Research on Data Ownership and Controllable Sharing Schemes in the Process of Logistics Data Flow
Abstract
1. Introduction
- (1)
- To develop a dynamic and secure data ownership verification system: this encompasses the implementation of chameleon signature methods within blockchain technology to facilitate publicly verifiable, non-transferable, and dynamically updatable ownership labels.
- (2)
- To create a manageable and safe data-sharing infrastructure: the suggested architecture utilizes proxy re-encryption and searchable encryption to guarantee that data are accessible solely to authorized individuals under specified ownership conditions, facilitating precise and revocable access control.
- (3)
- To furnish official security assurances: the technique is assessed using stringent cryptographic models, namely, Existential Unforgeability under Chosen Message Attack (EUF-CMA) and Indistinguishability under Keyword Guessing Attack (IND-KGA) to confirm its robustness against common adversarial tactics.
- (4)
- To illustrate practical applicability and efficacy: the proposed system is evaluated for computational and communication efficiency by performance analysis and simulation testing, confirming its appropriateness for implementation in intricate, large-scale logistics networks.
2. Related Work
2.1. Data Rights Confirmation
2.2. Controllable Sharing Based on Data Rights Confirmation
3. Methods
3.1. Chameleon Signature
- : initialization, input security parameter , output public verification parameter .
- : key generation algorithm, by inputting , outputs the chameleon hash public-private key pair .
- : chameleon hash algorithm, by inputting chameleon hash public key , and data M, outputs the chameleon hash and verification parameters .
- : chameleon hash verification algorithm, by inputting chameleon hash H, verification parameters R, data M, and public key , outputs the verification result x.
- : chameleon signature algorithm, by inputting chameleon hash H, verification parameters R, private key , data M, and signed message , outputs the verification parameter .
- : chameleon signature verification algorithm, by inputting chameleon hash H, public key , data M, signed message , verification parameters R and , outputs the verification result y.
3.2. Proxy Re-Encryption
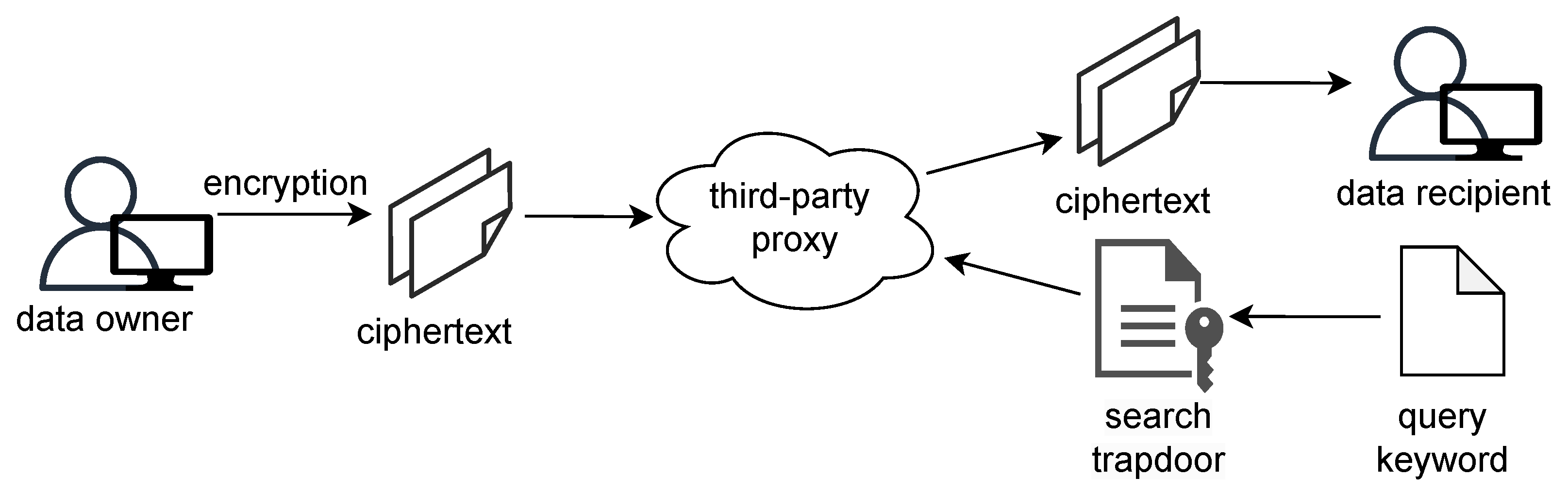
3.3. Searchable Encryption
4. System Framework
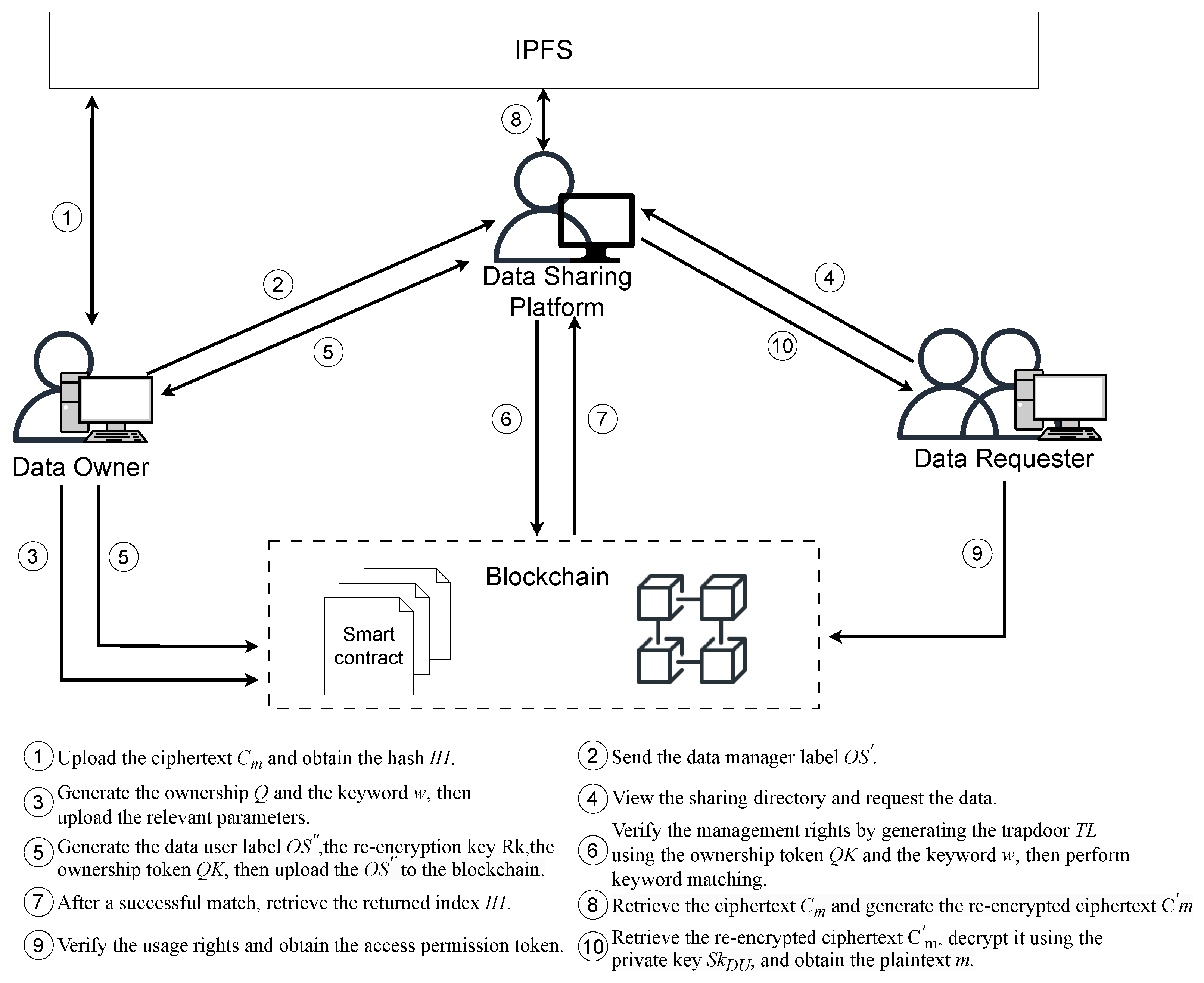
4.1. System Model
- (1)
- Data Owner: the data owner is responsible for generating tags for data control rights, management rights, and usage rights. They also create searchable encryption schemes and ownership tokens. The owner stores the data in the IPFS and records ownership tags on the blockchain. When data sharing is required, the data owner dynamically adjusts the ownership based on user needs, ensuring complete control over the data.
- (2)
- Data sharing platform: this facilitates data sharing between owners and requesters. The platform verifies its ownership and generates searchable encryption trapdoors to access ciphertext. It also manages the data that the owner intends to share and generates re-encrypted ciphertext for secure transmission.
- (3)
- Data Requester: they browse the data catalog provided by the data sharing platform and submit a data sharing request. By querying the ownership parameters stored on the blockchain, they verify the legitimacy of the data’s origin. Once the verification is successful, they use the validated ownership to obtain the requested data from the data sharing platform.
- (4)
- IPFS: this stores the data provided by the data owner and submits the storage index back to the data owner.
- (5)
- Blockchain: this stores the encrypted keywords, ownership information, and related public parameters uploaded by the data owner. It also verifies ownership validity and performs keyword matching.
4.2. Security Threats
- (1)
- Forged chameleon signature: malicious users may attempt to forge data ownership. They can generate fake ownership signature verification parameters based on the forged data ownership, thus gaining control over the data.
- (2)
- Keyword Guessing Attack and Indistinguishability: malicious users might try to bypass encryption protections. By querying and analyzing the encrypted index multiple times, they may infer keyword information and gain access to the data.
4.3. Security Model
4.3.1. Non-Forgeability of Chameleon Signature
- (1)
- Initialization phase: Challenger C selects , and as random oracles. Then, it generates the corresponding chameleon public-private key pair and .
- (2)
- Query phase: A uses message m to make a signing query. Challenger C generates the chameleon hash , the signature u, and the verification parameter r. C then returns to A.
- (3)
- Forgery phase: Adversary A outputs a forged signature and verification parameter . A has not previously queried . Then, C uses the verification algorithm to verify it. If the result is 1, A’s attack is successful; otherwise, it fails.
4.3.2. Keyword Guessing Attack Indistinguishability
- (1)
- Initialization phase: challenger C generates the public and private key pairs for the data owner and the data management platform. Random values , and the DDH hard parameters are provided.
- (2)
- Query phase: adversary A uses the data owner ’s public key, , and the data sharing platform ’s public key, , along with the forged ownership Q, to send an ownership token query to challenger C. Challenger C generates the ownership token in response and returns it to A. A then uses the ownership token , along with the public keys of the data owner , , and the data sharing platform , , to send a trapdoor query to challenger C. Challenger C generates the trapdoor and returns it to A.
- (3)
- Challenge phase: adversary A outputs , where it is not the same as the trapdoor queried in the previous phase. Challenger C generates the corresponding trapdoor, and uses the Test algorithm for search. If the output is 1, A succeeds in the attack; otherwise, it fails.
5. Scheme Design
Scheme Algorithm Definition
6. Scheme Analysis
6.1. Scheme Analysis
Correctness Analysis
6.2. Security Analysis
6.2.1. Chameleon Signature Unforgeability
6.2.2. Indistinguishability of Keyword Guessing Attacks
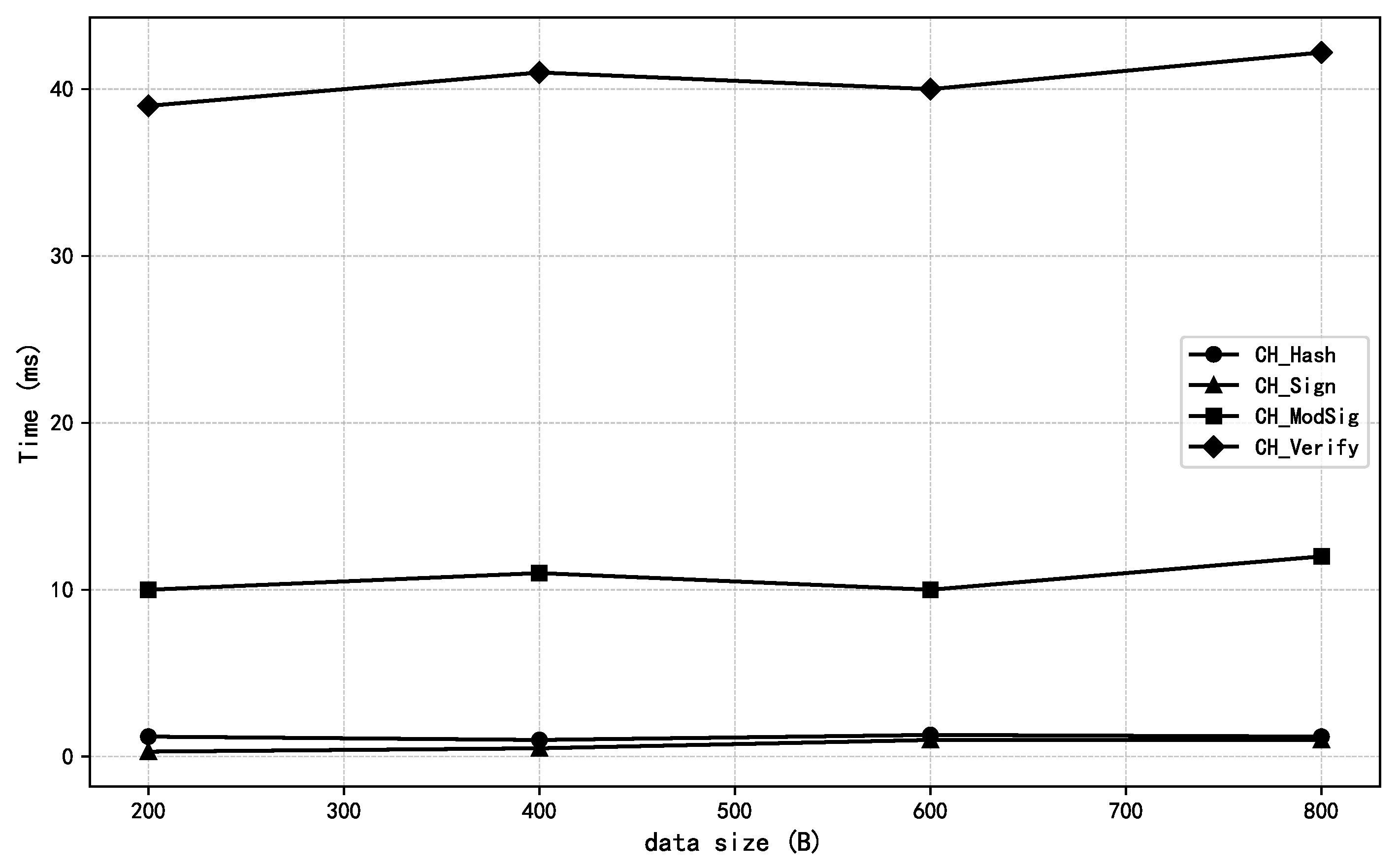
6.3. Performance Analysis
6.3.1. Functionality Analysis
6.3.2. Efficiency Analysis
6.3.3. Chameleon Signature
6.3.4. Ownership-Based Searchable Proxy Re-Encryption
7. Discussion & Conclusions
7.1. Discussion
7.2. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Cao, M.; Zhang, Q. Supply chain collaboration: Impact on collaborative advantage and firm performance. J. Oper. Manag. 2011, 29, 163–180. [Google Scholar] [CrossRef]
- Zheng, C.; Li, Y.; Dou, R. Who should own the data? The impact of data value creation on data ownership. Comput. Ind. Eng. 2024, 190, 110093. [Google Scholar] [CrossRef]
- Mochram, R.A.A.; Makawowor, C.T.; Tanujaya, K.M.; Moniaga, J.V.; Jabar, B.A. Systematic literature review: Blockchain security in NFT ownership. In Proceedings of the 2022 International Conference on Electrical and Information Technology (IEIT), Malang, Indonesia, 15–16 September 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 302–306. [Google Scholar]
- Abbas, A.E.; van Velzen, T.; Ofe, H.; van de Kaa, G.; Zuiderwijk, A.; de Reuver, M. Beyond control over data: Conceptualizing data sovereignty from a social contract perspective. Electron. Mark. 2024, 34, 20. [Google Scholar] [CrossRef]
- Spaan, M.; Hoppenbrouwers, S.; Hofmans, B. OMIT: An Instrument to Aid Implementation of a Data Ownership Model in Data Governance. In Proceedings of the 2023 International Conference on Advanced Enterprise Information System (AEIS), London, UK, 1–3 December 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 21–27. [Google Scholar]
- Xia, X.; Li, X. Researching on Cloud Service Architecture of Data Products. In Proceedings of the 2023 IEEE International Symposium on Broadband Multimedia Systems and Broadcasting (BMSB), Beijing, China, 14–16 June 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar]
- Gupta, P.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R. TrailChain: Traceability of data ownership across blockchain-enabled multiple marketplaces. J. Netw. Comput. Appl. 2022, 203, 103389. [Google Scholar] [CrossRef]
- Piasecki, J.; Cheah, P.Y. Ownership of individual-level health data, data sharing, and data governance. BMC Med. Ethics 2022, 23, 104. [Google Scholar] [CrossRef] [PubMed]
- Zeng, S.; Cao, B.; Sun, Y.; Sun, C.; Wan, Z.; Peng, M. Blockchain-Assisted Cross-Domain Data Sharing in Industrial IoT. IEEE Internet Things J. 2023, 11, 26778–26792. [Google Scholar] [CrossRef]
- Xu, G.; Chiang, J.M.H. The Core Value of Web3. 0: Recognition and Measurement of Data Assets. J. Inf. Technol. Econ. Dev. 2023, 13, 92. [Google Scholar]
- Blazy, O.; Kakvi, S.A.; Kiltz, E.; Pan, J. Tightly-secure signatures from chameleon hash functions. In Proceedings of the Public-Key Cryptography–PKC 2015: 18th IACR International Conference on Practice and Theory in Public-Key Cryptography, Gaithersburg, MD, USA, 30 March–1 April 2015; Proceedings 18. Springer: Berlin/Heidelberg, Germany, 2015; pp. 256–279. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 557–564. [Google Scholar]
- Yang, Z.; Huang, Y.; Li, X.; Wang, W. Efficient Secure Data Provenance Scheme in Multimedia Outsourcing and Sharing. Comput. Mater. Contin. 2018, 56, 1. [Google Scholar]
- Huang, Y.; Shen, W.; Qin, J. Certificateless cloud storage auditing supporting data ownership transfer. Comput. Secur. 2024, 139, 103738. [Google Scholar] [CrossRef]
- Zhao, H.; Zhao, B.; Cheng, S. The Mechanism of Confirming Big Data Property Rights Based on Smart Contract. In Proceedings of the 2019 4th International Conference on Intelligent Information Technology, Da Nang, Vietnam, 20–23 February 2019; pp. 78–82. [Google Scholar]
- Shao, J.; Cao, Z.; Liang, X.; Lin, H. Proxy re-encryption with keyword search. Inf. Sci. 2010, 180, 2576–2587. [Google Scholar] [CrossRef]
- Zhao, X.; Su, Q. Time-limited ownership delegation scheme with revocation security for healthcare. Clust. Comput. 2024, 27, 12105–12121. [Google Scholar] [CrossRef]
- Wang, L.; Huang, S.; Zuo, L.; Li, J.; Liu, W. RCDS: A right-confirmable data-sharing model based on symbol mapping coding and blockchain. Front. Inf. Technol. Electron. Eng. 2023, 24, 1194–1213. [Google Scholar] [CrossRef]
- Wang, Q.; Liu, Y. Blockchain empowered dynamic access control for secure data sharing in collaborative emergency management. Inf. Process. Manag. 2025, 62, 103960. [Google Scholar] [CrossRef]
- Amanat, A.; Rizwan, M.; Maple, C.; Zikria, Y.B.; Almadhor, A.S.; Kim, S.W. Blockchain and cloud computing-based secure electronic healthcare records storage and sharing. Front. Public Health 2022, 10, 938707. [Google Scholar] [CrossRef]
- Krawczyk, H.; Rabin, T. Chameleon Hashing and Signatures. Cryptology ePrint Archive. 1998. Available online: https://eprint.iacr.org/1998/010/ (accessed on 19 February 2025).
- Yang, K.; Zhang, Z.; Youliang, T.; Ma, J. A secure authentication framework to guarantee the traceability of avatars in metaverse. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3817–3832. [Google Scholar] [CrossRef]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Espoo, Finland, 31 May–4 June 1998; Springer: Berlin/Heidelberg, Germany, 1998; pp. 127–144. [Google Scholar]
- Kushilevitz, E.; Ostrovsky, R. Replication is not needed: Single database, computationally-private information retrieval. In Proceedings of the Proceedings 38th Annual Symposium on Foundations of Computer Science, Miami Beach, FL, USA, 20–22 October 1997; IEEE: Piscataway, NJ, USA, 1997; pp. 364–373. [Google Scholar]
- Boneh, D.; Di Crescenzo, G.; Ostrovsky, R.; Persiano, G. Public key encryption with keyword search. In Proceedings of the Advances in Cryptology-EUROCRYPT 2004: International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Proceedings 23. Springer: Berlin/Heidelberg, Germany, 2004; pp. 506–522. [Google Scholar]
- Chen, Z.; Zhang, L.; Cai, W.; Laili, Y.; Wang, X.; Wang, F.; Wang, H. Multi-workflow dynamic scheduling in product design: A generalizable approach based on meta-reinforcement learning. J. Manuf. Syst. 2025, 79, 334–346. [Google Scholar] [CrossRef]
- Hu, X.; Li, J.; Li, F.; Wang, J.; Wang, Y. Priority rule-based heuristics for distributed multi-project scheduling considering global resource failures. J. Oper. Res. Soc. 2025, 1–20. [Google Scholar] [CrossRef]




| Parameter | Meaning |
|---|---|
| The public key and private key of user i | |
| The chameleon hash public key and private key of user i | |
| Re-encryption key | |
| Chameleon hash | |
| Chameleon signature | |
| Public verification parameters | |
| Searchable encryption trapdoor | |
| Data ownership and ownership tokens | |
| The address hash value returned by IPFS | |
| r | Chameleon signature verification parameter |
| Data control rights, data management rights, data usage rights |
| Scheme | Data Ownership | Ownership Authorization | Dynamic Ownership Change | Permission Control | Public Verification |
|---|---|---|---|---|---|
| Reference [7] | ✓ | ✓ | × | × | ✓ |
| Reference [17] | ✓ | × | × | ✓ | ✓ |
| Reference [19] | ✓ | ✓ | × | × | × |
| Reference [20] | ✓ | × | ✓ | × | ✓ |
| Ours | ✓ | ✓ | ✓ | ✓ | ✓ |
| Algorithm | Reference [22] | Ours |
|---|---|---|
| - |
| Algorithm | Reference [22] | Ours |
|---|---|---|
| Algorithm | Reference [16] | Ours |
|---|---|---|
| - | ||
| Algorithm | Reference [16] | Ours |
|---|---|---|
| - | ||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, Z.; Shi, Z.; Wang, W.; Kong, R.; Fu, D.; Qiu, J. Research on Data Ownership and Controllable Sharing Schemes in the Process of Logistics Data Flow. Electronics 2025, 14, 1714. https://doi.org/10.3390/electronics14091714
Liu Z, Shi Z, Wang W, Kong R, Fu D, Qiu J. Research on Data Ownership and Controllable Sharing Schemes in the Process of Logistics Data Flow. Electronics. 2025; 14(9):1714. https://doi.org/10.3390/electronics14091714
Chicago/Turabian StyleLiu, Ziqi, Zhanling Shi, Wenjing Wang, Rui Kong, Deqian Fu, and Jianlong Qiu. 2025. "Research on Data Ownership and Controllable Sharing Schemes in the Process of Logistics Data Flow" Electronics 14, no. 9: 1714. https://doi.org/10.3390/electronics14091714
APA StyleLiu, Z., Shi, Z., Wang, W., Kong, R., Fu, D., & Qiu, J. (2025). Research on Data Ownership and Controllable Sharing Schemes in the Process of Logistics Data Flow. Electronics, 14(9), 1714. https://doi.org/10.3390/electronics14091714






