1. Introduction
With the rapid development of mobile internet technology, the broadcast characteristics of wireless information have led to severe information leakage problems. Physical layer security has increasingly attracted research interests in 5th-Generation (5G) mobile communication because it can ensure safe protection from information theory even when eavesdroppers have a powerful computing ability [
1]. Massive multiple-input multiple-output (MIMO) is a promising technology in 5G which can be used to improve the spectrum efficiency and security of wireless communication. Moreover, massive MIMO can be used to enhance the security and power transfer efficiency of a simultaneous wireless information and power transfer (SWIPT) system because it can beamform the energy and information more accurately with large array gain [
2,
3].
Secure problems in massive MIMO systems have been investigated in References [
4,
5,
6,
7,
8,
9,
10,
11]. The authors in Reference [
4] studied the impact of residual hardware impairment (HWI) on massive MIMO secure communication and showed the HWI has a negative impact on information security. In Reference [
5], S. Timilsina et al. studied the effect of active eavesdropping on physical layer security and revealed that active eavesdroppers had a stronger ability to eavesdrop confidential information with higher pilot power. In Reference [
6], Z. Chu et al. studied a MIMO secrecy channel with SWIPT. The minimum harvested energy is maximized under the secrecy rate requirements. In Reference [
7], H. D. Tuan et al. considered the problem of power allocation to maximize the worst links’ secrecy throughput or the network’s secure energy efficiency (SEE) under various scenarios of available channel state information. In Reference [
8], C. Du et al. studied massive MIMO relay-assisted secure communication systems, which considered the channel reciprocity in time division duplexing (TDD) mode and the energy harvesting at the relay. An energy efficiency power allocation (EEPA) scheme is proposed to maximize SEE. In Reference [
9], J. He et al. studied the effect of channel aging on full-duplex massive MIMO spectral efficiency (SE) and energy efficiency (EE) and proposed four power allocation schemes. In Reference [
10], S. Timilsina et al. studied relay-assisted massive MIMO downlink secure transmission with the random and zero-space degrees of freedom of artificial noise (AN) matrix vectors. In Reference [
11], J. Zhu et al. studied the influence of phase noise on the downlink of secure massive MIMO with a SWIPT system. The closed-form lower bound on the worst-case secrecy rate is derived. However, most of the above works focus on security rate optimization. Energy efficiency has been one of the key performance indexes for 5G because green communication has become the developing trend and direction of the future society [
12]. Therefore, it is important to optimize SEE for massive MIMO with SWIPT.
In this paper, we consider secure transmission in massive MIMO systems with SWIPT. A secure energy-efficiency resource allocation (SERA) algorithm for massive MIMO systems with SWIPT is proposed. The users utilize the harvesting energy in the previous time slot to transmit pilot information, and the active eavesdropper transmits the same pilot information as a user to achieve the purpose of eavesdropping. To reduce the eavesdropping ability of the active eavesdropper, the base station (BS) uses AN auxiliary communication. At the BS, the power splitting ratio is used to reasonably allocate the information transmission power and the AN transmission power. The AN matrix-vector at the BS adopts the null space beamforming [
13], which is simplified by the properties of the Wishart matrix. By adopting a variable substitution method, the non-convex SEE maximization problem is converted into a series of parameter optimization subproblems by fractional programming. A joint power splitting ratio and the BS transmitted power allocation algorithm are proposed to maximize the minimum (max–min) SEE of the user. Simulation results are also compared with the users’ system SEE maximization in Reference [
14,
15] and the secure rate maximization in Reference [
16] to confirm the effectiveness and superiority of the SERA algorithm.
Notation: Bold letters denote matrices or vectors, denotes conjugate transposes of matrices or vectors, denotes transpose of matrices or vectors, denotes trace of matrices, denotes mathematical expectation, ⊗ are the Kronecker product, and .
2. System Model
As shown in
Figure 1, a single-cell downlink massive MIMO system with SWIPT consists of one BS connected with
K users and one eavesdropper [
17,
18,
19]. The number of transmitting antennas at BS is
N, which satisfies
. Each user and the eavesdropper are equipped with a single antenna. The BS simultaneously serves
K users in the same time-frequency resource block [
20]. Especially, it is assumed that the active eavesdropper perfectly knows the pilot sequence transmitted by the
mth user node [
21], where
. Without loss of generally, we suppose that each time slot has a unit length. Each time slot has two parts. In the first time slot
, users use the energy harvested by the previous time block to transmit pilot information to the BS. The active eavesdropper also transmits pilot information to the BS. In the
time slot, BS transmits information or energy to users and the eavesdropper. The user’s terminal receiver decodes the signal into two parts; one part is used for information decoding, and the other is used for energy harvesting. The eavesdropper mainly is used for information decoding [
15].
The BS-to-user and BS-to-eavesdropper channels are denoted by
, which is given by
where
and
are the small scale Rayleigh fading and where
and
are the path loss from BS-to-user and BS-to-eavesdropper channels, respectively. The path loss is modeled as
and
, where
r is the path loss exponent factor,
is the distance between the BS and user
m, and
d is the distance between the BS and eavesdropper [
5].
In TDD massive MIMO, the users-to-BS and eavesdropper-to-BS channels are estimated at the BS via uplink pilots transmitted. The BS stores the channel state information (CSI) through channel reciprocity. The superimposed pilot signal received at BS is
where
and
express the average transmit powers from the users and the eavesdropper;
, where
and
for
and
.
is the noise with independent and identically distributed (i.i.d.)
distribution for each element. Assuming that BS uses the minimum mean squared error (MMSE) estimation, the BS-to-user channel is obtained as follows [
5,
19]:
where
,
i,
,
is the estimation error matrix.
To prevent the eavesdropper from stealing confidential information, the BS introduces AN subsidiary communications [
13]. The BS uses the power splitting ratio to information power and AN transmission power [
5,
19]; the transmission information at BS is given as follows:
where
represents the transmit power;
, where
is the power splitting ratio coefficient of the BS for user
; channel matrices
and
denote the precoding matrix for the data and AN [
13,
22];
is the signal vector transmitted to
K users satisfying
; and
is an AN sequence.
The users utilize the power splitting ratio to decode information from BS simultaneously, where one part is used to harvest energy and the other part is decoded into useful information, and the eavesdropper mainly wiretaps useful information from BS [
23]. Therefore, the
mth user and the eavesdropper receiving useful information is given as follows [
5,
19,
20]:
where
express the power splitting receiver from users. The first item denotes the desired signal, the second term is the beamforming gain uncertainty, the third term is the inter-user interference, and the remaining terms are AN leaked to legitimate users and the additive white Gaussian noise (AWGN) at the
mth user node. The
mth user harvest energy is given by
where
is the energy conversion efficiency for user
m, which transfers the harvested energy into electric energy stored by the users and eavesdropper.
Provided that the worst-case uncorrelated additive noise distributed as independent Gaussian noise has the same variance [
5], the achievable rate of the
mth user can be lower bounded by the following expression
where
is given by
where
is the effective noise which is defined as follows:
Provided that the eavesdropper eliminates the other users interference terms [
5,
19], the upper bounded achievable rate of the
mth user signal leaked into eavesdropper can be written as
where
is expressed as
Hence, the
mth user achievable secure rate is as follows [
5,
19]:
Using wishart matrix to simplify Equations (8)–(14) as in References [
5,
19], the harvesting energy by user
m can be written as follows:
The achievable secure rate of user
m is given by [
5,
19]
The achievable rate of the
mth user signal leaked into eavesdropper is simplified as follows [
5,
19]:
where
,
,
, and
.
3. Problem Formulation and Energy-Efficient Algorithm
With the above analysis for achievable rate and energy for user and eavesdropper, the max–min SEE optimization problem of the system can be expressed as
In , the objective is to maximize and minimize SEE of the system. and are the transmit power constraints, and is the energy harvested constraint for user m. and denote the power consumption of the mth user and circuit consumption, and denotes the power consumption coefficient.
The optimal solution to Equation (18) can be solved by fractional programming [
24] to find zero roots of the following parameter optimization problem
[
25]:
According to the conclusions in References [
24,
25], the optimal solution to Equation (19) is
such that
is held. We define
as
Due to the non-smoothness of the objective function, we introduce a new variable
t to transform the equivalent non-smooth optimization problem in Equation (20) into a smooth optimization problem. Equation (18) can be equivalently reformulated as
has four optimization variables. First, fix BS’ power splitting ratio coefficient and the transmit power are used to obtain a suboptimal solution. Then, use the suboptimal solution of iterative optimization power splitting ratio coefficient and the BS transmit power . Finally, update variable t.
Firstly, optimize
. Because
is only associated with
from Equations (16) and (20), which is monotonic decreasing function about
,
depends on constraint
.
Then, optimize
, and
is a hard problem. In Equation (21), the difference of two convex functions is non-convex. Therefore, we need to replace the non-convex part in Equation (21) by linear approximation and we rewrite constraint
; let
Finally, we use the difference of convex functions algorithm (DCA) from References [
14,
26].
is as follows:
In Equation (25),
is the difference between two concave functions, which can be effectively solved by sequential convex programming. At step
n, we get an iterative power allocation. We use first-order Taylor expansion
We further transform
into
now is a smooth and standard convex optimization problem, and thus, it can be efficiently solved by successive convex approximation (SCA) method [
15].
Up till now, the convex programming
is capable of successively approximating the solution of the original SEE optimization problem. We will employ the bisection method in one-dimension to update
where
is the optimal values of
in Equation (22) and where
and
are the optimal values of
and
from Algorithm 1.
| Algorithm 1 SCA algorithm for solving Equation (26) |
Initialization Set and the tolerance . Set ,calculate repeat Solve (27) to obtain and Set , and and Calculate until
|
Based on the above discussion, we propose a SERA algorithm for the max–min SEE in massive MIMO systems by Algorithm 2.
Then, we characterize the computational complexity of the proposed algorithm to get a better insight into the computational complexity of the SERA algorithm. The SCA method complexity is
[
27];
is the convergence precision, and
I denotes the value of iterations. Therefore, the total computational complexity of the SERA algorithm is about
, and
L is the length of the value.
| Algorithm 2 SERA algorithm for the min user’ SEE maximization. |
InitializationN, K, , , , , , , for . SEE initial value , tolerance , iteration index , the maximum iteration number . repeat Set Solve (28) for given and obtain the and using SCA method. ifthen else if then else end end until
|
4. Simulation Results
In this part, simulation results are presented to show the effectiveness of the proposed algorithm. The simulation parameters are given as follows. The number of users is
. The coordinates of BS are (40,0)m; the users are randomly distributed in the rectangular area
m. The path loss model is adopted with path loss exponent
. The background noise is
dBm [
14], and the user fixed circuit power loss is
dBm.
Figure 2 compares the minimum SEE of each algorithm for different
. When the transmit power
of the BS increases, the minimum SEE obtained by the min user’ SEE maximization and users’ system SEE maximization gradually increases to remain unchanged; this is because the increase of the BS transmit power resistant against eavesdroppers achieves a balance in the information rates leaked into the eavesdropper. Moreover, as can be seen from the secure rate maximization algorithm, with the increase of power, the ultimate SEE decreases. Therefore, it shows the stability of the SERA algorithm.
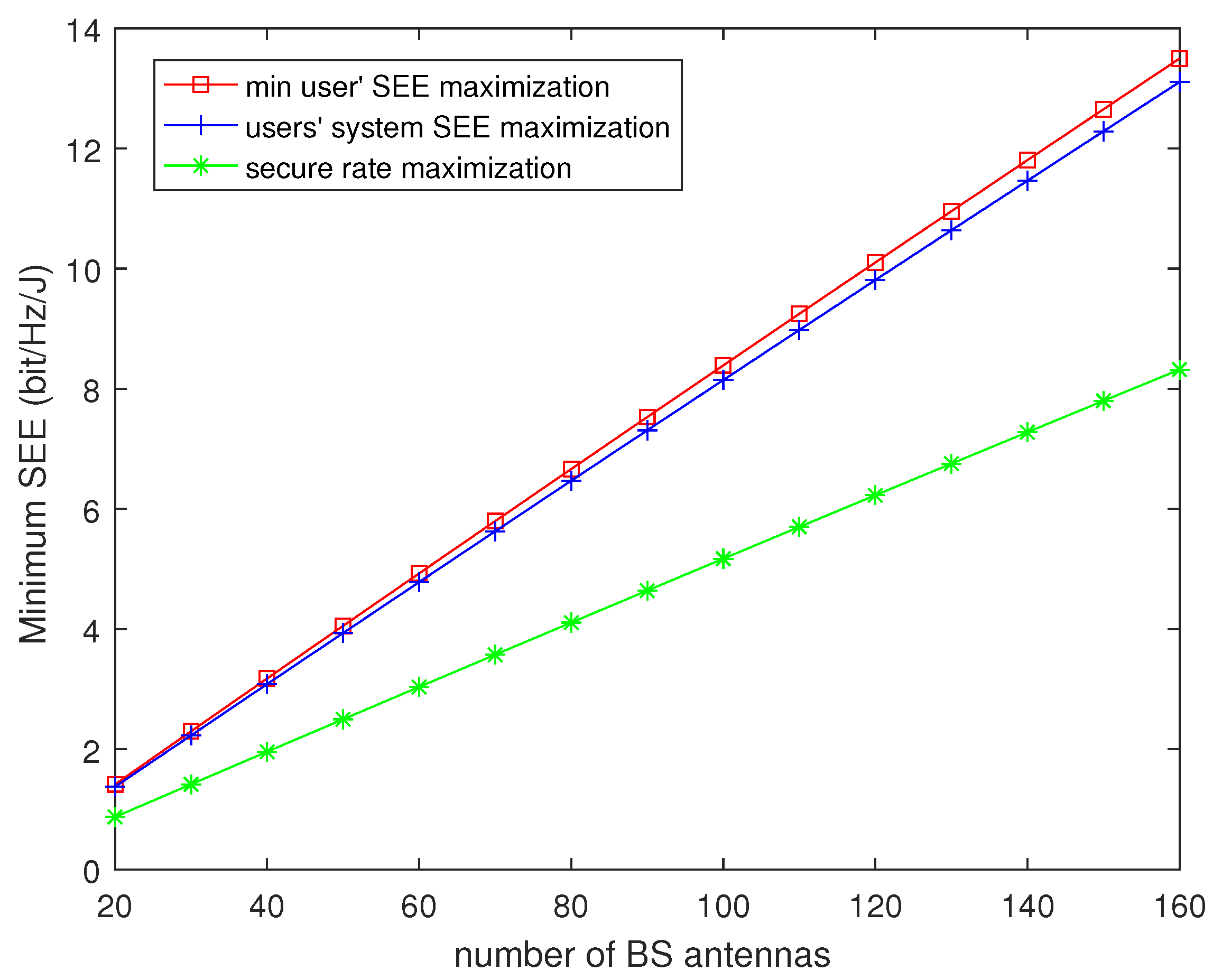
Figure 3 shows the minimum SEE of the three algorithms for the different number of BS antennas. The minimum SEE is monotone increasing with the antenna number of BS for three algorithms. This is because of the array gain due to the multi-antenna diversity. As the number of BS antennas increases, the secure rate of three algorithms increases faster than the power consumption. In addition, it can be observed that the minimum SEE performance of the SERA algorithm is better than the other two algorithms.
In
Figure 4, we show the convergence performance of the different
. It can be seen that the SERA algorithm can quickly converge. In the three cases under consideration, the number of iterations that the algorithm converges to the optimal value is within four times. When the number of BS antennas is
, the numerical results reveal that the performance of the
dBm has increased about 20.1% and 41.5% more than
dBm and
dBm.
In
Figure 5, we show the minimum SEE versus the eavesdropper transmit power under different algorithms. When the number of BS antennas is
and BS transmit power
dBm, as the eavesdropper transmit power increases, the minimum SEE gradually decreases. From Equation (4), increasing the eavesdropper transmit power impacts the channel estimation. This leads to a decrease in the SEE and an increase in the information rates leaked into the eavesdropper.
Figure 6 shows the minimum SEE of the three algorithms for a different number of users. The minimum SEE is monotone decreasing with the number of users. The minimum SEE obtained by SERA algorithms is about 3% and 62.2% compared with the users’ system SEE maximization and secure rate maximization algorithm when the number of users
K is 4 and BS maximum transmit power is
dBm. In addition, it can be observed that the minimum SEE performance of the SERA algorithm is better than the other two algorithms.