Root Contracting: A Novel Method and Utility for Implementing Design by Contract in Domain-Driven Design with Event Sourcing
Abstract
1. Introduction
- Contracting with a simple utility. Using a utility library like uContract, which does not alter the host language, allows root-contracted programs to compile directly without pre- or post-processing. This method simplifies adapting to changes in the host language compared to existing DbC extensions.
- Collocated contracts and targets. Root contracting inlines assertions of an aggregate’s properties as code segments that are collocated with the targets that the assertions verify in the program text.
- Contracts as source code. Contracts are written in standard programming constructs understood by compilers, unlike annotations or comments in some DbC extensions, which are not checked by compilers.
- Comprehensive support for contract evaluation and monitoring. Contracts can be activated or deactivated as recommended by DbC in the development, testing, or production phases.
- Economy of contracts. Contracts apply only to aggregate roots; objects within aggregates are not subject to contracts. Therefore, contract management and maintenance focus exclusively on aggregate roots.
2. Background and Motivation
2.1. A Historical Perspective on DbC and DbC Extensions
- Contract specification refers to the language constructs used to write the precondition, postcondition, and class invariant. Contracts are assertions that define the obligations and benefits of a software supplier and its client. The precondition establishes the client’s obligations, while the postcondition states the guarantees provided by the supplier. The class invariant defines properties that each instance of a class must maintain before and after any invocation of its methods.
- Contract monitoring is the mechanism to configure runtime contract checking. Because executing contracts requires additional computation, software developers and operators should have the option to enable or disable specific types of contracts at runtime. For example, they can activate every type of contract during development and only keep the precondition enabled during operation.
- Subcontracting involves applying contracts within an inheritance hierarchy. Specifically, a derived class’s contracts are determined according to the subcontracting rules: an overriding method’s precondition is combined with its overridden method’s precondition using logical OR, and the postcondition with logical AND; a derived class’s class invariant is combined with that of the base class using logical AND.
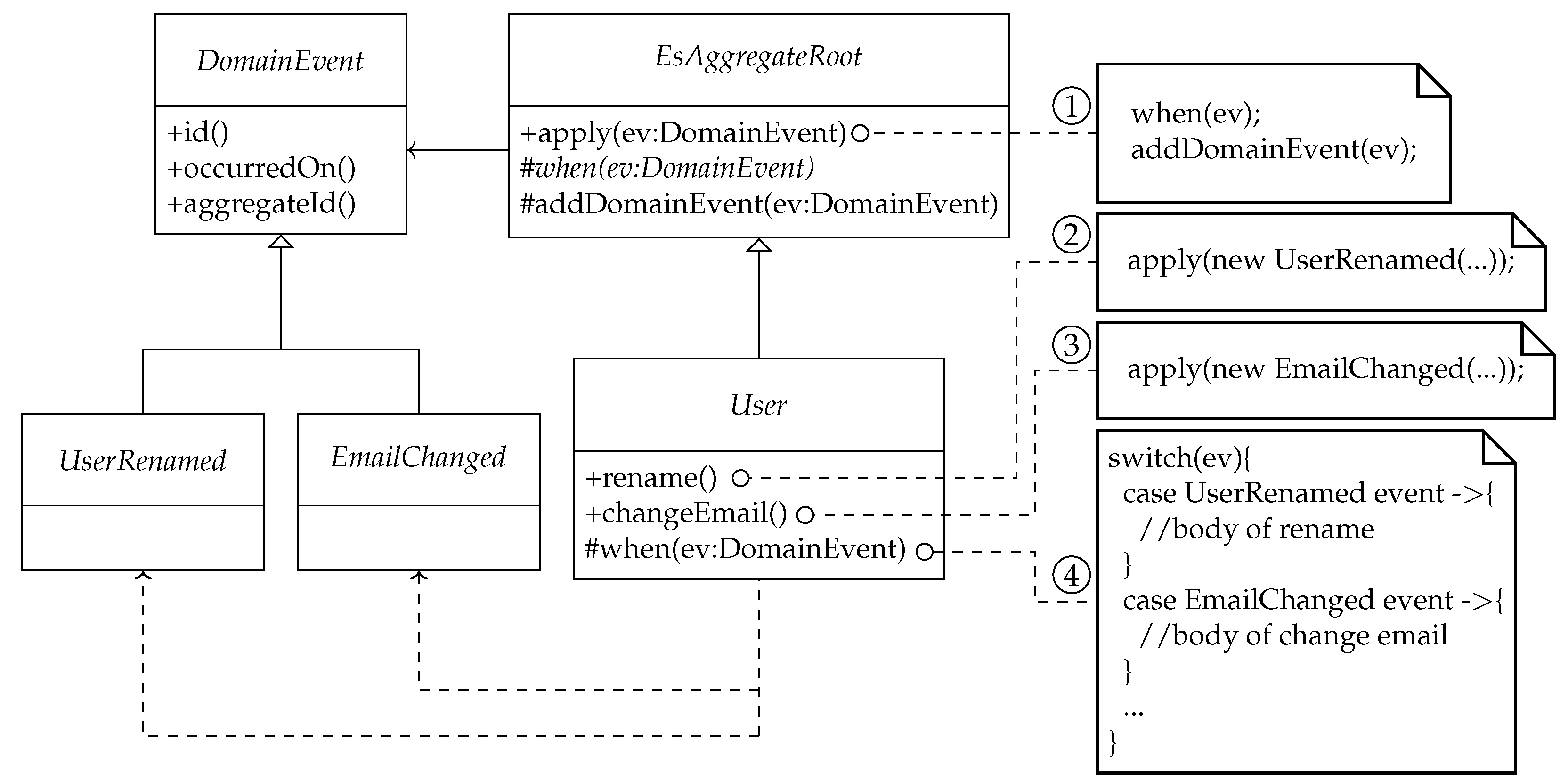
2.2. A Pattern-Based Design of Event-Sourced Aggregates
2.3. Motivation of Root Contracting
3. The Proposed Method of Root Contracting
3.1. Aggregate Root Correctness Rules
3.1.1. Correctness Rules for Normal Situations
3.1.2. Correctness Rules for Exceptional Situations
3.2. The Proposed Root Contracting
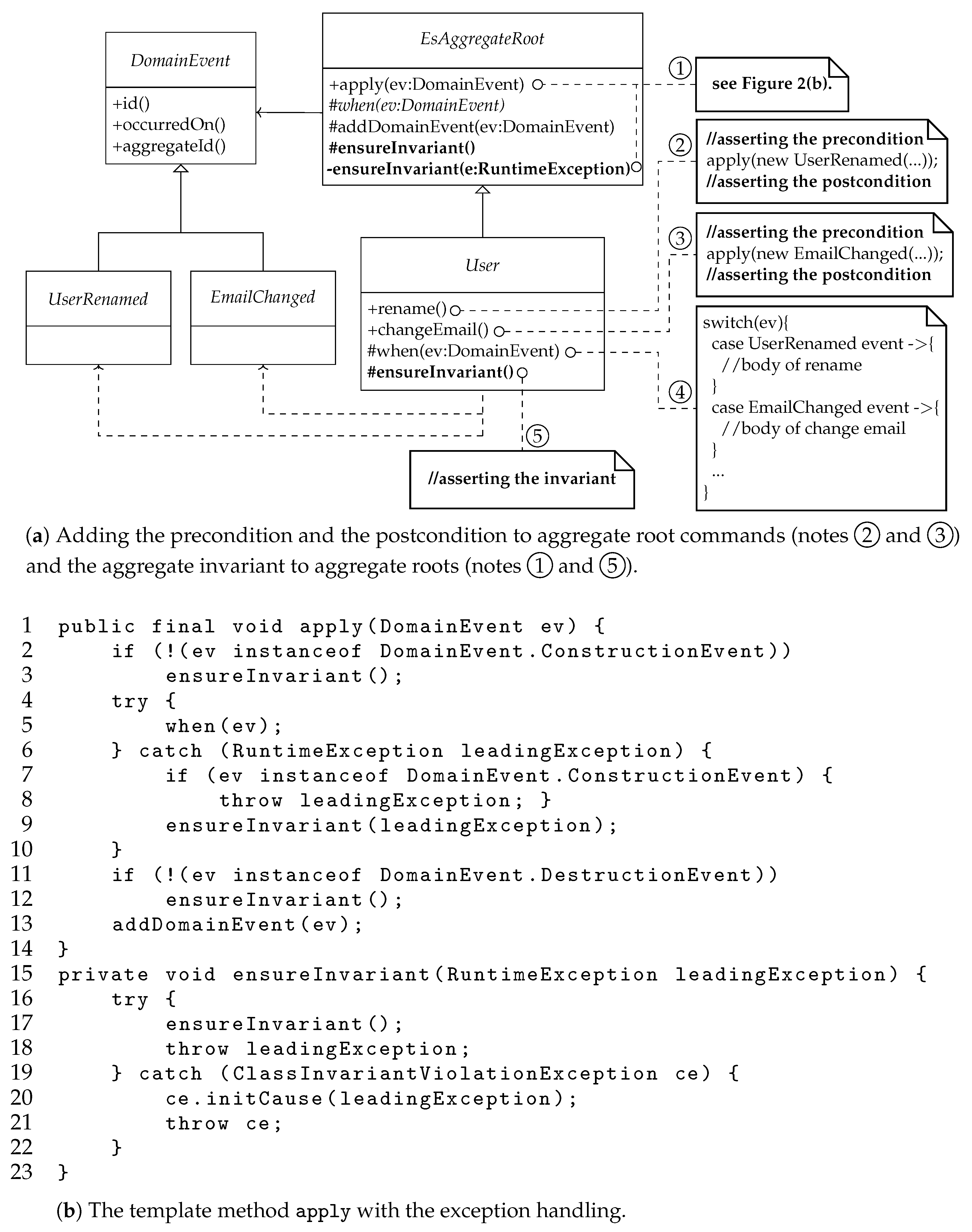
3.2.1. Adding Precondition and Postcondition Checks in Command Bodies
3.2.2. Adding Invariant Checks and Exception Handling in Template Method
- Lines 2–3, the template method apply ensures the aggregate invariant by calling the hook operation ensureInvariant except when the event is a construction event, in which case the aggregate does not yet exist. A concrete aggregate root overrides the hook operation as shown in the User class; see note ➄ of Figure 2a.
- Lines 4–10, the try-catch block delegates event processing to the primitive operation when for business processing and handles any exception raised there. In lines 7–8, an exception raised in processing a construction event is rethrown without asserting the aggregate invariant since the aggregate was not created. For any other event that raises an exception, the exception is delegated to the operation ensureInvariant(RuntimeException) for further processing (see the last bullet point below).
- Lines 11–12, the template method apply checks for an aggregate root destruction event and skips asserting the aggregate invariant through ensureInvariant since the aggregate has been deleted. Otherwise, the aggregate invariant is asserted for other events.
- Lines 15–23, the method ensureInvariant(RuntimeException) takes a business processing exception raised by the operation when as its parameter and rethrows it if the aggregate invariant asserts successfully; otherwise, it throws an invariant violation exception, making the raised exception its cause. Semantically, the client can attempt a retry in the former case since the aggregate invariant holds despite the raised exception; the client should not attempt a retry in the latter case since the aggregate invariant does not hold.
3.2.3. An Example of rename Command in User Aggregate
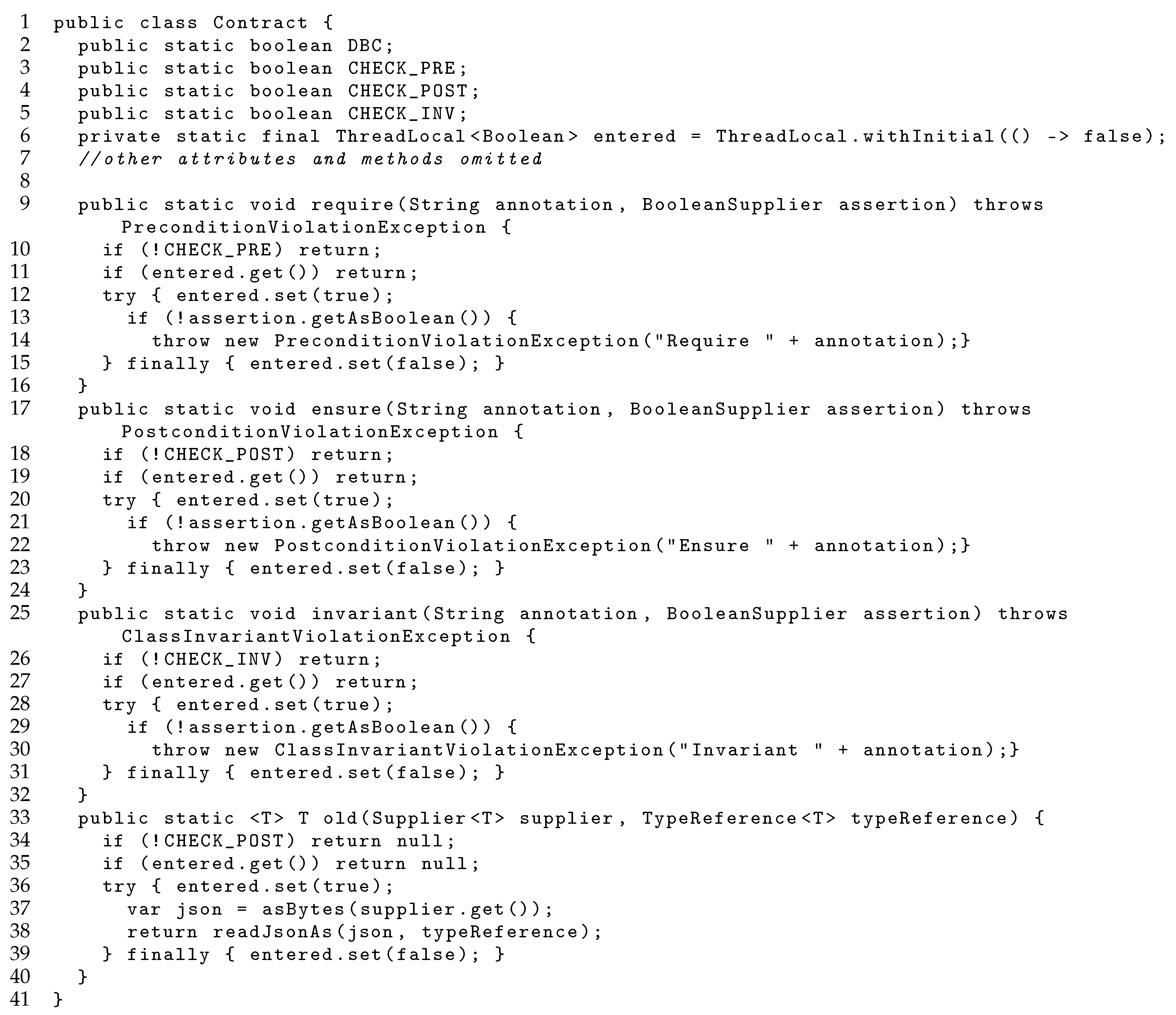
4. uContract: An Open-Source Java Utility for Root Contracting
4.1. Contract Specification
4.2. Contract Monitoring
4.3. Subcontracting
4.4. Other Important Implementation Details
5. Experiment: Performance Overhead Analysis
5.1. Experiment Setup
5.1.1. Experiment Subject: ezKanban’s Workflow Aggregate
5.1.2. Experiment Design
5.2. Results
5.2.1. Experiment 1: Performance Overhead of Root Contracting with uContract
- (1)
- The execution of the all_off configuration spends 0.407–0.495 ms. The execution times are attributed to checking the flags CHECK_PRE, CHECK_POST, and CHECK_INV and handling the lambda functions in the assertions (see Section 5.3).
- (2)
- The execution times of the default pre_on configuration are 0.677–0.768 ms, an increase of about 0.2–0.3 ms compared to their counterparts in the all_off configuration. As the precondition mainly checks the input value to be non-null or non-empty, the execution times only increase slightly.
- (3)
- The execution times of the pre_post_on configuration fall in the range of 19.916–546.059 ms, a significant increase compared to their counterparts in the default pre_on configuration. The increases reflect mainly the time spent to check that the stages untouched by a command remain unchanged, as will be explored below in Table 6.
- (4)
- The execution times of the all_on configuration are 20.592–550.035 ms, a relatively small increase of about 0.6–5.8 ms from the pre_post_on configuration due to further checking the class invariant. In this experiment setup, the overhead is much smaller compared to the overhead of checking the postcondition.
5.2.2. Experiment 2: Precondition Performance Overhead of Standard Java vs. uContract
5.3. Discussion of Experimental Findings
6. Comparative Evaluation
6.1. A Taxonomy of Contract Specification
6.2. A Quality-Attributes-Based Comparison
6.2.1. Sustainability
6.2.2. Usability
- Source compatibility (SC) indicates whether the extended DbC tool can be used without modifying the host language, IDE, or existing pluggable features.
- No symbolic barrier (NSB) determines whether a contract and its target are related from the compiler’s point of view. A symbolic barrier exists if a change in the contract does not cause the compiler to generate an error on its target, or vice versa.
- Line number information for debugging (LNIFD) specifies whether a DbC tool shows the line number of the assertion statement that raises a contract violation exception.
- Syntax-aware specification (SAS) determines whether a compiler or an interpreter checks syntax errors in contracts.
- Collocation of contract and target (COCAT) indicates whether contracts collocate with the contracted target.
- Low decommissioning impact (LDI) defines the level of impact on the contracted program caused by decommissioning contracts.
6.2.3. Portability
6.2.4. Developability
6.2.5. Overall Ratings
6.3. Other Relevant Aspects
7. Discussion
7.1. Correctness and Robustness
7.2. Applicability of Root Contracting in Broader Contexts
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Emily, H.; Oliver, B. Event-driven architectures in modern systems: Designing scalable, resilient, and real-time solutions. Int. J. Trend Sci. Res. Dev. 2020, 4, 1958–1976. [Google Scholar]
- Overeem, M.; Spoor, M.; Jansen, S.; Brinkkemper, S. An Empirical Characterization of Event Sourced Systems and Their Schema Evolution—Lessons from Industry. J. Syst. Softw. 2021, 178, 110970. [Google Scholar] [CrossRef]
- Evans, E. Domain-Driven Design Reference: Definitions and Pattern Summaries; Dog Ear Publishing: Indianapolis, IN, USA, 2014. [Google Scholar]
- Myllynen, T.; Kamau, E.; Mustapha, S.D.; Babatunde, G.O.; Alabi, A.A. Developing a Conceptual Model for Cross-Domain Microservices Using Event-Driven and Domain-Driven Design. Int. J. Multidiscip. Res. Growth Eval. 2023, 4, 635–638. [Google Scholar] [CrossRef]
- Meyer, B. Object-Oriented Software Construction, 2nd ed.; Prentice Hall: Englewood Cliffs, NJ, USA, 1997. [Google Scholar]
- Evans, E. Domain-Driven Design: Tackling Complexity in the Heart of Software; Addison-Wesley Professional: Boston, MA, USA, 2004. [Google Scholar]
- Wirfs-brock, R.J. Driven to ... Discovering Your Design Values. IEEE Softw. 2007, 24, 9–11. [Google Scholar] [CrossRef]
- Larman, C. Applying UML and Patterns: An Introduction to Object-Oriented Analysis and Design and Iterative Development, 3rd ed.; Pearson: Upper Saddle River, NJ, USA, 2004. [Google Scholar]
- Kramer, R. iContract – the Java Design by Contract Tool. In Proceedings of the Technology of Object-Oriented Languages, TOOLS 26 (Cat. No. 98EX176), Santa Barbara, CA, USA, 3–7 August 1998; pp. 295–307. [Google Scholar] [CrossRef]
- Duncan, A.; Hölzle, U. Adding Contracts to Java with Handshake; Technical Report TRCS98-32; The University of California at Santa Barbara: Santa Barbara, CA, USA, 1998. [Google Scholar]
- Bartetzko, D.; Fischer, C.; Möller, M.; Wehrheim, H. Jass—Java with Assertions. Electron. Notes Theor. Comput. Sci. 2001, 55, 103–117. [Google Scholar] [CrossRef]
- Karaorman, M.; Abercrombie, P. jContractor: Introducing Design-by-Contract to Java Using Reflective Bytecode Instrumentation. Form. Methods Syst. Des. 2005, 27, 275–312. [Google Scholar] [CrossRef][Green Version]
- Lackner, M.; Krall, A.; Puntigam, F. Supporting Design by Contract in Java. J. Object Technol. 2002, 1, 57–76. [Google Scholar] [CrossRef]
- Burdy, L.; Cheon, Y.; Cok, D.R.; Ernst, M.D.; Kiniry, J.R.; Leavens, G.T.; Leino, K.R.M.; Poll, E. An overview of JML tools and applications. Int. J. Softw. Tools Technol. Transf. 2005, 7, 212–232. [Google Scholar] [CrossRef]
- Leavens, G.T.; Cheon, Y. Design by Contract with JML. Available online: http://www.jmlspecs.org/jmldbc.pdf (accessed on 19 September 2025).
- Leavens, G.T.; Baker, A.L.; Ruby, C. Preliminary Design of JML: A Behavioral Interface Specification Language for Java. ACM SIGSOFT Softw. Eng. Notes 2006, 31, 1–38. [Google Scholar] [CrossRef]
- Feldman, Y.A.; Barzilay, O.; Tyszberowicz, S. Jose: Aspects for Design by Contract. In Proceedings of the Fourth IEEE International Conference on Software Engineering and Formal Methods (SEFM’06), Pune, India, 11–15 September 2006; pp. 80–89. [Google Scholar] [CrossRef]
- Chen, C.T.; Cheng, Y.C.; Hsieh, C.Y. Contract Specification in Java: Classification, Characterization, and a New Marker Method. IEICE Trans. Inf. Syst. 2008, E91.D, 2685–2692. [Google Scholar] [CrossRef][Green Version]
- Lê, N.M. Cofoja. Available online: https://github.com/nhatminhle/cofoja (accessed on 19 September 2025).
- Barnett, M.; Leino, K.R.M.; Schulte, W. The Spec# Programming System: An Overview. In Proceedings of the Construction and Analysis of Safe, Secure, and Interoperable Smart Devices, Marseille, France, 10–14 March 2004; Barthe, G., Burdy, L., Huisman, M., Lanet, J.L., Muntean, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 49–69. [Google Scholar]
- Chavacava. dbc4go. Available online: https://github.com/chavacava/dbc4go (accessed on 19 September 2025).
- Cheng, Y.C.; Chen, C.T.; Hsieh, C.Y. ezcontract: Using marker library and bytecode instrumentation to support design by contract in java. In Proceedings of the 14th Asia-Pacific Software Engineering Conference (APSEC’07), Nagoya, Japan, 4–7 December 2007; pp. 502–509. [Google Scholar] [CrossRef]
- Meyer, B. Applying ‘Design by Contract’. Computer 1992, 25, 40–51. [Google Scholar] [CrossRef]
- OpenJML. OpenJML. Available online: https://github.com/OpenJML/OpenJML (accessed on 19 September 2025).
- Microsoft. Code Contracts. Available online: https://learn.microsoft.com/en-us/dotnet/framework/debug-trace-profile/code-contracts (accessed on 19 September 2025).
- Zimarev, A. Hands-On Domain-Driven Design with .NET Core: Tackling Complexity in the Heart of Software by Putting DDD Principles into Practice; Packt Publishing Ltd.: Birmingham, UK, 2019. [Google Scholar]
- Millett, S.; Tune, N. Patterns, Principles, and Practices of Domain-Driven Design; Wrox Press: Indianapolis, IN, USA, 2015. [Google Scholar]
- Vernon, V. Implementing Domain-Driven Design; Addison-Wesley Professional: Boston, MA, USA, 2013. [Google Scholar]
- Khononov, V. Learning Domain-Driven Design: Aligning Software Architecture and Business Strategy; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2021. [Google Scholar]
- Gamma, E.; Helm, R.; Johnson, R.; Vlissides, J. Design Patterns: Elements of Reusable Object-Oriented Software; Addison-Wesley Professional: Boston, MA, USA, 1995. [Google Scholar]
- Hu, Y.H.; Chen, C.T.; Cheng, Y.C. How We Develop an Online Kanban Board Game in Two Months? In Proceedings of the 2022 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 14–16 December 2022; pp. 1901–1906. [Google Scholar] [CrossRef]
- Martin, R.C.; Grenning, J.; Brown, S. Clean Architecture: A Craftsman’s Guide to Software Structure and Design; Prentice Hall: Englewood Cliffs, NJ, USA, 2018. [Google Scholar]
- Smart, J.F.; Molak, J. BDD in Action: Behavior-Driven Development for the Whole Software Lifecycle, 2nd ed.; Manning: Greenwich, CT, USA, 2023. [Google Scholar]
- Kumar, A. CQRS (Command Query Responsibility Segregation); Independently published, 2019. Available online: https://www.amazon.com/-/zh_TW/CQRS-Command-Query-Responsibility-Segregation/dp/1795874775#detailBullets_feature_div (accessed on 19 September 2025).
- Zhong, C.; Li, S.; Huang, H.; Liu, X.; Chen, Z.; Zhang, Y.; Zhang, H. Domain-driven design for microservices: An evidence-based investigation. IEEE Trans. Softw. Eng. 2024, 50, 1425–1449. [Google Scholar] [CrossRef]
- Chen, C.T.; Cheng, Y.C.; Hsieh, C.Y.; Wu, I.L. Exception handling refactorings: Directed by goals and driven by bug fixing. J. Syst. Softw. 2009, 82, 333–345. [Google Scholar] [CrossRef]
- Garcia, A.F.; Rubira, C.M.; Romanovsky, A.; Xu, J. A comparative study of exception handling mechanisms for building dependable object-oriented software. J. Syst. Softw. 2001, 59, 197–222. [Google Scholar] [CrossRef]
- Chen, C.T.; ezKanban team of Software System Lab of Taipei Tech. uContract v2.0.0. Available online: https://gitlab.com/TeddyChen/ucontract (accessed on 19 September 2025).
- Chen, C.T.; ezKanban team of Software System Lab of Taipei Tech. Root-Contracting. Available online: https://gitlab.com/TeddyChen/root-contracting (accessed on 19 September 2025).
- Ecma International. Standard ECMA-404: The JSON Data Interchange Syntax. Available online: https://www.ecma-international.org/wp-content/uploads/ECMA-404_2nd_edition_december_2017.pdf (accessed on 19 September 2025).
- Oracle and/or Its Affiliates. Class ThreadLocal<T>. Available online: https://docs.oracle.com/javase/8/docs/api/java/lang/ThreadLocal.html (accessed on 19 September 2025).
- Anderson, D.J. Kanban: Successful Evolutionary Change for Your Technology Business; Blue Hole Press: Milford, CT, USA, 2010. [Google Scholar]
- Khorikov, V. Unit Testing Principles, Practices, and Patterns; Manning Publications: Greenwich, CT, USA, 2020. [Google Scholar]
- Oracle and/or Its Affiliates. About Java Flight Recorder. Available online: https://docs.oracle.com/javacomponents/jmc-5-4/jfr-runtime-guide/about.htm#JFRUH170 (accessed on 15 October 2025).
- Chen, C.T.; Yen, Y.C.; Hu, Y.H.; Cheng, Y.C. uContract_performance_experiment. Available online: https://gitlab.com/TeddyChen/ucontract_performance_experiment (accessed on 24 October 2025).
- Oracle and/or Its Affiliates. The Invokedynamic Instruction. Available online: https://docs.oracle.com/javase/7/docs/technotes/guides/vm/multiple-language-support.html#invokedynamic (accessed on 19 September 2025).
- Pabón, L. godbc v1.1.0. Available online: https://github.com/lpabon/godbc (accessed on 19 September 2025).
- Boost.org. boost-1.88.0. Available online: https://github.com/boostorg/contract (accessed on 19 September 2025).
- Parquery. icontract 2.7.1. Available online: https://github.com/Parquery/icontract (accessed on 19 September 2025).
- Ede, R. contracts v0.6.6. Available online: https://crates.io/crates/contracts (accessed on 19 September 2025).
- Aghaei, M. An Experimental Evaluation of Java Design-by-Contract Extensions. Master’s Thesis, University of Oulu, Oulu, Finland, 2018. [Google Scholar]
- Tschannen, J.; Furia, C.A.; Nordio, M.; Polikarpova, N. AutoProof: Auto-active Functional Verification of Object-oriented Programs. arXiv 2015, arXiv:1501.03063. [Google Scholar] [CrossRef]
- OpenJML. OpenJML—Formal Methods Tool for Java and the Java Modeling Language (JML). Available online: https://www.openjml.org/documentation/introduction.html (accessed on 12 October 2025).
- Leitner, A.; Ciupa, I.; Oriol, M.; Meyer, B.; Fiva, A. Contract Driven Development = Test Driven Development—Writing Test Cases. In Proceedings of the 6th Joint Meeting of the European Software Engineering Conference and the ACM SIGSOFT Symposium on The Foundations of Software Engineering, Dubrovnik, Croatia, 3–7 September 2007; pp. 425–434. [Google Scholar] [CrossRef]
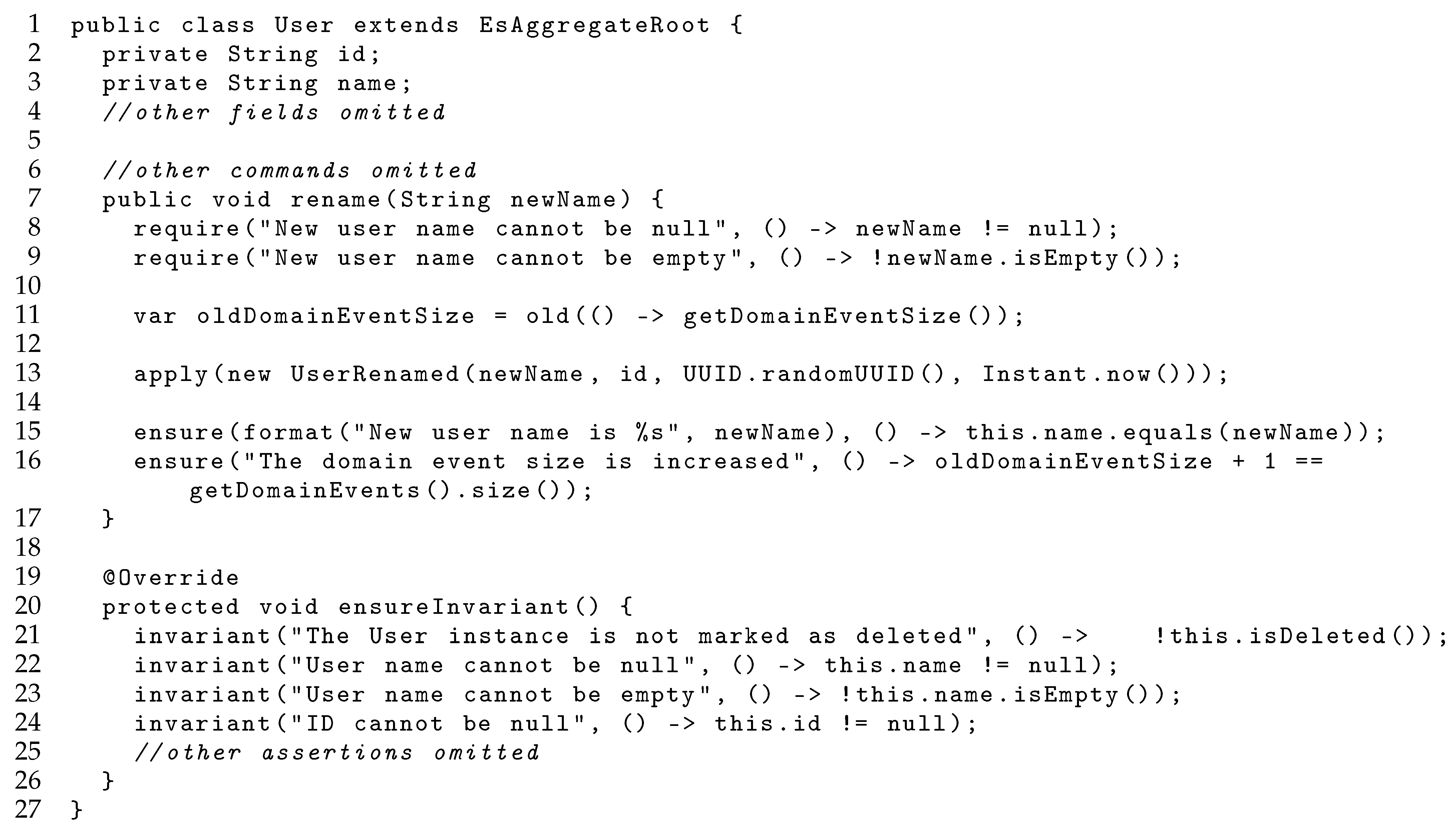



| Contract Type | Note(s) in Figure 2a | uContract Function(s) | Lines in Figure 3 |
|---|---|---|---|
| precondition | ➁ and ➂ | require | lines 8–9 |
| postcondition | ➁ and ➂ | old and ensure | line 11 and lines 15–16 |
| aggregate invariant | ➄ | invariant | lines 21–24 |
| Feature | Existing DbC Extenstions | Root Contracting with uContract |
|---|---|---|
| Contract Specification Targets | Classes and interfaces | Event-sourced aggregate roots |
| DbC Support | Full support | No subcontracting |
| Contract Translation | Full language compilers, preprocessors, and postprocessors | No translation needed |
| Contract Type | Name of Operation/ Utility Function | Configuration | |||
|---|---|---|---|---|---|
| all_off | pre_on | pre_post_on | all_on | ||
| Precondition | require or ignore | v | v | v | |
| Postcondition | old | v | v | ||
| ensureAssignable | v | v | |||
| ensure | v | v | |||
| Class Invariant | invariant | v | |||
| Computer Specifications | |
|---|---|
| Processor | Intel(R) Core(TM) i7-10700 CPU @ 2.90 GHz |
| Memory | 16.0 GB DDR4-2933 MHz |
| Storage | 1 TB HDD ST1000DM010-2EP102, 256 GB SSD HFM256GDJTNG-8310A |
| System Type | 64-bit operating system, x64-based processor |
| Operating System | Windows 10 Pro [Version 10.0.19045.5854] |
| Configuration | Average Execution Time (ms) | ||
|---|---|---|---|
| Small | Medium | Large | |
| all_off | 0.495 | 0.445 | 0.407 |
| pre_on | 0.696 | 0.677 | 0.768 |
| pre_post_on | 19.916 | 92.623 | 546.059 |
| all_on | 20.592 | 98.445 | 550.035 |
| Contract Type | Name of Operation/ Utility Function | Average Execution Time (ms) | ||
|---|---|---|---|---|
| Small | Medium | Large | ||
| Precondition | require or ignore | 0.178 | 0.184 | 0.247 |
| Postcondition | old | 8.589 | 13.658 | 38.703 |
| ensureAssignable | 10.814 | 82.874 | 497.745 | |
| ensure | 0.728 | 1.362 | 12.353 | |
| Class Invariant | invariant | 0.283 | 0.367 | 0.987 |
| Total Contract Execution Time | 20.592 | 98.445 | 550.035 | |
| Contract Type | Name of Operation/ Utility Function | Average Proportion of Contract CPU Time(%) | ||
|---|---|---|---|---|
| Small | Medium | Large | ||
| Precondition | require or ignore | ≈0.00 | 0.05 | 0.04 |
| Postcondition | old | 97.00 | 88.67 | 60.89 |
| ensureAssignable | 2.08 | 2.46 | 14.48 | |
| ensure | 0.92 | 7.81 | 23.39 | |
| Class Invariant | invariant | ≈0.00 | 0.82 | 1.16 |
| Total Proportion of Contract CPU Time | ≈100.00 | 99.81 | 99.95 | |
| Contract Type | Name of Operation/ Utility Function | Average Execution Time(ms) | |||||
|---|---|---|---|---|---|---|---|
| Small | Medium | Large | |||||
| (1) | (2) | (1) | (2) | (1) | (2) | ||
| Precondition | require or ignore | 0.161 | 0.298 | 0.203 | 0.330 | 0.313 | 0.451 |
| Postcondition | old | N/A | 0.014 | N/A | 0.013 | N/A | 0.011 |
| ensureAssignable | N/A | 0.027 | N/A | 0.024 | N/A | 0.025 | |
| ensure | N/A | 0.262 | N/A | 0.241 | N/A | 0.235 | |
| Class Invariant | invariant | N/A | 0.095 | N/A | 0.069 | N/A | 0.046 |
| Total Time | 0.161 | 0.696 | 0.203 | 0.677 | 0.313 | 0.768 | |
| DbC Tools (Language) | Quality Attributes | Overall Rating (12 Points) | |||
|---|---|---|---|---|---|
| Sustainability | Usability | Portablity | Developability | ||
| uContract(Java) | High | High | High | High/Medium | 12/11 |
| godbc(Go) | High | High | High | High | 12 |
| Boost.Contract(C++) | Medium | High | Low | Medium | 8 |
| contracts(Rust) | Medium | High | Low | Medium | 8 |
| icontract(Python) | High | High | Low | Medium | 9 |
| deal(Python) | High | High | Low | Medium | 9 |
| decorator-contracts (TypeScript & ECMAScript) | High | High | Low | Medium | 9 |
| Digital Mars C++ compiler(C++) | Low | Low | Medium | Low | 5 |
| JML/OpenJML(Java) | Low | Medium | Medium | Low | 6 |
| dbc4go(Go) | Low | Medium | Medium | Low | 6 |
| DbC Tools (Language) | Contract Translation Phases | ||
|---|---|---|---|
| Preprocessing | Compilation | Post-Processing | |
| uContract(Java) | N/A | host language | N/A |
| godbc(Go) | N/A | host language | N/A |
| Boost.Contract(C++) | host language | host language | N/A |
| contracts(Rust) | host language | host language | N/A |
| icontract(Python) | N/A | host language (interpretation) | N/A |
| deal(Python) | N/A | host language (interpretation) | N/A |
| decorator-contracts (TypeScript & ECMAScript) | N/A | host language | N/A |
| Digital Mars C++ compiler(C++) | N/A | custom | N/A |
| JML/OpenJML(Java) | custom | custom | N/A |
| dbc4go(Go) | custom | host language | N/A |
| DbC Tools (Language) | Attributes | |||||
|---|---|---|---|---|---|---|
| SC | NSB | LNIFD | SAS | COCAT | LDI | |
| uContract(Java) | V | V | V | V | V | |
| godbc(Go) | V | V | V | V | V | |
| Boost.Contract(C++) | V | V | V | V | V | |
| contracts(Rust) | V | V | V | V | V | |
| icontract(Python) | V | V | V | V | V | |
| deal(Python) | V | V | V | V | V | |
| decorator-contracts (TypeScript & ECMAScript) | V | V | V | V | V | |
| Digital Mars C++ compiler(C++) | V | V | ||||
| JML/OpenJML(Java) | V | V | V | |||
| dbc4go(Go) | V | V | V | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, C.-T.; Yen, Y.-C.; Hu, Y.-H.; Cheng, Y.C. Root Contracting: A Novel Method and Utility for Implementing Design by Contract in Domain-Driven Design with Event Sourcing. Electronics 2025, 14, 4205. https://doi.org/10.3390/electronics14214205
Chen C-T, Yen Y-C, Hu Y-H, Cheng YC. Root Contracting: A Novel Method and Utility for Implementing Design by Contract in Domain-Driven Design with Event Sourcing. Electronics. 2025; 14(21):4205. https://doi.org/10.3390/electronics14214205
Chicago/Turabian StyleChen, Chien-Tsun, Yi-Chun Yen, Yu-Hsiang Hu, and Yu Chin Cheng. 2025. "Root Contracting: A Novel Method and Utility for Implementing Design by Contract in Domain-Driven Design with Event Sourcing" Electronics 14, no. 21: 4205. https://doi.org/10.3390/electronics14214205
APA StyleChen, C.-T., Yen, Y.-C., Hu, Y.-H., & Cheng, Y. C. (2025). Root Contracting: A Novel Method and Utility for Implementing Design by Contract in Domain-Driven Design with Event Sourcing. Electronics, 14(21), 4205. https://doi.org/10.3390/electronics14214205









