Abstract
One of the three main use cases of the fifth generation of mobile networks (5G) is massive machine-type communications (mMTC). The latter refers to the highly synchronized accesses to the cellular base stations from a great number of wireless devices, as a product of the automated exchange of small amounts of data. Clearly, an efficient mMTC is required to support the Internet-of-Things (IoT). Nevertheless, the method to change from idle to connected mode, known as the random access procedure (RAP), of 4G has been directly inherited by 5G, at least, until the first phase of standardization. Research has demonstrated the RAP is inefficient to support mMTC, hence, access control schemes are needed to obtain an adequate performance. In this paper, we compare the benefits of using different filtering methods to configure an access control scheme included in the 5G standards: the access class barring (ACB), according to the intensity of access requests. These filtering methods are a key component of our proposed ACB configuration scheme, which can lead to more than a three-fold increase in the probability of successfully completing the random access procedure under the most typical network configuration and mMTC scenario.
1. Introduction
The first phase of standardization for the future 5th generation of mobile networks (5G) was concluded in the Release 15 of the 3GPP Evolved Universal Terrestrial Radio Access (E-UTRA) specifications [1]. Previous mobile generations, 3G and 4G, have merely focused on providing a faster and better mobile broadband service. Instead, 5G relies on three main use cases: massive machine-type communication (mMTC), enhanced mobile broadband (eMBB), and ultra-reliable low-latency communication (URLLC). The support for mMTC and URLLC are the main distinctive characteristics of 5G, and are expected to enable a great number of novel applications. These include, among others, the Internet-of-Things (IoT), where every daily-life object is connected to the Internet to empower a wide range of functionalities.
Nevertheless, the Release 15 of the 3GPP specifications introduced few advances in terms of mMTC support when compared to Release 14. One of the most critical requirements to efficiently support mMTC in 5G was to introduce enhancements to the random access procedure (RAP) of 4G. The RAP is the method used by user equipments (UEs) to switch from idle to connected mode. In other words, it is the method used by UEs for initial access to the cellular network.
Several studies have demonstrated the inefficacy of the RAP, as defined by the 3GPP [1], to support mMTC in 4G [2,3,4,5]. Specifically, severe congestion can occur when a bulk of UE access attempts occur in a highly synchronized manner. The latter, which is a typical behavior in mMTC applications, is likely to exceed the signaling capacity of the cellular system. Since the RAP remains the same in 5G, the same limitations and problems persist.
Enhancements are expected to be introduced to the RAP in the following standardization phases of 5G. At the present time, it remains uncertain whether these will be sufficient to support mMTC applications efficiently. On the other hand, access control schemes present an appealing solution to congestion. Because of this, a wide range of access control schemes have been proposed in the literature [6,7,8,9,10,11].
One of the most promising access control schemes is the access class barring (ACB); hence, it has been included in the LTE-A Radio Resource Control (RRC) specifications [1]. The ACB scheme redistributes the UE access attempts through time. For this, each UE may delay the beginning of its RAP according to the barring parameters: barring rate and mean barring time. If the barring parameters are correctly configured, sporadic periods of congestion can be relieved in exchange for a longer access delay. This is true even if barring parameters are selected beforehand and remain fixed throughout the congestion period [5,10,12,13]. However, congestion is a transitory phenomenon, so an adequate performance under several conditions can only be obtained by continuously adapting the barring parameters to the intensity of access attempts. Doing otherwise would increase the access delay of UEs during intervals in which no congestion occurs, but also fail to relieve congestion episodes that are more severe than expected. Needless to say, correctly configuring the barring parameters in real-time is a complicated task.
Numerous methods to continuously adapt the barring parameters have been proposed in the literature [9,14,15,16,17,18]; we refer to these methods simply as ACB configuration (ACBC) schemes. In other words, we use the term ACBC scheme to refer to any method or approach to select the barring parameters. In theory, some of the above-mentioned schemes can lead to a near-optimal performance in terms of success probability (i.e., probability of successfully completing the RAP) and access delay. However, most of these ACBC schemes were not designed for 3GPP cellular networks. Specifically, such a high performance is normally achieved by assuming an idealized ACB scheme and by setting extremely precise barring parameters, for which complex processes and bold assumptions are oftentimes needed. As a consequence, most of the ACBC schemes proposed in the literature cannot be implemented in the cellular systems [9,11,14,17].
Tello-Oquendo et al. presented one of the few ACBC schemes that were specifically designed for 3GPP cellular networks [18]. In particular, a reinforcement learning approach was utilized. However, results show that the performance achieved under the most typical mMTC scenario with the proposed ACBC scheme is lower than that of correctly selecting the fixed barring parameters beforehand.
In our previous work, we proposed an ACBC scheme that incorporates a filtering block [19]. In this block, the well-known least-mean square (LMS) algorithm was implemented. In particular, two different applications of the LMS were investigated: the adaptive line enhancer (ALE) and a novel twist on the latter, referred to as “pulling” ALE (PALE) [19]; preliminary work on the benefits of the PALE can be found in [8]. During previous work, we found our ACBC scheme is one of the few that can be implemented in 3GPP networks and that can provide a near-optimal performance, which greatly surpasses that of the ACB with fixed parameters, under different access request intensities [8,19].
The main motivation of the present study is to investigate the potential benefits of our ACBC scheme with different filtering methods, namely, the recursive least-squares (RLS) algorithm or fixed finite-duration impulse response (FIR) filters instead of the LMS. Each of these presents different characteristics in terms of the rate of convergence, numerical stability, and simplicity. Therefore, the main contributions of this paper are described in the following.
- Two different filtering methods are investigated, namely the RLS adaptive algorithm and a FIR filter. The benefits of these methods are compared to those of the LMS. The latter was the only algorithm considered in our previous work [8,19].
- An in-depth analysis of the tracking capabilities of the LMS and RLS adaptive algorithms in transient environments is presented.
We observed several filtering methods lead to an adequate operation of our ACBC scheme under the most typical mMTC scenario. However, the main difference between implementing an adaptive algorithm and a simple FIR filter is that, for the latter method, an additional mechanism is needed to reduce the access delay of UEs in mMTC scenarios that can be handled by the RAP itself. That is, when the intensity of access attempts is low when compared to the capacity of the RAP. Clearly, increasing the access delay of UEs in these cases is not beneficial. On the other hand, such a mechanism is not needed if some adaptive algorithm configurations are implemented.
The rest of the paper is organized as follows. The RAP and the ACB scheme are described in Section 2. Next, our ACBC scheme, the studied filtering methods, and the methodology used to assess the benefits of these methods are explained in Section 3. Our main results are presented in Section 4 and Section 5 concludes the paper.
2. Random Access Procedure (RAP) and Access Class Barring (ACB) Scheme
This section describes the random access (RA) as defined in the 3GPP standards. It comprises the access control and the contention-based RAP [1,20]. Throughout this study, the ACB, as defined in the 3GPP standards [1], is studied and we assume no other access control scheme is implemented. Figure 1 provides a brief description of the RA in 3GPP networks with the ACB scheme.
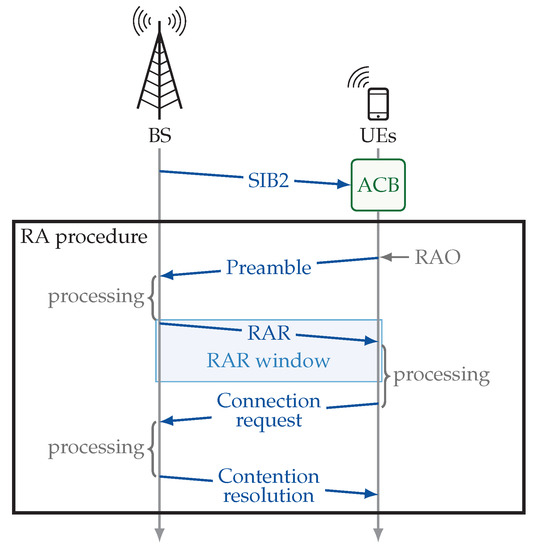
Figure 1.
Random access (RA) in LTE-A: ACB scheme and RAP.
The first step for a UE to switch from idle to connected mode is to acquire the network configuration parameters. Once these have been obtained, the UE is subject to the ACB scheme and, finally, it performs the RAP. The network operates in a time-slotted channel in which the minimum unit for scheduling is the subframe.
The configuration parameters are broadcast by the cellular base station (BS) through the System Information Blocks (SIBs). The SIB1 includes, among other parameters, the periodicity of other SIBs in the parameter ms [1]. The SIB2 includes some basic parameters such as the periodicity of the time/frequency resources in which preamble transmissions are allowed (known as random access opportunities, RAOs) and the barring parameters [1,4,5,21].
The jth SIB2 transmission includes a barring rate and a mean barring time [1]. Only special categories of high-priority UEs may not be subject to the ACB scheme. The rest of the UEs subject to the ACB scheme must perform a barring check before initiating the RAP (i.e., before the transmission of their first preamble) as described in Algorithm 1 [1,22].
| Algorithm 1 Access class barring (ACB) scheme. |
|
UEs that succeed in a barring check are no longer subject to the ACB scheme [23] and proceed to perform the RAP as follows.
Preamble: Each UE randomly selects one out of the r available preambles and sends it towards the BS in a RAO through the random access channel (RACH). Multiple UEs can access the BS in the same RAO using different preambles due to their orthogonality. As a result, BS decodes the preambles transmitted without (wireless channel) errors by exactly one UE.
In this study, we assume the BS cannot decode preambles transmitted by multiple UEs simultaneously; we refer to these as collided preambles. This assumption goes in line with the 3GPP recommendations for the performance analysis of the RACH [2] and with most of the literature [3,14,15,24,25,26,27]. The interested reader may refer to [12] for details on the two main assumptions related to collisions during the RAP and their impact on performance.
Next, the UE waits for a predefined time window, known as the RA response (RAR) window, to receive a RAR message from the BS.
RAR: The BS computes an identifier for each successfully decoded preamble and sends the RAR message through the physical downlink control channel (PDCCH). It includes, among other data, uplink grants for the transmission of the next message, Msg3. Up to one RAR message can be sent per subframe, but it may contain several uplink grants; each of which is associated with a successfully decoded preamble.
The PDCCH resources are limited, so a maximum of uplink grants can be sent within a RAR window. Since up to three uplink grants can be sent per subframe in a RAR message, the number of available uplink grants per RAR window depends on its length.
Connection request and contention resolution: After receiving the corresponding uplink grant, the UEs schedule the transmission of the connection request message (Msg3) to the BS through dedicated resources. Then, the BS responds to each connection request with a contention resolution message (Msg4). The transmission of both of these messages is protected by a hybrid automatic repeat request (HARQ) mechanism.
The maximum number of allowed preamble transmissions for each UE is broadcast by the BS through the SIB2 [1]. Access failure can occur, for example, due to a preamble collision or to wireless channel errors during contention resolution. Whenever an access failure occurs, and if the maximum number of preamble transmissions has not been reached, the UE waits for a random backoff time (determined by the backoff indicator); then, it randomly selects and transmits a new preamble at the next RAO.
3. Access Class Barring Configuration (ACBC) Scheme
This section describes the structure of our ACBC scheme and the configuration of the selected filtering methods. It is important to emphasize our ACBC scheme, first introduced in [8], was designed to operate under the 3GPP specifications, hence, it can be directly implemented in 4G and 5G networks.
Figure 2 illustrates the block diagram that describes the operation of the RAP with our ACBC scheme. Two main blocks are clearly identified in the figure: the RA and the ACBC scheme. The RA, depicted in the upper part of Figure 2, operates as described in Section 2.
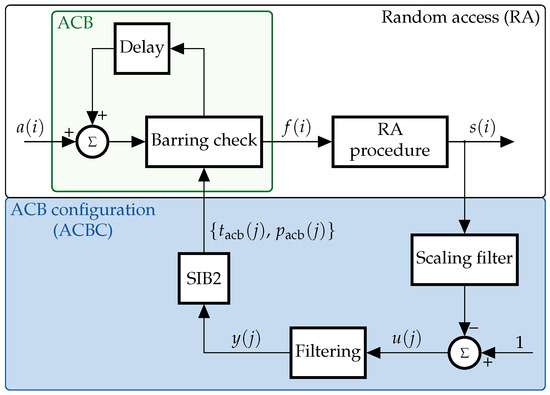
Figure 2.
Block diagram of the RAP with our ACBC scheme. The random access is performed at each RAO, whereas the ACBC can only be performed once every RAOs.
Let be the number of UEs that attempt to switch from idle to connected mode for the first time at the ith RAO; these UEs are subject to the ACB scheme. Hereafter we refer to simply as the UE arrivals.
Next, let be the number of UEs whose barring check at the ith RAO is successful. These UEs begin the RAP at the ith RAO; hence, is also the number of UEs whose first preamble is transmitted at the ith RAO. Finally, is the number of UEs that will receive an uplink grant at the ith RAR window. That is, as a response to a preamble transmitted at the ith RAO. Therefore, the discrete time index i stands for the epoch number. The epoch duration is one RAO since the RA is performed at each and every RAO.
The lower part of Figure 2 depicts the structure of our ACBC scheme, where the BS calculates the barring parameters: mean barring time and barring rate that will be broadcast through the jth SIB2. The SIB2 is broadcast once every RAOs, hence, these parameters are adapted according to the perceived access intensity throughout this period. As such, the discrete time index j stands for the epoch number when the epoch duration is RAOs. Therefore, the ACBC scheme operates at a time scale that is times greater than that of the RA block. Specifically, the jth SIB2 is broadcast at the th RAO. Therefore, the barring parameters remain constant from the th until the th RAO. Throughout this study we assume is selected beforehand and remains fixed throughout the operation of the network. Hence, the latter is simply denoted as . In the following, we describe the process to calculate .
The BS calculates the ratio of idle to available resources immediately before the jth SIB2 transmission. For this, let be the number of contending UEs (i.e., the total number of preamble transmissions) at the ith RAO. Please observe the number of successful preambles at an arbitrary RAO i is a random variable. From there, the theoretical PRACH (uplink) capacity can be defined as the maximum expected value of the latter random variable for a given number of available preambles r and for any . The PRACH capacity is achieved when the number of contending UEs is
and is calculated by Lin et al. [15] as
Next, let be the theoretical capacity of the channels involved in the RAP: PRACH and PDCCH. The capacity of the PDCCH is exclusively determined by the number of available uplink grants per RAR window [2]. Hence, the capacity of the RAP is the minimum between the PRACH capacity and the PDCCH capacity,
We refer to simply as the RAP capacity.
With this information, the ratio of idle to available resources is calculated immediately before the jth SIB2 transmission (i.e., at the th RAO) by means of the scaling filter block and the comparator shown in the bottom right corner of Figure 2 as
where is the column vector of coefficients of the scaling filter
and is the vector that contains the number of uplink grants assigned at each of the RAOs within the SIB2 period. Next, serves as the input to the filtering process, whose output is used to calculate the barring rate for the jth SIB2 broadcast interval
Hence, decreases with the ratio of idle to available resources. This increases the probability of delaying the beginning of the RAP when most of the resources have been utilized.
The filtering block in our ACBC scheme (at the bottom of Figure 2) is generic, which means different filtering methods can be implemented at this point. In the following, we describe three possibilities: two adaptive filtering algorithms and FIR filters with fixed coefficients.
3.1. Recursive Least-Squares (RLS) Algorithm
The RLS is an adaptive algorithm that minimizes the total squared error between its output and the desired response. In particular, it is a recursive implementation of the method of least squares. The RLS can be derived from the least-mean square (LMS) algorithm, described in the next subsection, and is renowned for its fast rate of convergence. For instance, the rate of convergence of the RLS can be up to an order of magnitude faster than that of the LMS. In exchange, its numerical complexity is in the order of , which is higher than that of the LMS. Nevertheless, the mathematical formulation and implementation of the RLS is relatively simple [28].
The internal structure of the RLS algorithm is illustrated in Figure 3. A buffer has been incorporated to clearly illustrate that the ratio of idle resources during the last M SIB2 intervals
is the input to the algorithm. That is, a single value of is the input to the buffer as indicated by the thin arrow, and the output of the buffer is a vector, as indicated by the thick arrows.
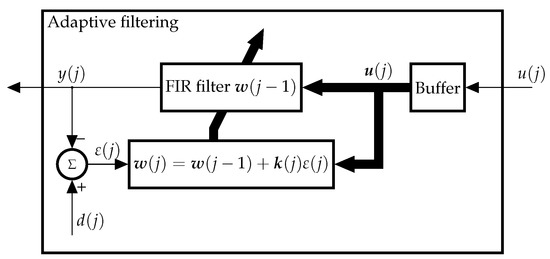
Figure 3.
Block diagram of the RLS adaptive filter algorithm.
The RLS is summarized in Algorithm 2, and consists of a filtering and an adaptive process.
In the filtering process, the output of the FIR filter is computed from .
In the adaptive process, the output is compared to the desired response to adapt the weights of the FIR filter
The parameter is the a priori error, which represents an estimate of the desired response based on the old least-squares estimate of . It is essential to emphasize that is different to the a posteriori estimation error , calculated in the LMS algorithm (see next subsection).
Regarding the configuration of the RLS in our ACBC scheme, the desired response is set to be for all j. By doing so, the RLS algorithm is set to minimize the distance between the output and its maximum value, , which in turn “pulls” the output toward the aforementioned maximum value. This increases the barring rate and, in turn, reduces the access delay of UEs. This effect will be described in detail on page 16.
The RLS algorithm has two parameters that must be selected empirically, the regularization parameter and the forgetting factor . The latter determines the rate at which the effect of the previous inputs on the algorithm is minimised. There is no exact method to select nor . However, the following recommendations exist [28].
- Regularization parameter : Select a small positive value when the input (in our case ) is relatively high with respect to its sudden variations. Select a large positive value otherwise.
- Forgetting factor : Select a positive value that is close to, but less than, 1. This ensures that past the values of the input are forgotten by the algorithm. On the other hand, corresponds to the method of least squares.
The beginning of Section 4 focuses on finding adequate values for and .
| Algorithm 2 RLS adaptive algorithm. |
| Require: the number of filter coefficients M Require: regularization parameter Require: forgetting factor
|
3.2. Least-Mean Square (LMS) Algorithm
The LMS algorithm is widely used because of its simplicity and numerical robustness [28]. Concretely, the complexity of the LMS scales linearly with the filter length M. The LMS is an application of the method of stochastic gradient descent, hence, it belongs to a different family of algorithms to that of the RLS. The internal structure of the LMS is depicted in Figure 4 and Algorithm 3 summarizes its operation.
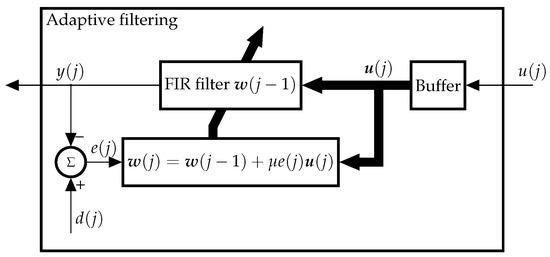
Figure 4.
Block diagram of the LMS adaptive algorithm.
| Algorithm 3 LMS adaptive algorithm. |
| Require: the number of filter coefficients M Require: the adaptation step size
|
As with the RLS, the LMS comprises a filtering and an adaptive process. An important difference between these two algorithms is that the output is compared to the desired response to obtain the error in the LMS, whereas the a priori error is calculated in the RLS.
The correct selection of the rate of adjustment is essential for the LMS to be stable. In particular, the value of must be selected to satisfy
where is the Euclidean norm operator.
Two different configurations of the LMS algorithm are considered: an adaptive line enhancer (ALE) and a “pulling” ALE (PALE). In the ALE, the primary input is a delayed version of , namely , while the desired output is set to . In the PALE, the primary input is simply and the desired output is set to for all j. The latter configuration has a similar effect on the filter output as the one described above for the RLS configuration.
3.3. Simple Low-Pass FIR Filter
Besides investigating the benefits of our ACBC scheme with the two previously described adaptive filter algorithms, we also consider the inclusion of a simple FIR filter with fixed weights . We refer to this as the low-pass filtering (LPF) method.
The filter weights must be chosen to ensure the following two conditions are met.
For this, let be the degree of the decreasing polynomial function that determines the fixed weights of the filter. Naturally, the rapidness of the response of the fixed filter to sudden changes in the input increases with , but so does its sensitivity. In other words, the selection of creates a trade-off between the responsiveness and the stability of the filter output.
In particular, we choose the filter weights as
where is the normalization factor.
3.4. Methodology
In this study, we aim to compare the tracking capabilities of the RLS adaptive algorithm to those of the LMS and simple fixed FIR filters in a transient environment: the traffic model 2 defined by the 3GPP [2]. The latter represents a highly synchronized mMTC scenario, in which the UE arrivals follow a distribution over 10 s. Several studies have confirmed the traffic model 2 leads to severe congestion if no access control scheme is implemented [2,3,4,5,12,13].
Results presented in the following section were obtained by simulation. In particular, a C-based simulator is used, which closely replicates the arrival process of the UEs, the ACB scheme, and the RAP as described in the specifications [1,22]. In each simulation, the adaptive algorithm is initialized and the filter weights are stabilized (if applicable). Then, n = 30,000 UE arrivals are scheduled within the distribution period which begins at . The jth SIB2 is broadcast at the th RAO, where is a discrete random time shift, selected from a uniform distribution between 0 and . A simulation run is concluded when every UE has terminated the RA procedure. The number of simulation runs is set to the smallest number that ensures the cumulative results obtained up to the last simulation differ from those obtained up to the previous simulation by less than percent.
The first step in our analyses is to use a non-synchronized mMTC scenario, the traffic model 1, to identify an adequate configuration of the RLS algorithm. The traffic model 1 can be seen as a stationary scenario of finite duration with a low access intensity, in which UE arrivals follow a uniform distribution over 60 s. As such, the traffic model 1 (stationary scenario) is used to “train” the RLS algorithm to provide an adequate response in a transient scenario. For this, we set the UEs to ignore the ACB scheme and assess two main characteristics: the rate of convergence of the output of the filter and the relative amplitude of its variations with respect to the mean value. It is important to emphasize that similar trial and error approaches to set the configuration of adaptive algorithms are the most common in the practice, especially in transient scenarios [29]. The main characteristics of both traffic models are listed in Table 1.

Table 1.
Characteristics of the different traffic models defined by the 3GPP for the performance evaluation of the RAP [2].
In our experiments, we assume the most typical configuration of the RACH, as suggested by the 3GPP [2]. The number of available preambles is set to ; this is the most typical value for this parameter. Furthermore, it allows us to evaluate the RAP in a scenario in which the number of successful accesses is greatly affected by r, but also by the number of available uplink grants . In addition, we assume the shortest possible period for the SIB transmissions, 80 ms. These values are listed in Table 2, along with other values selected for the most relevant configuration parameters.

Table 2.
Parameters for the selected network configuration.
To assess the benefits of the RLS algorithm, we test several values for parameter and , whereas other configuration parameters remain fixed. For example, is a widely used filter length that led to satisfactory results in our preliminary tests with the RLS algorithm. Furthermore, it is the filter length that maximizes the benefits of the LMS algorithm [19]. Therefore, it is selected throughout the remainder of the paper for every filter.
In addition, we select an intuitive value for the mean barring rate s among those available in the SIB2; as it will be seen throughout the following section, this value leads to a sufficiently high for all the selected filtering methods under the traffic model 2. Certainly, an optimal value for this parameter could be selected, but it is out of the scope of this paper to optimize the performance of each of the studied filtering methods under the selected scenario. Furthermore, selecting a value higher than only causes a slight increase in the access delay when compared to the results presented in this paper. The interested reader may refer to [19], where our ACBC scheme with the LMS algorithm was optimized, and apply an analogous procedure for the RLS algorithm. The configuration parameters for the filtering methods studied in this paper are listed in Table 3.

Table 3.
Parameters for the selected filter configurations.
In particular, we are set to find configurations of the RLS and fixed FIR filters that successfully reduce the variations of with the fastest possible convergence toward . Under the traffic model 1, n = 30,000 UE accesses are uniformly distributed within 60 s. Since RAOs occur once every subframes and the subframe duration is 1 ms, there are = 12,000 RAOs in the distribution period.
Let A be the random variable that defines the number of UE arrivals at an arbitrary RAO within the distribution period. Hence, , shown in Figure 2, is the outcome of a single experiment for random variable A at the ith RAO. Please observe , hence, we have . Since the intensity of access attempts under the traffic model 1 is considerably low when compared to the RAP capacity, the number of successful accesses per RAO highly resembles that of UE arrivals (i.e., , for all i). As a consequence, can be approximated by substituting with , a column vector of length whose entries are , in (5).
which gives for . This value has been confirmed by simulation and by an analytical model [12].
4. Results
In this section, we assess the benefits of our ACBC scheme with different filtering methods. As a starting point, we find adequate values for the regularization parameter and the forgetting factor , which determine the response of the RLS algorithm. Next, we briefly study the response of the LPF method (fixed FIR filters) and of the LMS algorithm. Next, we assess the benefits provided by the different filtering methods under the traffic model 2, when compared to an ACB scheme with fixed parameters (static ACB) and to our ACBC scheme with no filtering (i.e., where ). The section concludes with the comparison of the response of the different filtering methods under the traffic model 2.
Adequate values for parameters and are selected by observing the response of the algorithm. The latter is illustrated in Figure 5 for and , given , along with the calculated . Clearly, the response is not adequate with as presents a drastic drop around , hence, the response of the RLS is not stable. On the other hand, the difference in the response between selecting and is minimal; both of these values of greatly reduce the variations of given a sufficiently low value of is selected, for example, . Figure 5 shows is also an acceptable candidate for the regularization parameter, whereas higher values of should be avoided, as the amplitude of variations of is high when compared to its mean.
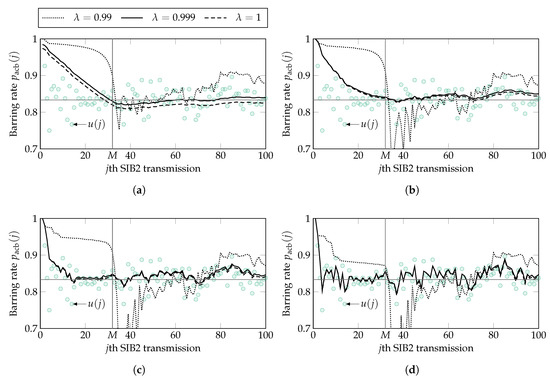
Figure 5.
Ratio of idle to available resources and barring rate calculated at the jth SIB2 for a single simulation run and for the RLS algorithm with and (a) ; (b) ; (c) ; and (d) . The horizontal line is located at .
It has been observed in the literature that parameter plays a similar role in the RLS algorithm as the complement of parameter in the LMS algorithm [28]. In our previous studies we observed is an adequate value for the adaptation step size in our ACBC scheme. Hence, results presented in Figure 5 confirm the relation between and , as an adequate response is obtained with . The latter value of is selected throughout the remainder of the paper, in combination of . As it can be seen, with this combination converges toward around .
Regarding the LPF method, it is immediate to see in Figure 6 that converges toward at exactly for , and the rate of convergence increases slightly with . It is also interesting to observe that the calculated with the RLS, given and , shown in Figure 5b, is highly similar to that of the LPF method. On the other hand, the calculated with the LMS presents a different behavior to both the RLS and LPF methods. For example, and converges toward approximately until .
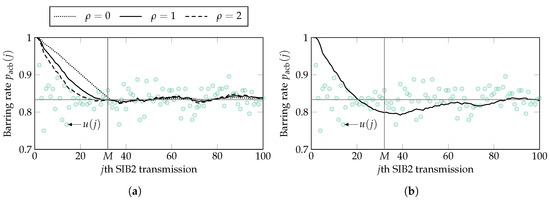
Figure 6.
Ratio of idle to available resources and barring rate calculated at the jth SIB2 for a single simulation run and under the traffic model 1 for the (a) LPF with and (b) the LMS ALE algorithm. The horizontal line is located at .
Next, we investigate whether the difference in the response of the filters provides different benefits to our ACBC scheme. For this, we consider three key performance indicators (KPIs):
- Success probability, defined as the probability to successfully complete the RAP. The minimum success probability considered as acceptable is . Hence, the main goal of our ACBC scheme is to guarantee that more than 95% of the UEs successfully complete the RAP.
- Access delay, defined as the time elapsed since the arrival of a specific UE and the successful completion of its RAP. This KPI is assessed in terms of the 95th percentile. That is, the delay of 95% of the UEs that successfully complete the RAP is lower than, or equal, to the reported value.
- Number of preamble transmissions to successfully complete the RAP. This KPI is assessed in terms of its expected value.
It is important to emphasize that the success probability under the traffic model 2 with no implemented ACB scheme is only , which is poor. In addition, the benefits of our ACBC scheme are minor when no filtering is performed and . Specifically, the success probability with s and no filtering is only , which is still unacceptable. The reason for such a poor performance is that the UE arrivals and the number of successful accesses per RAO present high variations with respect to their mean value. These variations remain present in and, naturally, in . On the other hand, filtering away these variations in leads to a stable that is closely related to the intensity of UE accesses in a larger time scale to that of the SIB2 period.
Figure 7 shows the 95th percentile of access delay and the expected number of preamble transmissions for the studied filtering methods. The success probability obtained with our ACBC scheme with each of the filtering methods included in Figure 7 is higher than , hence, the difference between them, in this KPI, is negligible. In contrast, the success probability under the traffic model 2 without ACB scheme is only . For benchmark purposes, Figure 7 also includes the KPIs obtained with the optimal configuration of a static ACB. The optimal configuration for the latter is defined as the combination of fixed barring parameters that leads to a success probability of or higher with the shortest 95th percentile of access delay. In particular, we found the optimal configuration of the static ACB to be and s, which yields a success probability of .
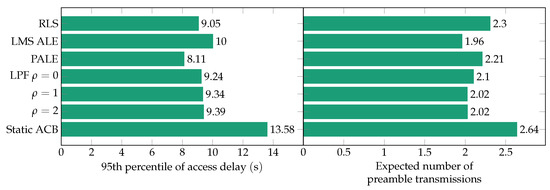
Figure 7.
95th percentile of access delay and expected number of preamble transmissions obtained with our ACBC scheme and with each of the studied filtering methods; the KPIs obtained with the optimal configuration of an ACB scheme with fixed parameters (static ACB) are also included. The success probability for these is higher than .
As it can be seen, regardless of the selected filtering method, the 95th percentile of access delay and the expected number of preamble transmissions are reduced by more than 26% and 12%, respectively, when compared to the optimal static ACB implementation. It can also be seen in Figure 7 that the different values of for the LPF method have a minimal impact on performance. Specifically, the difference in each of the two KPIs shown in the figure for the different valued of is less than 4%.
On the other hand, there is a significant difference between the KPIs obtained with each of the adaptive algorithm configurations. In particular, the ALE leads to the longest access delay but to the lowest number of transmissions, whereas the opposite occurs with the PALE. The RLS leads to an access delay that is in between both LMS configurations, but to the highest number of preamble transmissions. This difference is caused by the “pulling” effect of the PALE and RLS algorithms, which is absent from the ALE.
Figure 8 clearly illustrates the difference in the calculated with the ALE, PALE, RLS, and LPF methods. The number of UE arrivals and successful accesses at each RAO with the RLS algorithm are also illustrated as a reference in Figure 8a. From this figure, it can be seen the number of UE accesses and successful accesses per RAO are highly variable. Furthermore, the number of successful accesses per RAO closely follows that of UE arrivals in the interval . Then, for , the number of successful accesses approaches . This behavior is highly desirable, as it maximizes the utilization of resources and, in turn, reduces the access delay of UEs.
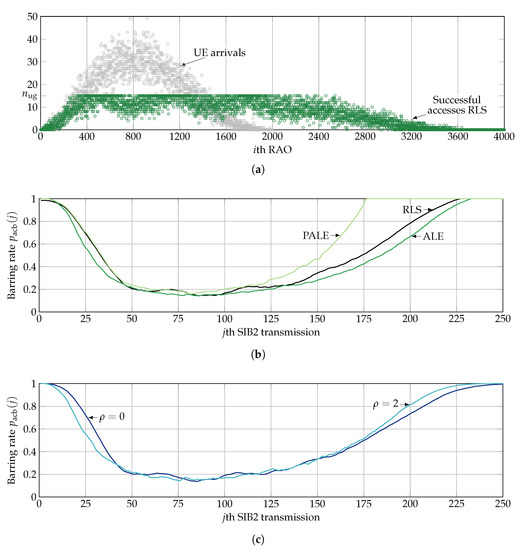
Figure 8.
(a) Number of UE arrivals and successful accesses per RAO with the RLS algorithm, and barring rate calculated at the jth SIB2 for a single simulation run and under the traffic model 2 with the (b) RLS, ALE LMS, and PALE LMS and (c) LPF with . Results derived from a single simulation.
Next, Figure 8b,c exhibit that the LMS algorithm with the ALE configuration operates as a low-pass filter with output . That is, the calculated with the ALE configuration highly resembles that with the LPF method with both . On the other hand, the PALE and the RLS “pull” the latter toward . As a consequence, the calculated with the PALE and RLS are higher than those with the ALE and LPF methods. However, it is important to observe that the “pulling” effect is greater for the PALE than for the RLS. For instance, increases more rapidly for the PALE than for the RLS as the number of UE arrivals drops (i.e., after the 2000th RAO, which corresponds to the 150th SIB2 transmission). The reason for this effect is the rapid response of the RLS, which converges more rapidly toward , calculated with the M most recent values of . As a result, the benefits provided by the RLS are in between those provided by the ALE and the PALE.
On the other hand, the calculated with both is closely similar in the period , and the difference is observed when rapid changes in the number of successful accesses occur. Naturally, the rate of change of with respect of is more rapid for than for . However, this difference is not evident in the 95th percentile of access delay, illustrated in Figure 7.
5. Conclusions
In this paper, we investigated the impact of implementing different filtering methods to our ACBC scheme under a typical mMTC scenario: the traffic model 2. The latter leads to severe congestion when no access control scheme is implemented.
Based on the behavior described in Section 4, it is safe to claim that our ACBC scheme can operate efficiently with several filtering methods, and its performance is compromised only if this process is omitted. That is, when compared to the optimal configuration of a static ACB scheme, our ACBC scheme can reduce the 95th percentile of access delay by more than 26%, while increasing the success probability and reducing the number of preamble transmissions with numerous filtering methods.
One of the main advantages of selecting an adaptive algorithm, such as the LMS and the RLS, is the “pulling” effect provided by setting the desired response to 1. By doing so, the access delay of UEs is further reduced. The latter is of utmost importance under scenarios in which the number of UE accesses is considerably low when compared to the RAP capacity, such as the traffic model 1. In these scenarios, an access control scheme is not needed and increasing the access delay of UEs may be counterproductive. On the other hand, correctly configuring the LMS and RLS algorithms is not straightforward and different methods to reduce the access delay in these scenarios exist. For example, the mean barring time can be set to be a function of the barring rate, hence reducing the barring time as the barring rate increases. Furthermore, if the access delay is not relevant at all, implementing a simple FIR filter in our ACBC scheme would be equally effective as implementing an adaptive algorithm, but the former eliminates the difficulty of selecting correct configuration parameters.
Author Contributions
Conceptualization, I.L.-M., M.A.R.-H. and V.P.; Methodology, I.L.-M. and M.A.R.-H.; Project administration, V.P.; Software, I.L.-M.; Supervision, V.P. and J.M.-B.; Visualization, I.L.-M.
Funding
This research has been supported in part by the Ministry of Economy and Competitiveness of Spain under Grant TIN2013-47272-C2-1-R and Grant TEC2015-71932-REDT. The research of I. Leyva-Mayorga was partially funded by grant 383936 CONACYT-GEM 2014.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Radio Resource Control (RRC); Protocol Specification, 3GPP TS 36.331 V15.3.0; 3GPP: Sophia Antipolis Cedex, France, 2018.
- Study on RAN Improvements for Machine-Type Communications; 3GPP TR 37.868; 3GPP: Sophia Antipolis Cedex, France, 2011.
- Wei, C.H.; Bianchi, G.; Cheng, R.G. Modeling and analysis of random access channels with bursty arrivals in OFDMA wireless networks. IEEE Trans. Wirel. Commun. 2015, 14, 1940–1953. [Google Scholar] [CrossRef]
- Laya, A.; Alonso, L.; Alonso-Zarate, J. Is the random access channel of LTE and LTE-A suitable for M2M Communications? A survey of alternatives. IEEE Commun. Surv. Tutor. 2014, 16, 4–16. [Google Scholar] [CrossRef]
- Biral, A.; Centenaro, M.; Zanella, A.; Vangelista, L.; Zorzi, M. The challenges of M2M massive access in wireless cellular networks. Digit. Commun. Netw. 2015, 1, 1–19. [Google Scholar] [CrossRef]
- Soltanmohammadi, E.; Ghavami, K.; Naraghi-Pour, M. A survey of traffic issues in machine-to-machine communications over LTE. IEEE Internet Things J. 2016, 3, 865–884. [Google Scholar] [CrossRef]
- Wang, Y.P.E.; Lin, X.; Adhikary, A.; Grovlen, A.; Sui, Y.; Blankenship, Y.; Bergman, J.; Razaghi, H.S. A primer on 3GPP narrowband Internet-of-Things. IEEE Commun. Mag. 2017, 55, 117–123. [Google Scholar] [CrossRef]
- Leyva-Mayorga, I.; Rodriguez-Hernandez, M.A.; Pla, V.; Martinez-Bauset, J.; Tello-Oquendo, L. An adaptive access class barring scheme for handling massive M2M communications in LTE-A. In Proceedings of the European Wireless 2017, 23th European Wireless Conference, Dresden, Germany, 17–19 May 2017; pp. 143–148. [Google Scholar]
- Duan, S.; Shah-Mansouri, V.; Wang, Z.; Wong, V.W.S. D-ACB: Adaptive congestion control algorithm for bursty M2M traffic in LTE networks. IEEE Trans. Veh. Technol. 2016, 65, 9847–9861. [Google Scholar] [CrossRef]
- Ferdouse, L.; Anpalagan, A.; Misra, S. Congestion and overload control techniques in massive M2M systems: A survey. Trans. Emerg. Telecommun. Technol. 2015, 28, e2936. [Google Scholar] [CrossRef]
- Abbas, R.; Shirvanimoghaddam, M.; Li, Y.; Vucetic, B. Random access for M2M communications with QoS guarantees. IEEE Trans. Commun. 2017, 65, 2889–2903. [Google Scholar] [CrossRef]
- Leyva-Mayorga, I.; Tello-Oquendo, L.; Pla, V.; Martinez-Bauset, J.; Casares-Giner, V. On the accurate performance evaluation of the LTE-A random access procedure and the access class barring scheme. IEEE Trans. Wirel. Commun. 2017, 16, 7785–7799. [Google Scholar] [CrossRef]
- Tello-Oquendo, L.; Leyva-Mayorga, I.; Pla, V.; Martinez-Bauset, J.; Vidal, J.R.; Casares-Giner, V.; Guijarro, L. Performance analysis and optimal access class barring parameter configuration in LTE-A networks with massive M2M traffic. IEEE Trans. Veh. Technol. 2018, 67, 3505–3520. [Google Scholar] [CrossRef]
- Tavana, M.; Rahmati, A.; Shah-Mansouri, V. Congestion control with adaptive access class barring for LTE M2M overload using Kalman filters. Comput. Netw. 2018, 141, 222–233. [Google Scholar] [CrossRef]
- Lin, T.M.; Lee, C.H.; Cheng, J.P.; Chen, W.T. PRADA: Prioritized random access with dynamic access barring for MTC in 3GPP LTE-A networks. IEEE Trans. Veh. Technol. 2014, 63, 2467–2472. [Google Scholar] [CrossRef]
- De Andrade, T.P.C.; Astudillo, C.A.; Sekijima, L.R.; da Fonseca, N.L.S. The random access procedure in Long Term Evolution networks for the Internet-of-Things. IEEE Commun. Mag. 2017, 55, 124–131. [Google Scholar] [CrossRef]
- Wang, Z.; Wong, V.W.S. Optimal access class barring for stationary machine type communication devices with timing advance information. IEEE Trans. Wirel. Commun. 2015, 14, 5374–5387. [Google Scholar] [CrossRef]
- Tello-Oquendo, L.; Pacheco-Paramo, D.; Pla, V.; Martinez-Bauset, J. Reinforcement Learning-Based ACB in LTE-A Networks for Handling Massive M2M and H2H Communications. In Proceedings of the IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Leyva-Mayorga, I.; Rodriguez-Hernandez, M.A.; Pla, V.; Martinez-Bauset, J.; Tello-Oquendo, L. Adaptive access class barring for efficient mMTC. Comput. Netw. 2019, 149, 252–264. [Google Scholar] [CrossRef]
- Medium Access Control (MAC) Protocol Specification; 3GPP TS 36.321 V15.2.0; 3GPP: Sophia Antipolis Cedex, France, 2018.
- Physical Channels and Modulation; 3GPP TS 36.211 V14.2.0; 3GPP: Sophia Antipolis Cedex, France, 2017.
- Service Accessibility; 3GPP TS 22.011 V13.6.0; 3GPP: Sophia Antipolis Cedex, France, 2016.
- Kalalas, C.; Alonso-Zarate, J. Reliability analysis of the random access channel of LTE with access class barring for smart grid monitoring traffic. In Proceedings of the IEEE International Conference on Communications Workshops (ICC Workshops), Paris, France, 21–25 May 2017; pp. 724–730. [Google Scholar] [CrossRef]
- Leyva-Mayorga, I.; Tello-Oquendo, L.; Pla, V.; Martinez-Bauset, J.; Casares-Giner, V. Performance analysis of access class barring for handling massive M2M traffic in LTE-A networks. In Proceedings of the IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Arouk, O.; Ksentini, A. General model for RACH procedure performance analysis. IEEE Commun. Lett. 2016, 20, 372–375. [Google Scholar] [CrossRef]
- Zhang, Z.; Chao, H.; Wang, W.; Li, X. Performance analysis and UE-side improvement of extended access barring for machine type communications in LTE. In Proceedings of the IEEE 79th Vehicular Technology Conference (VTC Spring), Seoul, Korea, 18–21 May 2014; pp. 1–5. [Google Scholar] [CrossRef]
- Cheng, R.G.; Chen, J.; Chen, D.W.; Wei, C.H. Modeling and analysis of an extended access barring algorithm for machine-type communications in LTE-A networks. IEEE Trans. Wirel. Commun. 2015, 14, 2956–2968. [Google Scholar] [CrossRef]
- Haykin, S. Adaptive Filter Theory, 4th ed.; Prentice Hall: Upper Saddle River, NJ, USA, 2002. [Google Scholar]
- Widrow, B.; Glover, J.R.; McCool, J.M.; Kaunitz, J.; Williams, C.S.; Hearn, R.H.; Zeidler, J.R.; Dong, J.E.; Goodlin, R.C. Adaptive noise cancelling: Principles and applications. Proc. IEEE 1975, 63, 1692–1716. [Google Scholar] [CrossRef]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).