Block-Cipher No-Hit-Zone Sequence-Assisted Spectrum Control Scheme for Distributed Systems
Abstract
1. Introduction
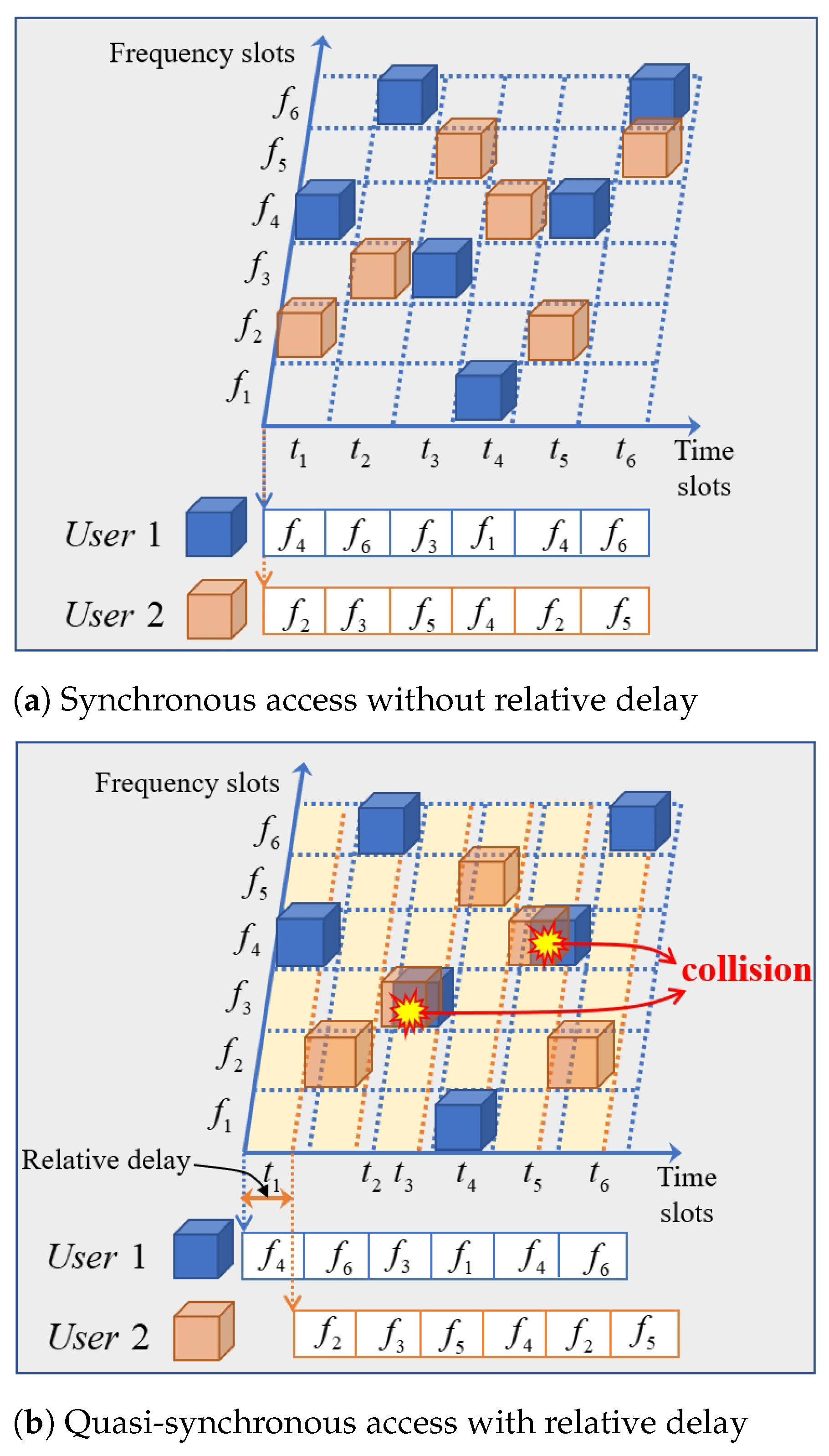
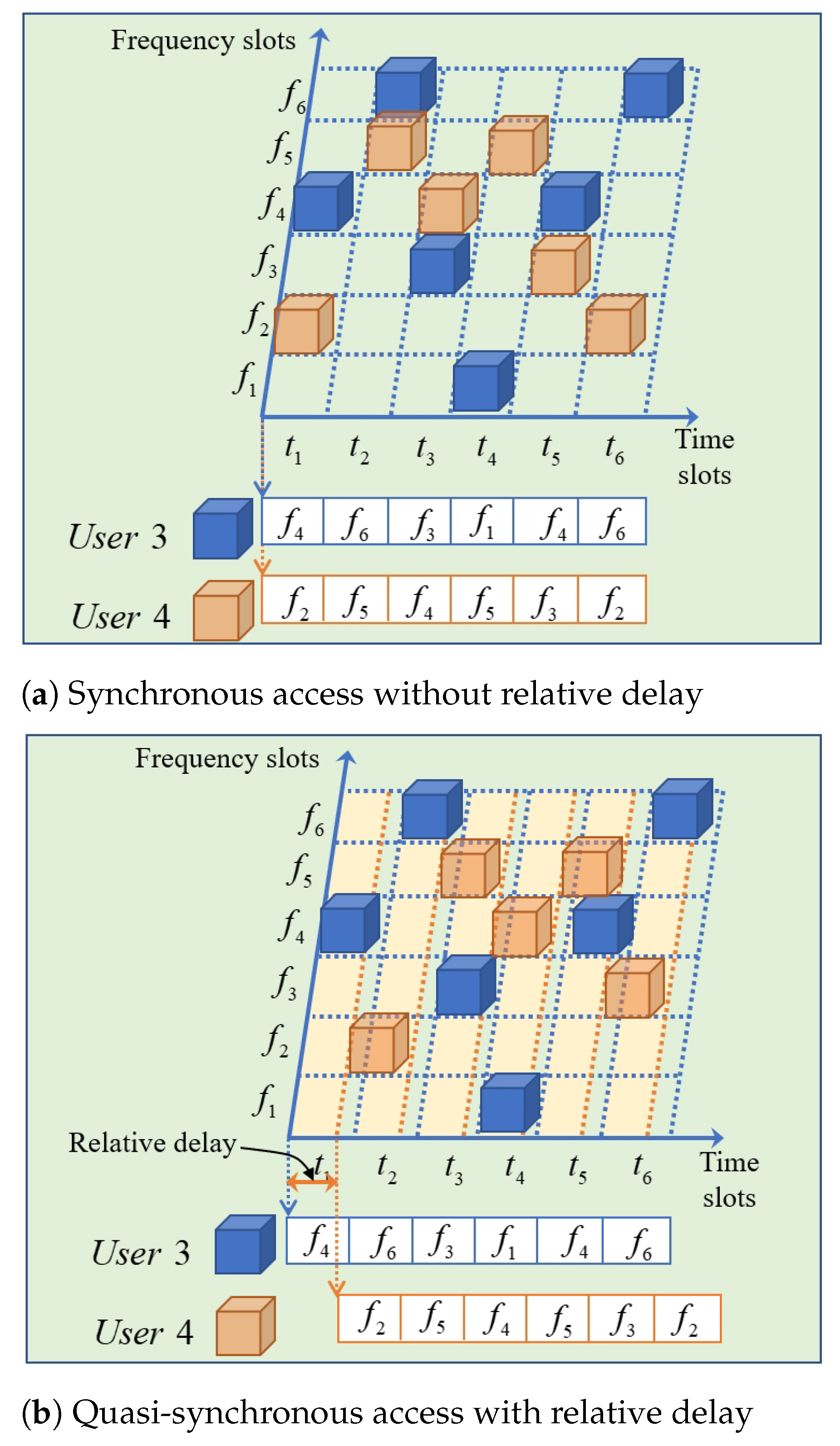
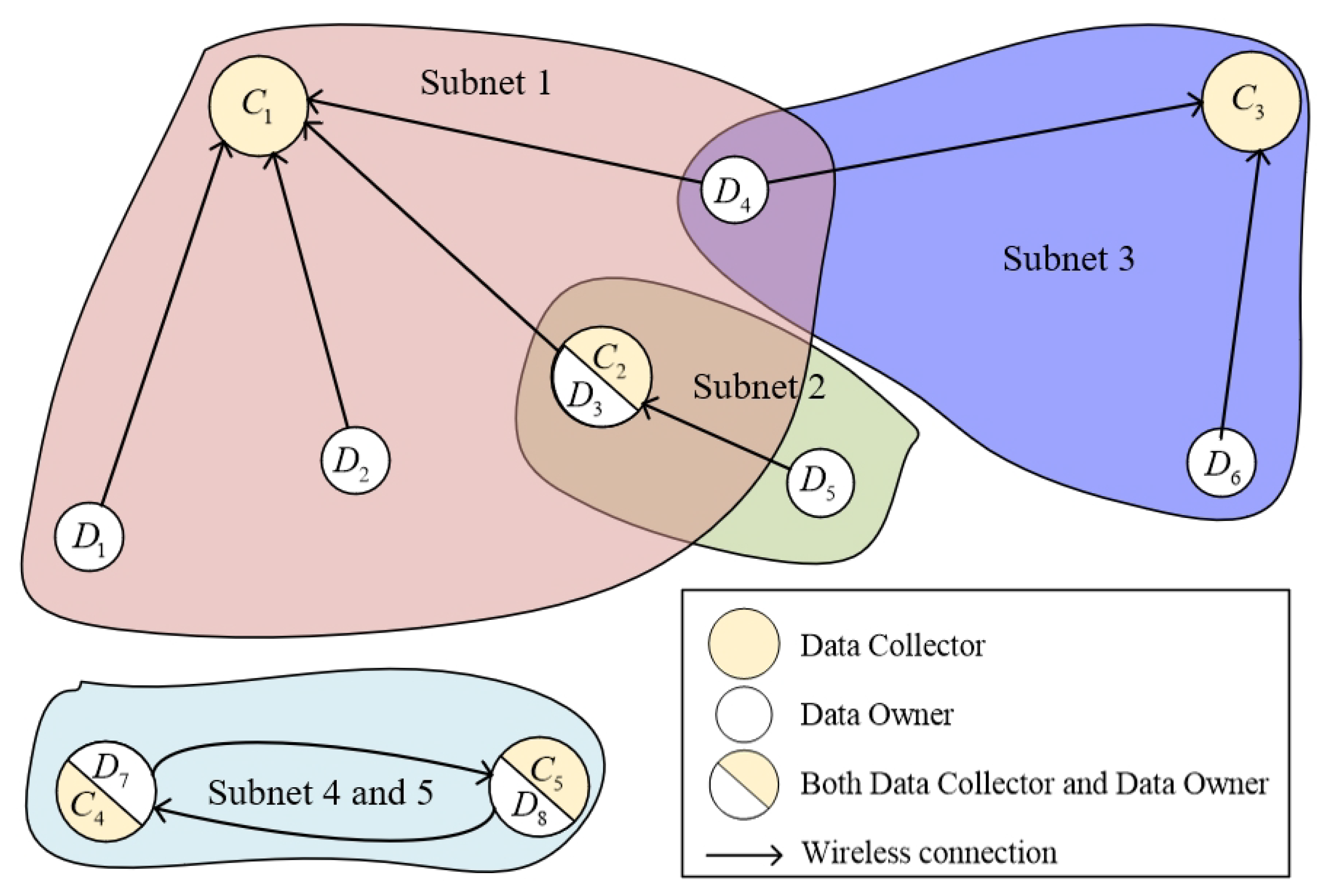
- DS Communication Network Architecture: We propose a DS communication network architecture consisting of multiple devices that dynamically adjust spectrum allocation schemes using control sequences. The network model supports quasi-synchronous access and tolerates signal-relative delay at the receiver. Each device accesses spectrum resources through its own control sequence, ensuring flexible and efficient utilization of the spectrum.
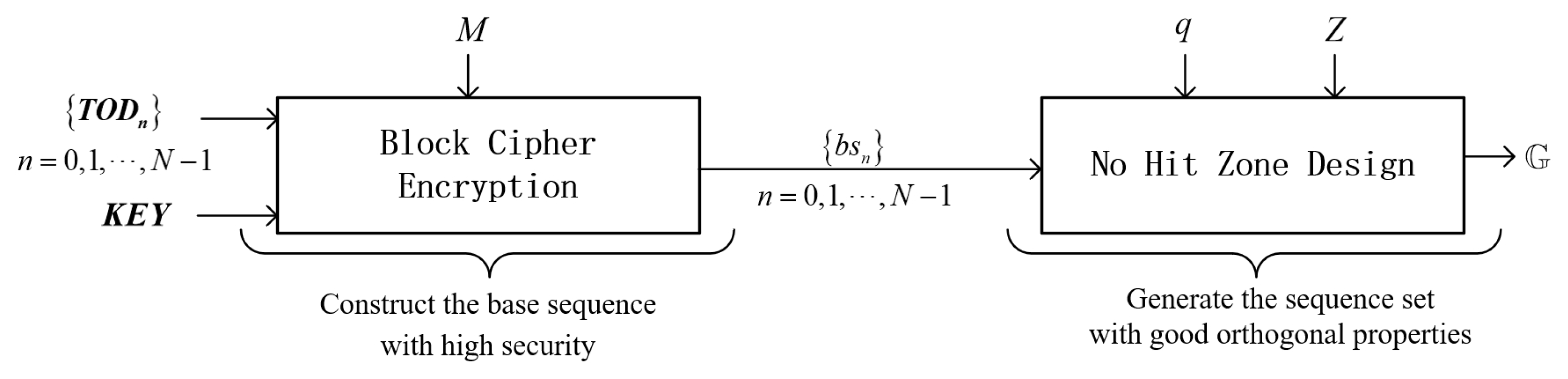
- BC-NHZ sequence-assisted spectrum control scheme: The novel BC-NHZ scheme is introduced, leveraging block cipher encryption to construct a secure NHZ sequence set. This scheme provides robust privacy protection, making the spectrum utilization scheme resistant to deciphering by non-cooperative entities. Additionally, it ensures communication spectrum orthogonality and effectively mitigates MAI among distributed devices, even under conditions of relative delay.
- Performance Analysis and Validation: The performance of the proposed scheme is analyzed through mathematical reasoning and validated via simulation. The results demonstrate that the proposed approach outperforms baseline methods in terms of complexity and network capacity. This makes the BC-NHZ scheme well-suited for DS communication networks, particularly for ensuring high communication quality and privacy protection in decentralized devices with terminal access.
2. Related Work
3. Preliminaries
3.1. Definition of No-Hit Zone
3.2. System Model
3.3. Complexity Metric
4. The Block-Cipher No-Hit-Zone Sequence Set
4.1. The Construction of BC-NHZ Sequence Set
4.2. Parameter Optimality Analysis
4.3. A Numerical Example of BC-NHZ Sequence Set
5. Simulation Results
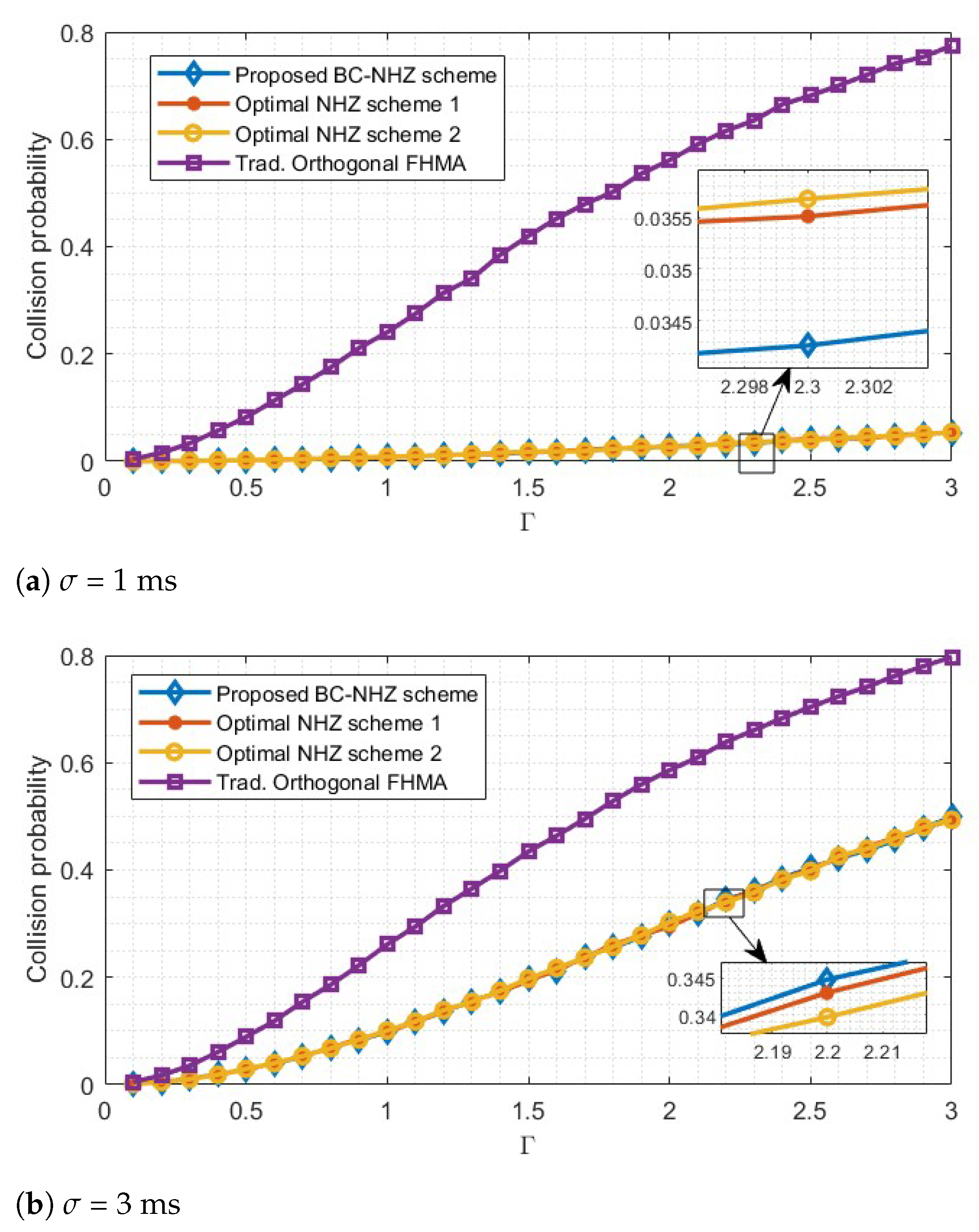
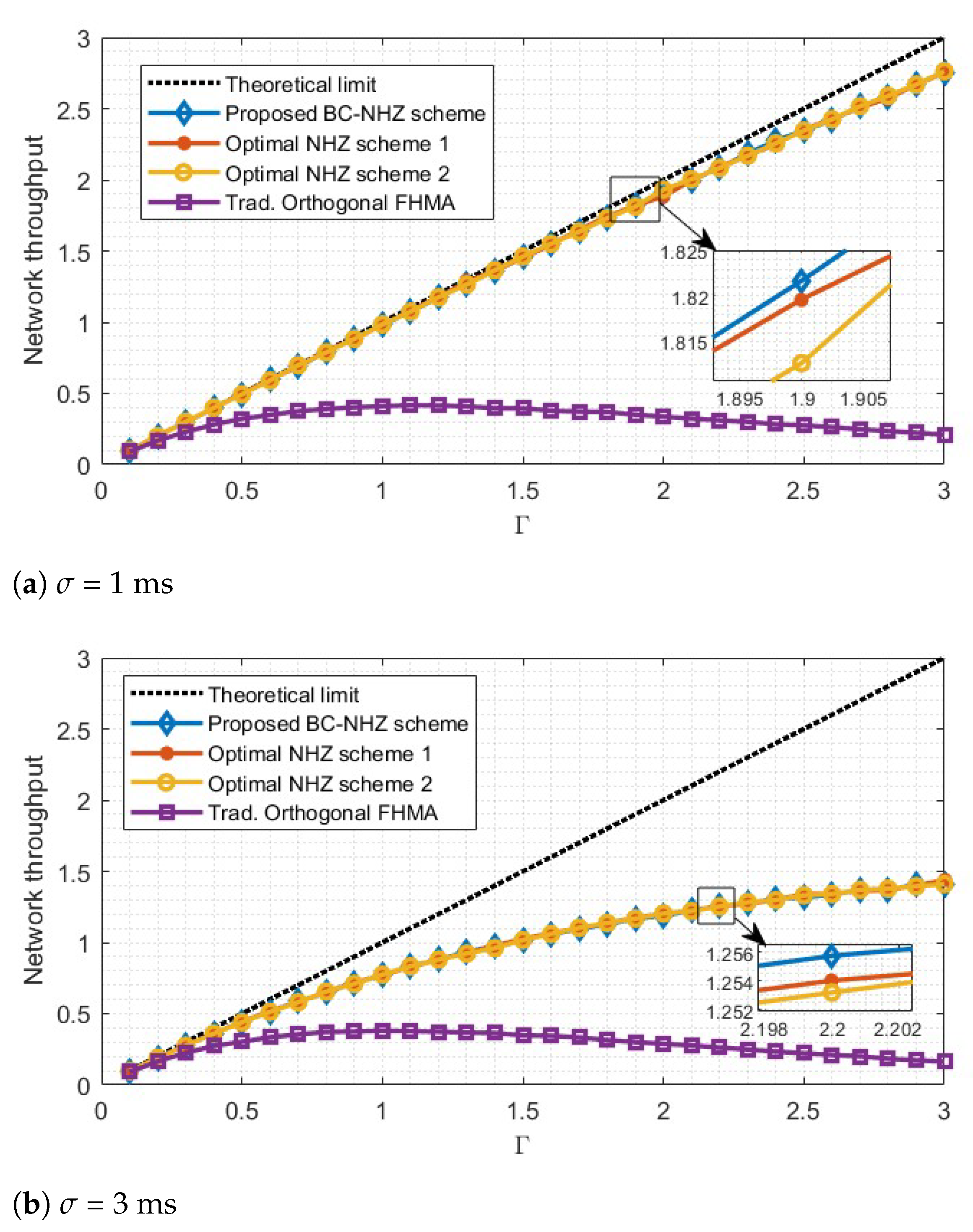
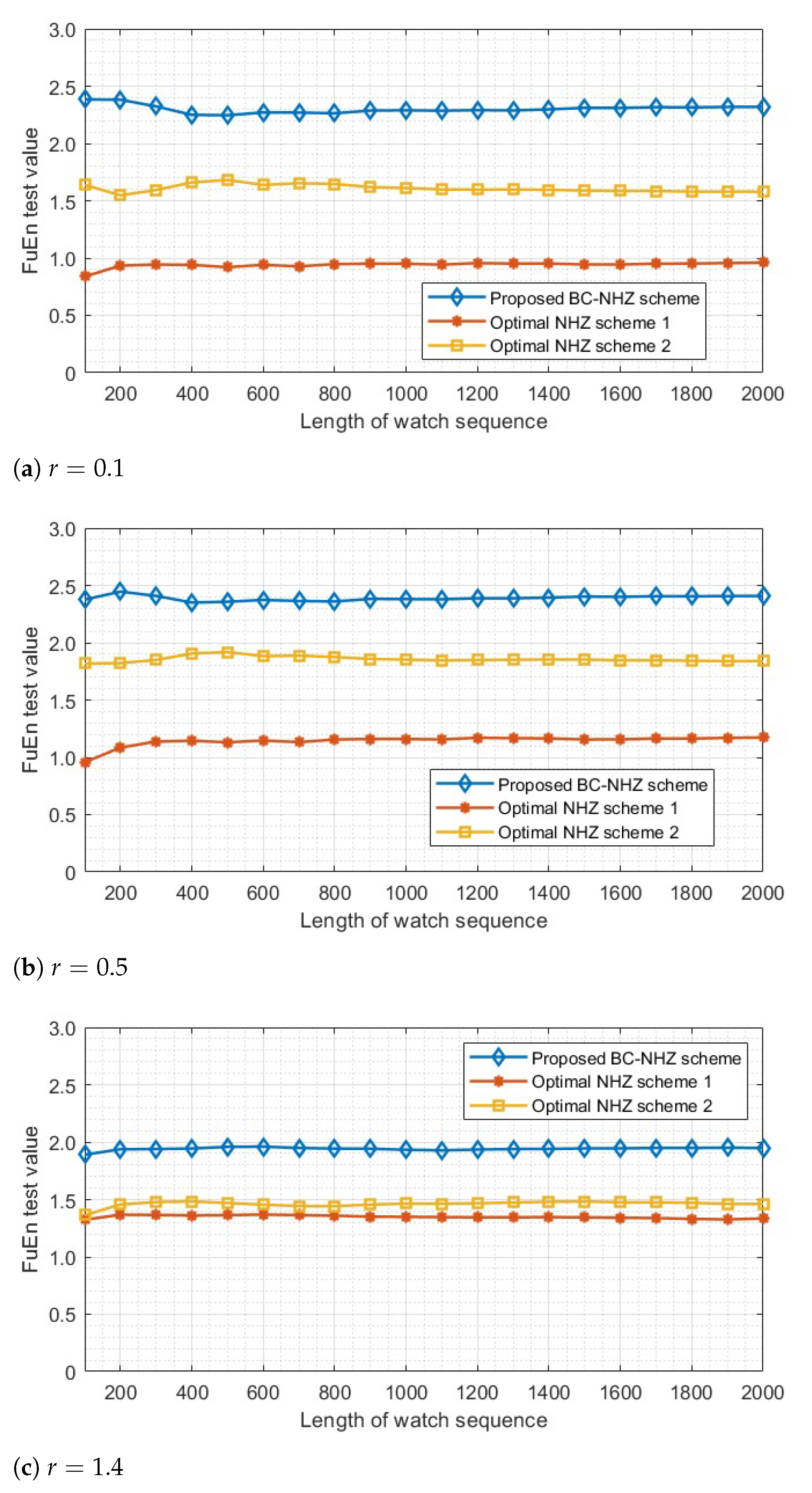
- The quasi-synchronous access mechanism is adopted by practical systems, and consists of several . ’s relative delay is independently distributed over for any .
- The shared communication spectrum B is divided equally into 20 frequency slots. The proposed BC-NHZ or the baseline schemes control the communication carrier frequency and continuously vary over frequency slots with a width of 1 MHz, switching the frequency at each time interval T = 1 ms.
- The simulation time length is 260 s, and each hopping interval consists of protection time = 0.2 ms and transmission time = 0.8 ms.
- The length of the transmitted service packet is hopping intervals, and the packet services arrival between data owners are independent and satisfy the Poisson distribution of the DS network’s total arrival rate .
- For a fair comparison, the adopted spectrum control sequence sets in the following simulations have similar values of parameters, i.e., the frequency-slot size q, the NHZ width Z, the family size M, and so forth.
5.1. Network Capacity
5.2. Complexity Metric
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Li, T.; Sahu, A.K.; Talwalkar, A.; Smith, V. Federated Learning: Challenges, Methods, and Future Directions. IEEE Signal Process. Mag. 2020, 37, 50–60. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.W. Channel Sounding for Multi-User Massive MIMO in Distributed Antenna System Environment. Electronics 2019, 8, 36. [Google Scholar] [CrossRef]
- Chen, J.; Ran, X. Deep Learning with Edge Computing: A Review. Proc. IEEE 2019, 107, 1655–1674. [Google Scholar] [CrossRef]
- Dai, F.; Hossain, M.A.; Wang, Y. State of the Art in Parallel and Distributed Systems: Emerging Trends and Challenges. Electronics 2025, 14, 677. [Google Scholar] [CrossRef]
- Ghosh, P.; Basu, K.; Das, S.K. A Game Theory-Based Pricing Strategy to Support Single/Multiclass Job Allocation Schemes for Bandwidth-Constrained Distributed Computing Systems. IEEE Trans. Parallel Distrib. Syst. 2007, 18, 289–306. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security. IEEE Commun. Surv. Tutorials 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Zhang, C.; Hu, C.; Wu, T.; Zhu, L.; Liu, X. Achieving Efficient and Privacy-Preserving Neural Network Training and Prediction in Cloud Environments. IEEE Trans. Dependable Secur. Comput. 2023, 20, 4245–4257. [Google Scholar] [CrossRef]
- Lee, S.; Jeong, T. Large-Scale Distributed System and Design Methodology for Real-Time Cluster Services and Environments. Electronics 2022, 11, 4037. [Google Scholar] [CrossRef]
- Maxim, A.; Pauca, O.; Caruntu, C.F. Coalitional Distributed Model Predictive Control Strategy with Switching Topologies for Multi-Agent Systems. Electronics 2024, 13, 792. [Google Scholar] [CrossRef]
- Miller, D.E. A Comparison of LQR Optimal Performance in the Decentralized and Centralized Settings. IEEE Trans. Autom. Control 2016, 61, 2308–2311. [Google Scholar] [CrossRef]
- Short, M.; Abugchem, F.; Abrar, U. Dependable Control for Wireless Distributed Control Systems. Electronics 2015, 4, 857–878. [Google Scholar] [CrossRef]
- Zhou, Y.; Cui, F.; Che, J.; Ni, M.; Zhang, Z.; Li, J. Elastic Balancing of Communication Efficiency and Performance in Federated Learning with Staged Clustering. Electronics 2025, 14, 745. [Google Scholar] [CrossRef]
- Zhang, C.; Luo, X.; Liang, J.; Liu, X.; Zhu, L.; Guo, S. POTA: Privacy-Preserving Online Multi-Task Assignment with Path Planning. IEEE Trans. Mob. Comput. 2024, 23, 5999–6011. [Google Scholar] [CrossRef]
- Li, C.; Guan, L.; Wu, H.; Cheng, N.; Li, Z.; Shen, X.S. Dynamic Spectrum Control-Assisted Secure and Efficient Transmission Scheme in Heterogeneous Cellular Networks. Engineering 2022, 17, 220–231. [Google Scholar] [CrossRef]
- Ali, S.; Saad, W.; Rajatheva, N.; Chang, K.; Steinbach, D.; Sliwa, B.; Wietfeld, C.; Mei, K.; Shiri, H.; Zepernick, H.J.; et al. 6G White Paper on Machine Learning in Wireless Communication Networks. arXiv 2020. [Google Scholar] [CrossRef]
- Zhu, X.; Liu, J.; Lu, L.; Zhang, T.; Qiu, T.; Wang, C.; Liu, Y. Enabling Intelligent Connectivity: A Survey of Secure ISAC in 6G Networks. IEEE Commun. Surv. Tutor. 2024; early access. [Google Scholar] [CrossRef]
- Chen, R.; Li, Z.; Shi, J.; Guan, L.; Zhang, J. High Secure Sequence Design in Frequency Hopping Communications. China Commun. 2019, 16, 139–150. [Google Scholar]
- Li, C.; Qi, P.; Wang, D.; Li, Z. On the Anti-Interference Tolerance of Cognitive Frequency Hopping Communication Systems. IEEE Trans. Reliab. 2020, 69, 1453–1464. [Google Scholar] [CrossRef]
- Guan, L.; Li, Z.; Xiao, S.; Si, J.; Wan, J. A Family of Adaptive Frequency Slot Number FH Sequences for High Security and Reliability Communication. In Proceedings of the 2015 European Intelligence and Security Informatics Conference, Manchester, UK, 7–9 September 2015; pp. 30–36. [Google Scholar] [CrossRef]
- Chen, W.; Wang, Z.; Xie, H.; Yu, W. Characterization of Surface EMG Signal Based on Fuzzy Entropy. IEEE Trans. Neural Syst. Rehabil. Eng. 2007, 15, 266–272. [Google Scholar] [CrossRef]
- Chen, X.; Si, J.; Li, Z.; Cai, J.; Bai, B. A New Complexity Metric for FH/SS Sequences Using Fuzzy Entropy. Sci. China Inf. Sci. 2011, 54, 1491–1499. [Google Scholar] [CrossRef]
- Li, Z.; Cai, J.; Chang, Y. Determining the complexity of FH/SS sequence by approximate entropy. IEEE Trans. Commun. 2009, 57, 812–820. [Google Scholar] [CrossRef]
- Li, Z.; Chang, Y.; Jin, L.; Cai, J. Analysis of FHMA Performance on Block Cipher Based Frequency-Hopping Sequences. IEEE Commun. Lett. 2004, 8, 434–436. [Google Scholar] [CrossRef]
- Li, Z.; Chang, Y.; Kou, W.; Jin, L.; Wang, Y. A Family of FH Sequences Based on 3DES Block Cipher for FHMA Communications. In Proceedings of the 2004 IEEE International Conference on Communications, Paris, France, 20–24 June 2004; Volume 1, pp. 311–315. [Google Scholar] [CrossRef]
- Li, Z.; Chang, Y.; Jin, L. A Novel Family of Frequency Hopping Sequences for Multi-Hop Bluetooth Networks. IEEE Trans. Consum. Electron. 2003, 49, 1084–1089. [Google Scholar] [CrossRef]
- Guo, L.; Zhang, C.; Sun, J.; Fang, Y. A Privacy-Preserving Attribute-Based Authentication System for Mobile Health Networks. IEEE Trans. Mob. Comput. 2014, 13, 1927–1941. [Google Scholar] [CrossRef]
- Tan, H.; Zheng, W.; Guan, Y.; Lu, R. A Privacy-Preserving Attribute-Based Authenticated Key Management Scheme for Accountable Vehicular Communications. IEEE Trans. Veh. Technol. 2023, 72, 3622–3635. [Google Scholar] [CrossRef]
- Guan, L.; Zan, L.; Si, J.; Liang, X. Performance Analysis of Cognitive Bluetooth Networks Based on the Orthogonal FH Sequences. In Proceedings of the 2014 IEEE International Conference on Computer and Information Technology, Xi’an, China, 11–13 September 2014; pp. 869–875. [Google Scholar] [CrossRef]
- Guan, L.; Li, Z.; Si, J.; Huang, Y. Generation and Characterization of Orthogonal FH Sequences for the Cognitive Network. Sci. China Inf. Sci. 2015, 58, 1–11. [Google Scholar] [CrossRef]
- Ye, W. Two classes of frequency hopping sequences with no-hit zone. In Proceedings of the 7th International Symposium on Communications Theory and Applications, Ambleside, UK, 13–18 July 2003; pp. 304–306. [Google Scholar]
- Peng, D.; Fan, P.; Lee, M.H. Lower bounds on the periodic Hamming correlations of frequency hopping sequences with low hit zone. Sci. China Ser. F Inf. Sci. 2006, 49, 208–218. [Google Scholar] [CrossRef]
- Bao, J.; Ji, L. New Families of Optimal Frequency Hopping Sequence Sets. IEEE Trans. Inf. Theory 2016, 62, 5209–5224. [Google Scholar] [CrossRef]
- Peng, D.; Han, H. Theoretical boundary and design for frequency/time series hopping in collision-free zone. J. Chengdu Inst. Inf. Eng. 2015, 30, 1–6. [Google Scholar] [CrossRef]
- Zhou, L.; Han, H.; Liu, X. Frequency-hopping sequence sets with no-hit-zone through Cartesian product. Cryptogr. Commun. 2020, 12, 485–497. [Google Scholar] [CrossRef]
- Liu, X.; Zhou, L.; Zeng, Q.; Niu, X. On the Average Hamming Correlation of Frequency-Hopping Sequence Sets with Low Hit Zone. In Proceedings of the 2019 International Symposium on Networks, Computers and Communications (ISNCC), Istanbul, Turkey, 18–20 June 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, X.; Hong, S.; Zeng, Q.; Zhou, L. NHZ frequency hopping sequence sets under aperiodic Hamming correlation: Tighter bound and optimal constructions. Cryptogr. Commun. 2022, 14, 347–356. [Google Scholar] [CrossRef]
- Gao, W.; Guan, L.; Li, Z.; Si, J.; Hui, P.; Fu, H. An Extended Family of No-Hit-Zone Frequency Hopping Sequences for UAVs Cluster Communication. In Proceedings of the 2022 14th International Conference on Wireless Communications and Signal Processing, Nanjing, China, 1–3 November 2022; pp. 928–932. [Google Scholar] [CrossRef]
- Zeng, Q.; Chen, J.; Niu, X.; Zhou, L.; Liu, X. Optimal No-Hit-Zone Sequences With Wide-Gap for Improved FHMA Systems Under Follower Jamming. IEEE Trans. Commun. 2024, 73, 1652–1662. [Google Scholar] [CrossRef]
- Zeng, Q.; Zhou, Z.; Liu, X.; Liu, Z. Strong No-Hit-Zone Sequences for Improved Quasi-Orthogonal FHMA Systems: Sequence Design and Performance Analysis. IEEE Trans. Commun. 2019, 67, 5336–5345. [Google Scholar] [CrossRef]
| Length | Family Size | Frequency-Slot Size | NHZ Width | Basic Sequence | Reference |
|---|---|---|---|---|---|
| m | v | - | [33] | ||
| Optimal NHZ sequence set in [33] | [34] | ||||
| r | m | v | - | [36] | |
| v | - | [38] | |||
| m | v | Optimal sequence sets in [32] | [39] | ||
| r | m | v | Block ciper sequence | This paper |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gao, W.; Guan, L.; Hui, P.; Zhang, H.; Li, Z. Block-Cipher No-Hit-Zone Sequence-Assisted Spectrum Control Scheme for Distributed Systems. Electronics 2025, 14, 1802. https://doi.org/10.3390/electronics14091802
Gao W, Guan L, Hui P, Zhang H, Li Z. Block-Cipher No-Hit-Zone Sequence-Assisted Spectrum Control Scheme for Distributed Systems. Electronics. 2025; 14(9):1802. https://doi.org/10.3390/electronics14091802
Chicago/Turabian StyleGao, Wendong, Lei Guan, Pei Hui, Hanwen Zhang, and Zan Li. 2025. "Block-Cipher No-Hit-Zone Sequence-Assisted Spectrum Control Scheme for Distributed Systems" Electronics 14, no. 9: 1802. https://doi.org/10.3390/electronics14091802
APA StyleGao, W., Guan, L., Hui, P., Zhang, H., & Li, Z. (2025). Block-Cipher No-Hit-Zone Sequence-Assisted Spectrum Control Scheme for Distributed Systems. Electronics, 14(9), 1802. https://doi.org/10.3390/electronics14091802




