Content-Centric Clustering and Power-Diverse Allocation in Downlink Network-Coded Multiple Access System
Abstract
1. Introduction
- We propose a power-diverse downlink NCMA framework that exploits content heterogeneity to improve throughput without requiring channel-state information.
- Content-centric clustering followed by priority-driven power allocation is introduced in this paper, which enhances the MUD and throughput performance. The proposed scheme achieves higher throughput than existing PB-NCMA and PR-NCMA schemes in low-to-medium Signal-to-Noise Ratio (SNR) regions.
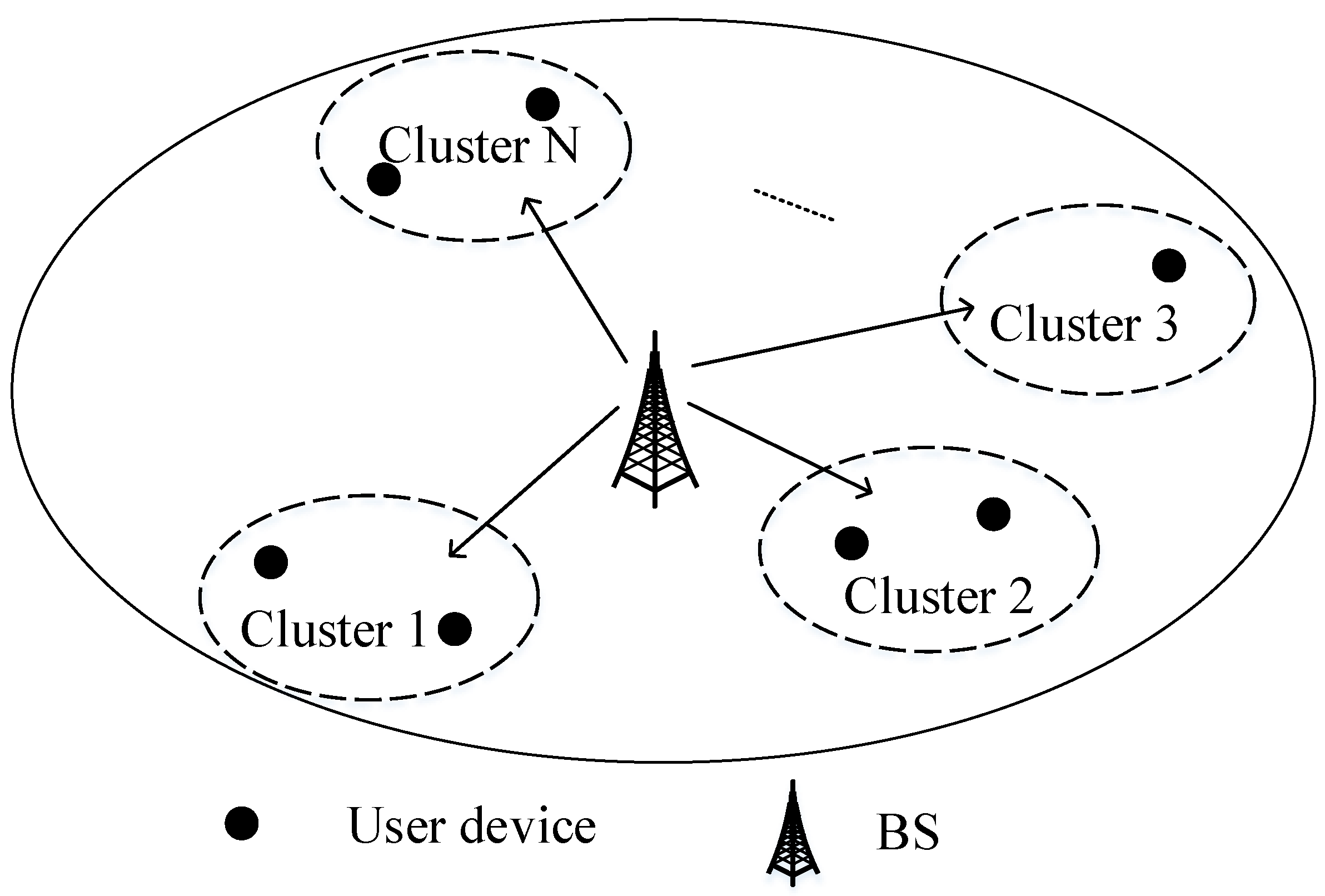
2. Multiuser NCMA Downlink System
2.1. System Model
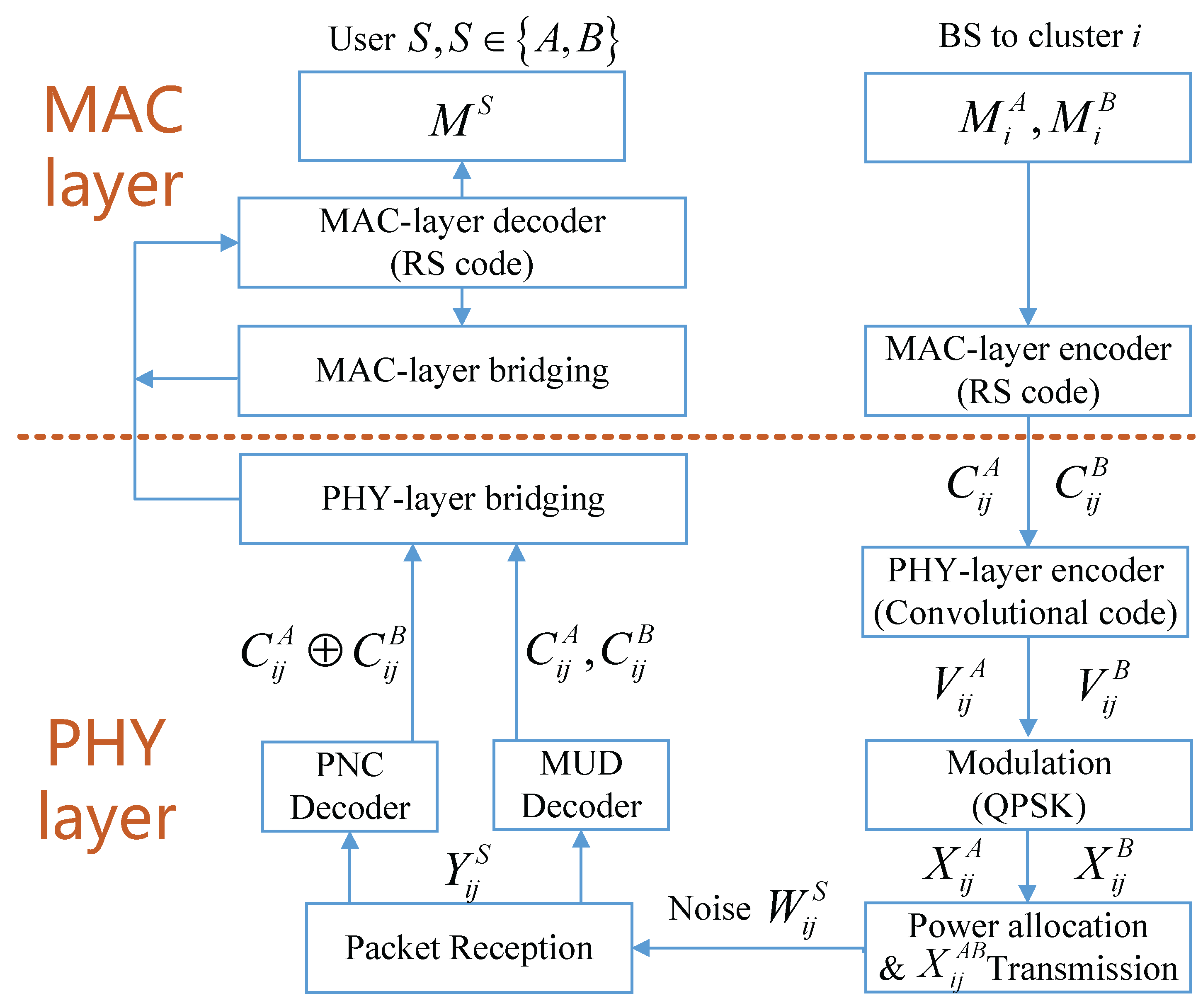
2.2. Information Processing of PD-NCMA
3. Dynamic Clustering and Power Allocation Design in PD-NCMA
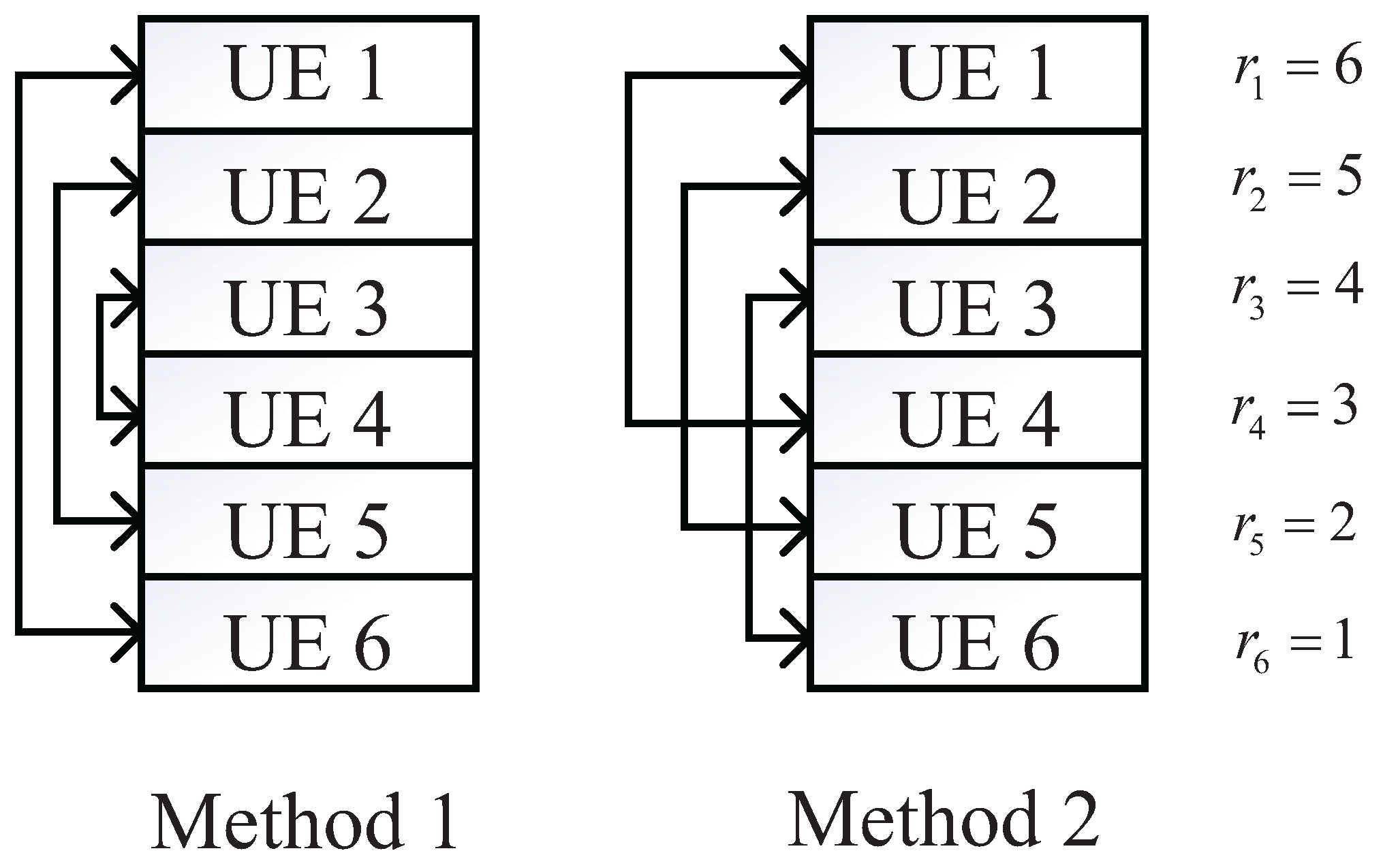
3.1. Content-Centric Clustering
- Method 1: User device with message priority forms a cluster with . (i.e., the user device with the highest message priority forms a cluster with the lowest one ). If M is an even number, user devices are clustered pairwise. Nevertheless, a device with the priority forms a single-user cluster if M is an odd number.
- Method 2: Two cases are considered in Method 2. If M is an even number, users are first sorted and divided into 2 groups. Group 1 and group 2 are denoted as and , respectively. Then, a user device with message priority forms a cluster with (i.e., the user device with message priority forms a cluster with ). If M is an odd number, users are first sorted and divided into 2 groups: and . Then, a user device with message priority forms a cluster with . Furthermore, a device with priority forms a single user cluster.
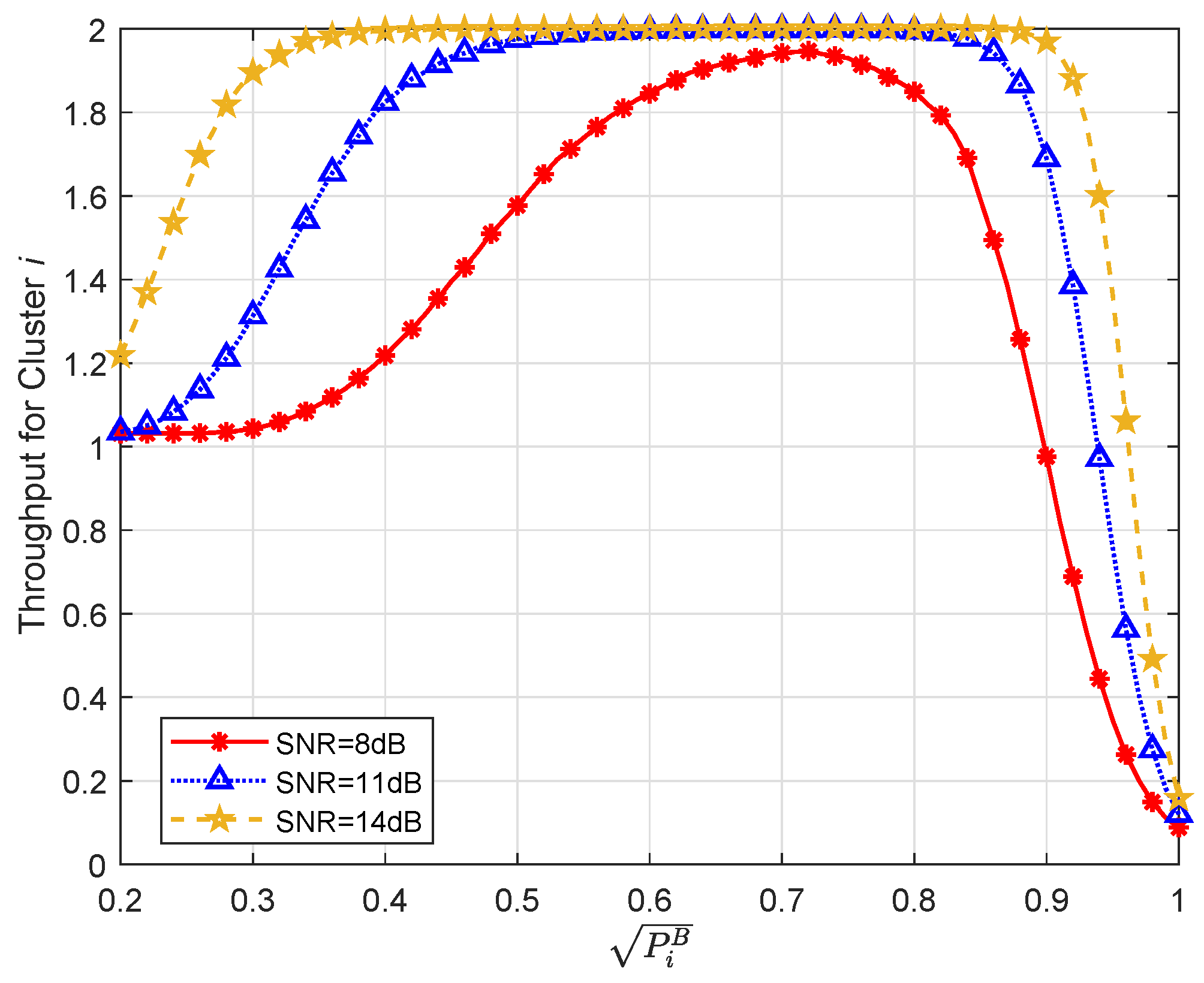
3.2. Dynamic Power Allocation
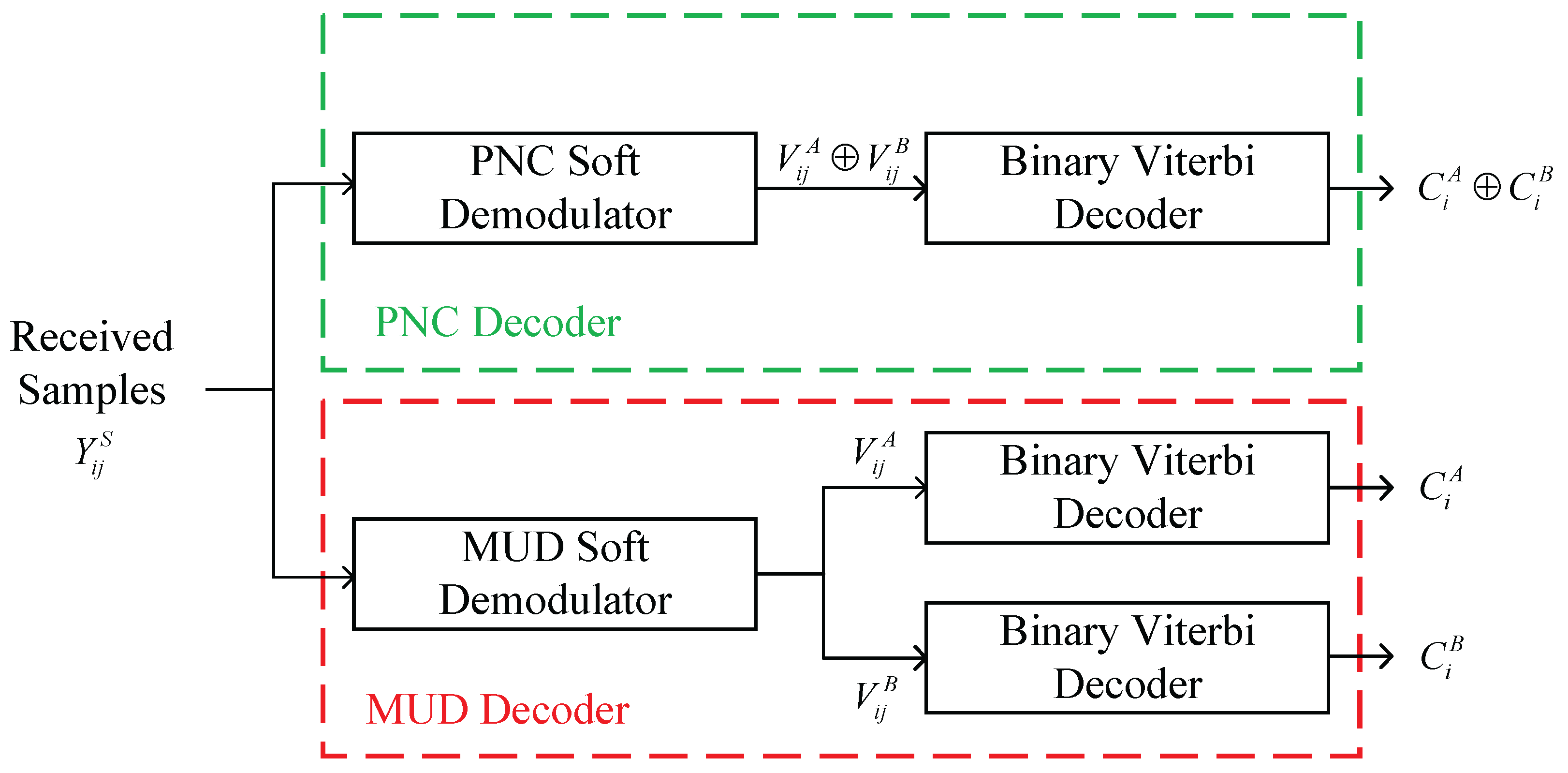
3.3. PHY Layer Processing and Union Bound
3.4. Throughput Analysis
3.5. Complexity Analysis
4. Simulation Results
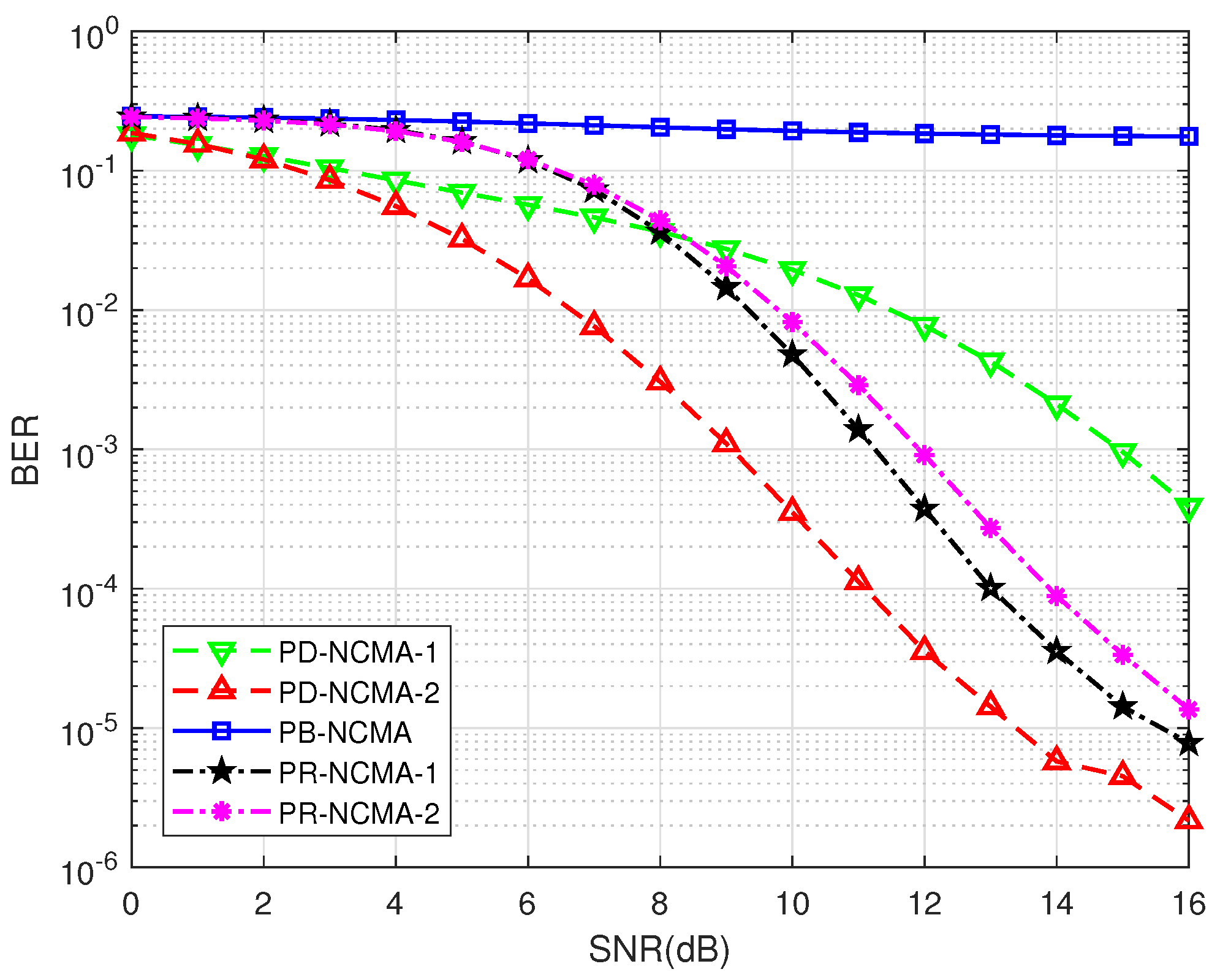
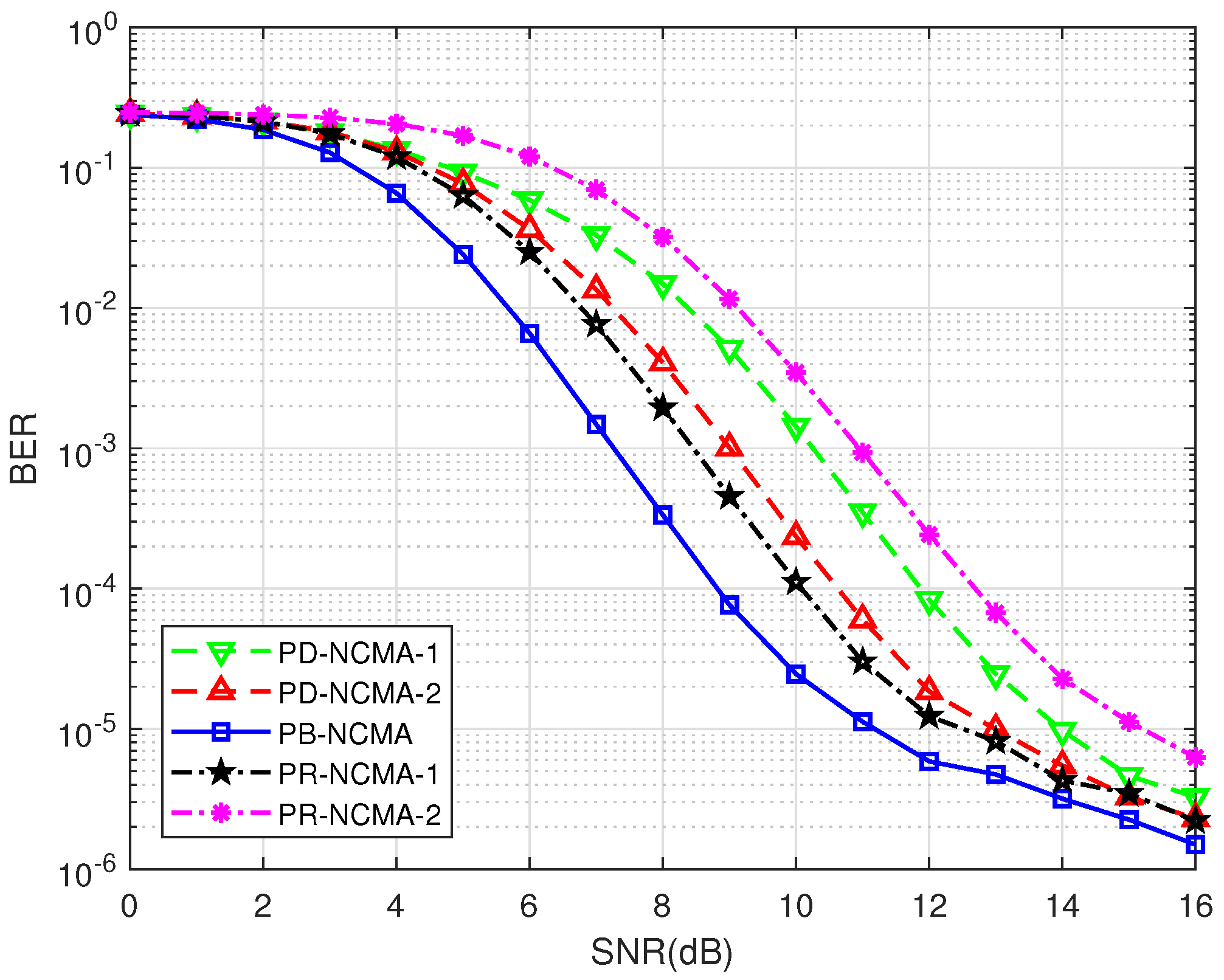
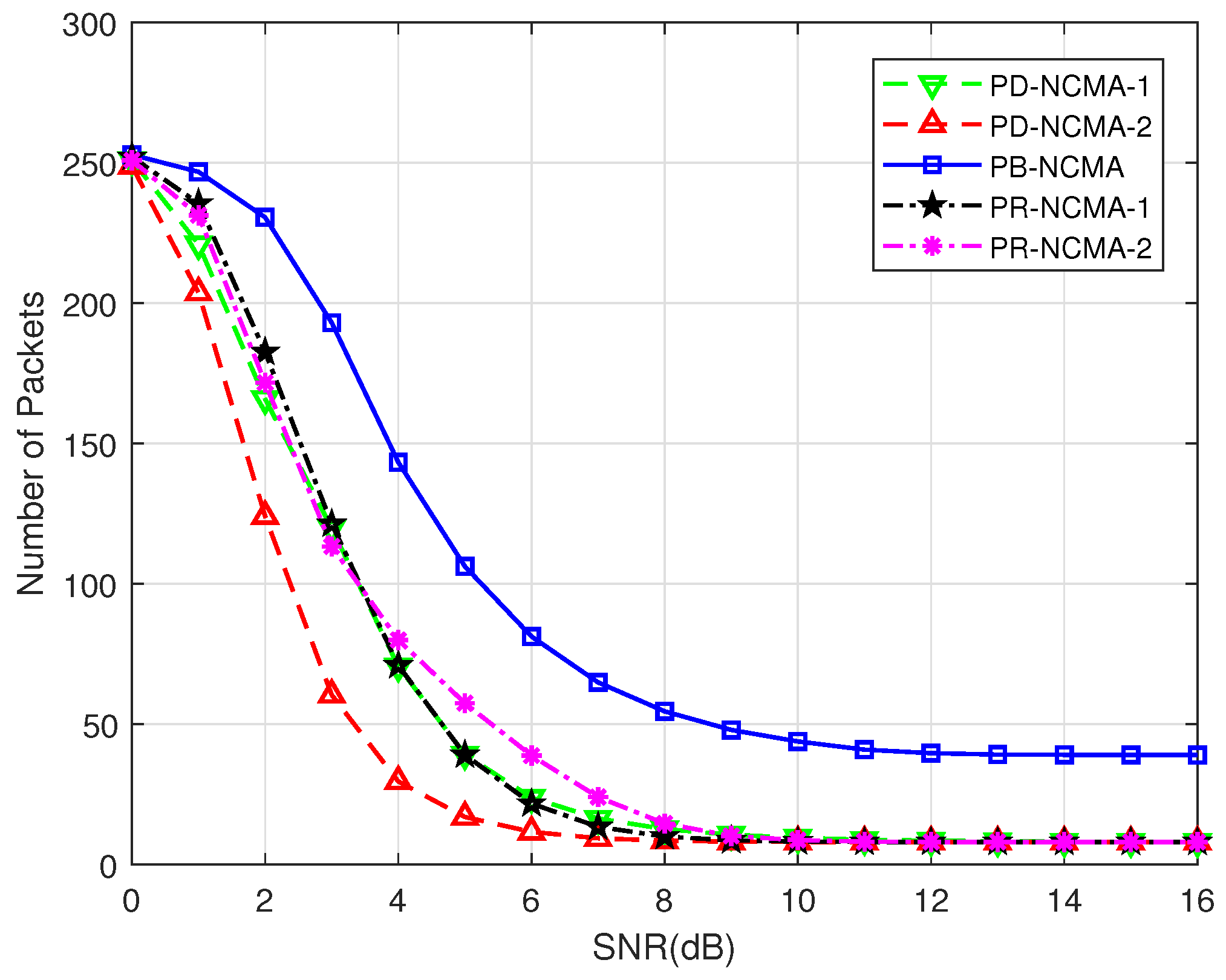
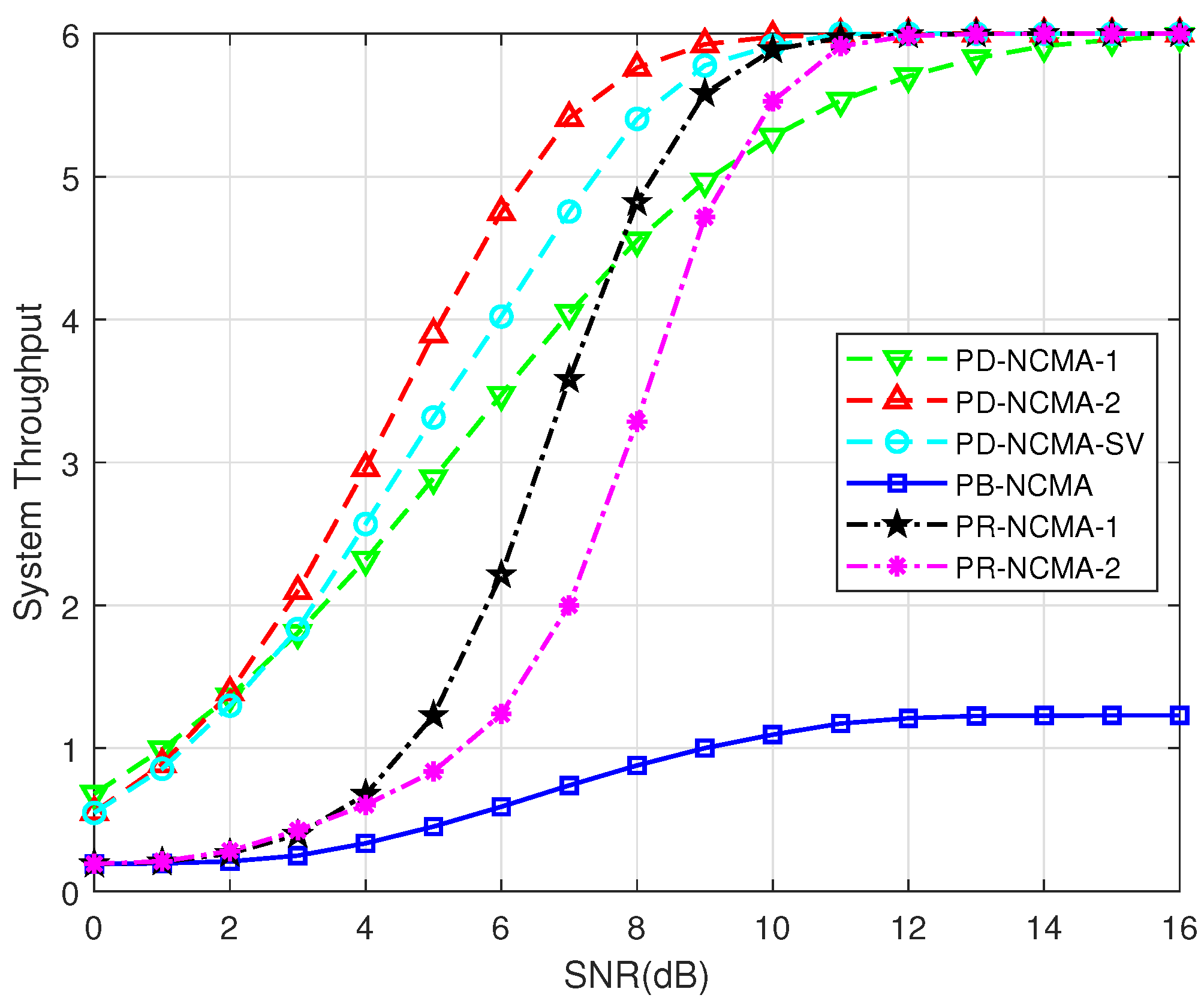
- PB-NCMA [13]: Conventional NCMA method with a power-balanced design.
- PR-NCMA-1 [15]: Phase rotation-based NCMA method with a relative phase offset of 25°.
- PR-NCMA-2 [15]: Phase rotation-based NCMA method with a relative phase offset of 45°.
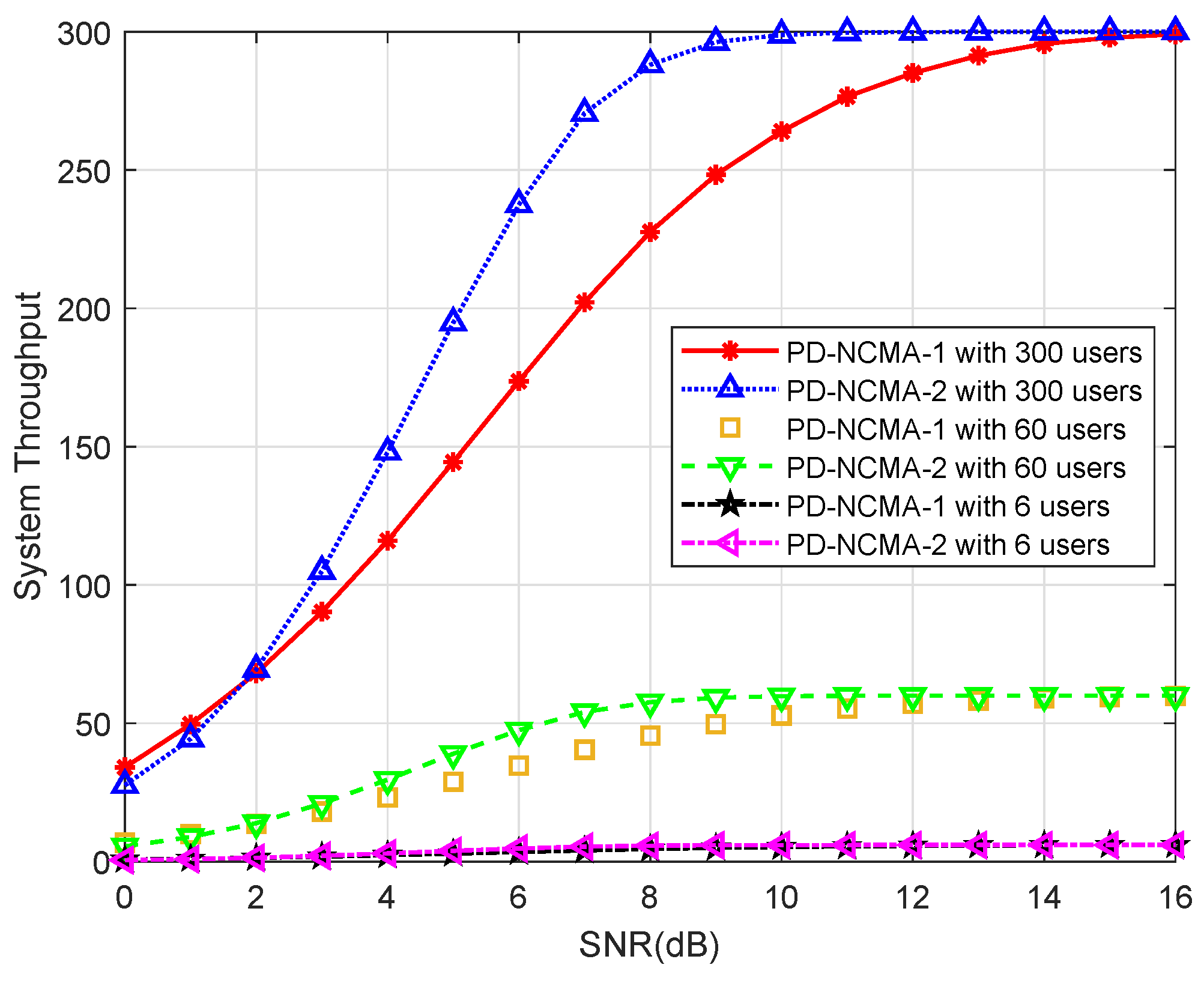
- PD-NCMA-1: Proposed power-diverse NCMA scheme with Clustering Method 1.
- PD-NCMA-2: Proposed power-diverse NCMA scheme with Clustering Method 2.
4.1. BER Performance of PNC and MUD Decoders
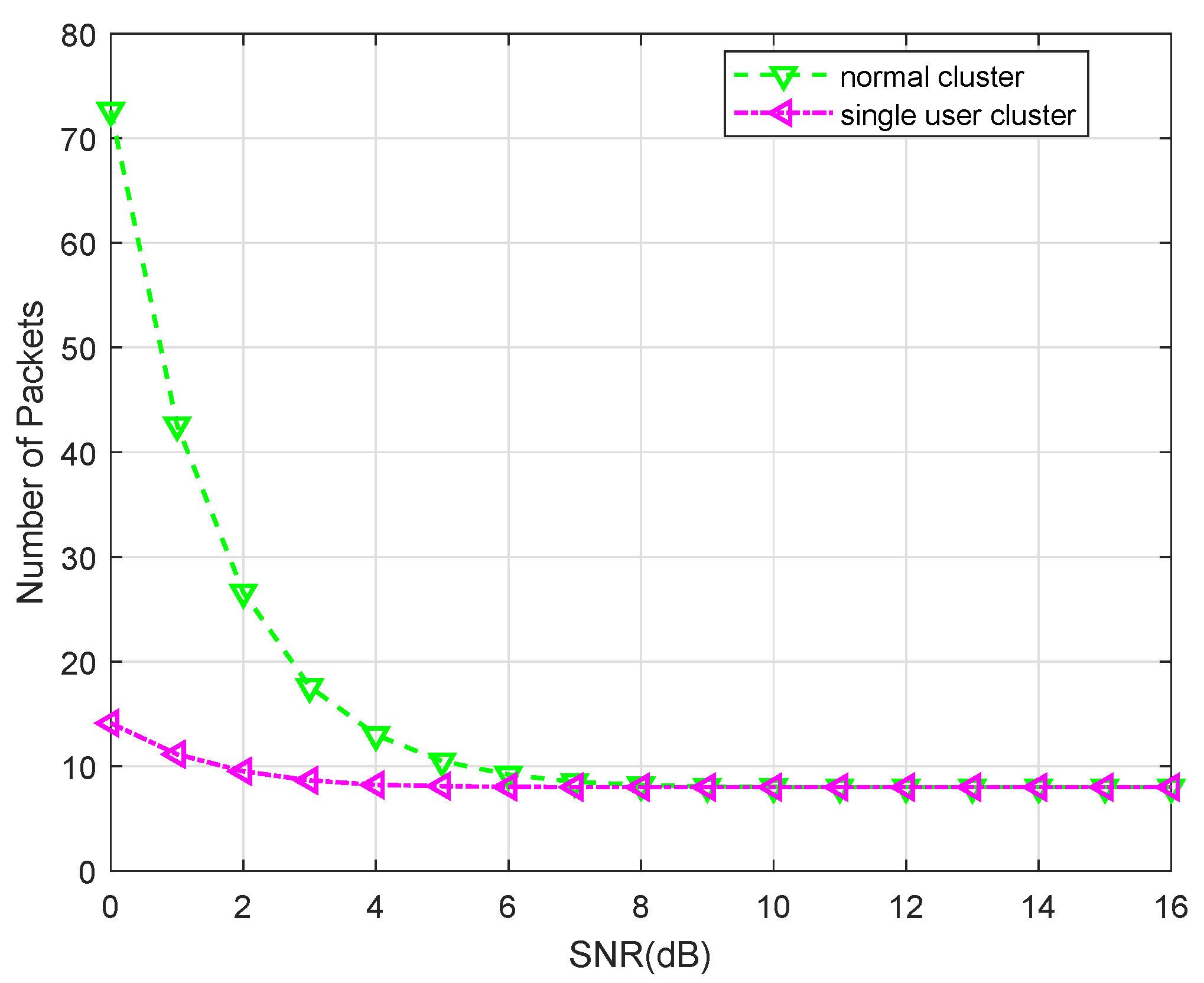
4.2. Packets Number Comparison
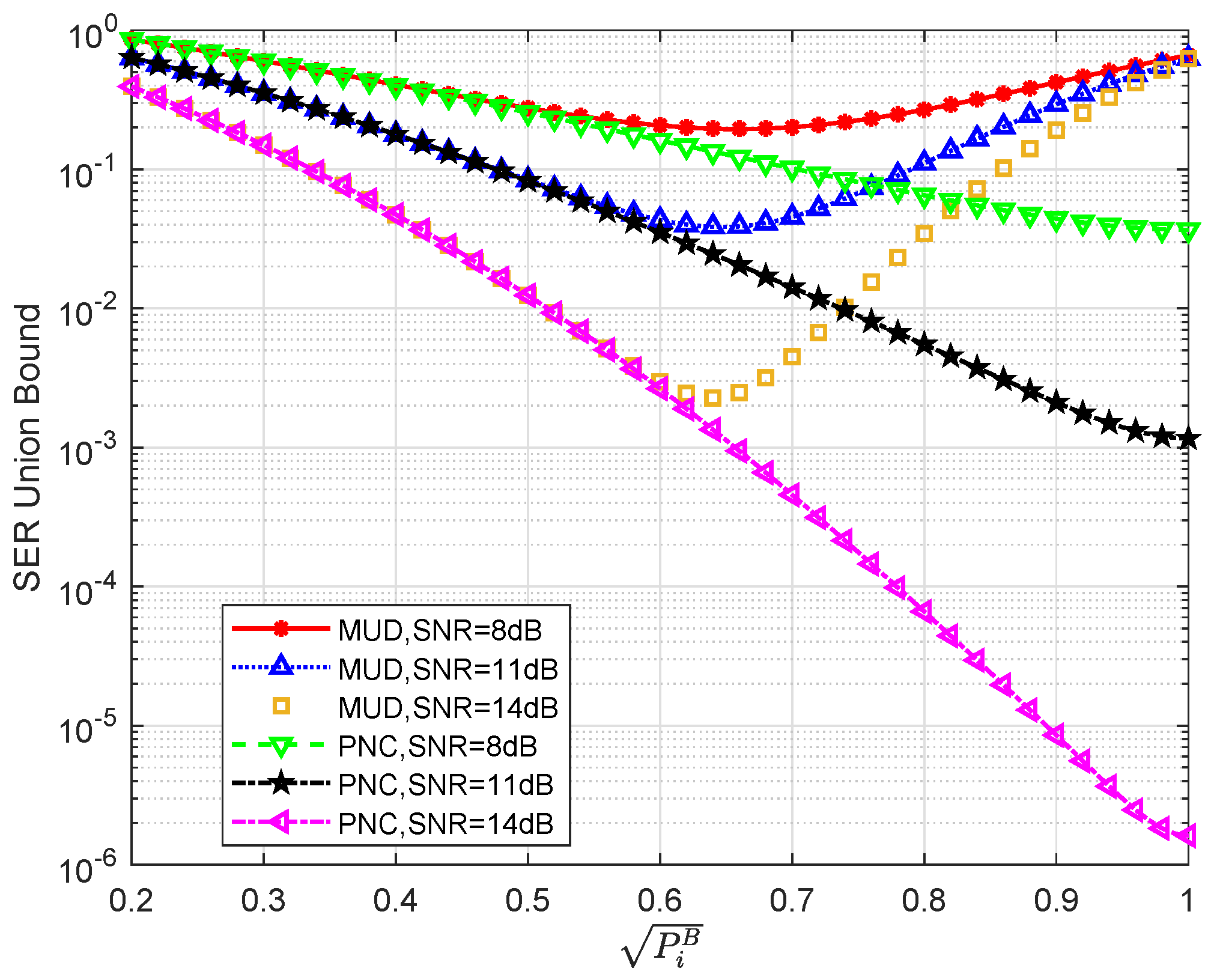
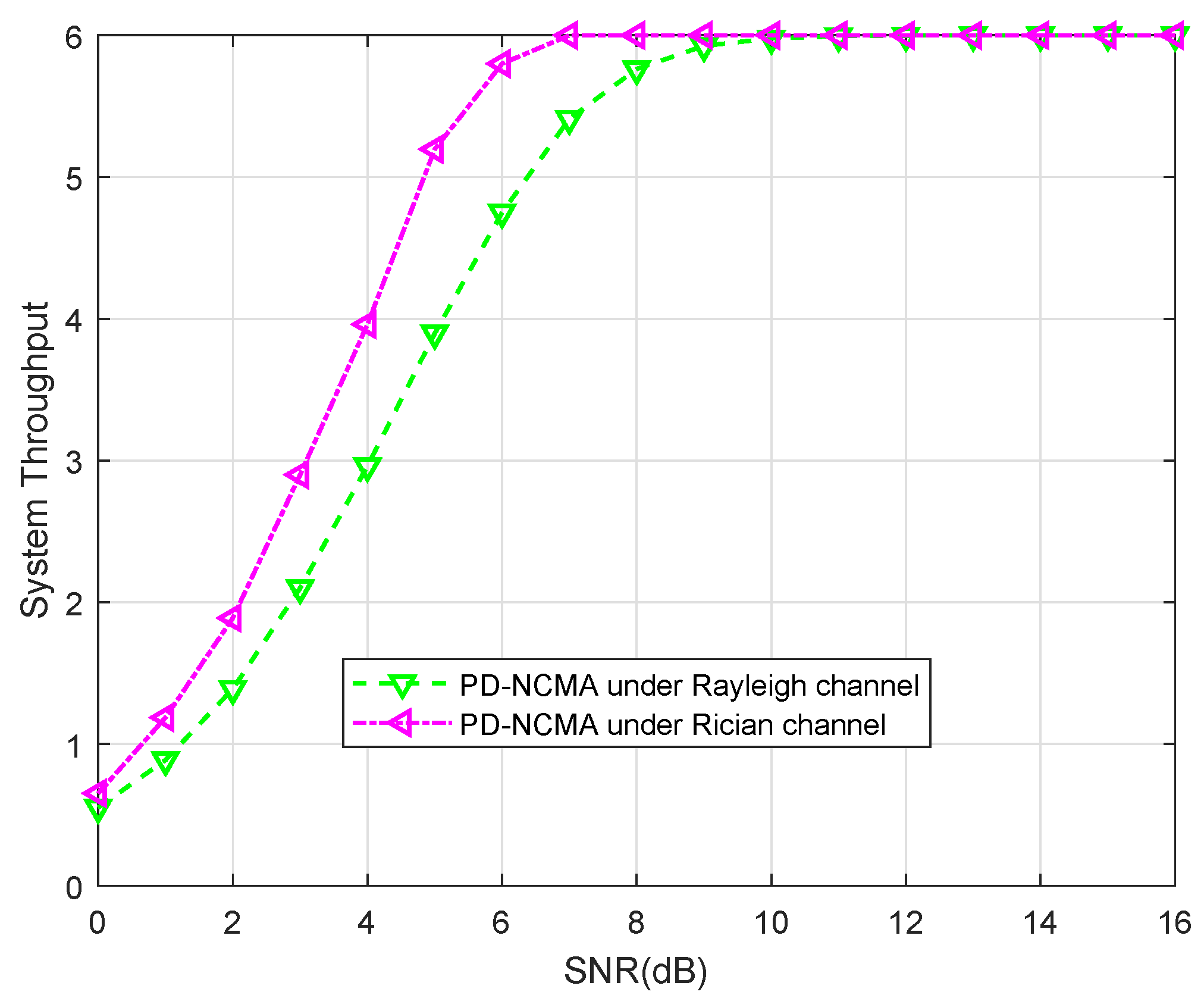
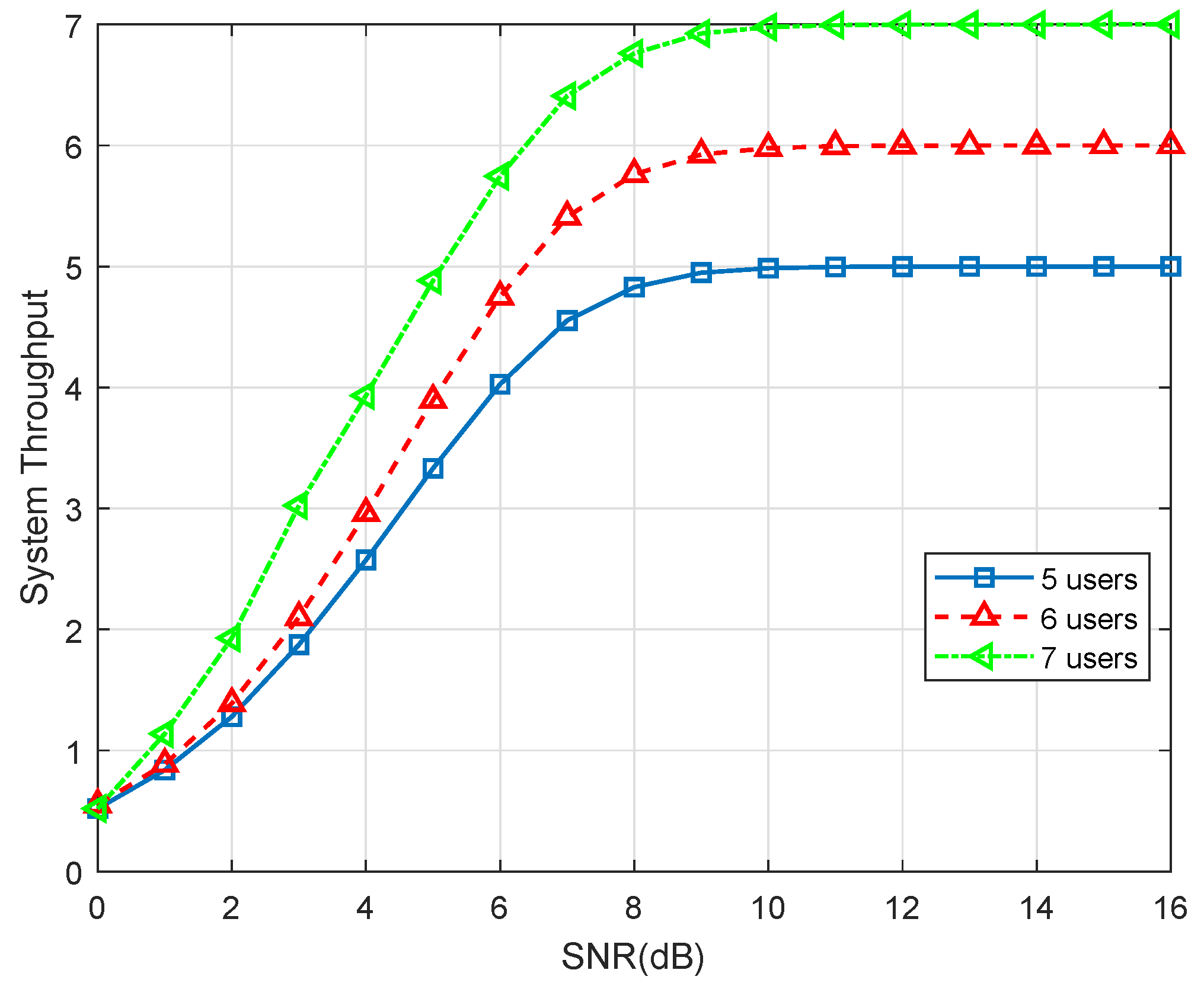
4.3. SER Union Bound and Throughput Performance
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Mondal, S.; Bepari, D.; Chandra, A.; Singh, K.; Li, C.P.; Ding, Z. A Comprehensive Survey on NOMA-Based Backscatter Communication for IoT Applications. IEEE Internet Things J. 2025, 12, 18929–18953. [Google Scholar] [CrossRef]
- Tusha, A.; Arslan, H. Interference Burden in Wireless Communications: A Comprehensive Survey from PHY Layer Perspective. IEEE Commun. Surv. Tutor. 2025, 27, 2204–2246. [Google Scholar] [CrossRef]
- Chen, J.; Xiao, Y.; Lei, X.; Ding, Y.; Niu, H.; Liu, K.; Zhong, Y.; Yang, S.; Fusco, V.; Xiang, W. A Survey on Directional Modulation: Opportunities, Challenges, Recent Advances, Implementations, and Future Trends. IEEE Internet Things J. 2025, 12, 32581–32615. [Google Scholar] [CrossRef]
- Wang, X.; Chen, H.; Tan, F. Hybrid OMA/NOMA Mode Selection and Resource Allocation in Space-Air-Ground Integrated Networks. IEEE Trans. Veh. Technol. 2024, 74, 699–713. [Google Scholar] [CrossRef]
- Khan, M.S.; Jangsher, S.; Qureshi, H.K.; Hassan, S.A.; Mumtaz, S.; Al-Dweik, A. Edge Users Spectrum Efficiency Maximization Using Spatially Aligned Carrier Aggregated NOMA in Dense Multi-Cell Networks. IEEE Trans. Veh. Technol. 2025, 74, 6138–6152. [Google Scholar] [CrossRef]
- Miuccio, L.; Panno, D.; Riolo, S. An Energy-Efficient DL-Aided Massive Multiple Access Scheme for IoT Scenarios in Beyond 5G Networks. IEEE Internet Things J. 2023, 10, 7936–7959. [Google Scholar] [CrossRef]
- Nie, D.; Yu, W.; Foh, C.H.; Ni, Q. A NOMA-Enhanced Two-Step RACH Procedure for Low-Latency Access in 5G Networks. IEEE Internet Things J. 2025, 12, 11568–11580. [Google Scholar] [CrossRef]
- Li, J.; Zheng, L.; Dang, S.; Chen, X.; Wen, M.; Peng, Y. Composition Index Modulation for Physical Layer Security in NOMA Networks. IEEE Trans. Veh. Technol. 2025, 74, 6868–6872. [Google Scholar] [CrossRef]
- Lu, L.; You, L.; Liew, S.C. Network-Coded Multiple Access. IEEE Trans. Mob. Comput. 2014, 13, 2853–2869. [Google Scholar] [CrossRef]
- Zhang, S.; Liew, S.C.; Lam, P.P. Hot Topic: Physical-Layer Network Coding. In Proceedings of the 12th Annual International Conference on Mobile Computing and Networking, Los Angeles, CA, USA, 23–29 September 2006; Voluem 8, pp. 358–365. [Google Scholar]
- You, L.; Liew, S.C.; Lu, L. Network-Coded Multiple Access II: Toward Real-Time Operation With Improved Performance. IEEE J. Sel. Areas Commun. 2015, 33, 264–280. [Google Scholar] [CrossRef]
- Pan, H.; Lu, L.; Liew, S.C. Network-Coded Multiple Access with High-Order Modulations. IEEE Trans. Veh. Technol. 2017, 66, 9776–9792. [Google Scholar] [CrossRef]
- Pan, H.; Lu, L.; Liew, S.C. Practical Power-Balanced Non-Orthogonal Multiple Access. IEEE J. Sel. Areas Commun. 2017, 35, 2312–2327. [Google Scholar] [CrossRef]
- Pan, H.; Lu, L.; Liew, S.C. Multiuser rate-diverse network-coded multiple access. In Proceedings of the 2017 IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017; pp. 2398–2402. [Google Scholar]
- Pan, H.; Liew, S.C.; Liang, J.; Shao, Y.; Lu, L. Network-Coded Multiple Access on Unmanned Aerial Vehicle. IEEE J. Sel. Areas Commun. 2018, 36, 2071–2086. [Google Scholar] [CrossRef]
- Pan, H.; Liang, J.; Liew, S.C. Practical NOMA-Based Coordinated Direct and Relay Transmission. IEEE Wirel. Commun. Lett. 2021, 10, 170–174. [Google Scholar] [CrossRef]
- Chen, Q.; Wang, W.; Yu, F.R.; Tao, M.; Zhang, Z. Content Caching Oriented Popularity Prediction: A Weighted Clustering Approach. IEEE Trans. Wirel. Commun. 2021, 20, 623–636. [Google Scholar] [CrossRef]
- Zhang, Z.; Tao, M. Deep Learning for Wireless Coded Caching with Unknown and Time-Variant Content Popularity. IEEE Trans. Wirel. Commun. 2021, 20, 1152–1163. [Google Scholar] [CrossRef]
- Tao, M.; Chen, E.; Zhou, H.; Yu, W. Content-Centric Sparse Multicast Beamforming for Cache-Enabled Cloud RAN. IEEE Trans. Wirel. Commun. 2016, 15, 6118–6131. [Google Scholar] [CrossRef]
- Shao, X.; Yang, C.; Chen, D.; Zhao, N.; Yu, F.R. Dynamic IoT Device Clustering and Energy Management with Hybrid NOMA Systems. IEEE Trans. Ind. Inform. 2018, 14, 4622–4630. [Google Scholar] [CrossRef]
- Pan, H.; Liang, J.; Liew, S.C.; Leung, V.C.; Li, J. Timely Information Update with Nonorthogonal Multiple Access. IEEE Trans. Ind. Inform. 2021, 17, 4096–4106. [Google Scholar] [CrossRef]
- Tse, D.; Viswanath, P. Fundamentals of Wireless Communications; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]




Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Q.; Xiang, X.; Dang, J.; Li, C. Content-Centric Clustering and Power-Diverse Allocation in Downlink Network-Coded Multiple Access System. Electronics 2025, 14, 4477. https://doi.org/10.3390/electronics14224477
Li Q, Xiang X, Dang J, Li C. Content-Centric Clustering and Power-Diverse Allocation in Downlink Network-Coded Multiple Access System. Electronics. 2025; 14(22):4477. https://doi.org/10.3390/electronics14224477
Chicago/Turabian StyleLi, Qiao, Xin Xiang, Jiahao Dang, and Chunhui Li. 2025. "Content-Centric Clustering and Power-Diverse Allocation in Downlink Network-Coded Multiple Access System" Electronics 14, no. 22: 4477. https://doi.org/10.3390/electronics14224477
APA StyleLi, Q., Xiang, X., Dang, J., & Li, C. (2025). Content-Centric Clustering and Power-Diverse Allocation in Downlink Network-Coded Multiple Access System. Electronics, 14(22), 4477. https://doi.org/10.3390/electronics14224477




