Two-Source Asymmetric Turbo-Coded Cooperative Spatial Modulation Scheme with Code Matched Interleaver
Abstract
1. Introduction
- An asymmetric turbo-coded SM (ATC-SM) technique is proposed. The proposed scheme adopts a higher order modulation such as 16QAM, 32QAM and 64QAM.
- The proposed scheme is further extended to coded-cooperative scenarios with two sources, such as the asymmetric turbo-coded cooperative SM (ATCC-SM) technique.
- The asymmetric turbo-coded vertical bell labs layered space-time (ATC-VBLAST) is also devised as an appropriate benchmark for the proposed ATC-SM scheme. Similarly, the asymmetric turbo-coded cooperative vertical bell labs layered space-time (ATCC-VBLAST) scheme is utilized as a suitable benchmark for ATCC-SM under identical conditions.
- A joint iterative ATC decoder for two sources is also implemented at the destination node.
2. Asymmetric Turbo Code (ATC)
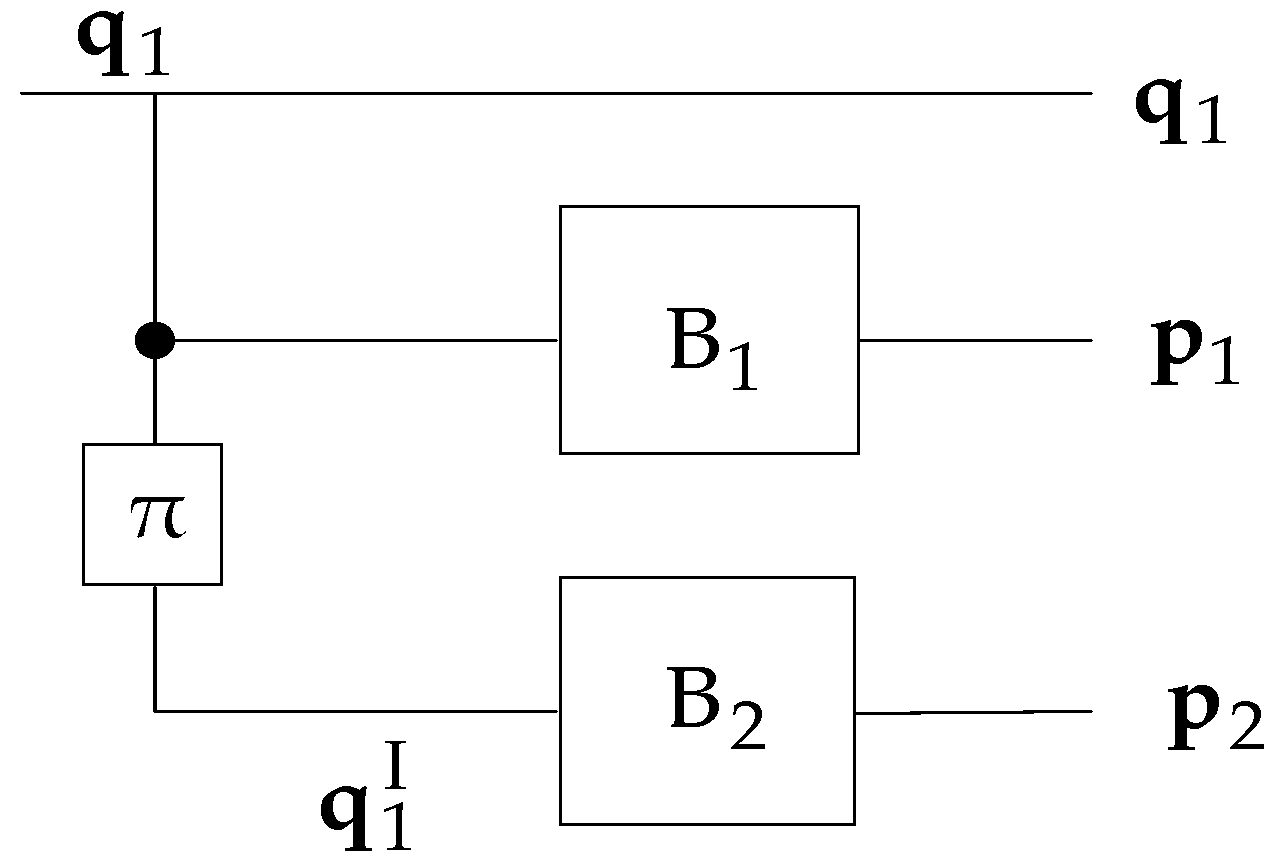
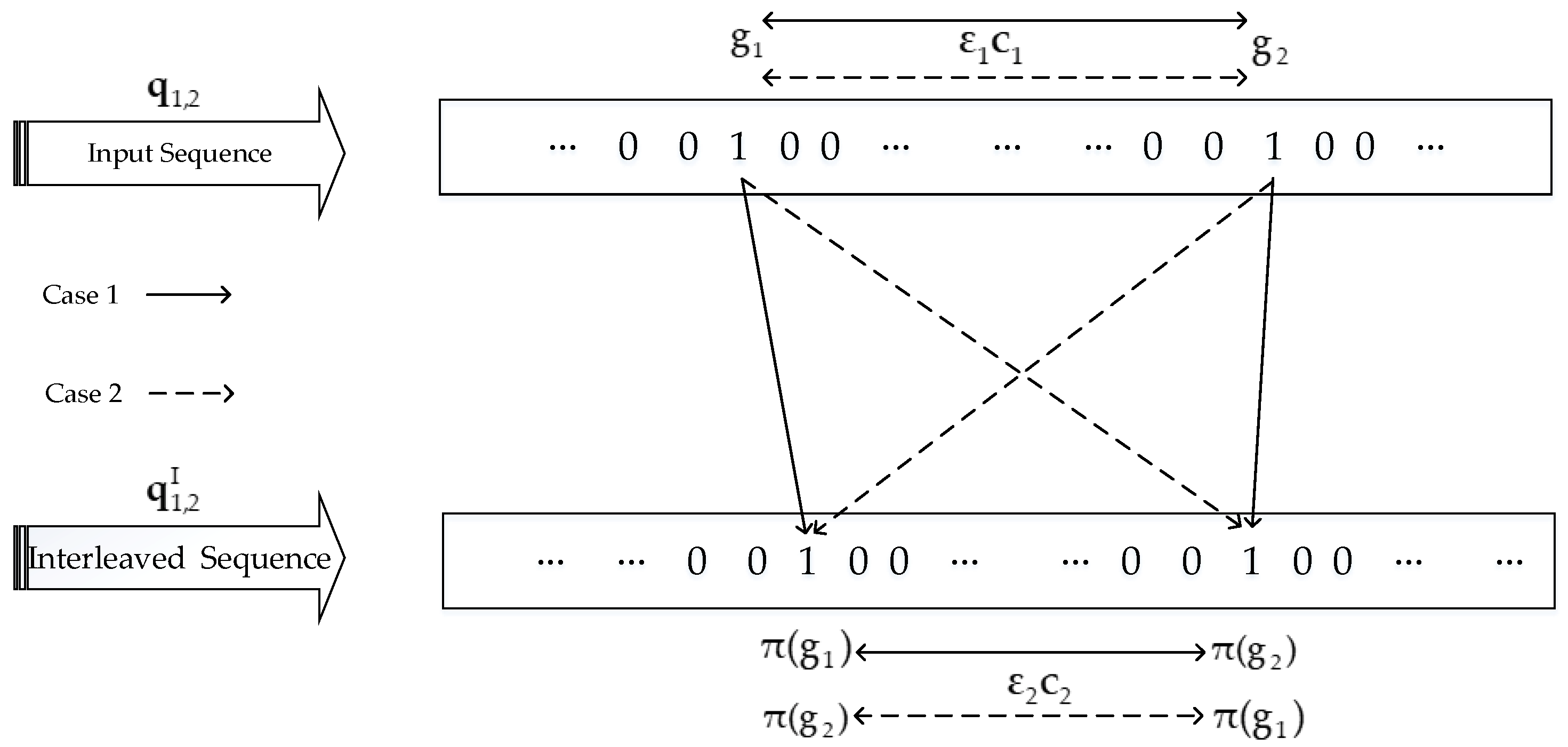
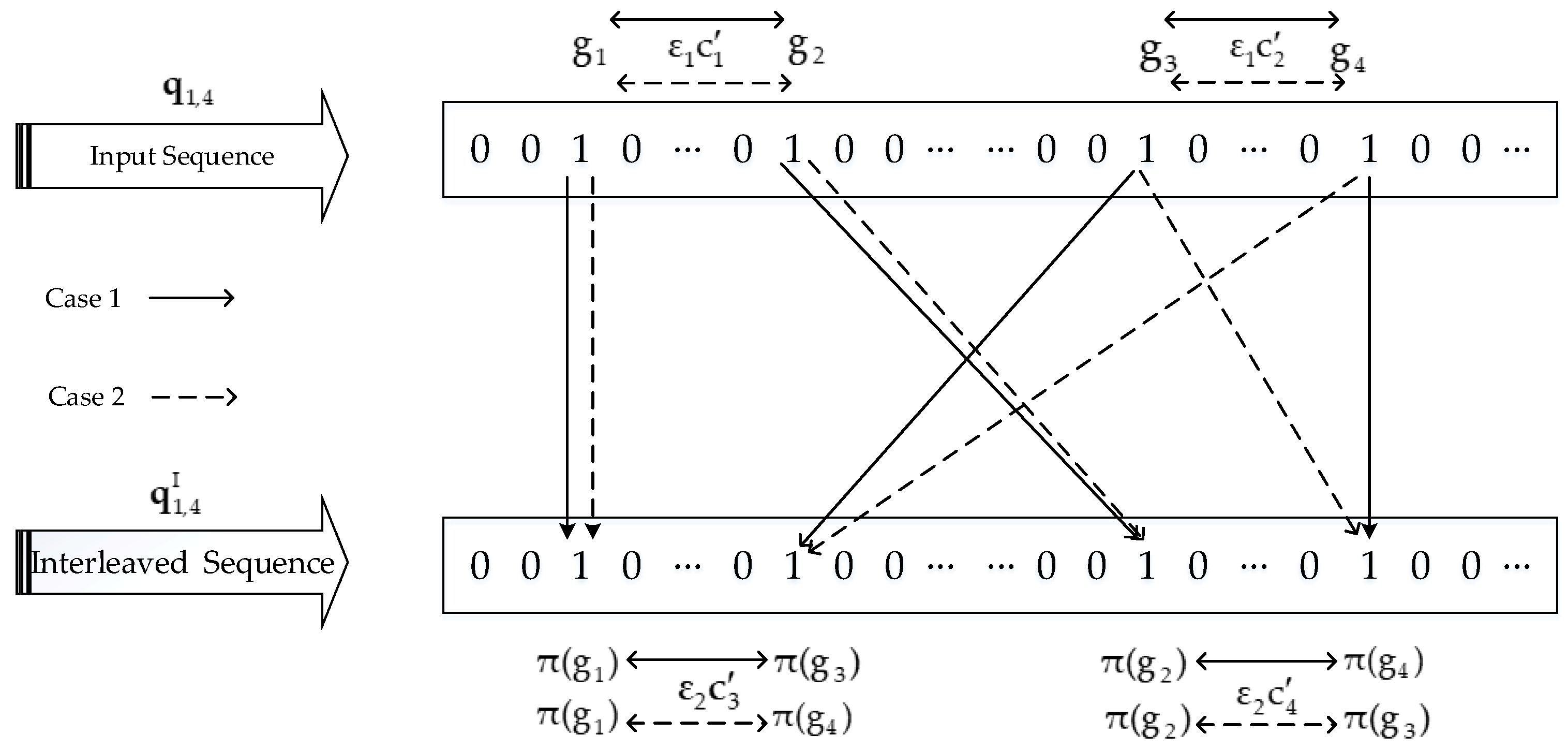
2.1. Code Matched Interleaver
- Let us randomly choose an integer from the finite set , where N denotes the size of the interleaver.
- Compare the selected integer with S previous selected integers, where . If the absolute value of the difference between the current selected integer and any of the S previous selected integers is smaller than S [31], then go back to the first step and search for a proper integer.
- Check whether the weight-2 and 4 mapping conditions are simultaneously satisfied by the current interleaver output. If they are not satisfied, then go back to the first step.
- When a specified number of iterations is reached, if we do not find an integer from the set to make it satisfy both the second and third steps simultaneously, then the value S is reduced by 1 and the process is restarted from the first step.
- The selected integer is saved as the current interleaver output. Repeat the process until we obtain all N interleaver outputs.
2.2. Asymmetric Turbo-Coded Spatial Modulation (ATC-SM) Scheme with CMI
2.3. Asymmetric Turbo-Coded VBLAST (ATC-VBLAST) Scheme Based on CMI
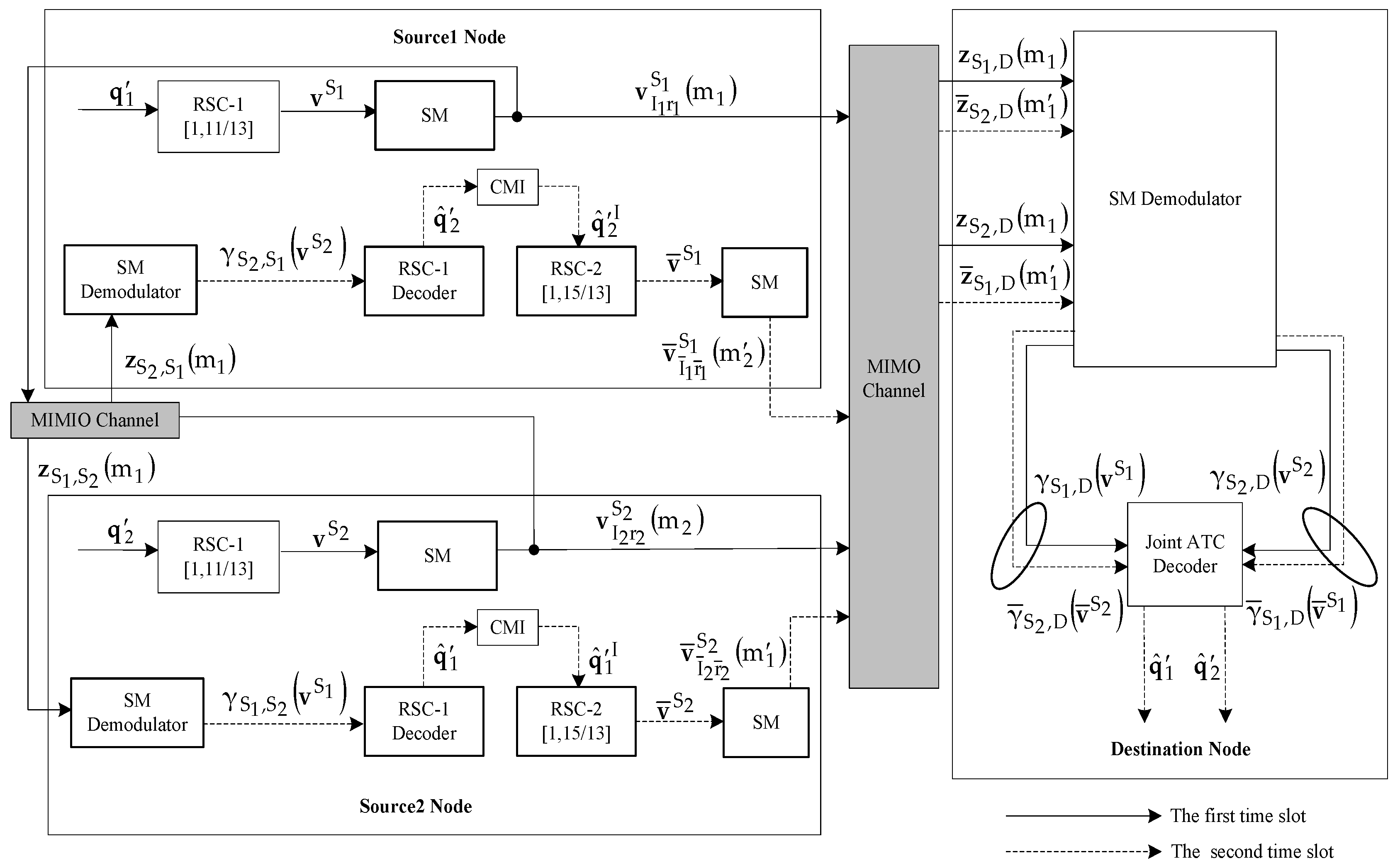
3. Two-Source Asymmetric Turbo-Coded Cooperative (ATCC) Scheme Based on CMI
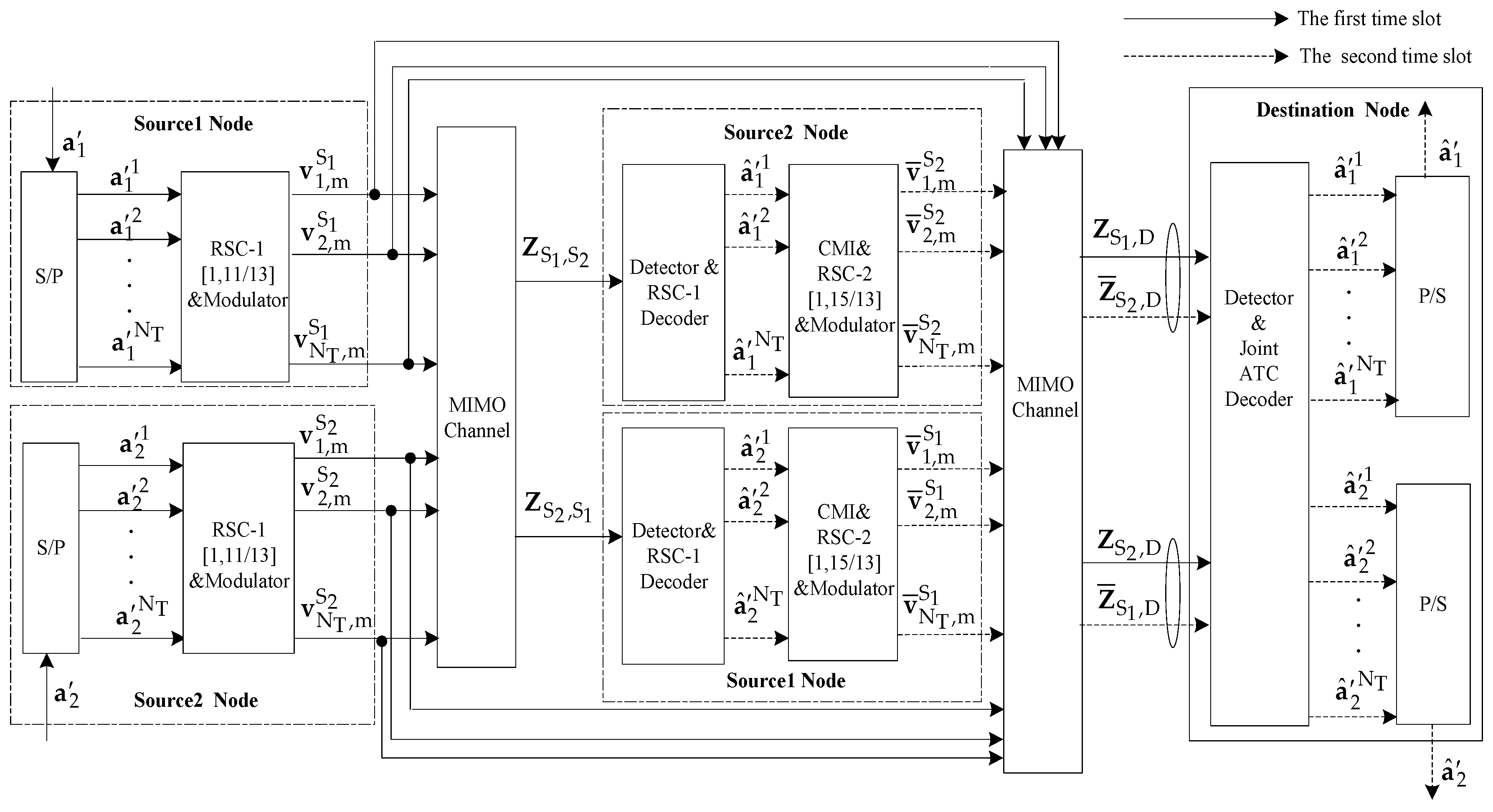
3.1. Two-Source Asymmetric Turbo-Coded Cooperative Spatial Modulation (ATCC-SM) Scheme Based on CMI
3.2. Two-Source Asymmetric Turbo-Coded Cooperative VBLAST (ATCC-VBLAST) Scheme Based on CMI
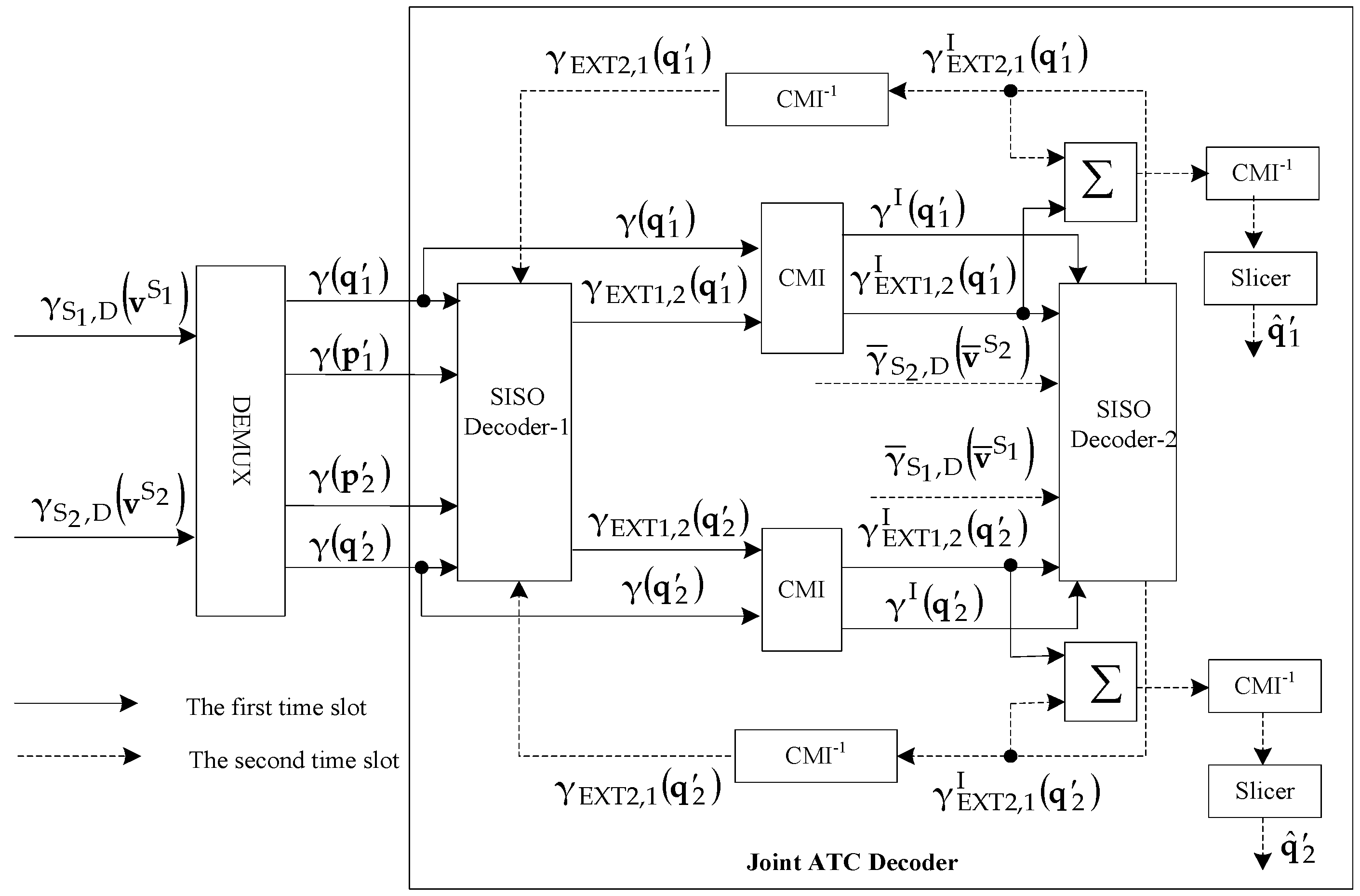
4. Joint Iterative ATC Decoder
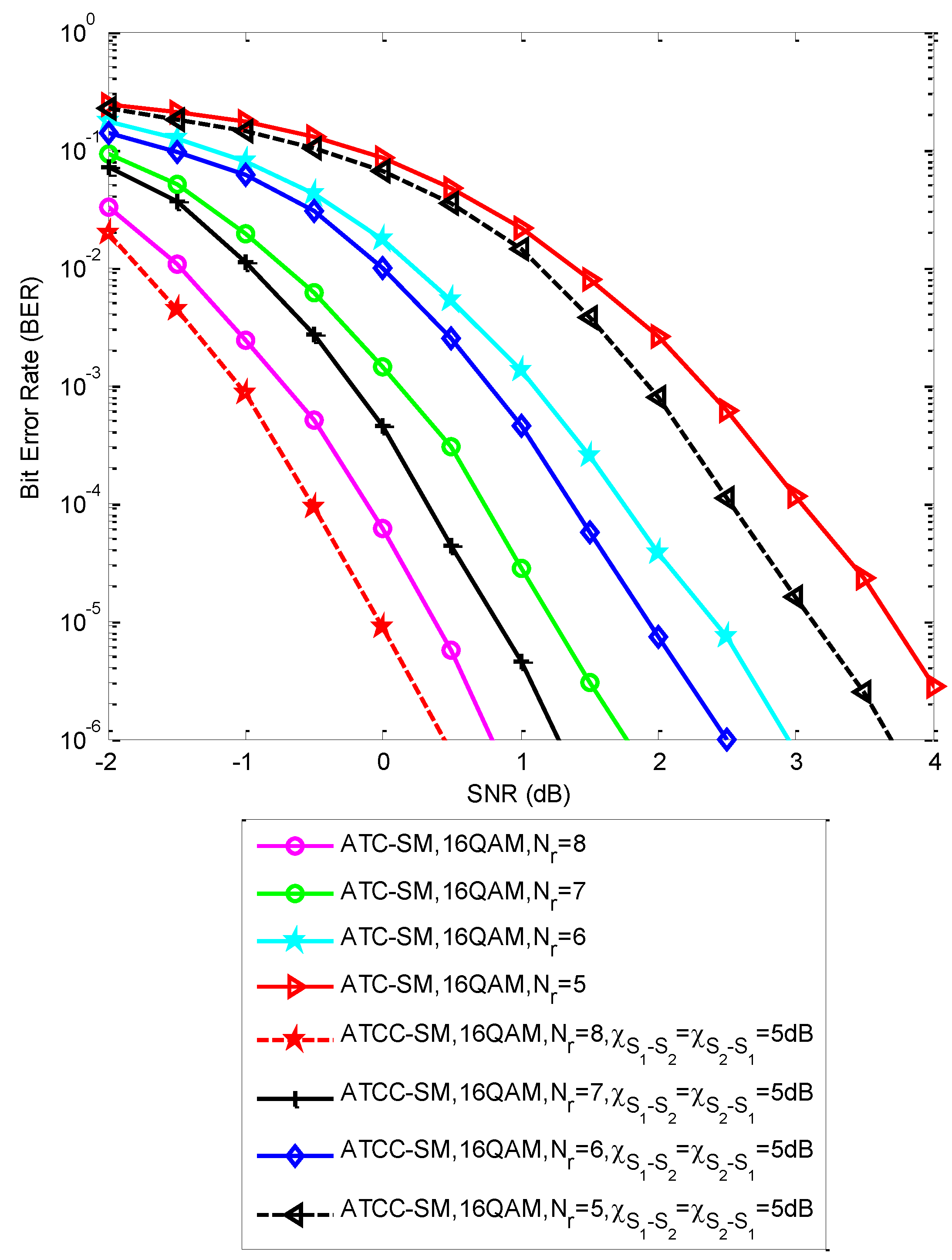
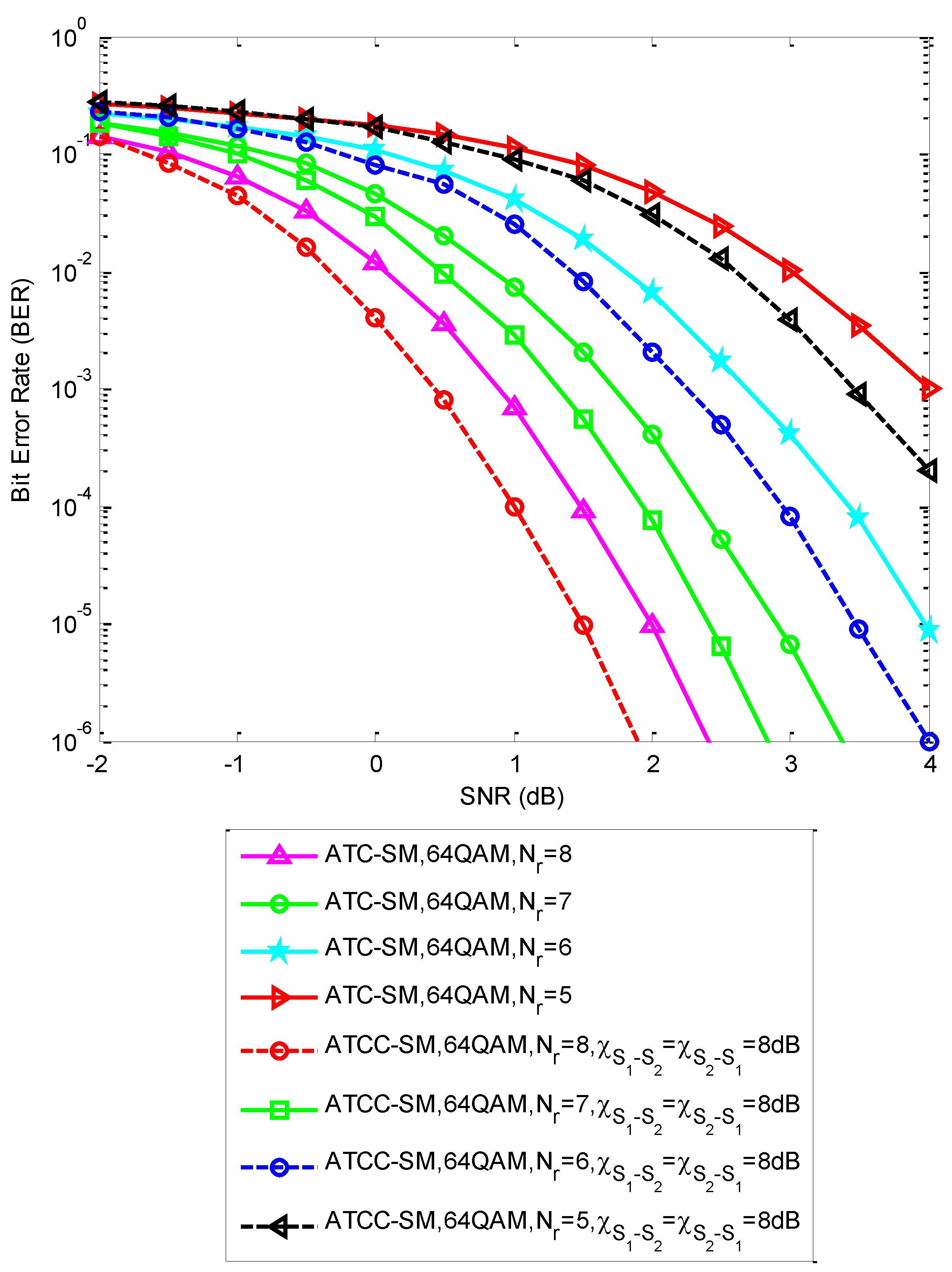
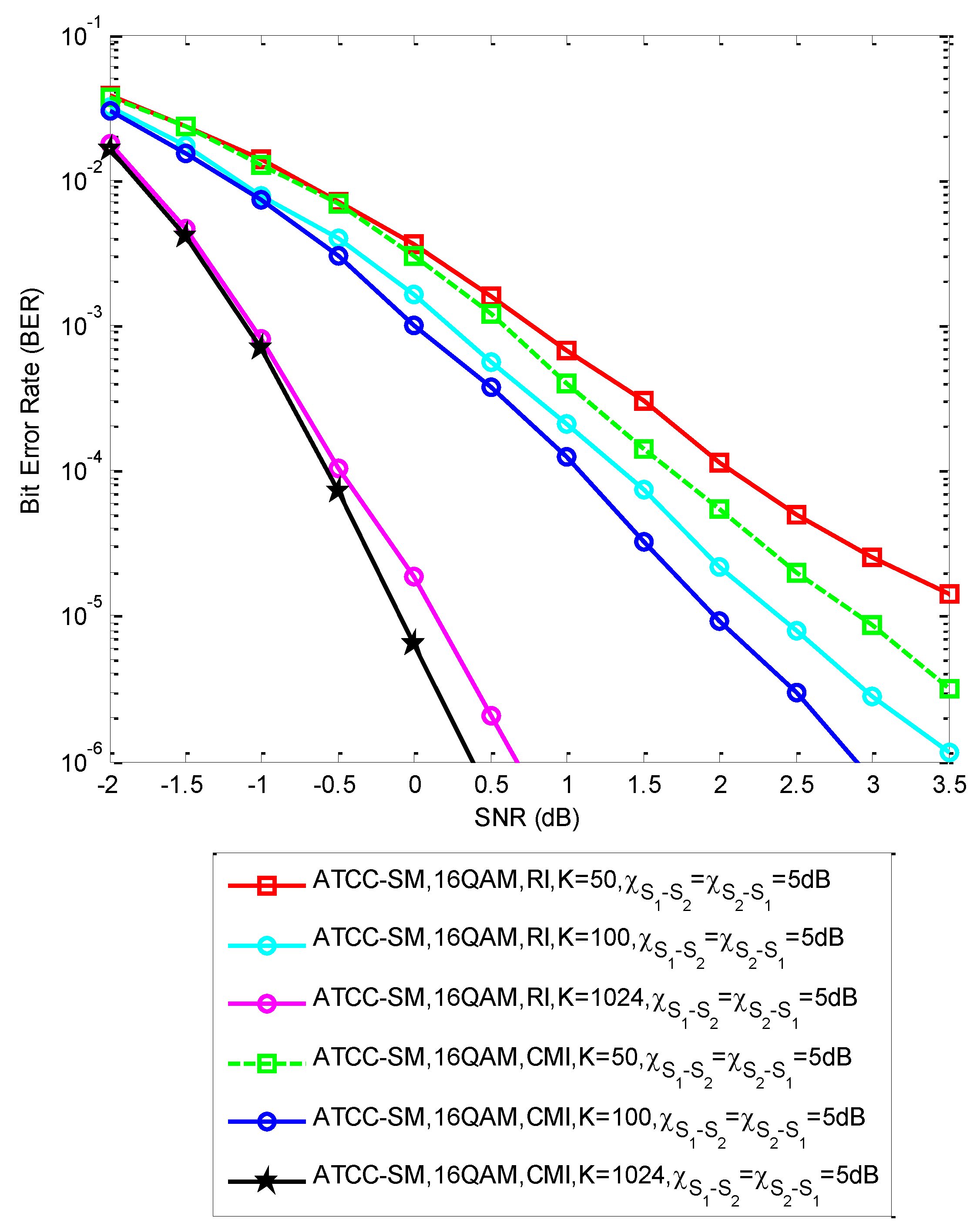
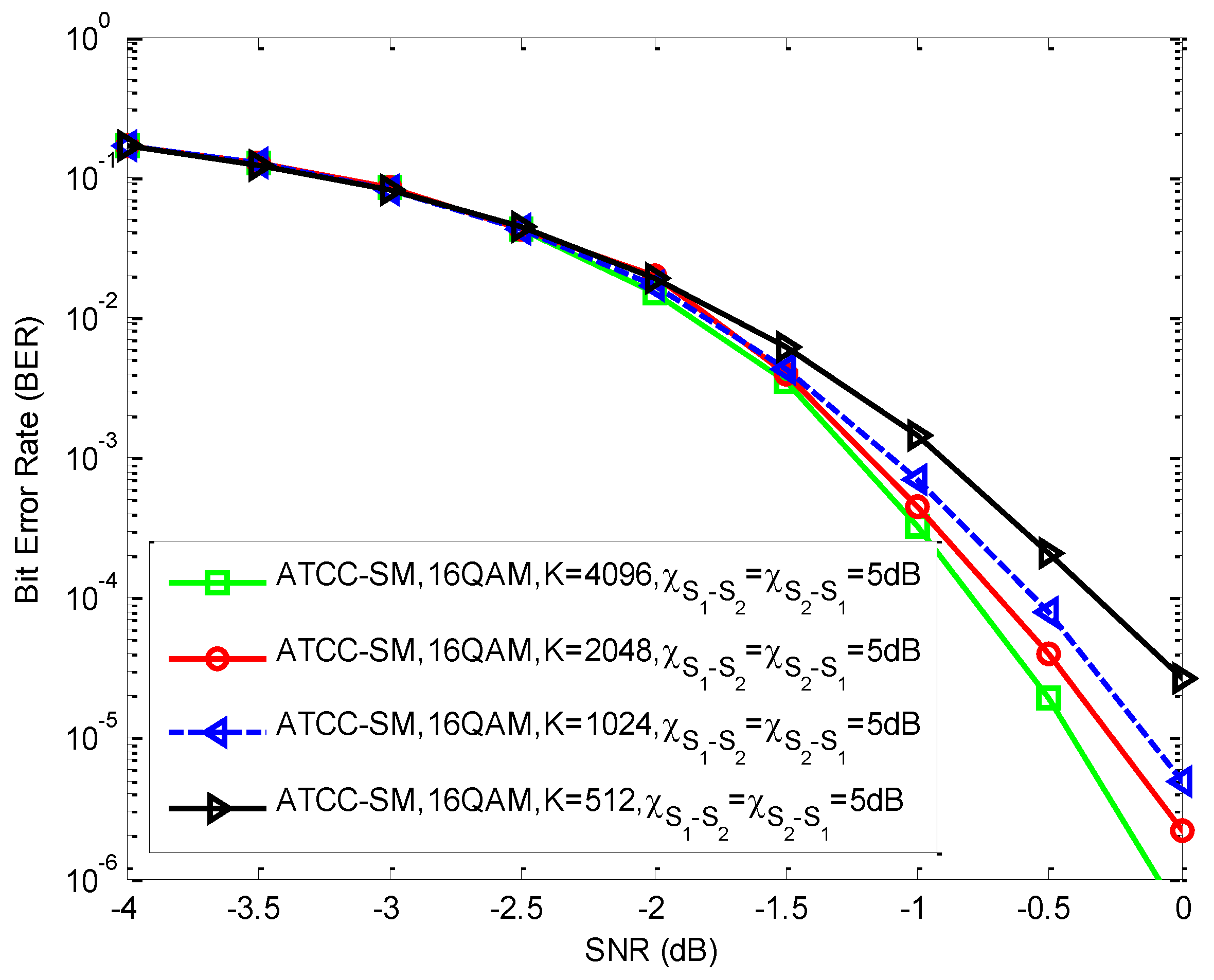
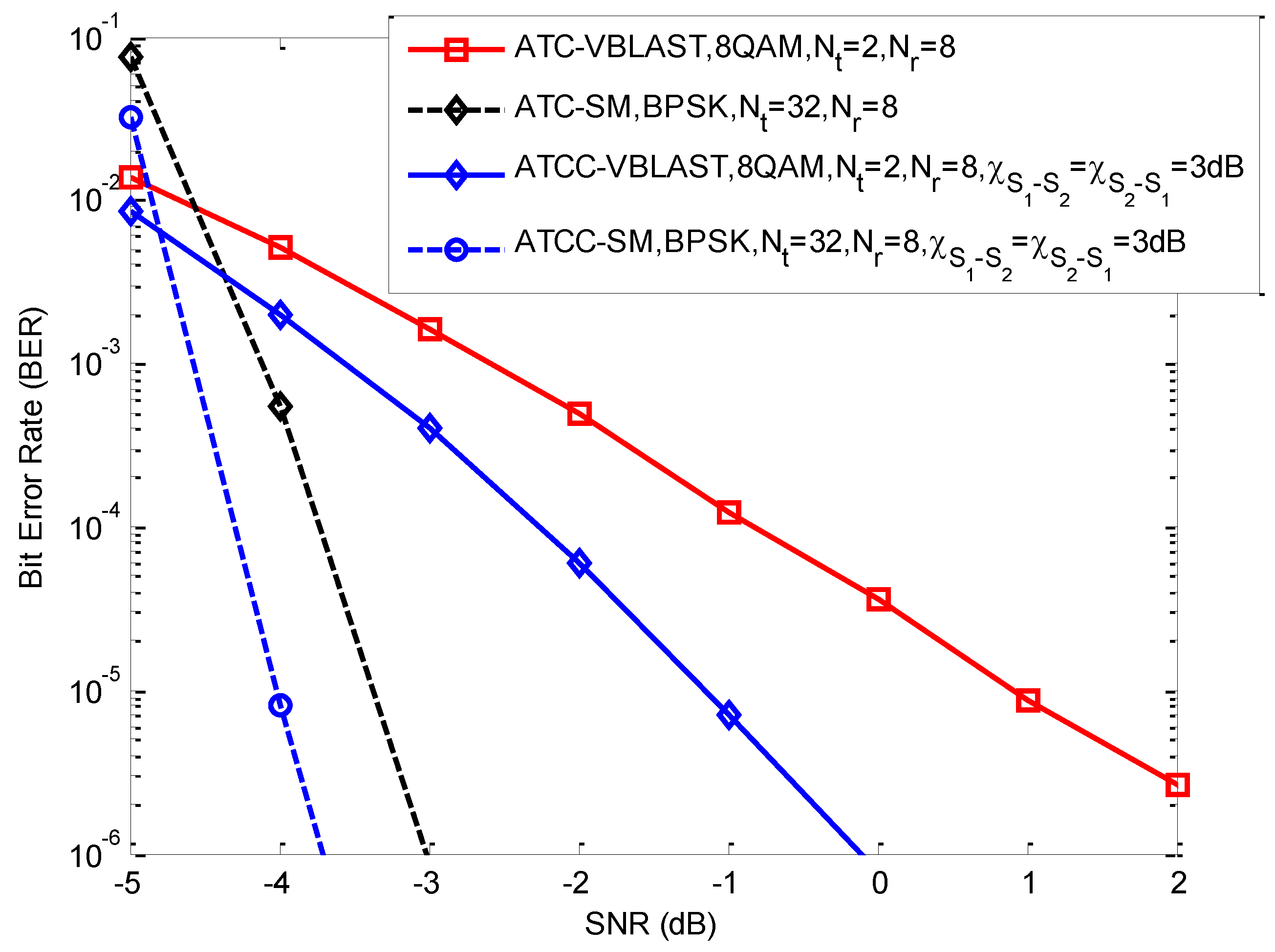
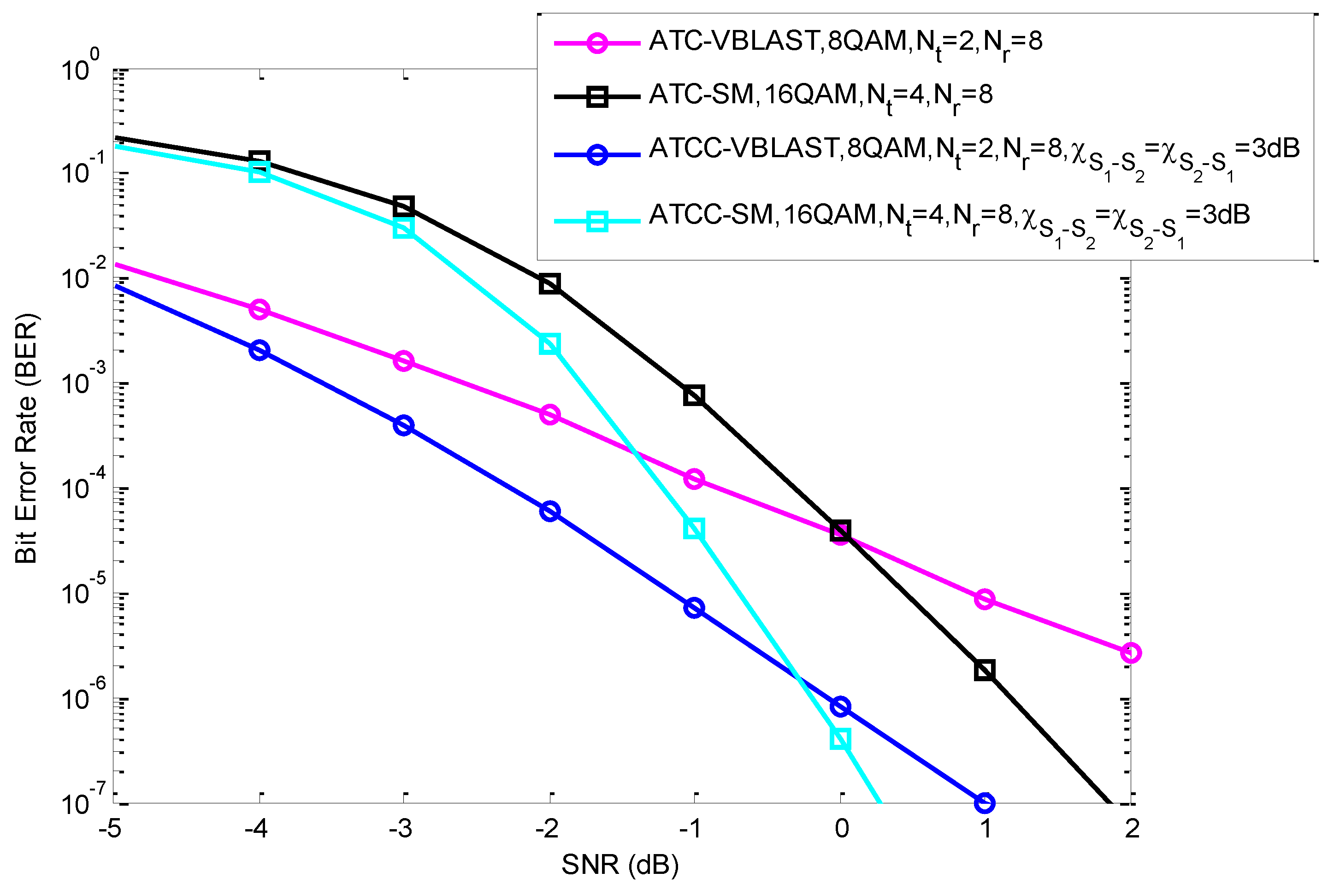
5. Results and Discussion
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Barry, J.R.; Lee, E.A.; Messerschmitt, D.G. Digital Communication, 3rd ed.; Springer: New York, NY, USA, 2004; ISBN 978-1-4615-0227-2. [Google Scholar]
- Mughal, S.; Yang, F.-F.; Xu, H. Polar Coded Space-time Block Coded Spatial Modulation Based on Plotkin’s Construction for Coded Cooperative Networks. IET Commun. 2018, 12, 237–245. [Google Scholar] [CrossRef]
- Umar, R.; Yang, F.-F.; Xu, H. Multi-level construction of polar coded single carrier-FDMA based on MIMO antennas for coded cooperative wireless communications. IET Commun. 2018, 12, 1253–1262. [Google Scholar] [CrossRef]
- Garg, J.; Mehta, R.; Gupta, K. A Review on cooperative communication protocols in wireless world. Int. J. Wirel. Mob. Netw. 2013, 5, 107–126. [Google Scholar] [CrossRef]
- Sendonaris, A.; Erkip, E.; Aazhang, B. User cooperation diversity. Part I. System description. IEEE Trans. Commun. 2003, 51, 1927–1938. [Google Scholar] [CrossRef]
- Sendonaris, A.; Erkip, E.; Aazhang, B. User cooperation diversity. Part II. System description. IEEE Trans. Commun. 2003, 51, 1939–1948. [Google Scholar] [CrossRef]
- Hunter, T.E.; Nosratinia, A. Diversity through coded cooperation. IEEE Trans. Wirel. Commun. 2006, 5, 283–289. [Google Scholar] [CrossRef]
- Martinez, J.E.; Crespo, P.M. Depolarizing Channel Mismatch and Estimation Protocols for Quantum Turbo codes. Entropy 2019, 21, 1133. [Google Scholar] [CrossRef]
- Nguyen, T.T.B.; Tan, T.N.; Lee, H. Efficient QC-LDPC Encoder for 5G New Radio. Electronics 2019, 8, 668. [Google Scholar] [CrossRef]
- Goela, N.; Abbe, E.; Gastpar, M. Polar codes for broadcast channels. IEEE Trans. Inf. Theory 2015, 61, 758–782. [Google Scholar] [CrossRef]
- Wu, X.P.; Haas, H.; Grant, P.M. Cooperative spatial modulation for cellular networks. IEEE Trans. Commun. 2018, 66, 3683–3693. [Google Scholar] [CrossRef]
- He, C.; Gitlin, R.D. System performance of cooperative massive MIMO downlink 5G cellular systems. In Proceedings of the IEEE 17th Annual Wireless and Microwave Technology Conference, Clearwater, FL, USA, 11–13 April 2016. [Google Scholar] [CrossRef]
- Shamganth, K.; Sibley, M.J.N. A survey on relay selection in cooperative device-to-device (D2D) communication for 5G cellular networks. In Proceedings of the IEEE International Conference on Energy, Communications, Data Analytics and Soft Computing, Chennai, India, 1–2 August 2017. [Google Scholar] [CrossRef]
- Mesleh, R.Y.; Haas, H. Spatial modulation. IEEE Trans. Veh. Technol. 2008, 57, 2228–2241. [Google Scholar] [CrossRef]
- Basar, E.; Aygolu, U. New trellis code design for spatial modulation. IEEE Trans. Wirel. Commun. 2011, 10, 2670–2680. [Google Scholar] [CrossRef]
- Kamruzzaman, M.M. Relay Assisted Multiple Input Multiple Output Wireless Communication System for Multiple Access Channel Coding Using Hybrid-STBC-VBLAST. In Proceedings of the 26th Wireless and Optical Communication Conference, Newark, NJ, USA, 7–8 April 2017. [Google Scholar] [CrossRef]
- Robles, J.; Cortez, J. Fast Scalable Fixed-Point Architecture Proposal of A QR Decomposition for STBC-VBLAST Receiver. In Proceedings of the Wireless Telecommunications Symposium, Chicago, IL, USA, 26–28 April 2017. [Google Scholar] [CrossRef]
- Jeganathan, J.; Ghrayeb, A.; Szczecinski, L. Spatial modulation: Optimal detection and performance analysis. IEEE Commun. Lett. 2008, 12, 545–547. [Google Scholar] [CrossRef]
- Govender, R.; Pillay, N.; Xu, H. Soft-output space-time block coded spatial modulation. IET Commun. 2014, 8, 2786–2796. [Google Scholar] [CrossRef]
- Feng, D.; Xu, H.; Zheng, J. Nonbinary LDPC-coded spatial modulation. IEEE Trans. Wirel. Commun. 2018, 17, 2786–2799. [Google Scholar] [CrossRef]
- Akuon, P.; Xu, H. Polar coded spatial modulation. IET Commun. 2014, 8, 1459–1466. [Google Scholar] [CrossRef]
- Mughal, S.; Yang, F.-F. Coded cooperative spatial modulation based on multi-level construction of polar code. Telecommun. Syst. 2019, 70, 435–446. [Google Scholar] [CrossRef]
- Berrou, C.; Glavieux, A. Near optimum limit error correcting coding and decoding: Turbo codes. IEEE Trans. Commun. 1996, 44, 1261–1271. [Google Scholar] [CrossRef]
- Umar, R.; Yang, F. Turbo Coded OFDM Combined with MIMO Antennas Based on Matched Interleaver for Coded-Cooperative Wireless Communication. Information 2017, 8, 63. [Google Scholar] [CrossRef]
- Bohorquez, R.G.; Nour, C.A. On the Equivalence of Interleavers for Turbo Codes. IEEE Wirel. Commun. Lett. 2015, 4, 58–61. [Google Scholar] [CrossRef][Green Version]
- Kraidy, G.M. On Progressive Edge-Growth Interleavers for Turbo Codes. IEEE Commun. Lett. 2016, 20, 200–203. [Google Scholar] [CrossRef]
- Ejaz, S.; Yang, F.-F. Turbo codes with modified code matched interleaver for coded-cooperation in half-duplex wireless relay networks. Frequenz 2015, 69, 171–184. [Google Scholar] [CrossRef]
- Feng, W.; Yuan, J. A code-matched interleaver design for turbo codes. IEEE Trans. Commun. 2002, 50, 926–937. [Google Scholar] [CrossRef]
- Omeira, M.S.; Hamad, G.M. A Code-matched Collision-free S-random Interleaver for Turbo Codes. In Proceedings of the IEEE Seventh International Conference on Intelligent Computing and Information Systems, Cairo, Egypt, 12–14 December 2015. [Google Scholar] [CrossRef]
- Mughal, S.; Yang, F.-F.; Ejaz, S. Asymmetric turbo code for coded cooperative wireless communication based on matched interleaver with channel estimation and multi-receive antennas at the destination. Radioengineering 2017, 26, 878–889. [Google Scholar] [CrossRef]
- Ramasamy, K.; Siddiqi, M.U. A new class of asymmetric turbo code for 3g systems. AEU Int. J. Electron. Commun. 2006, 60, 447–458. [Google Scholar] [CrossRef]
- Choi, S.J.; Shim, S.J.; You, Y.H. Novel MIMO Detection with Improved Complexity for Near-ML Detection in MIMO-OFDM Systems. IEEE Access 2019, 7, 60389–60398. [Google Scholar] [CrossRef]
- Vaz, A.C.; Nayak, C.G.; Nayak, D. Performance Comparison between Turbo and Polar codes. In Proceedings of the 3rd International Conference on Electronics, Communication and Aerospace Technology, Coimbatore, India, 12–14 June 2019. [Google Scholar] [CrossRef]
- Vucetic, B.; Yuan, J. Turbo Codes: Principles and Applications; Springer: New York, NY, USA, 2012; ISBN 978-1-4615-4469-2. [Google Scholar]
- Liu, Z.; Wu, B.; Ye, T.C. Improved Turbo Decoding with Multivariable Taylor Series Expansion. IEEE Commun. Lett. 2018, 22, 37–40. [Google Scholar] [CrossRef]




© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, C.; Yang, F.; Umar, R.; Mughal, S. Two-Source Asymmetric Turbo-Coded Cooperative Spatial Modulation Scheme with Code Matched Interleaver. Electronics 2020, 9, 169. https://doi.org/10.3390/electronics9010169
Zhao C, Yang F, Umar R, Mughal S. Two-Source Asymmetric Turbo-Coded Cooperative Spatial Modulation Scheme with Code Matched Interleaver. Electronics. 2020; 9(1):169. https://doi.org/10.3390/electronics9010169
Chicago/Turabian StyleZhao, Chunli, Fengfan Yang, Rahim Umar, and Shoaib Mughal. 2020. "Two-Source Asymmetric Turbo-Coded Cooperative Spatial Modulation Scheme with Code Matched Interleaver" Electronics 9, no. 1: 169. https://doi.org/10.3390/electronics9010169
APA StyleZhao, C., Yang, F., Umar, R., & Mughal, S. (2020). Two-Source Asymmetric Turbo-Coded Cooperative Spatial Modulation Scheme with Code Matched Interleaver. Electronics, 9(1), 169. https://doi.org/10.3390/electronics9010169




