SCConv-Denoising Diffusion Probabilistic Model Anomaly Detection Based on TimesNet
Abstract
1. Introduction
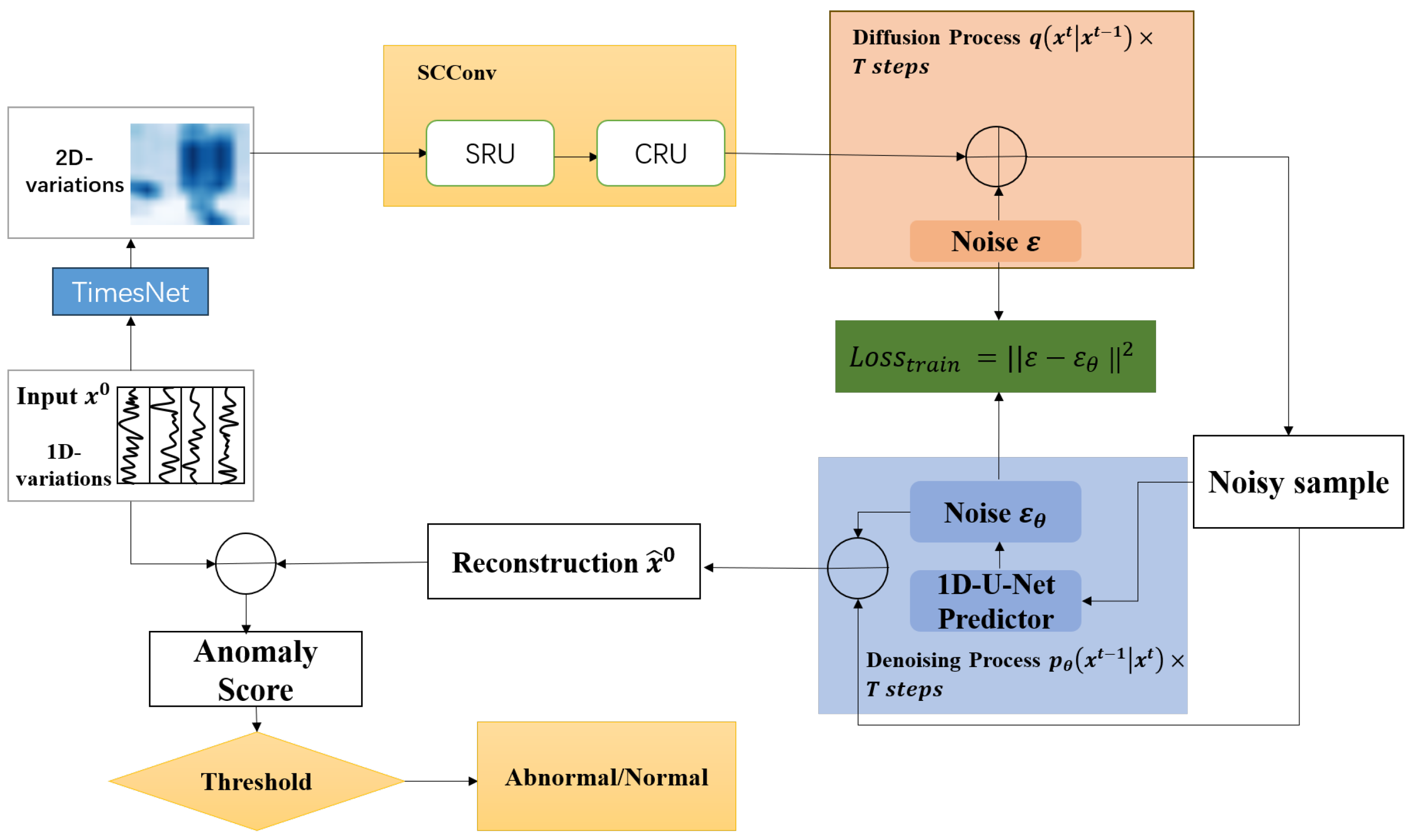
- We integrated Denoising Diffusion Probabilistic Models (DDPMs) into TimesNet’s architecture. This enables the iterative refinement of noisy input representations during training, enhancing robustness against sensor drift and adversarial perturbations.
- We designed a lightweight Spatial and Channel Reconstruction Convolution (SCConv) module that dynamically suppresses redundant features. This integration enables more effective multi-scale feature extraction, enhances the ability to capture multi-scale data characteristics, and improves anomaly detection performance.
- SDADT jointly optimizes periodicity modeling (via TimesBlock), noise resilience (via DDPMs), and feature efficiency (via SCConv) and demonstrates that our method achieves promising performance in anomaly detection.
2. Related Work
- Traditional Detection Methods: Conventional time series anomaly detection approaches, which build normal operating models of systems or data to find anomalies based on deviations, mostly rely on statistical and rule-based analytical techniques. For example, Rigatos et al. used a derivative-free nonlinear Kalman filter to estimate system states, measured the deviation between observed and estimated values, and set a confidence interval to recognize attacks [9].
- Machine Learning Detection Methods: These methods detect anomalies or attacks by learning the system’s behavior under normal conditions, even when such behaviors are not included in prior knowledge. In order to detect anomalous traffic patterns with a low false negative rate, Hao et al. created a hybrid machine learning algorithm that combines a dynamic threshold model based on the seasonal autoregressive integrated moving average (SARIMA) with an LSTM model [10].
- Deep Learning Detection Methods: Deep learning’s benefit for CPS attack detection is its capacity to glean useful features from intricate, extensive, and multimodal data, increasing the precision and robustness of identifying different kinds of attacks. By using GANs to train anomaly detection models and recognize network attack behaviors in intricate multisensor industrial networks, Freitas P et al. presented a novel framework to detect malicious behavior in CPSs [11].
3. Materials and Methods
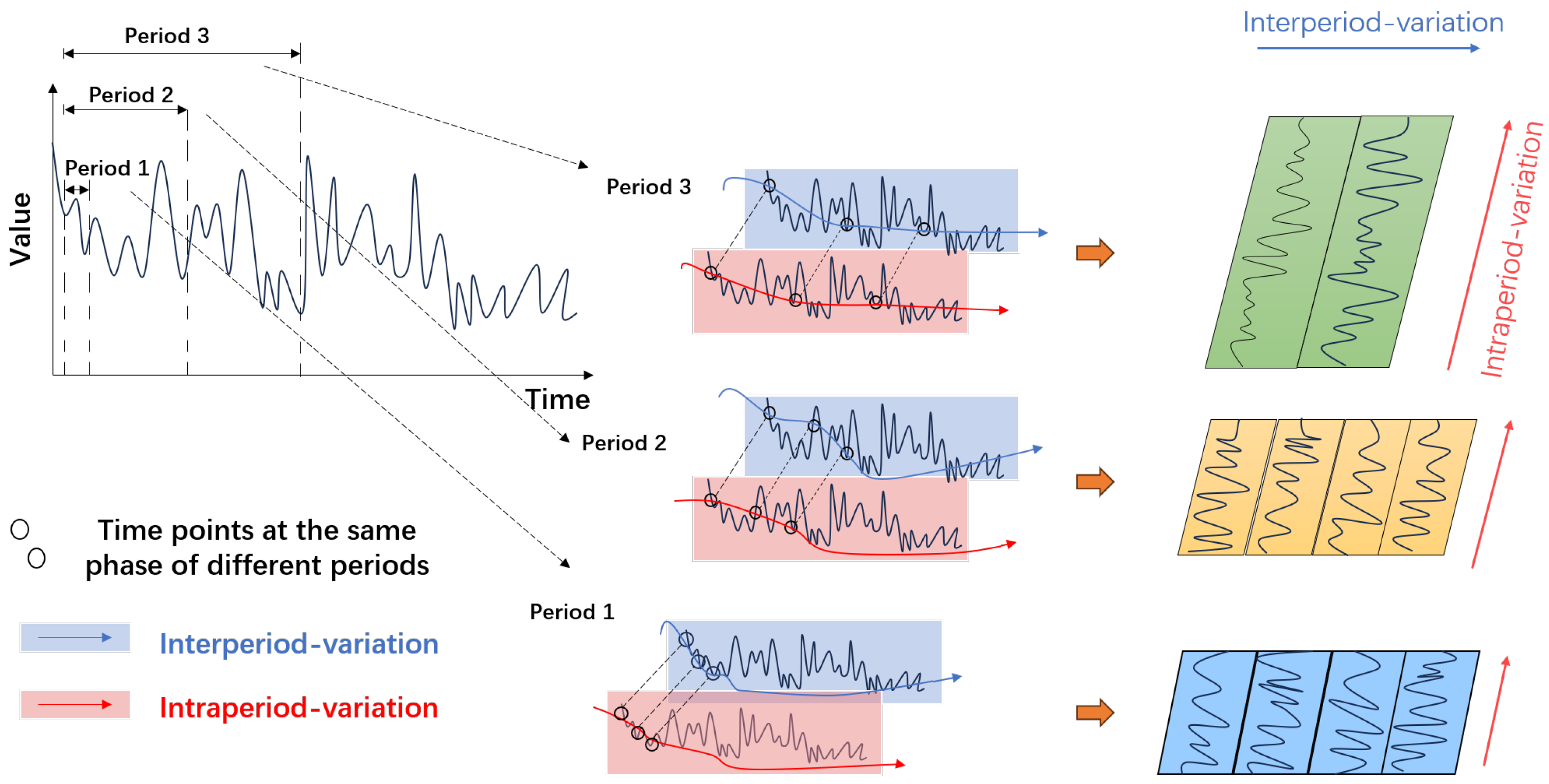
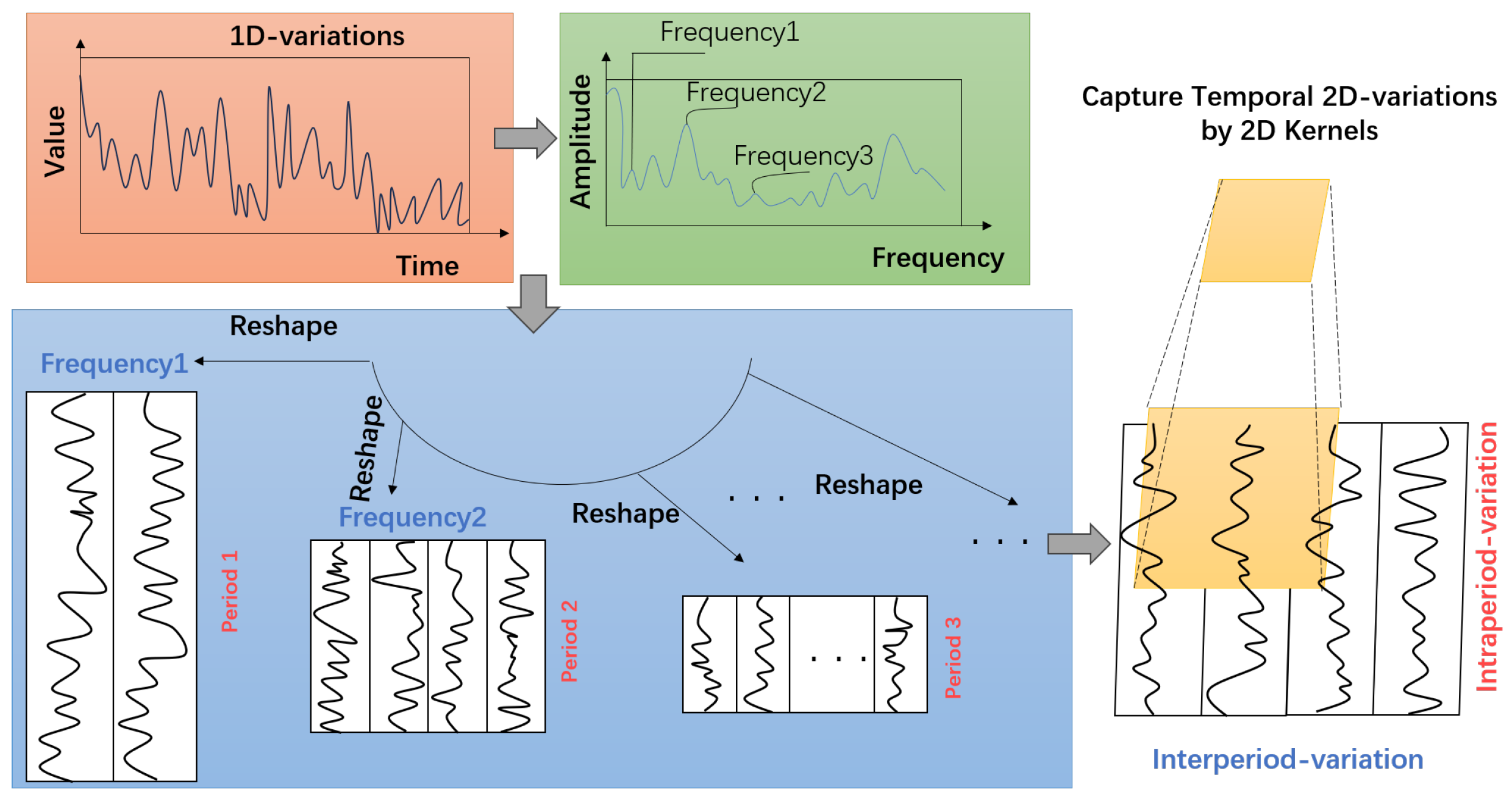
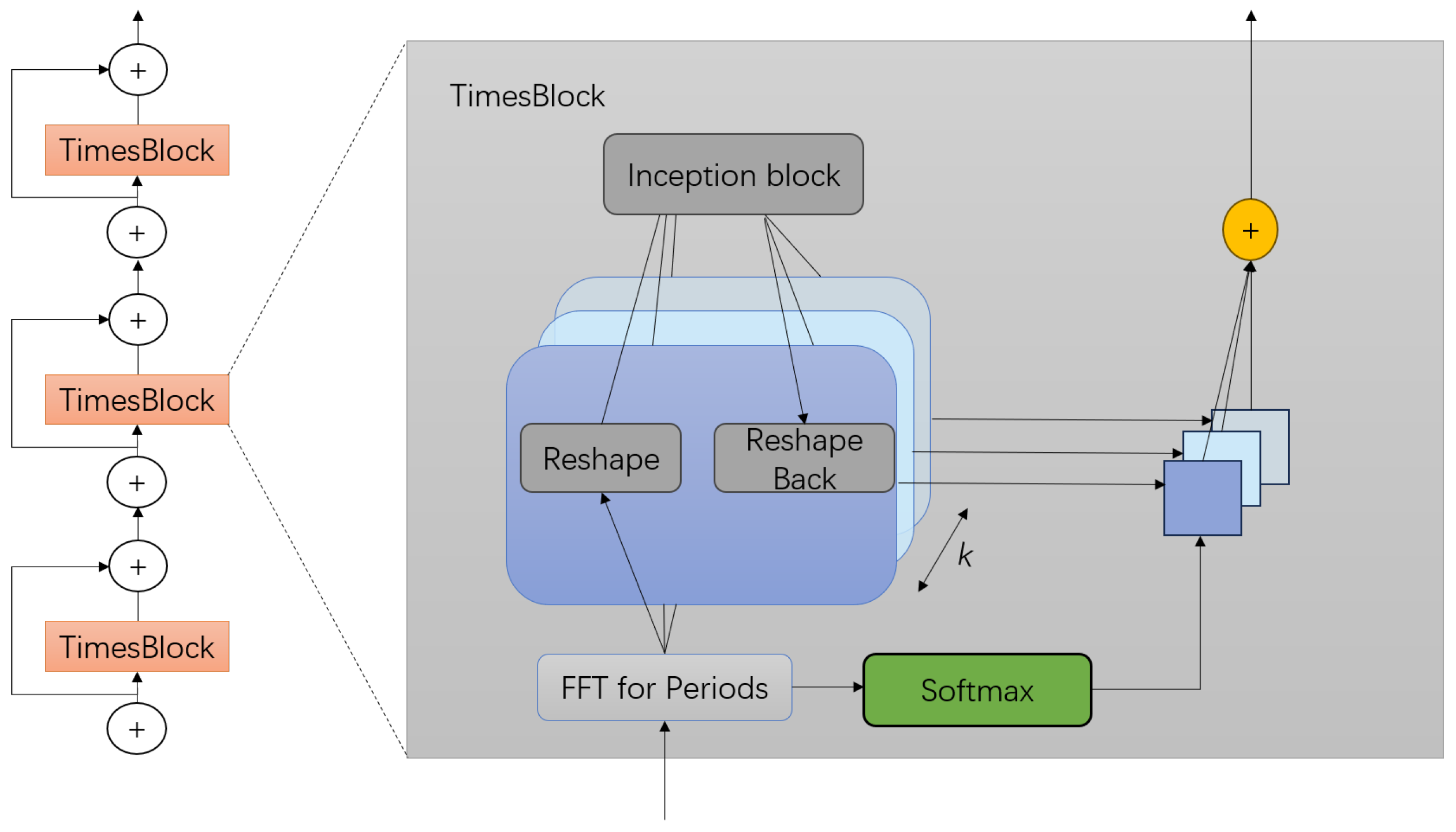
3.1. TimesNet
- (1)
- Transforming the 1D time series into a 2D tensor.
- (2)
- Capturing the 2D temporal variation representation.
- (3)
- Converting the 2D tensor into a 1D space.
- (4)
- Adaptive Aggregation
3.2. DDPMs
3.3. SCConv
3.4. Anomaly Score
4. Experiment
4.1. Dataset
- SWaT (Secure Water Treatment) is a CPS cyber security research testbed that replicates an actual industrial water treatment system [23]. Developed by the Singapore University of Technology and Design (SUTD), it aims to study potential cyber attacks and defense measures in critical infrastructure.
- The PSM (Prognostics Server Machine) dataset is a time series dataset for server machine metrics, mainly used for anomaly detection tasks [24]. It was collected by eBay and contains server performance indicators recorded every minute over a period of 21 weeks.
- The SMD (Server Machine Dataset) is designed for multivariate time series anomaly detection [25]. It comprises system performance metrics collected by sensors from servers during their regular operation. This dataset is commonly used in both industry and academia for research related to server anomaly detection.
- The SMAP (Soil Moisture Active Passive) was launched by NASA in January 2015; the SMAP mission combines an L-band radar and radiometer to provide accurate, frequent observations of soil moisture at a spatial resolution of approximately 9 km (radiometer) and 3 km (radar) [26]. The dataset is mainly used for tasks such as remote sensing monitoring and anomaly detection.
4.2. Baselines
- LSTM [27]: LSTM is used in anomaly detection by learning normal patterns from time series data. It predicts the next step or reconstructs the input, and anomalies are identified when the prediction or reconstruction error exceeds a predetermined threshold.
- Transformers [28]: Transformers model global dependencies in time series data and identify anomalies by using the self-attention mechanism. Anomalies are identified when the prediction error or reconstruction error of the sequence exceeds a predefined threshold after learning the patterns of normal data.
- LogTrans [29]: LogTrans uses a logarithmic sparse self-attention mechanism to capture time series dependencies both locally and globally. By learning the normal patterns of the data, it performs anomaly detection when the prediction error exceeds a predefined threshold.
- Reformer [30]: To manage a lengthy time series, Reformer employs an effective locality-sensitive hashing self-attention mechanism. By comparing the difference between the actual and predicted values, it learns the typical patterns of behavior and identifies anomalies.
- Pyraformer [31]: Pyraformer efficiently captures multi-scale dependencies in a time series through its pyramid-structured attention mechanism. This enables the model to identify anomaly patterns when processing a long time series, facilitating effective anomaly detection.
- ETSformer [32]: ETSformer detects anomalies by decomposing the time series into three components: level, trend, and seasonality. Anomalies are identified by recognizing abnormal changes in these components. If certain patterns in the data deviate from the expected level, trend, or seasonal behavior, they are flagged as anomalies, enabling effective anomaly detection.
- LightTS [33]: LightTS captures anomaly patterns in a time series efficiently through its self-attention mechanism and multi-scale modeling.
- Dlinear [34]: Dlinear breaks down time series data into trend and seasonal components in order to identify anomalies. It then applies linear models to process these components separately. By learning the linear relationships within the time series, Dlinear identifies anomaly points that deviate from the normal trend.
- CARLA [35]: CARLA utilizes self-supervised contrastive learning to generate embedding representations of a time series. It maximizes the similarity between normal data and minimizes the difference for anomalous data, thereby enabling effective anomaly detection.
4.3. Evaluation Metrics
4.4. Data Preprocessing
4.5. Experimental Setup
4.6. Overall Performance
4.7. Ablation Study
4.8. Hyperparameter Sensitivity Analysis
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| CPSs | Cyber Physical Systems |
| SCConv | Spatial and Channel Reconstruction Convolution |
| DDPMs | Denoising Diffusion Probabilistic Models |
| FFT | Fast Fourier Transform |
| SRU | Spatial Reconstruction Unit |
| CRU | Channel Reconstruction Unit |
| GN | Group Normalization |
| GWC | Group-wise Convolution |
| PWC | Point-wise Convolution |
| MSE | Mean Squared Error |
| SWaT | Secure Water Treatment |
| PSM | Prognostics Server Machine |
| SMD | Server Machine Dataset |
| SMAP | Soil Moisture Active Passive |
| PA | Point Adjustment |
| SR | Spectral Residual |
References
- Deng, A.; Hooi, B. Graph neural network-based anomaly detection in multivariate time series. In Proceedings of the AAAI Conference on Artificial Intelligence, Virtual Event, 2–9 February 2021; Volume 35, pp. 4027–4035. [Google Scholar]
- Ogie, R.I. Cyber security incidents on critical infrastructure and industrial networks. In Proceedings of the 9th International Conference on Computer and Automation Engineering, Sydney, Australia, 18–21 February 2017; pp. 254–258. [Google Scholar]
- Zhai, L.; Vamvoudakis, K.G. A data-based private learning framework for enhanced security against replay attacks in cyber-physical systems. Int. J. Robust Nonlinear Control 2021, 31, 1817–1833. [Google Scholar] [CrossRef]
- Zamanzadeh Darban, Z.; Webb, G.I.; Pan, S.; Aggarwal, C.; Salehi, M. Deep learning for time series anomaly detection: A survey. ACM Comput. Surv. 2024, 57, 1–42. [Google Scholar] [CrossRef]
- Canizo, M.; Triguero, I.; Conde, A.; Onieva, E. Multi-head CNN–RNN for multi-time series anomaly detection: An industrial case study. Neurocomputing 2019, 363, 246–260. [Google Scholar] [CrossRef]
- Kim, J.; Kang, H.; Kang, P. Time-series anomaly detection with stacked Transformer representations and 1D convolutional network. Eng. Appl. Artif. Intell. 2023, 120, 105964. [Google Scholar] [CrossRef]
- Wu, H.; Hu, T.; Liu, Y.; Zhou, H.; Wang, J.; Long, M. Timesnet: Temporal 2d-variation modeling for general time series analysis. arXiv 2022, arXiv:2210.02186. [Google Scholar]
- Gaba, S.; Budhiraja, I.; Kumar, V.; Martha, S.; Khurmi, J.; Singh, A.; Singh, K.K.; Askar, S.S.; Abouhawwash, M. A systematic analysis of enhancing cyber security using deep learning for cyber physical systems. IEEE Access 2024, 12, 6017–6035. [Google Scholar] [CrossRef]
- Rigatos, G.; Zervos, N.; Serpanos, D.; Siadimas, V.; Siano, P.; Abbaszadeh, M. Fault diagnosis of gas-turbine power units with the Derivative-free nonlinear Kalman Filter. Electr. Power Syst. Res. 2019, 174, 105810. [Google Scholar] [CrossRef]
- Hao, W.; Yang, T.; Yang, Q. Hybrid statistical-machine learning for real-time anomaly detection in industrial cyber–physical systems. IEEE Trans. Autom. Sci. Eng. 2021, 20, 32–46. [Google Scholar] [CrossRef]
- de Araujo-Filho, P.F.; Kaddoum, G.; Campelo, D.R.; Santos, A.G.; Macêdo, D.; Zanchettin, C. Intrusion detection for cyber–physical systems using generative adversarial networks in fog environment. IEEE Internet Things J. 2020, 8, 6247–6256. [Google Scholar] [CrossRef]
- Pang, G.; Shen, C.; Cao, L.; Hengel, A.V.D. Deep learning for anomaly detection: A review. ACM Comput. Surv. (CSUR) 2021, 54, 1–38. [Google Scholar] [CrossRef]
- Zhou, X.; Liang, W.; Shimizu, S.; Ma, J.; Jin, Q. Siamese neural network based few-shot learning for anomaly detection in industrial cyber-physical systems. IEEE Trans. Ind. Inform. 2020, 17, 5790–5798. [Google Scholar] [CrossRef]
- Akowuah, F.; Kong, F. Real-time adaptive sensor attack detection in autonomous cyber-physical systems. In Proceedings of the 2021 IEEE 27th Real-Time and Embedded Technology and Applications Symposium (RTAS), Nashville, TN, USA, 18–21 May 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 237–250. [Google Scholar]
- Li, J.; Wen, Y.; He, L. Scconv: Spatial and channel reconstruction convolution for feature redundancy. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Vancouver, BC, Canada, 17–24 June 2023; pp. 6153–6162. [Google Scholar]
- Li, G.; Jung, J.J. Deep learning for anomaly detection in multivariate time series: Approaches, applications, and challenges. Inf. Fusion 2023, 91, 93–102. [Google Scholar] [CrossRef]
- Jiang, W.; Hong, Y.; Zhou, B.; He, X.; Cheng, C. A GAN-based anomaly detection approach for imbalanced industrial time series. IEEE Access 2019, 7, 143608–143619. [Google Scholar] [CrossRef]
- Niu, Z.; Yu, K.; Wu, X. LSTM-based VAE-GAN for time-series anomaly detection. Sensors 2020, 20, 3738. [Google Scholar] [CrossRef] [PubMed]
- Wyatt, J.; Leach, A.; Schmon, S.M.; Willcocks, C.G. Anoddpm: Anomaly detection with denoising diffusion probabilistic models using simplex noise. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, New Orleans, LA, USA, 18–24 June 2022; pp. 650–656. [Google Scholar]
- Wu, H.; Xu, J.; Wang, J.; Long, M. Autoformer: Decomposition transformers with auto-correlation for long-term series forecasting. Adv. Neural Inf. Process. Syst. 2021, 34, 22419–22430. [Google Scholar]
- Sohl-Dickstein, J.; Weiss, E.; Maheswaranathan, N.; Ganguli, S. Deep unsupervised learning using nonequilibrium thermodynamics. In Proceedings of the International Conference on Machine Learning, PMLR, Lille, France, 7–9 July 2015; pp. 2256–2265. [Google Scholar]
- Wu, Y.; He, K. Group normalization. In Proceedings of the European Conference on Computer Vision (ECCV), Munich, Germany, 8–14 September 2018; pp. 3–19. [Google Scholar]
- Mathur, A.P.; Tippenhauer, N.O. SWaT: A water treatment testbed for research and training on ICS security. In Proceedings of the 2016 International Workshop on Cyber-Physical Systems for Smart Water Networks (CySWater), Vienna, Austria, 11 April 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 31–36. [Google Scholar]
- Abdulaal, A.; Liu, Z.; Lancewicki, T. Practical approach to asynchronous multivariate time series anomaly detection and localization. In Proceedings of the 27th ACM SIGKDD Conference on Knowledge Discovery & Data Mining, Singapore, 14–18 August 2021; pp. 2485–2494. [Google Scholar]
- Su, Y.; Zhao, Y.; Niu, C.; Liu, R.; Sun, W.; Pei, D. Robust anomaly detection for multivariate time series through stochastic recurrent neural network. In Proceedings of the 25th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, Anchorage, AK, USA, 4–8 August 2019; pp. 2828–2837. [Google Scholar]
- Zhao, H.; Wang, Y.; Duan, J.; Huang, C.; Cao, D.; Tong, Y.; Xu, B.; Bai, J.; Tong, J.; Zhang, Q. Multivariate time-series anomaly detection via graph attention network. In Proceedings of the 2020 IEEE International Conference on Data Mining (ICDM), Sorrento, Italy, 17–20 November 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 841–850. [Google Scholar]
- Hochreiter, S. Long Short-term Memory. Neural Comput. 1997, 9, 1735–1780. [Google Scholar] [CrossRef]
- Vaswani, A. Attention is all you need. Adv. Neural Inf. Process. Syst. 2017. [Google Scholar]
- Li, S.; Jin, X.; Xuan, Y.; Zhou, X.; Chen, W.; Wang, Y.X.; Yan, X. Enhancing the locality and breaking the memory bottleneck of transformer on time series forecasting. Adv. Neural Inf. Process. Syst. 2019, 32. [Google Scholar]
- Kitaev, N.; Kaiser, Ł.; Levskaya, A. Reformer: The efficient transformer. arXiv 2020, arXiv:2001.04451. [Google Scholar]
- Liu, S.; Yu, H.; Liao, C.; Li, J.; Lin, W.; Liu, A.X.; Dustdar, S. Pyraformer: Low-Complexity Pyramidal Attention for Long-Range Time Series Modeling and Forecasting. 2022. Available online: https://openreview.net/forum?id=0EXmFzUn5I (accessed on 10 February 2025).
- Woo, G.; Liu, C.; Sahoo, D.; Kumar, A.; Hoi, S. Etsformer: Exponential smoothing transformers for time-series forecasting. arXiv 2022, arXiv:2202.01381. [Google Scholar]
- Zhang, T.; Zhang, Y.; Cao, W.; Bian, J.; Yi, X.; Zheng, S.; Li, J. Less is more: Fast multivariate time series forecasting with light sampling-oriented mlp structures. arXiv 2022, arXiv:2207.01186. [Google Scholar]
- Zeng, A.; Chen, M.; Zhang, L.; Xu, Q. Are transformers effective for time series forecasting? In Proceedings of the AAAI Conference on Artificial Intelligence, Washington, DC, USA, 7–14 February 2023; Volume 37, pp. 11121–11128. [Google Scholar]
- Darban, Z.Z.; Webb, G.I.; Pan, S.; Aggarwal, C.C.; Salehi, M. CARLA: Self-supervised contrastive representation learning for time series anomaly detection. Pattern Recognit. 2025, 157, 110874. [Google Scholar] [CrossRef]
- Ren, H.; Xu, B.; Wang, Y.; Yi, C.; Huang, C.; Kou, X.; Xing, T.; Yang, M.; Tong, J.; Zhang, Q. Time-series anomaly detection service at microsoft. In Proceedings of the 25th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, Anchorage, AK, USA, 4–8 August 2019; pp. 3009–3017. [Google Scholar]
- Xu, H.; Chen, W.; Zhao, N.; Li, Z.; Bu, J.; Li, Z.; Liu, Y.; Zhao, Y.; Pei, D.; Feng, Y.; et al. Unsupervised anomaly detection via variational auto-encoder for seasonal kpis in web applications. In Proceedings of the 2018 World Wide Web Conference, Lyon, France, 23–27 April 2018; pp. 187–196. [Google Scholar]





| Dataset | #Features | #Train | #Test | Anomaly% |
|---|---|---|---|---|
| SWaT | 51 | 495,000 | 449,919 | 12.10% |
| PSM | 25 | 132,481 | 87,841 | 27.80% |
| SMD | 38 | 708,405 | 708,420 | 4.2% |
| SMAP | 25 | 135,183 | 427,617 | 13.13% |
| Dataset | Epoch | Batch_Size | k | Seq_Len | Group Number | Image_Size |
|---|---|---|---|---|---|---|
| SWaT | 3 | 128 | 5 | 15 | 4 | 128 |
| PSM | 3 | 128 | 3 | 15 | 4 | 128 |
| SMD | 10 | 128 | 3 | 75 | 4 | 64 |
| SMAP | 3 | 128 | 1 | 50 | 4 | 64 |
| Method | SMD | SWaT | PSM | SMAP | Avg (F1) (%) | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| P | R | F1 | P | R | F1 | P | R | F1 | P | R | F1 | ||
| LSTM | 78.52 | 65.47 | 71.41 | 78.06 | 91.72 | 84.34 | 69.24 | 99.53 | 81.67 | 91.06 | 57.49 | 70.48 | 76.98 |
| Transformer | 83.58 | 76.13 | 79.56 | 68.84 | 96.53 | 80.37 | 62.75 | 96.56 | 76.07 | 89.37 | 57.12 | 69.70 | 76.43 |
| LogTrans | 83.46 | 70.13 | 76.21 | 68.67 | 97.32 | 80.52 | 63.06 | 98 | 76.74 | 89.15 | 57.59 | 69.97 | 75.86 |
| Reformer | 82.58 | 69.24 | 75.32 | 72.5 | 96.53 | 82.8 | 59.93 | 95.38 | 73.61 | 90.91 | 57.44 | 70.40 | 75.53 |
| Pyraformer | 85.61 | 80.61 | 83.04 | 87.92 | 96 | 91.78 | 71.67 | 96.02 | 82.08 | 92.54 | 57.71 | 71.09 | 81.99 |
| ETSformer | 87.44 | 79.23 | 83.13 | 90.02 | 80.36 | 84.91 | 99.31 | 85.28 | 91.76 | 92.25 | 55.75 | 69.50 | 82.325 |
| LightTS | 87.1 | 78.42 | 82.53 | 91.98 | 94.72 | 93.33 | 98.37 | 95.97 | 97.15 | 92.58 | 55.27 | 69.21 | 85.56 |
| Dlinear | 83.62 | 71.52 | 77.1 | 80.91 | 95.3 | 87.52 | 98.28 | 89.26 | 93.55 | 92.32 | 55.41 | 69.26 | 81.86 |
| CARLA | 67.57 | 84.65 | 75.15 | 98.91 | 71.32 | 82.88 | 98.33 | 95.93 | 97.18 | 92.03 | 58.10 | 71.23 | 81.61 |
| SDADT (ours) | 88.25 | 82.8 | 85.39 | 92.38 | 93.15 | 94.00 | 98.66 | 97.65 | 98.15 | 93.60 | 57.70 | 71.39 | 86.73 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, J.; Yang, X.; Ren, Z. SCConv-Denoising Diffusion Probabilistic Model Anomaly Detection Based on TimesNet. Electronics 2025, 14, 746. https://doi.org/10.3390/electronics14040746
Zhou J, Yang X, Ren Z. SCConv-Denoising Diffusion Probabilistic Model Anomaly Detection Based on TimesNet. Electronics. 2025; 14(4):746. https://doi.org/10.3390/electronics14040746
Chicago/Turabian StyleZhou, Jingquan, Xinhe Yang, and Zhu Ren. 2025. "SCConv-Denoising Diffusion Probabilistic Model Anomaly Detection Based on TimesNet" Electronics 14, no. 4: 746. https://doi.org/10.3390/electronics14040746
APA StyleZhou, J., Yang, X., & Ren, Z. (2025). SCConv-Denoising Diffusion Probabilistic Model Anomaly Detection Based on TimesNet. Electronics, 14(4), 746. https://doi.org/10.3390/electronics14040746





