1. Introduction
As a promising alternative complementary to current radio frequency (RF) wireless communications, visible light communication (VLC) can simultaneously provide illumination and data communication by exploiting the existing lighting infrastructure, and it has been regarded as a potential technology for indoor 5G communications, Internet of Things (IoTs), and device-to-device communications [
1].
Due to the broadcasting nature, VLC is especially applicable for massive connectivity, supporting multiple users to access the same wireless resource. Non-orthogonal multiple access (NOMA) as a novel multiple access protocol where multiple users are multiplexed in the power domain via superposition coding at the transmitter and de-multiplexed by successive interference cancellation (SIC) at the receiver is particularly suitable for VLC systems. The throughput [
2], coverage probability [
3], reliability [
4], spectral-energy efficiency [
5], and users’ fairness [
6] of NOMA VLC systems have been well investigated. Meanwhile, the security problem of NOMA VLC systems has become increasingly important [
7]. If eavesdroppers appear at the same region illuminated by light-emitting diodes (LEDs) as the NOMA legitimate users, the useful information is inevitably susceptible to eavesdropping. Physical-layer security [
8] has emerged as a promising approach to protect information from eavesdropping and has drawn much attention in recent years of those who aim to achieve secure transmission at the physical layer.
With the development of multi-antenna technology, optical multiple-input multiple-output (MIMO) or multiple-input single-output (MISO) VLC systems can greatly enhance physical-layer security by fully exploiting the spatial degree of freedom. Meanwhile, to satisfy the requirement of massive connectivity for the next wireless communication, there is an urgent need for multiple users to access the communication system. However, existing work on the security problem of MISO (or MIMO) VLC systems focused mainly on a single legitimate user suffering security threats from one or multiple eavesdroppers [
9,
10]. As to the existing MISO-VLC systems with multi-user [
11,
12], although precoding has been used to improve secrecy performance, multiple users access the system in the conventional orthogonal multiple access (OMA) scheme, which greatly limits the accessed number of users. Applying NOMA to a multi-user MISO VLC system can not only take advantage of the potential of NOMA to really support multiple users, but can also enhance the physical-layer security via multi-antenna technology, such as beamforming/precoding, artificial noise and transmit antenna selection technology, etc. However, thus far, the secrecy performance of a MISO-NOMA VLC system has not yet been studied. It is necessary to investigate the physical layer security of MISO-NOMA VLC systems. This is due to the fact that: (1) to effectively support massive connectivity, which is important for ensuring the forthcoming 5G network to support the IoTs functionalities, it is necessary to study on NOMA VLC systems; (2) in practical application, multiple LEDs are often deployed to meet the lighting requirements. Multiple LEDs assignment enables the MISO or MIMO transmission scheme and also constructs a multi-antenna transmitting system. To meet the practical LEDs assignment and further improve the physical-layer security performance of multiple NOMA users, multi-antenna technology with multiple LEDs at the transmitter could be adopted.
In this paper, we investigate the physical-layer security of a two-user MISO-NOMA VLC system, where multiple LEDs serve two legitimate users via downlink NOMA in the presence of a passive eavesdropper. All the LEDs are utilized to transmit signals with equal power. Both the legitimate users and the eavesdropper employ a photodiode (PD) receiver to detect and receive the optical signal. Selection combination technology is utilized at the legitimate users and the eavesdropper. The optical signal radiated from LED to the user with weak channel gain (called a weak user) should be first decoded by the user with strong channel gain (called a strong user) so as to enable SIC at the strong user. Therefore, the secrecy performance of the weak user is conditioned on the fact that the strong user does not release any information about the weak user [
13]. Hence, the physical-layer security of the strong user in a two-user MISO-NOMA VLC system is analyzed and measured by the secrecy outage probability (SOP) performance criteria. To demonstrate the superiority of the MISO-NOMA VLC system over the single-input single-output (SISO) NOMA VLC system, numerical simulations are made based on typical parameters of indoor LED transmitters and PD receivers, and results show that the SOP performance of the strong user in the MISO-NOMA VLC system is superior to that in the SISO-NOMA VLC system. In addition, the SOP of the strong user depends highly on the room arrangement, the difference between the legitimate channel and the eavesdropper channel, and the properties of the LEDs and the PD.
It should be noted that in the proposed two-user MISO-NOMA VLC system, each of the legitimate users and the eavesdropper is with a single PD receiver, which is the most common case until now. As to a MIMO-NOMA VLC system where the legitimate users and/or the eavesdropper are with multiple PD receivers, it is necessary to take more factors into consideration, such as the geometric layout of the PD receivers and the complicated channel estimation [
14,
15] for the MIMO case, which would increase the difficulty of the system implementation and make the computational complexity high. However, MIMO technique is an efficient way to increase system capacity and extend system coverage, as will be studied in our future work.
The rest of this paper is organized as follows. In
Section 2, the MISO-NOMA VLC system model is proposed, and the statistical characteristics of the intensity modulation direct detection (IM/DD) channel and the signal-to-noise ratio (SNR) is also investigated. In
Section 3, the physical-layer security performance of the strong NOMA user is analyzed. Numerical results are presented in
Section 4 to verify the theoretical analysis. Finally, conclusions are given in
Section 5.
2. System Model
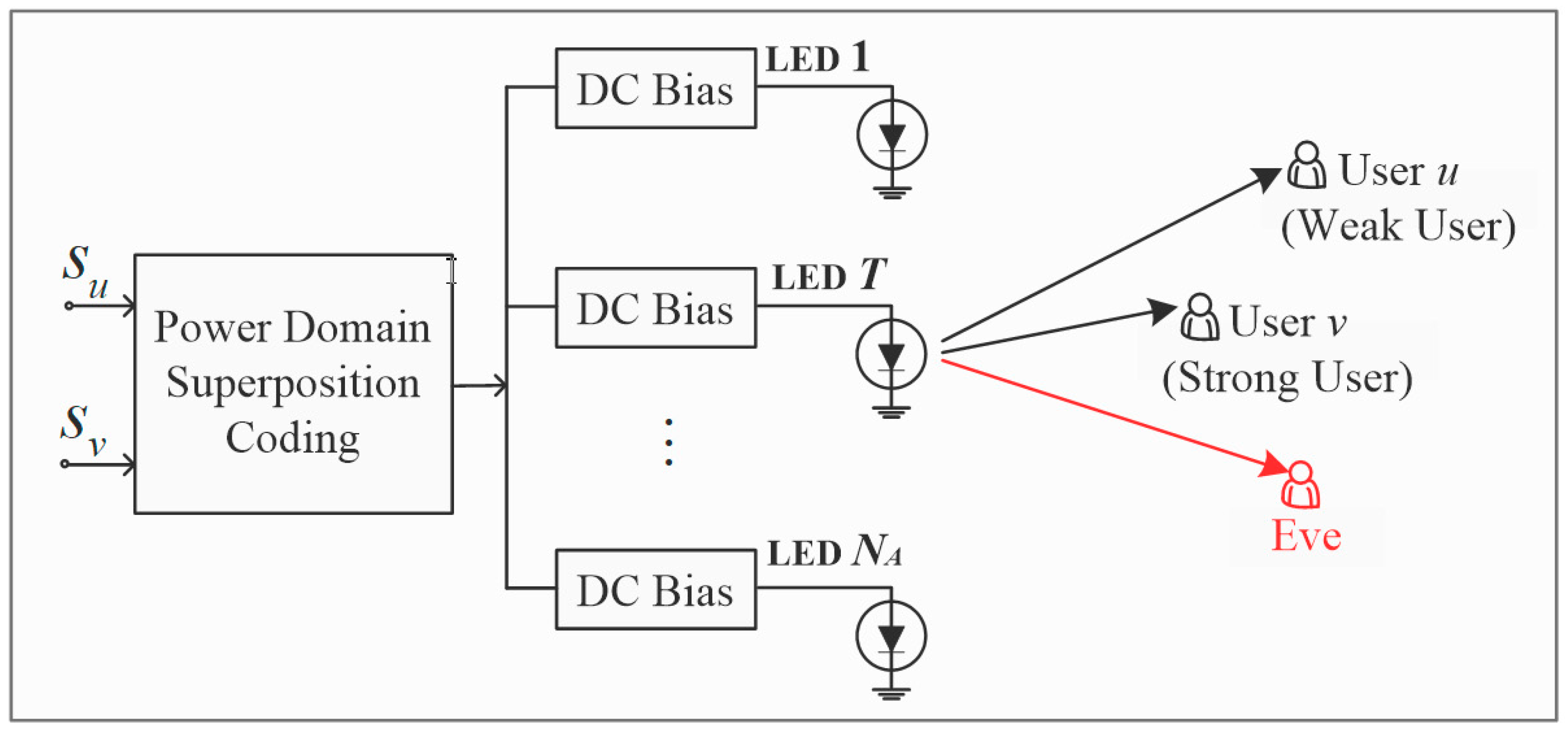
The MISO-NOMA VLC system is shown in
Figure 1, where
NA LEDs serves user
u and user
v via downlink NOMA in the presence of a passive Eve (eavesdropper). Each of the legitimate users and Eve is with a PD receiver (Series 5T, Centronic Silicon PD, Croydon, London, UK). All the PD receivers are within the illuminating region of LED (BXRA-56C5300-H-00, Bridgelux LED, Fremont, CA, USA), and selection combination is utilized at the legitimate users and Eve. Since the secrecy performance of the weak user is conditioned on the fact that the strong user does not release any information about the weak user, we put emphasis on the physical-layer security of the strong user.
At the transmitting terminal, the signals of the two NOMA legitimate users are first superposed in power in an electrical domain. Then, a direct current (DC) bias is added to the superposition coding signal to satisfy a certain requirement of illumination before the electrical-to-optical conversion of LED. Hence, the signal from the T-th LED, T ∈{1, …, NA}, can be expressed as , where is the DC bias, which is utilized to set the average radiated optical power of LED and adjust the indoor illumination level; is the total electrical power of the signal in the electrical domain, and each LED transmits signal with equal power of ; represents the signal of the i-th legitimate user, , which is assumed to be with zero mean and ; and is the power allocation coefficient of the T-th LED for the i-th legitimate user. Assuming the fixed power allocation scheme is used, then and remains constant for each LED and is respectively expressed as and below for simplicity. According to the NOMA principle, more power will be allocated to the weak user, while less power is allocated to the strong user for any LED, i.e., . Since there exist only two NOMA users in the system, the coefficients should also satisfy and , . Due to the expectation , the superposition coding signal does not contribute to the average optical power and therefore does not influence the illumination level. Due to the limited dynamic range and the linear electrical-to-optical conversion characteristics of LED, constraint should also be satisfied, thus the signal at the input of the IM/DD channel can be a non-negative real signal.
At the receiving terminal, the arrived optical intensity signal is first converted into a current signal via photo-electric conversion of the PD receiver, and then the constant DC offset is removed, and noise is added in the electrical domain. For the NOMA legitimate user
i, the received signal can be given by
, where
is the DC gain of the IM/DD channel between the
T-th LED and the user
i;
is the additive white Gaussian noise of the channel and is assumed to be with zero mean and variance
. Without loss of generality, it is assumed that the channel power gain satisfies
, where
,
is respectively the channel power gain of the weak user and the strong user. According to the NOMA principle, the strong user can perform SIC while the weak user cannot. Therefore, in the two-user MISO-NOMA VLC system, the peak SNR [
10] in the channel from the
T-th LED to the strong user
v can be given by:
While the peak signal-to-interference-plus-noise ratio (SINR) in the channel from the
T-th LED to the weak user
u is:
where
is defined as the transmission SNR of the LED transmitter to the NOMA legitimate user.
Eve is assumed to be aware of the decoding orders and power allocation coefficients, and by adopting the multi-user detection technique, it can distinguish the multi-user signal and subtract the interference generated by the superposed signals from each other. This is a common assumption in analyzing the secrecy performance of the NOMA system [
16,
17]. The SNR for Eve to detect the message of user
can be given by
, where
and
is the noise variance of the eavesdropper channel.
2.1. Statistical Characteristics of the IM/DD Channel
In the IM/DD channel, information is carried by the optical intensity. The light from the LED is successively concentrated and filtered by an optical concentrator and a filter in front of the PD receiver. In general, the received signals at the PD receiver include both the line-of-sight (LOS) and the diffuse component. However, it has been demonstrated by Zeng et al. [
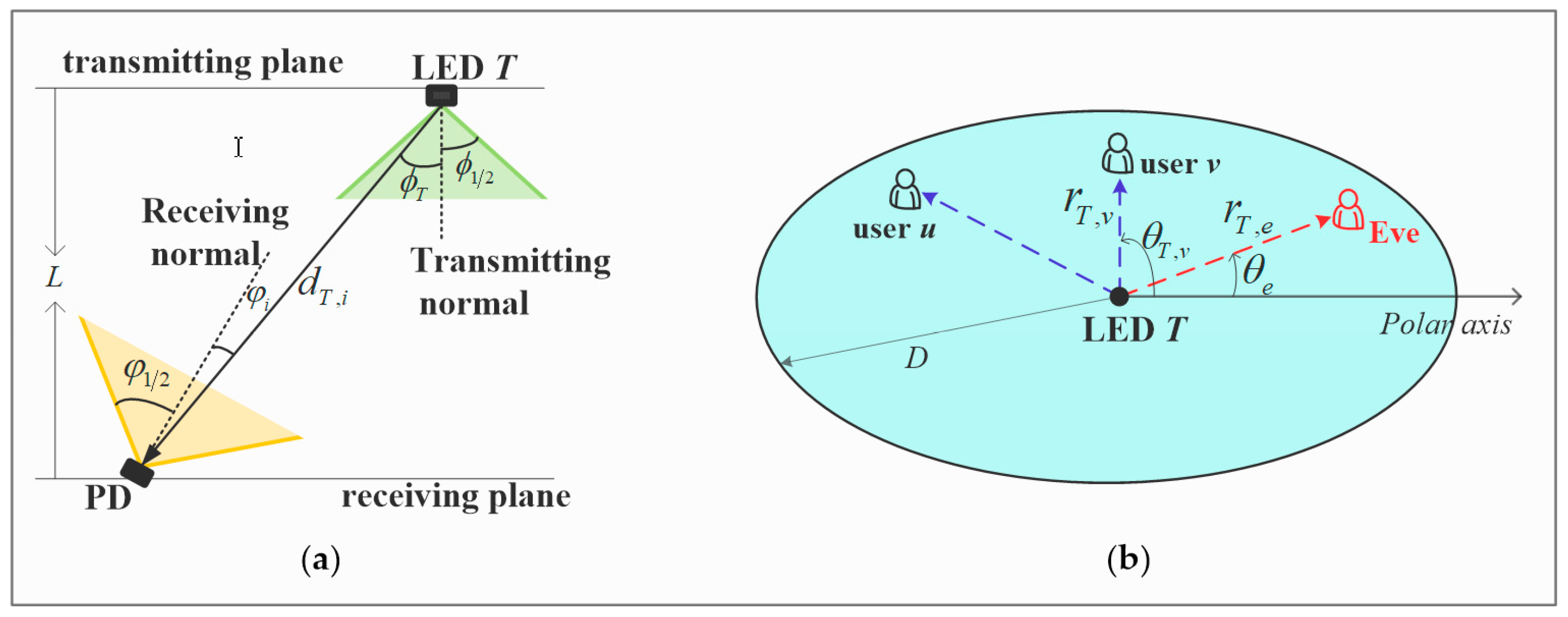
18] that even the strongest diffuse component is at least 7 dB lower than the weakest LOS component. Hence, only the LOS path is taken into account in this paper. The cross-section and the top view of the IM/DD channel are shown in
Figure 2.
If the LED works in a generalized Lambertian radiation pattern, the DC gain of the IM/DD channel from the T-th LED to user i can be described as , where is the angle of irradiance with respect to the transmitting normal of the T-th LED plane; is the angle of incidence with respect to the receiving normal of the i-th PD receiver plane; is the field of view (FOV) of the PD receiver; is a rectangular function and is equal to 1 only if , and the FOV of both the legitimate users and Eve is assumed to be wide enough to receive signal from LED; dT,i is the transmission distance between the T-th LED and the i-th PD receiver; is the order of Lambertian radiation, and ; is the semi-angle at half illuminance of the LED; is the optical concentrator gain and , where is the refractive index of the optical concentrator utilized at the PD receiver front-end and is the optical filter coefficient; S and η are the effective physical detecting area and the responsivity of the PD receiver, respectively.
For simplicity, it is assumed that
and the PD receiver has strong adaptive adjustment ability, which is easy to implement in practical application, since various sensors such as the gyroscope sensor, the accelerometer sensor, and the electronic compass sensor are embedded in people’s hand phone, and then the incidence angle can be adjusted to be zero [
19]. The two-dimensional illuminated region of the
T-th LED on the PD receiver plane is assumed to be a circle with a radius of
D, and the projection of the
T-th LED on the PD receiver plane is located at the center, then we can get
, where
L is the vertical distance between the LED plane and the PD plane in three-dimensional space, and
is the distance between the
T-th LED projection and user
i, as shown in
Figure 2b. We can also get
from
Figure 2a. Therefore, the channel power gain of the channel from the
T-th LED to user
i can be written as
, where
is often a constant.
Conditioned on the fact that the NOMA legitimate users
are uniformly located in this disc, the probability density function (PDF) of
is given by
. Utilizing the method of calculating the function of random variables, the PDF of the unordered channel power gain can be given by:
and the cumulative distribution function (CDF) of the unordered channel power gain can be given by:
where
and
.
Adopting order statistics [
20], the CDF of the ordered channel power gain for the two-user MISO-NOMA VLC system can be given by:
2.2. Statistical Characteristic of the SNR
With the statistical characteristic of the channel, the CDF of the SNR of the strong user
v can be given by:
and the CDF of the SINR of the weak user
u can be given by:
where
.
Since the channel power gain of the eavesdropper channel is
where
is the distance between the
T-th LED projection on the PD plane and Eve, the CDF of the SNR for Eve to detect the message of user
i is given by
, and the PDF of the SNR for Eve to detect the message of user
i is given by:
where
.
With these statistical characteristics known, it is suitable to use SOP to measure the secrecy performance. A secrecy outage event occurs when the secrecy rate of user k (k ∈{u, v}) is lower than the target rate, which can be written as , where is the probability of the occurrence of an event ; is the secrecy rate of user k and is given by , where and are respectively the achievable rate of the legitimate user and the eavesdropper, and [x]+ = max{x, 0}; Rth is the predefined target rate.
3. Secrecy Performance Analysis
The selection combination strategy is utilized at the PD receiver of the legitimate user and Eve. Then, the CDF of the SNR of the strong user
v is given by:
and the CDF of the SNR of the weak user
u is given by:
and the CDF of the SNR for Eve to detect the message of user
i,
i ∈{
u,
v} is given by:
and the PDF of the SNR for Eve to detect the message of user
i,
i ∈{
u,
v} is given by:
For the MISO-NOMA VLC system, where two NOMA users are in the presence of a single eavesdropper, all LEDs are utilized to transmit signals with equal power, and the selection combination scheme is employed at the PD receiver for both the NOMA legitimate users and the eavesdropper. Then, the SOP of the strong user in the system can be given by:
Substituting (9) and (12) into (13), we get the SOP of the strong user, which is given by:
where
. First, utilizing the power series expansion formula in [
21] [Equation (1.110)] to expand
, then keeping the first two terms and neglecting the higher order terms, we get:
where
4. Numerical Results
In this section, we present insightful numerical results to disclose the SOP performance of the strong NOMA user.
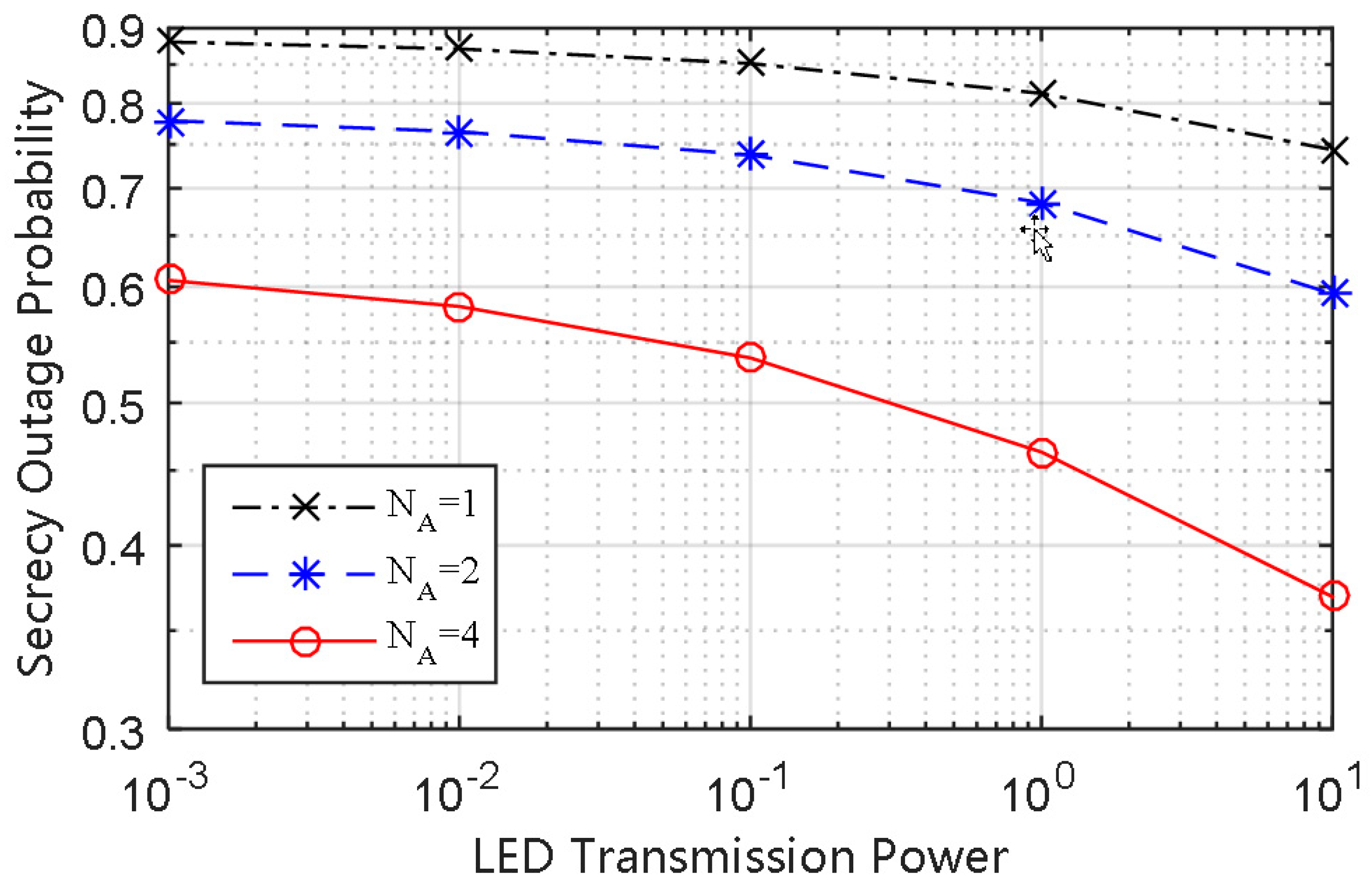
The SOP performance of the strong user versus a different number of LEDs is plotted in
Figure 3. It can be seen that the SOP performance of the MISO-NOMA VLC system (
NA > 1) is superior to that of the SISO-NOMA VLC system (
NA = 1). The SOP in the case of
NA = 1 is consistent with the result of [
7], where only a single LED is used, and multi-antenna technology has not been adopted.
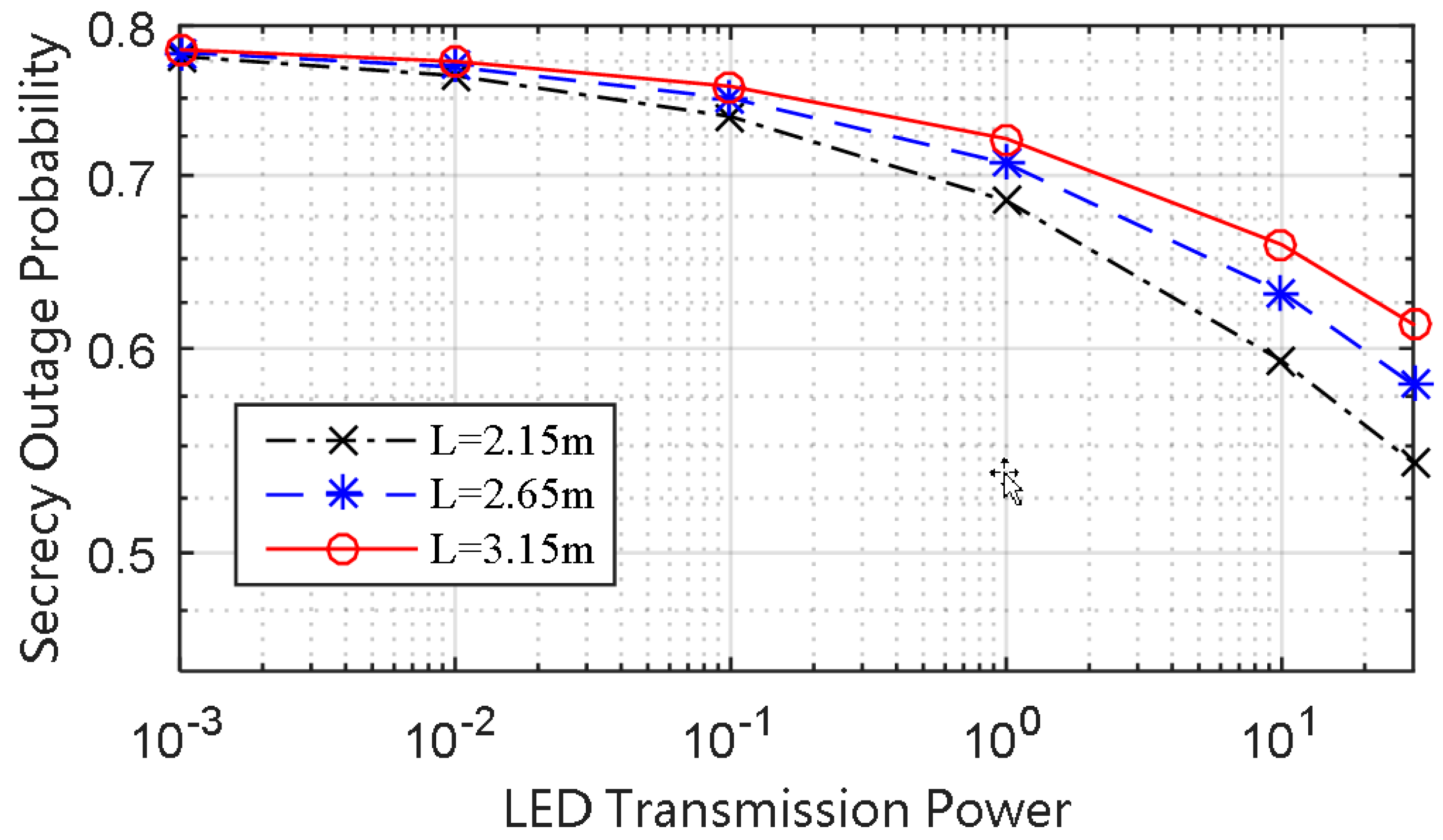
It can be seen from
Figure 4 that reducing the distance from the LED transmitting plane to the PD receiving plane can reduce the SOP, and this is due to the fact that the condition of the main channel gets better at a shorter relative distance between the LED transmitting plane to the PD receiving plane. Thus, we come to the conclusion that room arrangement has great influence on the secrecy performance with the location of the receiving plane remaining unchanged.
The SOP performance of the strong user versus different physical detecting areas of PD is plotted in
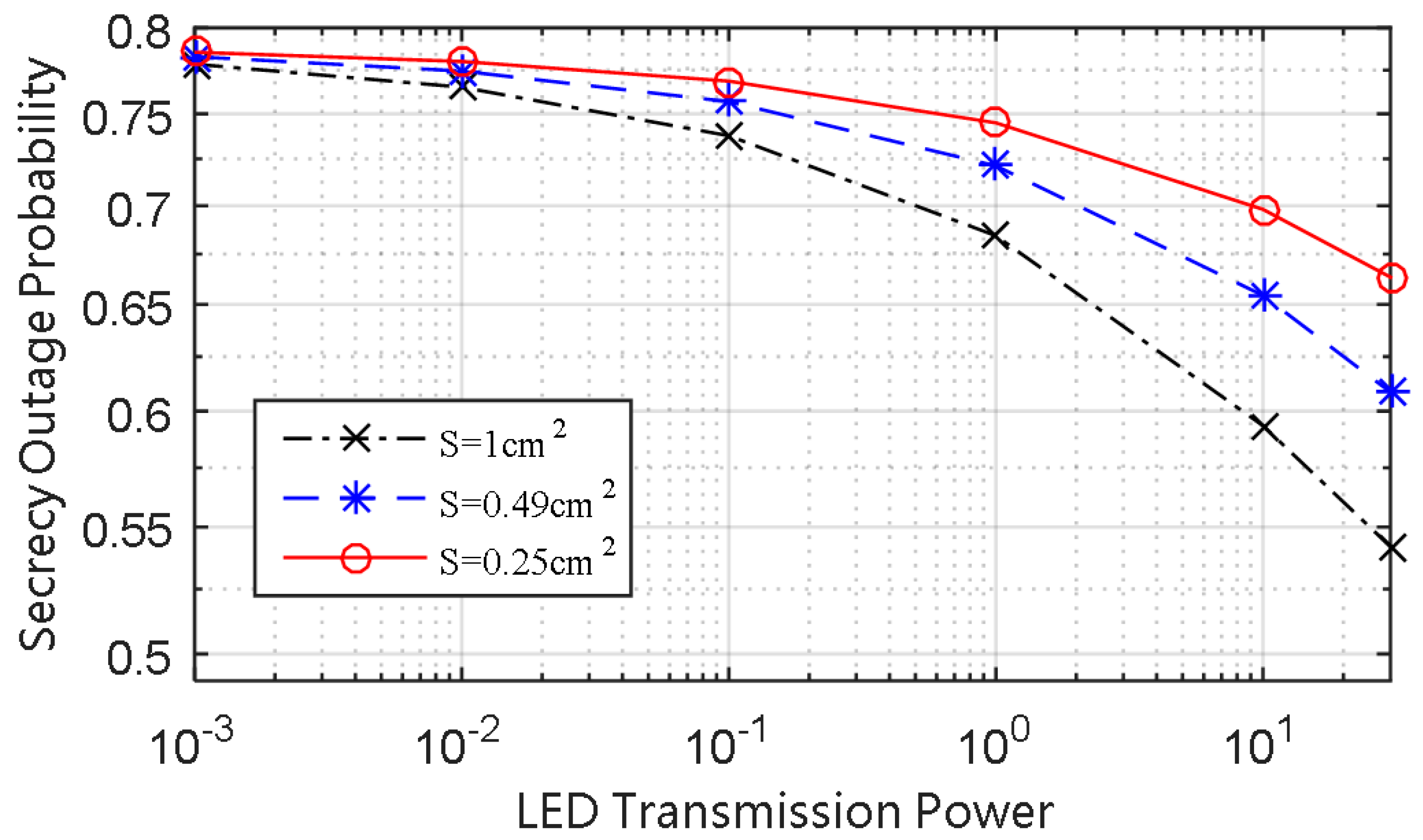
Figure 5, and we can see that enlarging the physical detecting area of PD can reduce the SOP. It can be seen from
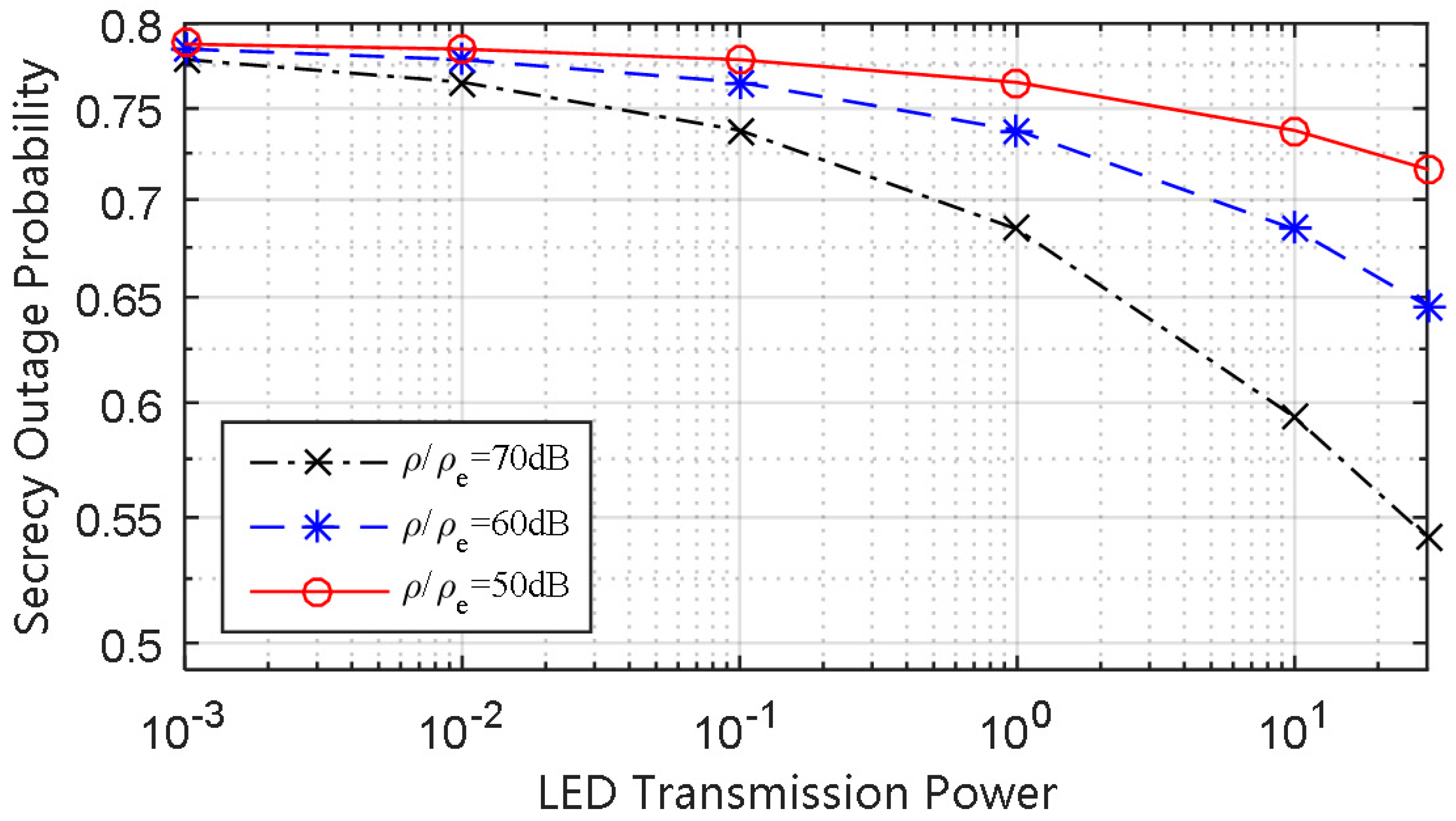
Figure 6 that when the LED transmission power is given, increasing the ratio of
to
can make the SOP of the strong user decrease. This is because the channel difference is enlarged between the strong legitimate channel and the eavesdropper channel with the increase of the ratio. Hence, in practical application, if the strong user could be far enough from the eavesdropper, the SOP of the strong user would remain at a moderate level.
Extending the approaches of the paper to a MIMO-NOMA VLC system with multiple LEDs transmitting and multiple PDs receiving would be of interest as a future direction. For a MIMO-NOMA VLC system, in addition to the above mentioned factors, how the geometric layout of the PD receivers, such as the respective orientation and the relative distance from each other, affects the security performance of the system should also be taken into account. Additionally, the complexity of various channel estimation algorithms for the MIMO case, such as the zero forcing, the least mean square, and the recursive least square algorithm, should also be compared and analyzed.