DoubleDeck: Decoupling Complex Control Logic of Network Protocols to Facilitate Efficient Hardware Implementation
Abstract
1. Introduction
- We have proposed DoubleDeck, a two-layer control model that facilitates hardware implementation of the protocol. DoubleDeck simplifies the design and implementation of complex protocol control by decoupling protocol control into protocol state conversion logic and processing logic.
- We designed the BDM mechanism, a bottom deck mapping mechanism. BDM provides a general solution to the mapping problem between the bottom state machine array and the hardware logic, which effectively reduces the workload of the staff to develop the bottom state machine array.
- Based on the DoubleDeck model, we implemented the Intellectual Property (IP) core of AS6802 protocol on Arria10 (Aletra FPGA) and conducted corresponding performance and resource overhead tests. Then, through the implementation of AS6802, Transmission Control Protocol (TCP) and Precision Time Protocol (PTP) processing control logic to evaluate the BDM mechanism.
2. Motivation
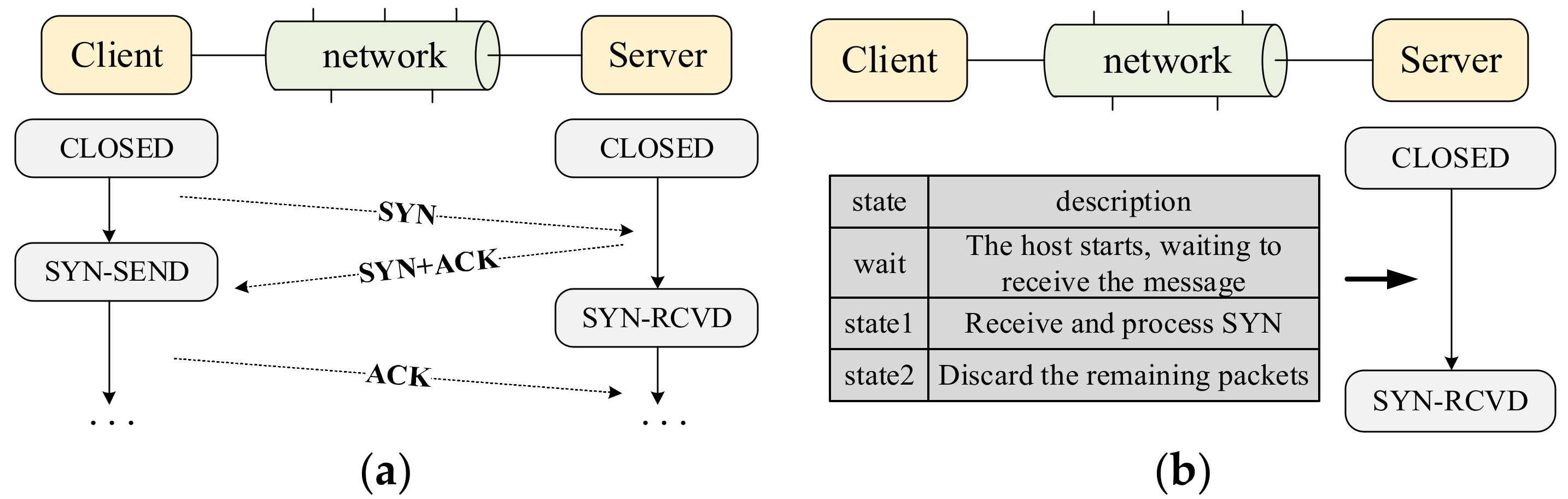
2.1. Features of Network Protocols
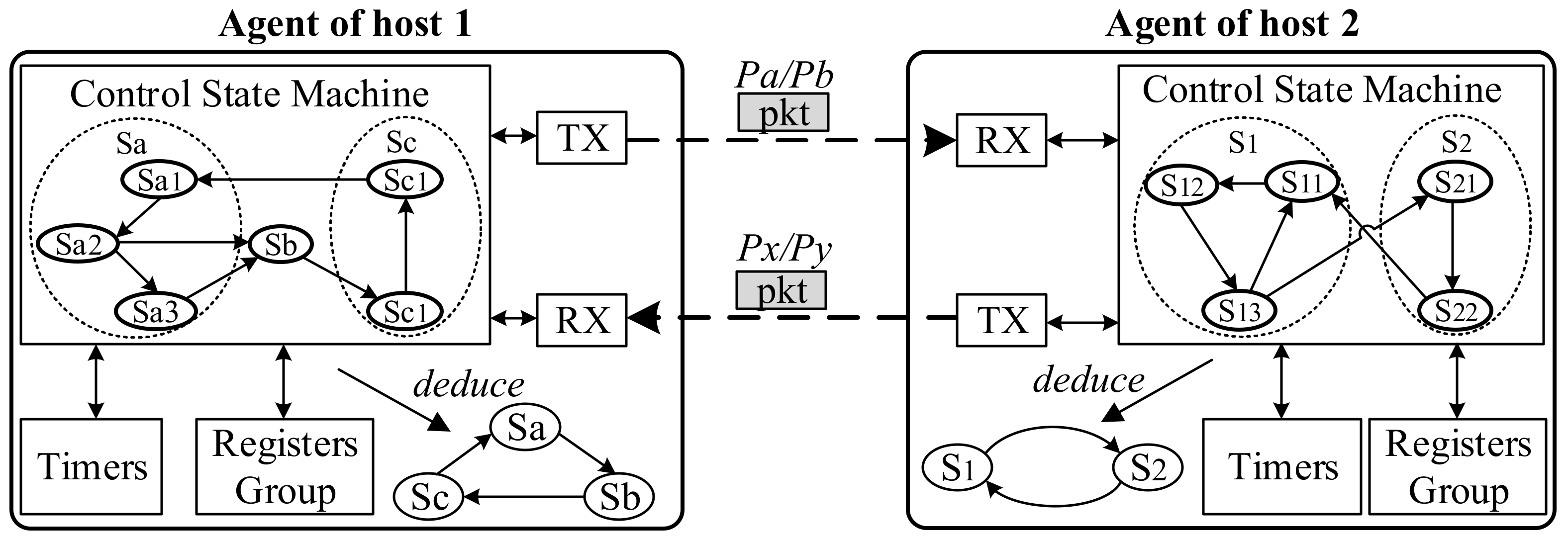
2.2. Decoupling of Protocol Control Logic
3. DoubleDeck Design
3.1. DoubleDeck Model
3.1.1. Design Ideas
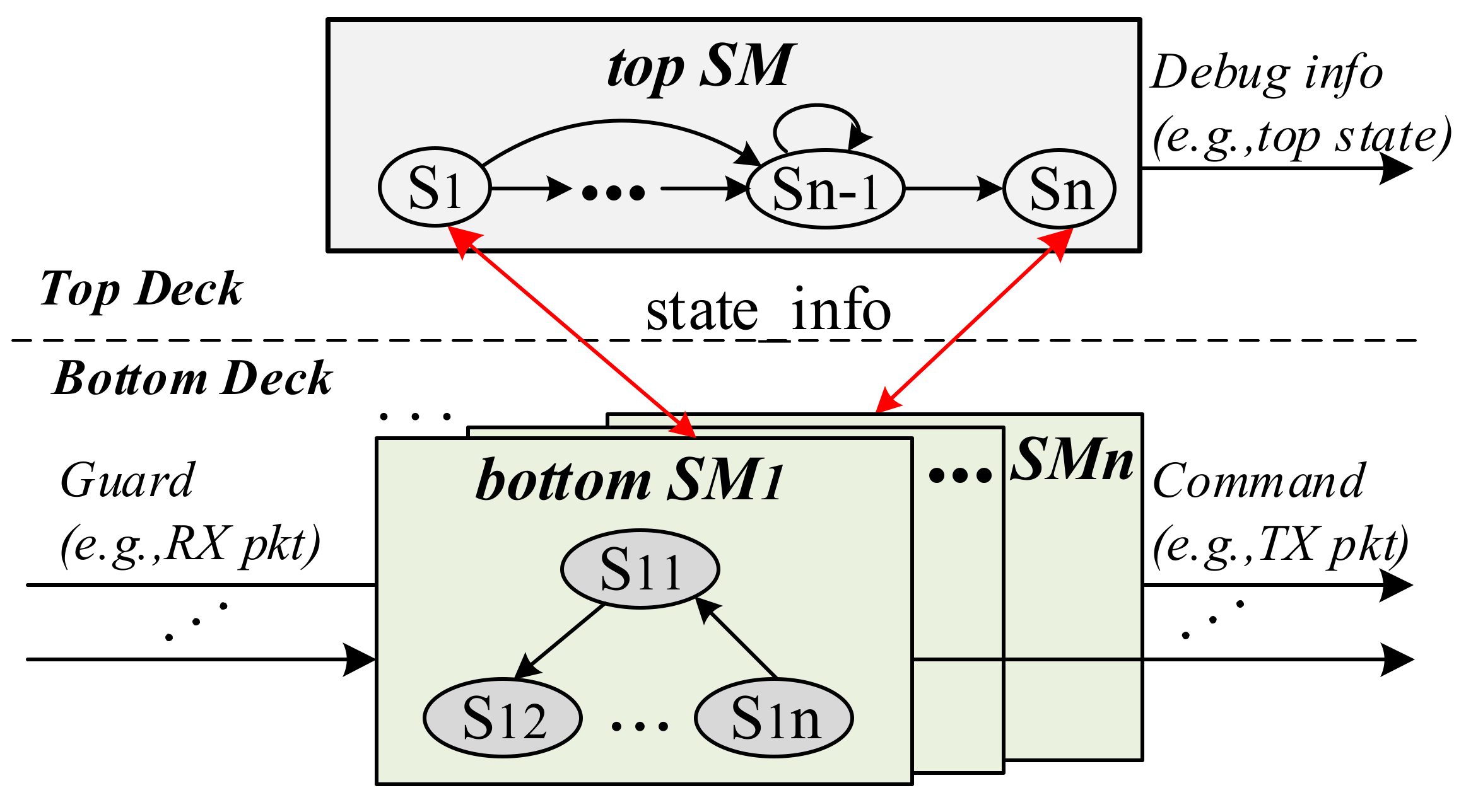
3.1.2. DoubleDeck Model Overview
3.2. The Bottom Deck Mapping Mechanism
3.2.1. Problem Formalization
- L represents the number of rows, ie L ∈ {num}, where num ∈ [1, N], N represents the total number of rows;
- G represents the set of triggering events, ie G ∈ {g}, where g ∈ g[N] is defined by the guardianship event;
- C represents the set of operation sequences, ie C ∈ {c}, where c ∈ c[N] is defined by the command event.
- F = (D, m, T, C), F is a graph.
- D represents a set of states, that is, D ∈ {P1, P2, …, PN, idle, guard, exit}, where Si = Li (i ∈ [1, N]).
- m represents the total number of states, m = N + 3.
- T represents the set of transition conditions, that is, T ∈ {T1, T2, …, TN, start, end, finish}, where Ti = gi(i ∈ [1, N]), and g [N] is defined by the Guard structure.
- C represents the set of action events corresponding to the state, that is, C ∈ {c1, c2, …, cN}, where c[N] is defined by the Command structure
3.2.2. Deck-Map Algorithm
| Algorithm 1 Deck-Map |
| Input: table Tabtransition |
| Output: SFSM Fcode |
| 1: Fcode.state_num = len(Tabtransition.line) + len(initial_states) |
| 2: for index = 0 to Fcode.state_num do F.D.append (idle) |
| 3: if index >= len(Tabtransition.line) then #general initial_states = [idle, guard, exit] |
| 4: Fcode.state.append(initial_states) # initial_transition = [start,finish,end] |
| 5: Fcode. initial_states.transition[index] = initial_transition[index] |
| 6: else # The following code maps the state of table and SFSM |
| 7: Fcode.state.append(process_states[index]) |
| 8: Fcode.guard.transition[index] = Tabtransition.line[index].Guard |
| 9: end if # Control the transition from processing state to guard state and exit state |
| 10: if next_state in Tabtransition.line[index].Command then |
| 11: Fcode. process_states[index].transition = finsih |
| 12: Fcode. process_states[index].next_state = exit |
| 13: else |
| 14: Fcode. process_states[index].transition = end |
| 15: Fcode. process_states[index]. next_state = guard |
| 16: end if |
| 17: end for |
3.2.3. Workflow of the Bottom Deck Mapping Mechanism
4. DoubleDeck Hardware Design
4.1. Top Deck Design
4.2. Bottom Deck Design
- RX. RX mainly has the function of integrating data. For the data plane key and the information carried by VDI and SDI in Top Deck, the RX module encapsulates them into a pre-defined data format.
- SFSM. SFSM contains multiple processing states. Each processing state corresponds to a row of entries in the state transition table of the global state. After DoubleDeck enters the initial state, SFSM will enter the wait state. When the guard meets the transition condition of a certain processing state, SFSM will enter the processing state and execute the corresponding command event.
- Timer. In many protocols, the processing time of the state is limited and varies. Timer is a module for maintaining timeout events. Because each state has different time limits, we use timer as a submodule of the bottom state machine.
- TX. For the processing results of the bottom state machine, the TX module sends these results to the data plane and Top Deck according to a pre-defined data structure without performing any additional operations.
4.3. Communication Mechanism
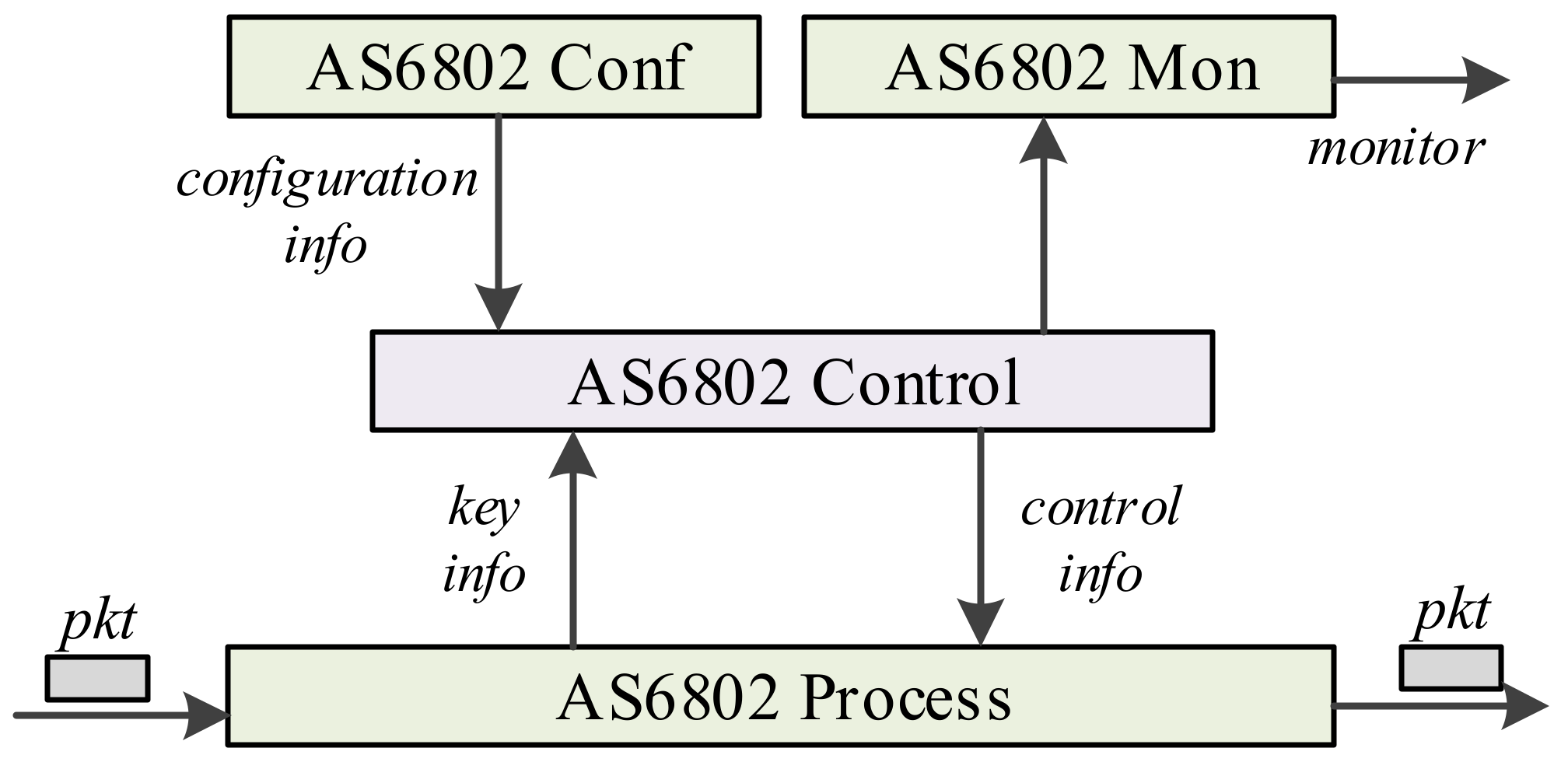
5. Application and Evaluation
5.1. Application
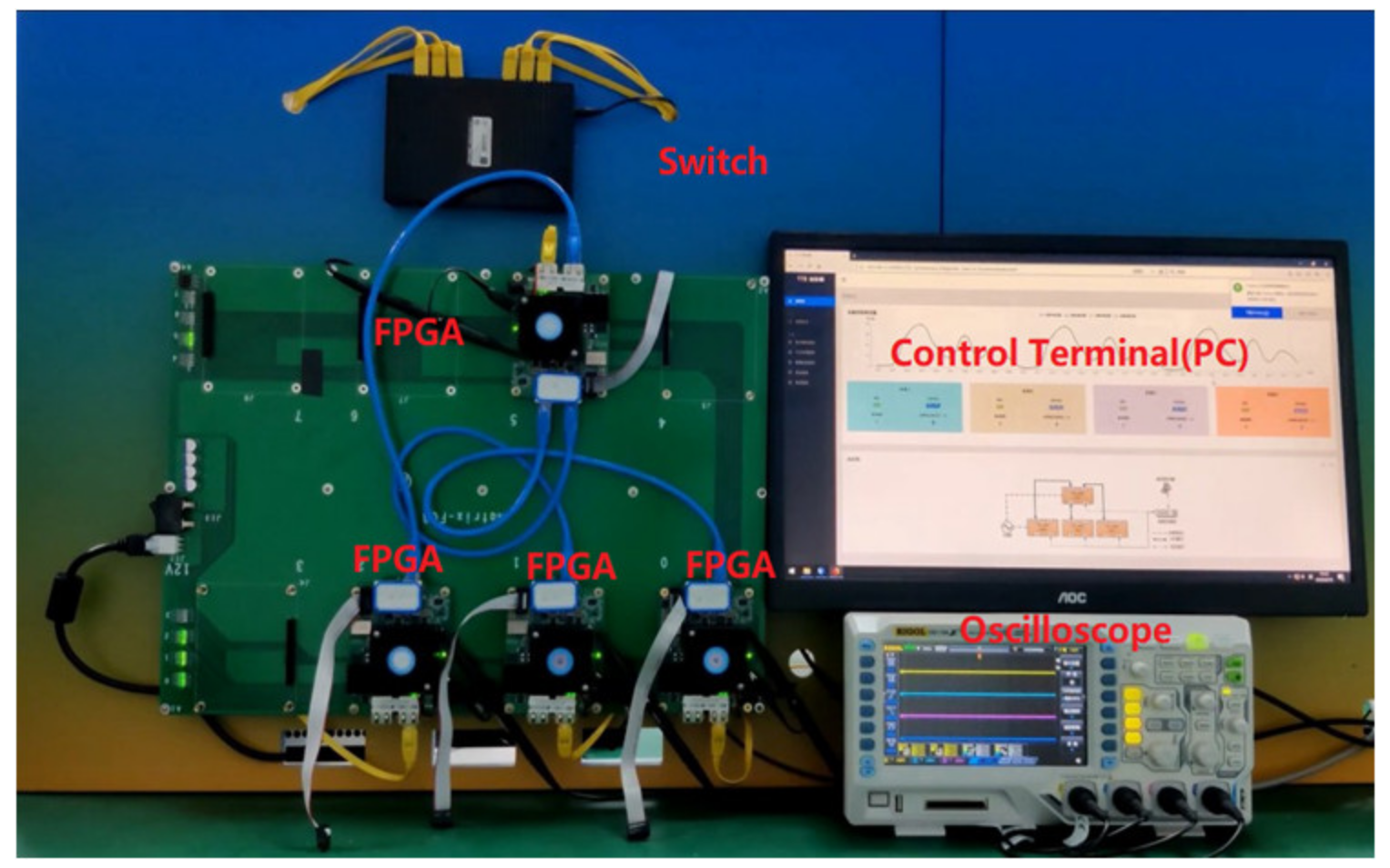
5.1.1. Model Feasibility
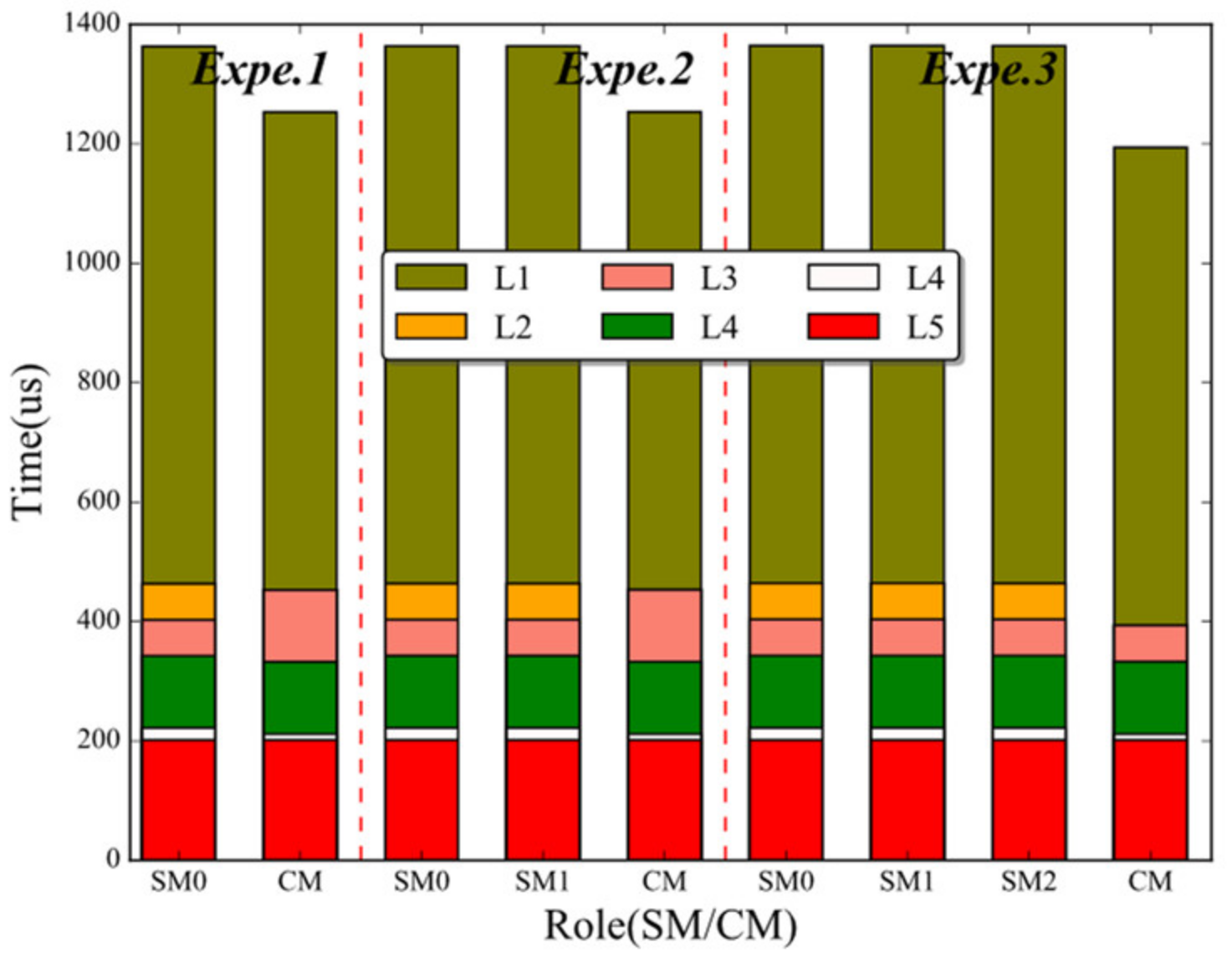
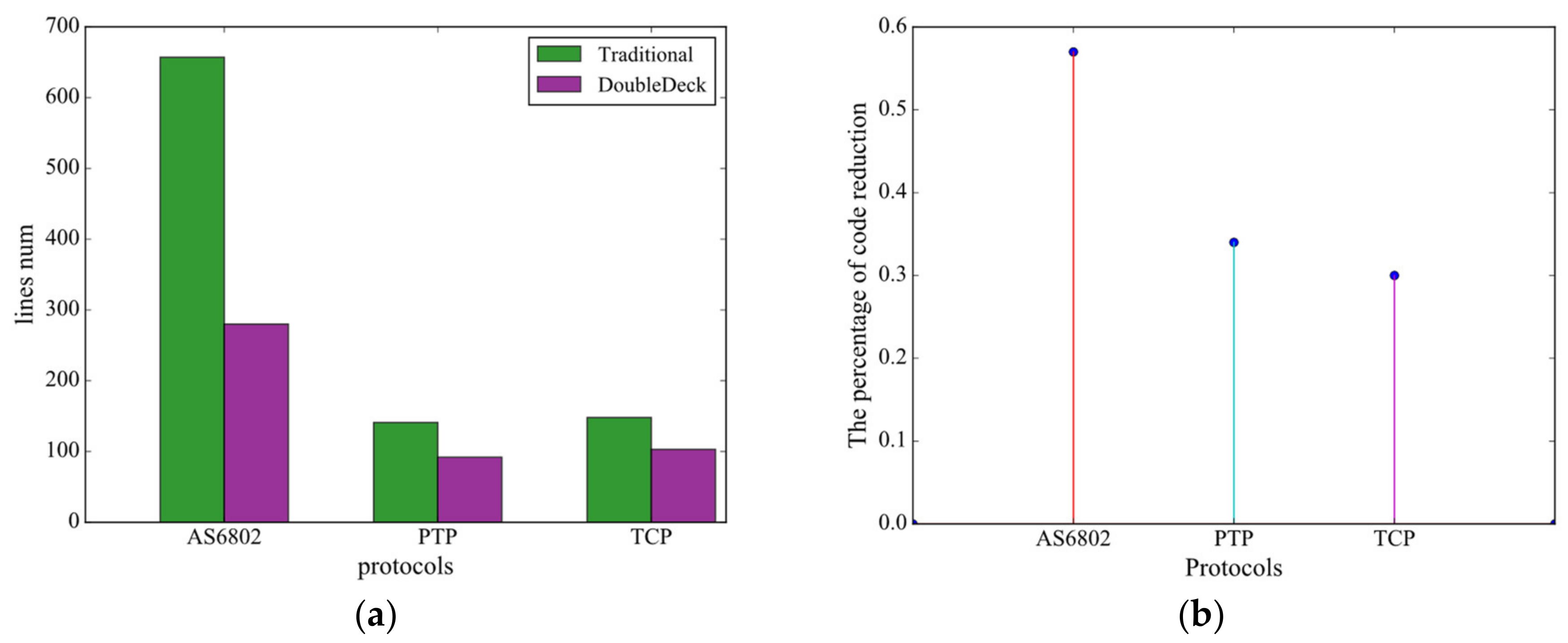
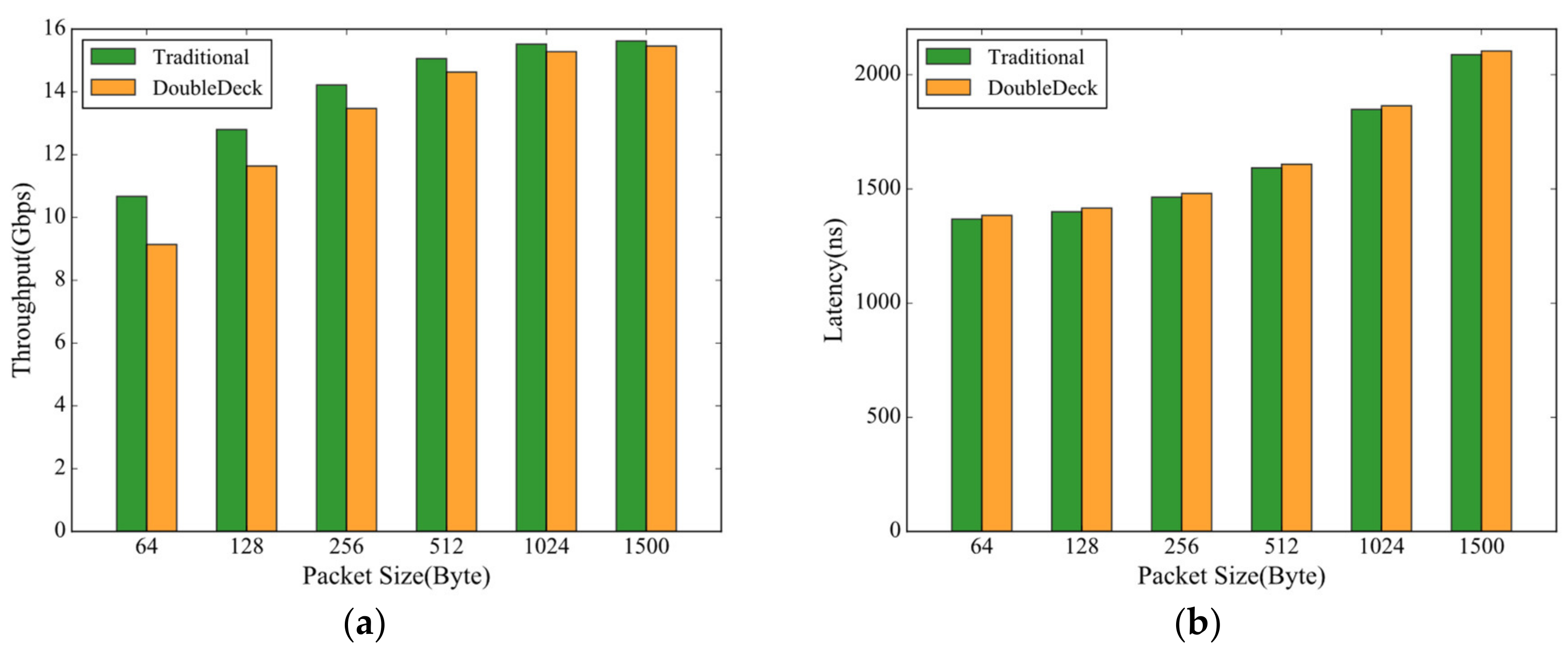
5.1.2. Performance and Resource Utilization
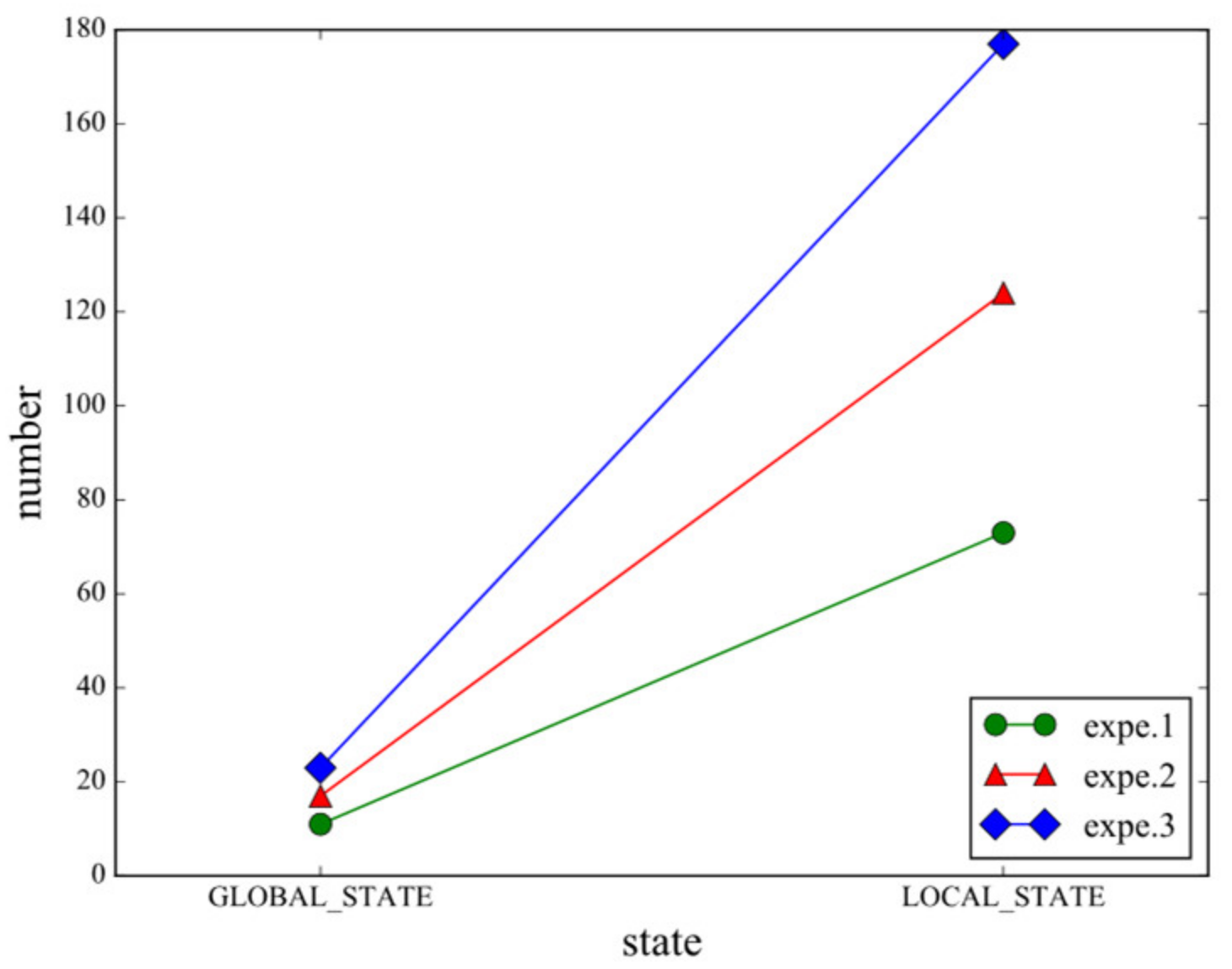
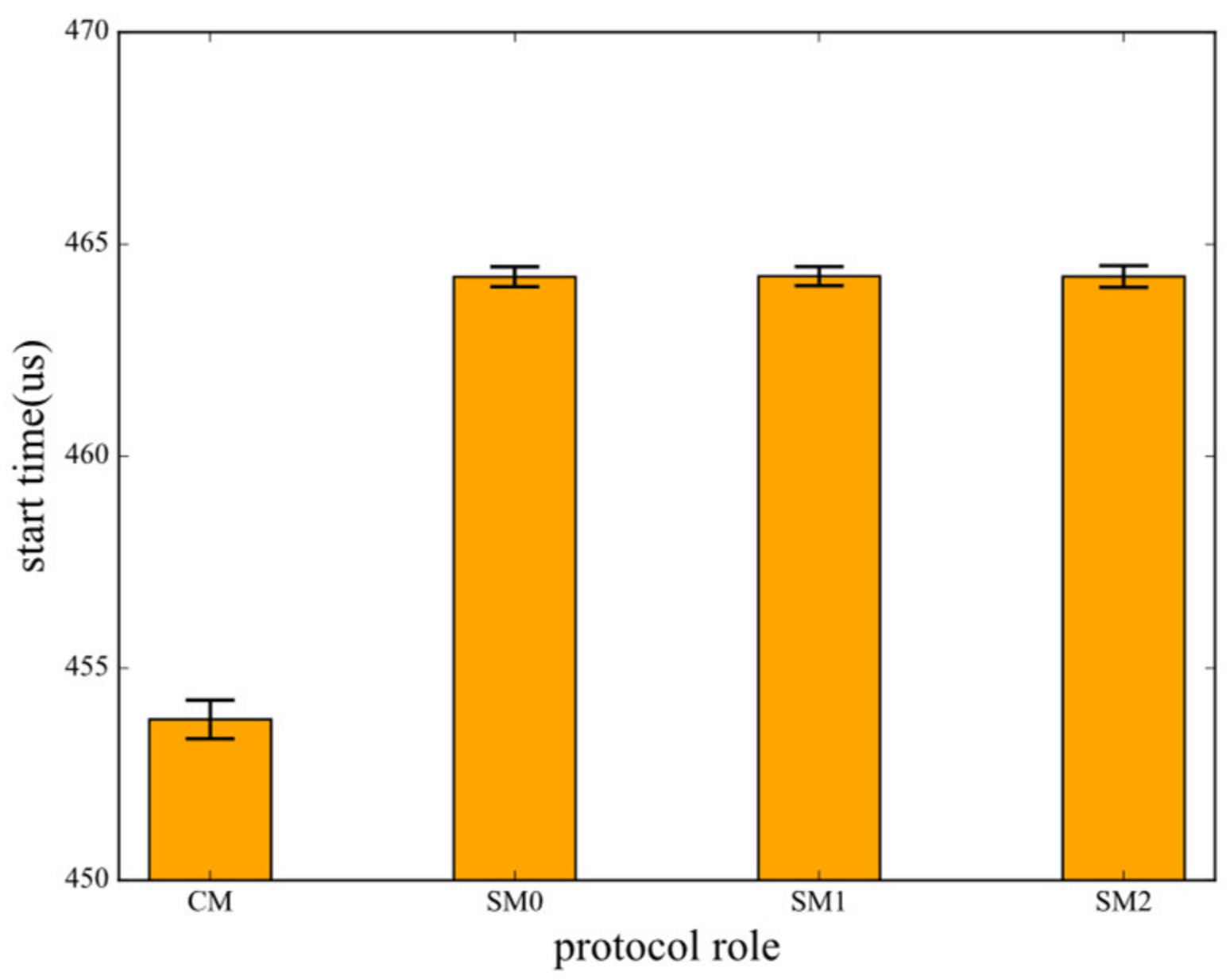
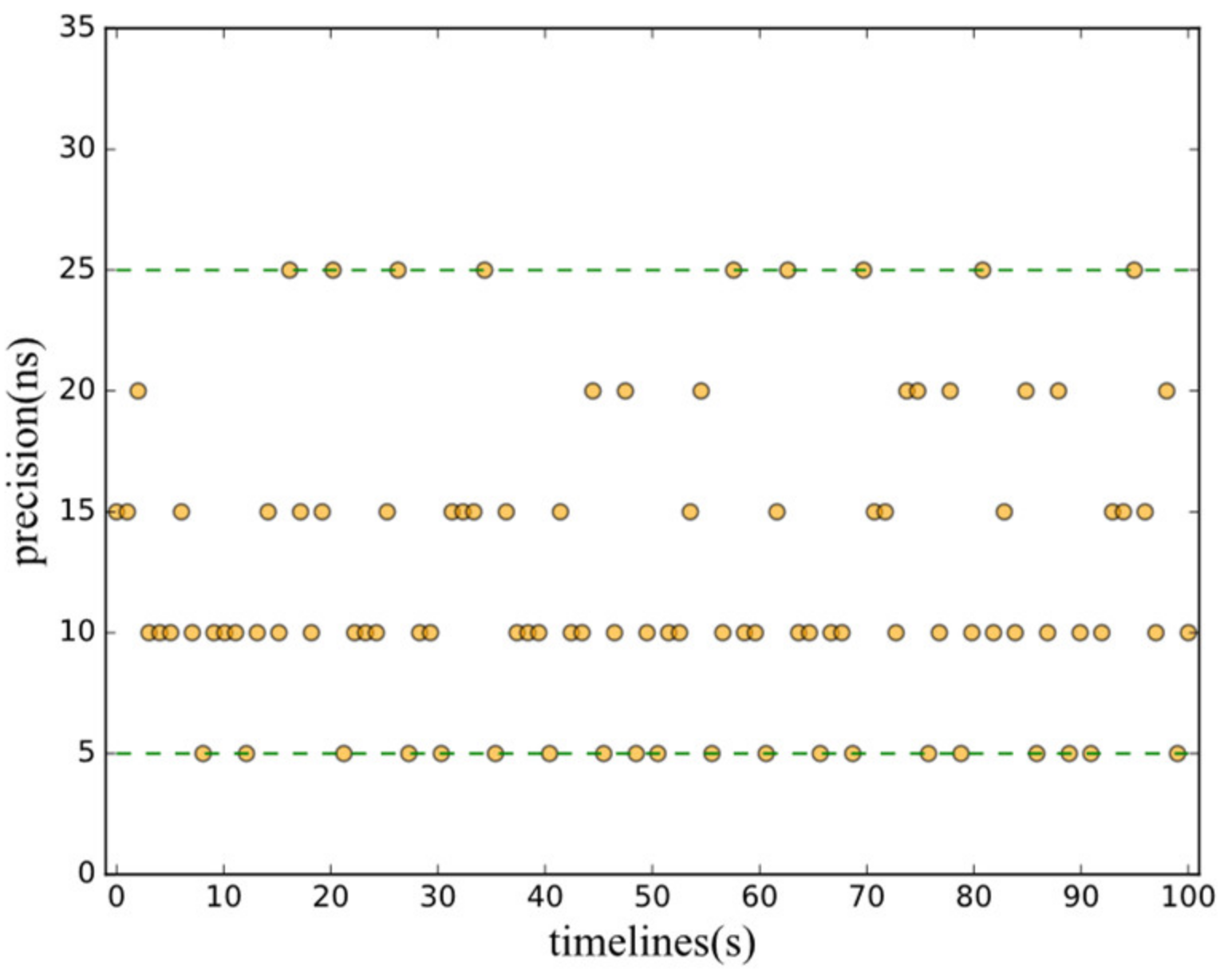
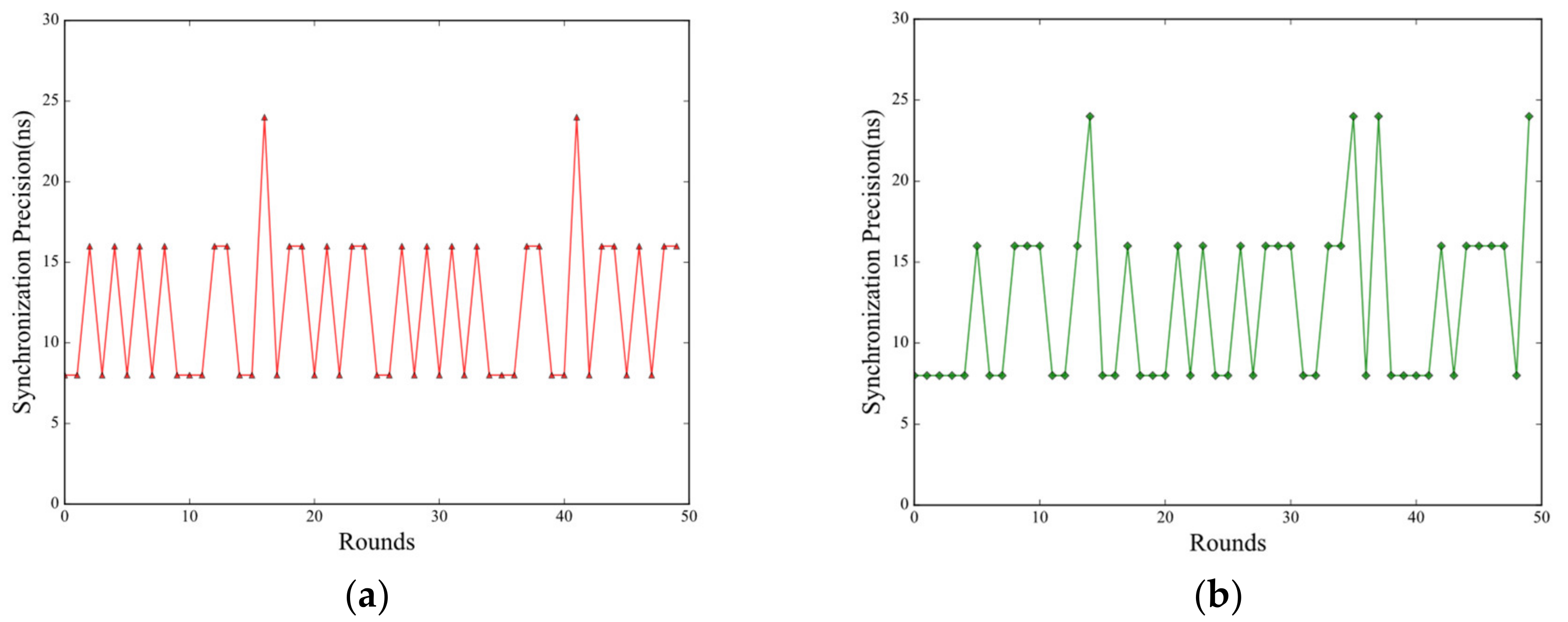
5.2. Evaluation for BDM Mechanism
6. Related Works
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Segall, A. Distributed network protocols. IEEE Trans. Inf. Theory 1983, 29, 23–35. [Google Scholar] [CrossRef]
- Yi, Y.; Wei, Q.; Jin, L.Y.; Lu, T.; Zhi, G.S. A hierarchical model of control logic for simplifying complex networks protocol design. In Proceedings of the 17th Annual IFIP International Conference on Network and Parallel Computing, Zhengzhou, China, 28–30 September 2020. [Google Scholar]
- Jamshed, M.A.; Moon, Y.; Kim, D.; Han, D.; Park, K. MOS: A reusable networking stack for flow monitoring middleboxes. In Proceedings of the 14th {USENIX} Symposium on Networked Systems Design and Implementation ({NSDI} 17), Boston, MA, USA, 27–29 March 2017; pp. 113–129. [Google Scholar]
- Li, J.; Sun, Z.; Yan, J.; Yang, X.; Jiang, Y.; Quan, W. DrawerPipe: A Reconfigurable Pipeline for Network Processing on FPGA-Based SmartNIC. Electronics 2020, 9, 59. [Google Scholar] [CrossRef]
- Pfaff, B.; Pettit, J.; Koponen, T.; Jackson, E.; Zhou, A.; Rajahalme, J.; Gross, J.; Wang, A.; Stringer, J.; Shelar, P.; et al. The design and implementation of open vswitch. In Proceedings of the 12th {USENIX} Symposium on Networked Systems Design and Implementation ({NSDI} 15), Oakland, CA, USA, 4–6 May 2015; pp. 117–130. [Google Scholar]
- Kotulski, Z.; Nowak, T.W.; Sepczuk, M.; Tunia, M.A. 5G networks: Types of isolation and their parameters in RAN and CN slices. Comput. Netw. 2020, 171, 107135. [Google Scholar] [CrossRef]
- Nasrallah, A.; Thyagaturu, A.S.; Alharbi, Z.; Wang, C.; Shao, X.; Reisslein, M.; ElBakoury, H. Ultra-low latency (ULL) networks: The IEEE TSN and IETF DetNet standards and related 5G ULL Research. IEEE Commun. Surv. Tutor. 2018, 21, 88–145. [Google Scholar] [CrossRef]
- Nasrallah, A.; Thyagaturu, A.S.; Alharbi, Z.; Wang, C.; Shao, X.; Reisslein, M.; Elbakoury, H. Performance comparison of IEEE 802.1 TSN time aware shaper (TAS) and asynchronous traffic shaper (ATS). IEEE Access 2019, 7, 44165–44181. [Google Scholar] [CrossRef]
- Gandhi, R.; Liu, H.H.; Hu, Y.C.; Lu, G.; Padhye, J.; Yuan, L.; Zhang, M. Duet: Cloud scale load balancing with hardware and software. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 27–38. [Google Scholar] [CrossRef]
- Hong, C.Y.; Caesar, M.; Godfrey, P.B. Finishing flows quickly with preemptive scheduling. ACM SIGCOMM Comput. Commun. Rev. 2012, 42, 127–138. [Google Scholar] [CrossRef]
- Firestone, D. {VFP}: A Virtual Switch Platform for Host {SDN} in the Public Cloud. In Proceedings of the 14th {USENIX} Symposium on Networked Systems Design and Implementation ({NSDI} 17), Boston, MA, USA, 27–29 March 2017; pp. 315–328. [Google Scholar]
- Firestone, D.; Putnam, A.; Mundkur, S.; Chiou, D.; Dabagh, A.; Andrewartha, M.; Angepat, H.; Bhanu, V.; Caulfield, A.; Chung, E.; et al. Azure accelerated networking: SmartNICs in the public cloud. In Proceedings of the 15th {USENIX} Symposium on Networked Systems Design and Implementation ({NSDI} 18), Renton, WA, USA, 9–11 April 2018; pp. 51–66. [Google Scholar]
- Weaver, N.; Paxson, V.; Gonzalez, J.M. The shunt: An FPGA-based accelerator for network intrusion prevention. In Proceedings of the 2007 ACM/SIGDA 15th International Symposium on Field Programmable Gate Arrays, Monterey, CA, USA, 18–20 February 2007; pp. 199–206. [Google Scholar]
- Kundel, R.; Burkert, T.; Griwodz, C.; Koldehofe, B. Chaining of hardware accelerated Virtual Network Functions in PCIe Environments. In Proceedings of the 20th International Middleware Conference Demos and Posters, Davis, CA, USA, 9–13 December 2019; pp. 13–14. [Google Scholar]
- Steinhammer, K.; Ademaj, A. Hardware implementation of the Time-Triggered Ethernet controller. In Embedded System Design: Topics, Techniques and Trends; Springer: Berlin/Heidelberg, Germany, 2007; pp. 325–338. [Google Scholar]
- Qi, Y.; Zhong, J.; Jiang, R.; Jia, Y.; Li, A.; Huang, L.; Han, W. FSM-Based Cyber Security Status Analysis Method. In Proceedings of the 2019 IEEE Fourth International Conference on Data Science in Cyberspace (DSC), Hangzhou, China, 23–25 June 2019; IEEE: New York, NY, USA, 2019; pp. 510–515. [Google Scholar]
- Moshref, M.; Bhargava, A.; Gupta, A.; Yu, M.; Govindan, R. Flow-level state transition as a new switch primitive for SDN. In Proceedings of the Third Workshop on Hot Topics in Software Defined Networking, Chicago, IL, USA, 17–22 August 2014; pp. 61–66. [Google Scholar]
- Lamport, L.; Malkhi, D.; Zhou, L. Reconfiguring a state machine. ACM SIGACT News 2010, 41, 63–73. [Google Scholar] [CrossRef]
- Fragal, V.H.; Simao, A.; Mousavi, M.R. Hierarchical featured state machines. Sci. Comput. Program. 2019, 171, 67–88. [Google Scholar] [CrossRef]
- Oliveira, A.; Melo, A.; Sklyarov, V. Specification, Implementation and Testing of HFSMs in Dynamically Reconfigurable FPGAs. International Workshop on Field Programmable Logic and Applications; Springer: Berlin/Heidelberg, Germany, 1999; pp. 313–322. [Google Scholar]
- Kopetz, H.; Ademaj, A.; Grillinger, P.; Steinhammer, K. The time-triggered ethernet (TTE) design. In Proceedings of the Eighth IEEE International Symposium on Object-Oriented Real-Time Distributed Computing (ISORC’05), Seattle, WA, USA, 18–20 May 2005; IEEE: Piscataway, NJ, USA, 2005; pp. 22–33. [Google Scholar]
- HuNan Hua Xin Tong Networks. AS6802 Core. Available online: https://gitee.com/huaxintong/as6802_core (accessed on 10 September 2020).
- Eidson, C.; Fischer, M.; White, J. IEEE-1588™ Standard for a precision clock synchronization protocol for networked measurement and control systems. In Proceedings of the 34th Annual Precise Time and Time Interval Systems and Applications Meeting, Reston, VA, USA, 3–5 December 2002; pp. 243–254. [Google Scholar]
- Fall, K.R.; Stevens, W.R. The Protocols. In TCP/IP Illustrated; Addison-Wesley: Boston, MA, USA, 2011; Volume 1. [Google Scholar]
- National University of Defense Technology. Available online: https://gitee.com/opentsn/openTSN (accessed on 10 September 2020).
- Ullah, S.; Choi, J.; Oh, H. IPsec for high speed network links: Performance analysis and enhancements. Future Gener. Comput. Syst. 2020, 107, 112–125. [Google Scholar] [CrossRef]
- Wang, L.; Cheng, R.; Lee, S.D.; Cheung, D. Accelerating probabilistic frequent itemset mining: A model-based approach. In Proceedings of the 19th ACM International Conference on Information and Knowledge Management, New York, NY, USA, 26–30 October 2010; pp. 429–438. [Google Scholar]
- Bosshart, P.; Daly, D.; Gibb, G.; Izzard, M.; McKeown, N.; Rexford, J.; Schlesinger, C.; Talayco, D.; Vahdat, A.; Varghese, G.; et al. P4: Programming protocol-independent packet processors. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 87–95. [Google Scholar] [CrossRef]


| State | Guard | Next State | Command | ||||
|---|---|---|---|---|---|---|---|
| RX Packet | Timer T1 | Register Local_t | TX Packet | Timer T1 | Register Local_t | ||
| S1(S11) | Pa | No timeout | - | S1(S12) | - | T1++ | 0 |
| S1(S12) | - | Timeout | - | S1(S13) | Px | 0 | local_t++ |
| S1(S13) | Pb | No timeout | - | S2(S21) | - | T1++ | local_t++ |
| S2(S21) | - | - | t0 | S2(S22) | Py | - | local_t++ |
| S2(S22) | Pa | - | <t0 | S1(S11) | - | - | local_t++ |
| Global State | Num(LS) | Global State | Num(LS) | Global State | Num(LS) |
|---|---|---|---|---|---|
| SM_INTEGRATE | 4 | SM_SYNC | 9 | CM_WAIT | 2 |
| SM_UNSYNC | 6 | SM_STABLE | 7 | CM_SYNC | 6 |
| SM_FLOOD | 5 | CM_INTEGRATE | 2 | CM_STABLE | 5 |
| SM_START | 3 | CM_UNSYNC | 3 | - | - |
| SM_TENTATIVE | 8 | CM_ENABLED | 1 | - | - |
| AS6802 IP | FPGA | Percentage | |
|---|---|---|---|
| Slice LUTs | 23,982 | 367,180 | 6.53% |
| Slice Registers | 21,516 | 734,360 | 2.93% |
| Block Memory | 387,104 | 29,306,880 | 1.32% |
| Module | Submodule | Slice LUTs | Slice Registers | Block Memory |
|---|---|---|---|---|
| PTP | Control logic (DoubleDeck) | 182 | 287 | 3983 |
| Control logic (Traditional) | 112 | 231 | 2393 | |
| Processing logic | 3740 | 4692 | 56,203 | |
| TCP proxy | Control logic (DoubleDeck) | 112 | 98 | 3428 |
| Control logic (Traditional) | 71 | 46 | 2234 | |
| Processing logic | 961 | 1334 | 13,532 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, Y.; Fu, W.; Yan, J.; Tang, L.; Sun, Z. DoubleDeck: Decoupling Complex Control Logic of Network Protocols to Facilitate Efficient Hardware Implementation. Electronics 2020, 9, 1647. https://doi.org/10.3390/electronics9101647
Yang Y, Fu W, Yan J, Tang L, Sun Z. DoubleDeck: Decoupling Complex Control Logic of Network Protocols to Facilitate Efficient Hardware Implementation. Electronics. 2020; 9(10):1647. https://doi.org/10.3390/electronics9101647
Chicago/Turabian StyleYang, Yi, Wenwen Fu, Jinli Yan, Lu Tang, and Zhigang Sun. 2020. "DoubleDeck: Decoupling Complex Control Logic of Network Protocols to Facilitate Efficient Hardware Implementation" Electronics 9, no. 10: 1647. https://doi.org/10.3390/electronics9101647
APA StyleYang, Y., Fu, W., Yan, J., Tang, L., & Sun, Z. (2020). DoubleDeck: Decoupling Complex Control Logic of Network Protocols to Facilitate Efficient Hardware Implementation. Electronics, 9(10), 1647. https://doi.org/10.3390/electronics9101647




