A Multi-Objective Evolutionary Algorithm Based on KNN-Graph for Traffic Network Attack
Abstract
1. Introduction
- (1)
- (2)
- (3)
- (1)
- We design a new vulnerability index based on the traffic information that represents the network function. This makes the result more suitable for specific functions of a traffic network.
- (2)
- We regard the vulnerability of the network as a confrontation between the network attacker and the network itself and convert it into a multi-objective optimization problem by considering the attack cost and attack efficiency simultaneously.
- (3)
- We propose a KNN-Graph based reproduction operator for MOEAs to improve the convergence of MOEAs.
2. Model of Network Attack
2.1. Subway Network Model
2.2. Optimization Model Construction of Complex Network
2.2.1. Network Transmission Efficiency
2.2.2. Network Attack Cost
2.2.3. Representation of an Attack Plan
3. An MOEA Based on KNN-Graph
3.1. Clustering Based Reproduction Operators
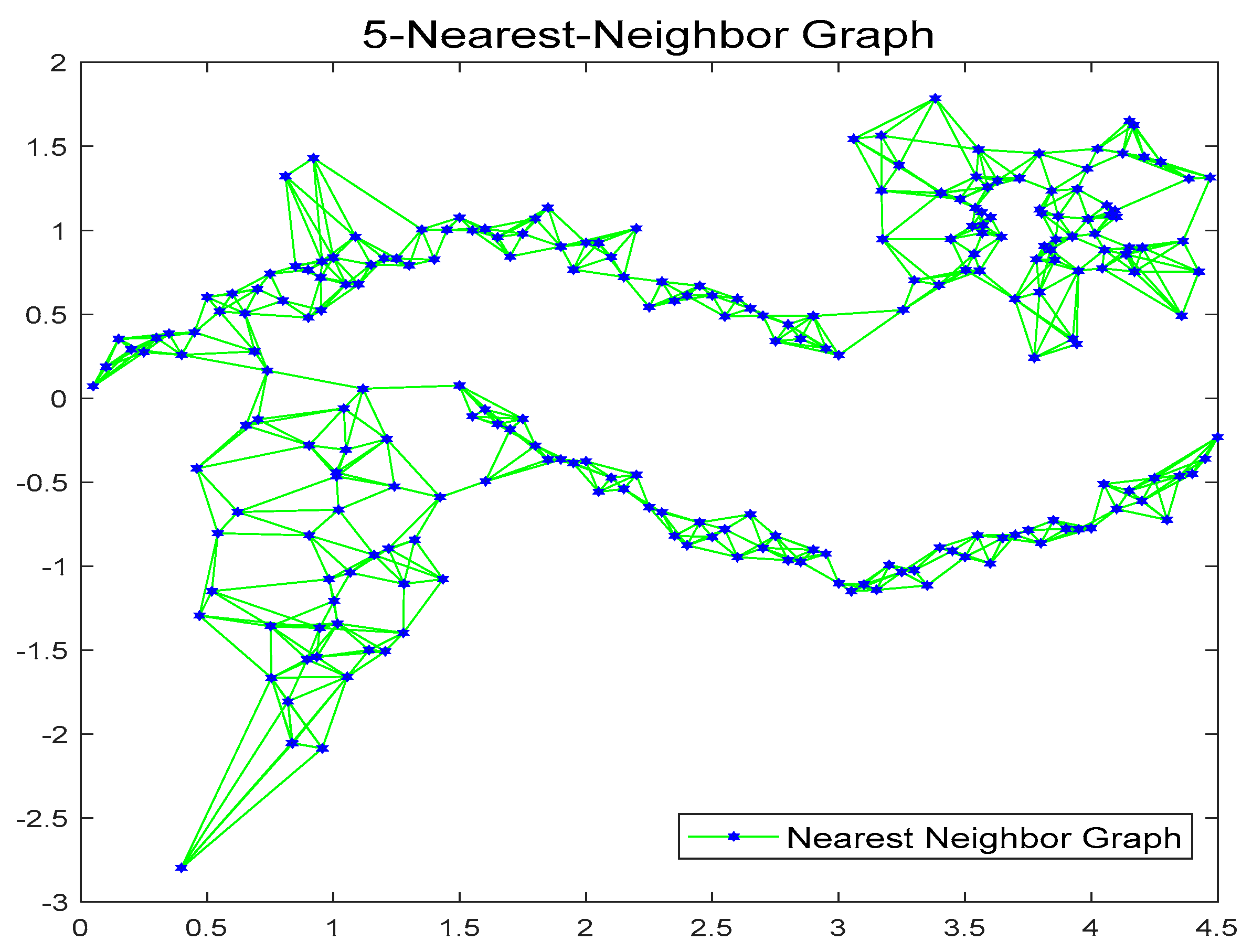
3.2. Establishment of KNN-Graph
3.3. Proposed Algorithm Based on KNN-Graph
| Algorithm 1 MOEA—KG |
| Input: n: Population size Time: The maximum number of generations K: Number of neighbors-graph : probability of mating restriction Output: : Final population
|
| Algorithm 2 Reproduction Operator: |
| Input: : mating pool : a parent solution : scaling operator ; crossover probability Output: : a new candidate solution
|
| Algorithm 3 Environment Selection of SMS—EMOA: |
| Input: : a combination of the old population and the newly generated solutions n: population size Output: : the new population
|
| Algorithm 4 Environment Selection of SPEA2: |
| Input: : a combination of the old population and the newly generated solutions n: population size Output: : the new population
|
4. Experimental Study
4.1. Performance Index
- (1)
- Inverted Generational Distance (IGD)
- (2)
- Hypervolume (HV)
4.2. Comparison and Analysis of KNN-Graph Based Operator on General Problems
4.3. Parameter Sensitivity
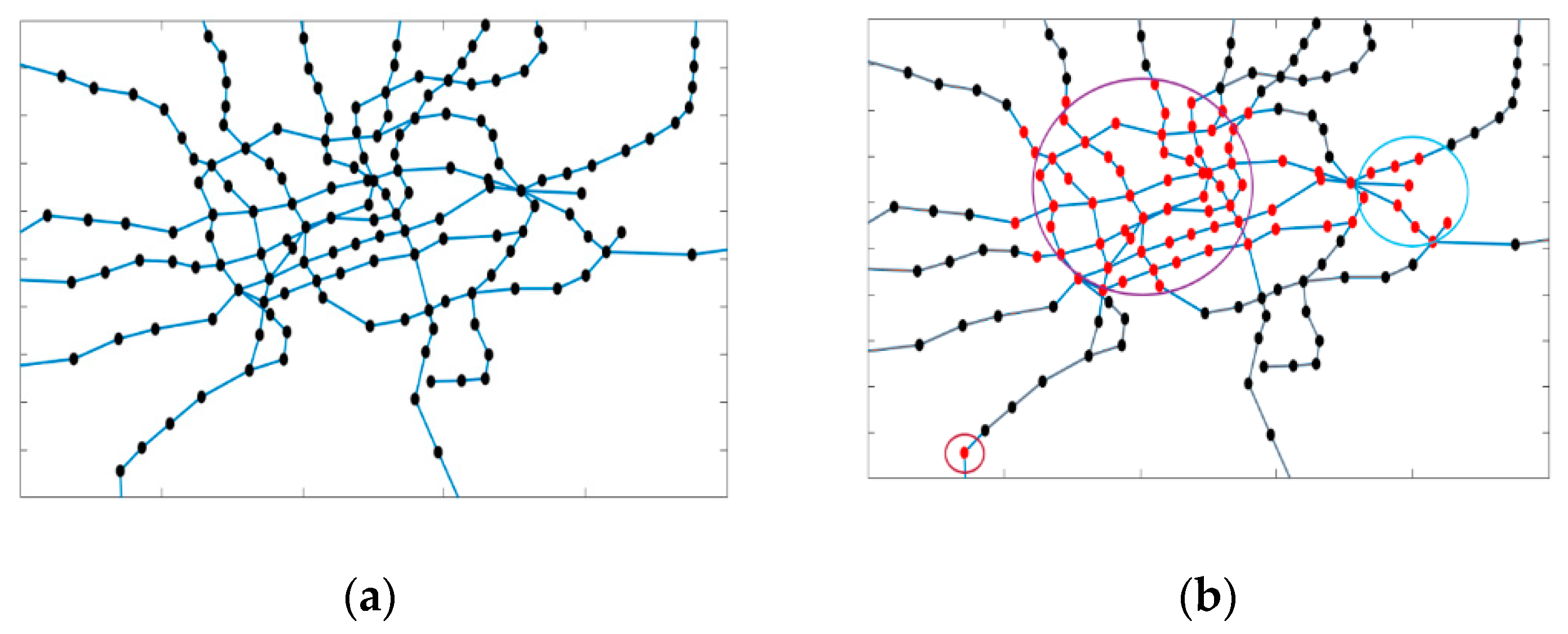
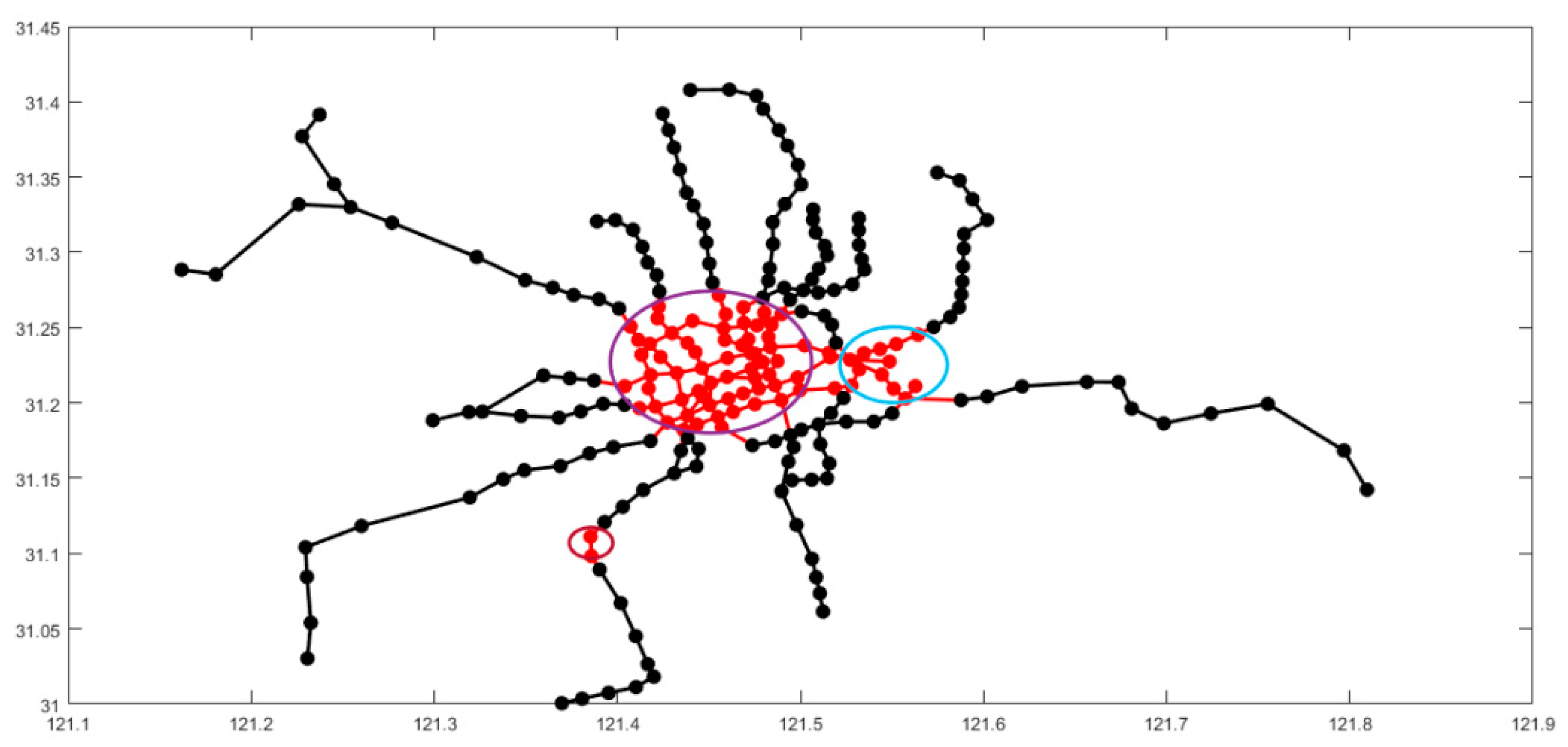
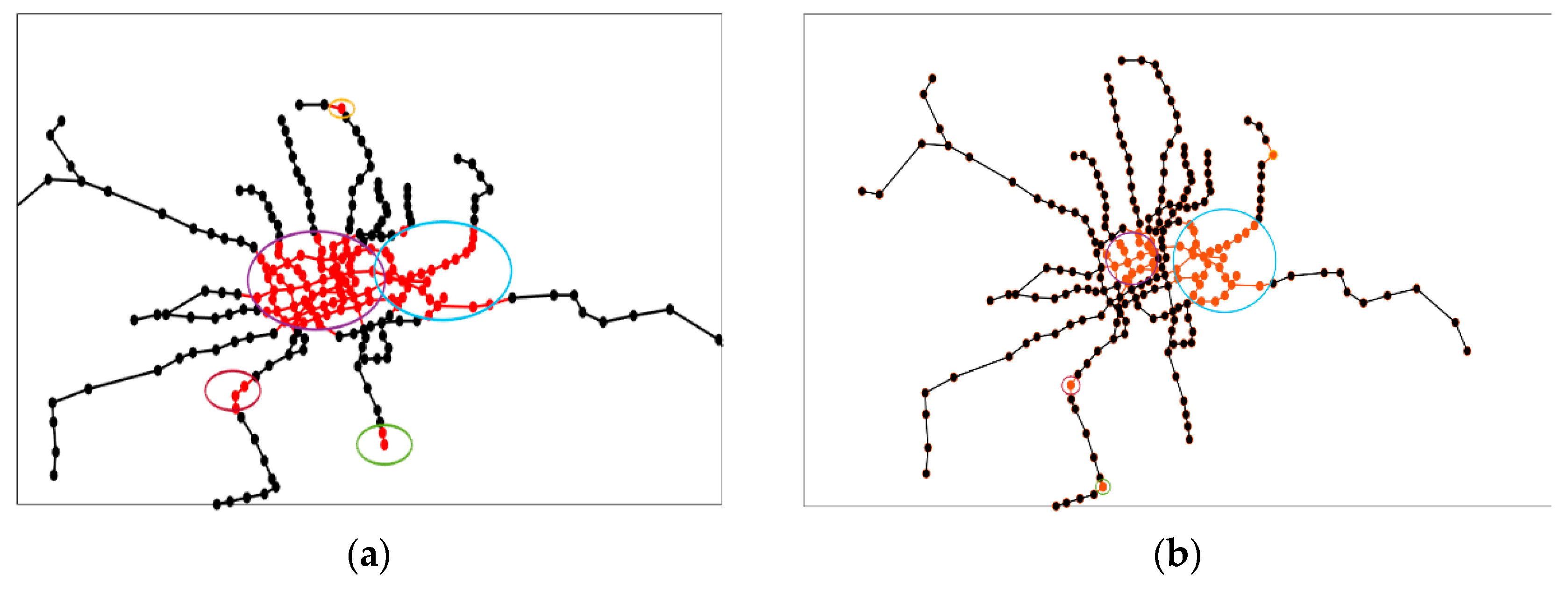
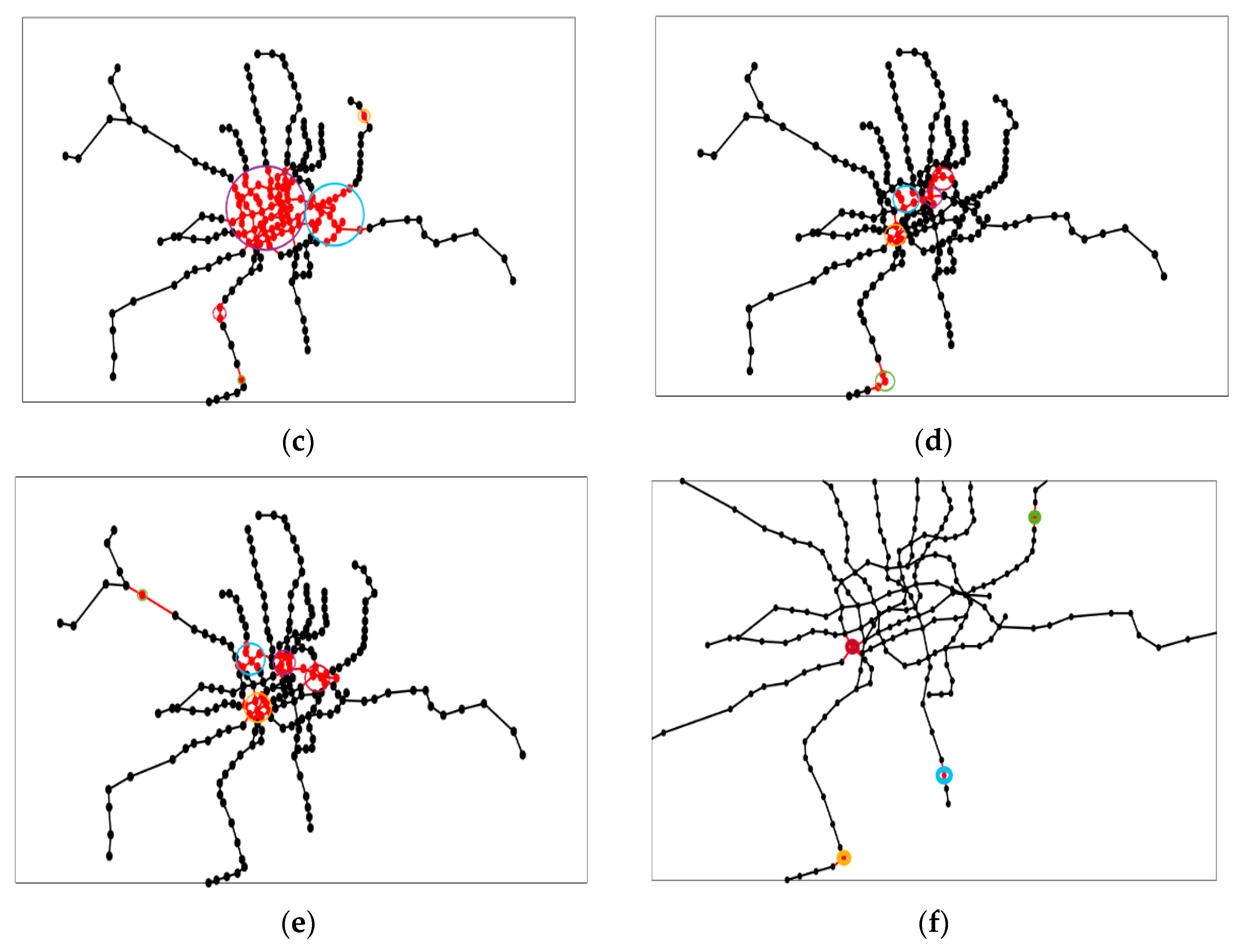
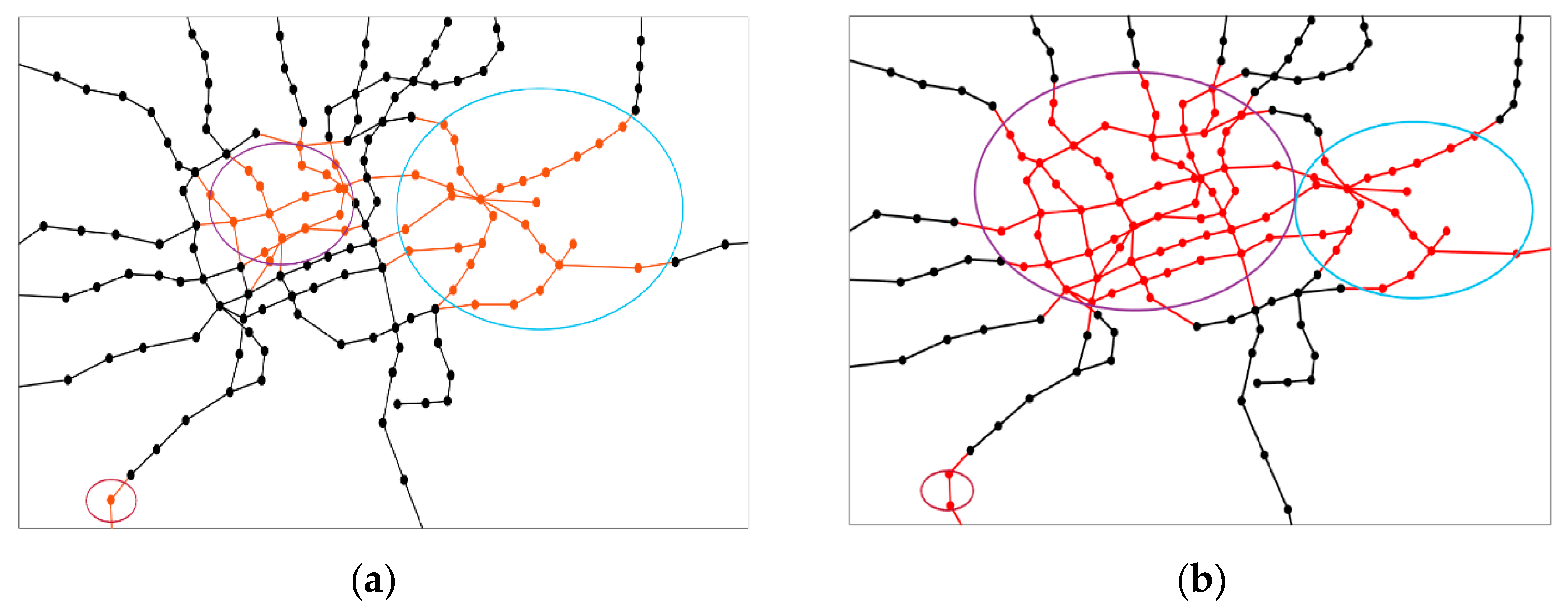
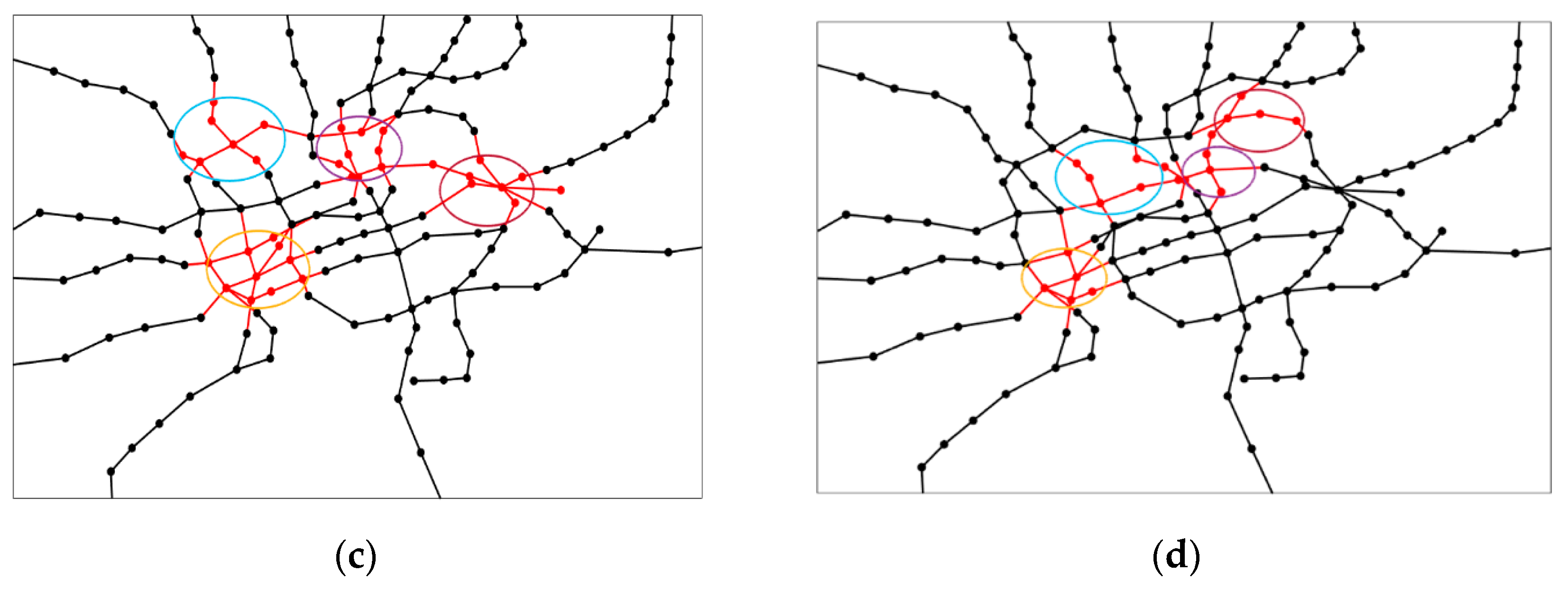
4.4. Results of Network Attack Plan
4.5. Discussion
5. Conclusions and Future Research Directions
Author Contributions
Funding
Conflicts of Interest
References
- Newman, M.E. Finding community structure in networks using the eigenvectors of matrices. Phys. Rev. E 2006, 74, 036104. [Google Scholar] [CrossRef] [PubMed]
- Tanveer, A.; Xue, J.L.; Boon, C.S.; Juan, C.C. Social network analysis based localization technique with clustered closeness centrality for 3d wireless sensor networks. Electronics 2020, 9, 738. [Google Scholar]
- Yustus, E.O.; Sang-Gon, L.; Hoon, J.L. Hierarchical multi-blockchain architecture for scalable internet of things environment. Electronics 2020, 9, 1050. [Google Scholar]
- Antonio, V.; Sérgio, S.; Diogo, D.; Filipe, C.P.; Salviano, S. low-cost lorawan node for agro-intelligence IoT. Electronics 2020, 9, 987. [Google Scholar]
- Stephan, M.; Wagner, N.N. Assessing the vulnerability of supply chains using graph theory. Int. J. Prod. Econ. 2010, 126, 121–129. [Google Scholar]
- Zhao, H.; Zhang, W.; Wang, Y. An effective method to calculate frequency response of distribution networks for plc applications. Electronics 2019, 8, 649. [Google Scholar] [CrossRef]
- Chen, D.Z.; Wang, H. Computing L1 Shortest Paths among Polygonal Obstacles in the Plane. Algorithmica 2019, 81, 2430–2483. [Google Scholar] [CrossRef]
- Moradi, M.; Parsa, S. A Genetic Algorithm Hybridized with an Efficient Mutation Operator for Identifying Hidden Communities of Complex Networks. In Proceedings of the 2018 9th International Symposium on Telecommunications (IST), Tehran, Iran, 17–19 December 2018. [Google Scholar]
- Zhang, Q.; Hao, Y.; Li, Z. Assessing potential likelihood and impacts of landslides on transportation network vulnerability. Transp. Res. Part D 2020, 82, 102304. [Google Scholar] [CrossRef]
- Erik, J.; Lars-Göran, M.a. Road network vulnerability analysis of area-covering disruptions: A grid-based approach with case study. Transp. Res. Part A 2012, 46, 746–760. [Google Scholar]
- Liu, P.; Dai, F.; Yan, K. System model and simulation of “Cloud Operations” based on complex network. Command Control Simul. 2016, 38, 6–11. [Google Scholar]
- Biswas, R.S.; Pal, A.; Werho, T. A Graph Theoretic Approach to Power System Vulnerability Identification. In IEEE Transactions on Power Systems; IEEE: Piscataway, NJ, USA, 2020; p. 1. [Google Scholar]
- Yan, F.; Liu, S.F.; Leng, H. Study on analysis of attack graphs based on conversion. Acta Electron. Sin. 2014, 42, 2477–2480. [Google Scholar]
- Liu, J.; Lu, H.; Chen, M. Macro Perspective Research on Transportation Safety: An Empirical Analysis of Network Characteristics and Vulnerability. Sustainability 2020, 12, 6267. [Google Scholar] [CrossRef]
- Schaffer, J.D. Multiple Objective Optimization with Vector Evaluated Genetic Algorithms. In Proceedings of the First International Conference on Genetic Algorithms and Their Applications, Pittsburgh, PA, USA, 24–26 July 1985; Lawrence Erlbaum Associates: Mahwah, NJ, USA, 1985. [Google Scholar]
- Zhou, A.; Qu, B.Y.; Li, H. Multiobjective evolutionary algorithms: A survey of the state of the art. Swarm Evol. Comput. 2011, 1, 32–49. [Google Scholar] [CrossRef]
- Zhou, A.; Zhang, Q.; Zhang, G. Multi-objective evolutionary algorithm based on mixture Gaussin models. J. Softw. 2014, 25, 913928. [Google Scholar]
- Deb, K.; Pratap, A.; Agarwal, S.; Meyarivan, T. A fast and elitist multi-objective genetic algorithm: NSGA-II. IEEE Trans. Evol. Comput. 2002, 6, 182–197. [Google Scholar] [CrossRef]
- Zitzler, E.; Laumanns, M.; Thiele, L. SPEA2: Improving the Strength Pareto Evolutionary Algorithm; Tech. Rep. TIK-Rep. 103; Swiss Federal Institute of Technology (ETH): Zurich, Switzerland, 2001. [Google Scholar]
- Zitzler, E.; Künzli, S. Indicator-Based Selection in Multi-Objective Search. In Parallel Problem Solving Nature; Springer: Berlin, Germany, 2004; pp. 832–842. [Google Scholar]
- Beume, N.; Naujoks, B.; Emmerich, M. SMS-EMOA: Multi-objective selection based on dominated hypervolume. Eur. J. Oper. Res. 2007, 181, 1653–1669. [Google Scholar] [CrossRef]
- Zhang, Q.; Li, H. MOEA/D: A multi-objective evolutionary algorithm based on decomposition. IEEE Trans. Evol. Comput. 2007, 11, 712–731. [Google Scholar] [CrossRef]
- Liu, H.L.; Gu, F.; Zhang, Q. Decomposition of a multi-objective optimization problem into a number of simple multi-objective subproblems. IEEE Trans. Evol. Comput. 2013, 18, 450–455. [Google Scholar] [CrossRef]
- Li, H.; Zhang, Q. Multi-objective optimization problems with complicated Pareto sets, MOEA/D and NSGA-II. IEEE Trans. Evol. Comput. 2009, 13, 284–302. [Google Scholar] [CrossRef]
- Zhang, H.; Zhou, A.; Song, S.; Zhang, Q.; Gao, X.Z.; Zhang, J. A self-organizing multi-objective evolutionary algorithm. IEEE Trans. Evol. Comput. 2016, 20, 792–806. [Google Scholar] [CrossRef]
- Sun, J.; Zhang, H.; Zhou, A.; Zhang, Q.; Zhang, K.; Tu, Z.; Ye, K. Learning from a stream of nonstationary and dependent data in multi-objective evolutionary optimization. IEEE Trans. Evol. Comput. 2019, 23, 541–555. [Google Scholar] [CrossRef]
- Li, X.; Song, S.; Zhang, H. Evolutionary multi-objective optimization with clustering-based self-adaptive mating restriction strategy. Soft Comput. 2019, 23, 3303–3325. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, H.; Zhang, Y. A Spectral Clustering-Based Multi-Source Mating Selection Strategy in Evolutionary Multi-Objective Optimization. IEEE Access 2019, 7, 131851–131864. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, H.; Zhang, Y. Adaptive population structure learning in evolutionary multi-objective optimization. Soft Comput. 2019, 3, 10025–10042. [Google Scholar] [CrossRef]
- Albert, R.; Jeong, H.; Barabasi, A.L. Error and attack tolerance of complex networks. Nature 2000, 406, 378–382. [Google Scholar] [CrossRef]
- Crucitti, P.; Latora, V.; Marchior, M. Error and attack tolerance of complex networks. Physica 2004, 340, 388–394. [Google Scholar] [CrossRef]
- Zhang, L.; Huang, S.G.; Zhao, W.J. Research on optimal network topology based on genetic algorithm. Microelectron. Comput. 2009, 26, 64–66. [Google Scholar]
- Zhang, H.; Zhang, X.; Song, S. An Affinity propagation-based multi-objective evolutionary algorithm for selecting optimal aiming points of missiles. Soft Comput. 2017, 21, 3013–3031. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, Z.; Zhang, H. Fuzzy c-means clustering-based mating restriction for multi-objective optimization. Int. J. Mach. Learn. Cybern. 2017, 9, 1–13. [Google Scholar]
- Zhang, H.; Song, S.; Zhou, A. A clustering based multi-objective evolutionary algorithm. In Proceedings of the 2016 IEEE Congress on Evolutionary Computation (CEC), Beijing, China, 6–11 July 2014; pp. 2758–2770. [Google Scholar]
- Zhang, H.; Zhang, X.; Gao, X.Z. Self-organizing multi-objective optimization based on decomposition with neighborhood ensemble. Neurocomputing 2016, 173, 1868–1884. [Google Scholar] [CrossRef]
- Zitzler, E.; Laumanns, M.; Thiele, L. SPEA2: Improving the strength Pareto evolutionary algorithm for multi-objective optimization; Evolutionary Methods for Design, Optimization and Control with Applications to Industrial Problems. In Proceedings of the EUROGEN’2001, Athens, Greece, 19–21 September 2001. [Google Scholar]
- Buche, D.; Uidati, G.; Stoll, P. Self-Organizing Maps for Pareto Optimization of Airfoils. Lect. Notes Comput. Ence 2002, 2439, 122–131. [Google Scholar]
- Zitzler, E.; Thiele, L.; Laumanns, M. Performance assessment of multi-objective optimizers: An analysis and review. IEEE Trans. Evol. Comput. 2003, 7, 117–132. [Google Scholar] [CrossRef]
- Zitzler, E.; Thiele, L. Multi-objective evolutionary algorithms: A comparative case study and the strength Pareto approach. IEEE Trans. Evol. Comput. 1999, 3, 257–271. [Google Scholar] [CrossRef]
- Zhang, Q.; Zhou, A.; Jin, Y. RM-MEDA: A regularity model-based multi-objective estimation of distribution algorithm. IEEE Trans. Evol. Comput. 2008, 12, 41–63. [Google Scholar] [CrossRef]
- Gu, F.; Liu, H.L.; Tan, K.C. A multi-objective evolutionary algorithm using dynamic weight design method. Int. J. Innov. Comput. Inf. Control 2012, 8, 3677–3688. [Google Scholar]
- Zhang, Q.; Zhou, A.; Zhao, S. Multi-Objective Optimization Test Instances for the CEC 2009 Special Session and Competition. In University of Essex, Colchester, UK and Nanyang Technological University, Singapore, Special Session on Performance Assessment of Multi-Objective Optimization Algorithms, Technical Report; Mechanical Engineering: New York, NY, USA, 2008. [Google Scholar]






| Instance | Parameter Settings |
|---|---|
| Public parameter | Population size N: 100 |
| The maximum number of evolutions T: 300 | |
| Number of operations: 30 | |
| DE operator | , |
| MOEA/D-DE | Neighborhood size NS: 5 |
| Parent selection probability : 0.9 | |
| Number of new solutions nr: 0.2 | |
| IM-MOEA | Number of reference vectors K: 10 |
| RM-MEDA | Number of clusters K: 5 |
| Number of clustering iterations: 50 | |
| Sampling expansion rate: 0.25 | |
| SMEA | Initial learning rate : 0.9 |
| Neighbor mating pool size H: 10 | |
| Mating limit probability : 0.9 | |
| Proposed MOEA | Nearest neighbor size K: 10 |
| Gaussian similarity bandwidth σ: 1 | |
| Mating restriction probability β: 0.7 |
| Instance. | SMS-EMOA-DE | SMS-EMOA-KG |
|---|---|---|
| IGD | ||
| GLT1 | 1.4693 × 10−1 (2.12 × 10−2) − | 1.8742 × 10−3 (6.57 × 10−5) |
| GLT2 | 9.0037 × 10−1 (5.12 × 10−1) − | 2.9636 × 10−2 (8.15 × 10−4) |
| GLT3 | 2.0581 × 10−1 (4.16 × 10−2) − | 5.7233 × 10−3 (1.61 × 10−3) |
| GLT4 | 2.2679 × 10−1 (3.10 × 10−2) − | 2.9274 × 10−2 (4.57 × 10−2) |
| GLT5 | 1.8252 × 10−1 (6.64 × 10−2) − | 6.5220 × 10−2 (5.92 × 10−3) |
| GLT6 | 3.1223 × 10−1 (2.64 × 10−1) = | 1.2574 × 10−1 (7.16 × 10−2) |
| +/−/= | 0/5/1 | - |
| Instance | SPEA2-DE | SPEA2-KG |
|---|---|---|
| IGD | ||
| GLT1 | 1.3775 × 10−1 (2.60 × 10−2) − | 2.6329 × 10−3 (1.27 × 10−4) |
| GLT2 | 5.9186 × 10−1 (3.30 × 10−1) − | 3.0671 × 10−2 (1.21 × 10−3) |
| GLT3 | 1.6531 × 10−1 (5.41 × 10−2) − | 8.3622 × 10−3 (5.54 × 10−3) |
| GLT4 | 2.1576 × 10−1 (3.18 × 10−2) − | 6.1220 × 10−3 (1.26 × 10−4) |
| GLT5 | 5.6489 × 10−2 (2.20 × 10−2) = | 4.2734 × 10−2 (1.94 × 10−3) |
| GLT6 | 1.9984 × 10−1 (2.66 × 10−1) = | 7.9232 × 10−2 (6.32 × 10−2) |
| +/−/= | 0/4/2 | - |
| Instance | MOEA/D-DE | RM-MEDA | IMMOEA | SMEA | SMS-EMOA-KG | SPEA2-KG |
|---|---|---|---|---|---|---|
| IGD | ||||||
| GLT1 | 3.6774 × 10−3 (2.61 × 10−5) [3] | 4.2663 × 10−3 (1.23 × 10−3) [4] | 2.2247 × 10−2 (2.71 × 10−3) [6] | 1.4459 × 10−2 (9.85 × 10−3) [5] | 2.4453 × 10−3 (3.71 × 10−3) [1] | 2.9421 × 10−3 (1.39 × 10−3) [2] |
| GLT2 | 3.2232 × 10−1 (3.61 × 10−2) [4] | 3.2144 × 10−2 (1.17 × 10−3) [3] | 3.8994 × 10−1 (8.99 × 10−2) [6] | 3.2742 × 10−2 (1.92 × 10−3) [5] | 2.9920 × 10−2 (4.30 × 10−4) [1] | 3.0933 × 10−2 (6.18 × 10−4) [2] |
| GLT3 | 2.1921 × 10−2 (3.85 × 10−3) [3] | 1.3770 × 10−2 (1.15 × 10−2) [2] | 1.1284 × 10−1 (3.50 × 10−2) [6] | 3.8291 × 10−2 (4.23 × 10−3) [5] | 5.2081 × 10−3 (2.01 × 10−4) [1] | 2.3559 × 10−2 (3.60 × 10−2) [4] |
| GLT4 | 9.5931 × 10−3 (5.31 × 10−5) [4] | 6.2274 × 10−3 (2.06 × 10−4) [2] | 2.7685 × 10−2 (8.94 × 10−3) [5] | 4.8657 × 10−2 (8.25 × 10−2) [6] | 8.1160 × 10−3 (2.05 × 10−3) [3] | 6.2081 × 10−3 (1.85 × 10−3) [1] |
| GLT5 | 1.37291 × 10−1 (1.10 × 10−3) [6] | 5.1563 × 10−2 (2.09 × 10−3) [2] | 7.7029 × 10−2 (4.17 × 10−3) [5] | 7.5621 × 10−2 (6.99 × 10−3) [4] | 6.8898 × 10−2 (3.05 × 10−3) [3] | 4.3850 × 10−2 (1.26 × 10−3) [1] |
| GLT6 | 8.3443 × 10−2 (6.88 × 10−3) [6] | 5.2764 × 10−2 (7.66 × 10−4) [1] | 7.3297 × 10−2 (1.00 × 10−3) [2] | 8.0387 × 10−2 (4.19 × 10−3) [5] | 7.6088 × 10−1 (6.68 × 10−2) [3] | 7.6102 × 10−2 (2.03 × 10−2) [4] |
| UF1 | 8.6461 × 10−2 (2.28 × 10−2) [3] | 9.5013 × 10−2 (7.04 × 10−3) [5] | 9.7365 × 10−2 (7.44 × 10−3) [6] | 8.2864 × 10−2 (1.18 × 10−2) [2] | 8.1144 × 10−2 (2.95 × 10−2) [1] | 9.2310 × 10−2 (4.60 × 10−2) [4] |
| UF2 | 3.9917 × 10−2 (2.25 × 10−2) [5] | 3.3042 × 10−2 (6.31 × 10−3) [3] | 3.8612 × 10−2 (9.89 × 10−3) [4] | 5.2072 × 10−2 (5.48 × 10−3) [6] | 3.0435 × 10−2 (6.83 × 10−3) [1] | 3.0879 × 10−2 (4.21 × 10−3) [2] |
| UF3 | 2.0154 × 10−1 (7.46 × 10−2) [6] | 1.0445 × 10−1 (6.51 × 10−2) [1] | 1.3722 × 10−1 (1.54 × 10−2) [2] | 1.6362 × 10−1 (1.00 × 10−2) [5] | 1.6010 × 10−1 (2.10 × 10−2) [3] | 1.6331 × 10−1 (2.89 × 10−2) [4] |
| UF4 | 9.6573 × 10−2 (8.07 × 10−3) [5] | 1.0032 × 10−1 (8.35 × 10−3) [6] | 8.7950 × 10−2 (3.88 × 10−3) [4] | 7.5709 × 10−2 (1.02 × 10−2) [2] | 7.2361 × 10−2 (8.24 × 10−3) [1] | 7.6709 × 10−2 (1.21 × 10−2) [3] |
| UF5 | 9.3052 × 10−1 (2.04 × 10−1) [1] | 1.2277 (4.80 × 10−1) [4] | 1.1768(1.99 × 10−1) [2] | 1.3446 (2.37 × 10−1) [5] | 1.1961 (2.40 × 10−1) [3] | 1.3565 (2.28 × 10−1) [6] |
| UF6 | 3.2487 × 10−1 (9.43 × 10−2) [2] | 4.8169 × 10−1 (9.66 × 10−2) [5] | 2.9028 × 10−1 (4.60 × 10−2) [1] | 5.1783 × 10−1 (7.30 × 10−2) [6] | 4.0794 × 10−1 (4.58 × 10−2) [3] | 4.2120 × 10−1 (4.63 × 10−2) [4] |
| UF7 | 1.3295 × 10−1 (2.07 × 10−1) [6] | 6.6774 × 10−2 (1.24 × 10−2) [3] | 1.1074 × 10−1 (8.74 × 10−2) [5] | 4.6647 × 10−2 (2.15 × 10−2) [2] | 7.1989 × 10−2 (1.10 × 10−1) [4] | 4.5395 × 10−2 (1.30 × 10−2) [1] |
| UF8 | 3.8785 × 10−1 (2.15 × 10−2) [5] | 3.6714 × 10−1 (3.99 × 10−2) [3] | 3.7651 × 10−1 (6.40 × 10−3) [4] | 3.5880 × 10−1 (9.20 × 10−2) [2] | 3.3582 × 10−1 (7.13 × 10−2) [1] | 6.6597 × 10−1 (1.46 × 10−1) [6] |
| UF9 | 3.2838 × 10−1 (8.93 × 10−2) [3] | 4.9841 × 10−1 (1.13 × 10−1) [5] | 3.9872 × 10−1 (4.10 × 10−2) [4] | 2.4864 × 10−1 (1.00 × 10−1) [1] | 3.1443 × 10−1 (9.29 × 10−2) [2] | 9.5494 × 10−1 (2.02 × 10−1) [6] |
| UF10 | 1.0303(1.13 × 10−1) [2] | 2.6789(2.80 × 10−1) [5] | 3.1850 × 10−1 (7.19 × 10−3) [1] | 2.7334(2.43 × 10−1) [6] | 1.5658(1.44 × 10−1) [3] | 2.5390(4.22 × 10−1) [4] |
| HV | ||||||
| GLT1 | 5.6182 × 10−1 (3.14 × 10−4) [4] | 5.6428 × 10−1 (9.64 × 10−3) [3] | 5.0380 × 10−1 (5.95 × 10−3) [6] | 5.2400 × 10−1 (2.39 × 10−2) [5] | 5.6610 × 10−1 (2.10 × 10−2) [1] | 5.6588 × 10−1 (9.46 × 10−3) [2] |
| GLT2 | 9.5478 (2.78 × 10−2) [5] | 9.8375 (1.07 × 10−2) [4] | 8.7650 (3.02 × 10−1) [6] | 9.8701 (6.89 × 10−3) [2] | 9.9096 (4.73 × 10−4) [1] | 9.8408 (6.59 × 10−3) [3] |
| GLT3 | 1.1535 (6.90 × 10−4) [5] | 1.1559 (9.23 × 10−4) [3] | 1.1446 (3.30 × 10−3) [6] | 1.1552 (4.69 × 10−4) [4] | 1.1588 (8.23 × 10−5) [1] | 1.1560 (3.36 × 10−3) [2] |
| GLT4 | 1.4070 (4.89 × 10−4) [3] | 1.4080 (9.38 × 10−4) [2] | 1.3709 (1.32 × 10−2) [5] | 1.3791 (5.15 × 10−2) [4] | 1.2153 (3.89 × 10−1) [6] | 1.4081 (9.02 × 10−4) [1] |
| GLT5 | 1.2656 (9.88 × 10−4) [3] | 1.2679 (3.01 × 10−3) [2] | 1.2580 (1.42 × 10−3) [4] | 1.2382 (6.38 × 10−3) [6] | 1.2560 (4.47 × 10−3) [5] | 1.2817 (1.49 × 10−3) [1] |
| GLT6 | 1.2502 (4.76 × 10−3) [2] | 1.2591 (1.33 × 10−3) [1] | 1.2357 (4.54 × 10−3) [3] | 1.2316 (1.11 × 10−2) [4] | 1.1409 (8.06 × 10−2) [5] | 1.1284 (4.31 × 10−2) [6] |
| UF1 | 7.1640 × 10−1 (4.06 × 10−2) [3] | 7.0686 × 10−1 (1.44 × 10−2) [5] | 7.3922 × 10−1 (2.21 × 10−2) [1] | 7.2245 × 10−1 (2.18 × 10−2) [2] | 7.0417 × 10−1 (5.24 × 10−2) [6] | 7.1295 × 10−1 (6.68 × 10−2) [4] |
| UF2 | 8.1799 × 10−1 (2.73 × 10−2) [5] | 8.2188 × 10−1 (5.42 × 10−3) [4] | 8.2465 × 10−1 (7.17 × 10−3) [3] | 7.9779 × 10−1 (7.70 × 10−3) [6] | 8.2827 × 10−1 (8.18 × 10−3) [1] | 8.2650 × 10−1 (5.58 × 10−3) [2] |
| UF3 | 5.3662 × 10−1 (1.07 × 10−1) [6] | 6.9713 × 10−1 (9.91 × 10−2) [1] | 6.3494 × 10−1 (3.75 × 10−2) [2] | 6.2063 × 10−1 (1.28 × 10−2) [3] | 6.0526 × 10−1 (4.27 × 10−2) [4] | 6.0525 × 10−1 (4.62 × 10−2) [5] |
| UF4 | 3.7932 × 10−1 (1.21 × 10−2) [5] | 3.7227 × 10−1 (1.28 × 10−2) [6] | 3.9313 × 10−1 (8.06 × 10−3) [4] | 3.9360 × 10−1 (1.55 × 10−2) [3] | 3.9765 × 10−1 (1.14 × 10−2) [1] | 3.9606 × 10−1 (2.02 × 10−2) [2] |
| UF5 | 3.7857 × 10−3 (7.59 × 10−3) [1] | 0.0000 (0.00) [2] | 0.0000 (0.00) [2] | 0.0000 (0.00) [2] | 0.0000 (0.00) [2] | 0.0000 (0.00) [2] |
| UF6 | 2.8723 × 10−1 (1.01 × 10−1) [1] | 5.8323 × 10−2 (8.76 × 10−3) [4] | 2.6305 × 10−1 (2.56 × 10−2) [2] | 6.0804 × 10−2 (3.03 × 10−2) [5] | 1.3355 × 10−1 (5.15 × 10−2) [3] | 9.7642 × 10−2 (6.55 × 10−2) [6] |
| UF7 | 5.5604 × 10−1 (1.76 × 10−1) [5] | 5.9038 × 10−1 (2.25 × 10−2) [4] | 5.4816 × 10−1 (1.04 × 10−1) [6] | 6.2335 × 10−1 (3.72 × 10−2) [2] | 6.1029 × 10−1 (1.07 × 10−1) [3] | 6.2370 × 10−1 (2.38 × 10−2) [1] |
| UF8 | 3.8148 × 10−1 (2.15 × 10−2) [4] | 1.9583 × 10−1 (6.27 × 10−2) [5] | 4.1458 × 10−1 (9.78 × 10−3) [2] | 3.8590 × 10−1 (4.13 × 10−2) [3] | 4.2332 × 10−1 (3.34 × 10−2) [1] | 2.8157 × 10−2 (2.84 × 10−2) [6] |
| UF9 | 5.9709 × 10−1 (1.33 × 10−1) [3] | 3.3671 × 10−1 (1.41 × 10−1) [5] | 4.4102 × 10−1 (3.11 × 10−2) [4] | 7.6286 × 10−1 (5.12 × 10−2) [1] | 6.8028 × 10−1 (1.17 × 10−1) [2] | 1.3613 × 10−2 (2.82 × 10−2) [6] |
| UF10 | 1.0574 × 10−4 (2.59 × 10−4) [2] | 0.0000 (0.00) [3] | 2.9112 × 10−1 (2.53 × 10−2) [1] | 0.0000 (0.00) [3] | 0.0000 (0.00) [3] | 0.0000 (0.00) [3] |
| Mean Rank | 3.7813 | 3.375 | 3.75 | 3.8125 | 2.4688 | 3.3125 |
| SMS-EMOA-KG | MOEA/D-DE | RM-MEDA | IM-MEDA | SMEA | |
|---|---|---|---|---|---|
| Mean of HV | 0.86261 | 0.8342 | 0.8357 | 0.8350 | 0.8370 |
| Variance of HV | 0.0518 | 0.0519 | 0.0385 | 0.0340 | 0.0763 |
| Attacked Time | 0~19 | 20~39 | 40~59 | 60~79 | 80~100 |
|---|---|---|---|---|---|
| Count | 151 | 22 | 35 | 33 | 2 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, J.; Wang, S.; Zhang, H.; Zhou, A. A Multi-Objective Evolutionary Algorithm Based on KNN-Graph for Traffic Network Attack. Electronics 2020, 9, 1589. https://doi.org/10.3390/electronics9101589
Li J, Wang S, Zhang H, Zhou A. A Multi-Objective Evolutionary Algorithm Based on KNN-Graph for Traffic Network Attack. Electronics. 2020; 9(10):1589. https://doi.org/10.3390/electronics9101589
Chicago/Turabian StyleLi, Junhui, Shuai Wang, Hu Zhang, and Aimin Zhou. 2020. "A Multi-Objective Evolutionary Algorithm Based on KNN-Graph for Traffic Network Attack" Electronics 9, no. 10: 1589. https://doi.org/10.3390/electronics9101589
APA StyleLi, J., Wang, S., Zhang, H., & Zhou, A. (2020). A Multi-Objective Evolutionary Algorithm Based on KNN-Graph for Traffic Network Attack. Electronics, 9(10), 1589. https://doi.org/10.3390/electronics9101589






