Multi-Modal Semantic Fusion for Smart Contract Vulnerability Detection in Cloud-Based Blockchain Analytics Platforms
Abstract
1. Introduction
- Precise extraction of key code for vulnerabilities: This paper parses the source code of smart contracts into an abstract syntax tree (AST) and extracts the key fragments of vulnerabilities based on a predefined set of vulnerability features. Each segment was further analyzed through data flow and control flow dependency analysis, resulting in the generation of critical code for vulnerabilities that fully retain the functionality, control, and exception ranges.
- Multi-modal complementary feature extraction: Based on the key vulnerability code, this paper synchronizes it into two complementary modalities of text and image. This mechanism takes into account both the long-term dependencies of the contract code and the fine-grained structural information, breaking through the information bottleneck of a single modality.
- Multi-modal deep fusion strategy: This paper aligns and concatenates the text and image embedding vectors at the node level, forming a unified representation that simultaneously incorporates global semantics and local structural features. This significantly enhances the model’s ability to express complex vulnerability patterns.
2. Related Work
2.1. Smart Contract Vulnerability Detection Methods
2.2. Machine-Learning-Driven Vulnerability Detection Technologies
2.3. Exploration of Multi-Modal and Graph Representation Learning Fusion
2.4. Difference from Traditional Software Vulnerability Detection
2.5. Comparative Summary and Innovation Highlights
3. System Model
3.1. Model Definition
3.2. Comparison with Existing Multi-Modal Fusion Methods
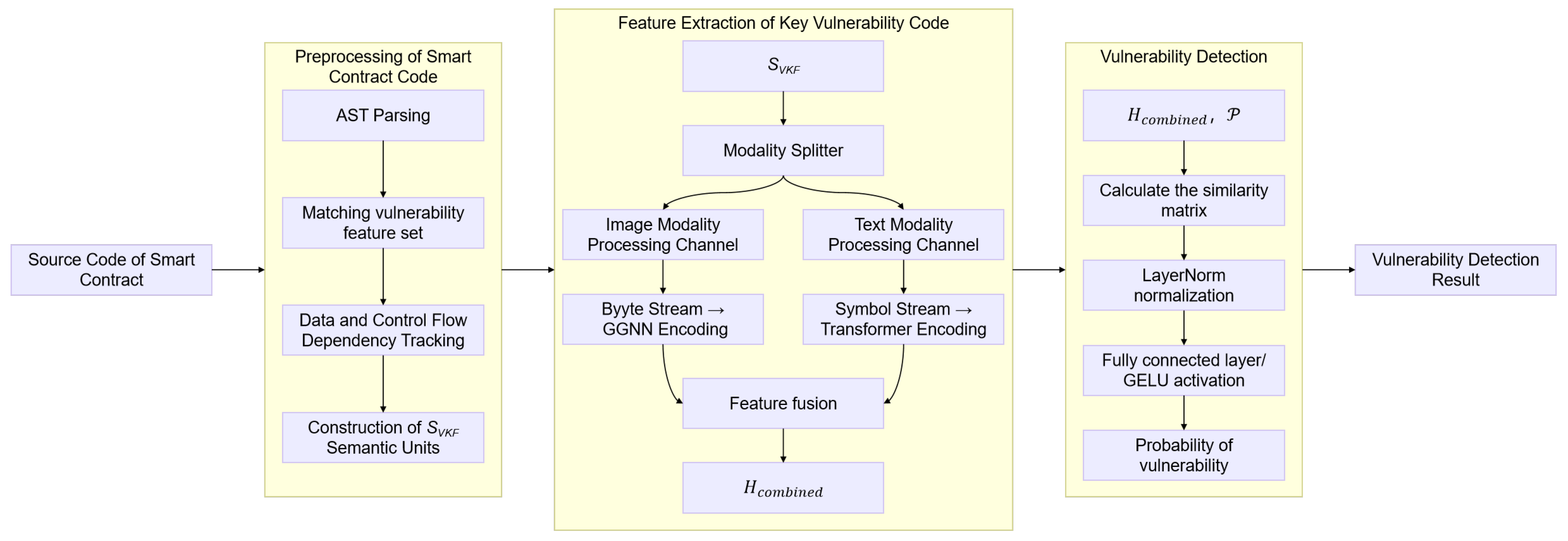
4. Smart Contract Code Vulnerability Detection Method Based on Multi-Modal Semantic Fusion
4.1. Preprocessing of Smart Contract Code
| Algorithm 1 Pseudocode of the smart contract code preprocessing algorithm |
set of vulnerability features similarity threshold
|
4.2. Feature Extraction of Key Vulnerability Code
4.2.1. Text Feature Extraction
4.2.2. Image Feature Embedding
4.2.3. Multi-Modal Fusion of Image–Text Features
4.3. Vulnerability Detection
| Algorithm 2 Multi-Modal Vulnerability Detection Process |
|
5. Framework Deployment in Cloud-Based BaaS Environment
6. Experimental
- RQ1: Can our proposed method effectively detect common vulnerabilities in smart contracts, and is its vulnerability detection better than that of existing methods?
- RQ2: Does adding multi-modal semantic fusion help improve model performance?
- RQ3: How does the proposed multi-modal fusion mechanism (Transformer–GGNN with attention alignment) improve vulnerability detection accuracy and interpretability compared to unimodal and static fusion baselines? Can it be applied on a large scale?
6.1. Experimental Setup
6.2. Resource Consumption Analysis
6.3. Computational Cost and Energy-Efficiency Analysis
6.4. Detection Performance Comparison (Addressing RQ1)
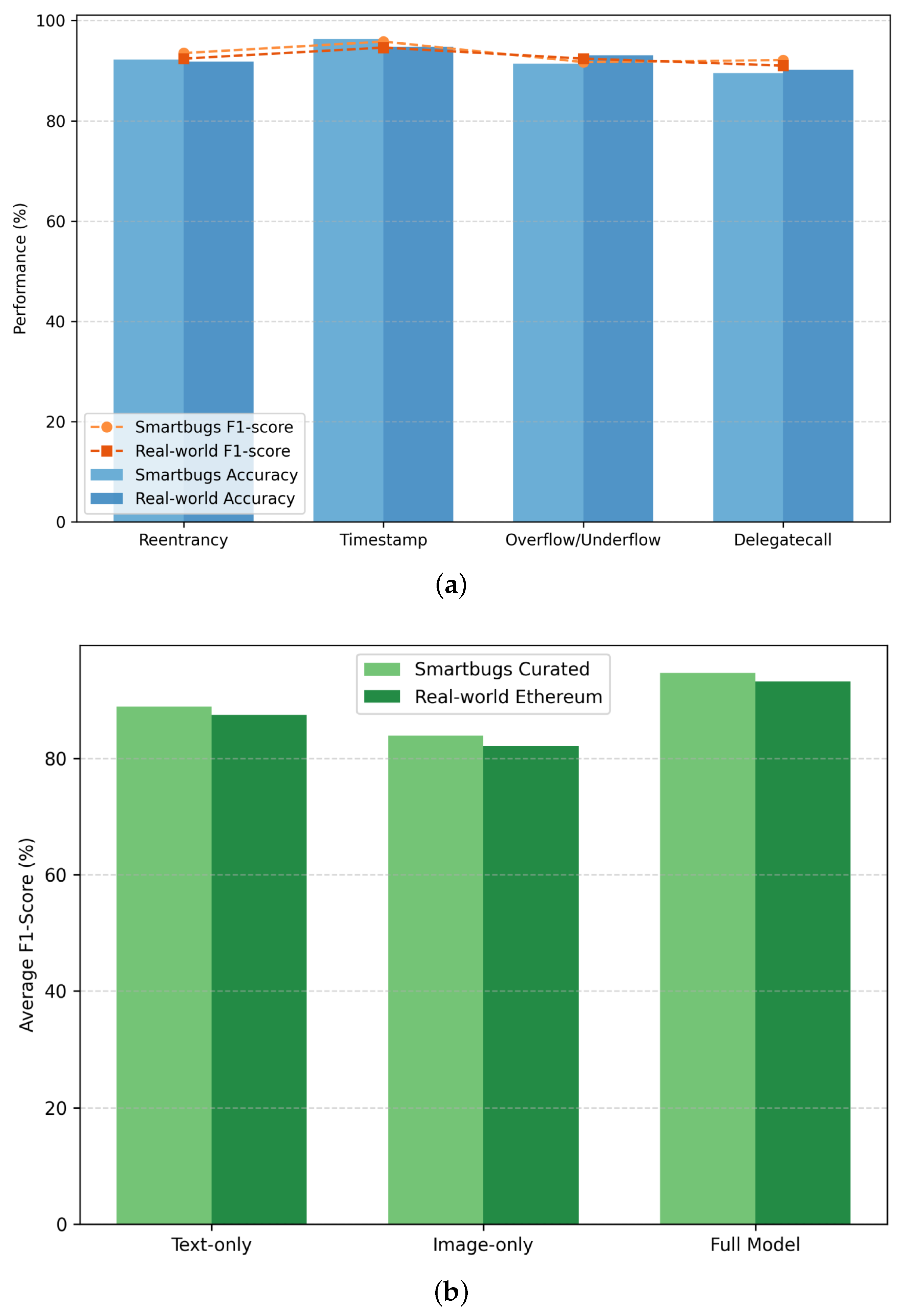
6.5. Ablation Experiments (Addressing RQ2)
6.6. Efficiency Studies (Addressing RQ3)
6.7. Dataset Diversity Discussion
6.8. Cross-Language Adaptability and Portability Analysis
6.9. Qualitative Case Analysis and Reproducibility Statement
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Glossary of Symbols and Variables
- Appendix Overview: The symbols and variables summarized in this glossary are grouped according to their functional role in the proposed multi-modal framework. Specifically, variables such as , , and correspond to semantic-level representations extracted from the Transformer encoder; symbols including , , and refer to structural-level representations learned by the GGNN; and higher-level notations such as z, , and denote system-level outputs and training objectives. Evaluation-related variables (e.g., Acc, , and ) describe performance metrics used in experimental validation. This structured organization facilitates quick reference and improves readability, ensuring consistent interpretation of all mathematical symbols throughout the manuscript.
| Symbol/Variable | Description |
|---|---|
| C | Smart contract under analysis. |
| Graph representation of a contract, where V and E denote node and edge sets, respectively. | |
| Token embedding of the i-th code token extracted by the Transformer encoder. | |
| Hidden state of the i-th node in the GGNN structural encoder. | |
| Attention weight between semantic feature and structural feature in the fusion layer. | |
| Semantic encoder based on Transformer architecture. | |
| Structural encoder based on gated graph neural network (GGNN). | |
| z | Final multi-modal fused representation combining textual and structural features. |
| y | Ground truth vulnerability label (0 = non-vulnerable, 1 = vulnerable). |
| Predicted vulnerability probability output by the model. | |
| Overall loss function used for model training (e.g., cross-entropy loss). | |
| Learning rate parameter in model optimization. | |
| d | Dimensionality of feature vectors in Transformer and GGNN encoders. |
| Activation function (e.g., ReLU or sigmoid) applied to feature transformations. | |
| ⊕ | Concatenation or fusion operator between modality features. |
| N | Number of nodes in the contract graph. |
| Edge set capturing data or control dependencies between nodes. | |
| True/false positive/negative counts used for evaluation metrics. | |
| Accuracy, precision, recall, and F1-score performance metrics. | |
| Training time and inference time per contract, respectively. |
References
- Ma, W.; Li, W. Blockchain technology and internal control effectiveness. Financ. Res. Lett. 2024, 64, 1544–6123. [Google Scholar] [CrossRef]
- Lu, Z.; Tang, Q.; Zhang, Y. BoR: Toward High-Performance Permissioned Blockchain in RDMA-Enabled Network. IEEE Trans. Serv. Comput. 2020, 13, 342–355. [Google Scholar]
- Li, Y.; Xu, J.; Liang, W. GraphMF: QoS Prediction for Large Scale Blockchain Service Selection. In Proceedings of the 2020 3rd International Conference on Smart BlockChain (SmartBlock), Zhengzhou, China, 23–25 October 2020; pp. 167–172. [Google Scholar]
- Liu, Z.; Jiang, M.; Zhang, S.; Zhang, J.; Liu, Y. A Smart Contract Vulnerability Detection Mechanism Based on Deep Learning and Expert Rules. IEEE Access 2023, 11, 77990–77999. [Google Scholar] [CrossRef]
- Yang, H.; Zhang, J.; Gu, X.; Cui, Z. Smart Contract Vulnerability Detection based on Abstract Syntax Tree. In Proceedings of the 2022 8th International Symposium on System Security, Safety, and Reliability (ISSSR), Chongqing, China, 27–28 October 2022; pp. 169–170. [Google Scholar]
- Li, X.; Liu, J.; Chen, X.; Zhang, Q. A Symbolic Execution-Based Approach for Smart Contract Vulnerability Detection. In Proceedings of the 2023 IEEE 6th International Conference on Automation, Electronics and Electrical Engineering (AUTEEE), Shenyang, China, 15–17 December 2023; pp. 468–472. [Google Scholar]
- Durieux, T.; Ferreira, J.F.; Abreu, R.; Cruz, P. Empirical Review of Automated Analysis Tools on 47,587 Ethereum Smart Contracts. In Proceedings of the IEEE/ACM 42nd International Conference on Software Engineering, Seoul, Republic of Korea, 27 June–19 July 2020; pp. 530–541. [Google Scholar]
- Xu, X.; Hu, T.; Li, B.; Liao, L. CCDetector: Detect Chaincode Vulnerabilities Based on Knowledge Graph. In Proceedings of the 2023 IEEE 47th Annual Computers, Software, and Applications Conference (COMPSAC), Torino, Italy, 26–30 June 2023; pp. 699–704. [Google Scholar]
- Qian, P.; Liu, Z.; He, Q.; Zimmermann, R.; Wang, X. Towards Automated Reentrancy Detection for Smart Contracts Based on Sequential Models. IEEE Access 2020, 8, 19685–19695. [Google Scholar] [CrossRef]
- Feist, J.; Grieco, G.; Groce, A. Slither: A Static Analysis Framework for Smart Contracts. In Proceedings of the 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Montreal, QC, Canada, 27 May 2019; pp. 8–15. [Google Scholar]
- Cai, J.; Li, B.; Zhang, J.; Sun, X.; Chen, B. Combine Sliced Joint Graph with Graph Neural Networks for Smart Contract Vulnerability Detection. In Proceedings of the 2023 IEEE International Conference on Software Analysis, Evolution and Reengineering (SANER), Macao, China, 21–24 March 2023; pp. 851–852. [Google Scholar]
- Yaseen, H.; Hassan, S.I. Comparative Analysis of Smart Contract Vulnerability Detection: Traditional RegEx vs. DL CodeBert Model. In Proceedings of the 2025 Second International Conference Cognitive Robotics and Intelligent Systems (ICC-ROBINS), Coimbatore, India, 25–26 June 2025; pp. 237–242. [Google Scholar]
- Jeon, S.; Lee, G.; Kim, H.; Woo, S.S. Design and Evaluation of Highly Accurate Smart Contract Code Vulnerability Detection Framework. Data Min. Knowl. Discov. 2024, 38, 888–912. [Google Scholar] [CrossRef]
- Tahir, U.; Siyal, F.; Ianni, M.; Guzzo, A.; Fortino, G. Exploiting Bytecode Analysis for Reentrancy Vulnerability Detection in Ethereum Smart Contracts. In Proceedings of the 2023 IEEE International Conference Dependable, Autonomic and Secure Computing (DASC/PiCom/CBDCom/CyberSciTech), Abu Dhabi, United Arab Emirates, 14–17 November 2023; pp. 779–783. [Google Scholar]
- Li, M.; Ren, X.; Fu, H.; Li, Z.; Sun, J. Enhancing Reentrancy Vulnerability Detection and Repair with a Hybrid Model Framework. In Proceedings of the 2024 31st Asia-Pacific Software Engineering Conference (APSEC), Chongqing, China, 3–6 December 2024; pp. 161–170. [Google Scholar]
- Hu, S.; Huang, T.; İlhan, F.; Tekin, S.F.; Liu, L. Large Language Model-Powered Smart Contract Vulnerability Detection: New Perspectives. In Proceedings of the 2023 5th IEEE International Conference Trust, Privacy and Security in Intelligent Systems and Applications (TPS-ISA), Atlanta, GA, USA, 1–3 November 2023; pp. 297–306. [Google Scholar]
- Cheong, Y.-Y.; Choi, L.Y.; Shin, J.; Kim, T.; Ahn, J.; Im, D.-H. GNN-based Ethereum Smart Contract Multi-Label Vulnerability Detection. In Proceedings of the 2024 International Conference on Information Networking (ICOIN), Ho Chi Minh City, Vietnam, 17–19 January 2024; pp. 57–61. [Google Scholar]
- Huang, Q.; He, Y.; Xing, Z.; Yu, M.; Xu, X.; Lu, Q. Enhancing Fine-Grained Smart Contract Vulnerability Detection Through Domain Features and Transparent Interpretation. IEEE Trans. Reliab. 2025, 74, 4207–4221. [Google Scholar] [CrossRef]
- Luu, L.; Chu, D.; Olickel, H.; Saxena, P.; Hobor, A. Making Smart Contracts Smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Mueller, B. A Framework for Bug Hunting on the Ethereum Blockchain. 2016. Available online: https://github.com/ConsenSys/mythril (accessed on 7 October 2025).
- Zhuang, Y.; Liu, Z.; Qian, P.; Liu, Q.; Wang, X.; He, Q. Smart Contract Vulnerability Detection using Graph Neural Network. In Proceedings of the 29th International Joint Conference on Artificial Intelligence, Yokohama, Japan, 11–17 July 2020; pp. 3283–3290. [Google Scholar]
- Qian, P.; Liu, Z.; Yin, Y.; He, Q. Cross-Modality Mutual Learning for Enhancing Smart Contract Vulnerability Detection on Bytecode. In Proceedings of the ACM Web Conference 2023, Austin, TX, USA, 30 April–4 May 2023. [Google Scholar]


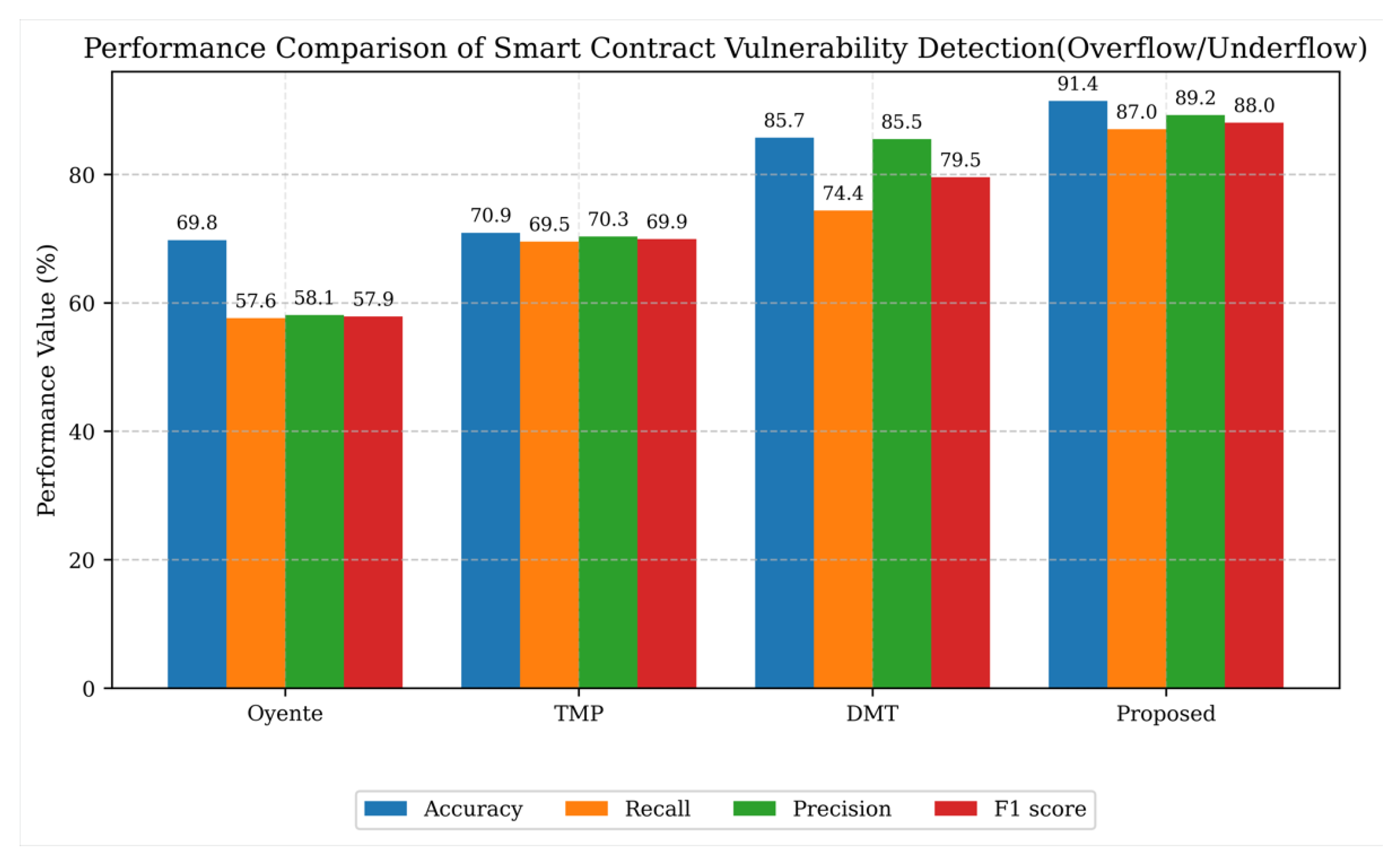
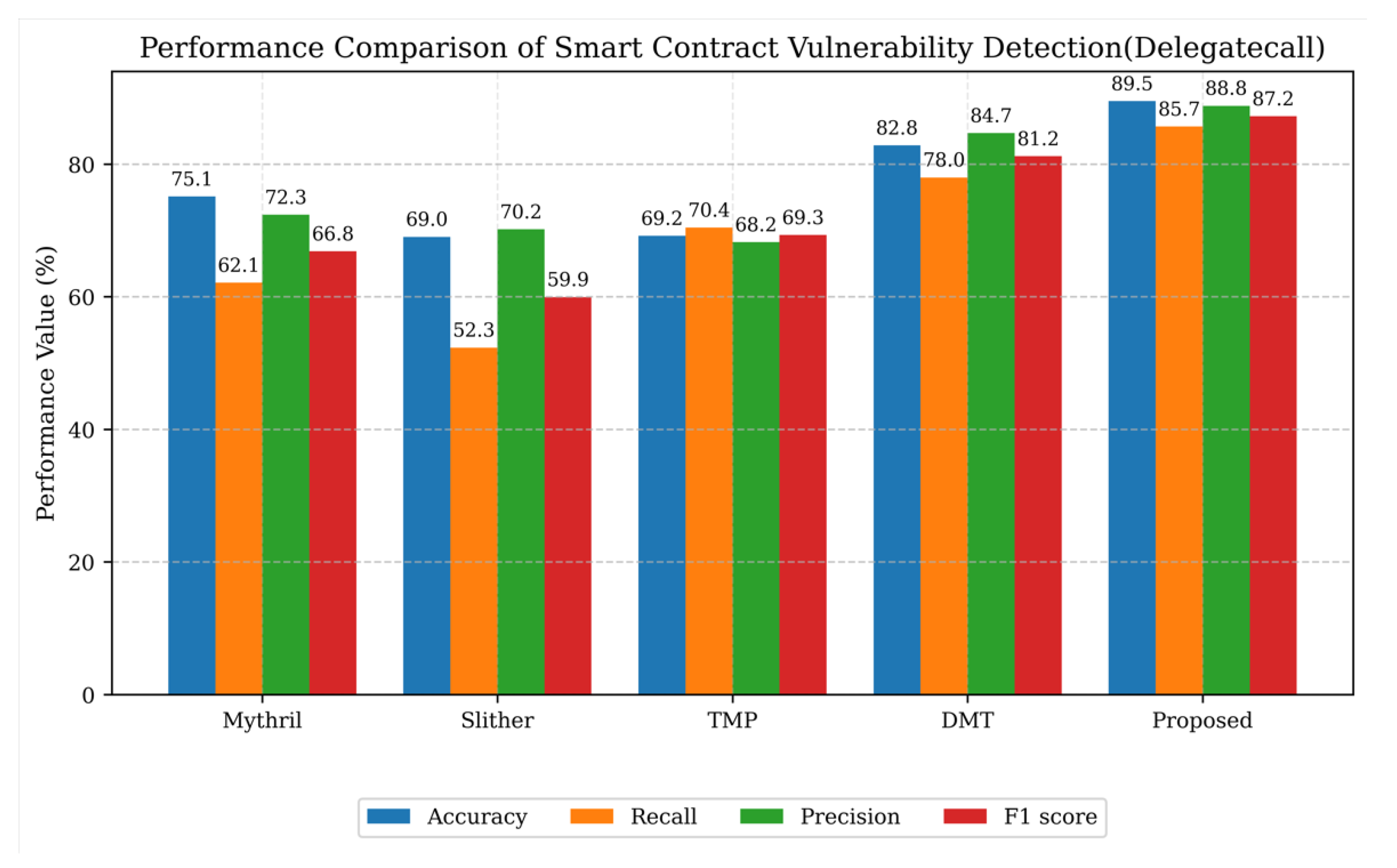
| Category | Methods | Input Features | Strengths | Limitations |
|---|---|---|---|---|
| Static Analysis | Oyente, Mythril | Symbolic traces | Interpretable | High false positives |
| Deep Learning | VulDeeSmart, TMP | Tokenized code, graphs | Automated learning | Requires large datasets |
| Graph-based | GGNN, VulHunter | AST/CFG/DFG | Captures structure | Ignores semantics |
| Multi-modal | DMT, DeepVul-Graph | Text + Graph fusion | Robust integration | Static fusion |
| Proposed (Ours) | MMVul-Detection | Transformer + GGNN + attention | Adaptive fusion | Higher training cost |
| Dataset Configuration | |
|---|---|
| Dataset | Smartbugs Curated |
| Supplementary Dataset | 1200 real-world Ethereum mainnet contracts |
| Vulnerability Type | Re-entrancy |
| Timestamp | |
| Overflow/Underflow | |
| Delegatecall | |
| Baseline Methods | |
| Symbolic Execution | Oyente [19] |
| Industrial Tool | Mythril [20] |
| Industrial Tool | Slither [10] |
| Graph-based Model | TMP [21] |
| Neural network Model | DMT [22] |
| Evaluation Metrics | |
| Performance Metrics | Accuracy, Precision, Recall, F1-score |
| Hardware/Software Environment | |
| OS | Windows 10 |
| CPU | Intel Core i5-14600 |
| RAM | 16 GB |
| GPU | NVIDIA GTX4070 |
| Deep Learning Framework | PyTorch 1.12 |
| Method | Vulnerability | Recall | Precision | Accuracy | F1-Score |
|---|---|---|---|---|---|
| w/o Text feature | Re-entrancy | 88.7 | 89.8 | 88.9 | 89.3 |
| w/o Image feature | 79.8 | 80.8 | 79.5 | 80.6 | |
| Full model | 96.2 | 97.1 | 96.5 | 95.8 | |
| w/o Text feature | Timestamp | 79.2 | 80.2 | 81.4 | 80.7 |
| w/o Image feature | 85.6 | 85.6 | 87.9 | 83.9 | |
| Full model | 92.5 | 93.1 | 92.8 | 91.2 | |
| w/o Text feature | Overflow/Underflow | 80.4 | 81.6 | 83.7 | 81.1 |
| w/o Image feature | 88.9 | 86.9 | 89.2 | 84.5 | |
| Full model | 92.8 | 93.8 | 93.1 | 91.7 | |
| w/o Text feature | Delegatecall | 81.6 | 85.6 | 83.9 | 82.9 |
| w/o Image feature | 87.5 | 84.7 | 88.8 | 84.3 | |
| Full model | 93.4 | 94.4 | 93.7 | 92.1 |
| Oyente | Mythril | Slither | Proposed | |
|---|---|---|---|---|
| Time/s | 45 | 30 | 10 | 2 |
| Contract Name | Vulnerability Type | Detection Result |
|---|---|---|
| EtherBank.sol | Re-entrancy | Detected ✓ |
| LotteryDAO.sol | Timestamp Dependency | Missed ✗ |
| SafeToken.sol | Arithmetic Overflow | Detected ✓ |
| MultiSend.sol | Delegatecall Misuse | Detected ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zeng, X.; Wen, Q.; Qin, S. Multi-Modal Semantic Fusion for Smart Contract Vulnerability Detection in Cloud-Based Blockchain Analytics Platforms. Electronics 2025, 14, 4188. https://doi.org/10.3390/electronics14214188
Zeng X, Wen Q, Qin S. Multi-Modal Semantic Fusion for Smart Contract Vulnerability Detection in Cloud-Based Blockchain Analytics Platforms. Electronics. 2025; 14(21):4188. https://doi.org/10.3390/electronics14214188
Chicago/Turabian StyleZeng, Xingyu, Qiaoyan Wen, and Sujuan Qin. 2025. "Multi-Modal Semantic Fusion for Smart Contract Vulnerability Detection in Cloud-Based Blockchain Analytics Platforms" Electronics 14, no. 21: 4188. https://doi.org/10.3390/electronics14214188
APA StyleZeng, X., Wen, Q., & Qin, S. (2025). Multi-Modal Semantic Fusion for Smart Contract Vulnerability Detection in Cloud-Based Blockchain Analytics Platforms. Electronics, 14(21), 4188. https://doi.org/10.3390/electronics14214188





