Practical Homomorphic Authentication in Cloud-Assisted VANETs with Blockchain-Based Healthcare Monitoring for Pandemic Control
Abstract
1. Introduction
2. Related Works
3. Preliminaries
3.1. Homomorphic Encryption
3.2. Elliptic Curve Cryptography (ECC)
3.3. Hash Function
- With a random message x of arbitrary length, the message digest of its fixed length output can be easily calculated.
- It is hard to compute with the given y.
- It is computationally infeasible to find such that , providing that x is given.
3.4. Notations
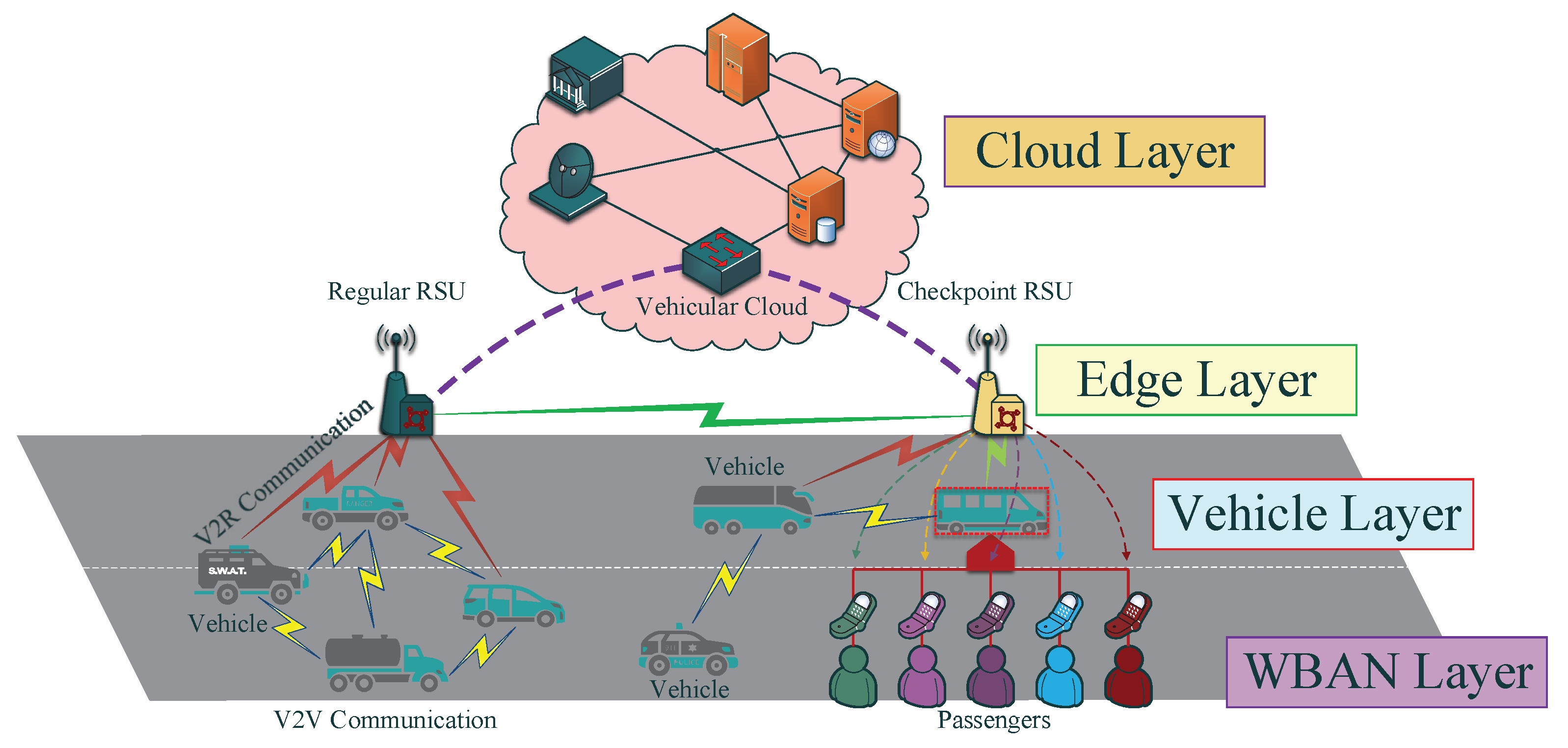
3.5. System Model
3.6. Security Requirements
- Conditional Privacy Preserving: considering as one of the crucial features for privacy protection, conditional privacy contains two aspects: user privacy protection and targeted vehicle information retrieving. That is, the confidential user information should be safely stored in the whole session. The illegal tracking toward specific vehicle cannot succeed. Meanwhile, the responsible for VANET system management should be able to reveal the real identity of suspect vehicle if necessary.
- Anonymity: due to the open wireless transmission features, VANET communication channels may be eavesdropped by malicious devices. Normally, messages that originated from the same device naturally carry unique data patterns. In this case, by analyzing the eavesdropped information, vital parameters, such as transmitting frequency, user location may be exposed, which severely endangers user privacy. For this consideration, the anonymity of each VANET device should be guaranteed.
- Unforgeability: in practical VANET transmission, adversary may selectively forge the valid certificates, session keys, or signatures to pass the verification process. Hence, unforgeability against chosen message attack is the major property in secure data exchange.
- Mutual Authentication: in the VANET design, mutual authentication is the fundamental but leading security property, which guarantees that both VANET entities in one communication session could authenticate each other. In this way, the impersonation attack towards certain device can be prevented.
- Non-repudiation: non-repudiation ensures the validity of the transmitted information. The message sender of VANET cannot deny the authenticity of the issued signature on the transmitted messages.
- Session Key Establishment: upon mutual authentication, the unique session key between individual vehicle and VANET system should be established, so as to provide subsequent secure data exchange.
4. Proposed Design
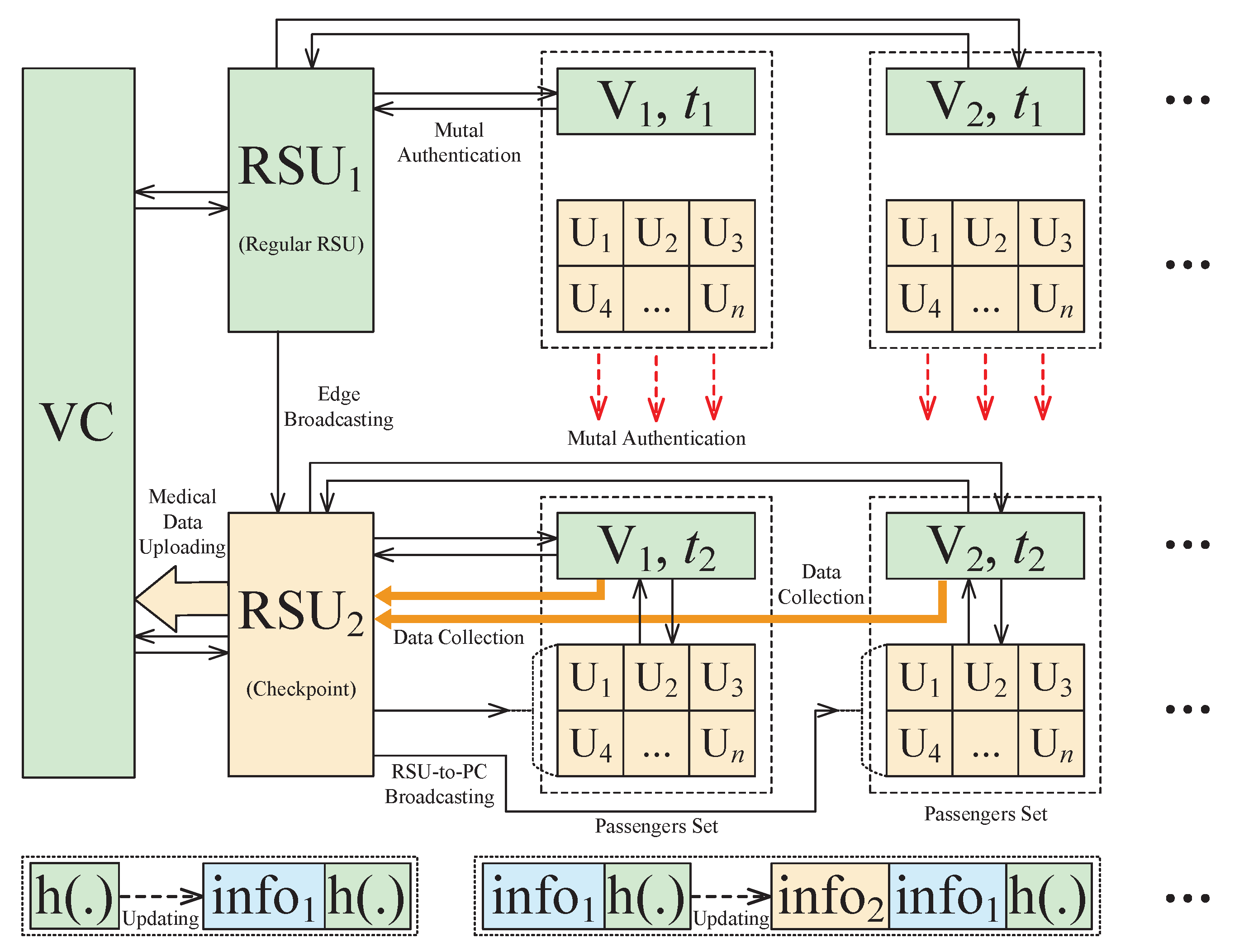
4.1. Device Initilization Phase
4.2. Blockchain-Based Key Agreement Phase
4.3. Healthcare Monitoring Strategy
5. Security Analysis
5.1. Security Discussions
5.2. Security Properties Comparison
6. Performance Analysis
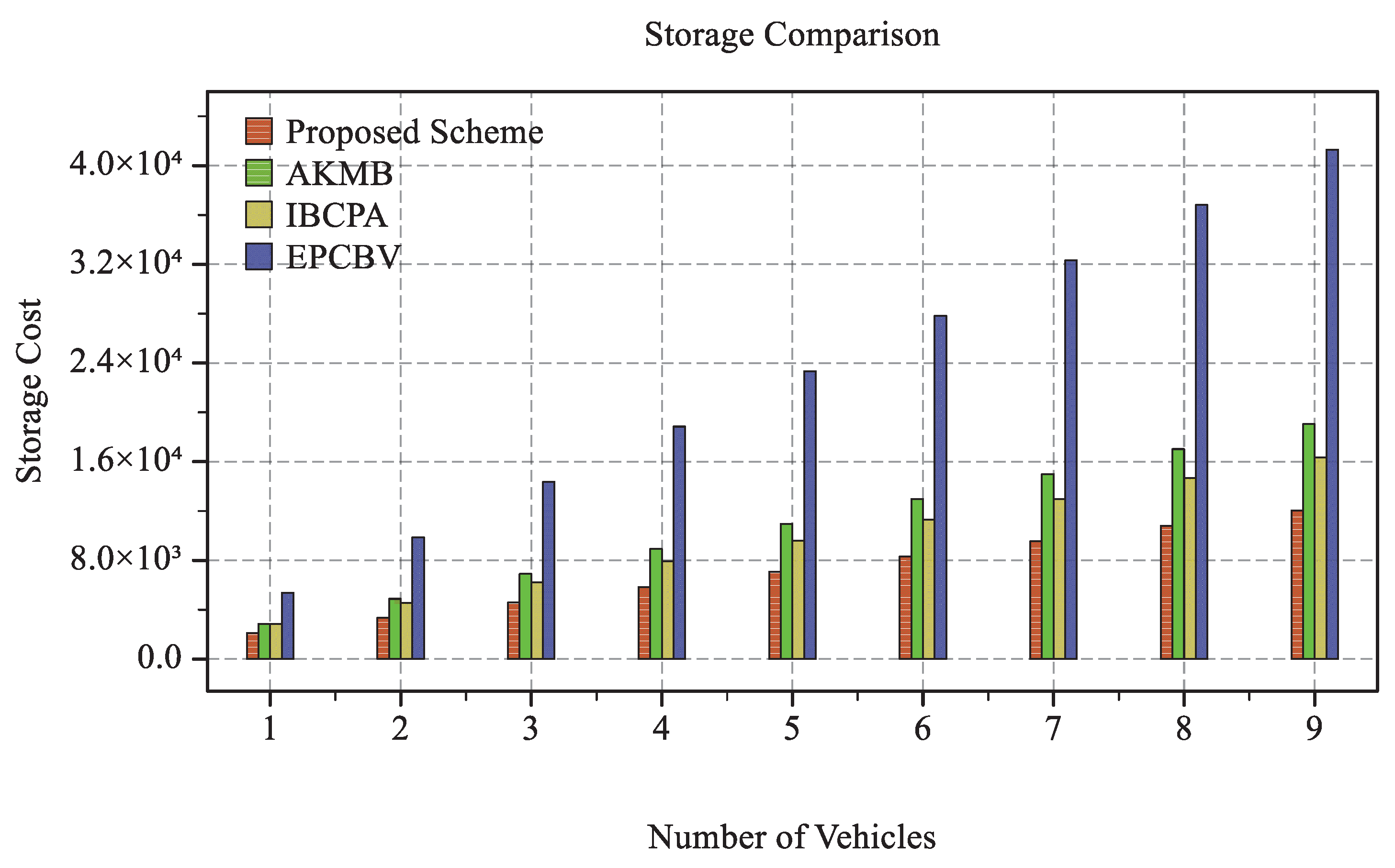
6.1. Storage Overhead
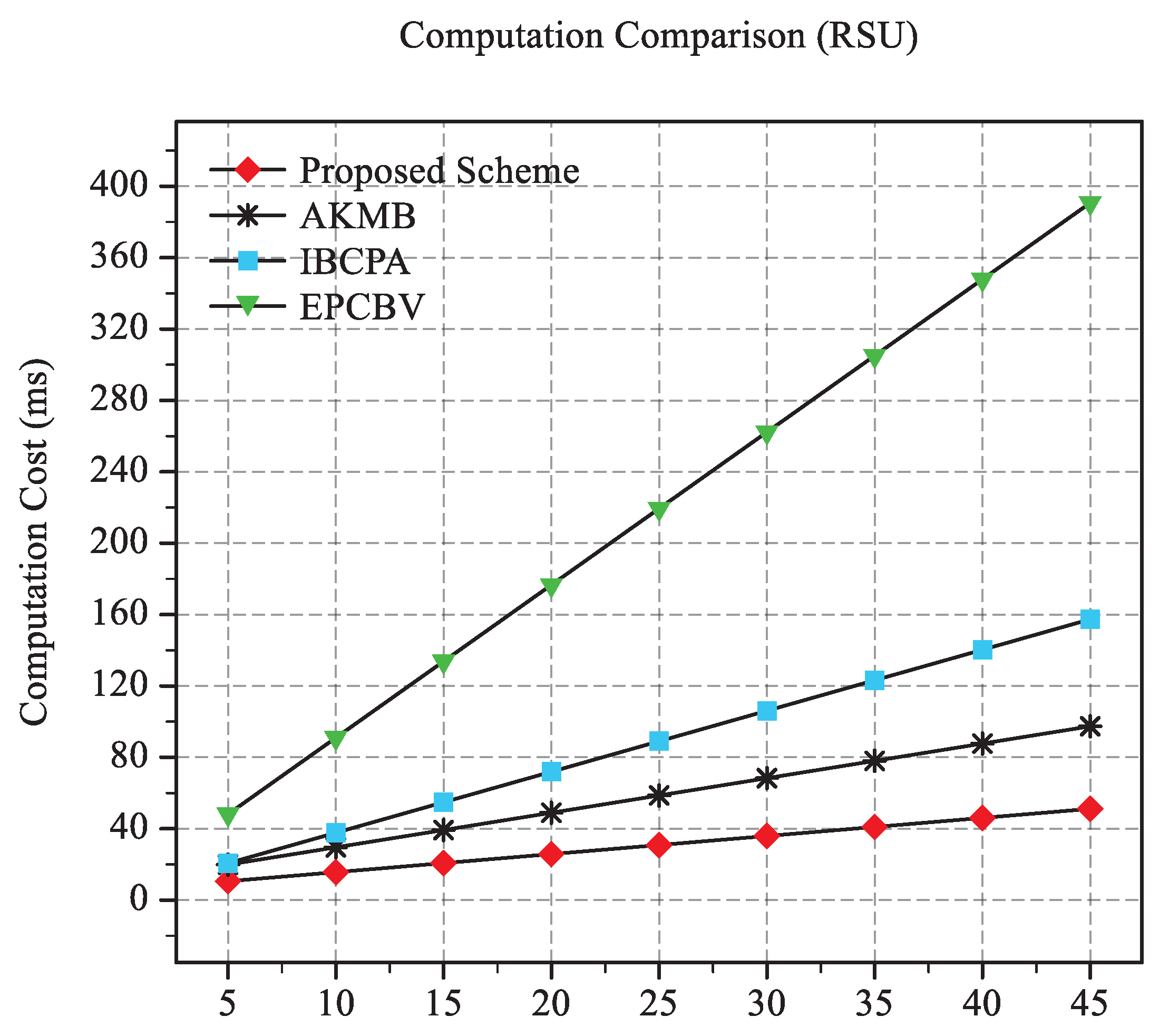
6.2. Computation Cost
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Zhang, L.; Wu, Q.; Solanas, A.; Domingo-Ferrer, J. A Scalable Robust Authentication Protocol for Secure Vehicular Communications. IEEE Trans. Veh. Technol. 2010, 59, 1606–1617. [Google Scholar] [CrossRef]
- Kaur, K.; Garg, S.; Kaddoum, G.; Gagnon, F.; Ahmed, S.H. Blockchain-Based Lightweight Authentication Mechanism for Vehicular Fog Infrastructure. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Huang, D.; Misra, S.; Verma, M.; Xue, G. PACP: An Efficient Pseudonymous Authentication-Based Conditional Privacy Protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2011, 12, 736–746. [Google Scholar] [CrossRef]
- Yao, Y.; Chang, X.; Mišić, J.; Mišić, V.B.; Li, L. BLA: Blockchain-Assisted Lightweight Anonymous Authentication for Distributed Vehicular Fog Services. IEEE Internet Things J. 2019, 6, 3775–3784. [Google Scholar] [CrossRef]
- Tan, H.; Chung, I. Secure Authentication and Group Key Distribution Scheme for WBANs Based on Smartphone ECG Sensor. IEEE Access 2019, 7, 151459–151474. [Google Scholar] [CrossRef]
- Li, J.; Lu, H.; Guizani, M. ACPN: A Novel Authentication Framework with Conditional Privacy-Preservation and Non-Repudiation for VANETs. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 938–948. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Lo, N.; Tsai, J. An Efficient Conditional Privacy-Preserving Authentication Scheme for Vehicular Sensor Networks Without Pairings. IEEE Trans. Intell. Transp. Syst. 2016, 17, 1319–1328. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Liang, X.; Shen, X. A Dynamic Privacy-Preserving Key Management Scheme for Location-Based Services in VANETs. IEEE Trans. Intell. Transp. Syst. 2012, 13, 127–139. [Google Scholar] [CrossRef]
- Tan, H.; Choi, D.; Kim, P.; Pan, S.; Chung, I. Secure Certificateless Authentication and Road Message Dissemination Protocol in VANETs. Wirel. Commun. Mob. Comput. 2018, 2018, 1–13. [Google Scholar] [CrossRef]
- Shao, J.; Lin, X.; Lu, R.; Zuo, C. A Threshold Anonymous Authentication Protocol for VANETs. IEEE Trans. Veh. Technol. 2016, 65, 1711–1720. [Google Scholar] [CrossRef]
- Zhang, Q.; Gan, Y.; Zhang, Q.; Wang, R.; Tan, Y. A Dynamic and Cross-Domain Authentication Asymmetric Group Key Agreement in Telemedicine Application. IEEE Access 2018, 6, 24064–24074. [Google Scholar]
- Tian, Z.; Shi, W.; Wang, Y.; Zhu, C.; Du, X.; Su, S.; Sun, Y.; Guizani, N. Real-Time Lateral Movement Detection Based on Evidence Reasoning Network for Edge Computing Environment. IEEE Trans. Ind. Inform. 2019, 15, 4285–4294. [Google Scholar] [CrossRef]
- Tan, H.; Choi, D.; Kim, P.; Pan, S.; Chung, I. An Efficient Hash-based RFID Grouping Authentication Protocol Providing Missing Tags Detection. J. Internet Technol. 2018, 19, 481–488. [Google Scholar]
- Alazzawi, M.A.; Lu, H.; Yassin, A.A.; Chen, K. Efficient Conditional Anonymity With Message Integrity and Authentication in a Vehicular Ad-Hoc Network. IEEE Access 2019, 7, 71424–71435. [Google Scholar] [CrossRef]
- Hao, Y.; Cheng, Y.; Zhou, C.; Song, W. A Distributed Key Management Framework with Cooperative Message Authentication in VANETs. IEEE J. Sel. Areas Commun. 2011, 29, 616–629. [Google Scholar] [CrossRef]
- Wasef, A.; Shen, X. EMAP: Expedite Message Authentication Protocol for Vehicular Ad Hoc Networks. IEEE Trans. Mob. Comput. 2013, 12, 78–89. [Google Scholar] [CrossRef]
- Tan, H.; Chung, I. A Secure and Efficient Group Key Management Protocol with Cooperative Sensor Association in WBANs. Sensors 2018, 18, 3930. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Wang, H.; Wang, L.; Choo, K.R.; Vinel, A. A Provably-Secure Cross-Domain Handshake Scheme with Symptoms-Matching for Mobile Healthcare Social Network. IEEE Trans. Dependable Secur. Comput. 2018, 15, 633–645. [Google Scholar] [CrossRef]
- Chuang, M.; Lee, J. TEAM: Trust-Extended Authentication Mechanism for Vehicular Ad Hoc Networks. IEEE Syst. J. 2014, 8, 749–758. [Google Scholar] [CrossRef]
- Zhu, X.; Jiang, S.; Wang, L.; Li, H. Efficient Privacy-Preserving Authentication for Vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2014, 63, 907–919. [Google Scholar] [CrossRef]
- Shen, J.; Tan, H.; Ren, Y.; Liu, Q.; Wang, B. A Practical RFID Grouping Authentication Protocol in Multiple-Tag Arrangement With Adequate Security Assurance. In Proceedings of the 2016 18th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Korea, 31 January–3 February 2016; pp. 693–699. [Google Scholar]
- Tan, H.; Chung, I. A Secure Cloud-Assisted Certificateless Group Authentication Scheme for VANETs in Big Data Environment. In Proceedings of the 2019 International Conference on Big Data Engineering (BDE2019), Hong Kong, China, 11–13 June 2019; pp. 107–113. [Google Scholar]
- Wang, F.; Xu, Y.; Zhang, H.; Zhang, Y.; Zhu, L. 2FLIP: A Two-Factor Lightweight Privacy-Preserving Authentication Scheme for VANET. IEEE Trans. Veh. Technol. 2016, 65, 896–911. [Google Scholar] [CrossRef]
- Tan, H.; Song, Y.; Xuan, S.; Pan, S.; Chung, I. Secure D2D Group Authentication Employing Smartphone Sensor Behavior Analysis. Symmetry 2018, 11, 969. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Zeadally, S.; Liang, K. BPAS: Blockchain-Assisted Privacy-Preserving Authentication System for Vehicular Ad Hoc Networks. IEEE Trans. Ind. Inform. 2020, 16, 4146–4155. [Google Scholar] [CrossRef]
- Zhou, T.; Shen, J.; Li, X.; Wang, C.; Tan, H. Logarithmic Encryption Scheme for Cyber-Physical Systems Employing Fibonacci Q-matrix. Future Gener. Comput. Syst. 2020, 108, 1307–1313. [Google Scholar] [CrossRef]
- Tan, H.; Xuan, S.; Chung, I. HCDA: Efficient Pairing-Free Homographic Key Management for Dynamic Cross-Domain Authentication in VANETs. Symmetry 2020, 12, 1003. [Google Scholar] [CrossRef]
- Lu, Z.; Wang, Q.; Qu, G.; Zhang, H.; Liu, Z. A Blockchain-Based Privacy-Preserving Authentication Scheme for VANETs. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2019, 27, 2792–2801. [Google Scholar] [CrossRef]
- Li, Y.; Chen, W.; Cai, Z.; Fang, Y. CAKA: A Novel Certificateless-Based Cross-Domain Authenticated Key Agreement Protocol for Wireless Mesh Networks. Wirel. Netw. 2016, 22, 2523–2535. [Google Scholar] [CrossRef]
- Liu, B.; Jia, D.; Wang, J.; Lu, K.; Wu, L. Cloud-Assisted Safety Message Dissemination in VANET–Cellular Heterogeneous Wireless Network. IEEE Syst. J. 2017, 11, 128–139. [Google Scholar] [CrossRef]
- Tan, H.; Gui, Z.; Chung, I. A Secure and Efficient Certificateless Authentication Scheme With Unsupervised Anomaly Detection in VANETs. IEEE Access 2018, 6, 74260–74276. [Google Scholar] [CrossRef]
- Wang, Y.; Ding, Y.; Wu, Q.; Wei, Y.; Qin, B.; Wang, H. Privacy-Preserving Cloud-Based Road Condition Monitoring With Source Authentication in VANETs. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1779–1790. [Google Scholar] [CrossRef]
- Cui, J.; Wei, L.; Zhang, J.; Xu, Y.; Zhong, H. An Efficient Message-Authentication Scheme Based on Edge Computing for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2019, 20, 1621–1632. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Wang, H.; Kumar, N.; Choo, K.R. An Efficient and Provably Secure Authenticated Key Agreement Protocol for Fog-Based Vehicular Ad-Hoc Networks. IEEE Internet Things J. 2019, 6, 8065–8075. [Google Scholar] [CrossRef]
- Tan, H.; Choi, D.; Kim, P.; Pan, S.; Chung, I. Comments on ‘Dual Authentication and Key Management Techniques for Secure Data Transmission in Vehicular Ad Hoc Networks’. IEEE Trans. Intell. Transp. Syst. 2017, 19, 2149–2151. [Google Scholar] [CrossRef]
- Lin, C.; Deng, D.; Yao, C. Resource Allocation in Vehicular Cloud Computing Systems With Heterogeneous Vehicles and Roadside Units. IEEE Internet Things J. 2018, 5, 3692–3700. [Google Scholar] [CrossRef]
- Ullah, A.; Yaqoob, S.; Imran, M.; Ning, H. Emergency Message Dissemination Schemes Based on Congestion Avoidance in VANET and Vehicular FoG Computing. IEEE Access 2019, 7, 1570–1585. [Google Scholar] [CrossRef]
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Advances in Cryptology—EUROCRYPT ’99; Springer: Berlin/Heidelberg, Germany, 1999; pp. 223–238. [Google Scholar]
- Smart, N.P. The Discrete Logarithm Problem on Elliptic Curves of Trace One. J. Cryptol. 1999, 12, 193–196. [Google Scholar] [CrossRef]
- Merkle, R.C. A Fast Software One-way Hash Function. J. Cryptol. 1990, 3, 43–58. [Google Scholar] [CrossRef]
- Tan, H.; Chung, I. Secure Authentication and Key Management With Blockchain in VANETs. IEEE Access 2020, 8, 2482–2498. [Google Scholar] [CrossRef]
- Gayathri, N.B.; Thumbur, G.; Reddy, P.V.; Muhammad, Z.U.R. Efficient Pairing-Free Certificateless Authentication Scheme With Batch Verification for Vehicular Ad-Hoc Networks. IEEE Access 2018, 6, 31808–31819. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
| Symbol | Description |
|---|---|
| , | Vehicular Cloud, Road-Side Units |
| Vehicle Identities | |
| Cyclic Group | |
| P | Generator of |
| Identities | |
| Vehicle Encryption Key Set | |
| Vehicle Decryption Key Set | |
| Partial Secret Key Set | |
| Encryption Key Set | |
| Decryption Key Set | |
| Large Prime Values | |
| Vehicle Partial Secret Key Set | |
| Additional Information | |
| Route Records |
| No. | Original Identity Set | Location | Name/Addr./SSN/ | Route Info. | Add. Info. | |
|---|---|---|---|---|---|---|
| Type | ||||||
| RSU | 1 | ◯ | ∖ | ∖ | ||
| 2 | ◯ | ∖ | ∖ | |||
| ⋯ | ⋯ | ⋯ | ⋯ | ⋯ | ⋯ | |
| i | ◯ | ∖ | ∖ | |||
| Vehicle | 1 | ∖ | ◯ | |||
| 2 | ∖ | ◯ | ||||
| ⋯ | ⋯ | ⋯ | ⋯ | ⋯ | ⋯ | |
| j | ∖ | ◯ | ||||
| Passenger | 1 | ∖ | ◯ | ∖ | ||
| 2 | ∖ | ◯ | ∖ | |||
| ⋯ | ⋯ | ⋯ | ⋯ | ⋯ | ⋯ | |
| n | ∖ | ◯ | ∖ |
| Scheme | AKMB [42] | IBCPA [7] | EPCBV [43] | The Proposed Scheme |
|---|---|---|---|---|
| Anonymous Identity Updating | × | × | × | ◯ |
| Unforgeability | ◯ | ◯ | ◯ | ◯ |
| Collusion Attack Resilience | ◯ | × | ◯ | ◯ |
| Sibiling Attack Resilience | ◯ | × | × | ◯ |
| Session Key Establishment | ◯ | ◯ | ◯ | ◯ |
| Conditional Privacy Preserving | ◯ | ◯ | ◯ | ◯ |
| Scalability | × | × | ◯ | ◯ |
| Key Escrow Resilience | ◯ | ◯ | ◯ | ◯ |
| Replay Attack Resistance | × | ◯ | ◯ | ◯ |
| Unlinkability | × | × | × | ◯ |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tan, H.; Kim, P.; Chung, I. Practical Homomorphic Authentication in Cloud-Assisted VANETs with Blockchain-Based Healthcare Monitoring for Pandemic Control. Electronics 2020, 9, 1683. https://doi.org/10.3390/electronics9101683
Tan H, Kim P, Chung I. Practical Homomorphic Authentication in Cloud-Assisted VANETs with Blockchain-Based Healthcare Monitoring for Pandemic Control. Electronics. 2020; 9(10):1683. https://doi.org/10.3390/electronics9101683
Chicago/Turabian StyleTan, Haowen, Pankoo Kim, and Ilyong Chung. 2020. "Practical Homomorphic Authentication in Cloud-Assisted VANETs with Blockchain-Based Healthcare Monitoring for Pandemic Control" Electronics 9, no. 10: 1683. https://doi.org/10.3390/electronics9101683
APA StyleTan, H., Kim, P., & Chung, I. (2020). Practical Homomorphic Authentication in Cloud-Assisted VANETs with Blockchain-Based Healthcare Monitoring for Pandemic Control. Electronics, 9(10), 1683. https://doi.org/10.3390/electronics9101683







