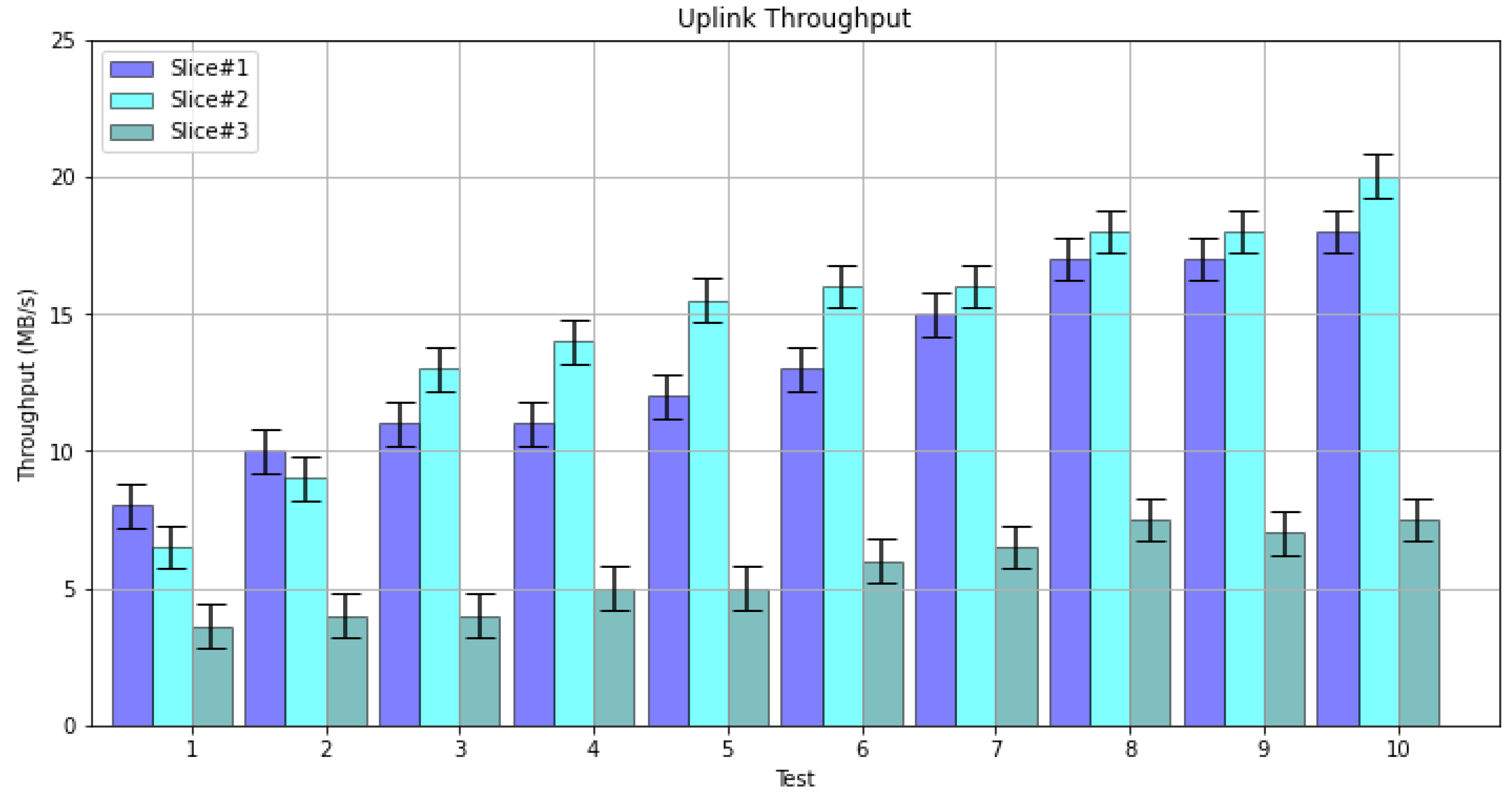
7. Experimental Results
8. Discussion
9. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| 3GPP | Third Generation Partnership Project |
| 5GPP | Fifth Generation partnership Project |
| IBN | Intent Based Networking |
| LTE | Long-Term Evolution |
| EPC | Evolved Packet Core |
| RAN | Radio Access Network |
| SDN | Third Generation Partnership Project |
| NFV | Network Function Virtualization |
| VNFs | Virtual Network Functions |
| GAN | Generative Adversarial Network |
| OSM | Open Source MANO |
| VIM | Virtual Infrastructure Manager |
| VNFM | VNF Manager |
| OAI | OpenAirInterface |
| DL | Deep Learning |
| IETF | Internet Engineering Task Force |
| SDR | Software Defined Radio |
References
- Katsalis, K.; Nikaein, N.; Schiller, E.; Ksentini, A.; Braun, T. Network slices toward 5G communications: Slicing the LTE network. IEEE Commun. Mag. 2017, 55, 146–154. [Google Scholar] [CrossRef]
- Afolabi, I.; Taleb, T.; Frangoudis, P.A.; Bagaa, M.; Ksentini, A. Network Slicing-Based Customization of 5G Mobile Services. IEEE Netw. 2019, 33, 134–141. [Google Scholar] [CrossRef]
- Abbas, K.; Afaq, M.; Ahmed Khan, T.; Rafiq, A.; Iqbal, J.; Ul Islam, I.; Song, W.C. An efficient SDN-based LTE-WiFi spectrum aggregation system for heterogeneous 5G networks. Trans. Emerg. Telecommun. Technol. 2020, e3943. [Google Scholar] [CrossRef]
- Abbas, K.; Ahmed, K.T.; Rafiq, A.; Song, W.C.; Seok, S.J. An LTE-WiFi Spectrum Aggregation System for 5G Network: A Testbed. In Proceedings of the IEEE 2020 International Conference on Information Networking (ICOIN), Barcelona, Spain, 7–10 January 2020; pp. 753–755. [Google Scholar]
- Saqib, M.; Khan, F.Z.; Ahmed, M.; Mehmood, R.M. A critical review on security approaches to software-defined wireless sensor networking. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719889906. [Google Scholar] [CrossRef]
- Li, X.; Ni, R.; Chen, J.; Lyu, Y.; Rong, Z.; Du, R. End-to-End Network Slicing in Radio Access Network, Transport Network and Core Network Domains. IEEE Access 2020, 8, 29525–29537. [Google Scholar] [CrossRef]
- Pang, L.; Yang, C.; Chen, D.; Song, Y.; Guizani, M. A survey on intent-driven networks. IEEE Access 2020, 8, 22862–22873. [Google Scholar] [CrossRef]
- Wei, Y.; Peng, M.; Liu, Y. Intent-based networks for 6G: Insights and challenges. Digit. Commun. Netw. 2020, 6, 270–280. [Google Scholar] [CrossRef]
- Zeydan, E.; Turk, Y. Recent Advances in Intent-Based Networking: A Survey. In Proceedings of the 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), Antwerp, Belgium, 25–28 May 2020; pp. 1–5. [Google Scholar]
- IETF. Intent-Based Networking. Available online: https://tools.ietf.org/html/draft-irtf-nmrg-ibn-concepts-definitions-01 (accessed on 12 August 2020).
- Cisco. Intent-Based Networking. Available online: https://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise-networks/digital-network-architecture/nb-09-intent-networking-wp-cte-en.pdf (accessed on 10 August 2020).
- Huawei. Intent-Driven Network. Available online: https://carrier.huawei.com/~/media/CNBG/Downloads/Spotlight/all-cloud-network-towards-5g/idn-en.pdf (accessed on 3 July 2020).
- Fossati, F.; Moretti, S.; Perny, P.; Secci, S. Multi-resource allocation for network slicing. IEEE/ACM Trans. Netw. 2020, 28, 1311–1324. [Google Scholar] [CrossRef]
- Shen, X.; Gao, J.; Wu, W.; Lyu, K.; Li, M.; Zhuang, W.; Li, X.; Rao, J. AI-assisted network-slicing based next-generation wireless networks. IEEE Open J. Veh. Technol. 2020, 1, 45–66. [Google Scholar] [CrossRef]
- Khan, P.W.; Abbas, K.; Shaiba, H.; Muthanna, A.; Abuarqoub, A.; Khayyat, M. Energy Efficient Computation Offloading Mechanism in Multi-Server Mobile Edge Computing—An Integer Linear Optimization Approach. Electronics 2020, 9, 1010. [Google Scholar] [CrossRef]
- Devlic, A.; Hamidian, A.; Liang, D.; Eriksson, M.; Consoli, A.; Lundstedt, J. NESMO: Network slicing management and orchestration framework. In Proceedings of the 2017 IEEE International Conference on Communications Workshops (ICC Workshops), Paris, France, 21–25 May 2017; pp. 1202–1208. [Google Scholar]
- Afaq, M.; Iqbal, J.; Ahmed, T.; Islam, I.U.; Khan, M.; Khan, M.S. Towards 5G network slicing for vehicular ad-hoc networks: An end-to-end approach. Comput. Commun. 2020, 149, 252–258. [Google Scholar] [CrossRef]
- OSM. Open Source Mano. Available online: https://osm-download.etsi.org/ftp/Documentation/201902-osm-scope-white-paper/#!02-osm-scope-and-functionality.md (accessed on 5 June 2020).
- ONAP. ONAP: Open Networking Automation Platform. Available online: https://www.onap.org/ (accessed on 5 June 2020).
- Cloudify. Cloudify: A Open Source Network Orchestrator. Available online: https://cloudify.co/ (accessed on 6 June 2020).
- OpenBaton. OpenBaton: NFV MANO-Based Framework. Available online: https://openbaton.github.io/ (accessed on 6 June 2020).
- Katsalis, K.; Nikaein, N.; Huang, A. JOX: An event-driven orchestrator for 5G network slicing. In Proceedings of the NOMS 2018-2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018; pp. 1–9. [Google Scholar]
- Mosaic5G. Network Sharing Using FlexRAN. Available online: http://mosaic5g.io/flexran/ (accessed on 10 October 2020).
- Meneses, F.; Fernandes, M.; Corujo, D.; Aguiar, R.L. SliMANO: An expandable framework for the management and orchestration of end-to-end network slices. In Proceedings of the 2019 IEEE 8th International Conference on Cloud Networking (CloudNet), Coimbra, Portugal, 4–6 November 2019; pp. 1–6. [Google Scholar]
- Materna. Dataset. Available online: http://gwa.ewi.tudelft.nl/datasets/gwa-t-13-materna/ (accessed on 2 October 2020).
- Ferrus, R.; Sallent, O.; Pérez-Romero, J.; Agusti, R. On 5G radio access network slicing: Radio interface protocol features and configuration. IEEE Commun. Mag. 2018, 56, 184–192. [Google Scholar] [CrossRef]
- Ferrús, R.; Sallent, O.; Pérez-Romero, J.; Agusti, R. On the automation of RAN slicing provisioning and cell planning in NG-RAN. In Proceedings of the 2018 European Conference on Networks and Communications (EuCNC), Ljubljana, Slovenia, 18–21 June 2018; pp. 37–42. [Google Scholar]
- Elayoubi, S.E.; Jemaa, S.B.; Altman, Z.; Galindo-Serrano, A. 5G RAN slicing for verticals: Enablers and challenges. IEEE Commun. Mag. 2019, 57, 28–34. [Google Scholar] [CrossRef]
- Du, P.; Nakao, A. Understanding Intelligent RAN Slicing for Future Mobile Networks Through Field Test. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; pp. 1–6. [Google Scholar]
- Albonda, H.D.R.; Pérez-Romero, J. An efficient RAN slicing strategy for a heterogeneous network with eMBB and V2X services. IEEE Access 2019, 7, 44771–44782. [Google Scholar] [CrossRef]
- Sciancalepore, V.; Di Renzo, M.; Costa-Perez, X. STORNS: Stochastic radio access network slicing. In Proceedings of the ICC 2019-2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar]
- Xiang, H.; Peng, M.; Sun, Y.; Yan, S. Mode Selection and Resource Allocation in Sliced Fog Radio Access Networks: A Reinforcement Learning Approach. IEEE Trans. Veh. Technol. 2020, 69, 4271–4284. [Google Scholar] [CrossRef]
- Marabissi, D.; Fantacci, R. Heterogeneous public safety network architecture based on RAN slicing. IEEE Access 2017, 5, 24668–24677. [Google Scholar] [CrossRef]
- Popovski, P.; Trillingsgaard, K.F.; Simeone, O.; Durisi, G. 5G wireless network slicing for eMBB, URLLC, and mMTC: A communication-theoretic view. IEEE Access 2018, 6, 55765–55779. [Google Scholar] [CrossRef]
- Yan, M.; Feng, G.; Zhou, J.; Sun, Y.; Liang, Y.C. Intelligent resource scheduling for 5G radio access network slicing. IEEE Trans. Veh. Technol. 2019, 68, 7691–7703. [Google Scholar] [CrossRef]
- Xiang, H.; Yan, S.; Peng, M. A realization of fog-RAN slicing via deep reinforcement learning. IEEE Trans. Wirel. Commun. 2020, 19, 2515–2527. [Google Scholar] [CrossRef]
- Raza, M.R.; Natalino, C.; Öhlen, P.; Wosinska, L.; Monti, P. Reinforcement learning for slicing in a 5G flexible RAN. J. Light. Technol. 2019, 37, 5161–5169. [Google Scholar] [CrossRef]
- Rafiq, A.; Mehmood, A.; Ahmed Khan, T.; Abbas, K.; Afaq, M.; Wang Cheol, S. Intent-Based End-to-End Network Service Orchestration System for Multi-Platforms. Sustainability 2020, 12, 2782. [Google Scholar] [CrossRef]
- Khan, T.A.; Mehmood, A.; Rivera, J.J.D.; Song, W.C. Machine Learning Approach for Automatic Configuration and Management of 5G Platforms. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; pp. 1–6. [Google Scholar]
- Khan, T.A.; Mehmood, A.; Ravera, J.J.D.; Muhammad, A.; Abbas, K.; Song, W.C. Intent-Based Orchestration of Network Slices and Resource Assurance using Machine Learning. In Proceedings of the NOMS 2020-2020 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 20–24 April 2020; pp. 1–2. [Google Scholar]
- Khan, T.A.; Afaq, M.; Abbas, K.; Rafiq, A.; Mehmood, A.; Song, W.C. Generic Intent-Based Networking approach for end-to-end Slice Orchestration and Lifecycle Management. 한국통신학회 학술대회논문집 2020, 468–469. [Google Scholar]
- Foukas, X.; Nikaein, N.; Kassem, M.M.; Marina, M.K.; Kontovasilis, K. FlexRAN: A flexible and programmable platform for software-defined radio access networks. In Proceedings of the 12th International on Conference on emerging Networking EXperiments and Technologies, Irvine, CA, USA, 6 December 2016; pp. 427–441. [Google Scholar]
- Hua, Y.; Li, R.; Zhao, Z.; Chen, X.; Zhang, H. GAN-powered Deep Distributional Reinforcement Learning for Resource Management in Network Slicing. IEEE J. Sel. Areas Commun. 2019, 38, 334–349. [Google Scholar] [CrossRef]
- Goodfellow, I.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative adversarial nets. Adv. Neural Inf. Process. Syst. 2014, 2672–2680. [Google Scholar]
- OpenAirInterface. OAI: An Open-Source Community. Available online: https://www.openairinterface.org (accessed on 10 June 2020).






| Work | Core Slicing | RAN Slicing | Transport Slicing | Orchestration & Automation | Resource Monitoring | Intelligent Resource Management | Intent-Based Networking | Life Cycle Management |
|---|---|---|---|---|---|---|---|---|
| [1] | JUJU NFV management framework | FlexRAN Controller | No | JOX, JUJU Framework | No | No | No | Yes |
| [6] | Yes | Yes | Yes | Huawei Orchestrator | No | No | No | No |
| [23] | Dedicated Core Network | FlexRAN Controller | No | No | Monitioring using ELK | No | No | Yes |
| [24] | Yes | Yes | No | OSM MANO | No | No | No | No |
| [26] | No | Yes | No | No | No | No | No | No |
| [27] | No | Yes | No | Yes | Yes | No | No | No |
| [28] | No | Yes | No | No | Yes | RL & heuristic based algorithm | No | No |
| [29] | No | Yes | No | No | Yes | Intelligent Networking | No | No |
| [30] | No | Yes | Yes | RL algotithm | No | No | ||
| [35] | No | Intelligent Resources Scheduling | No | No | No | DL & ML algorithm | No | No |
| Our Work | OSM | FlexRAN Controller | No | OSM, FlexRAN & IBN | Openstack & FlexRAN | GAN model | Yes | Yes |
| Component | System Specifications |
|---|---|
| FlexRAN | OS: UBUNTU 16.04 RAM: 16 GB CPU: CORE-i5 3.0 GHZ SSD: 500 GB |
| OSM | OS: UBUNTU 18 LTS RAM: 252 GB CPU: 32 Cores 2.10 GHZ H/D: 2 TB OSM Version: 7 Openstack Version: stein |
| IBN tool | OS: Window 10 RAM: 16 GB CPU: Core I5 3.0 GHZ H/D: 1 TB Programming languages: PHP, JAVA Database: MYSQL |
| SDR USRP B210 | Frequency Range: 70 MHz-6 GHz Channels: 2TX * 2RX |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abbas, K.; Afaq, M.; Ahmed Khan, T.; Rafiq, A.; Song, W.-C. Slicing the Core Network and Radio Access Network Domains through Intent-Based Networking for 5G Networks. Electronics 2020, 9, 1710. https://doi.org/10.3390/electronics9101710
Abbas K, Afaq M, Ahmed Khan T, Rafiq A, Song W-C. Slicing the Core Network and Radio Access Network Domains through Intent-Based Networking for 5G Networks. Electronics. 2020; 9(10):1710. https://doi.org/10.3390/electronics9101710
Chicago/Turabian StyleAbbas, Khizar, Muhammad Afaq, Talha Ahmed Khan, Adeel Rafiq, and Wang-Cheol Song. 2020. "Slicing the Core Network and Radio Access Network Domains through Intent-Based Networking for 5G Networks" Electronics 9, no. 10: 1710. https://doi.org/10.3390/electronics9101710
APA StyleAbbas, K., Afaq, M., Ahmed Khan, T., Rafiq, A., & Song, W.-C. (2020). Slicing the Core Network and Radio Access Network Domains through Intent-Based Networking for 5G Networks. Electronics, 9(10), 1710. https://doi.org/10.3390/electronics9101710






