Safety Analysis of AADL Models for Grid Cyber-Physical Systems via Model Checking of Stochastic Games
Abstract
:1. Introduction
2. Preliminaries
2.1. AADL
2.2. Model Checking of Stochastic Multi-Player Games
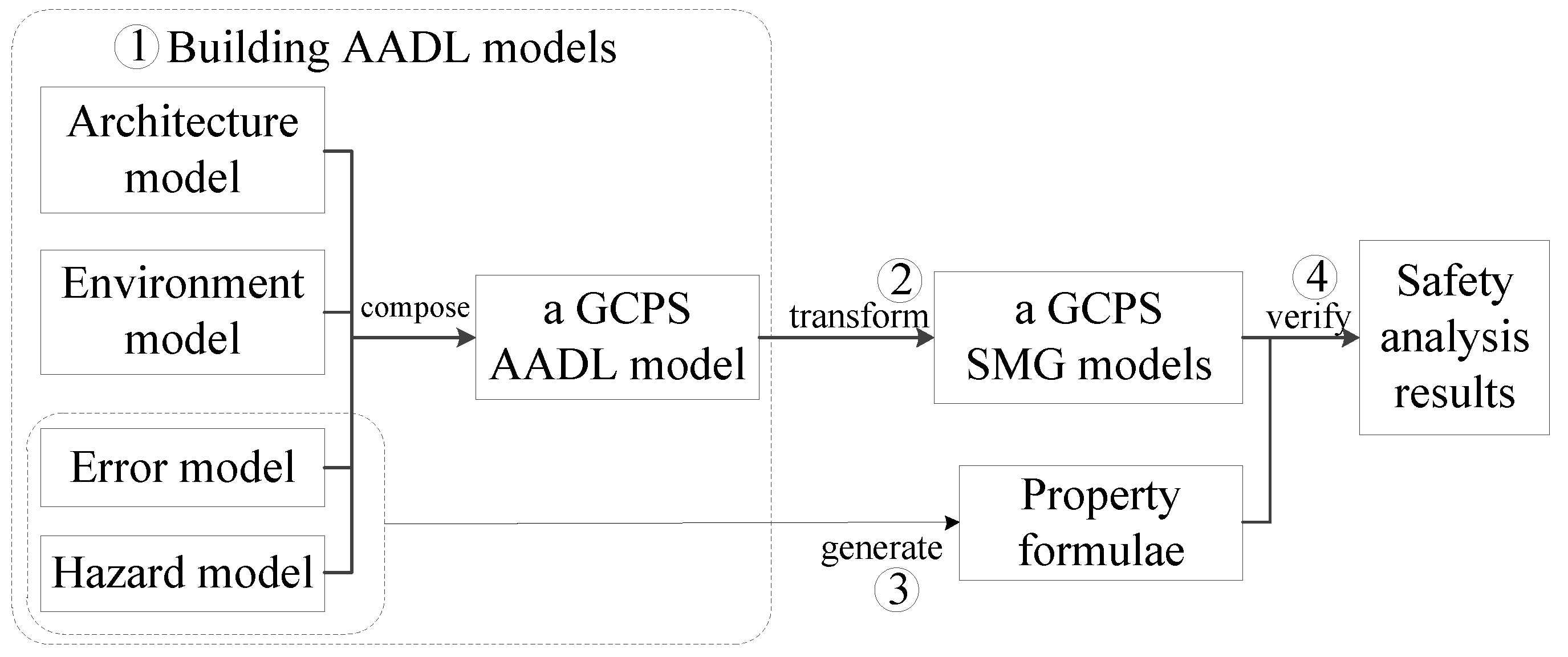
3. Approach
3.1. Building AADL Models for GCPSs
3.2. Transforming AADL Models to SMG Models
- is the set of players formed by a GCPS and its environment.
- is the set of states, where and are sets of states owned by the system and the environment players, respectively, and .
- is the set of actions, where and are sets of actions controlled by the system and the environment players, respectively. In this paper, for all commands, actions are and .
- is a (partial) transition function based on error transitions, hazard transitions, error propagations and hazard propagations.
- is a set of all the predicates that are built over state variables including error states and hazards.
- is a labelling function for hazard sources.
3.3. Generating Property Formulae
3.4. Verifying Property Formulae for Safety Analysis
4. Model Transformation
4.1. Formalization of AADL Models
4.1.1. Basic Elements of an AADL Model
- , where: S is a finite set of error states; is an initial error state; is a finite set of atomic propositions built over error states.
- , where: A is a finite set of actions based on error events in the triggered condition; For a probabilistic error transition function , is established based on probabilities of error events.
- , where: S is a finite set of hazards; is a finite set of atomic propositions built over hazards.
- A is a finite set of actions based on hazard triggers in the triggered condition; is a probabilistic hazard transition function and is established based on probabilities of hazard triggers;
- , where: S is a finite set of hazard sources; is a finite set of atomic propositions built over hazard sources; is a labelling function.
4.1.2. Other Five Constituent Parts of an AADL Model
4.2. Model Transformation Rules
4.2.1. Basic Rules
- , where is a set of error states in a component, and is a local variable. The value range of this variable is corresponding to the number of error states. Each value represents an error state and 0 is for an initial error state.
- , where is a set of error events, and is a set of probability values for transitions in commands. Each probability value is defined as a double constant.
- , where is a set of hazards in a component, and is equal to of the same component. The value range of is added with the the number of hazards. Each added value represents a hazard.
- , where is a set of hazard triggers, and is a set of probability values for transitions in commands. Each probability value is defined as a double constant.
- , where is a set of hazard sources, and is a set of formulae. Each formula represents a variable with the value of the corresponding state of an error state or a probability value of an error event.
4.2.2. Rules for Error Propagations
- 1.
- For , is a corresponding command of . The source error state and the triggered condition of is encoded as the guard. If error events are included in the triggered condition, they are transformed to a probability value for a transition of the command. The outgoing propagation point in the destination of is encoded as a local variable (0 denotes no error, 1 denotes an error). The value 1 is assigned to this variable as an update of a transition for the command. This variable with value 1 will be used as the triggered condition by other components.
- 2.
- If the triggered condition of does not contain incoming propagation points, is better than . is the value of the state variable that is corresponding to the source error state of . The probability values of error events in the triggered condition is added to . The variable corresponding to the source error state will be used as the triggered condition by other components.
4.2.3. Rules for Error Transitions and Hazard Transitions
- 1.
- If is not related to the environment component, the source error state and triggered condition of are transformed to the guard, the destination error state is transformed to a transition t, and error events are transformed to a probability for the transition t. If there are no error events in an error transition, the probability is 1. If there are outgoing propagation points, their corresponding variables should be recovered in the recovered error transition.
- 2.
- Additionally, if is an error transition specifying the occurrence of interference in the environment component, the action of the command is disturb which will synchronize with the affected error transitions in GCPSs.
- 3.
- Moreover, if is an error transition in a component of a GCPS and it is affected by the incoming propagation point from the environment, the action of the command is disturb which will synchronize with the error transitions in the environment. This action is transformed from the error propagation between the environment and a component of a GCPS. If a component does not has error transitions caused by the environment, a command from true to true with the action disturb should be added to this component.
4.2.4. Rules for Logical Operators and Primitives
4.2.5. Rules for Composite Error Behaviors
4.2.6. Rules for Hazard Propagations
4.3. Completeness and Consistency of Model Transformation Rules
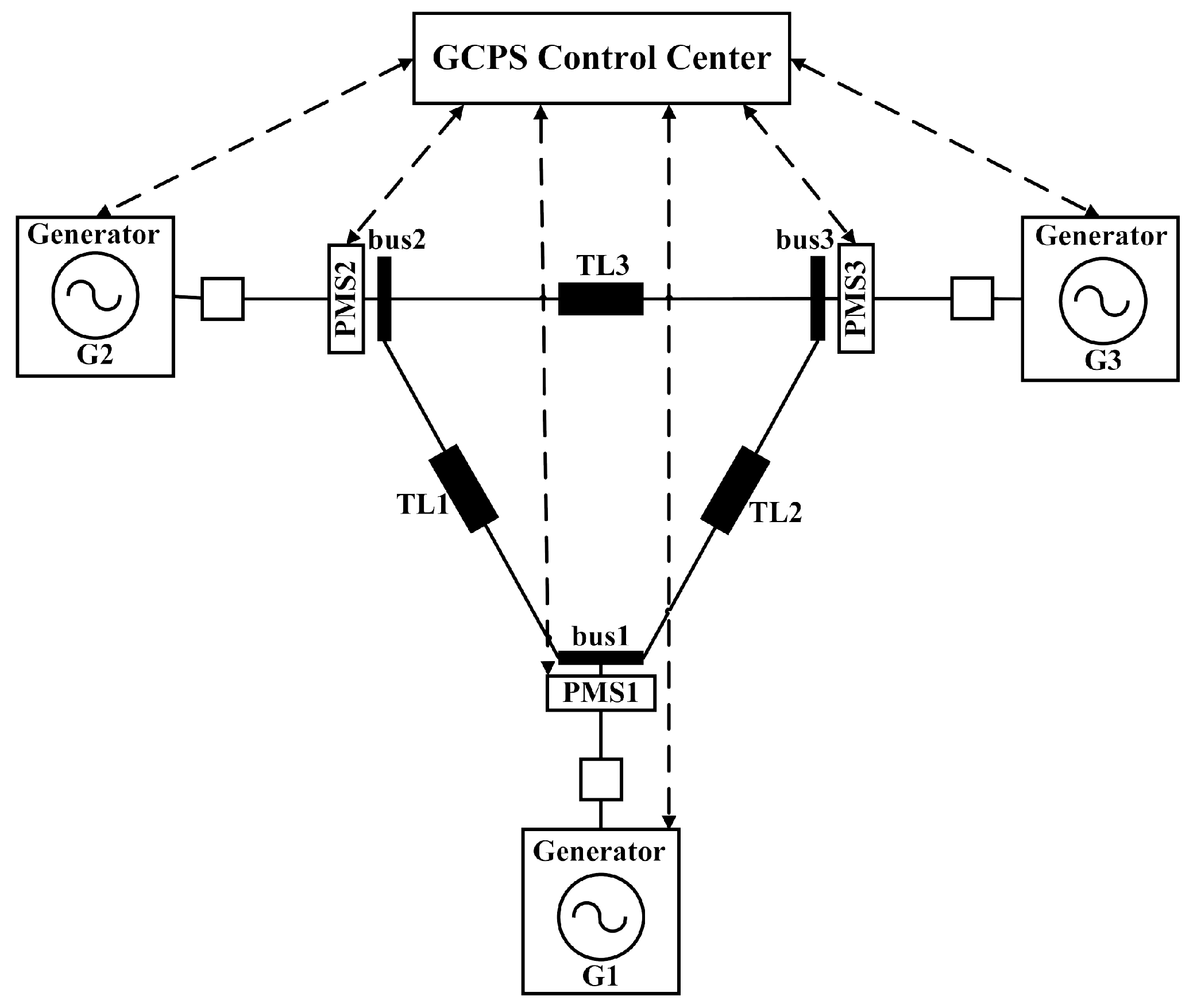
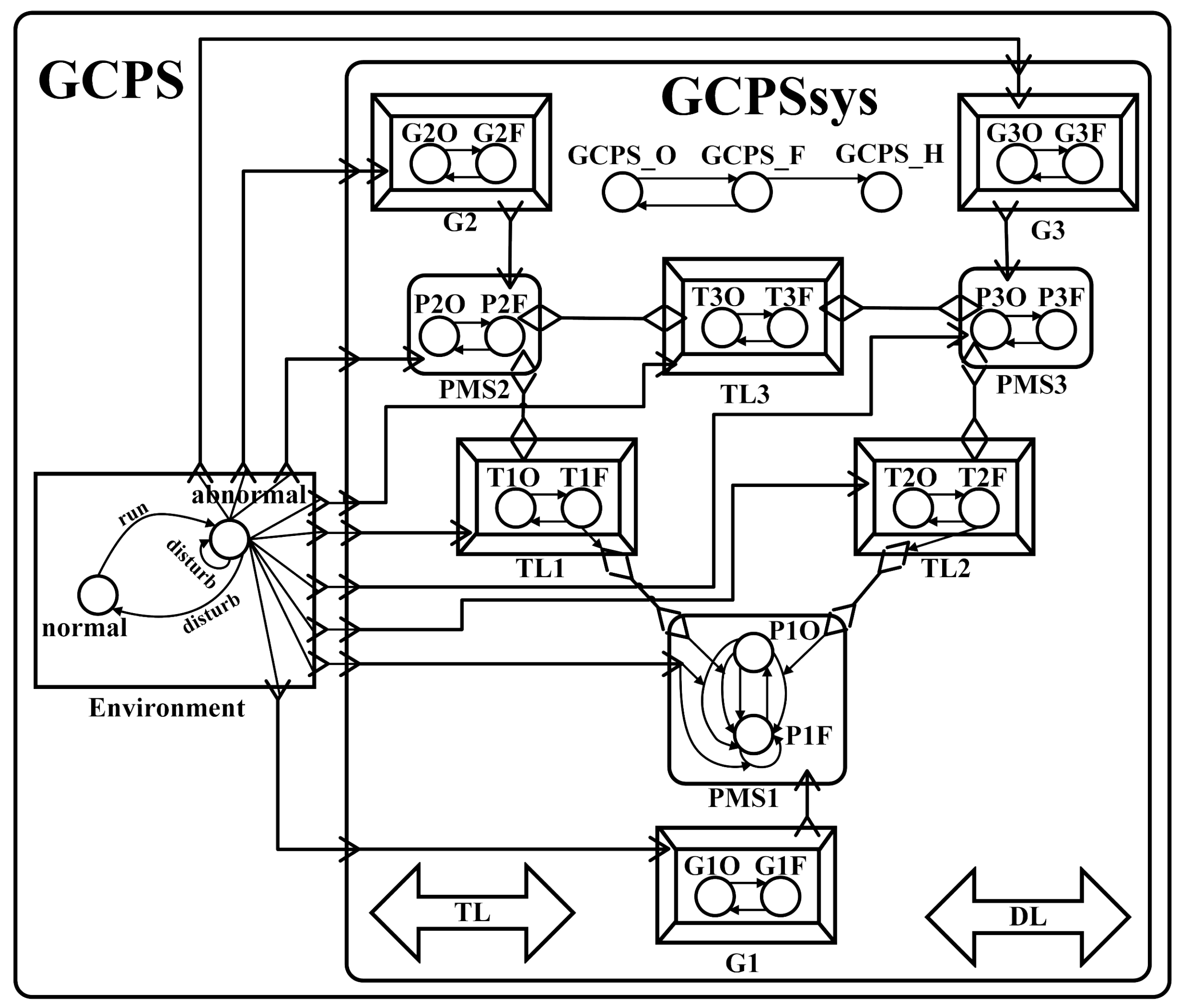
5. Case Study
5.1. A GCPS, Its AADL Model and Transformed SMG Model
5.2. Results
5.3. Discussion
6. Related Work
7. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Yu, X.; Xue, Y. Smart grids: A cyber–physical systems perspective. Proc. IEEE 2016, 104, 1058–1070. [Google Scholar] [CrossRef]
- Huang, Z.; Wang, C.; Zhu, T.; Nayak, A. Cascading failures in smart grid: Joint effect of load propagation and interdependence. IEEE Access 2015, 3, 2520–2530. [Google Scholar] [CrossRef]
- Huang, Z.; Wang, C.; Stojmenovic, M.; Nayak, A. Characterization of cascading failures in interdependent cyber-physical systems. IEEE Trans. Comput. 2015, 64, 2158–2168. [Google Scholar] [CrossRef]
- Rahnamay-Naeini, M.; Hayat, M.M. Cascading Failures in Interdependent Infrastructures: An Interdependent Markov-Chain Approach. IEEE Trans. Smart Grid 2016, 7, 1997–2006. [Google Scholar] [CrossRef]
- Wei, M.; Lu, Z.; Tang, Y.; Lu, X. How Can Cyber-Physical Interdependence Affect the Mitigation of Cascading Power Failure? In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communication, Honolulu, HI, USA, 16–19 April 2018; pp. 2501–2509. [Google Scholar]
- Buldyrev, S.V.; Parshani, R.; Paul, G.; Stanley, H.E.; Havlin, S. Catastrophic cascade of failures in interdependent networks. Nature 2010, 464, 1025–1028. [Google Scholar] [CrossRef] [PubMed]
- Vellaithurai, C.; Srivastava, A.; Zonouz, S.; Berthier, R. CPIndex: Cyber-Physical Vulnerability Assessment for Power-Grid Infrastructures. IEEE Trans. Smart Grid 2015, 6, 566–575. [Google Scholar] [CrossRef]
- Xun, P.; Zhu, P.; Zhang, Z.; Cui, P.; Xiong, Y. Detectors on Edge Nodes against False Data Injection on Transmission Lines of Smart Grid. Electronics 2018, 7, 89. [Google Scholar] [CrossRef]
- Wadhawan, Y.; AlMajali, A.; Neuman, C. A Comprehensive Analysis of Smart Grid Systems against Cyber-Physical Attacks. Electronics 2018, 7, 249. [Google Scholar] [CrossRef]
- Kundur, P.; Balu, N.J.; Lauby, M.G. Power System Stability and Control; McGraw-Hill: New York, NY, USA, 1994; Volume 7. [Google Scholar]
- Nguyen, H.H.; Tan, R.; Yau, D.K. Safety-assured collaborative load management in smart grids. In Proceedings of the 2014 ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Berlin, Germany, 14–17 April 2014; pp. 151–162. [Google Scholar]
- SAE International. AS5506C—(R) Architecture Analysis and Design Language (AADL); SAE International: Warrendale, PA, USA, 2017. [Google Scholar]
- Wei, X.; Dong, Y.; Li, X.; Wong, W.E. Architecture-level hazard analysis using AADL. J. Syst. Softw. 2018, 137, 580–604. [Google Scholar] [CrossRef]
- Wei, X.; Dong, Y.; Yang, M.; Hu, N.; Ye, H. Hazard analysis for AADL model. In Proceedings of the 2014 IEEE 20th International Conference on Embedded and Real-Time Computing Systems and Applications (RTCSA), Chongqing, China, 20–22 August 2014; pp. 1–10. [Google Scholar] [CrossRef]
- Bozzano, M.; Cimatti, A.; Katoen, J.P.; Nguyen, V.Y.; Noll, T.; Roveri, M. Safety, Dependability and Performance Analysis of Extended AADL Models. Comput. J. 2011, 54, 754–775. [Google Scholar] [CrossRef]
- Bozzano, M.; Bruintjes, H.; Cimatti, A.; Katoen, J.P.; Noll, T.; Tonetta, S. The COMPASS 3.0 Toolset. In Proceedings of the fifth International Symposium on Model-Based Safety and Assessment (IMBSA 2017), Trento, Italy, 11–13 September 2017. [Google Scholar]
- Wei, X.; Dong, Y.; Ye, H. QaSten: Integrating Quantitative Verification with Safety Analysis for AADL Model. In Proceedings of the 2015 International Symposium on Theoretical Aspects of Software Engineering (TASE), Nanjing, China, 12–14 September 2015; pp. 103–110. [Google Scholar] [CrossRef]
- SAE International. (R) SAE Architecture Analysis and Design Language (AADL) Annex Volume 1: Annex E: Error Model Annex; SAE International: Warrendale, PA, USA, 2015. [Google Scholar]
- Simaitis, A. Automatic Verification of Competitive Stochastic Systems. Ph.D. Thesis, Department of Computer Science, University of Oxford, Oxford, UK, 2014. [Google Scholar]
- Svoreňová, M.; Kwiatkowska, M. Quantitative verification and strategy synthesis for stochastic games. Eur. J. Control 2016, 30, 15–30. [Google Scholar] [CrossRef]
- Kwiatkowska, M. Model Checking and Strategy Synthesis for Stochastic Games: From Theory to Practice. In Proceedings of the 43rd International Colloquium on Automata, Languages, and Programming (ICALP 2016), Rome, Italy, 12–15 July 2016. [Google Scholar]
- Kwiatkowska, M.; Parker, D.; Wiltsche, C. PRISM-games 2.0: A Tool for Multi-Objective Strategy Synthesis for Stochastic Games. In Proceedings of the 22nd International Conference on Tools and Algorithms for the Construction and Analysis of Systems (TACAS’16), Eindhoven, The Netherlands, 2–8 April 2016. [Google Scholar]
- Dehnert, C.; Junges, S.; Katoen, J.P.; Volk, M. A storm is coming: A modern probabilistic model-checker. In Proceedings of the International Conference on Computer Aided Verification, Heidelberg, Germany, 24–28 July 2017; Springer: Cham, Switzerland, 2017; pp. 592–600. [Google Scholar]
- WSCC 9-Bus System. Available online: http://icseg.iti.illinois.edu/wscc-9-bus-system/ (accessed on 10 September 2018).
- Markov Reward Model Checker. Available online: http://www.mrmc-tool.org/trac/ (accessed on 1 February 2019).
- Morozov, A.; Mutzke, T.; Ren, B.; Janschek, K. AADL-based stochastic error propagation analysis for reliable system design of a medical patient table. In Proceedings of the 2018 Annual Reliability and Maintainability Symposium (RAMS), Reno, NV, USA, 22–25 January 2018; pp. 1–7. [Google Scholar]
- Dong, Y.; Wei, X.; Xiao, M. Overview: System Architecture Virtual Integration based on an AADL Model. In Symposium on Real-Time and Hybrid Systems; Springer: Cham, Switzerland, 2018; pp. 105–115. [Google Scholar]
- Bernardi, S.; Merseguer, J.; Petriu, D. An UML Profile for Dependability Analysis and Modeling of Software Systems; Technical Report RR-08-05; University of Zaragoza: Zaragoza, Spain, 2008. [Google Scholar]
- Qi, J.; Sun, K.; Mei, S. An interaction model for simulation and mitigation of cascading failures. IEEE Trans. Power Syst. 2015, 30, 804–819. [Google Scholar] [CrossRef]
- Xin, S.; Guo, Q.; Sun, H.; Zhang, B.; Wang, J.; Chen, C. Cyber-physical modeling and cyber-contingency assessment of hierarchical control systems. IEEE Trans. Smart Grid 2015, 6, 2375–2385. [Google Scholar] [CrossRef]
- Qin, B.; Liu, D.; Cao, M.; Zou, J. Formal modeling and verification of flexible load control for power grid CPS based on differential dynamic logic. In Proceedings of the 2017 IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 26–28 November 2017; pp. 1–6. [Google Scholar] [CrossRef]






| No. | AADL Model | PRISM-Games Language |
|---|---|---|
| 1 | Component implementation, e.g., system implementation sys.i; | Module, e.g., module sys_i; |
| 2 | Error states and hazards, e.g., srcState: initial error state; dstState: error state; overVoltage: hazard; | Integer variable, e.g., stateVar : [0..2] init 0; (0 for srcState, 1 for dstState, 2 for OverVoltage) |
| 3 | Initial error state | Initial value (0) of the variable |
| 4 | Error event and hazard trigger with occurrence property, e.g., errEvent: error event; (with 0.1) | double constants for probability values, e.g., const double proErrEvent = 0.1; // for itself. (1-proErrEvent) // for others represented by true. |
| 5 | Hazard source, e.g., hs1: error state dstState; hs2: error event errEvent; | Formula e.g., formula hs1 = stateVar = 1; formula hs2 = 0.1; |
| State | Components | sys |
|---|---|---|
| GCPSsysFailed | GCPSsys | 0.29638545685060275 |
| OverVoltage | GCPSsys | 0.00553889850028547 |
| LowPower | GCPSsys | |
| EquipDamage | GCPSsys |
| Iterations/ | 360 | 3600 | 36,000 | 360,000 |
|---|---|---|---|---|
| State | (Probability/Time(s)) | (Probability/Time(s)) | (Probability/Time(s)) | (Probability/Time(s)) |
| GCPSsysFailed | 0.29563894732784135 | 0.29638545685060275 | 0.29646006198918473 | 0.2964675220331432 |
| 51 | 583 | 3845 | 38,844 | |
| OverVoltage | 0.005498371833365312 | 0.00553889850028547 | 0.0055429599223609655 | 0.005543366152586064 |
| 40 | 583 | 4093 | 43,007 | |
| LowPower | ||||
| 46 | 449 | 4690 | 48,084 | |
| EquipDamage | ||||
| 41 | 391 | 4439 | 46,209 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wei, X.; Dong, Y.; Sun, P.; Xiao, M. Safety Analysis of AADL Models for Grid Cyber-Physical Systems via Model Checking of Stochastic Games. Electronics 2019, 8, 212. https://doi.org/10.3390/electronics8020212
Wei X, Dong Y, Sun P, Xiao M. Safety Analysis of AADL Models for Grid Cyber-Physical Systems via Model Checking of Stochastic Games. Electronics. 2019; 8(2):212. https://doi.org/10.3390/electronics8020212
Chicago/Turabian StyleWei, Xiaomin, Yunwei Dong, Pengpeng Sun, and Mingrui Xiao. 2019. "Safety Analysis of AADL Models for Grid Cyber-Physical Systems via Model Checking of Stochastic Games" Electronics 8, no. 2: 212. https://doi.org/10.3390/electronics8020212
APA StyleWei, X., Dong, Y., Sun, P., & Xiao, M. (2019). Safety Analysis of AADL Models for Grid Cyber-Physical Systems via Model Checking of Stochastic Games. Electronics, 8(2), 212. https://doi.org/10.3390/electronics8020212





