A Novel Authentication Protocol with Strong Security for Roaming Service in Global Mobile Networks
Abstract
:1. Introduction
2. Review and Cryptanalysis of Madhusudhan and Shashidhara’s Protocol
2.1. Review of Madhusudhan and Shashidhara’s Scheme
2.1.1. Initialization Phase
2.1.2. Registration Phase
- Step 1.
- chooses identity , password , and produces a nonce N. Next, calculates and submits it to securely.
- Step 2.
- Upon obtaining the registration request, calculates , , mod . Then, initializes the value of the counter K to zero and saves in the database. Finally, submits to via a secret manner.
- Step 3.
- After getting the reply message from , computes and stores in the mobile device.
2.1.3. Authentication Phase
- Step 1.
- types in and . The mobile device computes and checks . The request is rejected if they are not equal. Otherwise, produces a nonce and computes , and . Finally, submits the login request to .
- Step 2.
- Upon receiving , produces a nonce , and encrypts with using . Then, submits to .
- Step 3.
- After obtaining , checks and finds the secret key . Next, retrieves by calculating and calculates , mod , . Then, checks if is preserved in the database. If so, calculates mod and checks . Non-equality results in the termination of the session, or else calculates mod and submits to .
- Step 4.
- When getting , retrieves by calculating and computes . Then, forwards the message to .
- Step 5.
- Upon obtaining , calculates (In Madhusudhan and Shashidhara’s scheme [32], . However, combined with the context, the formula should be , and we correct it here.) and . Then, checks . The equality means is authenticated by .
2.2. Cryptanalysis of Madhusudhan and Shashidhara’s Scheme
2.2.1. Transmitting Messages in Plaintext
2.2.2. User Impersonation Attack
2.2.3. Session Key Compromise Attack
2.2.4. Mobile Device Breach Attack
- Step 1.
- chooses a pair from the identity dictionary and password dictionary.
- Step 2.
- calculates .
- Step 3.
- tests the correctness of by checking .
- Step 4.
- repeats the above steps until the right pair is found.
2.2.5. Lack of Bidirectional Authentication
2.2.6. Stolen Verifier Attack
2.2.7. Other Weaknesses
3. Our Proposed Scheme
3.1. Initialization Phase
3.2. Registration Phase
- Step R1.
- :first chooses , , and a nonce b. Then, calculates and transmits the registration request to with a secure method.
- Step R2.
- A Smart Card :checks if exists in the system. If so, is asked to send a new one. Otherwise, computes mod , , and . Then, stores the parameters in a smart card () and forwards it to over a secure manner.
- Step R3.
- When obtaining the , activates it and stores b into it.
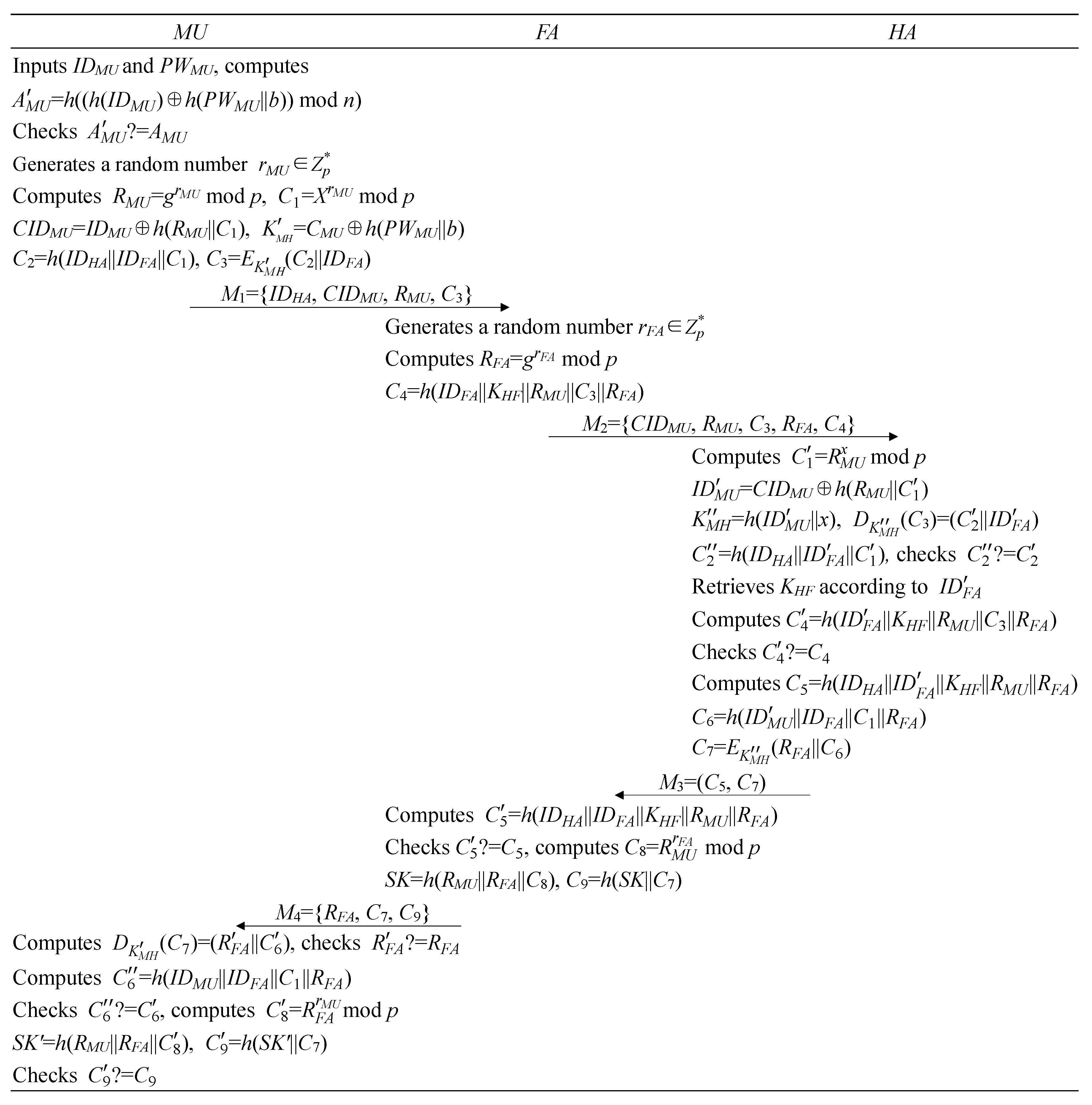
3.3. Login and Authentication Phase
- Step V1.
- : .inserts the into the mobile terminal and types in and . computes mod and verifies . Unequal means that entered incorrect or , and the session is terminated by . The card will be locked if there are three consecutive failures on the password. Otherwise, produces a nonce and calculates mod p, mod p, , , , and . Then, submits the login request to .
- Step V2.
- : .When receiving from a roaming user, produces a nonce and computes mod p and . Then, forwards the message to .
- Step V3.
- : .Upon obtaining the message from , calculates mod p, , , and . Then, calculates and checks . Unequal will lead to the rejection of the session. Otherwise, is authenticated by . Next, retrieves the according to . Then, calculates and authenticates by checking . If the verification passes, calculates , , , and forwards to .
- Step V4.
- : .When receiving the message from , calculates , and the validity of is verified if . Then, calculates mod p, the session key , and . Then, submits the message to .
- Step V5.
- When receiving from , calculates and checks if is equal to the received . Then, calculates , and the validity of is verified if . Next, calculates mod p, , , and the validity of is verified if . Finally, as a shared session key between and , is used by them for further security communication.
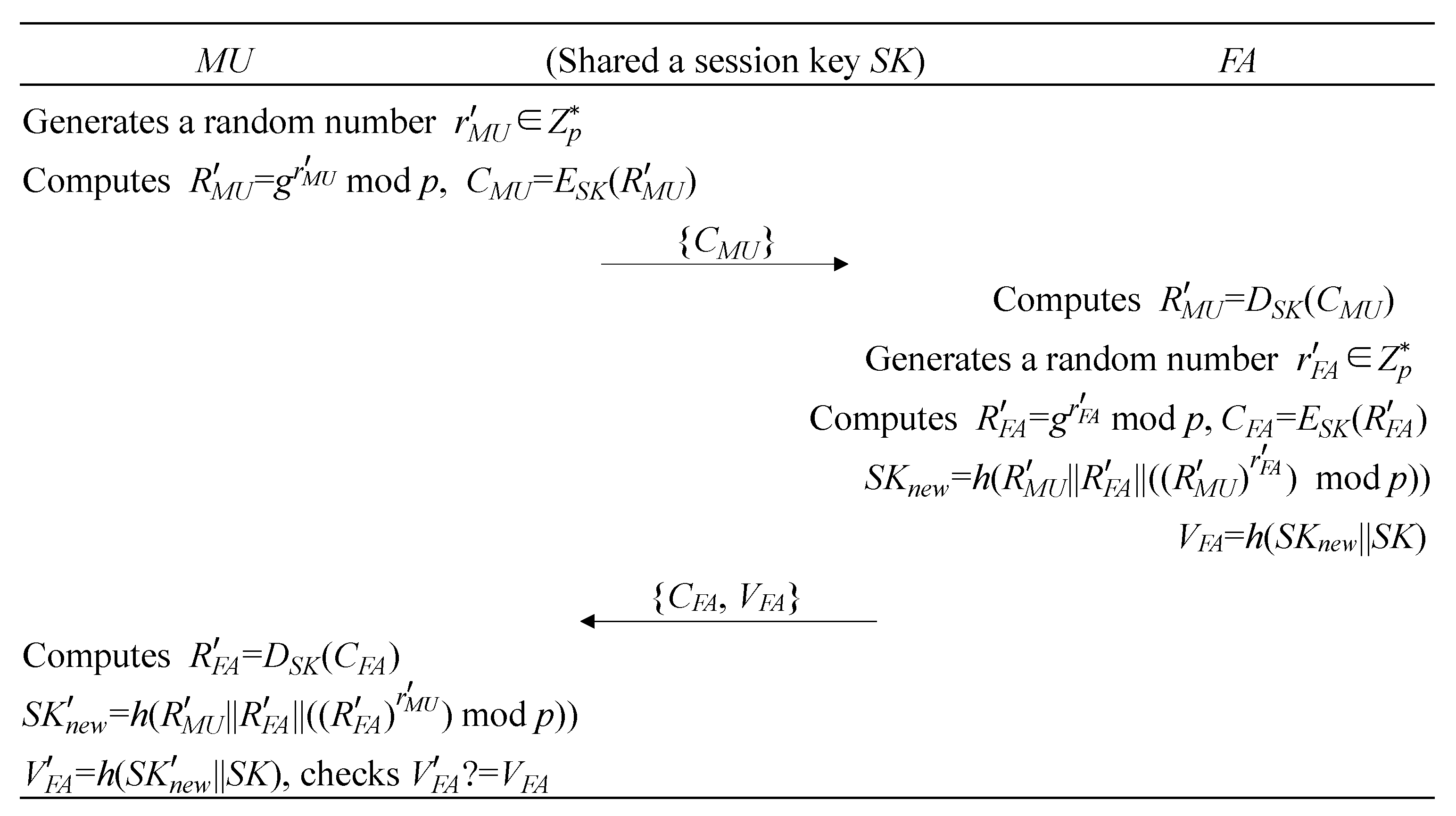
3.4. Session Key Update Phase
- Step S1.
- produces a new nonce and calculates mod p, . Then, submits to for session key update.
- Step S2.
- retrieves by decrypting using . Next, produces a new nonce and calculates mod p, , mod , and . Then, sends the message to .
- Step S3.
- When receiving the message, first retrieves by decrypting using . Then, calculates mod , and checks . Unequal means and fail to agree on a new session key. Otherwise, they share a new session key .
3.5. Password Change Phase
- Step P1.
- inserts the into the mobile terminal and types and .
- Step P2.
- computes mod and verifies . If they are not equal, which means that entered incorrect or , the request is rejected by . On the contrary, is asked to type a new password.
- Step P3.
- inputs a new password . calculates , mod , . Finally, replaces and with and , respectively.
4. Formal Proof
4.1. Basic Knowledge
- DLP (Discrete Logarithm Problem): Given and , it is hard to compute a.
- CDHP (Computation Diffie–Hellman Problem): If and are known, it is hard to compute , and denotes the probability for to break the CDHP.
4.2. Basic Knowledge for the Proof
- : sends message m to . If m is correct, the normal operations in will be done on ; or the query will be stopped.
- : All messages in the authentication phase will be eavesdropped by .
- : If or generates a session key, the key will be returned to .
- : can get all information stored in of .
- : gets all long-term secret data of , and this is for strong forward security [41].
- : is for or . Finally, has to choose a session to make a challenge. If does not reach or , which will be explained later, the result is ⊥. Else, a bit is chosen. If , the session key is returned. Otherwise, a random string is returned.
- : As shown in [41], it is Strong Forward Security-fresh for and . is if any of the following conditions do not appear:
- -
- or is asked.
- -
- or is queried before .
- : The advantage for breaking is the probability of correctly guessing generated in over , or , where is guessed by . If is the number of queries, is negligibly bigger than and is .
4.3. Process of the Proof
- Game : The random oracles are added in the real scheme. If more queries are used by or the game is finished, but without answer, a new bit is produced. We know that .
- Game : All queries in Section 4.2 are brought in. However, there are five queries: , , , , and . The operations for five queries correspond to the five steps in Section 3.3. Furthermore, three lists are required: is to store the results of hash queries from the simulator ; is to store the hash queries from ; is to store the transcripts of the sessions. When a string is asked for the hash result, the simulator returns the result r if the tuple can be found in the list. However, if there is no such result, the simulator picks up a random string as the result and stores the tuple in the corresponding list. cannot know the difference between and , and .
- Game : The collisions between different sessions are discussed in this game. There are two cases below:
- The probability for collision of random numbers and is at most .
- The probability for collision of hash results is .
Therefore, we know . - Game : We consider the case that can impersonate the entities via forging hash results without hash query.
- -
- : checks if , and , . However, cannot be checked. The probability is for this case.
- -
- : checks if , and , , . Furthermore, cannot be checked. The probability is for the first and second hash result and for the last.
- -
- : checks if , , and , . The probability for the first result is and for the second is .
- -
- : checks if , , , , and , . The probability for the first result is and for the second is .
Therefore, is the same as , and the probability . - Game : We inject the CDH problem in this game, with random oracles added again. Based on [41,42], must be asked first to crack the scheme. Two cases can be listed:
- With the most number of chance , can select one password from P to start a session. Such an active attack has the success probability .
- For passive attacks, two subcases are demonstrated below:
- (a)
- queries are used. Finally, should be found in , and the probability is . Therefore, the probability for this subcase is .
- (b)
- can be replaced with the combination of all queries. Similar to the last subcase, the probability is .
We make and get . - Game : This game is for strong forward security. With the concept of , should be asked after , so we can only consider old messages here. Like , the probability for and occurring in the same session is , and . Till now, , and there is no advantage for .
5. Formal Verification by ProVerif
- : .
- : .
- : .
- : .
6. Security Analysis and Comparisons
6.1. Resist Smart Card Loss (Off-Line Password Guessing) Attack
6.2. User Anonymity
6.3. Proper Bidirectional Authentication
6.4. Resist Impersonation Attack
6.5. Session Key Security
6.6. Resist Insider Attack
6.7. Secure Session Key Update
6.8. Comparison with Other Related Protocols
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Wang, J.; Gao, Y.; Yin, X.; Li, F.; Kim, H.J. An Enhanced PEGASIS Algorithm with Mobile Sink Support for Wireless Sensor Networks. Wirel. Commun. Mob. Comput. 2018, 1–9. [Google Scholar] [CrossRef]
- Nguyen, T.; Pan, J.; Dao, T. An Improved Flower Pollination Algorithm for Optimizing Layouts of Nodes in Wireless Sensor Network. IEEE Access 2019, 7, 75985–75998. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Sangaiahand, A.K.; Hye-Jin, K. Energy Efficient Routing Algorithm with Mobile Sink Support for Wireless Sensor Networks. Sensors 2019, 19, 1494. [Google Scholar] [CrossRef] [PubMed]
- Wang, J.; Gao, Y.; Sangaiahand, A.K.; Hye-Jin, K. An Improved Routing Schema with Special Clustering using PSO Algorithm for Heterogeneous Wireless Sensor Network. Sensors 2019, 19, 671. [Google Scholar] [CrossRef] [PubMed]
- He, S.; Xie, K.; Xie, K.; Xu, C.; Jin, W. Interference-aware Multi-source Transmission in Multi-radio and Multi-channel Wireless Network. IEEE Syst. J. 2019, 13, 2507–2518. [Google Scholar] [CrossRef]
- He, S.; Xie, K.; Chen, W.; Zhang, D.; Wen, J. Energy-aware Routing for SWIPT in Multi-hop Energy-constrained Wireless Network. IEEE Access 2018, 6, 17996–18008. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Niu, J.; Wu, F.; Liao, J.; Choo, K.K.R. A robust and energy efficient authentication protocol for industrial internet of things. IEEE Internet Things J. 2018, 5, 1606–1615. [Google Scholar] [CrossRef]
- Li, X.; Liu, S.; Wu, F.; Kumari, S.; Rodrigues, J.J.P.C. Privacy Preserving Data Aggregation Scheme for Mobile Edge Computing Assisted IoT Applications. IEEE Internet Things J. 2019, 6, 4755–4763. [Google Scholar] [CrossRef]
- Li, W.; Chen, Z.; Gao, X.; Liu, W.; Wang, J. Multi-Model Framework for Indoor Localization under Mobile Edge Computing Environment. IEEE Internet Things J. 2019, 6, 4844–4853. [Google Scholar] [CrossRef]
- Yin, Y.; Xu, Y.; Xu, W.; Min, G.; Pei, Y. Collaborative Service Selection via Ensemble Learning in Mixed Mobile Network Environments. Entropy 2017, 19, 358. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Wenbing, W.; Se-Jung, L. An Asynchronous Clustering and Mobile Data Gathering Schema based on Timer Mechanism in Wireless Sensor Networks. Comput. Mater. Contin. 2019, 58, 711–725. [Google Scholar] [CrossRef]
- Wang, J.; Ju, C.; Gao, Y.; Sangaiah, A.K.; jun Kim, G. A PSO based Energy Efficient Coverage Control Algorithm for Wireless Sensor Networks. Comput. Mater. Contin. 2018, 56, 433–446. [Google Scholar]
- Zhang, J.; Jin, X.; Sum, J.; Wang, J.; Li, K. Dual model learning combined with multiple feature selection for accurate visual tracking. IEEE Access 2019, 7, 43956–43969. [Google Scholar] [CrossRef]
- Zhang, J.; Lu, C.; Li, X.; Kim, H.J.; Wang, J. A full convolutional network based on DenseNet for remote sensing scene classification. Math. Biosci. Eng. 2019, 16, 3345–3367. [Google Scholar] [CrossRef]
- Liu, Y.N.; Wang, Y.P.; Wang, X.F.; Xia, Z.; Xu, J.F. Privacy-preserving raw data collection without a trusted authority for IoT. Comput. Netw. 2019, 148, 340–348. [Google Scholar] [CrossRef]
- Song, J.; Liu, Y.; Shao, J.; Tang, C. A Dynamic Membership Data Aggregation (DMDA) Protocol for Smart Grid. IEEE Syst. J. 2019. [Google Scholar] [CrossRef]
- Zhang, S.; Choo, K.K.R.; Liu, Q.; Wang, G. Enhancing privacy through uniform grid and caching in location-based services. Future Gener. Comput. Syst. 2018, 86, 881–892. [Google Scholar] [CrossRef]
- Zhang, S.; Mao, X.; Choo, K.K.R.; Peng, T.; Wang, G. A trajectory privacy-preserving scheme based on a dual-K mechanism for continuous location-based services. Inf. Sci. 2019. [Google Scholar] [CrossRef]
- Zhu, J.; Ma, J. A new authentication scheme with anonymity for wireless environments. IEEE Trans. Consum. Electron. 2004, 50, 231–235. [Google Scholar]
- Lee, C.C.; Hwang, M.S.; Liao, I.E. Security enhancement on a new authentication scheme with anonymity for wireless environments. IEEE Trans. Ind. Electron. 2006, 53, 1683–1687. [Google Scholar] [CrossRef]
- Wu, C.C.; Lee, W.B.; Tsaur, W.J. A secure authentication scheme with anonymity for wireless communications. IEEE Commun. Lett. 2008, 12, 722–723. [Google Scholar]
- Chang, C.C.; Lee, C.Y.; Chiu, Y.C. Enhanced authentication scheme with anonymity for roaming service in global mobility networks. Comput. Commun. 2009, 32, 611–618. [Google Scholar] [CrossRef]
- Xu, J.; Zhu, W.T.; Feng, D.G. An efficient mutual authentication and key agreement protocol preserving user anonymity in mobile networks. Comput. Commun. 2011, 34, 319–325. [Google Scholar] [CrossRef]
- He, D.; Ma, M.; Zhang, Y.; Chen, C.; Bu, J. A strong user authentication scheme with smart cards for wireless communications. Comput. Commun. 2011, 34, 367–374. [Google Scholar] [CrossRef]
- Li, C.T.; Lee, C.C. A novel user authentication and privacy preserving scheme with smart cards for wireless communications. Math. Comput. Model. 2012, 55, 35–44. [Google Scholar] [CrossRef]
- Yoon, E.J.; Yoo, K.Y.; Ha, K.S. A user friendly authentication scheme with anonymity for wireless communications. Comput. Electr. Eng. 2011, 37, 356–364. [Google Scholar] [CrossRef]
- Niu, J.; Li, X. A novel user authentication scheme with anonymity for wireless communications. Secur. Commun. Netw. 2014, 7, 1467–1476. [Google Scholar] [CrossRef]
- Mun, H.; Han, K.; Lee, Y.S.; Yeun, C.Y.; Choi, H.H. Enhanced secure anonymous authentication scheme for roaming service in global mobility networks. Math. Comput. Model. 2012, 55, 214–222. [Google Scholar] [CrossRef]
- Zhao, D.; Peng, H.; Li, L.; Yang, Y. A secure and effective anonymous authentication scheme for roaming service in global mobility networks. Wirel. Pers. Commun. 2014, 78, 247–269. [Google Scholar] [CrossRef]
- Karuppiah, M.; Saravanan, R. A secure authentication scheme with user anonymity for roaming service in global mobility networks. Wirel. Pers. Commun. 2015, 84, 2055–2078. [Google Scholar] [CrossRef]
- Li, X.; Sangaiah, A.K.; Kumari, S.; Wu, F.; Shen, J.; Khan, M.K. An efficient authentication and key agreement scheme with user anonymity for roaming service in smart city. Pers. Ubiquitous Comput. 2017, 21, 791–805. [Google Scholar] [CrossRef]
- Madhusudhan, R.; Shashidhara. A secure and lightweight authentication scheme for roaming service in global mobile networks. J. Inf. Secur. Appl. 2018, 38, 96–110. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Park, Y.; Tanwar, S. Design of an anonymity-preserving group formation based authentication protocol in global mobility networks. IEEE Access 2018, 6, 20673–20693. [Google Scholar] [CrossRef]
- Xu, G.; Liu, J.; Lu, Y.; Zeng, X.; Zhang, Y.; Li, X. A novel efficient MAKA protocol with desynchronization for anonymous roaming service in Global Mobility Networks. J. Netw. Comput. Appl. 2018, 107, 83–92. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Choo, K.K.R. A robust biometrics based three-factor authentication scheme for global mobility networks in smart city. Future Gener. Comput. Syst. 2018, 83, 607–618. [Google Scholar] [CrossRef]
- Wei, F.; Vijayakumar, P.; Jiang, Q.; Zhang, R. A mobile intelligent terminal based anonymous authenticated key exchange protocol for roaming service in global mobility networks. IEEE Trans. Sustain. Comput. 2018. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Understanding security failures of two-factor authentication schemes for real-time applications in hierarchical wireless sensor networks. Ad Hoc Netw. 2014, 20, 1–15. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; He, D.; Wang, P. On the challenges in designing identity-based privacy-preserving authentication schemes for mobile devices. IEEE Syst. J. 2018, 12, 916–925. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C. Anonymous Two-Factor Authentication in Distributed Systems: Certain Goals Are Beyond Attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Bresson, E.; Chevassut, O.; Pointcheval, D. Security proofs for an efficient password-based key exchange. In Proceedings of the 10th ACM Conference on Computer and Communications Security, Washington, DC, USA, 27–30 October 2003; ACM: New York, NY, USA, 2003; pp. 241–250. [Google Scholar]
- Xu, L.; Wu, F. An improved and provable remote user authentication scheme based on elliptic curve cryptosystem with user anonymity. Secur. Commun. Netw. 2015, 8, 245–260. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. A privacy-preserving and provable user authentication scheme for wireless sensor networks based on internet of things security. J. Ambient. Intell. Humaniz. Comput. 2017, 8, 101–116. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Two birds with one stone: Two-factor authentication with security beyond conventional bound. IEEE Trans. Dependable Secur. Comput. 2016, 15, 708–722. [Google Scholar] [CrossRef]





| Symbol | Meaning |
|---|---|
| , | a mobile user and the corresponding identity and password |
| , | ’s home agent and the identity |
| , | a foreign agent and the identity |
| secret and public key pair of | |
| a secret key shared between and | |
| two large prime numbers | |
| g | a generator of |
| an integer between for the fuzzy verifier | |
| a pair of symmetric encryption and decryption algorithms | |
| the hash function | |
| the random integers generated by and | |
| ⊕ | the XOR operation |
| l | secure length |
| an adversary |
| Protocol in [30] | Protocol in [32] | Our Protocol | |
|---|---|---|---|
| Resist mobile device/smart card breach attack | √ | × | √ |
| Resist insider attack | √ | √ | √ |
| Resist user impersonation attack | √ | × | √ |
| Resist stolen verifier attack | × | × | √ |
| User anonymity | √ | √ | √ |
| Local password change | × | √ | √ |
| Proper bidirectional authentication | √ | × | √ |
| Session key security | √ | × | √ |
| Forward secrecy | × | × | √ |
| Session key update | × | × | √ |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, S.; Li, X.; Wu, F.; Liao, J.; Wang, J.; Lin, D. A Novel Authentication Protocol with Strong Security for Roaming Service in Global Mobile Networks. Electronics 2019, 8, 939. https://doi.org/10.3390/electronics8090939
Liu S, Li X, Wu F, Liao J, Wang J, Lin D. A Novel Authentication Protocol with Strong Security for Roaming Service in Global Mobile Networks. Electronics. 2019; 8(9):939. https://doi.org/10.3390/electronics8090939
Chicago/Turabian StyleLiu, Shanpeng, Xiong Li, Fan Wu, Junguo Liao, Jin Wang, and Dingbao Lin. 2019. "A Novel Authentication Protocol with Strong Security for Roaming Service in Global Mobile Networks" Electronics 8, no. 9: 939. https://doi.org/10.3390/electronics8090939
APA StyleLiu, S., Li, X., Wu, F., Liao, J., Wang, J., & Lin, D. (2019). A Novel Authentication Protocol with Strong Security for Roaming Service in Global Mobile Networks. Electronics, 8(9), 939. https://doi.org/10.3390/electronics8090939





