An Energy Efficient and Formally Secured Certificate-Based Signcryption for Wireless Body Area Networks with the Internet of Things
Abstract
1. Introduction
1.1. Authors’ Motivations and Contributions
- We first provide the basic syntax for certificate based signcryption and then construct the scheme practically for WBAN with IoT;
- The proposed scheme is shown to be resistant against various attacks through informal security analysis concerning integrity, confidentiality, replay, unforgeability, and forward secrecy, respectively;
- We also generate the high level protocol specification language (HLPSL) code for our scheme in AVISPA Tool for the formal security checking, and the simulation results authenticates that the proposed scheme is SAFE, according to the checking structure of two well-known checker models, i.e., on-the-fly model checker (OFMC) and constraint logic-based attack searcher (ATSE);
- We perform the computational cost and communication overhead comparison analysis with the relevant existing schemes, which demonstrates the presented scheme, in addition, is far more efficient.
1.2. Structure of The Paper
2. Preliminaries
2.1. Hyper-Elliptic Curve
2.2. Hyper-Elliptic Curve Discrete Logarithm Problem
2.3. Automated Validation Tool for Security Validation and Application (AVISPA)
2.4. Syntax of Certificate-based Signcryption (CB-SN)
- Setup: Certifier’s authority (CsA) recognizes a security parameter 𝜇 as input data and runs the setup algorithm to make essential parameters set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3} and a master secret key Y and public key T = 𝛶.𝒹, respectively. The essential parameters set is directly accessible on a network, anyway Y is kept by the CsA secret.
- Public variable generation (PVG): Each actor with identity IDA, runs the PVG algorithm to produce his public variable PVA by taking input, an essential parameter set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3}. Then, the actor having identity IDA, has sent the pair (PVA, IDA) to CsA via an insecure link.
- Certificate generation (CG): By taking input (PVA, IDA), the essential parameter set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3} and Y, CsA run the CG algorithm to produce a certificate CertA for each actor with identity IDA and hand over a certificate with auxiliary variable (𝑒𝓇𝑡A, 𝒶𝓊𝓍A) to the actors via unsecured link.
- Actor’s key generation (AKG): Inputting the pair of an auxiliary variable (CertA, auxA), an essential parameter set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3} and the identity IDA of each actor, the participated actor’s with identity IDA produces his private and public keys (AA, QA).
- Signcryption generation (SG): The SG algorithm is executed by the sender actor to produce signcryption text 𝜓 = {C,A,S}, of a message, m, and delivers 𝜓 to the receiver through an unsecured network. It takes as input the certificate of the sender and receiver (Certs, Certu), the identity of a sender and receivers (IDs, IDu), private and public key of the sender (As, Qs), a message (m), an essential parameter set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3}, and public key of receiver Qu.
- Unsigncryptions (US): The US algorithm is executed by the receiver actor to verify and decrypts the received signcryption text 𝜓 = {C,A,S}. It takes as input the certificate of the sender Certs, the identity of a sender and receivers (IDs, IDu), private and public key of the receiver (Au,Qu), a signcryption text 𝜓 = {C,A,S}, and essential parameter set.
3. Proposed Architecture
4. Constructions of CB-SN
- Setup: The CsA produce an essential parameter set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3} and after that the CsA select a master secret key Y{1,2, …, t − 1} and calculate the master public key T = Y.d, respectively. The essential parameters set is directly accessible on a network and the master secret key Y is kept by the CsA secret.
- PVG: Given an essential parameter set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3}, each actor with identity IDA, choose a random number 𝜔A and computes his public variable A = 𝜔A.𝒹. Then the actor with identity IDA delivers (PVA, IDA) to the CsA by using the open channel.
- CG: Given an essential parameter set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3}, public variable and identity of each actor (PVA, IDA) and master secret key Y, CsA select a random number 𝜒A𝜖 {1, 2…., 𝑡 − 1} and calculate 𝜑A = 𝜒A.𝒹. After that, CsA computes the certificate CertA = 𝜑A + PVA and auxiliary variable auxA = 1 (CertA, IDA). 𝜒A + 𝛶, then, hands over a certificate CertA with auxiliary variable (CertA, auxA) to the actors via insecure link.
- AKG: Given the tuple (CertA, auxA), identity IDA of each actor, and essential parameter set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3}, each actor makes their private key AA = H1 (CertA, IDA). wA + auxA make their public key as QA = AA. d.
- SG: Given an essential parameter set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3}, the sender and receiver’s certificates (Certs, Certu), the identity of the sender and the receiver (IDs, IDu), the private and public key of the sender (As, Qs), a massage (m), and public key of receiver Qu. Then the sender produces a signcryption tuple 𝜓 = {C, A} by utilizing the following steps:
- The sender first computes the public key of receiver Qu ≟ H2 (Certu, IDu). Certu + T;
- Next, choose a random number 𝛺𝜖 {1, 2, …, t − 1} and compute 𝛽 = 𝛺 . 𝒹;
- Select a fresh nonce N;
- Compute the session key = 𝛺 . u and produced the cipher text = ℇ (𝓂‖ N);
- Compute the hash value 𝛬 = 2(𝓂‖ N) and signature = 𝛺 - 𝛬 , As;
- Then, hand over 𝜓 = {, 𝛬, } to the receiver using insecure channel.
- US: Given the sender’s certificate Certs, identity of a sender and receivers (IDs, IDu), private and public key of the receiver (Au,Qu), a signcryption text 𝜓 = {C, A, S}, essential parameter set {hε𝒸, δ, ℑ𝑡, 𝒹, hε𝒸, 𝛵, 1, 2, 3}, and public key of sender Qs. The receiver performs the following steps to verify and decrypts the received signcryption text 𝜓= {C. A, S}.
- The receiver first computes the public key of sender Qs ≟ H2 (Certs, IDs). Certs + 𝛵;
- Compute 𝛽 = S . d + 𝛬 . Qs;
- Recover the secret key SK = Au . 𝛽 and produced the plaintext (m‖ N) = D (C);
- Compute the hash value 𝛬/ = H2(m‖ N);
- Accept the signcryption text 𝜓 = {,𝛬,} if 𝛬/ = H2(m‖ N) ≟ 𝛬 = H2(m‖ N).
4.1. Correctness
- u ≟ 2 (𝑒𝓇𝑡u, IDu). 𝑒𝓇𝑡u + 𝛵
- = 2 (𝑒𝓇𝑡u, IDu) . (𝜑u+ u ) + 𝛶, where 𝑒𝓇𝑡u= 𝜑u+ u and 𝛵 = 𝛶.𝒹
- = 2 (𝑒𝓇𝑡u, IDu) . (𝜑u+ 𝜔u.𝒹) + 𝛶. 𝒹, where u = 𝜔u.𝒹
- = 2 (𝑒𝓇𝑡u, IDu) . (𝜒u.𝒹 + 𝜔u.𝒹) + 𝛶. 𝒹, where 𝜑u= u.𝒹
- = 𝜒u .𝒹. 2 (𝑒𝓇𝑡u, IDu) + 𝜔u.𝒹. 2 (𝑒𝓇𝑡u, IDu) + 𝛶.𝒹
- = (𝜒u . 2 (𝑒𝓇𝑡u, IDu)+ 𝜔u. 2 (𝑒𝓇𝑡u, IDu)+ 𝛶). 𝒹
- = (𝒶𝓊𝓍u + 𝜔u. 2 (𝑒𝓇𝑡u, IDu)), where 𝒶𝓊𝓍u = 1 (𝑒𝓇𝑡u, IDu) . 𝜒u + 𝛶
- = 𝒜u, where 𝒜u = 1 (𝑒𝓇𝑡u, IDu).𝜔u + 𝒶𝓊𝓍u
- = 𝒜u .𝒹 = u , while it same process at the receiver side for making the public key of the sender, by using the following computations.
- s ≟ 2 (𝑒𝓇𝑡s, IDs) . 𝑒𝓇𝑡s + 𝛵
- = 2 (𝑒𝓇𝑡s, IDs) . (𝜑s + s ) + 𝛶. 𝒹, where 𝑒𝓇𝑡s = 𝜑s + s and 𝛵 = 𝛶.𝒹
- = 2 (𝑒𝓇𝑡s, IDs) . (𝜑s + 𝜔s . 𝒹) + 𝛶, where s = 𝜔s . 𝒹
- = 2 (𝑒𝓇𝑡s, IDs) . (𝜒s . 𝒹 + 𝜔s.𝒹) + 𝛶. 𝒹, where 𝜑s = 𝜒s . 𝒹
- = 𝜒s . 𝒹 . 2 (𝑒𝓇𝑡s, IDs) + 𝜔s . 𝒹 . 2 (𝑒𝓇𝑡s, IDs) + 𝛶. 𝒹
- = (𝜒s . 2 (𝑒𝓇𝑡s, IDs) + 𝜔s . 2 (𝑒𝓇𝑡s, IDs) + 𝛶) . 𝒹
- = (𝒶𝓊𝓍s + 𝜔s . 2 (𝑒𝓇𝑡s, IDs)) . 𝒹 where 𝒶𝓊𝓍s = 1 (𝑒𝓇𝑡s, IDs) . 𝜒s + 𝛶
- = 𝒜s . 𝒹, where 𝒜s = 1 (𝑒𝓇𝑡s, IDs) . 𝜔s + 𝒶𝓊𝓍s
- = 𝒜s . 𝒹 = s
- And the receiver also recovers the secret key by using the following steps:
- = 𝒜u . 𝛽
- = 𝒜u . (.𝒹 + 𝛬 . s), where 𝛽 = . 𝒹 + 𝛬 . s
- = 𝒜u . ( . 𝒹 + 𝛬 . 𝒜s . 𝒹), where s = 𝒜s . 𝒹
- = 𝒜u . (𝛺 – 𝛬 . 𝒜s . 𝒹 + 𝛬 . s . 𝒹)), where = 𝛺 – 𝛬 . 𝒜s
- = 𝒜u . 𝒹 (𝛺 – 𝛬 . 𝒜s + 𝛬 . 𝒜s) = 𝒜u . 𝒹= u . (𝛺) = , where 𝒜u . 𝒹 = u
5. Informal Security Analysis
5.1. Confidentiality
5.2. Integrity
5.3. Unforgeability
5.4. Public Verifiability
5.5. Forward Secrecy
5.6. Anti-Replay Attack
6. CB-SN Access Control for WBAN
6.1. Initialization
6.2. Registration
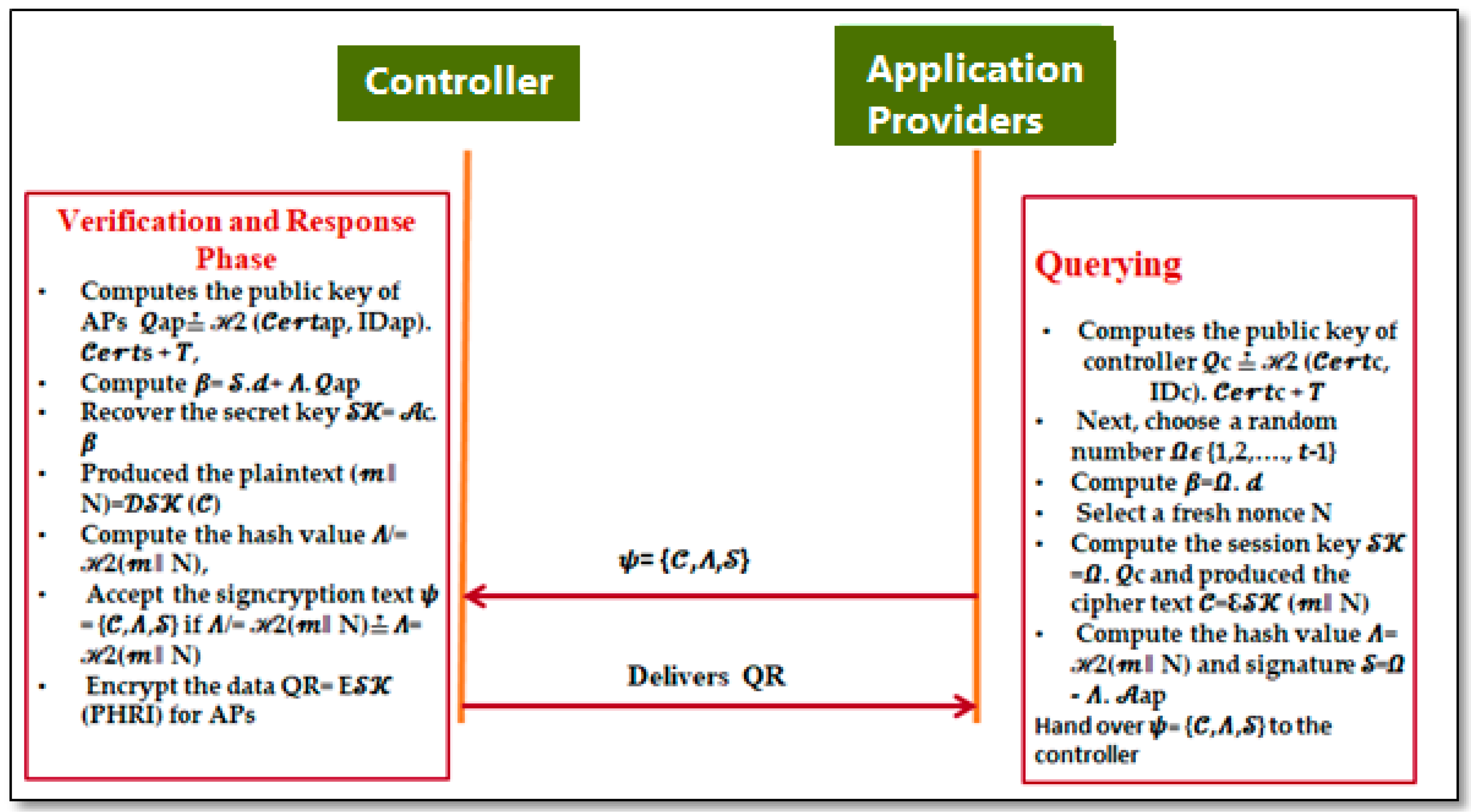
6.3. Querying Phase
6.4. Verification and Response
7. Performance
7.1. Security Performance
7.2. Computational Cost
7.3. Communication Cost
- The reduction in communication cost of the proposed CB-SN access control scheme from Li et al. [22] is (3|𝔖1| + |ID| + |𝓂|) (|𝒵n| + |H| + |𝓂|)/(3|𝔖1| + |ID| + |𝓂|) = (4176 −1616)/(4176)*100 = 61.30%,
- The reduction in communication cost of our designed CB-SN access control scheme from Omala et al. [15] is (|𝔖1| + |ID| + |𝓂| + |𝒵𝓆|)(|𝒵n| + |H|+|𝓂|)/(|𝔖1|+ |ID| + |𝓂| + |𝒵𝓆|) = (2288 − 1616)/(2288)*100 = 29.37%.
- The reduction in communication cost of of the proposed CB-SN access control scheme from Gao et al. [23] is (|ID| + |𝓂| + 5|𝒵𝓆|) − (|𝒵n| + |H| + |𝓂|)/(|ID| + |𝓂| + 5|𝒵𝓆|) = (1904 − 1616)/(1904)*100 = 15.12%.
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A. Implementations of CB-SN Access Control Scheme in AVISPA
| Algorithm A1 High level protocol specification language (HLPSL) code for application providers (Aps) role |
| role role_Aps(Aps:agent,Controller:agent,Qap:public_key,Qc:public_key,SND,RCV:channel(dy)) played_by Aps def = local State:nat, N:text, Minuss:hash_func, Omega:text, A:text, M:text, E:hash_func, Sk:symmetric_key init State := 0 transition 1. State=0 /\ RCV(start) =|> State':=1 /\ SND(Aps.Controller) 2. State=1 /\ RCV(Controller.{N'}_Qc) =|> State':=2 /\ A':=new() /\ Omega':=new() /\ Sk':=new() /\ M':=new() /\ secret(M',sec_2,{Aps}) /\ witness(Aps,Controller,auth_1,M') /\ SND(Aps.{E(M')}_Sk'.{Minuss(Omega'.A')}_inv(Qap)) end role role role_Aps(Aps:agent,Controller:agent,Qap:public_key,Qc:public_key,SND,RCV:channel(dy)) played_by Aps def = local State:nat, N:text, Minuss:hash_func, Omega:text, A:text, M:text, E: hash_func, Sk:symmetric_key init State:= 0 transition 1. State = 0 /\ RCV(start) =|> State':=1 /\ SND(Aps.Controller) 2. State = 1 /\ RCV(Controller.{N'}_Qc) =|> State':=2 /\ A':=new() /\ Omega':=new() /\ Sk':=new() /\ M':=new() /\ secret(M',sec_2,{Aps}) /\ witness(Aps,Controller,auth_1,M') /\ SND(Aps.{E(M')}_Sk'.{Minuss(Omega'.A')}_inv(Qap)) end role |
| Algorithm A2 HLPSL code for controller role. |
| role role_Controller(Aps:agent,Controller:agent,Qap:public_key,Qc:public_key,SND,RCV:channel(dy)) played_by Controller def = local State: nat, N:text, Minuss:hash_func, Omega:text, A:text, M:text, E: hash_func, Sk:symmetric_key init State := 0 transition 1. State=0 /\ RCV(Aps.Controller) =|> State':=1 /\ N':=new() /\ SND(Controller.{N'}_Qc) 6. State=1 /\ RCV(Aps.{E(M')}_Sk'.{Minuss(Omega'.A')}_inv(Qap)) =|> State':=2 /\ request(Controller,Aps,auth_1,M') /\ secret(M',sec_2,{Aps}) end role |
| Algorithm A3 HLPSL code for session and environmental role. |
| role session1 (Aps:agent,Controller:agent, Qap:public_key, Qc:public_key) def = local SND2,RCV2,SND1,RCV1:channel(dy) composition role_Controller(Aps,Controller,Qap,Qc,SND2,RCV2)/\ role_Aps(Aps,Controller,Qap,Qc,SND1,RCV1) end role role session2(Aps:agent,Controller:agent,Qap:public_key,Qc:public_key) def = local SND1,RCV1:channel(dy) composition role_Aps(Aps,Controller,Qap,Qc,SND1,RCV1) end role role environment() def = const hash_0:hash_func,qap:public_key,alice:agent,bob:agent, qc:public_key,const_1:agent,const_2:public_key, const_3:public_key,auth_1:protocol_id,sec_2:protocol_id intruder_knowledge = {alice,bob} composition session2(i,const_1,const_2,const_3) /\ session1(alice,bob,qap,qc) end role goal authentication_on auth_1 secrecy_of sec_2 end goal environment () |


References
- Alkhayyat, A.; Thabit, A.A.; Al-Mayali, F.A.; Abbasi, Q.H. WBSN in IoT Health-Based Application: Toward Delay and Energy Consumption Minimization. J. Sens. 2019, 2019, 2508452. [Google Scholar] [CrossRef]
- El-hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A Survey of the Internet of Things (IoT) Authentication Schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef] [PubMed]
- Chaudhary, S.; Singh, A.; Kakali, C. Wireless Body Sensor Network (WBSN) Security and Privacy Issues: A Survey. Int. J. Comp. Int. IoT 2019, 2, 515–521. [Google Scholar]
- Zhou, C. An improved lightweight certificateless generalized signcryption scheme for mobile-health system. Int. J. Dist. Sen. Netw. 2019. [Google Scholar] [CrossRef]
- Kumar, M.; Verma, H.K.; Sikka, G. A secure lightweight signature-based authentication for Cloud-IoT crowdsensing environments. Trans. Emerg. Telecommun. Technol. 2018. [Google Scholar] [CrossRef]
- Rajesh, S.; Paul, V.; Menon, V.G.; Khosravi, M.R. A Secure and Efficient Lightweight Symmetric Encryption Scheme for Transfer of Text Files between Embedded IoT Devices. Symmetry 2019, 11, 293. [Google Scholar] [CrossRef]
- Zheng, Y. Digital signcryption or how to achieve cost (signature & encryption) cost (signature)+ cost (encryption). In Advances in Cryptology, CRYPTO’97; Springer: Cham, Switzerland, 1997; pp. 165–179. [Google Scholar]
- Waheed, A.; Iqbal, J.; Din, N.; Islam, S.U.; Umar, A.I.; Amin, N.U. Improved Cryptanalysis of Provable Certificateless Generalized Signcryption. Int. J. Adv. Comput. Sci. Appl. 2019, 10. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Workshop on the Theory and Application of Cryptographic Techniques; Springer: Berlin, Germany, 1985; pp. 47–53. [Google Scholar]
- Malone-Lee, J. Identity Based Signcryption. Cryptology ePrint Archive; Report 2002/098. 2002. Available online: http://eprint.iacr.org/2002/098 (accessed on 30 July 2019).
- Luo, W.; Ma, W. Secure and Efficient Data Sharing Scheme Based on Certificateless Hybrid Signcryption for Cloud Storage. Electronics 2019, 8, 590. [Google Scholar] [CrossRef]
- Barbosa, M.; Farshim, P. Certificateless signcryption. In Proceedings of the ACM Symposium on Information, Computer and Communications Security, Tokyo, Japan, 18–20 March 2008; pp. 369–372. [Google Scholar]
- Lu, Y.; Li, J. Provably Secure Certificate Based Signcryption Scheme without Pairings. KSII Trans. Internet Inf. Syst. 2014, 8, 2554–2571. [Google Scholar]
- Li, F.; Han, Y.; Jin, C. Practical signcryption for secure communication of wireless sensor networks. Wirel. Pers. Commun. 2016, 89, 1391–1412. [Google Scholar] [CrossRef]
- Omala, A.A.; Mbandu, A.S.; Mutiria, K.D.; Jin, C.; Li, F. Provably Secure Heterogeneous Access Control Scheme for Wireless body area networks. JMS 2018, 42, 108. [Google Scholar] [CrossRef] [PubMed]
- Gentry, C. Certificate-Based Encryption and the Certificate Revocation Problem. In Proceedings of the International Conference on Theory Application of Cryptographic Techniques, Warsaw, Poland, 4–8 May 2003; pp. 272–293. [Google Scholar]
- Braeken, A.; Shabisha, P.; Touhafi, A.; Steenhaut, K. Pairing free and implicit certificate based signcryption scheme with proxy re-encryption for secure cloud data storage. In Proceedings of the 2017 3rd International Conference of Cloud Computing Technologies and Applications, Rabat, Morocco, 24–26 Octcber 2017. [Google Scholar]
- Le, M.-H.; Hwang, S.O. Certificate-Based Signcryption Scheme without Pairing: Directly Verifying Signcrypted Messages Using a Public Key. ETRI J. 2016, 38, 724–734. [Google Scholar] [CrossRef]
- Braeken, A. Pairing Free Certificate Based Signcryption Schemes Using ECQV Implicit Certificates. KSII Trans. Internet Inf. Syst. 2019, 13, 1546–1565. [Google Scholar]
- Cagalaban, G.; Kim, S. Towards a secure patient information access control in ubiquitous healthcare systems using identity-based signcryption. In Proceedings of the 13th International Conference on Advanced Communication Technology (ICACT), Seoul, Korea, 13–16 February 2011; pp. 863–867. [Google Scholar]
- Hu, C.; Zhang, N.; Li, H.; Cheng, X.; Liao, X. Body area network security: A fuzzy attribute-based signcryption scheme. IEEE J. Sel. Areas Commun. 2013, 31, 37–46. [Google Scholar] [CrossRef]
- Li, F.; Hong, J. Efficient Certificateless Access Control for Wireless body area networkss. IEEE Sens. J. 2016, 16, 5389–5396. [Google Scholar] [CrossRef]
- Li, F.; Han, Y.; Jin, C. Cost-effective and anonymous access control for wireless body area networkss. IEEE Syst. J. 2018, 12, 747–758. [Google Scholar] [CrossRef]
- Gao, G.M.; Peng, X.G.; Jin, L.Z. Efficient Access Control Scheme with Certificateless Signcryption for Wireless body area networkss. Int. J. Netw. Secur. 2019, 21, 428–437. [Google Scholar]
- Ullah, I.; Amin, N.U.; Naeem, M.; Khattak, S.J.; Ali, H. A Novel Provable Secured Signcryption Scheme PSSS: A Hyper-Elliptic Curve-Based Approach. Mathematics 2019, 7, 686. [Google Scholar] [CrossRef]
- Ullah, S.; Li, X.-Y.; Zhang, L.A. Review of Signcryption Schemes Based on Hyper Elliptic Curve. In Proceedings of the 3rd International Conference on Big Data Computing and Communications (BIGCOM), Chengdu, China, 10–11 August 2017. [Google Scholar]
- Ullah, I.; Haqb, U.I.; Amin, N.U.; Umar, I.A.; Khattak, H. Proxy Signcrypion Scheme Based on Hyper Elliptic Curves. IJC 2016, 20, 157–166. [Google Scholar]
- Khan, M.A.; Qureshi, I.M.; Khanzada, F. A Hybrid Communication Scheme for Efficient and Low-Cost Deployment of Future Flying Ad-Hoc Network (FANET). Drones 2019, 3, 16. [Google Scholar] [CrossRef]
- Rahman, A.U.; Ullah, I.; Naeem, M.; Anwar, R.; Amin, N.U.; Khattak, H.; Ullah, S. A Lightweight Multi-Message and Multi-Receiver Heterogeneous Hybrid Signcryption Scheme based on Hyper Elliptic Curve. Int. J. Adv. Comput. Sci. Appl. (IJACSA) 2018, 9, 160–167. [Google Scholar] [CrossRef]




| S.NO | Symbol | Explanation |
|---|---|---|
| 1 | hε𝒸 | Hyper-elliptic curve |
| 2 | Genus of hyper-elliptic curve | |
| 3 | 𝒹 | Divisor in hyper-elliptic curve |
| 4 | hε𝒸 | Jacobian of hyper-elliptic curve |
| 5 | 𝛶 | Master secret key |
| 6 | 𝛵 | Master public key |
| 7 | 1, 2, 3 | Hash functions |
| 8 | s, u | Public keys of sender and receiver |
| 9 | 𝒜s, 𝒜u | Private keys of sender and receiver |
| 10 | 𝑒𝓇𝑡s, 𝑒r𝑡u | Certificates for sender and receiver |
| 11 | IDs, IDu | Identities for sender and receiver |
| 12 | Session secret key | |
| 13 | N | A fresh nonce |
| 14 | 𝓂/ | Message/encrypted message |
| 15 | ℇ/ | Encryption/decryption |
| 16 | 𝜓 | Signcryption text |
| 17 | ‖ | Concatenation |
| Security Services | [22] | [15] | [24] | [17] | [19] S1 | [19] S2 | [19] S3 | Proposed |
|---|---|---|---|---|---|---|---|---|
| CFY | √ | √ | √ | √ | √ | √ | √ | √ |
| UFY | √ | √ | √ | √ | √ | √ | √ | √ |
| ATN | √ | √ | √ | √ | √ | √ | √ | √ |
| ITY | √ | √ | √ | √ | √ | √ | √ | √ |
| ARA | √ | √ | √ | ⨵ | ⨵ | ⨵ | ⨵ | √ |
| FSY | ⨵ | ⨵ | ⨵ | √ | √ | √ | √ | √ |
| PVY | ⨵ | ⨵ | ⨵ | ⨵ | ⨵ | ⨵ | ⨵ | √ |
| ROM | √ | √ | √ | ⨵ | ⨵ | ⨵ | ⨵ | ⨵ |
| FVTA | ⨵ | ⨵ | ⨵ | ⨵ | ⨵ | ⨵ | ⨵ | √ |
| Schemes | Signcryption Generation (SG) (APs) | Unsigncryption (US) (Controller) | Total |
|---|---|---|---|
| Li et al. [22] | 1 𝓂𝓍𝓅 + 4 𝑒𝓈𝓂 | 2 𝒷𝓅 + 2 𝑒𝓈𝓂 +1 𝓂𝓍𝓅 | 2 𝒷𝓅 + 6 𝑒𝓈𝓂 +2 𝓂𝓍𝓅 |
| Omala et al. [15] | 3 𝑒𝓈𝓂 | 3 𝑒𝓈𝓂 | 6 𝑒𝓈𝓂 |
| Gao et al. [23] | 3 𝑒𝓈𝓂 | 4 𝑒𝓈𝓂 | 7 𝑒𝓈𝓂 |
| Braeken et al. [17] | 4 𝑒𝓈𝓂 | 5 𝑒𝓈𝓂 | 9 𝑒𝓈𝓂 |
| Braeken et al. [19] Scheme 1 | 5 𝑒𝓈𝓂 | 2 𝑒𝓈𝓂 | 7 𝑒𝓈𝓂 |
| Braeken et al. [19] Scheme 2 | 3 𝑒𝓈𝓂 | 4 𝑒𝓈𝓂 | 7 𝑒𝓈𝓂 |
| Braeken et al. [19] Scheme 3 | 4 𝑒𝓈𝓂 | 4 𝑒𝓈𝓂 | 8 𝑒𝓈𝓂 |
| Proposed CB-SN | 3 𝒽𝓈𝓂 | 4 𝒽𝓈𝓂 | 7 𝒽𝓈𝓂 |
| Schemes | Signcryption Generation (SG)(APs) | Unsigncryption (US) (Controller) | Total |
|---|---|---|---|
| Li et al. [22] | 5.13 ms | 31.81 ms | 36.94 ms |
| Omala et al. [15] | 2.91 ms | 2.91 ms | 5.82 ms |
| Gao et al. [23] | 2.91 ms | 3.88 ms | 6.77 ms |
| Braeken et al. [17] | 3.88 ms | 4.85 ms | 8.73 ms |
| Braeken et al. [19] Scheme 1 | 4.85 ms | 1.92 ms | 6.77 ms |
| Braeken et al. [19] Scheme 2 | 2.91 ms | 3.88 ms | 6.77 ms |
| Braeken et al. [19] Scheme 3 | 3.88 ms | 3.88 ms | 7.76 ms |
| Proposed CB-SN | 1.44 ms | 1.92 ms | 3.36 ms |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ullah, I.; Alomari, A.; Ul Amin, N.; Khan, M.A.; Khattak, H. An Energy Efficient and Formally Secured Certificate-Based Signcryption for Wireless Body Area Networks with the Internet of Things. Electronics 2019, 8, 1171. https://doi.org/10.3390/electronics8101171
Ullah I, Alomari A, Ul Amin N, Khan MA, Khattak H. An Energy Efficient and Formally Secured Certificate-Based Signcryption for Wireless Body Area Networks with the Internet of Things. Electronics. 2019; 8(10):1171. https://doi.org/10.3390/electronics8101171
Chicago/Turabian StyleUllah, Insaf, Abdullah Alomari, Noor Ul Amin, Muhammad Asghar Khan, and Hizbullah Khattak. 2019. "An Energy Efficient and Formally Secured Certificate-Based Signcryption for Wireless Body Area Networks with the Internet of Things" Electronics 8, no. 10: 1171. https://doi.org/10.3390/electronics8101171
APA StyleUllah, I., Alomari, A., Ul Amin, N., Khan, M. A., & Khattak, H. (2019). An Energy Efficient and Formally Secured Certificate-Based Signcryption for Wireless Body Area Networks with the Internet of Things. Electronics, 8(10), 1171. https://doi.org/10.3390/electronics8101171






