1. Introduction
Because electronic devices are commonly used to process data, the risk related to the potential for electromagnetic radiation spying and non-invasive data acquisition still exists (
Figure 1) [
1,
2,
3,
4,
5,
6,
7,
8].
This is dangerous because it leaves no trace of “intrusion”, and the loss of data is discovered too late. As newly available data acquisition methods appear, we need new methods to counteract this phenomenon [
9,
10,
11]. This is especially true when a growing number of new technological achievements are used to process data. Currently, it is common to process text data and transmit it to a device for graphic imaging by using the DVI digital standard [
12]. Cathode ray tube (CRT) monitors [
13] have been replaced by liquid crystal (LCD) displays. To allow users to operate a LCD panel in a more comfortable way, it is required to use software technology to improve the appearance of fonts displayed on the screen. Font edge smoothing mechanisms are being introduced in operating systems. Windows OS versions use the ClearType solution. In general, the solution adds specific stains on both sides of fonts. Practical impacts of the abovementioned compromising emanations signals will be presented below.
The risk of electromagnetic information infiltration can appear as a result of electromagnetic fields being generated by an electronic device that processes encoded data in the form of electrical signal changes [
14,
15,
16]. We can minimize the abovementioned risk by:
restricting the potential uncontrolled propagation and reducing the resulting electromagnetic emissions (spatial separation, screening, filtration) [
17];
appropriately forming the sources of those emissions (i.e., by reducing their effectiveness) [
2,
18,
19,
20].
In the first case, the levels of electromagnetic emissions are reduced to levels where any attempt to retrieve data from recorded emissions and present it in a graphical form (images) fails [
21,
22]. Forming a source of compromising emanations without having a significant impact on their absolute values results in losing their distinctive features (correlation with processed information), and thus, the data retrieved from the recorded compromising emanations and presented in graphical form remains illegible and useless (e.g., safe font) [
23,
24]. In this case, another advantage is the opportunity to reduce the energy radiated in the form of an electromagnetic field. This can be achieved by reducing both the changes in signal amplitude and by limiting the range of changes in the values of those amplitudes [
2].
The whole device filtration and screening method is a classic approach, and is the most frequently used method for the electromagnetic protection of processed data [
25,
26]. However, because of the impact on the appearance and weight of devices, we are looking for alternative solutions. For the VGA analogue standard, this protection adopts the form of video signal filtration. This solution has been presented by Kuhn [
1,
3] and by the authors of this paper in the form of the so-called filtration forming module (
Figure 2) [
26].
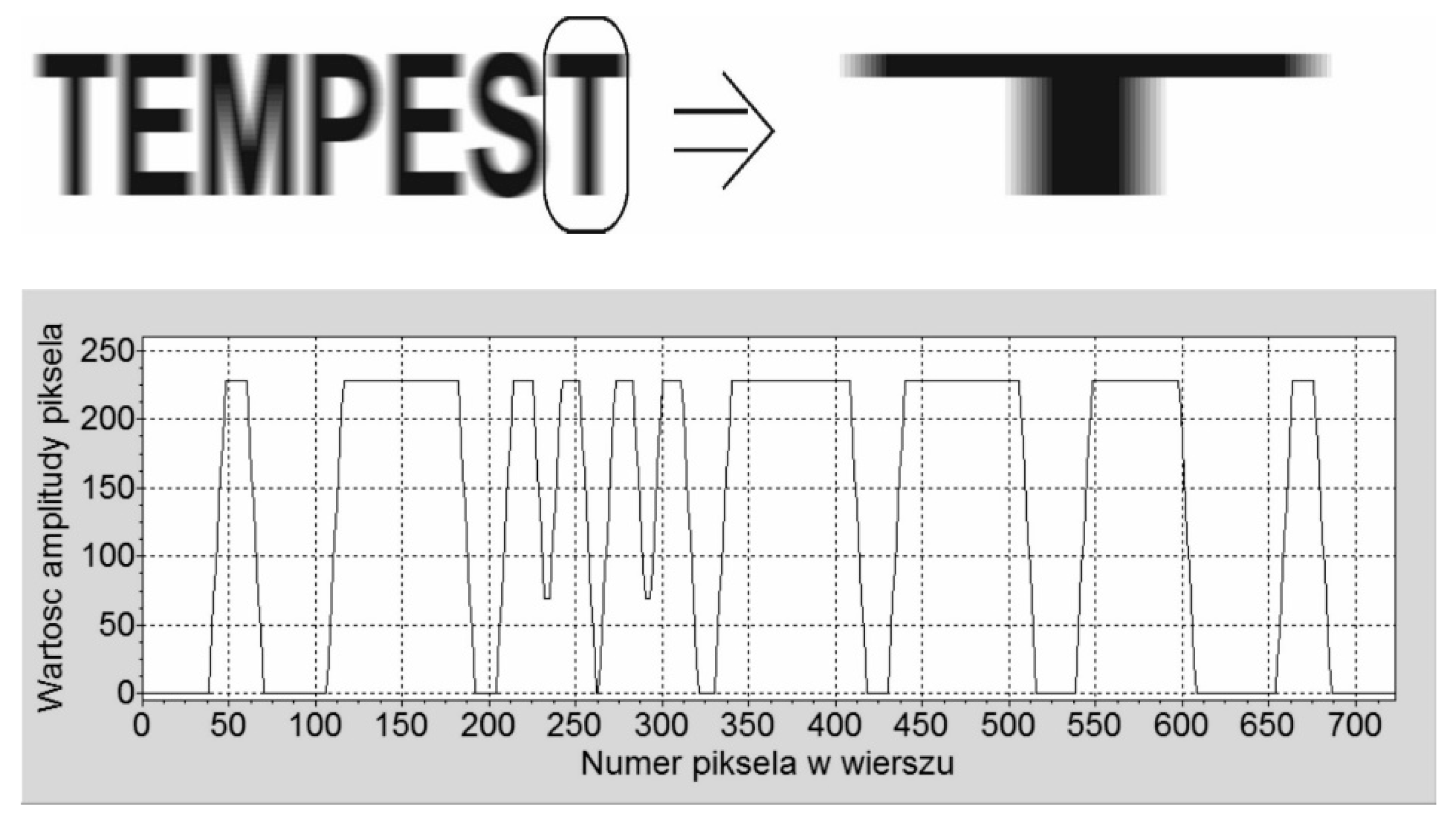
The aim of the abovementioned methods is to limit a signal spectrum by removing higher frequency components. Kuhn suggests removing 30% of the upper spectral frequency components. Those procedures increase the rise and fall time for electrical signals (as observed in the form of electrical signal voltage fluctuations that are subject to significant reduction (
Figure 3)) used to convey the processed information. This solution results in blurred vertical and diagonal edges of fonts displayed on the computer screen. The analogue source (VGA) electromagnetic infiltration process then becomes significantly more difficult (side channel attacks (SCAs) for radiated emissions have the nature of a high-pass filter, where higher components propagate much better. These are the higher components that are mainly responsible for retrieving information).
Similar effects are also obtained when using the abovementioned solution in the form of ClearType or Standard smoothing options. Enabling one of the options results in a slight blur of font edges (soft transition of colors from the background color and the font color for vertical and diagonal edges (ClearType) or only for the diagonal edges (Standard),
Figure 4), which improves the quality of characters displayed on LCD screens. Grey scale discolorations (Standard smoothing mode) or discolorations for various colors (ClearType smoothing mode) are added for this purpose. The smoothing option can be disabled, but only in Windows XP OS, where the procedure is fully effective. When starting from Windows 7 it is impossible to fully disable the font edge smoothing.
The solution involving restricting the video signal spectrum can be used only in VGA analogue standard mode, where a significant signal spectrum limitation will result in blurred characters being displayed, but it will not stop the operation (e.g., by shutting down the monitor). However, this solution is not universal.
Because of changes in electrical parameters combined with the changes in displayed image parameters, it would be necessary to change the filter parameters accordingly, which, consequently, makes the process more difficult to perform. In the case of digital signals, even a slight change in signal parameters may result in final device malfunctions. In the DVI standard, this is expressed by displaying misshaped pixels or by shutting down the monitor [
27].
Another significant method for protecting information includes using specially designed desktop fonts [
10], referred to as secure fonts or TEMPEST fonts. This method is important because of its versatility. The fonts used in electromagnetic protection of processed text data have been found to be effective for VGA, DVI standard, and laser printers [
10,
23,
28]. In addition, they are resistant to the optical character recognition method implemented in the commonly used OCR (Optical Character Recognition) software. The secure fonts are composed of only vertical and horizontal lines of various widths. They do not include any diagonal lines or any kind of decorative components. The characters look similar, yet at the same time are distinguishable and allow text data to be edited. The weak distinctive features of fonts that allow us to tell the difference between them disappear after passing through SCAs. By using a visual analysis (basic method for assessing compromising emanations) supported by correlative analysis, it is impossible to identify individual characters. In spite of the high resistance to electromagnetic infiltration shown by secure fonts, their introduction may face resistance from users caused by the discomfort that may be encountered in the initial stage of use.
The main purpose of this article is to present the risk of the loss of information, which is processed in IT devices using the digital DVI standard. This risk is connected with the possibility of non-invasive data acquisition using valuable emissions, of which the digital standard is a source. Simultaneously, a new solution in the form of the colors method is presented, which could support the protection of processed information. In the case of text data, pairs of colors for texts and backgrounds were selected, which decrease the sensitivity of the source of valuable emissions to electromagnetic infiltration processes.
2. Transition Minimized Differential Signaling (TMDS) Coding
Many ordinary users and IT system administrators share the view that the use of the DVI standard effectively eliminates the risk of electromagnetic information leakage. This belief is related to the fact that DVI is a digital standard that uses digitally encoded signals for transmission, and to decode information it is necessary to recover their original bit structure. However, many results of practical experiments show that the use of the DVI standard does not completely eliminate the risk of electromagnetic eavesdropping.
It should be remembered that the development of the DVI interface was associated with the emergence of modern digital displays, for which there was a need to create an interface for sending broadband signals from a digital source to a digital information receiver. The main purpose of using TMDS encoding and LVDS (Low-Voltage Differential Signaling) transmission was to ensure undistorted, error-free transmission between them. The 8-bit coding used was intended to reduce the level and interaction of electromagnetic emissions arising from changes in signals, but not to encrypt information.
However, as in the case of VGA video signals, it turns out that electromagnetic information capture boils down to recognizing the moment the signal (color information) changes, not its value. An additional consideration is the fact that DVI interface signals are transmitted in accordance with the VGA interface rules (VESA (Video Electronics Standards Association) and Industry Standards and Guidelines for Computer Display Monitor Timing).
Let us take a closer look at the process of creating a DVI signal. The 8-bit data generated in the graphics card is in the following form:
where
ak is 1 or
ak is 0 (
k = 0, ..., 7), also
l = 0, ..., 255, using specific rules (XOR operations, XNOR, bits stuffing) these are processed to 10-bit form, whose examples are shown in the
Table 1. In practice, it is as shown in
Figure 5.
By analyzing the above presented examples for numbers written in TMDS code (
Table 1) that determine display of the abovementioned colors on a screen, we can find that even a slight disorder in its logic sequence can disable its recovery and reading of data from the resulting string of numbers “0” and “1”.
Furthermore, the image obtained from the TMDS algorithm coded signal is almost invisible to the eye, which confirms that the example image is subject to TMDS coding, as shown in
Figure 6a. Its form after coding (see computer simulation), and subsequently after recovering from the resulting original signal, is presented in
Figure 6b. Any attempts to read the processed text fail.
However, this does not mean that TDMS encoding (i.e., DVI standard) is resistant to electromagnetic radiation spying [
1]. An electrical signal in the form of zeroes and ones arranged in sequence is a source of compromising emanations.
The radiated emission propagates in the space around the source and is subject to SCA (i.e., a filter acting the same way as a high-pass filter). As a result of such original signal distortions, the high-pass filtration of the (TMDS) coded signal, and the effect of the reception band of the measuring receiver (signal module), the form of compromising emanations becomes fully usable in the process of electromagnetic infiltration [
29].
Figure 7 presents the image obtained from the signal shown in
Figure 6b subjected to the abovementioned operations (calculating the derivative, i.e., the operation equal to the effect of a high-pass filter and calculating a signal module). The above-presented example shows that the transition of a coded video signal compliant with the TMDS algorithm through SCA makes it invisible to the human eye without having to decode the digital signal. Therefore, the DVI standard, similar to the VGA standard, must be subject to electromagnetic protection, contrary to belief regarding its security.
3. Materials and Methods
3.1. Theoretical Analysis
Most commonly, confidential information takes the form of text data. Typical applications, including MS Office with Word text editor, are used to process the data. Processing means editing, saving, and printing the text by using mainly black characters on a white background. However, the combinations of color pairs are diverse, and the user can customize them. For the purposes of this study, the color set was limited to the grayscale palette. The test results were supposed to provide an answer to the question of whether the option to choose a font and background color can result in increasing or reducing the level of processed text data electromagnetic protection, and additionally, whether there are any color pairs for which the electromagnetic protection level is higher than for others. The study covers the following two aspects:
The
x video signal bit structure using the TMDS coding for selected number pairs from the interval ranging from 0 to 255 (saturation level for individual colors) is similar. Then, it can be assumed that the value of correlation between
y signals specified at the output of a theoretical SCA will adopt significant values. Computer simulations to determine those pairs for defining the forms of
y compromising emanation signals were performed. The derivative was calculated, covering the
z signal (“0” and “1” strings) to provide it. This signal is generated artificially and consists of doubling each
x signal bit (therefore, the number of bits in the signal is 2
N):
where
n = 0, 1, ..., 2
N − 1, and
presents an integral part by dividing
n by 2. Finally, we obtain the
z string with a doubled number of each bit, as presented in
Table 2.
In practice, this appears as follows:
sequence xn/2 of bits “0” and “1”: {0, 0, 0, 1, 1, 0, 0, 1, 0, 0};
sequence zn of bits “0” and “1” after number of bits has been doubled: {0, 0, 0, 0, 0, 0, 1, 1, 1, 1, 0, 0, 0, 0, 1, 1, 0, 0, 0, 0}.
The derivative from the
z signal is calculated by considering the following conditions:
and
where
N defines the number of original image bits obtained in TMDS coding of each pixel of the abovementioned image containing the processed data.
3.2. Experimental Setup and Measurement Procedure
In order to verify the hypothesis presented above, the DVI standard signals corresponding to the text presented on the monitor screen were subjected to both theoretical analysis and practical experiments. In the first stage of operations, the purpose of these verifications was to check whether DVI standard signals could be a source of electromagnetic compromising emanations. The second stage involved checking whether the quality of these signals can be influenced by the appropriate selection of background and font colors, as well as the smoothing option.
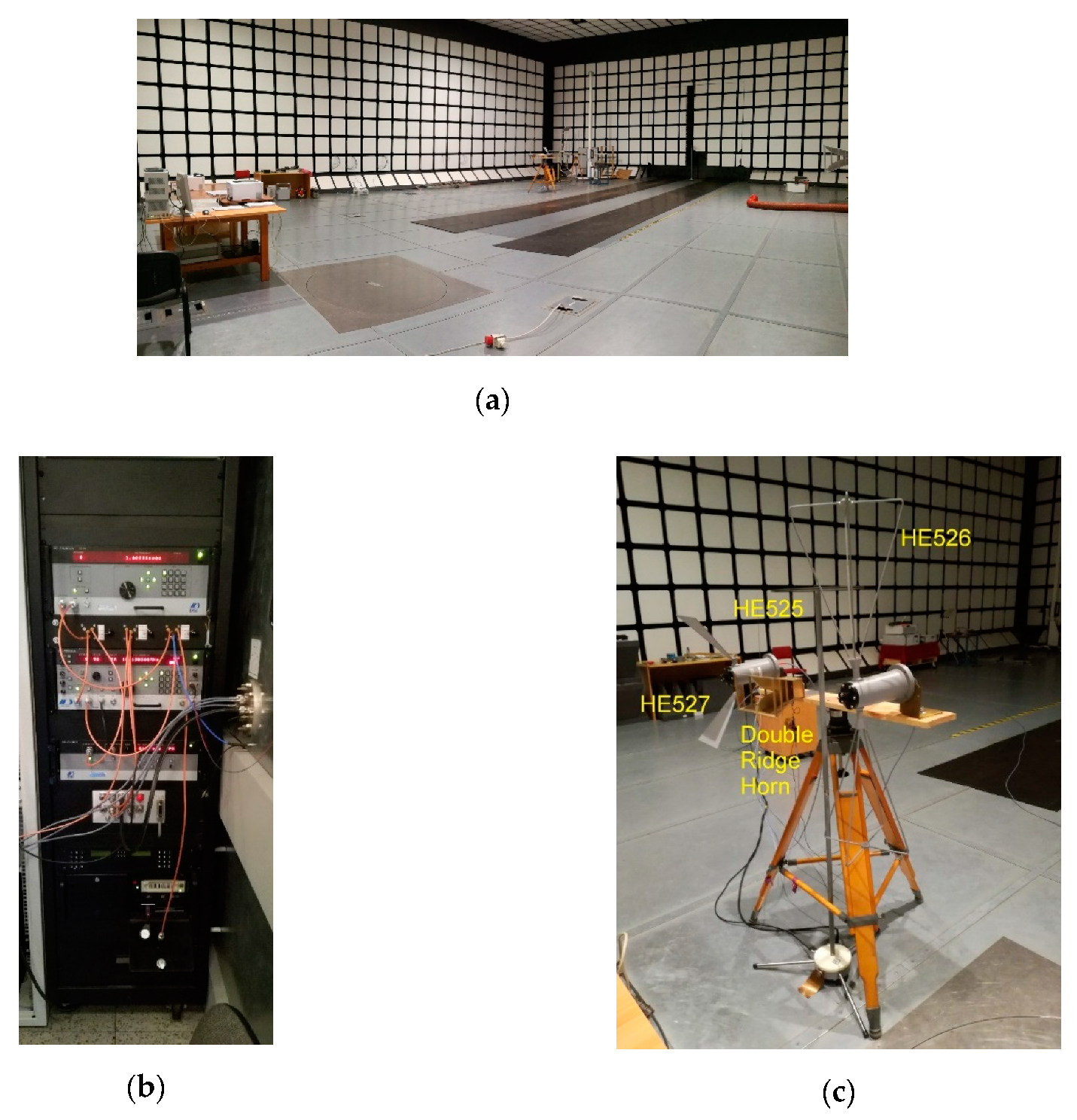
Practical experiments were carried out in an anechoic chamber (
Figure 8a), in which shielding in the frequency range from 1 MHz to 10 GHz ensures suppression of external electromagnetic fields at the level of 100 dB. In this case, only emissions with DVI standard as the source were measured. The electromagnetic emissions arising due to the operation of the DVI interface were recorded using the DSI-1550A receiver (
Figure 8b), along with a DSI-1580A microwave downconverter (up to 22 GHz) and a set of R&S (Rohde and Schwarz) AM524 low-noise antenna systems (100 Hz–1 GHz). The EMCO double ridge horn antenna with an amplifier was used in the frequency range above 1GHz (
Figure 8c). To visualize received electromagnetic emissions in real time, a hardware raster generator (HRG) was used [
30]. This is an external source of vertical and horizontal synchronization signals used to determine the operating conditions of the monitor, whose video path is controlled by the received emission [
31]. Additionally, an AD converter Signatec PDA-1000 (up to 1 Gs/s) was used to record the signals being tested. Experiments were carried out using the following measurement bandwidths: 50 MHz, 100 MHz, and 200 MHz. During tests, the monitor and the DVI interface cable were connected to the special (Tempest class) computer central unit (electromagnetically shielded). This allowed us to eliminate the computer impact on the recorded signals of video-signal-correlated emissions [
32,
33,
34]. The data displayed on the monitor included the following text: “protection”. The measurement distance was 1 m and met the requirements presented in document MIL-STD-461G, “Requirements for the Control of Electromagnetic Interference Characteristics of Subsystems and Equipment”.
The authors carried out many tests relating to the safety of digital video standards. Such tests lasted a very long time, often taking several days. During these tests, frequencies of valuable emissions were searched. The quality of the signals and possible reconstruction of the information were considered. Attempts at reconstruction of information were realized in real time using a hardware raster generator (HRG). The HRG was the source of the vertical and horizontal frequencies that allowed primary information to be reconstructed. The selected valuable emissions were recorded. Next, the signals were used to reconstruct information (for this purpose, a software raster generator was used) in the form of images, which were included in this paper.
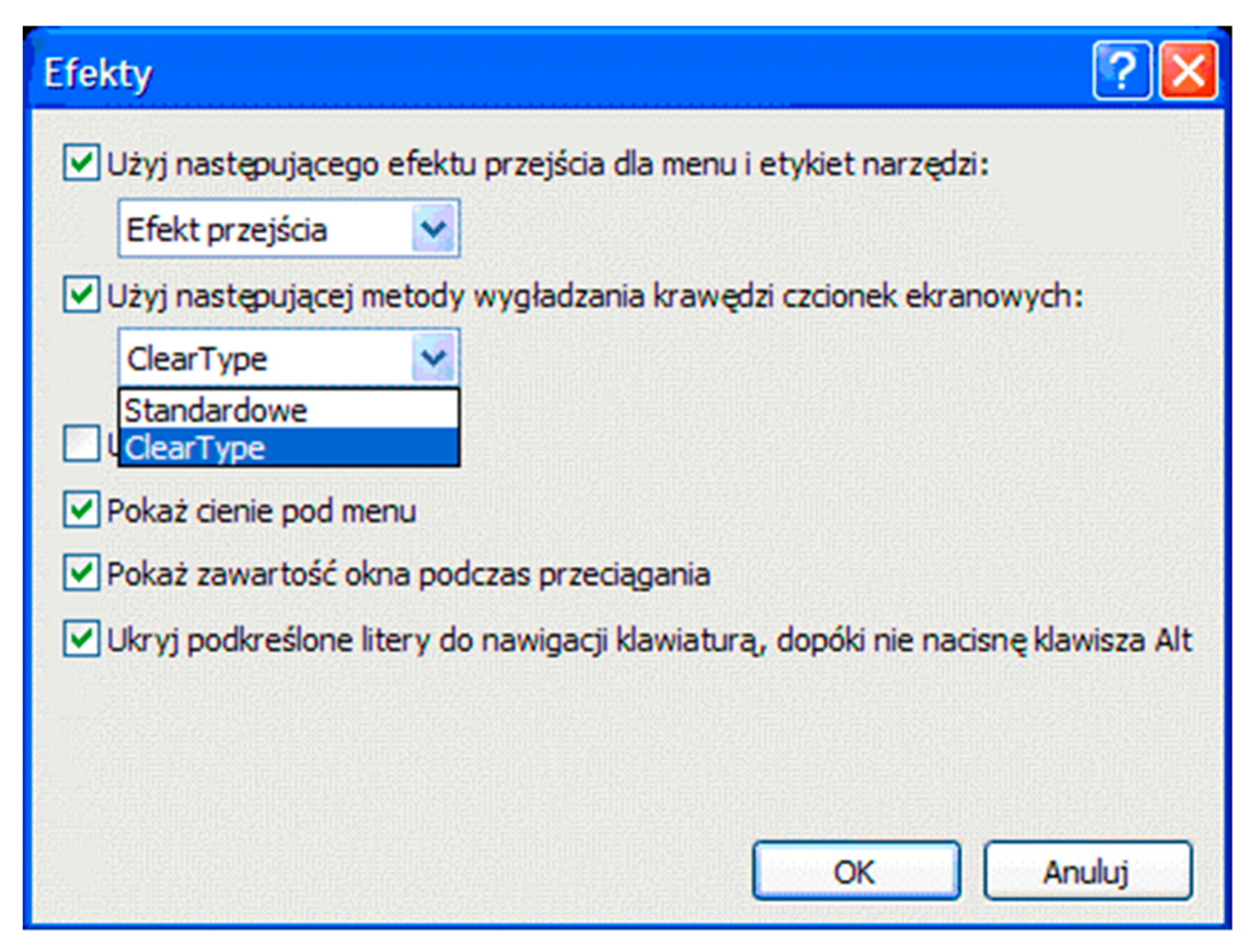
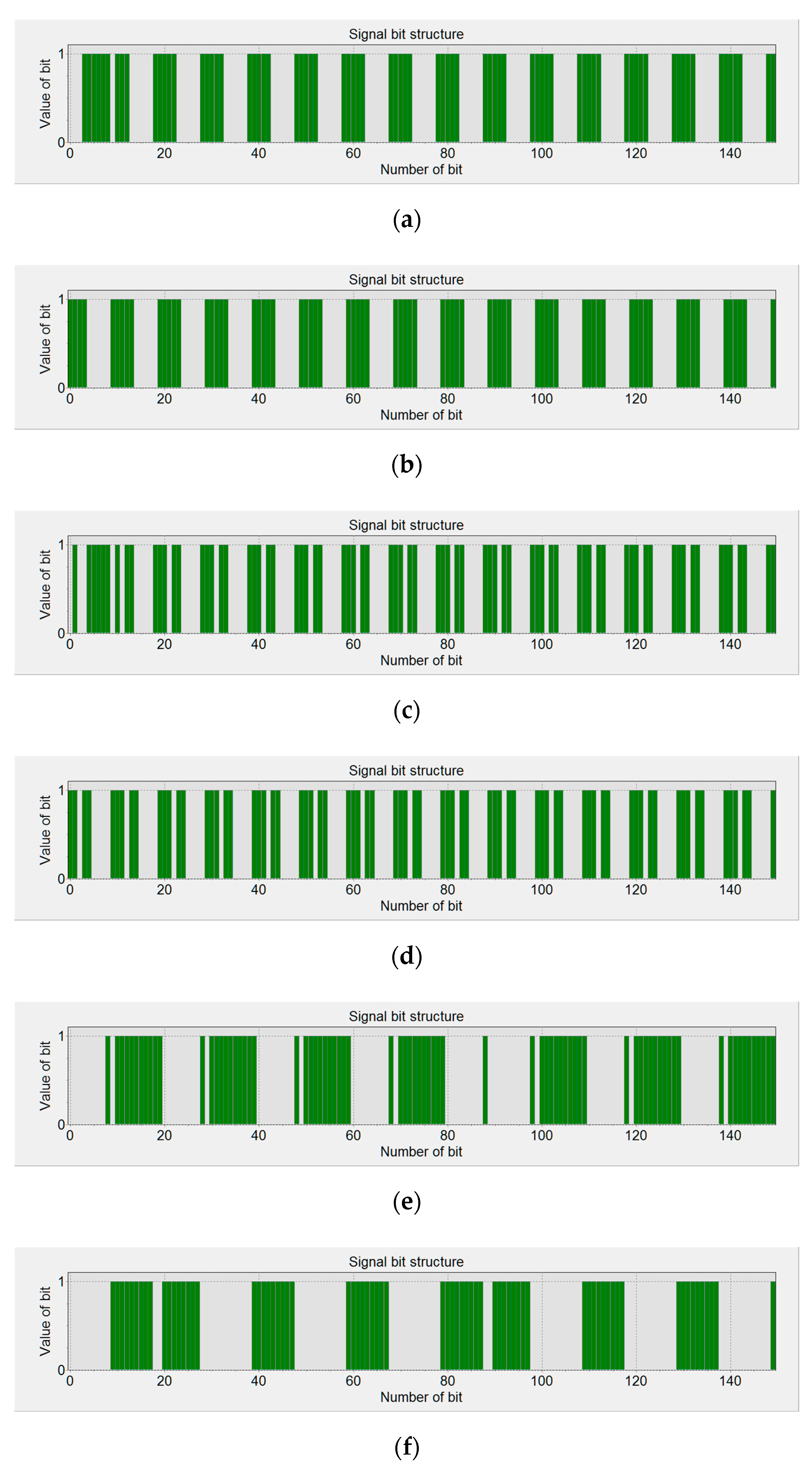
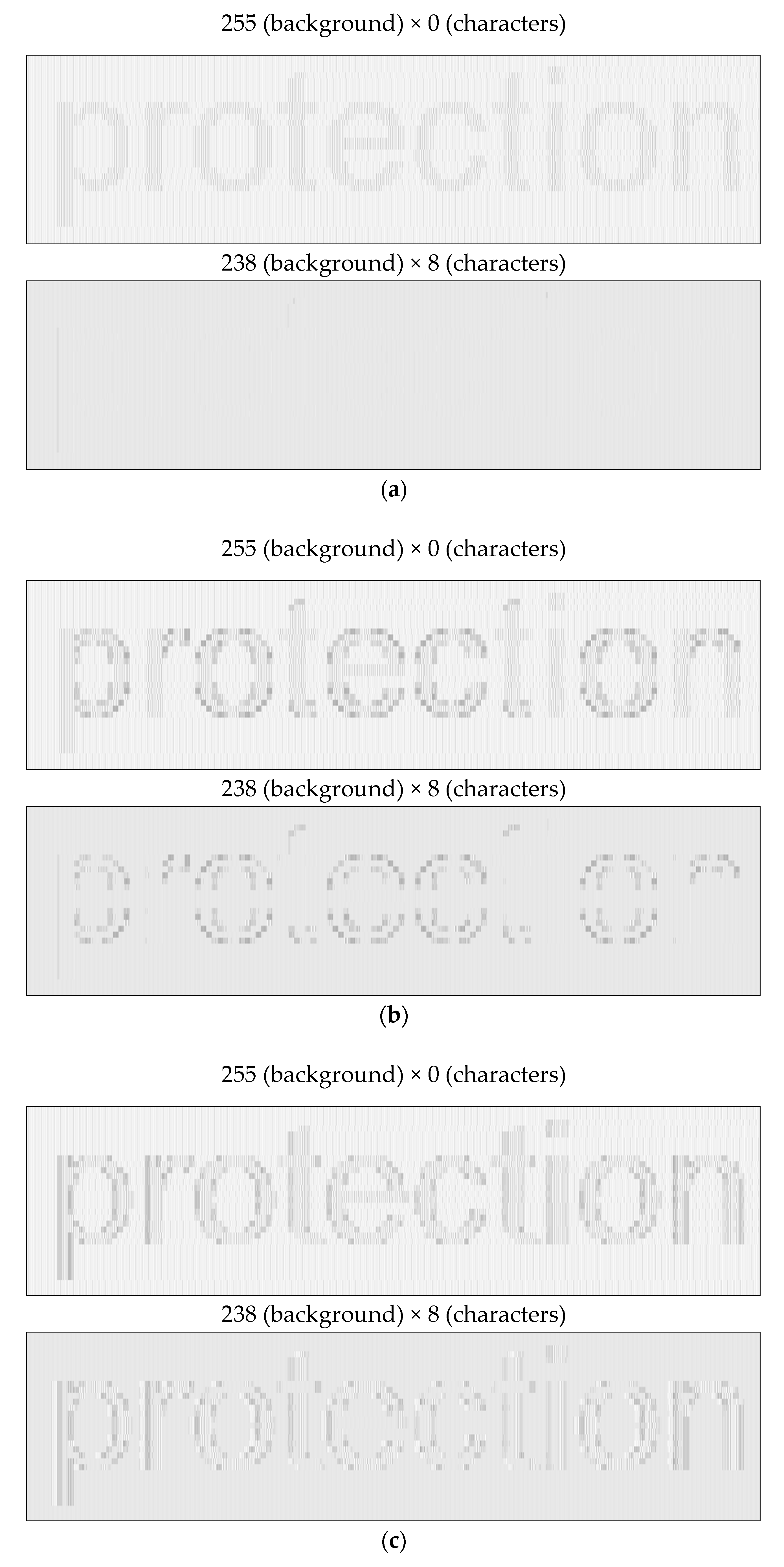
Tests were performed for three letter character display modes in Windows XP OS, using the following options: Standard, ClearType, and without smoothing (
Figure 4). Displaying text data in Standard and ClearType modes is the same for Windows 7, 8, and 10 operating systems.
It is worth noting the reason for introducing the font edge smoothing. This procedure is intended to improve the sharpness of characters displayed on a monitor. In addition, its purpose is to save printing materials. Edges in other colors (ClearType mode) are displayed by compromising individual character components (
Figure 4a), which in the smoothing mode are printed clearly in black. By contrast, the Standard mode replaces some black pixels (only diagonal lines) with grayscale pixels, which also results in lower printing material consumption.
5. Discussions
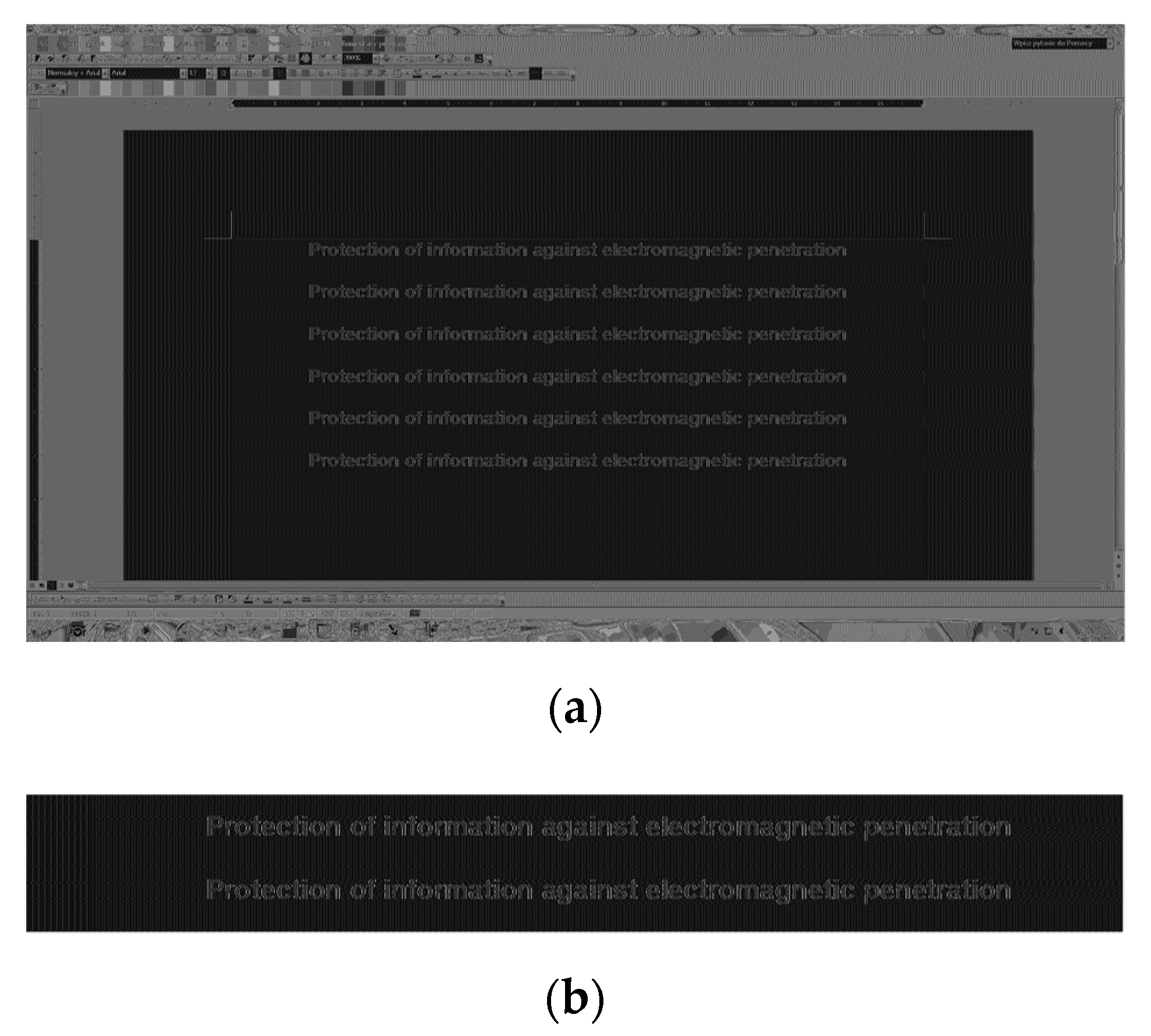
The retrieved images show that theoretical analysis results are only partially confirmed when compared to reality (
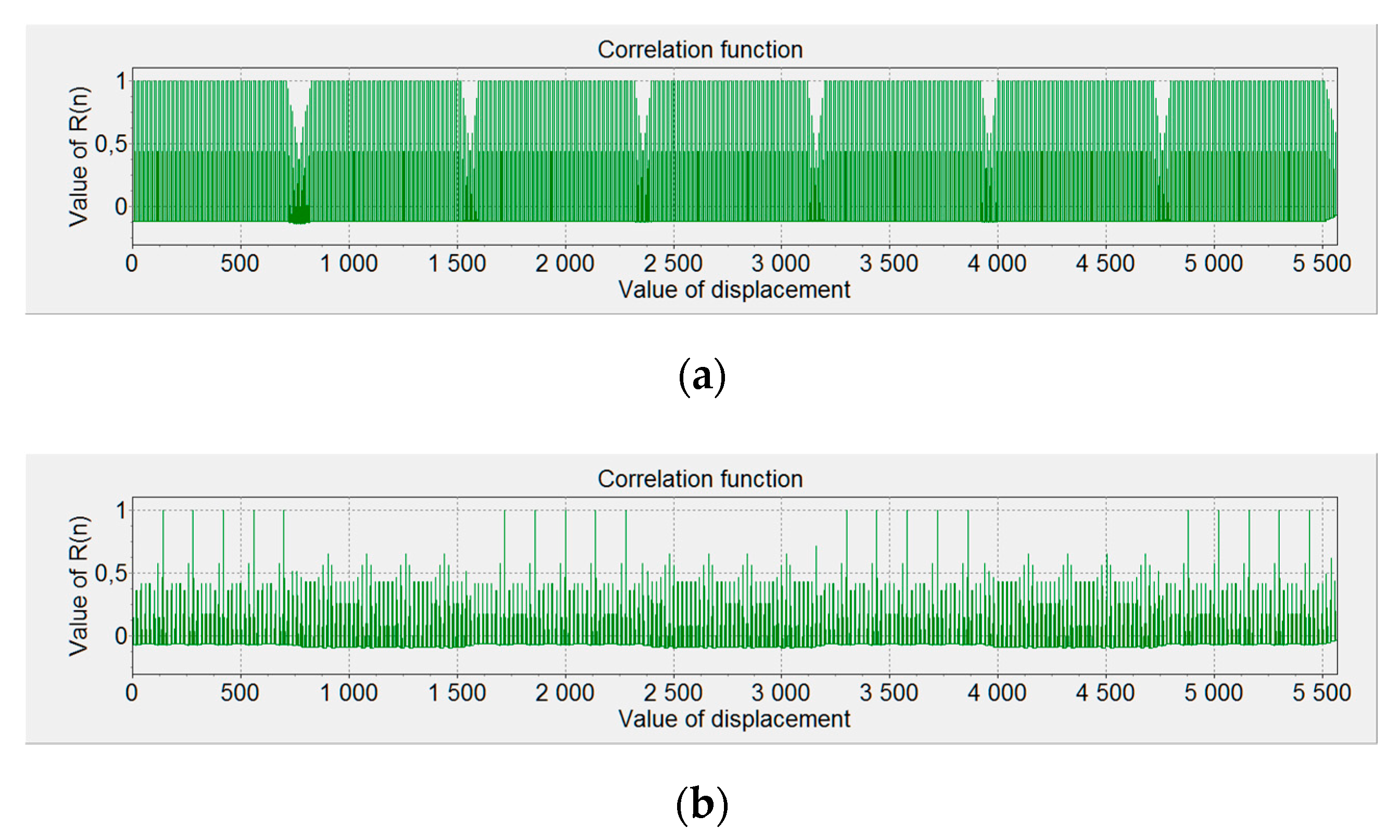
Figure 14b). The selection of color pairs does not provide an effective protection when using DVI standard against electromagnetic infiltration within the entire frequency range analyzed for the occurrence of electromagnetic emission signals. In addition, the use of font edge smoothing features can effectively reduce the level of electromagnetic protection covering the processed data. It is important that in the most recent and commonly used Windows operating systems (version 7, 8, and 10), the option of smoothing the font edges cannot be entirely disabled. The ClearType option is enabled as standard, which is especially exposed to electromagnetic infiltration, regardless of the color pair used. Initializing the Standard edge smoothing option highlights only the diagonal edges. This is because of the fact that no vertical edges are smoothed (as opposed to the ClearType smoothing option). Then, the colors for a selected pair (e.g., with values of 238 and 8) border directly on each other (as in the cases of fonts without edge smoothing—the first text line), while their bit structure is tightly correlated.
Moreover, as mentioned above, appropriate pairs of background and font colors can support the electromagnetic protection, because of their high correlation coefficient and SCA effect. For many frequencies where compromising emanations occur, some selected pair colors make it impossible to acquire information in a non-invasive way (
Figure 14b). The reason for this is the complexity of the radiating system, including the signal cable connecting the CPU with the monitor and the electronic monitoring systems. The impact of the radiating system’s geometrical arrangement on its radiation profile is very complex. Thus, the effectiveness of system radiation for various frequencies is different.
For instance, for color pairs with values of 255 and 0, the correlation value is very low. In this case, the set of frequencies where the compromising emanations occur is numerous. For the frequency 642 MHz, compromising emanations were recorded that allowed retrieval of the image, as shown in
Figure 17. However, for the same frequency with the color pair of 238 and 8, the retrieved data are completely invisible (see
Figure 14b, the first text line).
For DVI standard, using the TMDS coding algorithm means that the color pairs are no longer available. In the case of analogue VGA standard, this solution reduces the video signal amplitude jump, thus, reducing the effect of energy radiation in the form of electromagnetic waves [
2]. However, this refers only to ClearType smoothing (the third image line in
Figure 18), as only this option makes it possible to also smooth the vertical edges of fonts.
6. Conclusions
This paper presents the results of security studies and analyses for the DVI digital standard in processing sensitive information. Preliminary theoretical analyses confirmed that the DVI standard as the source of valuable emissions is very sensitive to eavesdropping processes. Images were presented that were reconstructed during computer simulation based on real video signals, which corresponded to images displayed on an eavesdropping screen. In this case, it was shown that the digital DVI standard is not safe from the viewpoint of protection of information must electromagnetic penetration. To increase the security level of this standard, different methods have be used. As an effective method involves using specific color pairs. The font edge smoothing options implemented in Windows operating systems were assessed for their level of effectiveness in the process of electromagnetic infiltration. The security of different standards using video signal coding according to the TMDS algorithm was related to the bit structures for two colors (from a grey scale palette), showing that the background and characters should be very similar. At the same time, the colors corresponding to those color bit structures have to provide sufficient contrast between the background and characters to make them distinguishable on a computer screen.
The conducted analysis of background–font color pairs using the mutual correlation coefficient value identified which color pairs can effectively increase the level of electromagnetic protection. This level of protection is elevated directly by limiting the number of sensitive emission frequencies. The color pairs that can affect the electromagnetic protection include the colors with the following values: 238 and 8, 210 and 22, 216 and 19, 198 and 28, 232 and 44. Further pairs could be listed, appropriate contrast between colors must be considered to make it easier to write the text.
In addition, it has been shown that font edge smoothing solutions used in Windows OS significantly impair the level of resistance to electromagnetic radiation spying. The feature of font smoothing extends the set of colors used to build fonts at the border of the background and the character, softening the transitions between colors.
As the color method is not fully effective, this method only limits the number of frequencies in which sensitive emissions appear. Likewise, the DVI standard also is not completely safe, so alternative methods need to be researched. The authors of this paper propose the use of safe fonts. However, this solution needs to be analyzed together with graphic options for Windows, Linux, or Mac OS.