Interference- and Demand-Aware Full-Duplex MAC for Next-Generation IoT: A Dual-Phase Contention Framework with Dynamic Priority Scheduling
Abstract
1. Introduction
1.1. Motivations
- What is an effective and low-overhead method for a terminal to communicate its dynamic QoS profile to the AP? We address this by defining the QoS profile as a 2-bit configuration, embedded in control frames, that classifies nodes as either uplink-dominant (UD) or downlink-dominant (DD) based on their primary traffic needs.
- What scheduling intelligence is required at the AP to optimally balance the dual objectives of satisfying diverse QoS contracts and maintaining network-wide interference below acceptable thresholds?
1.2. Contributions
- A Novel Interference- and Demand-Aware MAC Protocol: We propose a novel Interference- and Demand-Aware Full-Duplex MAC (IDA-FDMAC) framework that, for the first time, unifies the management of inter-node interference and diverse QoS demands. To achieve this, we design a novel dual-phase contention mechanism with dynamic priority scheduling. This core mechanism resolves the inherent conflict between the two objectives: the first phase efficiently resolves contention and mitigates primary interference, while the second leverages nodes’ QoS configurations (UD/DD) to perform demand-aware resource allocation.
- A Comprehensive Analytical Framework: For a rigorous assessment of the protocol’s capabilities, we construct a detailed theoretical model. This analytical framework is designed to jointly capture the effects of interference constraints and heterogeneous QoS demands. It enables the precise calculation of the success probability for the dual-phase contention process and the subsequent derivation of the total system throughput, while explicitly accounting for the unique characteristics of FD operation and the dynamic priority system.
- Extensive Performance Validation: The practical efficacy of the IDA-FDMAC protocol and the fidelity of our mathematical analysis are substantiated through extensive simulation campaigns. When benchmarked against comparable protocols, the results confirm that our solution achieves a marked improvement in overall system throughput and successfully delivers on the differentiated QoS objectives for various types of nodes.
2. Related Works
2.1. FD MAC Protocols for Interference Mitigation
2.2. FD MAC Protocols for QoS Provisioning
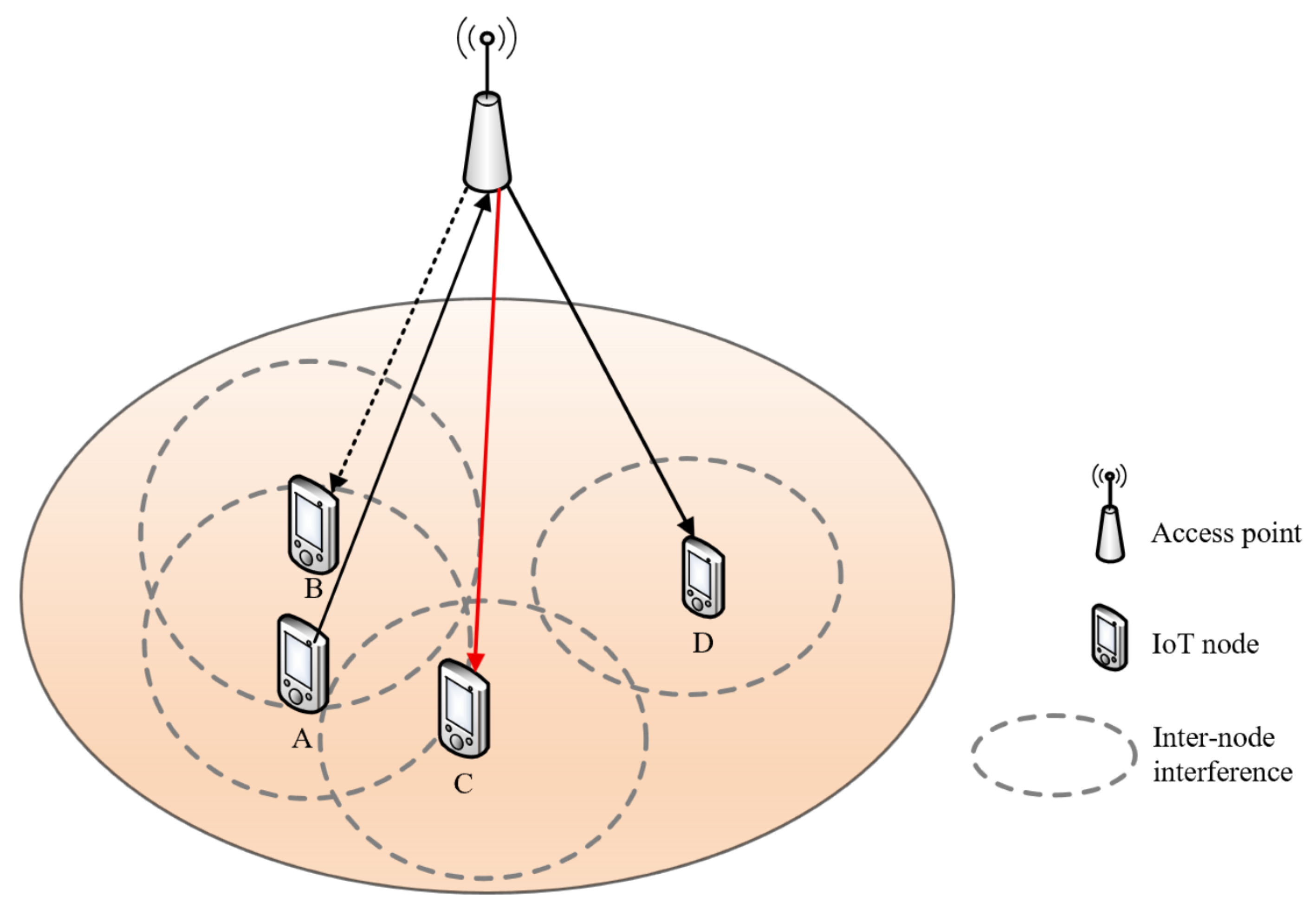
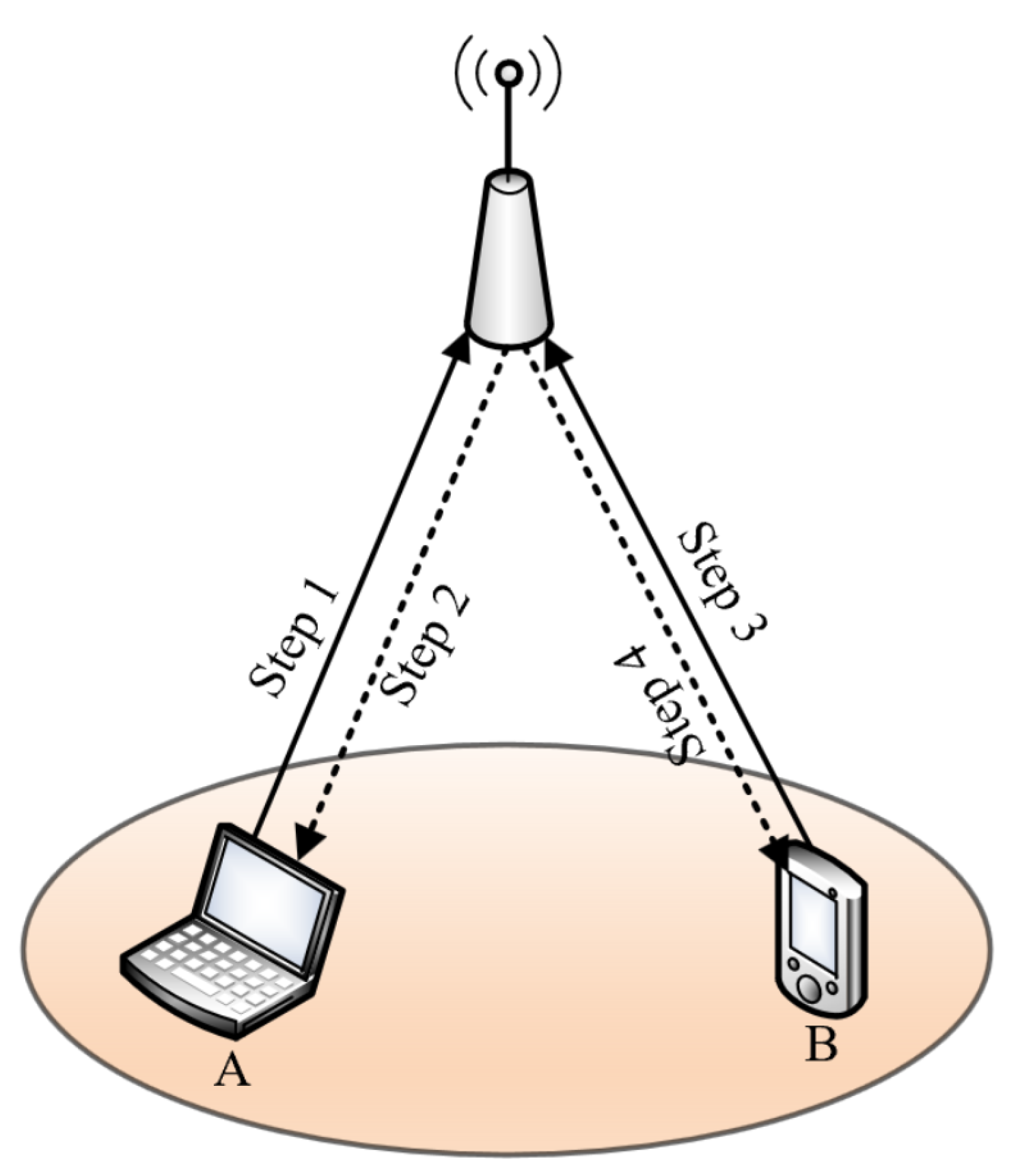
3. IDA-FDMAC Protocol
3.1. Protocol Architecture
- R1 (Priority-based Candidate Selection): Eligible nodes, as determined by the preceding TDC phase and their own interference/QoS assessments, compete using a frequency-domain method inspired by the T2F rule [30,31]. A dynamic priority system is embedded here, granting nodes different contention advantages based on their node type and the context of the current transmission.
- R2 (Signature-based Identification): All winners from R1 simultaneously transmit their unique signatures to the AP.
- R3 (Centralized Collision Resolution): The AP, which is assumed to know all node signatures, performs cross-correlation to identify the contenders. If a single signature is detected, that node is confirmed. If multiple signatures are detected (indicating a tie in R1), the AP deterministically selects one winner, thereby guaranteeing a collision-free outcome.
3.2. IDA-FDMAC Design Details
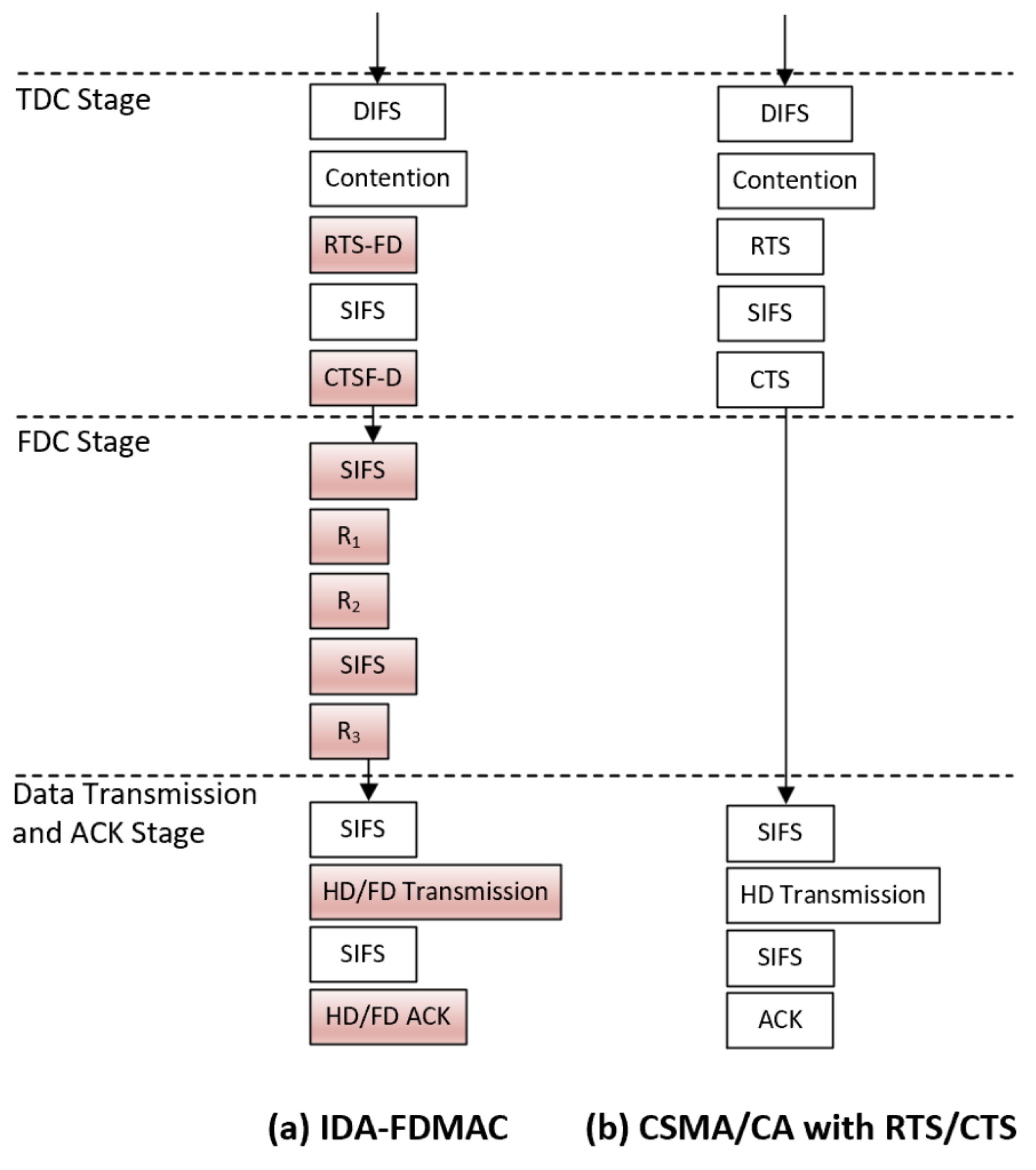
3.2.1. TDC Stage
- Case 1 (UD→AP): A UD node successfully acquires the channel, establishing itself as the uplink sender for the forthcoming FD transmission. The corresponding downlink receiver will be determined in the FDC stage.
- Case 2 (DD→AP): This outcome is similar to Case 1, but the designated uplink sender is a DD node.
- Case 3 (AP→UD): The AP wins the contention and addresses its RTS-FD to a specific UD node, which is then designated as the downlink receiver. The uplink sender remains to be selected via the FDC stage.
- Case 4 (AP→DD): This case mirrors Case 3, with the distinction that the selected downlink receiver is a DD node.
3.2.2. FDC Stage
- (Highest Priority): Subcarrier selection range is .
- (Medium Priority): Subcarrier selection range is .
- (Lowest Priority): Subcarrier selection range is .
- When a UD node wins TDC (Case 1: UD→AP): The highest priority () is given to DD nodes, as they have the most urgent need for a downlink slot. The current UD node (the TDC winner) is given medium priority () to potentially form a two-node FD link. Other UD nodes receive the lowest priority ().
- When a DD node wins TDC (Case 2: DD→AP): The current DD node receives the highest priority () to satisfy its own downlink demand. Other DD nodes have medium priority (), while all UD nodes have the lowest priority ().
- When AP targets a UD node (Case 3: AP→UD): The targeted UD node has the highest priority () to find an uplink partner. Other UD nodes have medium priority (), and DD nodes have the lowest priority ().
- When AP targets a DD node (Case 4: AP→DD): The highest priority () is assigned to UD nodes, as this creates a highly efficient FD pairing. The targeted DD node has medium priority (), while other DD nodes are given the lowest priority ().
3.2.3. Data Transmission and ACK Stage
3.2.4. Generalization of QoS Support
4. Performance Analysis
4.1. Analysis of the TDC Stage
- is the probability that the channel remains idle, with no node attempting a transmission.
- is the success probability for node i, where only node i transmits. For the AP (node 0), this is an aggregate probability, , where is the probability of the AP successfully sending an RTS-FD to node i, calculated as follows:Here, is the AP’s attempt rate towards node i, and the total attempt rate for the AP is .
- is the collision probability, occurring when two or more nodes transmit in the same slot.
4.2. Analysis of the FDC Stage
4.3. Throughput Expression
- Node i wins the TDC stage, thereby becoming the designated uplink sender.
- Another node (or the AP) wins the TDC stage, and node i subsequently wins the FDC stage to become the uplink sender.
- The AP wins the TDC stage and selects node i as the designated downlink receiver.
- Another node wins the TDC stage, and node i subsequently wins the FDC stage to become the downlink receiver.
5. Performance Evaluation
5.1. Validation of the Proposed IDA-FDMAC Protocol
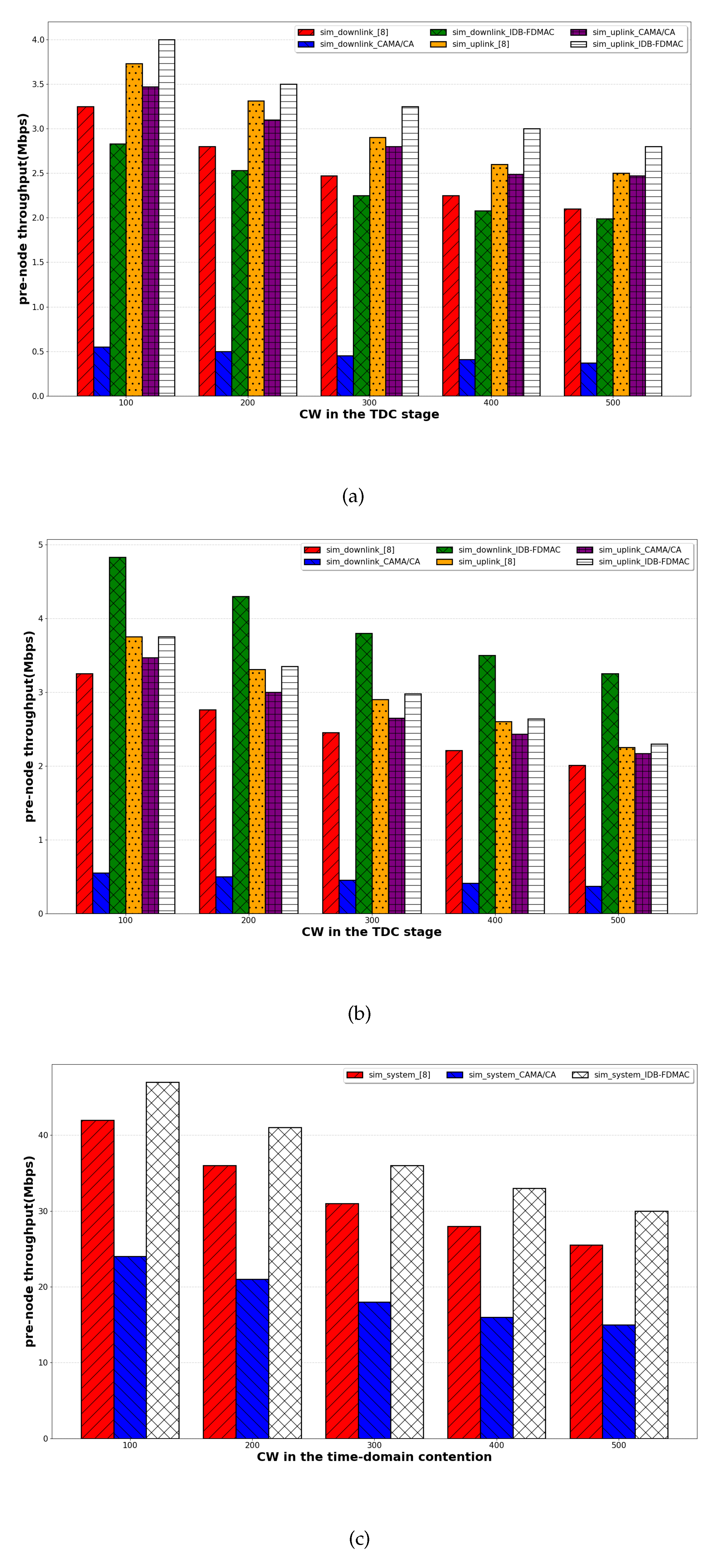
5.2. Comparison Among the Proposed IDA-FDMAC Protocol, the Full-Duplex Protocol in Ref. [9], and CSMA/CA
5.3. Performance Under Non-Saturated Conditions
5.3.1. Simulation Setup for Non-Saturated Traffic
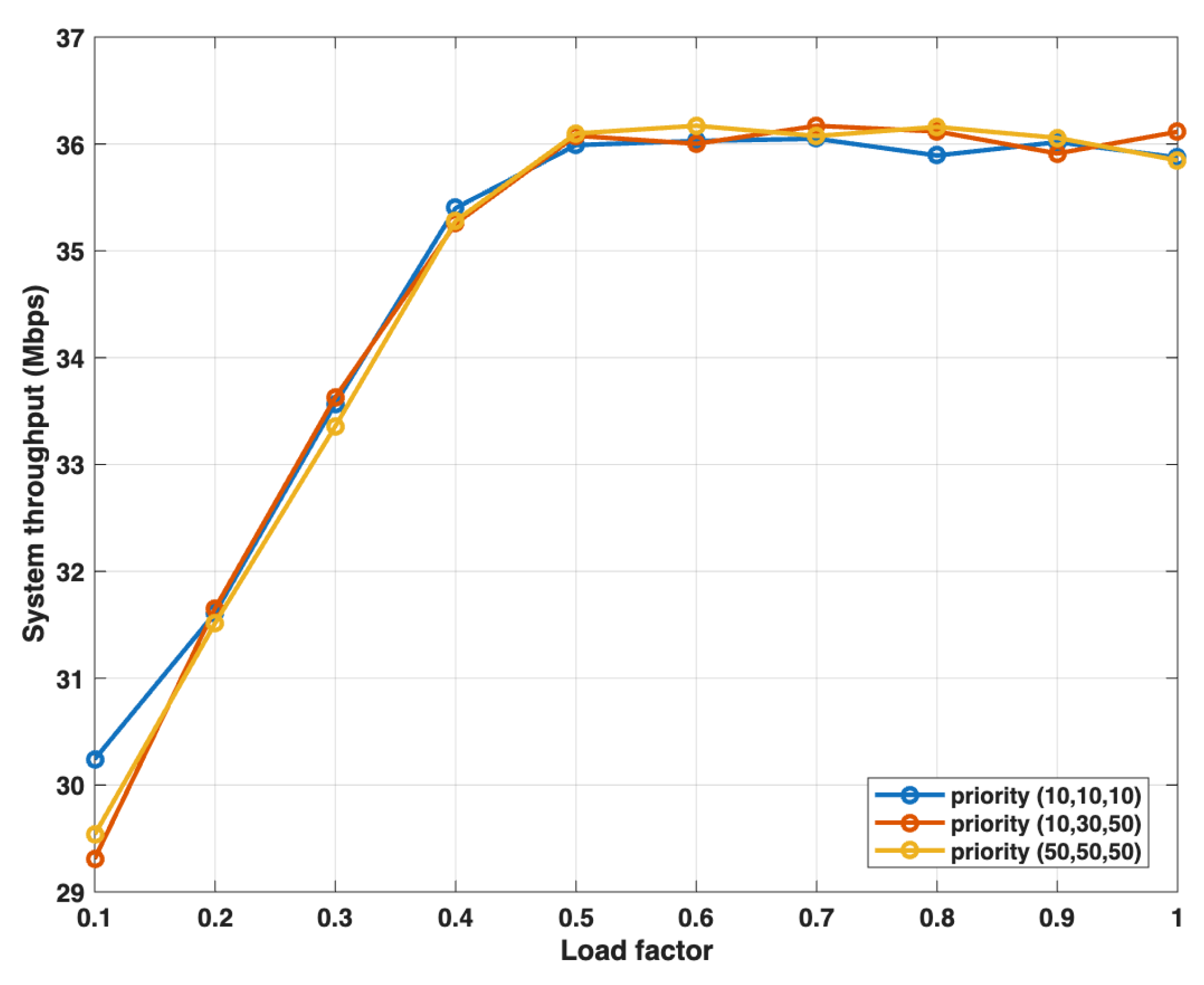
5.3.2. Analysis of System Throughput
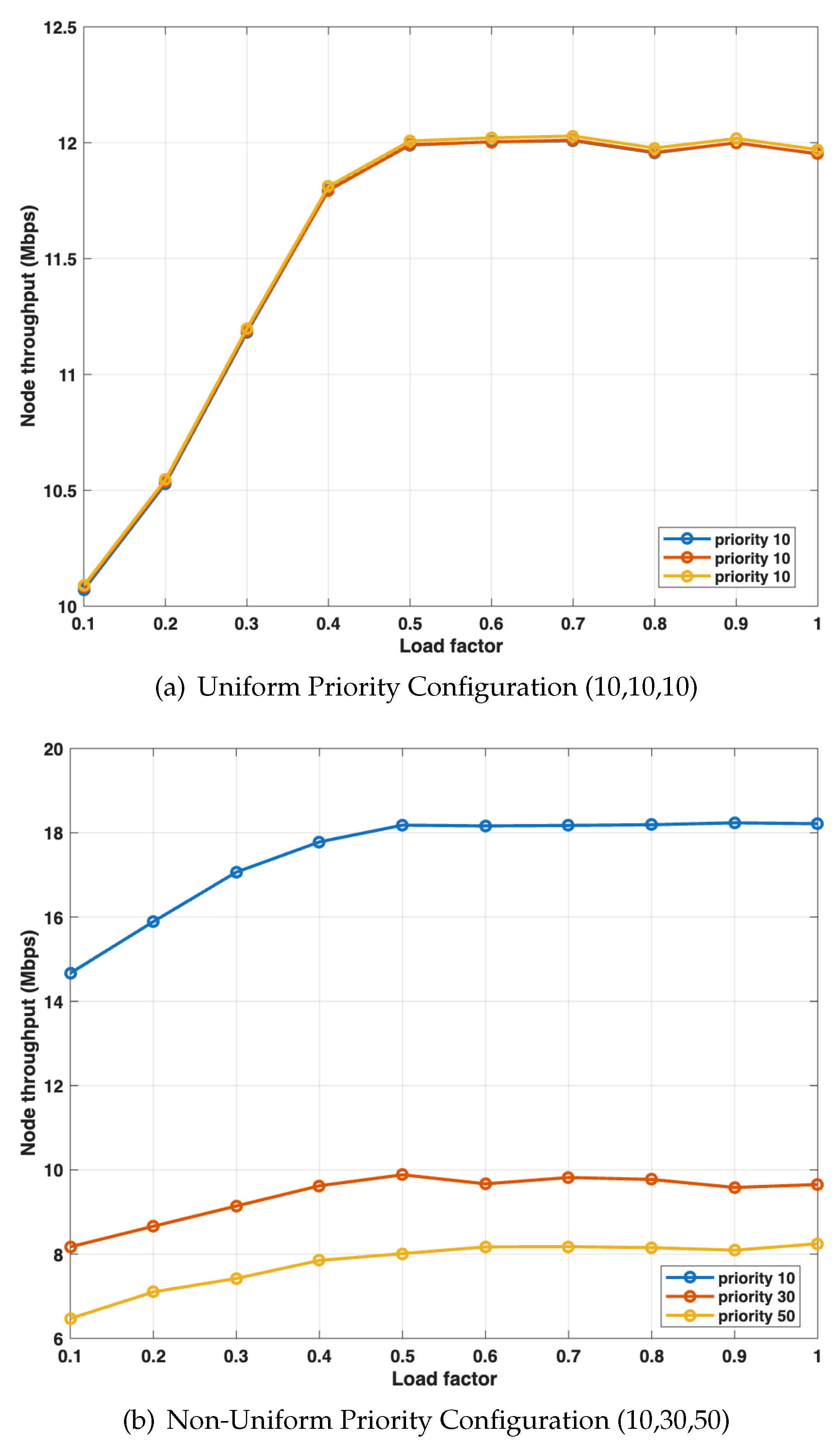
5.3.3. Analysis of QoS Differentiation
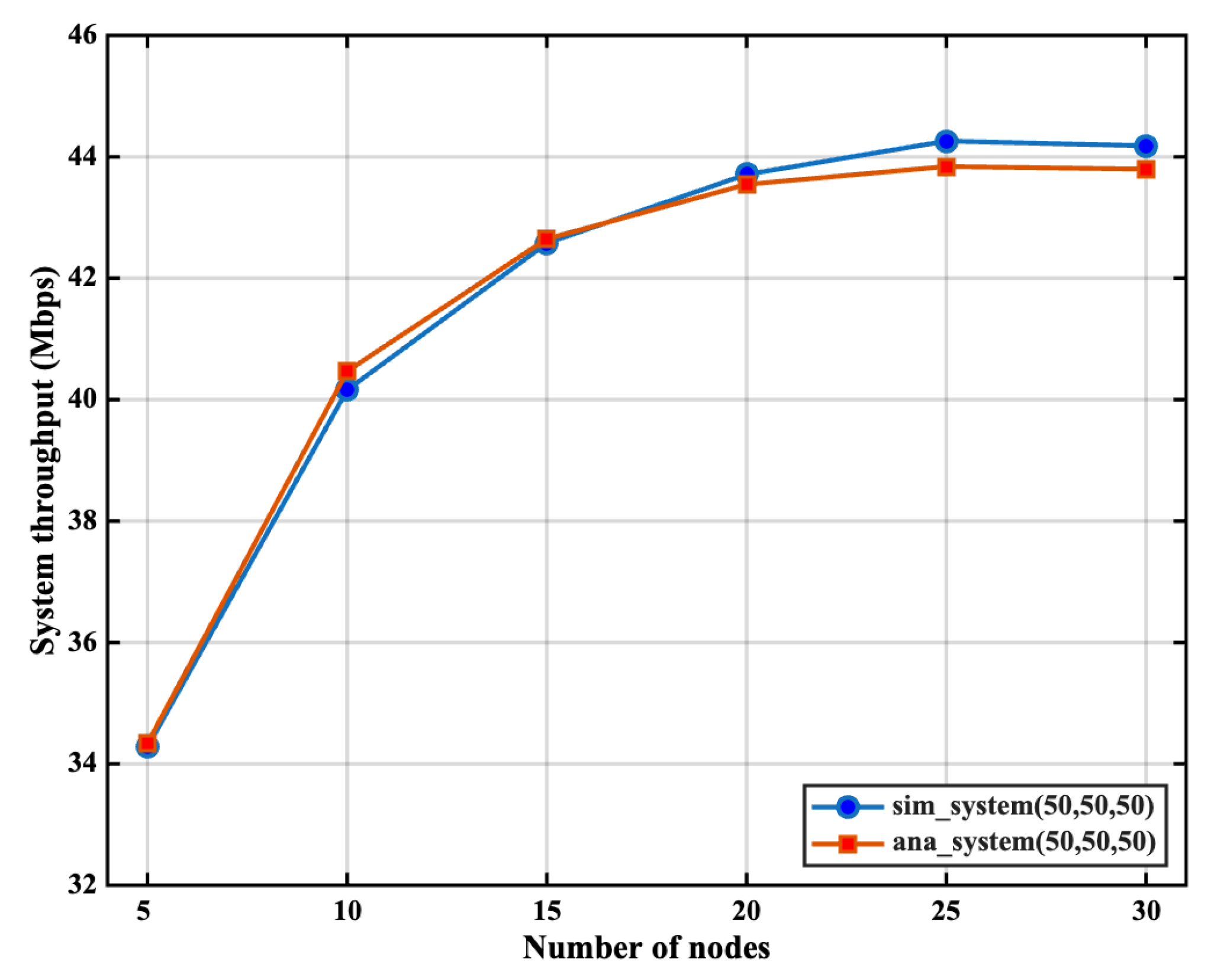
5.4. Scalability Analysis with Increasing Network Size
- Excellent Model–Simulation Agreement: There is a very close match between the analytical curve and the simulation data points across the entire range of network sizes. For instance, at 15 nodes, the analytical model predicts a throughput of 42.65 Mbps, while the simulation yields a result of 42.58 Mbps, demonstrating a negligible deviation. This consistency validates the accuracy of our theoretical model in predicting the protocol’s performance, even in larger-scale scenarios.
- Graceful Throughput Scaling: The system throughput initially increases as more nodes are added to the network. For example, as the number of nodes increases from 5 to 15, the total system throughput rises significantly from approximately 32.3 Mbps to 42.5 Mbps. This is because a higher number of active nodes increases the probability of successful channel access and the formation of efficient full-duplex pairs, leading to better overall channel utilization.
- Contention Impact in Dense Networks: As the number of nodes continues to increase beyond an optimal point (around 44 Mbps with 25 nodes in this configuration), the system throughput begins to saturate. This behavior is expected and is attributable to the rising probability of collisions in the time-domain contention (TDC) stage. Increased contention leads to longer backoff periods and more time spent on collision resolution, which slightly diminishes the gains from having more transmission opportunities.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
References
- Giordani, M.; Polese, M.; Mezzavilla, M.; Rangan, S.; Zorzi, M. Toward 6G networks: Use cases and technologies. IEEE Commun. Mag. 2020, 58, 55–61. [Google Scholar] [CrossRef]
- Bellalta, B. IEEE 802.11 ax: High-efficiency WLANs. IEEE Wirel. Commun. 2016, 23, 38–46. [Google Scholar] [CrossRef]
- Sabharwal, A.; Schniter, P.; Guo, D.; Bliss, D.W.; Rangarajan, S.; Wichman, R. In-band full-duplex wireless: Challenges and opportunities. IEEE J. Sel. Areas Commun. 2014, 32, 1637–1652. [Google Scholar] [CrossRef]
- Choi, J.I.; Jain, M.; Srinivasan, K.; Levis, P.; Katti, S. Achieving single channel, full duplex wireless communication. In Proceedings of the Sixteenth Annual International Conference on Mobile Computing and Networking, Chicago, IL, USA, 20–24 September 2010; pp. 1–12. [Google Scholar]
- Bharadia, D.; McMilin, E.; Katti, S. Full duplex radios. In Proceedings of the ACM SIGCOMM 2013 Conference on SIGCOMM, Hong Kong, China, 12–16 August 2013; pp. 375–386. [Google Scholar]
- Jain, M.; Choi, J.I.; Kim, T.; Bharadia, D.; Seth, S.; Srinivasan, K.; Levis, P.; Katti, S.; Sinha, P. Practical, real-time, full duplex wireless. In Proceedings of the 17th Annual International Conference on Mobile Computing and Networking, Las Vegas, NV, USA, 19–23 September 2011; pp. 301–312. [Google Scholar]
- Kim, S.; Stark, W.E. On the performance of full duplex wireless networks. In Proceedings of the 2013 47th Annual Conference on Information Sciences and Systems (CISS), Baltimore, MD, USA, 20–22 March 2013; pp. 1–6. [Google Scholar]
- Duarte, M.; Sabharwal, A.; Aggarwal, V.; Jana, R.; Ramakrishnan, K.K.; Rice, C.W.; Shankaranarayanan, N. Design and characterization of a full-duplex multiantenna system for WiFi networks. IEEE Trans. Veh. Technol. 2013, 63, 1160–1177. [Google Scholar] [CrossRef]
- Choi, W.; Lim, H.; Sabharwal, A. Power-controlled medium access control protocol for full-duplex WiFi networks. IEEE Trans. Wirel. Commun. 2015, 14, 3601–3613. [Google Scholar] [CrossRef]
- Qu, Q.; Li, B.; Yang, M.; Yan, Z.; Zuo, X.; Guan, Q. FuPlex: A full duplex MAC for the next generation WLAN. In Proceedings of the 2015 11th International Conference on Heterogeneous Networking for Quality, Reliability, Security and Robustness (QSHINE), Taipei, Taiwan, 19–20 August 2015; pp. 239–245. [Google Scholar]
- Goyal, S.; Liu, P.; Gurbuz, O.; Erkip, E.; Panwar, S. A distributed MAC protocol for full duplex radio. In Proceedings of the 2013 Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 3–6 November 2013; pp. 788–792. [Google Scholar]
- Kim, J.K.; Kim, W.K.; Kim, J.H. A new full duplex MAC protocol to solve the asymmetric transmission time. In Proceedings of the 2015 IEEE Globecom Workshops (GC Wkshps), San Diego, CA, USA, 6–10 December 2015; pp. 1–5. [Google Scholar]
- Kim, C.; Kim, C. A full duplex MAC protocol for efficient asymmetric transmission in WLAN. In Proceedings of the 2016 International Conference on Computing, Networking and Communications (ICNC), Kauai, HI, USA, 15–18 February 2016; pp. 1–5. [Google Scholar]
- Huang, X.; Yang, K.; Wu, F.; Leng, S. Power control for full-duplex relay-enhanced cellular networks with QoS guarantees. IEEE Access 2017, 5, 4859–4869. [Google Scholar] [CrossRef]
- Wen, D.; Yu, G. Time-division cellular networks with full-duplex base stations. IEEE Commun. Lett. 2015, 20, 392–395. [Google Scholar] [CrossRef]
- Cheng, W.; Zhang, X.; Zhang, H. Heterogeneous statistical QoS provisioning over 5G wireless full-duplex networks. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26–30 April 2015; pp. 55–63. [Google Scholar]
- Cheng, W.; Zhang, X.; Zhang, H. Heterogeneous statistical QoS provisioning for full-duplex D2D communications over 5G wireless networks. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–7. [Google Scholar]
- Baskar, N.; Selvaprabhu, P. Performance analysis of successive di-state full-duplex cooperative wireless cellular networks. Alex. Eng. J. 2024, 91, 139–151. [Google Scholar] [CrossRef]
- Yumen, Y.; Sakakura, S.; Sanada, K.; Hatano, H.; Mori, K. Throughput Analysis for Wireless Full-Duplex Multi-Hop Networks with RTS/CTS-Based MAC. Electronics 2022, 11, 892. [Google Scholar] [CrossRef]
- Ahmed, E.; Eltawil, A.M. On phase noise suppression in full-duplex systems. IEEE Trans. Wirel. Commun. 2014, 14, 1237–1251. [Google Scholar] [CrossRef]
- Shudrenko, Y.; Plöger, D.; Kuladinithi, K.; Timm-Giel, A. A novel approach to enhance the end-to-end quality of service for avionic wireless sensor networks. ACM Trans. Internet Technol. 2022, 22, 1–29. [Google Scholar] [CrossRef]
- Wang, J.; Chen, J.; Xiong, N.; Alfarraj, O.; Tolba, A.; Ren, Y. S-BDS: An effective blockchain-based data storage scheme in zero-trust IoT. ACM Trans. Internet Technol. 2023, 23, 1–23. [Google Scholar] [CrossRef]
- Teng, H.; Dong, M.; Liu, Y.; Tian, W.; Liu, X. A low-cost physical location discovery scheme for large-scale Internet of Things in smart city through joint use of vehicles and UAVs. Future Gener. Comput. Syst. 2021, 118, 310–326. [Google Scholar] [CrossRef]
- Bekele, B.E.; Tokarz, K.; Gebeyehu, N.Y.; Pochopień, B.; Mrozek, D. Performance Evaluation of UDP-Based Data Transmission with Acknowledgment for Various Network Topologies in IoT Environments. Electronics 2024, 13, 3697. [Google Scholar] [CrossRef]
- Vijarania, M.; Gupta, S.; Agrawal, A.; Adigun, M.O.; Ajagbe, S.A.; Awotunde, J.B. Energy Efficient Load-Balancing Mechanism in Integrated IoT–Fog–Cloud Environment. Electronics 2023, 12, 2543. [Google Scholar] [CrossRef]
- Hussain, M.Z.; Hanapi, Z.M. Efficient Secure Routing Mechanisms for the Low-Powered IoT Network: A Literature Review. Electronics 2023, 12, 482. [Google Scholar] [CrossRef]
- He, Y.; Huang, F.; Wang, D.; Chen, B.; Li, T.; Zhang, R. Performance Analysis and Optimization Design of AAV-Assisted Vehicle Platooning in NOMA-Enhanced Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2025, 26, 8810–8819. [Google Scholar] [CrossRef]
- Mead, J.A.; Singh, K.; Allu, R.; Katwe, M.; Ku, M.L.; Biswas, S. Secure RIS-Aided FD NOMA Communications for Hardware Impaired IoT Networks. IEEE Internet Things J. 2025, 12, 28332–28347. [Google Scholar] [CrossRef]
- Ma, Z.; Zhao, Q.; Zeng, Y.; Zhang, H.; Dai, H.N. AT-MAC: A novel full duplex MAC design for achieving asymmetric transmission. In Proceedings of the Mobile and Wireless Technologies 2016, Colmar, France, 11–13 July 2016; pp. 41–49. [Google Scholar]
- Sen, S.; Choudhury, R.R.; Nelakuditi, S. Listen (on the frequency domain) before you talk. In Proceedings of the 9th ACM SIGCOMM Workshop on Hot Topics in Networks, Monterey, CA, USA, 20–21 October 2010; pp. 1–6. [Google Scholar]
- Sen, S.; Roy Choudhury, R.; Nelakuditi, S. No time to countdown: Migrating backoff to the frequency domain. In Proceedings of the 17th Annual International Conference on Mobile Computing and Networking, Las Vegas, NV, USA, 19–23 September 2011; pp. 241–252. [Google Scholar]
- 802.11-2007; IoT Medium Access Control (MAC) and Physical Layer (PHY) Specifications. IEEE: Piscataway, NJ, USA, 2007.
- Misra, S.; Khatua, M. Semi-distributed backoff: Collision-aware migration from random to deterministic backoff. IEEE Trans. Mob. Comput. 2014, 14, 1071–1084. [Google Scholar] [CrossRef]
- Sen, S.; Roy Choudhury, R.; Nelakuditi, S. CSMA/CN: Carrier sense multiple access with collision notification. In Proceedings of the Sixteenth Annual International Conference on Mobile Computing and Networking, Chicago, IL, USA, 20–24 September 2010; pp. 25–36. [Google Scholar]
- Jardosh, A.P.; Ramachandran, K.N.; Almeroth, K.C.; Belding-Royer, E.M. Understanding congestion in IEEE 802.11 b wireless networks. In Proceedings of the 5th ACM SIGCOMM Conference on Internet Measurement, New Orleans, LA, USA, 19–21 October 2005; p. 25. [Google Scholar]
- 802.11e-2005; Part 11: IoT Medium Access Control (MAC) and Physical Layer (PHY) Specifications: Amendment 8: Medium Access Control (MAC) Quality of Service Enhancements. IEEE: Piscataway, NJ, USA, 2005.
- Zhang, H.; Zhao, Q.; Ma, Z.; Xu, F. Design and analysis of weighted frequency-domain contention in wireless LANs. IEEE Access 2017, 5, 1639–1648. [Google Scholar] [CrossRef]
- Bianchi, G. Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar] [CrossRef]
- Zhao, Q.; Tsang, D.H.; Sakurai, T. Modeling nonsaturated IEEE 802.11 DCF networks utilizing an arbitrary buffer size. IEEE Trans. Mob. Comput. 2010, 10, 1248–1263. [Google Scholar] [CrossRef]
- Zhao, Q.; Tsang, D.H.; Sakurai, T. A simple and approximate model for nonsaturated IEEE 802.11 DCF. IEEE Trans. Mob. Comput. 2009, 8, 1539–1553. [Google Scholar] [CrossRef]
- Ma, Z.; Zhao, Q.; Luan, T.H. Providing utility-optimal throughput guarantees in wireless LANs. IEEE Trans. Veh. Technol. 2015, 65, 7559–7567. [Google Scholar] [CrossRef]
- Xu, F.; Zhao, Q.; Zeng, Y. How well does CSMA/CN work in WLANs? IEEE Trans. Veh. Technol. 2015, 65, 7662–7669. [Google Scholar] [CrossRef]
- Nassiri, M.; Heusse, M.; Duda, A. A novel access method for supporting absolute and proportional priorities in 802.11 WLANs. In Proceedings of the IEEE INFOCOM 2008-The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 709–717. [Google Scholar]

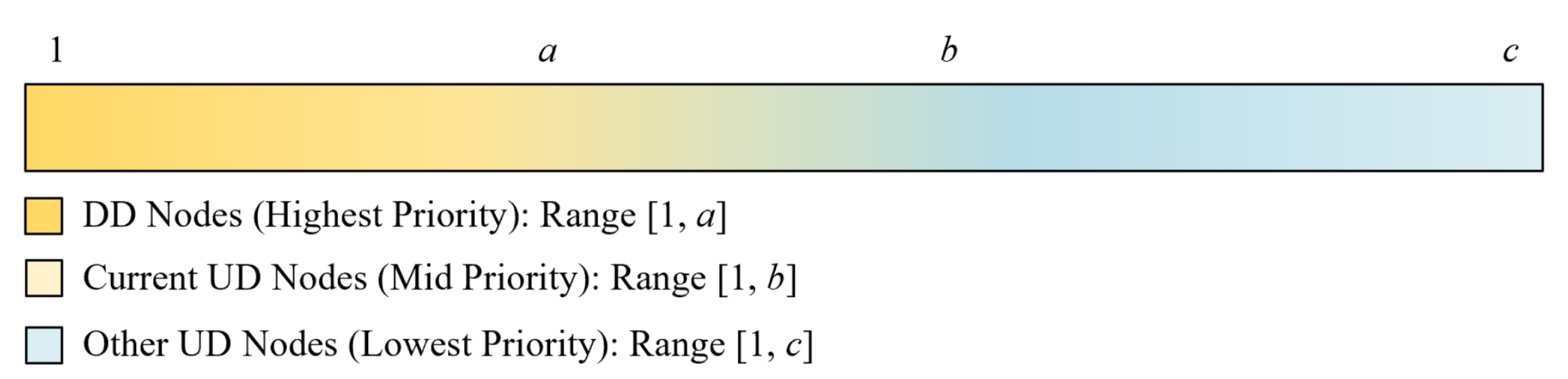


| Cases | TX Type |
|---|---|
| Case 1 (UD→AP) | 00 |
| Case 2 (DD→AP) | 01 |
| Case 3 (AP→UD) | 10 |
| Case 4 (AP→DD) | 11 |
| Parameter | Value |
|---|---|
| DIFS | 28 |
| SIFS | 10 |
| Slot time | 9 |
| RTS/RTS-FD | 38/38 bytes |
| CTS/CTS-FD | 44/52 bytes |
| ACK | 38 bytes |
| 8 | |
| 2 | |
| Payload | 1500 bytes |
| 6 Mbps | |
| 54 Mbps | |
| 222 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tian, L.; Liu, Z.; Qi, S.; Zhao, Q. Interference- and Demand-Aware Full-Duplex MAC for Next-Generation IoT: A Dual-Phase Contention Framework with Dynamic Priority Scheduling. Electronics 2025, 14, 3901. https://doi.org/10.3390/electronics14193901
Tian L, Liu Z, Qi S, Zhao Q. Interference- and Demand-Aware Full-Duplex MAC for Next-Generation IoT: A Dual-Phase Contention Framework with Dynamic Priority Scheduling. Electronics. 2025; 14(19):3901. https://doi.org/10.3390/electronics14193901
Chicago/Turabian StyleTian, Liwei, Zijie Liu, Shuhan Qi, and Qinglin Zhao. 2025. "Interference- and Demand-Aware Full-Duplex MAC for Next-Generation IoT: A Dual-Phase Contention Framework with Dynamic Priority Scheduling" Electronics 14, no. 19: 3901. https://doi.org/10.3390/electronics14193901
APA StyleTian, L., Liu, Z., Qi, S., & Zhao, Q. (2025). Interference- and Demand-Aware Full-Duplex MAC for Next-Generation IoT: A Dual-Phase Contention Framework with Dynamic Priority Scheduling. Electronics, 14(19), 3901. https://doi.org/10.3390/electronics14193901






