Abstract
A secret image sharing (SIS) scheme inserts a secret message into shadow images in a way that if shadow images are combined in a specific way, the secret image can be recovered. A 2-out-of-2 sharing digital image scheme (SDIS) adopts a color palette to share a digital color secret image into two shadow images, and the secret image can be recovered from two shadow images, while any one shadow image has no information about the secret image. This 2-out-of-2 SDIS may keep the shadow size small because by using a color palette, and thus has advantage of reducing storage. However, the previous works on SDIS are just 2-out-of-2 scheme and have limited functions. In this paper, we take the lead to study a general n-out-of-n SDIS which can be applied on more than two shadow. The proposed SDIS is implemented on the basis of 2-out-of-2 SDIS. Our main contribution has the higher contrast of binary meaningful shadow and the larger region in color shadows revealing cover image when compared with previous 2-out-of-2 SDISs. Meanwhile, our SDIS is resistant to colluder attack.
1. Introduction
A secret image sharing (SIS) scheme inserts a secret message into shadow images in a way that if shadow images are combined in a specific way, the secret image can be recovered. A SIS scheme is usually referred to by a threshold SIS, where , and can insert a secret image into n shadow images (referred to as shadows). In a -SIS, we may recover the secret image by using any k shadows, but cannot recover the secret image from or fewer shadows. There are various types of SIS. Here, we give a brief survey for three major types of SIS schemes: the visual cryptography scheme (VC), the polynomial-based SIS (PSIS), and the bit-wise Boolean-operation based SIS.
The so-called VC [1,2,3,4,5,6] has a novel stacking-to-see property such that the involved participants can easily stack shadows to visually decode the secret through the human eye. This property makes VC applicable in many scenarios. Although VC has the ease of decoding, it has poor visual quality of reconstructed image. Another SIS adopts -degree polynomial like Shamir’s secret sharing [7] to design -PSIS [8,9,10,11,12,13,14,15]. There are two major differences between VC and PSIS: the quality of recovered image and the decoding method. Unlike VC provided with the poor visual quality, the recovered secret image of PSIS is distortion-less. However, the decoding of VC only needs stacking operation but PSIS uses the computation of Lagrange interpolation to recover secret image. Some SIS schemes are based on Boolean operations [16,17,18,19,20]. Note: the stacking operation of VC, strictly speaking, is also a Boolean OR operation. However, this OR operation of VC is pixel-wise operation, which applied on black-and-white dots. However, Boolean operation in [16,17,18,19,20] is bit-wise operations, and can obtain a high-quality secret image (a distortion-less image like PSIS scheme). Besides, using -wise Boolean has much lower complexity when compared with Lagrange interpolation.
Recently, Wei et al. use the bit-wise XOR operation to design a sharing digital image scheme (SDIS) [17] to share a 256-color (or true color) digital image. Wei et al.’s -SDIS is also a type of -SIS where . Wei et al.’s -SDIS is the first SIS scheme using a 256-color palette. This color palette has 256 colors, where each color is composed of red (R), green (G), and blue (B) color planes. Each color and is chosen from a palette of 16,777,216(=2) colors (24 bits: each color plane has 8 bits). In VGA cards, 256 on-screen colors are chosen from a color palette, and these colors are most visible to the human eye and meanwhile conserve a bandwidth. When using a color palette, each pixel is represented by a color index in a 256-color color palette. Consider an example, a -pixel image. The file size is bytes (color indices) bytes (color palette) = 66,304 bytes, but is = 196,608 bytes for using 24-bit true color format. Thus, the file size of a color image can be kept small when represented by a color palette. Because Wei et al.’s -SDIS is based on color palette, and thus it has the advantage of reducing storage.
However, there are three weaknesses in Wei et al.’s SDIS: the incorrect assignment of color palette data for the color index 255, the erroneous recovery in secret image, and the partial region in shadow revealing the cover image. In [19], Yang et al. address these weaknesses and propose a new -SDIS. Both Wei et al.’s -SDIS and Yang et al.’s -SDIS are simple 2-out-of-2 scheme and have limited applications. In this paper, we take the lead to study a general -SDIS, which can be applied on any . The main weakness of Wei et al.’s -SDIS is the incorrect assignment of color palette data for some color indices, and this is tackled by using a complicated approach, partitioned sets, in Yang et al.’s -SDIS. In the proposed -SDIS, because of the number of shadows more than two, i.e., , a simple approach reducing Hamming weigh of a temporary block is adopted to easily solve this weakness. In addition, performance of our -SDIS are enhanced when compared with the previous -SDIS. The rest of this paper is organized as follows. Section 2 reviews Wei et al.’s -SDIS and Yang et al.’s -SDIS. The proposed -SDIS is presented in Section 3. Also, an approach of enhancing visual quality of color meaningful shadow is introduced. A very extreme attack, the -colluder attack, on the proposed -SDIS is discussed in Section 4. The experiment, discussion and comparison are in Section 5. Finally, Section 6 concludes the paper.
2. Preliminaries
Notations in this paper and their descriptions are listed in Table 1. These notations are used throughout the whole paper to describe all the schemes, Wei et al.’s -SDIS [17], Yang et al.’s -SDIS [19], and the proposed -SDIS.

Table 1.
Notations and Descriptions.
In [17], Wei et al. first proposed a simple -SDIS to insert a 256-color digital image into two binary noise-like shadows ( and ). In Wei et al.’s -SDIS, every 9-bit block B, i.e., , is obtained from the 256-color secret image and the color palette . Afterwards, the block B is subdivided into two blocks and on shadow 1 and shadow 2 , respectively, by using XOR operation. As shown in Figure 1, , where each bit , . Both shadow blocks of and are blocks. Accomplish all blocks until all pixels in and the data in are processed. Because every pixel in is represented as a block, shadow sizes are nine times expanded. The first 8 bits in B represents a color index, and the ninth bit in every block of (i.e., the bit ) is collected to covey the information. Therefore, from the XOR-ed results we may obtain color indices and the to recover . There are other two types of shadows for Wei et al.’s -SDIS. Noise-like shadows can be extended to two binary meaningful shadows and two color meaningful shadows , on which binary cover image and color cover image can be, respectively, visually viewed. In addition, Wei et al.’s -SDIS can also be extended to directly insert a true color without using .
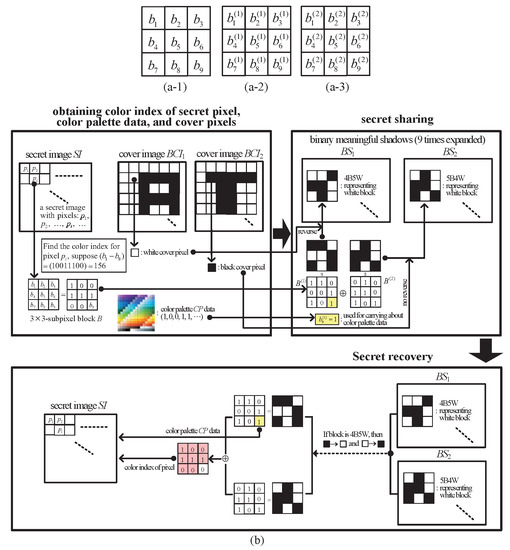
Figure 1.
Blocks of -SDIS: (a) secret block B, shadow blocks and (b) diagrammatical representation of Wei et al.’s -SDIS with binary meaningful shadows.
For more clearly describing Wei et al.’s -SDIS, Figure 1b illustrates diagrammatical representation of Wei et al.’s -SDIS with binary meaningful shadows, which includes three processes: (i) obtaining color indices of secret pixels, color palette data, and cover pixels, (ii) secret sharing, and (iii) secret recovery. Consider a secret pixel with a color index , and we may have with for carrying about data (suppose we embed for this time), and with . Then, we have . Meantime, both blocks and are blocks. For the corresponding position of this secret pixel , the cover pixels of and are white and black, respectively. We reverse the shadow block to to represent the white color pixel in , and we do not change to represent the black color pixel in . In secret recovery, the color index can be easily derived from the exclusive OR result from . In addition, the data can be obtained from every in .
However, Wei et al’s -SDIS has some weaknesses. For the color index 255, it has a problem with embedding the data of color palette. In addition, Wei et al.’s -SDIS with color meaningful shadows cannot correctly extract the block data for white cover pixels, and this will cause erroneous recovery in the secret image. Moreover, Wei et al.’s SDIS uses blocks on both shadows. Five black dots in a block B may not sufficiently demonstrate the visual quality of meaningful shadows.
It is obvious that more black subpixels in every block may enhance the visual quality of meaningful shadows and , and and . Accordingly, in [19], Yang et al. adopted block and block half and half on blocks and , such that the average number of black subpixels in and is enhanced from 5 to . This enhancement improved the visual quality of meaningful shadows. Meanwhile, Yang et al.’s -SDIS also solved the other two weaknesses of Wei et al.’s -SDIS.
3. Motivation and Design Concept
As described in Section 2, there are three weaknesses in Wei et al.’s SDIS: (1) the incorrect assignment of the color palette data for the color index 255, (2) the partial regions in meaningful shadows showing the content of the cover image, and (3) the erroneous recovery in secret image if the cover pixel is white in color meaningful shadows. Yang et al.’s -SDIS already tackled these weaknesses.
By delving into these three weaknesses, we can see that the third weakness is a minor weakness caused from an intrinsic nature of color. A trivial approach in [19], using a near white color pixel instead of white pixels in cover image, is very efficient in addressing this weakness. Therefore, the approach can be still adopted in the proposed -SDIS for solving this minor weakness. Our contribution is not just the extension from 2-out-of-2 scheme to n-out-of-n scheme. The proposed -SDIS, where , has better solutions for other two major weaknesses. Because the number of shadows is more than two, we can easily solve the first weaknesses (note: the detail will be described in Section 3). However, Yang et al.’s -SDIS uses a very complicated approach by partitioned sets to solve this weakness. For the second weakness, our -SDIS uses blocks in most shadows This approach has large average black subpixels in shadow blocks to enhance visual qualities of meaningful shadows. In addition, the proposed -SDIS embeds the information in but both -SDISs [17,19] use in shadow block . The bit obtained from the XOR-ed result B is more securely protected than the bit in one shadow block .
A secret block has 8 bits to represent a color index, and one bit for representing the data of color palette . Together with , this color index can represent a pixel in secret image . All 9-bit blocks are obtained from the secret image and the color palate . Suppose that T is a 9-bit temporary block. Equations (1) and (2) are main statements in this paper, on which we can design the proposed -SDIS. As shown in Equation (1), we may randomly generate blocks , and then determine a temporary block T via these blocks and the block B (see upper equation in Equation (1)). The content of T is provisional. Afterwards, T is divided into two blocks where . Using lower equation in Equation (1), we may insert T into two blocks based on Wei et al.’s -SDIS or Yang et al.’s -SDIS, which is dependent on the Hamming weigh of block T. In next subsection, we prove that lower equation in Equation (1) can be successfully accomplished. Via Equation (1), we can derive in Equation (2).
Equation (2) implies that the block B can be subdivide into n shadow blocks , and meanwhile can be recovered from . All the n shadows in the proposed -SDIS are illustrated in Figure 2. The operation of lower equation in Equation (1) using Wei et al.’ -SDIS is shown in Figure 2a, and using Yang et al.’s -SDIS is shown in Figure 2b.
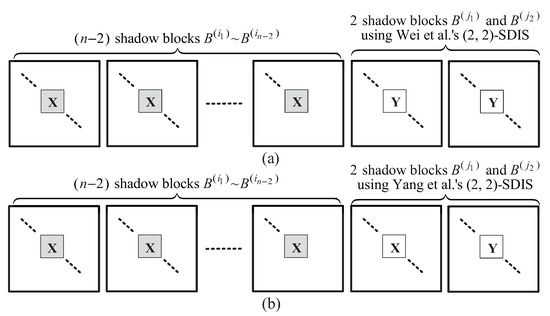
Figure 2.
Shadows of the proposed -SDIS: (a) using Wei et al.’s -SDIS for and (b) using Yang et al.’s -SDIS for and .
Moreover, in [17], the authors claimed that the -SDIS has a novel application to cover the transmission of confidential images. For example, as a supplementary aid to existing symmetric cryptography standards like DES which requires a pre-shared key, the -SDIS remains a safe and less risky means for key distribution. Because the prosed scheme is extended from 2-out-of-2 to n-out-of-n, it implies that our -SDIS can be applied on a group key distribution, which includes n members in this group. Besides the application in key distribution, the proposed scheme can be also applied to protection of secret image among multiple users. For instance, the colorful image of traffic or medical information are confidential, and our scheme provides a secure and high efficiency approach to safely keeping such image among n users, only all n users are able to recover the image with high quality.
Finally, in a shadow there are blocks with percentage of , and blocks with percentage of , respectively. The more blocks have the large number of black subpixels and may enhance visual qualities of meaningful shadows, and these percentages have more effective performance for large n.
4. The Proposed -SDIS
4.1. Sharing and Recovering Algorithms
A block diagram of the proposed -SDIS is illustrated in Figure 3. Shadows are noise-like, which is the same as Boolean-operation based SIS [18]. For the proposed -SDIS, we can complement the blocks for the corresponding white cover pixels to generate binary meaningful shadows from noise-like shadows , i.e., (or ) for black color and (or ) for white color. However, the scheme in [18] does dot has this property. On the other hand, to implement color meaningful shadows , the 1s in blocks are replaced with the color of the corresponding cover pixel, and leave 0s blank. Therefore, we only describe how to generate noise-like shadows, and how to recover the secret image and color palette from n noise-like shadows.
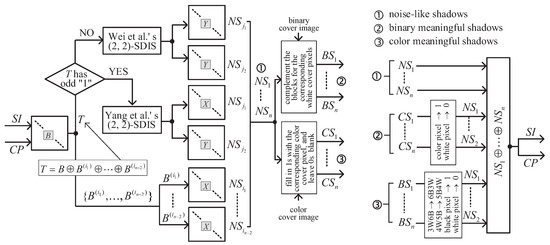
Figure 3.
Block diagram of the proposed -SDIS.
For noise-like shadows , detailed procedures of sharing and recovering procedures are briefly described step by step as follows.
Sharing Procedure
- (S-1)
- Obtain the block from the secret image and the color palate .
- (S-2)
- Randomly generate blocks .
- (S-3)
- By random blocks and the block B, calculate the temporary block T via .
- (S-4)
- If is 9, we reduce its Hamming weight to via modifying any one shadow block of ./* (1) In Lemma 1, we prove that the reduction of Hamming weight can always be accomplished (2) After step (S-4), the Hamming weight distribution is */.
- (S-5)
- If is odd () then construct two other shadows by ; else by , where ./* In Lemma 2, we prove that can be obtained from for odd , and from for even . */
- (S-6)
- Process all the blocks, and output shadow blocks on n noise-like shadows , respectively.
Recovering procedure:
- (S-1)
- Obtain B by XOR-ing via from n noise-like shadows ./* Theorem 1, demonstrates that we can obtain the original block from */
- (S-2)
- Recover the color index and the data of color palette , respectively, from B.
- (S-3)
- Repeat the above until all blocks in are processed, and finally and can be recovered.
4.2. Extension of -SDIS to Share True Color Secret Image
Same as -SDIS and VC in [5], the proposed -SDIS can be used to share a true color image. To share a true color secret image, we use a 25-subpixel block , which the first three 8-tuples, , , and , are used to represent and B color planes. The other one bit in is . This 25-subpixel block is shown in Figure 4a. Because we share and B colors directly, we do not need to use the bit to covey any information. Thus, this bit could be abandoned, or used as authentication bits to provide authentication capability like VC in [6] and PSIS in [10]. Collect , where , and append the bit to form red, green, and blue shadow blocks where as shown in Figure 4b.
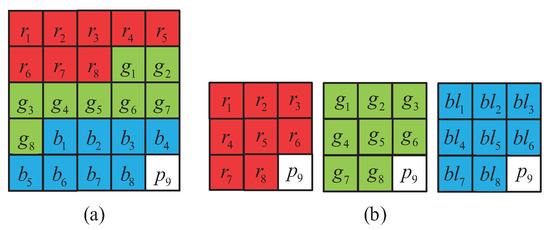
Figure 4.
Blocks for sharing true clor image: (a) 25-bit (b) 9-bit .
Detailed procedures of the proposed -SDIS for sharing and recovering true color image are briefly described step by step as follows.
Sharing procedure:
- (S-1)
- Obtain 24-bit true color , , and from the secret image , and random generate a bit to form a 25-bit block , as shown in Figure 4a./* Parity bit is not used to covey any information, and thus it can be randomly generated */
- (S-2)
- Subdivide the true color block to red, green, and blue shadow blocks .
- (S-3)
- Using as 9-bit block B in (S-1), respectively, to generate n shadow blocks , where , through (S-1) (S-6).
- (S-4)
- Collect every first 8 bits in , and append a black subpixel in the 25-th subpixel to generate a 25-bit shadow block , where ./* Because we do not use the 25-th bit in the XOR-ed result to convey any information, we can use black subpixel in 25-th subpixel for all shadow blocks to enhance the number of black subpixels. */
- (S-5)
- Process all the blocks, and output blocks on n noise-like shadows , respectively.
Recovering procedure:
- (R-1)
- Obtain every 25-bit block by XOR-ing via XOR-ing n noise-like shadows .
- (R-2)
- Recover a true color from the first 24 bits in , i.e., , , and .
- (R-3)
- Repeat the above until all blocks in are processed, and finally a true color is obtained.
4.3. Enhancing Visual Quality of Color Meaningful Shadow
Consider sharing 256-color (respectively, true color) , noise-like shadows , are (respectively, ) times expanded. Based on noise-like shadow , we can fill in 1s in shadow blocks with the color of the corresponding cover pixel in , and leave 0s blank to generate color meaningful shadow . Consider the case sharing 256-color . As shown in Figure 5a, there is a pixel with a blue color in . Suppose that the block at corresponding position for this pixel in is (see Figure 5b), and this block is a block with sub-pixels (see see Figure 5c). By putting the blue cover pixel into all black sub-pixels in Figure 5c, we have color meaningful shadow in Figure 5d. Noise-like shadow and color meaningful shadow have the same size subpixels and 9 times expanded when compared with .
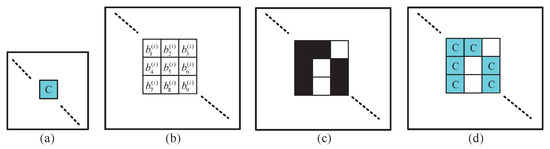
Figure 5.
Block patterns: (a) a pixel with a color in (b) the corresponding block in (c) the corresponding block in (d) the corresponding block in .
As shown in Figure 5d, the color at 1s in a block are the same. This is because and have the same size with pixels. To enhance visual quality of , we use a large color cover image with pixels (note: the original has only pixels). Obviously, this larger has the high resolution than . As shown in Figure 6, our new approach uses a large (see Figure 6a). By putting the color pixels in to into all 1s of in Figure 6b, we have the in Figure 6c. Because the color meaningful shadow has more colors, and will have the high resolution. By the same argument, this approach can also be applied to sharing true color .
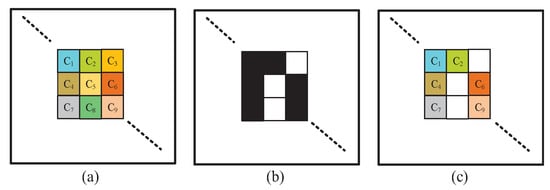
Figure 6.
Block patterns: (a) 9 color pixels with color in (b) the corresponding block in (c) the corresponding color block in .
5. Theorem and Security Analysis
5.1. Main Theorems and Examples
Lemma 1.
Suppose that the block T in Equation (1) is all-1 block, i.e., . We may change any two positions (one is and the other is ) in any one block , such that the equation holds, and is reduced from 9 to 7. Meanwhile, all blocks , are still blocks.
Proof.
As shown in Equation (1), all these blocks are blocks. We choose one block , and modify any two positions of and . This modification will change the 1 in the block T to 0 at these two chosen modified positions. After that, is reduced to . Meanwhile, because we change two positions by and , respectively, the Hamming weight is unchanged, and this shadow block is still a block. □
Lemma 2.
Blocks in step (S-5) can be obtained from for odd , and from for even .
Proof.
Let be block, and both and be blocks. We first prove that the possible Hamming weights of are , and the possible Hamming weights of are . Because both blocks and have the same Hamming weight 5, the number of positions of and crossing from vectors to should be the same. Suppose that this number is y. Therefore, the has the following form (see Equation (3)), where . Obviously, the Hamming weight of in Equation (3) is , and thus may be . □
Consider the XOR-ed block . Because blocks and have Hamming weights 6 and 5, respectively. The number of positions of and crossing from vectors to should differ with one. Suppose that the number crossing from vectors to of is , and the number of is x. Therefore, the has the following form (see Equation (4)), where . The Hamming weight of in Equation (4) is , and thus may be .
Because Wei et al.’s -SDIS uses two blocks (say and ), therefore using Wei et al.’s -SDIS has with even values . On the other hand, there are one block and one block (say and ) when using Yang et al.’s -SDIS. Thus, using Yang et al.’s -SDIS has with odd values . Finally, the above implies that can be obtained from for odd , and can be obtained from for even .
The following theorem shows that the proposed -SDIS is a n-out-of-n sharing scheme that we can recover and from n noise-like shadows , and cannot obtain and from or fewer shadows.
Theorem 1.
The proposed -SDIS is n-out-of-n sharing scheme that the XOR-ed result of n shadow blocks can represent color indices and the data of color palette.
Proof.
We first prove that sharing procedure can successfully generate n shadow blocks . Suppose that a block is composed of 8-bit color index and 1-bit data of color palette, which are obtained from and . By Equation (1), we first randomly generate blocks , and then calculate the temporary block T via . After step (S-4), the Hamming weight distribution of is (see Lemma 1). By Lemma 2, we can obtain from (respectively, ) for odd (respectively, even . Finally, we have n shadow blocks . Process all the blocks, and we can generate n noise-like shadows.
Next, we consider the recovery. As shown in Equation (2), we can recover the original block from . Therefore, we can determine the color index and the data of color palette . After obtaining all blocks, we can recover and . Because of , it is obvious that we cannot recover the original block B via or fewer shadow blocks. □
Let the ratio of average number of black subpixels in a block (i.e., the regions in shadows showing the content of cover image) for Wei et al.’s -SDIS, Yang et al.’s -SDIS, and the proposed -SDIS be . In addition, let the contrasts of binary meaningful shadows for Wei et al.’s -SDIS, Yang et al.’s -SDIS, and the proposed )-SDIS be . The following theorem demonstrates and .
Theorem 2.
The ratio of average numbers of black subpixels in a 9-bit block for Wei et al.’s -SDIS, Yang et al.’s -SDIS, and the proposed -SDIS are where . The contrasts of binary meaningful shadows for Wei et al.’s -SDIS, Yang et al.’s -SDIS, and the proposed -SDIS are , where .
Proof.
Wei et al.’s -SDIS has all blocks on both shadows, and thus . On the other hand, both shadows of Yang et al.’s -SDIS are composed of and blocks half and half. Therefore, we have . For the proposed -SDIS, Step (S-5) implies that Yang et al.’s -SDIS and Wei et al.’s -SDIS are evenly used in the proposed -SDIS. This is because the Hamming weights are odd and even half and half. Therefore, the value of is derived as follows.
It is obvious that with equality for . From these values , we have
The contrast is the difference of blackness for black block and white block. In binary meaningful shadows , we complement the blocks for the corresponding white cover pixels to generate white shadow blocks. Thus, if the number of black subpixels in a black shadow block is , then the he number black subpixels in a white shadow block is . Thus, we have . It is obvious that with equality for . From these values we have . □
An illustrative example gives a quick understanding for the proposed -SDIS.
Example 1.
Share and recover the following information and , where c is the color index and d is the data of color palette, by the proposed -SDIS.
Given , we have the block . By step (S-2), we randomly generate two blocks (say ). Suppose that these two random blocks are and with , and then we obtain the temporary block T via the following equation.
Because of , we should modify any two positions (one is and the other is ) in one block (say ), to reduce from 9 to 7. For example, we may modify as . Finally, we have with , and meanwhile the new block is still a block. Since is odd, we apply Yang et al.’s -SDIS to obtain , which can be determined from Equation (7). Finally, all four shadow blocks are , where are blocks, and is block.
Consider another case . We have the block . From step (S-2), we randomly select two blocks (say ). Suppose that these two random blocks are and , and then we obtain the temporary block T via Equation (8).
Since is even, we apply Wei et al.’s -SDIS to obtain , which can be determined from Equation (9). Finally, all four blocks are , where are blocks, and are blocks.
For recovery, consider the case: . The XOR-ed result is , and thus . For the other case: , the XOR-ed result is . Therefore, we have .
Let be the ratio of average numbers of black subpixels in a 25-bit shadow block for the proposed -SDIS sharing true color image. The following theorem demonstrates , i.e., the meaningful shadows of sharing true color secret image have the better visual quality than those of sharing 256-color secret image.
Theorem 3.
The ratio of average numbers of black subpixels in a 25-bit block for the proposed -SDIS sharing true color image is , where .
Proof.
If the blocks are (respectively, ) blocks, then the first 8 bits in has 6 black subpixels with percentage and 5 black subpixels with percentage (respectively, 5 black subpixels with percentage and 4 black subpixels with percentage). The average number of black pixels for the first 8 bits in is for blocks, and is for blocks. Therefore, the average number of black subpixels in every 8 bits in the first 24 bits of is , as derived below.
Because the 25-th bit in shadow block is always 1, and thus the value of is determined as . The following equation implies .
□
5.2. Security Analysis: The -Colluder Attack
Here, we consider an attack way that participants collude together and want to figure out and . The -colluder attack is a very extreme attack for the proposed -SDIS, because it needs participants jointly providing their shadows for guessing and . We first discuss the -colluder attack on Wei et al.’s -SDIS and Yang et al.’s -SDIS. Suppose that Participant 1 wants to predict and from his own shadow . Because the color palette information is conveyed by the ninth bit of every block on . Therefore, the can be completely obtained from . Even though Participant 1 has the color palette , but he cannot obtain the information about color index. An attacker has probability to figure out the correct color index of block B without any shadow. This value of is a brute-force probability, which tries all possible 256 colors in the color palette. However, for the -colluder attack, Participant 1 has . By cryptanalytic attacks relying on knowing one shadow (the first eight bit of ), Participant 1 may guess the color index. Let the successful probability to recover the block B for Wei et al.’s -SDIS and Yang et al.’s -SDIS be and , respectively, when collecting one shadow. Because both shadow blocks of Wei et al.’s -SDIS are all blocks , obviously is . On the other hand, shadow blocks of Yang et al.’s -SDIS are evenly composed of blocks and blocks. Thus, . Both probabilities and are higher than the brute-force probability . However, these probabilities and are still practically secure for guessing 256 colors.
Let the successful probability to recover the block B for -colluder attack, for the proposed -SDIS, be . In the following theorem, we theoretically prove .
Theorem 4.
The successful probability to recover the block B in the proposed -SDIS for -colluder attack is , where .
Proof.
Suppose that there are shadows (say ) for reconstruction, on which we may guess the type of shadow block in the corresponding position of . The block has block and block with probability and probability, respectively, which are derived below.
If is block (respectively, block), there is (respectively, ) probability to guess the correct color index , which is better than brute-force probability . Thus, is calculated as follows.
□
Since and , we have . About and , the relation is derived as follows.
For , the value of is , and approaches to for large n. In fact, the value of is almost the same as . For this extreme case, the -colluder attack, the security of the proposed -SDIS is close to that of Yang et al.’s -SDIS. By the same argument, for other cases collecting or shadows, the possible combination of collected shadows is more difficult to analyze compared with collecting shadows, and even less than the brute-force probability.
In the proposed -SDIS, the color palette information is conveyed by (the ninth bit in B), but not the ninth bit of the block in . Therefore, the color palette may be obtained from only one shadow for Wei et al.’s -SDIS and Yang et al.’s -SDIS. Even though an attacker has the information, he still cannot obtain the secret image . For the proposed -SDIS, the color palette information in B is securely protected and only can be determined from XOR-ing n blocks . This makes the cryptanalysis is more difficult for the proposed -SDIS. The following theorem demonstrates the successful probability to recover a correct color in for the proposed -SDIS when collecting shadows.
Theorem 5.
The successful probability to recover a correct color in for the proposed -SDIS when collecting shadows is .
Proof.
Each color information in is encapsulated in 24 blocks, which every block should be derived from . If colluders have shadows (say ), for a block B, they have the XOR-ed result , and can guess that the shadow block is block and block with probability and probability, respectively. For block, it implies that we have probability that the bit is the complementary bit in . On the other hand, we have probability that the bit is the complementary bit in for block. Therefore, the average probability of guessing is derived as Note: every block has one-bit color palette information, and a true color is represented by 24-bit , and B color planes. Because colluders can guess the bit with probability, is . □
Therefore, the value is less than , and this implies that the color palette cannot be recovered under -colluder attack.
6. Evaluation and Comparisons
6.1. Experimental Results
Seven experiments (Experiments ) are conducted to evaluate the proposed -SDIS from various aspects: (A) noise-like shadows sharing 256-color image for -SDIS (B) binary meaningful shadows sharing 256-color image for -SDIS (C) color meaningful shadows sharing 256-color image for -SDIS (D) color meaningful shadows sharing true color image for -SDIS (E) binary meaningful shadows and color meaningful shadows for -SDIS (F) binary meaningful shadows and color meaningful shadows for -SDIS (G) color meaningful shadows sharing 256-color image for -SDIS by the approach of enhancing visual quality.
Experiments are the -SDIS. Experiment A has noise-like shadows, and other four experiments are meaningful shadows. Experiments D demonstrates sharing true color secret image. Experiments E and F demonstrate binary and color meaningful shadows for -SDIS and -SDIS, respectively. In Experiment G, we redo Experiment C to enhance the visual quality of color meaningful shadows by using the approach in Figure 6.
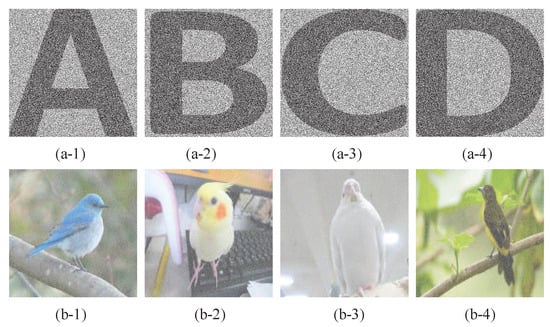
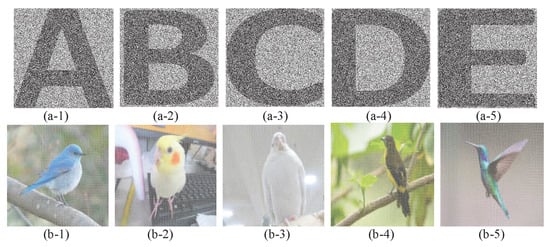
In all experiments, five binary cover images with black-and-white printed texts , and five color cover images with photos of birds are used. In addition, two secret images (Lena: 256-color image), (Kaleidoscope: true color image) are used. All these images (see Figure 7), (see Figure 8), and (see Figure 9) are pixels.

Figure 7.
Five color cover images with photos of birds: (a) (b) (c) (d) (e) .

Figure 8.
Five color cover images with photos of birds: (a) (b) (c) (d) (e) .

Figure 9.
Two secret images: (a) : 256-color Lena (b) : true color Kaleidoscope.
Because shadows may be 9 or 25 times expanded in experiments, for demonstrating all the images in a single page, the shadow images in experiments are not correctly proportional.
Experiment A.
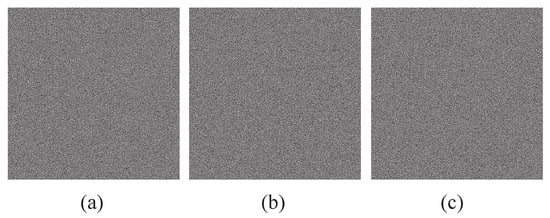
Three noise-like shadows of the proposed -SDIS sharing a 256-color secret image are demonstrated.
The secret image : 256-color Lena in Figure 9a is used to test the proposed -SDIS. Each noise-like shadow has blocks and blocks, which are the same as Yang et al.’s -SDIS. As shown in Figure 10, three noise-like shadows are expanded to pixels. Via recovering procedure, we can recover the original 256-color secret image Lena.

Figure 10.
Noise-like shadows of the proposed -SDIS: (a) (b) (c) .
Experiment B.
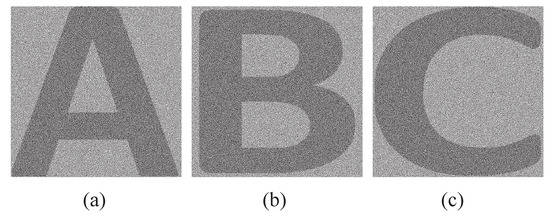
Three binary meaningful shadows of the proposed -SDIS sharing a 256-color secret image are demonstrated.
By revering (respectively, unchanging) the color of subpixels in a block of , and on and in Experiment A to represent the white (respectively, black) color in (A, B, and C in Figure 7a–c). The proposed -SDIS has the contrast (see Theorem 2). It is observed that the printed-texts A, B, and C are revealed indeed on , with the size of pixels (see Figure 11a–c). Consider recovery. We first transfer the block and block to block and block, respectively. Afterwards, via the recovering procedure, we may recover the 256-color secret image Lena.

Figure 11.
Binary meaningful shadows of the proposed -SDIS: (a) (b) (c) .
Experiment C.
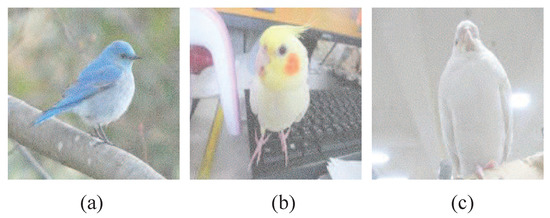
Three color meaningful shadows of the proposed -SDIS sharing a 256-color secret image are demonstrated.
By adopting the color pixels in into black subpixels in blocks , and on and , respectively, we generate three color meaningful shadows with the size of pixels. Each color meaningful shadow has . As shown in Figure 12a–c, it is observed that the images of three photos of birds in Figure 8a–c are revealed on . Consider recovery. We first transfer the color subpixel in every block to s and white subpixel to . Afterwards, via the recovering procedure, we may recover the 256-color secret image Lena.

Figure 12.
Color meaningful shadows of the proposed -SDIS: (a) (b) (c) .
Experiment D.
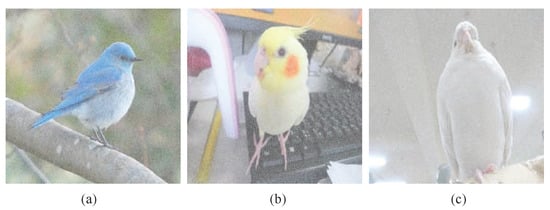
Three color meaningful shadows of the proposed -SDIS sharing a true color secret image are demonstrated.
The secret image : true color Kaleidoscope is used to test the proposed -SDIS sharing a true color secret image. For a secret pixel, we use the information of , and B color planes to form a 25-bit block. By adopting the color pixels in into three 25-subixle shadow blocks, we can generate three color meaningful shadows with the size of pixels (25 times expanded). Each color meaningful shadow has (see Theorem 3) larger than in Experiment C, to show the content of cover image. As shown in Figure 13a–c, it is observed that the images are revealed on . Via the recovering procedure, we may recover the true color secret image Kaleidoscope.

Figure 13.
Color meaningful shadows of the proposed -SDIS sharing a true color secret image: (a) (b) (c) .
Experiment E.
Four binary meaningful shadows and four color meaningful shadows of the proposed -SDIS sharing a 256-color secret image are demonstrated.
Four binary cover images printed-texts in Figure 7a–d, and four color cover images in Figure 8a–d are used. Finally, four binary meaningful shadows , and four color meaningful shadows are illustrated in Figure 14a,b, respectively. All these shadows have the sizes of pixels. Binary meaningful shadows of -SDIS have , and color meaningful shadows of -SDIS have . Both values are greater than (Experiment B) and (Experiment C), respectively.

Figure 14.
Binary snd color meaningful shadows of the proposed: (a) (b) .
Experiment F.
Five binary meaningful shadows and five color meaningful shadows of the proposed -SDIS sharing a 256-color secret image are demonstrated.
Five color cover images printed-texts in Figure 7a–e, and five color cover images in Figure 8a–e are used. Finally, fiver binary meaningful shadows , and five color meaningful shadows are illustrated in Figure 15a,b, respectively. All these shadows have the sizes of pixels. Binary meaningful shadows of -SDIS have , and color meaningful shadows of -SDIS have . Both values are better than those of -SDIS.

Figure 15.
Binary snd color meaningful shadows of the proposed: (a) (b) .
Experiment G.
Redo Experiment C, but use the approach of enhancing visual quality of color meaningful shadows. Three are demonstrated.
In Experiment C, three -pixel color cover images in Figure 8a–c are used. To enhance the visual quality of , we use another three -pixel , which has high resolution. These three images are omitted here for brevity. By using the approach in Figure 6, we use color pixels in into black subpixels in blocks , and on and , respectively to generate three color meaningful shadows with the size of pixels. As shown in Figure 16a–c, it is observed that Figure 16 has better visual quality than Figure 12. However, the photos used in this experiment may not clearly demonstrate the enhancement. Here, we use a cover image, a colorful centered fractal, for testing. Figure 17(a-1,b-1) shows two color meaningful shadows using the original one and new enhancement, respectively. For clear observation, cropped image areas of Figure 17(a-1,b-1) are shown in Figure 17(a-2,b-2). Visual inspection of cropped image areas in Figure 17(a-2,b-2) reveals that the original method spoils some edges and fine details in shadow images. Our enhancement has clear color sharpness, especially the clearness of edges.
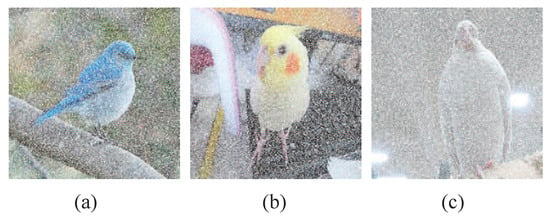
Figure 16.
Color meaningful shadows of -SDIS by the approach of enhancing visual quality: (a) (b) (c) .
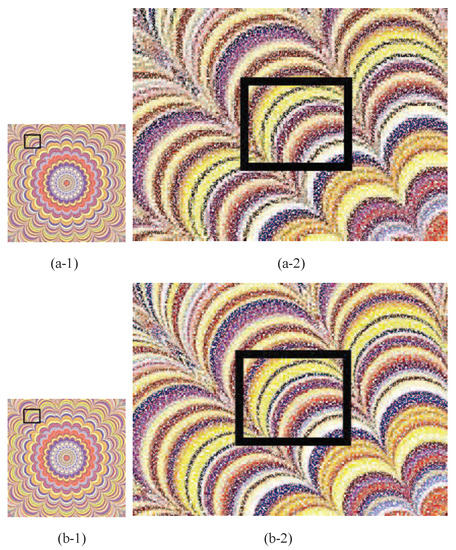
Figure 17.
Color meaningful shadows and enlarged parts of cropped image area for -SDIS: (a) using the original method (b) using the approach of enhancing visual quality.
For fairer comparison, we adopt visual quality assessment, the structural similarity (SSIM) index, and the feature similarity (FSIM) index to compare Figure 17(a-1) and Figure 17(b-1). Let the original image be a colorful centered fractal with the size pixels. According to the image quality assessment from Laboratory for Computational Vision in New York University (please refer to https://www.cns.nyu.edu/~lcv/ssim/#usage), to calculate SSIM and FSIM for color images, it would be better to convert the color image to gray image with the formula , and then calculate its SSIM and FSIM. Finally, SSIM and FSIM of Figure 17(a-1) are and , and SSIM and FSIM of Figure 17(b-1) are and , respectively. These values of SSIM and FSIM demonstrate a consistency with the performance in Figure 17(a-2,b-2).
6.2. Discussion and Comparison
6.2.1. Enhancing
In step (S-2), we first randomly generate blocks . Afterwards, in step (S-5), we evenly use Wei et al.’s -SDIS and Yang et al.’s -SDIS to generate two other shadows , where . Finally, is (see Equation (5)). In fact, we may further enhance by using block instead of block to generate , where block may be or . When using , the approach changes back to the original -SDIS. By this approach, the is enhanced to and for and , as derived in Equations (15) and (16), respectively.
Consider -colluder attack for the case using block with Hamming weight w. The following theorem demonstrates the successful probability to recover the block B under -colluder attack.
Theorem 6.
When using block in the proposed -SDIS, the successful probability to recover the block B for -colluder attack is .
Proof.
Suppose that using block with Hamming weight w in step (S-2). Consider the case that colluders already have shadows (say ) for reconstruction. Based on these shadows, colluders may guess the type of shadow block in the other shadow, The block has block, block and block with probability, probability and probability, respectively, which are derived below. Note: if is Equation (17) is reduced to Equation (12).
There is probability to guess the correct block B when is block, block, and block, respectively. Therefore, the is calculated as follows.
□
The value of is and for and 8. The values are about and , respectively, for large n. Even though these values are larger than for using block in step (S-2), it is still practically secure for applications. This is because our CP information is protected in the XOR-ed result, but not conveyed on in like -SDIS [17,19]. For example, when using as block. If colluders have shadows (say ), for a block B, they have the XOR-ed result , and can guess the shadow block is block with a very high probability for large n (note: for large n). It implies that there is about probability that the bit in B is the complementary bit of . By using the same argument in proof of Theorem 5, for this case, the successful probability to recover a correct color in is . Therefore, we cannot get the correct back. Although colluders may recover the first 8 bits in B, i.e., a color index by complementing the first 8 bits in with probability. This probability of guessing a color index is larger than the brute-force probability . However, colluders do not have the correct , and thus they cannot recover the original . Obviously, it is more difficult to apply -colluder attack on using as block, because is . This is why we claim that using block is still practically secure for applications.
To demonstrate the above phenomenon, we use as block in the proposed -SDIS. Five color meaning shadows using color cover images in Figure 8a–e are illustrated in Figure 18a, where the approach of enhancing visual quality in Section 4.3 is also adopted. Figure 18b are the 256-color (Lena), and its corresponding . The recovered 256-color secret image and the color palette are shown in Figure 18c. It is observed that these five color meaning shadows in Figure 18a have high resolutions with for , which have better visual qualities than those in Figure 15b. From, Figure 18c, there is not any secret information of and leaked for -colluder attack.

Figure 18.
The proposed -SDIS using block (a) five color meaningful shadows (b) 256-color and its corresponding (c) the recovered 256-color and color palette under -colluder attack.
6.2.2. Comparison
We extend -SDIS to the proposed -SDIS. Because the percentage of block is greater than , the resolution of binary and color meaningful shadows are enhanced. Note: Yang et al.’s -SDIS uses block and block half and half, while Wei et al.’s -SDIS only uses blocks. On the other hands, Wei et al.’s -SDIS has the incorrect assignment of color palette data for the color index 255. This problem comes from from all-1 9-bit vector. In [19], Yang et al. adopted a complicated approach using partitioned sets to address this problem. In the proposed -SDIS, the number of shadows of -SDIS is more than two, i.e., . Thus, we can easily adopt a simple approach by reducing to in step (S-4) via modifying any one shadow block to solve this problem. Meantime, as described in Section 5.1, we may enhance and simultaneously retain the practical security by using block.
As shown in Table 2, a complete comparison is given among Wei et al.’s -SDIS, Yang et al.’s -SDIS, and the proposed -SDIS. The comparison includes the structure of block, percentages of blocks, the region in color meaningful shadows revealing cover image, the contrast of binary meaningful shadows, enhancing , the embedding of color palette data, where to embed color palette data, enhancing visual quality of color meaningful shadows, encoding/decoding complexity, and the security. About the security, although the successful probability to recover B under -colluder attack for large n is larger than and . This value is still practical secure for practical application. Besides, the of the proposed -SDIS cannot be obtained under -colluder attack, but the of -SDIS can be obtained from only one shadow. Based on this observation, the proposed -SDIS is much securer than -SDIS.

Table 2.
Comparison of Three SDIS Schemes.
7. Conclusions
In this paper, we discussed the general -SDIS, which can be applied to any . The proposed -SDIS is skilfully implemented on basis of previous -SDIS. Our main contribution is theoretically to prove the proposed -SDIS being able to resist colluder attack. Meanwhile, the contrast of binary meaningful shadow and the region in color shadows revealing cover image are both enhanced. The main weakness of Wei et al.’s -SDIS is the incorrect assignment of color palette data for some color indices, and this is tackled by using partitioned sets in Yang et al.’s -SDIS. In the proposed -SDIS, because of the number of shadows more than two, i.e., , a simple approach reducing Hamming weigh of a temporary block can be adopted to easily solve this weakness. Since the proposed -SDIS is based on color palette and resistant to -colluder attack, and also enhances the visual quality of meaningful shadows, it is suitable for modern visual communication applications where features such as secure transmission, storage sensitive, and high-quality image reconstruction are required.
Author Contributions
Designing scheme, writing—original draft preparation, C.-N.Y.; security analysis, Q.-D.S.; editing and responding to reviewer, Y.-X.L.; experiment, C.-M.W.
Funding
Ministry of Science and Technology, under Grant MOST 107-2221-E-259-007, 108-2221-E-259-009-MY2; Natural Science Foundation of China under Grant No. 61502384,61571360,61872289.
Conflicts of Interest
The authors declare there is no conflicts of interest regarding the publication of this paper.
References
- Naor, M.; Shamir, A. Visual cryptography. In Advances in Cryptology-EUROCRYPT’94; LNCS 950; Springer: Berlin/Heidelberg, Germany, 1995; pp. 1–12. [Google Scholar]
- Shyu, S.J.; Jiang, H.W. General constructions for threshold multiple-secret visual cryptography Schemes. IEEE Trans. Inf. Forensics Secur. 2013, 8, 733–743. [Google Scholar] [CrossRef]
- Yang, C.N.; Wu, C.C.; Lin, Y.C. k out of n region-based progressive visual cryptography. IEEE Trans. Circuits Syst. Video Technol. 2017. [Google Scholar] [CrossRef]
- Karolin, M.; Meyyappan, T.; Thamarai, S.M. Encryption and decryption of color images using visual cryptography. Int. J. Pure Appl. Math. 2018, 118, 277–281. [Google Scholar]
- Kansal, I.; Kasana, S.S. Sharing two true colour images using (3,3)-extended visual cryptography technique. J. Mod. Opt. 2018, 65, 1949–1959. [Google Scholar]
- Yang, C.N.; Wu, F.H.; Peng, S.L. Enhancing multi-factor cheating prevention in visual cryptography based minimum (k, n)-connected graph. J. Vis. Commun. Image Represent. 2018, 55, 660–676. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. Assoc. Comput. Mach. 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Thien, C.C.; Lin, J.C. Secret image sharing. Comput. Graph. 2002, 26, 765–770. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N.; Wu, C.M.; Sun, Q.D.; Bi, W. Threshold changeable secret image sharing scheme based on interpolation polynomial. Multimed. Tools Appl. 2019, 78, 18653–18667. [Google Scholar] [CrossRef]
- Yang, C.N.; Chen, T.S.; Yu, K.H.; Wang, C.C. Improvements of image sharing with steganography and authentication. J. Syst. Softw. 2007, 80, 1070–1076. [Google Scholar] [CrossRef]
- Pakniat, N.; Noroozi, M.; Eslami, Z. Secret image sharing scheme with hierarchical threshold access structure. J. Vis. Commun. Image Represent. 2014, 25, 1093–1101. [Google Scholar] [CrossRef]
- Liu, Y.X.; Zhang, Y.Z.; Yang, C.N. Reducing file size and time complexity in secret sharing based document protection. Math. Biosci. Eng. 2019, 16, 4802–4817. [Google Scholar] [CrossRef]
- Kanso, A.; Ghebleh, M. An efficient lossless secret sharing scheme for medical images. J. Vis. Commun. Image Represent. 2018, 56, 245–255. [Google Scholar] [CrossRef]
- Li, P.; Liu, Z.; Yang, C.N. A construction method of (t, k, n)-essential secret image sharing scheme. Signal Process. Image Commun. 2018, 65, 210–220. [Google Scholar] [CrossRef]
- Wu, X.; Yang, C.N.; Zhuang, Y.T.; Hsu, S.C. Improving recovered image quality in secret Image sharing by simple modular arithmetic. Signal Process. Image Commun. 2018, 66, 42–49. [Google Scholar] [CrossRef]
- Lukac, R.; Plataniotis, K.N. Bit-level based secret sharing for image encryption. Pattern Recognit. 2005, 38, 767–772. [Google Scholar] [CrossRef]
- Wei, S.C.; Hou, Y.C.; Lu, Y.C. A technique for sharing a digital image. Comput. Stand. Interfaces 2015, 40, 53–61. [Google Scholar] [CrossRef]
- Yang, C.N.; Chen, C.H.; Cai, S.R. Enhanced Boolean-based multi secret image sharing scheme. J. Syst. Softw. 2016, 116, 22–34. [Google Scholar] [CrossRef]
- Yang, C.N.; Wu, C.H.; Yeh, Z.X.; Wang, D.; Kim, C. A new sharing digital image scheme with clearer shadow images. Comput. Stand. Interfaces 2017, 51, 118–131. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N.; Wu, S.Y.; Chou, Y.S. Progressive (k, n) secret image sharing schemes based on Boolean operations and covering codes. Signal Process. Image Commun. 2018, 66, 77–86. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).