Homomorphic Encryption and Network Coding in IoT Architectures: Advantages and Future Challenges
Abstract
:1. Introduction
2. Background
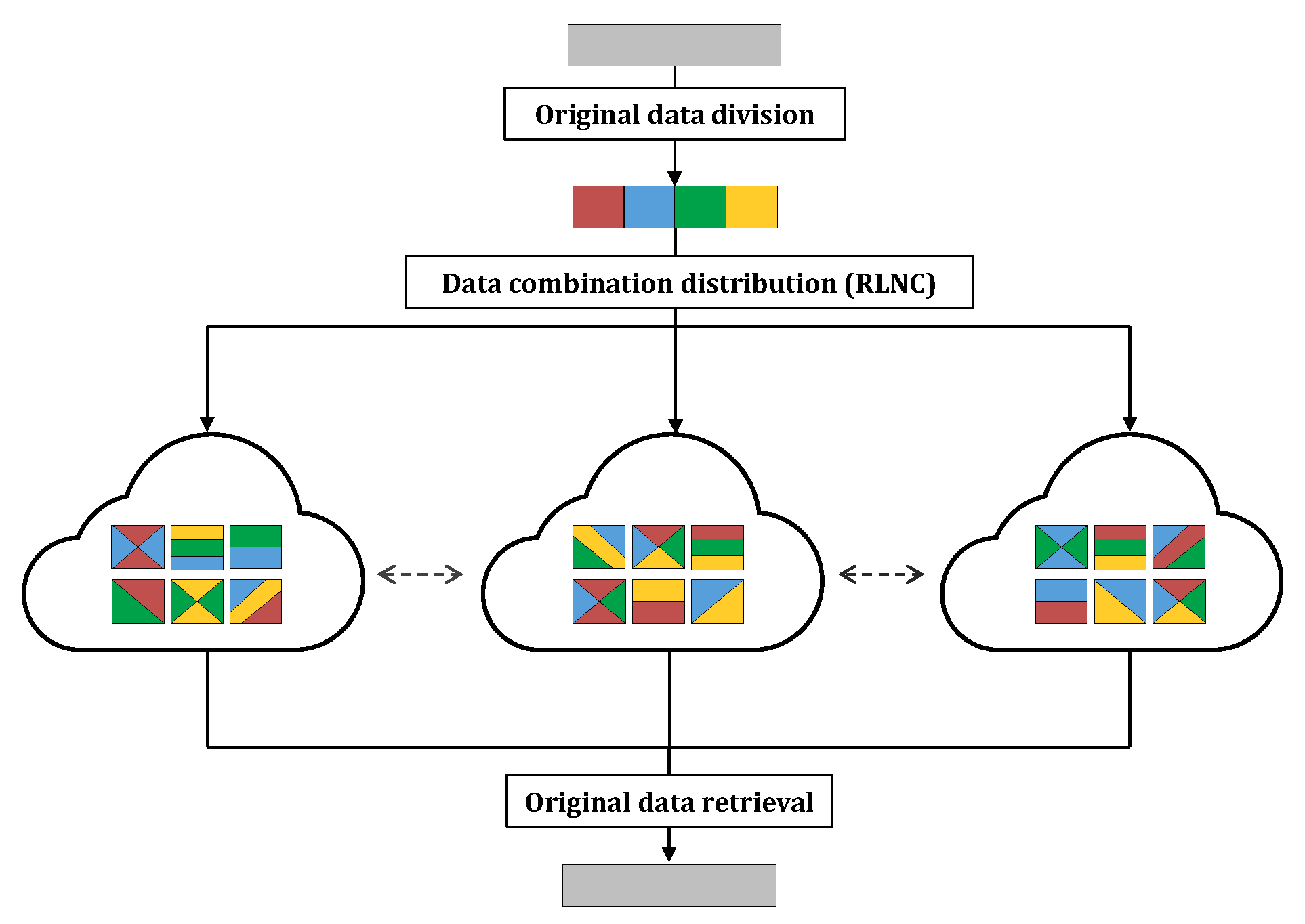
2.1. Network Coding
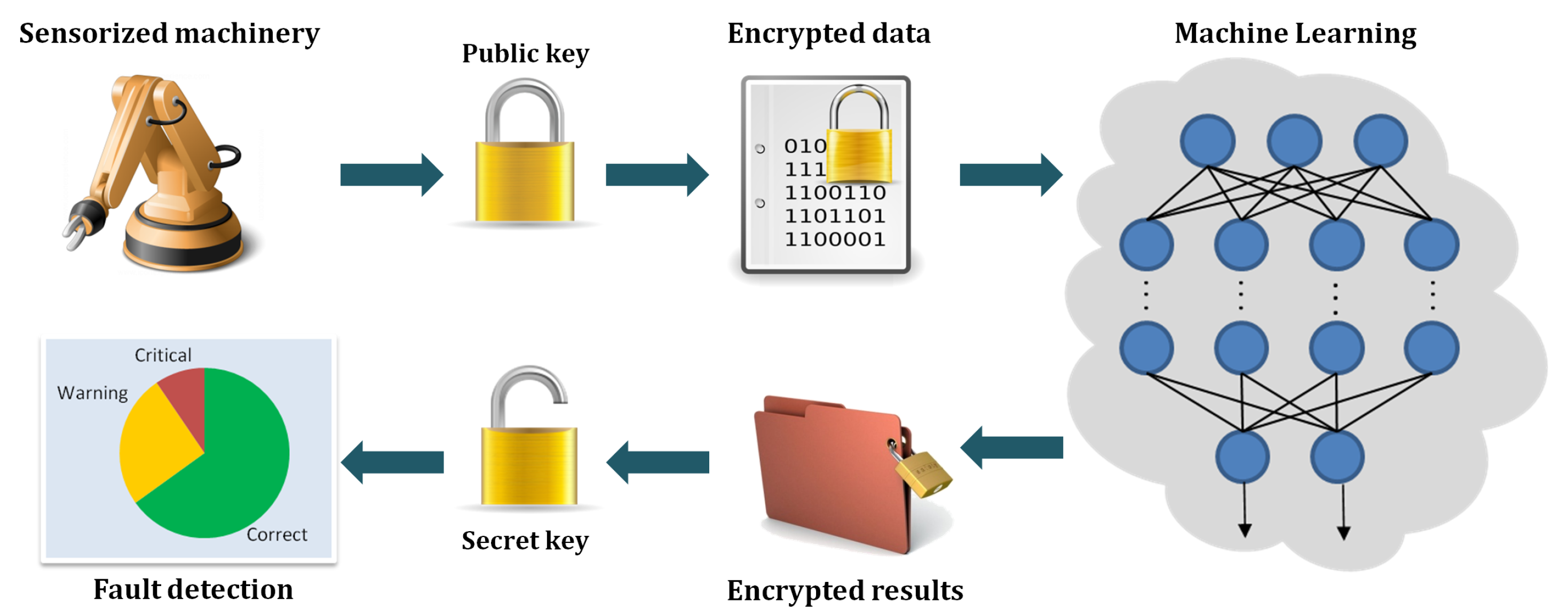
2.2. Homomorphic Encryption
3. Related Work
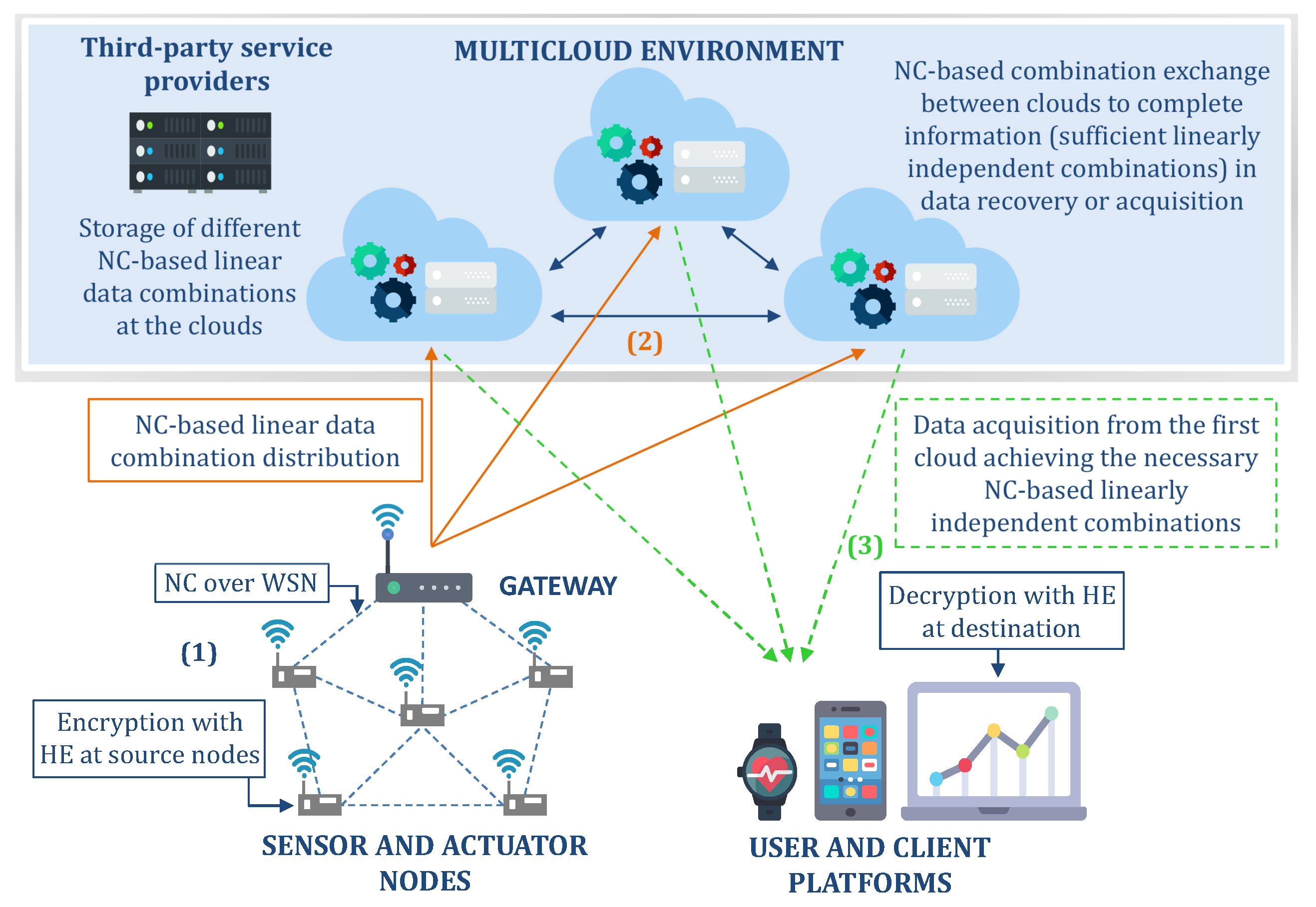
4. Benefits, Issues, and Open Challenges
4.1. Security, Privacy and Trust
4.2. Latency
4.3. Reliability and Availability
4.4. Service Outage
4.5. Flexibility and Scalability
4.6. Cost
4.7. Integration
4.8. IoT Communication Protocols
4.9. Discussion
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Lee, J.; Bagheri, B.; Kao, H.A. A Cyber-Physical Systems architecture for Industry 4.0-based manufacturing systems. Manuf. Lett. 2015, 3, 18–23. [Google Scholar] [CrossRef]
- Lu, Y. Industry 4.0: A survey on technologies, applications and open research issues. J. Ind. Inf. Integr. 2017, 6, 1–10. [Google Scholar] [CrossRef]
- Wollschlaeger, M.; Sauter, T.; Jasperneite, J. The Future of Industrial Communication: Automation Networks in the Era of the Internet of Things and Industry 4.0. IEEE Ind. Electron. Mag. 2017, 11, 17–27. [Google Scholar] [CrossRef]
- Gartner Inc. Analysts to Explore the Value and Impact of IoT on Business; Gartner Symposium/ITxpo: Barcelona, Spain, 2015. [Google Scholar]
- Zhong, R.; Xu, X.; Klotz, E.; Newman, S. Intelligent Manufacturing in the Context of Industry 4.0: A Review. Engineering 2017, 3, 616–630. [Google Scholar] [CrossRef]
- Zhan, Z.H.; Liu, X.F.; Gong, Y.J.; Zhang, J.; Chung, H.H.; Li, Y. Cloud computing resource scheduling and a survey of its evolutionary approaches. ACM Comput. Surv. 2015, 47, 63. [Google Scholar] [CrossRef]
- IDC. Worldwide and Regional Internet of Things 2014–2020 Forecast: A Virtuous Circle of Proven Value and Demand; IDC: Framingham, MA, USA, 2014. [Google Scholar]
- Sicari, S.; Rizzardi, A.; Grieco, L.; Coen-Porisini, A. Security, privacy and trust in Internet of things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Alert Logic. 5 Cybersecurity Statistics Every Small Business Should Know in 2018; Alert Logic: Houston, TX, USA, 2018. [Google Scholar]
- Al-Falahy, N.; Alani, O. Technologies for 5G Networks: Challenges and Opportunities. IT Prof. 2017, 19, 12–20. [Google Scholar] [CrossRef]
- Gentry, C. A Fully Homomophic Encryption Scheme. Ph.D. Thesis, Standford University, Stanford, CA, USA, 2009. [Google Scholar]
- Kumarage, H.; Khalil, I.; Alabdulatif, A.; Tari, Z.; Yi, X. Secure Data Analytics for Cloud-Integrated Internet of Things Applications. IEEE Cloud Comput. 2016, 3, 46–56. [Google Scholar] [CrossRef]
- Kim, M.; Song, Y.; Wang, S.; Xia, Y.; Jiang, X. Secure logistic regression based on homomorphic encryption: Design and evaluation. JMIR Med. Inform. 2018, 6, e19. [Google Scholar] [CrossRef] [PubMed]
- Ahlswede, R.; Cai, N.; Li, S.Y.; Yeung, R.W. Network information flow. IEEE Trans. Inf. Theory 2000, 46, 1204–1216. [Google Scholar] [CrossRef]
- Hansen, J.; Lucani, D.; Krigslund, J.; Médard, M.; Fitzek, F. Network coded software defined networking: Enabling 5G transmission and storage networks. IEEE Commun. Mag. 2015, 53, 100–107. [Google Scholar] [CrossRef]
- Fragouli, C.; Le Boudec, J.Y.; Widmer, J. Network coding: an instant primer. ACM SIGCOMM Comput. Commun. Rev. 2006, 36, 63–68. [Google Scholar] [CrossRef]
- Dimakis, A.G.; Godfrey, P.B.; Wu, Y.; Wainwright, M.J.; Ramchandran, K. Network coding for distributed storage systems. IEEE Trans. Inf. Theory 2010, 56, 4539–4551. [Google Scholar] [CrossRef]
- Sipos, M.; Fitzek, F.H.P.; Lucani, D.E.; Pedersen, M.V. Dynamic allocation and efficient distribution of data among multiple clouds using network coding. In Proceedings of the 2014 IEEE 3rd International Conference on Cloud Networking (CloudNet), Luxembourg, 8–10 October 2014; pp. 90–95. [Google Scholar]
- Ho, T.; Medard, M.; Koetter, R.; Karger, D.R.; Effros, M.; Shi, J.; Leong, B. A Random Linear Network Coding Approach to Multicast. IEEE Trans. Inf. Theory 2006, 52, 4413–4430. [Google Scholar] [CrossRef]
- Katti, S.; Rahul, H.; Hu, W.; Katabi, D.; Medard, M.; Crowcroft, J. XORs in the air: Practical wireless network coding. IEEE/ACM Trans. Netw. 2008, 16, 497–510. [Google Scholar] [CrossRef]
- Xie, L.; Chong, P.; Ho, I.; Guan, Y. A survey of inter-flow network coding in wireless mesh networks with unicast traffic. Comput. Netw. 2015, 91, 738–751. [Google Scholar] [CrossRef]
- Liu, A.; Zhang, Q.; Li, Z.; Choi, Y.J.; Li, J.; Komuro, N. A green and reliable communication modeling for industrial internet of things. Comput. Electr. Eng. 2017, 58, 364–381. [Google Scholar] [CrossRef]
- Hernández Marcano, N.; Heide, J.; Lucani, D.; Fitzek, F. Throughput, energy and overhead of multicast device-to-device communications with network-coded cooperation. Trans. Emerg. Telecommun. Technol. 2017, 28, e3011. [Google Scholar] [CrossRef]
- Szabo, D.; Gulyas, A.; Fitzek, F.H.P.; Lucani, D.E. Towards the Tactile Internet: Decreasing Communication Latency with Network Coding and Software Defined Networking. In Proceedings of the European Wireless 2015: 21th European Wireless Conference, Budapest, Hungary, 20–22 May 2015; pp. 1–6. [Google Scholar]
- Fragouli, C.; Soljanin, E. Network coding applications. Found. Trends® Netw. 2008, 2, 135–269. [Google Scholar] [CrossRef]
- Chen, H.C.H.; Hu, Y.; Lee, P.P.C.; Tang, Y. NCCloud: A Network-Coding-Based Storage System in a Cloud-of-Clouds. IEEE Trans. Comput. 2014, 63, 31–44. [Google Scholar] [CrossRef]
- Saleh, B.; Qiu, D. Performance Analysis of Network-Coding-Based P2P Live Streaming Systems. IEEE/ACM Trans. Netw. 2016, 24, 2140–2153. [Google Scholar] [CrossRef]
- Talooki, V.N.; Bassoli, R.; Lucani, D.E.; Rodriguez, J.; Fitzek, F.H.; Marques, H.; Tafazolli, R. Security concerns and countermeasures in network coding based communication systems: A survey. Comput. Netw. 2015, 83, 422–445. [Google Scholar] [CrossRef]
- Yao, S.; Chen, J.; Du, R.; Deng, L.; Wang, C. A survey of security network coding toward various attacks. In Proceedings of the 2014 IEEE 13th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Beijing, China, 24–26 September 2014; pp. 252–259. [Google Scholar]
- Acar, A.; Aksu, H.; Uluagac, A.; Conti, M. A survey on homomorphic encryption schemes: Theory and implementation. ACM Comput. Surv. 2018, 51, 79. [Google Scholar] [CrossRef]
- Mohan, M.; Devi, M.K.K.; Prakash, V.J. Homomorphic encryption-state of the art. In Proceedings of the 2017 International Conference on Intelligent Computing and Control (I2C2), Coimbatore, Tamil Nadu, India, 23–24 June 2017; pp. 1–6. [Google Scholar]
- Naehrig, M.; Lauter, K.; Vaikuntanathan, V. Can homomorphic encryption be practical? In Proceedings of the 3rd ACM Workshop on Cloud Computing Security Workshop, Chicago, IL, USA, 21 October 2011; pp. 113–124. [Google Scholar]
- Wang, L.; Li, J.; Ahmad, H. Challenges of fully homomorphic encryptions for the internet of things. IEICE Trans. Inf. Syst. 2016, E99D, 1982–1990. [Google Scholar] [CrossRef]
- Shafagh, H.; Hithnawi, A.; Burkhalter, L.; Fischli, P.; Duquennoy, S. Secure Sharing of Partially Homomorphic Encrypted IoT Data. In Proceedings of the 15th ACM Conference on Embedded Network Sensor Systems, Delft, The Netherlands, 6–8 November 2017. [Google Scholar]
- Yi, X.; Okamoto, E. Practical Internet voting system. J. Netw. Comput. Appl. 2013, 36, 378–387. [Google Scholar] [CrossRef]
- Will, M.A.; Nicholson, B.; Tiehuis, M.; Ko, R.K.L. Secure Voting in the Cloud Using Homomorphic Encryption and Mobile Agents. In Proceedings of the 2015 International Conference on Cloud Computing Research and Innovation (ICCCRI), Singapore, 26–27 October 2015; pp. 173–184. [Google Scholar]
- Graepel, T.; Lauter, K.; Naehrig, M. ML Confidential: Machine Learning on Encrypted Data. In Information Security and Cryptology—ICISC 2012; Kwon, T., Lee, M.K., Kwon, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 1–21. [Google Scholar] [Green Version]
- Li, P.; Li, J.; Huang, Z.; Li, T.; Gao, C.Z.; Yiu, S.M.; Chen, K. Multi-key privacy-preserving deep learning in cloud computing. Future Gener. Comput. Syst. 2017, 74, 76–85. [Google Scholar] [CrossRef]
- Georgakopoulos, D.; Jayaraman, P.; Fazia, M.; Villari, M.; Ranjan, R. Internet of Things and Edge Cloud Computing Roadmap for Manufacturing. IEEE Cloud Comput. 2016, 3, 66–73. [Google Scholar] [CrossRef]
- Fisher, O.; Watson, N.; Porcu, L.; Bacon, D.; Rigley, M.; Gomes, R. Cloud manufacturing as a sustainable process manufacturing route. J. Manuf. Syst. 2018, 47, 53–68. [Google Scholar] [CrossRef]
- Qu, T.; Lei, S.; Wang, Z.; Nie, D.; Chen, X.; Huang, G. IoT-based real-time production logistics synchronization system under smart cloud manufacturing. Int. J. Adv. Manuf. Technol. 2016, 84, 147–164. [Google Scholar] [CrossRef]
- Talha, S.; Ahmad, R.; Kiani, A.K.; Alam, M.M. Network Coding for Energy Efficient Transmission in Wireless Body Area Networks. Procedia Comput. Sci. 2017, 113, 435–440. [Google Scholar] [CrossRef]
- Muhammad, S.J.; Zhang, S.; Dyo, V. Network coding for reliable safety message communication in vehicular Ad-Hoc networks: A review. In Proceedings of the 2015 Fourth International Conference on Future Generation Communication Technology (FGCT), Luton, UK, 29–31 July 2015; pp. 1–6. [Google Scholar]
- Wang, Z.; Li, J.; Fang, M.; Li, Y.; Feng, B. A Reliable Routing Algorithm with Network Coding in Internet of Vehicles. China Commun. 2017, 14, 174–184. [Google Scholar] [CrossRef]
- Arya, N.; Rout, R.R.; Lingam, G. Network Coding Based Multiple Fault Tolerance Scheme in P2P Cloud Storage System. In Proceedings of the 2018 IEEE 13th International Conference on Industrial and Information Systems (ICIIS), Rupnagar, India, 1–2 December 2018; pp. 223–228. [Google Scholar]
- Mao, B.; Wu, S.; Jiang, H. Improving Storage Availability in Cloud-of-Clouds with Hybrid Redundant Data Distribution. In Proceedings of the 2015 IEEE International Parallel and Distributed Processing Symposium, Hyderabad, India, 25–29 May 2015; pp. 633–642. [Google Scholar]
- Peralta, G.; Garrido, P.; Bilbao, J.; Agüero, R.; Crespo, P. On the combination of multi-cloud and network coding for cost-efficient storage in industrial applications. Sensors 2019, 19, 1673. [Google Scholar] [CrossRef] [PubMed]
- Vuran, M.C.; Akan, Ö.B.; Akyildiz, I.F. Spatio-temporal correlation: theory and applications for wireless sensor networks. Comput. Netw. 2004, 45, 245–259. [Google Scholar] [CrossRef]
- Han, W.; Xiao, Y. Privacy preservation for V2G networks in smart grid: A survey. Comput. Commun. 2016, 91–92, 17–28. [Google Scholar] [CrossRef]
- Kocabas, O.; Soyata, T. Utilizing Homomorphic Encryption to Implement Secure and Private Medical Cloud Computing. In Proceedings of the 2015 IEEE 8th International Conference on Cloud Computing, New York, NY, USA, 27 June–2 July 2015; pp. 540–547. [Google Scholar]
- Hussein, A.F.; Kumar N, A.; Burbano-Fernandez, M.; Ramírez-González, G.; Abdulhay, E.; De Albuquerque, V.H.C. An Automated Remote Cloud-Based Heart Rate Variability Monitoring System. IEEE Access 2018, 6, 77055–77064. [Google Scholar] [CrossRef]
- Sun, X.; Zhang, P.; Liu, J.K.; Yu, J.; Xie, W. Private machine learning classification based on fully homomorphic encryption. IEEE Trans. Emerg. Top. Comput. 2019. [Google Scholar] [CrossRef]
- Chen, F.; Xiang, T.; Yang, Y.; Chow, S.S.M. Secure Cloud Storage Meets with Secure Network Coding. IEEE Trans. Comput. 2016, 65, 1936–1948. [Google Scholar] [CrossRef]
- Esfahani, A.; Mantas, G.; Rodriguez, J.; Neves, J. An efficient homomorphic MAC-based scheme against data and tag pollution attacks in network coding-enabled wireless networks. Int. J. Inf. Secur. 2017, 16, 627–639. [Google Scholar] [CrossRef]
- Liu, X.; Huang, J.; Zong, G. Public Auditing for Network Coding Based Secure Cloud Storage. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security And Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 713–720. [Google Scholar]
- He, S.; Zeng, W.; Xie, K.; Yang, H.; Lai, M.; Su, X. PPNC: Privacy preserving scheme for random linear network coding in smart grid. KSII Trans. Internet Inf. Syst. 2017, 11, 1510–1532. [Google Scholar]
- Sonami, M. Connect the Dots: IoT Security Risks in an Increasingly Connected World; IBM: Hong Kong, China, 2018. [Google Scholar]
- Zhou, J.; Cao, Z.; Dong, X.; Vasilakos, A.V. Security and Privacy for Cloud-Based IoT: Challenges. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- Nokia. 5G Connected Industry; Technical Report; Nokia: Espoo, Finland, 2018. [Google Scholar]
- Yan, J.; Meng, Y.; Lu, L.; Li, L. Industrial Big Data in an Industry 4.0 Environment: Challenges, Schemes, and Applications for Predictive Maintenance. IEEE Access 2017, 5, 23484–23491. [Google Scholar] [CrossRef]
- Ponemon Institute. Cost of Data Center Outages; Technical Report; Ponemon Institute: Traverse City, MI, USA, 2016. [Google Scholar]
- Naito, K. A survey on the internet-of-things: Standards, challenges and future prospects. J. Inf. Process. 2017, 25, 23–31. [Google Scholar] [CrossRef]
- Amazon Web Services, Inc. Amazon Elastic Compute Cloud: User Guide for Linux Instances. 2019. Available online: https://docs.amazonaws.cn/en_us/AWSEC2/latest/UserGuide/ec2-ug.pdf (accessed on 22 May 2019).
- Noura, M.; Atiquzzaman, M.; Gaedke, M. Interoperability in Internet of Things: Taxonomies and Open Challenges. Mobile Netw. Appl. 2019, 24, 796–809. [Google Scholar] [CrossRef]
- IEEE. IEEE 802.11ah-2016; Technical Report; IEEE: Piscataway, NJ, USA, 2017. [Google Scholar]
- Bluetooth. Bluetooth Low Energy (BLE). Available online: https://www.bluetooth.com/bluetooth-technology/radio-versions/ (accessed on 22 May 2019).
- IETF Tools. RFC 8376—Low-Power Wide Area Network (LPWAN) Overview. 2018. Available online: https://tools.ietf.org/html/rfc8376 (accessed on 22 May 2019).
- OASIS. MQTT Version 3.1.1. 2014. Available online: http://docs.oasis-open.org/mqtt/mqtt/v3.1.1/os/mqtt-v3.1.1-os.pdf (accessed on 22 May 2019).
- IETF Tools. RFC 7252—The Constrained Application Protocol (CoAP). 2014. Available online: https://tools.ietf.org/html/rfc7252 (accessed on 22 May 2019).
- Lepoint, T.; Naehrig, M. A comparison of the homomorphic encryption schemes FV and YASHE. In International Conference on Cryptology in Africa; Springer: Cham, Switzerland, 2014; pp. 318–335. [Google Scholar]
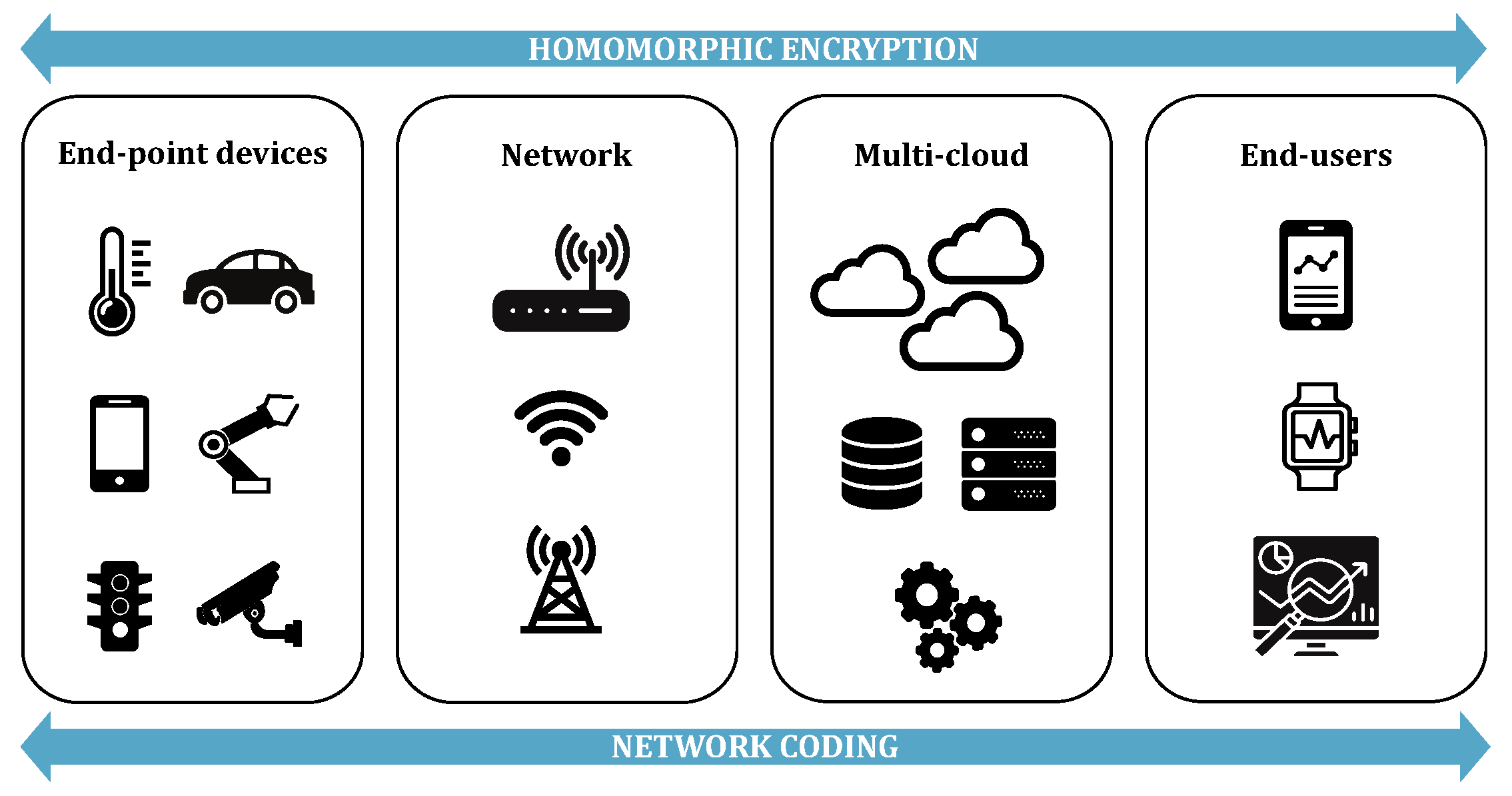
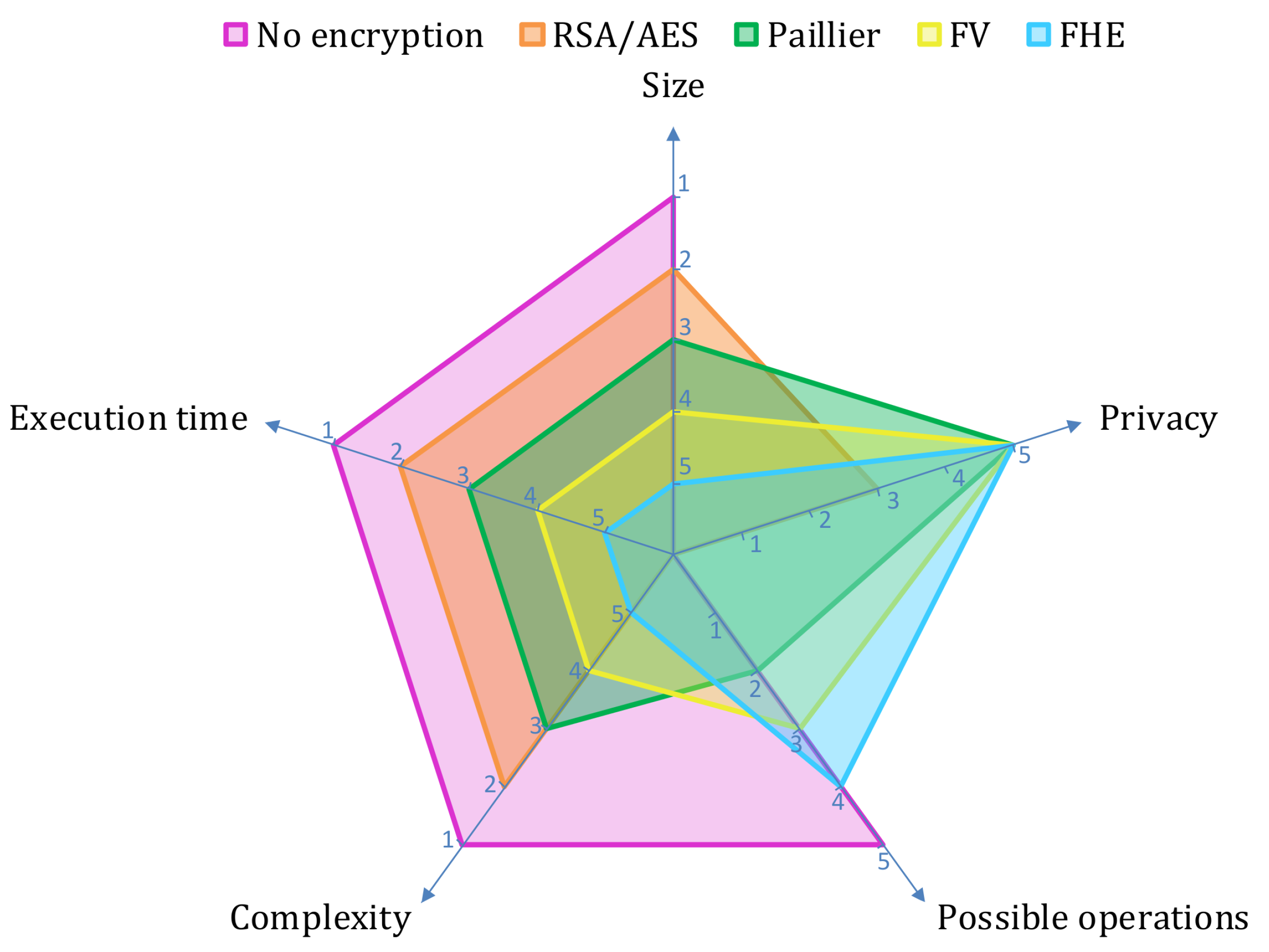
| Advantages | Disadvantages | |
|---|---|---|
| Homomorphic Encryption | • Provides end-to-end data privacy, allowing secure third-party cloud computations. | • Implies greater computational costs due to its inherent complexity. |
| • Enables private information sharing in multi-party scenarios among several data owners. | • Generates large ciphertext, which poses challenges to introduce HE to IoT lightweight communication protocols. | |
| • SHE or PHE can be used in applications which require simpler operations. | • The size of the encrypted data also implies higher transmission costs. | |
| Network Coding | • Improves the performance, e.g., latency and cost, of congested wireless networks and highly loaded multi-cloud deployments. | • Can lead to additional delays due to the introduction of a header overhead or complex recoding processes. |
| • Enhances system reliability and availability requiring less redundancy and recovery data. | • Data download speed can be compromised in an attempt to ensure reliability. | |
| • Distributes and stores data differently from the original form, increasing the architecture security level. | • Makes necessary to design new codes and distribution mechanisms to maintain a trade-off between reliability and performance. |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Peralta, G.; Cid-Fuentes, R.G.; Bilbao, J.; Crespo, P.M. Homomorphic Encryption and Network Coding in IoT Architectures: Advantages and Future Challenges. Electronics 2019, 8, 827. https://doi.org/10.3390/electronics8080827
Peralta G, Cid-Fuentes RG, Bilbao J, Crespo PM. Homomorphic Encryption and Network Coding in IoT Architectures: Advantages and Future Challenges. Electronics. 2019; 8(8):827. https://doi.org/10.3390/electronics8080827
Chicago/Turabian StylePeralta, Goiuri, Raul G. Cid-Fuentes, Josu Bilbao, and Pedro M. Crespo. 2019. "Homomorphic Encryption and Network Coding in IoT Architectures: Advantages and Future Challenges" Electronics 8, no. 8: 827. https://doi.org/10.3390/electronics8080827
APA StylePeralta, G., Cid-Fuentes, R. G., Bilbao, J., & Crespo, P. M. (2019). Homomorphic Encryption and Network Coding in IoT Architectures: Advantages and Future Challenges. Electronics, 8(8), 827. https://doi.org/10.3390/electronics8080827






