Abstract
In trans-border data (data transferred or accessed across national jurisdictions) exchange scenarios, identity authentication mechanisms serve as critical components for ensuring data security and privacy protection, with their effectiveness directly impacting the compliance and reliability of transnational operations. However, existing identity authentication systems face multiple challenges in trans-border contexts. Firstly, the transnational transfer of identity data struggles to meet the varying data-compliance requirements across different jurisdictions. Secondly, centralized authentication architectures exhibit vulnerabilities in trust chains, where single points of failure may lead to systemic risks. Thirdly, the inefficiency of certificate verification in traditional Public Key Infrastructure (PKI) systems fails to meet the real-time response demands of globalized business operations. These limitations severely constrain real-time identity verification in international business scenarios. To address these issues, this study proposes a trans-border distributed certificate-free identity authentication framework (STALE). The methodology adopts three key innovations. Firstly, it utilizes email addresses as unique user identifiers combined with a Certificateless Public Key Cryptography (CL-PKC) system for key distribution, eliminating both single-point dependency on traditional Certificate Authorities (CAs) and the key escrow issues inherent in Identity-Based Cryptography (IBC). Secondly, an enhanced Elliptic Curve Diffie–Hellman (ECDH) key-exchange protocol is introduced, employing forward-secure session key negotiation to significantly improve communication security in trans-border network environments. Finally, a distributed identity ledger is implemented, using the FISCO BCOS blockchain, enabling decentralized storage and verification of identity information while ensuring data immutability, full traceability, and General Data Protection Regulation (GDPR) compliance. Our experimental results demonstrate that the proposed method exhibits significant advantages in authentication efficiency, communication overhead, and computational cost compared to existing solutions.
1. Introduction
With the accelerated development of globalization and the digital economy, trans-border data transfer has become an important part of business and organizational operations. Authentication technology is the foundation for securing trans-border access control. Accurately identifying users can prevent unauthorized access, thereby reducing data leakage and security risks. In trans-border transactions and data transfers, participants belong to different countries and jurisdictions, which involves complex legal, interoperability, and security requirements. At the same time, trans-border operations often have high time-sensitive requirements, and the challenge of ensuring that business operations are carried out swiftly and securely in different regions, thereby safeguarding business continuity and compliance, is becoming increasingly prominent.
Currently, different countries and organizations have adopted various authentication standards and protocols, such as OAuth 2.0, SAML, and OpenID Connect. However, compatibility and interoperability among these standards remain limited, complicating efforts to establish a unified authentication framework for trans-border data access. Furthermore, due to regulatory and technical discrepancies across countries, identity authentication between trans-border entities is often protracted, posing challenges to meeting real-time requirements.
Among existing trans-border authentication systems, Public Key Infrastructure (PKI) is the most widely used. However, PKI relies on a centralized Certificate Authority (CA) to bind users’ identities to their public keys, leading to several critical issues in trans-border data scenarios. Firstly, a single point of failure exists: if a CA is compromised or fails then the security and availability of the entire system may be severely impacted [1]. Secondly, the chain of trust among CAs varies across jurisdictions, making trans-border trust chains susceptible to security threats [2]. Additionally, the complexity of certificate management poses a significant challenge, especially when key management spans multiple jurisdictions. In such cases, the processes of certificate issuance, revocation, and renewal become exceedingly intricate, increasing both the burden and cost of system administration.
The Identity-Based Encryption (IBE) system addresses some of PKI’s key-management issues. It allows users to use their identities as public keys, thereby eliminating reliance on traditional certificate management [3]. However, IBE introduces the risk of key escrow. In an IBE system, private keys are generated and managed by a Key-Generation Center (KGC), giving the KGC potential access to decrypt all user communications, which poses serious security risks. If the KGC is compromised or if internal personnel act maliciously, the privacy and security of the entire system are jeopardized. Additionally, the IBE system faces challenges with key revocation and updating. If a user’s private key is leaked or their identity information changes, effectively revoking the old key and updating it to a new key becomes a complex operational task [4]. Therefore, although IBE has certain advantages in simplifying key management, its inherent security risks and operational complexities still limit its broad application in trans-border scenarios.
At the same time, the certificate-based PKI encounters complex challenges, due to its reliance on extensive certificate management, while IBE introduces key escrow risks, as users’ private keys are controlled by a centralized trusted authority. In response to these limitations, Al-Riyami proposed Certificateless Public Key Cryptography (CL-PKC) in 2003 [5]. This innovative approach, which requires no certificates, addresses the complexities of certificate management in traditional PKI and removes the key escrow issue present in identity-based systems. CL-PKC enables users to generate complete private keys by combining the secret value with a partial private key provided by a KGC. This hybrid approach not only simplifies the authentication process but also enhances the security of key management.
Blockchain-based Distributed Ledger Technology offers a decentralized, secure, and efficient authentication method, addressing many limitations of traditional systems by eliminating the need for a central authority, reducing single points of failure, and enhancing security [6]. Blockchain’s immutable ledger ensures transparency and tamper-proof identity transactions. Cryptographic algorithms, such as Rivest–Shamir–Adleman (RSA) and asymmetric encryption, protect identity data during transmission and storage [7]. Smart contracts and optimized consensus mechanisms further improve efficiency and scalability by automating the identity verification process [8]. Recently, Decentralized Identity (DID) systems have also emerged, transferring identity control from institutions to individuals and enhancing privacy and autonomy [9]. Enabled by blockchain, DID offers decentralized trust management; however, it faces challenges in scalability and cross-jurisdictional privacy protection. DID’s reliance on issuers raises trust issues, as the degree of trust varies across regions. Thus, while DID systems offer privacy advantages, they still face performance and privacy hurdles in trans-border applications.
In addressing trans-jurisdictional identity authentication and authorization challenges, several fundamental requirements emerge as critical. Primarily, a decentralized architecture must ensure parity among all transnational participating entities, necessitating the elimination of centralized control points to prevent unilateral manipulation. Secondly, the identity management framework must simultaneously satisfy privacy regulation compliance while ensuring data authenticity and reliability, thereby reconciling contemporary demands for both regulatory adherence and trustworthiness. These requirements highlight three persistent challenges in current trans-border authentication systems: (1) the jurisdictional disparities in identity data transfer compliance, (2) the systemic vulnerabilities inherent in centralized authentication architectures’ trust chains, and (3) the operational inefficiencies in traditional PKI certificate verification processes that impede real-time responsiveness in global business contexts. Our research specifically targeted these limitations to advance secure and efficient identity verification in interconnected digital ecosystems.
To overcome these challenges, we present a trans-border distributed certificates authentication framework (STALE) that utilizes email addresses as decentralized identifiers. The proposed system applies CL-PKC to simplify key distribution and management, thereby avoiding the certificate management overhead and security risks characteristic of conventional PKI infrastructures. Our approach specifically addresses the trust dependency problems found in both traditional CA-based identity systems and DID solutions, which arise from divergent trust assumptions regarding credential issuers in cross-jurisdictional contexts. The framework incorporates the Elliptic Curve Diffie–Hellman (ECDH) protocol—a cryptographic method that allows secure key establishment over public channels through elliptic curve arithmetic—to substantially improve both the security properties and scalability of the authentication mechanism. This cryptographic primitive proves particularly effective in trans-border networking environments. Additionally, we employ blockchain technology to create a distributed identity information storage and verification system, removing centralized failure points while enhancing the reliability and verifiability of identity management in international contexts. The key innovations of this research include the following:
- To overcome the limitations of trust mechanisms in trans-border authentication, this paper proposes a trans-border distributed authentication method (STALE) based on a Certificateless Public Key Cryptosystem. The framework utilizes email addresses as unique user identifiers and CL-PKC-based key distribution, thus eliminating the single point of failure in traditional PKI architectures and the key escrow vulnerabilities in identity-based cryptosystems. Formal security analysis confirms that the scheme enables real-time dynamic authentication for cross-border digital identity verification.
- In the design of authentication protocols, this study presents key enhancements to the conventional ECDH key-exchange protocol. The improved scheme integrates forward secrecy and mutual authentication, significantly strengthening communication security in trans-border network environments while simultaneously improving authentication efficiency.
- To manage identity information securely, this work implements a distributed identity ledger architecture utilizing the FISCO BCOS consortium blockchain. The system employs rigorously designed smart contracts and an optimized consensus protocol to facilitate Decentralized Identity storage and verification. This approach guarantees tamper-proof data integrity, full auditability, and adherence to General Data Protection Regulation (GDPR) compliance standards.
The remainder of this paper is organized as follows. Section 2 presents an overview of existing authentication technologies and blockchain applications in identity management, analyzing their strengths and limitations. Section 3 introduces the core technologies utilized in this study, including CL-PKC, blockchain, and the AHAC framework. Section 4 provides a detailed explanation of the architecture and algorithms underlying the trans-border distributed certificateless identity authentication scheme. Section 5 outlines the experimental process and presents result analyses, validating the scheme’s performance in trans-border scenarios. Finally, Section 6 summarizes the research findings and discusses potential future research directions.
2. Related Works
The evolution of identity authentication technology has progressed from PKI to IBE then to CL-PKC and, more recently, to DID based on blockchain technology. This reflects a gradual shift in identity management towards decentralization, autonomy, and high security. Trans-border identity authentication technology has emerged as an important research area within the field of information technology. Particularly in the context of globalization, with the increasing frequency of trans-border transactions, communications, and data exchanges, higher standards are being set for identity authentication technologies. Accordingly, we summarize the current stages of development in identity authentication technologies and the state of research in trans-border scenarios as follows.
2.1. Public Key Infrastructure
PKI, as a common deployment in cyberspace, determines the uniqueness, authenticity, and legitimacy of an entity’s identity by maintaining digital certificates [10]. However, traditional PKI systems have several limitations in trans-border scenarios, such as closed security domains, complex trust models, excessive CA rights, susceptibility to single points of failure, and cross-domain authentication inefficiencies. To address these problems, researchers have proposed various improvement schemes, such as the cross-domain authentication scheme based on proxy re-signature technology [11]. This scheme uses proxy re-signature technology to achieve two-way authentication between users and cloud service providers, and it establishes inter-domain trust relationships directly through semi-trusted proxies, avoiding the complex process of certificate path construction and validation and reducing the trust path length. This approach simplifies the interactive authentication process and improves the efficiency of cross-domain authentication while retaining the advantages of PKI technology. Another option is to use blockchain technology to enhance traditional PKI [12]. Blockchain technology has the advantages of being open and transparent, immutable, decentralized, etc., which can well make up for the shortcomings of PKI in cross-domain authentication. For example, by constructing a cross-domain trust model based on the federation chain, setting each entity domain CA as a node of the blockchain, and establishing trust through the P2P network, consensus mechanism, and tamper-proof federation chain ledger, the complexity of cross-domain identity authentication is reduced. In addition, blockchain-based schemes have proposed efficient cross-domain data management schemes and cross-domain anonymous authentication schemes to improve response speed and protect user privacy [13]. Some studies propose cross-domain authentication schemes based on PKI and Certificateless Cryptosystems (CLCs), which introduce PKI-based multicenter authentication management mechanisms to control and track users’ anonymous identities in the security domains of different cryptosystems [14]. This scheme can resist replay attacks, substitution attacks, and man-in-the-middle attacks while achieving cross-domain authentication between different cryptosystems with high security and computational efficiency.
PKI technology research in trans-border scenarios mainly focuses on how to address the limitations of traditional PKI systems and improve the security, efficiency, and privacy protection of cross-domain authentication. However, centralized identity management in PKI, as well as the various improvement techniques based on it, still cannot overcome the challenges of trans-border and real-time identity authentication required for compliance in trans-border scenarios.
2.2. Identity-Based Encryption
IBE technology provides a new solution to the shortcomings of PKI-centralized identity management [15]. The core advantage of IBE technology is that the acquisition of public keys is no longer dependent on the PKI, but can be obtained directly from the trusted third-party Key-Generation Center, a PKG. This greatly simplifies the complexity of key management.
In trans-border scenarios, IBE technology can be further extended to cross-domain authentication [16]. For example, a blockchain-based IBE cross-domain authentication scheme can leverage the distributed ledger feature of blockchain to achieve trusted authentication and management of cross-domain identities, and the effectiveness of the mechanism has been demonstrated through experiments in IoT environments [17]. This scheme not only improves the security of authentication but also reduces reliance on a single trusted third party through decentralization and enhances the system’s resistance to attacks. Shao et al. [17] addressed the cross-chain communication problem through the IBE-BCIOT mechanism. They facilitated secure communication between different blockchain platforms by using IBE, which is crucial for trans-border IoT applications. Chen et al. [18] proposed the CT-MA-ABE mechanism to address the need to balance authority and privacy in trans-border authentication. The system uses a decentralized approach of blockchain certification authorities to ensure trustworthiness and privacy. It introduces the Universal Certificate Authority Pool (UCAP) to enhance privacy protection and speed up the authorization process. Its successful deployment between Zhuhai and Macau demonstrates its practical effectiveness in managing trans-border data interactions. Adams [19] discusses a privacy-preserving IBE architecture that reduces the trust required for PKG by using digital credentials and bilinear maps. This architecture aims to prevent collusion and enhance user privacy, making it more suitable for globalized applications. Scholars have also proposed a revocable stored identity-based encryption system for cloud-based data sharing. The system provides forward and backward security by allowing user revocation and ciphertext updates. These features are essential to maintain control over data in trans-border cloud environments [20].
Currently, many new approaches have been proposed for cross-domain authentication based on IBE technology, but IBE suffers from the obvious problem of key escrow, in which the PKG may decrypt all messages. To address this, Afroaz et al. [21] proposed an anonymous IBE scheme using ring signatures to mitigate this problem, ensuring that the key generator cannot determine which user received a particular key, thus enhancing the privacy and security of trans-border communication. Despite the significant advantages of IBE in trans-border scenarios, challenges such as key escrow issues and the need for trust in PKGs remain unresolved.
2.3. Certificateless Public Key Cryptography
CL-PKC was proposed to address the limitations of traditional PKI and identity-based cryptography (IBC) [22]. This approach eliminates the need for certificates and resolves the key escrow problem inherent in IBC, making it particularly suitable for environments that require secure and efficient cross-domain authentication.
CL-PKC has demonstrated its versatility and efficiency by being used in a variety of applications, including intelligent transport systems, Device-to-Device (D2D) communications, spatial information networks, and cryptographic schemes. CL-PKC has been adapted for secure D2D communications, which are a key component of modern communication networks. By employing multiple KGCs, CL-PKC can address conflicting security requirements such as privacy, anonymity, and traceability [23]. In spatial information networks, CL-PKC is used to develop an anonymous distributed key-management system. The system utilizes distributed key generation and temporary identification to protect privacy and ensure secure communication in dynamic and unstable network environments [24]. In dynamic WSNs, CL-PKC is used to efficiently manage keys, support node mobility, and ensure forward and backward key confidentiality. CL-PKC addresses security issues in D2D communications by using multiple KGCs to balance privacy, anonymity, and traceability. This approach enhances security in both in-coverage and out-of-coverage scenarios [25]. CL-PKC provides a lightweight cryptographic solution that can be effectively combined with blockchain to protect IoT networks. The decentralized nature of blockchain can help manage large numbers of IoT devices, ensuring secure communication and data integrity without the overhead of traditional PKI systems [26]. In the Industrial Internet of Things (IIoT), the problem of key escrow is solved and the security of cross-domain authentication and key agreement is enhanced by combining a certificateless public key signing scheme with an ad hoc Elliptic Curve Diffie–Hellman Ephemeral (ECDHE) key-exchange mechanism [27]. Additionally, cross-domain authentication is based on blockchain and certificateless signatures, using smart contracts to complete trusted authentication and fast identification of malicious devices through trust-value-based access control methods [28]. Cao et al. [29] introduced a certificateless cross-domain group authentication key-agreement scheme based on Elliptic Curve Cryptography (ECC), which is both scalable and efficient to satisfy the multiple participants for cross-domain key negotiation among multiple participants.
Certificateless encryption has significant advantages in trans-border authentication, and it can effectively solve the interoperability and key-management problems of cross-domain authentication. However, for real-time identity authentication in trans-border scenarios, although certificateless encryption helps to improve interoperability and simplify key management, there is still a lack of a complete solution for trusted identity systems that simultaneously solves the problems of identity information storage, real-time performance, and system compatibility.
2.4. Blockchain-Based Identity Authentication Technology
DID is a transformative technology in the field of identity management based on blockchain technology, which provides a self-sovereign approach that removes the dependency on a centralized authority and allows users to have full control over their identity information without having to rely on a centralized identity provider or certificate authority [30].
Currently, there are cross-domain identity management systems based on DID that enable cross-domain authentication and management of identities through smart contracts and blockchain technologies [31,32]. Oblivira [33] addresses privacy concerns during DID resolution by enabling oblivious resolution of DID requests. It ensures secure and private identity management by minimizing the risk of privacy leakage through side channels in the caching scheme. DID-based cross-domain authentication schemes offer significant advantages, in terms of privacy protection and security. However, these schemes also face some challenges, such as vulnerability to witch attacks, excessive storage overhead on the blockchain, and issues such as cross-domain identity trustworthiness that require further technological innovation and optimization. To this end, some researchers have also leveraged blockchain technology to support the DID model by providing a decentralized root of trust for entity identification and access control. This allows entities to generate and register their identifiers and credentials on the blockchain, thus facilitating secure key rotation and mitigating identity theft attacks through innovative cryptographic primitives such as infinite one-way hash chains [34]. DID supports privacy-preserving techniques such as zero-knowledge proofs, which allow for the authentication of identities without revealing sensitive information about users [35]. ICN-based DIDs and verifiable credential registries leverage the decentralized nature of ICNs to maintain the synchronization of data replicas across multiple locations. This approach reduces network overhead and query time and improves the efficiency of DID systems in trans-border scenarios [36].
Blockchain can augment CL-PKC-based distributed key-management schemes to provide a secure and efficient key-distribution mechanism. This approach leverages multiple trusted centers and interactive key-agreement protocols, which can be further protected by the blockchain’s consensus mechanism to prevent unauthorized key substitution [37]. The CL-PKC model combines CL-PKC with the blockchain to address data integrity issues in social networks. By combining the data integrity protection of blockchain with the efficient key management of CL-PKC, the model ensures secure data storage and access control. This combination mitigates the risks of data tampering and unauthorized data access that are prevalent in social networking environments [38].
In summary, these studies on identity management have made significant progress in addressing single points of failure, identity trustworthiness, and security, especially by introducing technologies such as decentralized trust management, blockchain, and CL-PKC regimes to enhance the efficiency of authentication and privacy protection. However, although these studies have effectively solved some key issues in centralized identity authentication—for example, the lack of systematic research on legal compliance—identity trustworthiness and real-time and technical scalability issues in the challenges faced by trans-border applications have led to the difficulties encountered by these theoretical solutions when they are put into practice. Therefore, how to combine these advanced authentication technologies with practical business scenarios, international regulations, and border data flow in combination with the real need to explore compliant, real-time, practical, and scalable trans-border identity systems is still an urgent problem to be solved.
3. Preliminaries
3.1. CL-PKC Formulation
Al-Riyami and Paterson proposed CL-PKC in 2003. Building on this research, Cheng, Zhaohui et al. [39] introduced a CL-PKC scheme based on the SM2 algorithm, which also supports implicit CL-PKC. In this scheme, users collaborate with a KGC to generate their key pairs. The user first generates a secret value, using the function KGC-RandomNumber(). This secret value serves as the user’s partial private key, and the function User-PartialKey() is then used to derive the user’s public value. The user submits this public value along with their email address to the KGC. Upon receiving the user’s email and public value, the KGC uses the function MasterKeyPair() to generate its master public/private key pair. It then employs the results from (), (), and KGC-RandomNumber() to calculate the user’s declared public key. Using these results along with the user’s public key as inputs to the function User-UserPartialKey(), the KGC returns the user’s declared public key and a partial private key to the user. The user then combines this partial private key with their own secret value to generate their complete private key using the function User-PrivateKey(). The user obtains their actual public key through User-RealPublicKey() and verifies the pairing of their public and private keys using the function User-PublicKey(). A detailed description of these functions is provided in Table 1:

Table 1.
Function descriptions.
3.2. AHAC Framework
The Advanced Hidden Access Control (AHAC) framework [40] represents an innovative cybersecurity solution. It introduces an independent control plane functioning as an access proxy service, effectively decoupling the port-knocking module from the access control module. By employing noise protocols, the framework achieves mutual authentication, enabling resource access without prior knowledge of IP addresses while intercepting unauthorized attempts and mitigating DDoS attacks. Notably, it utilizes ECC and ECDH algorithms to replace RSA-2048, enhancing security while reducing computational overhead and improving verification efficiency. The AHAC framework adopts a distributed and scalable architecture capable of supporting diverse network environments and application scenarios, ensuring both flexibility and operational efficiency. Its design allows seamless integration with existing zero-trust frameworks, making it suitable for network deployments of varying scales while delivering high availability and rapid response capabilities. The framework comprises five core components: the AHAC Agent, AHAC Server, Authorized Service Provider (ASP), AHAC Access Controller (AHAC-AC), and protected resources, as illustrated in Figure 1.
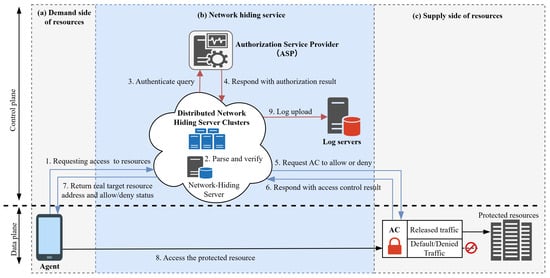
Figure 1.
AHAC architecture diagram.
The AHAC Agent operates as the primary module responsible for initiating knock requests on behalf of resource access entities. It supports diverse deployment modes, such as SDKs, standalone processes, client applications, mobile applications, web browsers, and server-side services. In trans-border data scenarios, the AHAC Agent assumes the role of the data requester. The AHAC Server, typically deployed as a server-side application, handles knock request validation and processing. Its key responsibilities include request authentication, interfacing with external authorization providers for identity verification, and enforcing access control through AHAC gatekeepers. In trans-border data exchanges, the AHAC Server serves as the data provider. This study’s experiments were performed within the AHAC framework, where mutual authentication is achieved through a combination of CL-PKC-based key distribution and ECDH key exchange, ensuring secure access communication. The ASP component provides extensible interfaces for identity, device, and policy verification, while also managing access endpoints for protected resources. Common ASP services include identity authentication, device attestation, and policy-based permission checks. To maintain synchronization during verification, HTTPS APIs or custom TCP-based protocols may be utilized. The AHAC-AC module enforces security policies, typically running as a server-side process. It adheres to a default-deny principle, ensuring the network-level invisibility of protected resources, often co-located with secured assets. Its functions include assigning access permissions (e.g., IP/port whitelisting) to authenticated agents and revoking access for unauthorized entities based on AHAC Server directives. Protected resources encompass critical assets managed by resource providers, which may include data APIs, application servers, network gateways, routers, and load balancers in distributed service architectures.
3.3. Blockchian
Blockchain technology has gained widespread attention for its features of decentralization, traceability, and immutability. With a federated chain managed by multiple institutions, the technology enhances transaction speed while preserving a certain degree of decentralization, among other advantages. In this scheme, authentication information is recorded on the federated chain (e.g., FISCO BCOS), and identity verification is executed through a smart contract. This approach enables decentralized digital identity verification on the blockchain, thereby enhancing the system’s flexibility and security.
The distributed ledger of FISCO BCOS, a core component of the authentication architecture, is fundamentally designed to provide an immutable and auditable registry for identity management and secure data exchange. The Distributed Ledger Technology (DLT) component is further optimized to serve as a secure repository for identity-related data (e.g., public values, partial public keys), enabling nodes to demonstrate ownership and control of their identities. Additionally, FISCO BCOS functions as a comprehensive registry for shared resource traceability, recording both successful and unsuccessful resource exchange transactions. This provides complete insight into the dynamics of collaboration between nodes in a distributed environment.
4. Methodology
4.1. System Architecture
In this scheme, email addresses are used as user identities (IDs), supporting real-time verification. In trans-border scenarios, email addresses serve as a reliable way to streamline identity verification, due to their global accessibility, uniqueness, and convenient real-time verification capabilities. The widespread adoption of email and its minimal privacy compliance challenges help ensure smooth and secure trans-border communication. Moreover, emails enable real-time communication for dynamic verification.
CL-PKC is utilized to encrypt email identities, providing a trusted identity identifier. In CL-PKC, user keys consist of two parts: one generated by the KGC and the other by the user. Specifically, the KGC assigns a partial private key to the user, who then combines it with their secret value to calculate a complete private key. This design addresses the reliance on a centralized CA in traditional PKI systems, as users no longer need to depend on a central authority for full key management, thereby resolving trans-border data transmission compliance issues. Even if the KGC is compromised, attackers cannot obtain the complete private key, protecting the security of identity data storage.
Blockchain’s Distributed Ledger Technology is used to store key information. By encrypting and storing user identity information on the blockchain, the system ensures data immutability. This combination significantly enhances transparency, security, and trust in trans-border identity authentication.
The scheme integrates the ECDHE key-exchange mechanism to markedly improve the efficiency and security of trans-border identity verification. Compared to traditional algorithms such as RSA, ECC provides the same level of security with shorter key lengths, reducing computational overhead and making it ideal for complex trans-border network environments. During authentication, ECDHE allows secure session key negotiation using temporary keys generated by both parties and their public keys, ensuring that even if communications are intercepted, attackers cannot retrieve the session key, thus providing forward secrecy to protect past communications. Furthermore, ECDHE’s dynamic key negotiation and low latency enhance real-time authentication and scalability, ensuring that authentication processes remain efficient and secure in trans-border contexts.
The system architecture is illustrated in Figure 2, comprising four components: User (Data Requester), Provider (Data Provider), Distributed KGC, and Consortium Blockchain. In the key generation system, the KGC serves as the Key-Generation Center and collaborates with regular users to generate user key pairs. Users and Providers, as regular users, generate public and secret values within the User key system, executing encryption and decryption functions. The functions of each component are as follows:
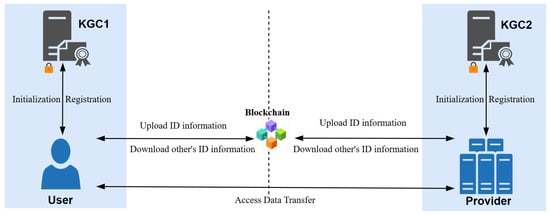
Figure 2.
The architecture of the STALE system.
- KGC: The KGC is responsible for generating the system’s master public key and master private key for the relevant participants and completing user identity registration. The KGC can be deployed in a distributed manner, with one KGC able to register identities for multiple entities.
- User: In trans-border data scenarios, the User acts as the data access requester. The User downloads the Provider’s identity information from the blockchain and calculates its public key. Using the ECC algorithm, the User encrypts the session data packet and sends it to the Provider, requesting access to resources.
- Provider: The Provider functions as the data provider in trans-border scenarios, responsible for decrypting data packets and completing identity verification. The Provider downloads the User’s identity information from the blockchain, calculates its public key, decrypts the encrypted data packet, and performs the authentication process to ensure the security and legitimacy of the request.
- Blockchain: The blockchain records each user’s identity information (email and public key) on-chain, supporting tamper-resistant identity information, which helps maintain the reliability of identity management. Even in scenarios that span multiple jurisdictions, the blockchain ensures the integrity and consistency of the data.
4.2. Workflow
4.2.1. System Initialization
The STALE scheme consists of two stages: identity registration and trans-border authentication. Before device registration begins, the system generates a series of public parameters, which are then distributed to each entity. The KGC serves as the key generation authority, responsible for generating the system’s master public key and master private key . The User generates their own secret and public values and sends their email and public value to the KGC. Upon receiving these, the KGC calculates the User’s declared public key and partial private key and then returns them to the User. The User then computes their private key and actual public key, using the received data and parameters. The notations used in this scheme and their meanings are shown in Table 2.

Table 2.
Notation Description.
4.2.2. Identity Registration Stage
During the identity registration phase, Users are required to generate their public–private key pairs and complete the blockchain registration process. As illustrated in Figure 3, all participating entities in trans-border scenarios must sequentially execute the full identity registration procedure. Upon successful registration, Users’ identity information—including email addresses and public keys—is stored on the blockchain in a structured data format (JSON, see Figure 4). This ensures decentralized authentication and secure sharing of identity data across the network.
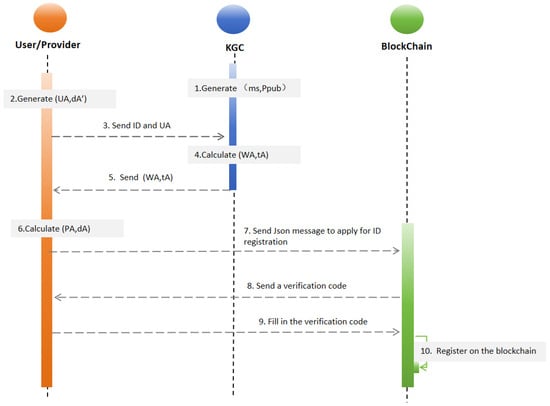
Figure 3.
Overview of the identity registration.

Figure 4.
JSON format of the identity information.
- Step 1: KGC generates the system parameters and the master public and private key pair, represented as .
- Step 2: Both the User and Provider send their respective identity IDs to the KGC. In this scheme, the identity ID is represented by an email address. Each entity (User and Provider) also generates its own public value and secret value, denoted as .
- Step 3: Upon receiving the identity information (ID) and public value from the User and Provider, the KGC combines these with the system parameters and the master key pair to compute the User’s declared public key and partial private key .
- Step 4: The KGC returns the User’s declared public key and partial private key to each respective entity (User and Provider).
- Step 5: Upon receiving the declared public key and partial private key from the KGC, both the User and Provider calculate their true private key , using their secret value and partial private key . They also calculate their true public key , using .
- Step 6: The User and Provider each verify their computed public key by comparing it with . If matches then the verification is successful, confirming the authenticity of the true public key ; otherwise, the public key is deemed invalid.
- Step 7: After successful verification, a JSON message is created to apply for identity registration on the blockchain. This JSON message contains the identity information (e.g., email and public key ).
- Step 8: The blockchain sends a verification code to the User and Provider to confirm the registration process.
- Step 9: The User and Provider fill in the verification code they received to authenticate their registration request.
- Step 10: Upon successful verification, the blockchain registers the identity information, making it immutable and accessible for trans-border authentication.
4.2.3. Authentication Stage
When a User wants to access the data resources of an overseas Provider, the two entities need to establish communication and complete authentication to obtain access authorization. First, the User downloads the Provider’s identity information from the blockchain, including the Provider’s email and public key. Then, the User performs an elliptic curve point multiplication operation using their private key and the Provider’s public key to generate a shared key. This shared key is used to encrypt the session packet, ensuring the security of information during transmission. Meanwhile, the Provider downloads the User’s public key information from the blockchain. The Provider then performs the same point multiplication operation, using their private key and the User’s public key to generate a shared key identical to that of the User. Upon receiving the knock packet, the Provider decrypts it, using the shared key, and verifies the integrity and validity of the information, ensuring successful and secure identity authentication. The specific steps are shown in Figure 5.
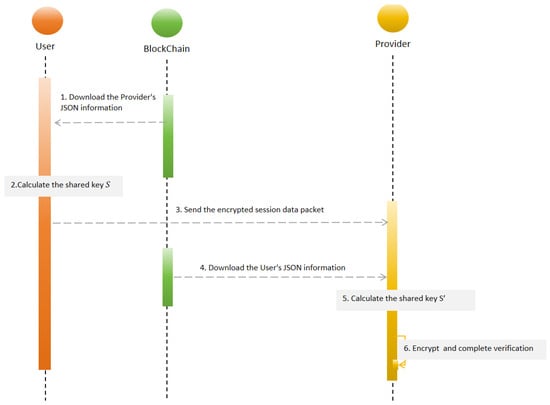
Figure 5.
Overview of the trans-border authentication.
- Step 1: The User downloads the Provider’s JSON identity information from the blockchain, which includes the Provider’s email and public key.
- Step 2: Using the downloaded public key of the Provider, the User calculates a shared key S by performing elliptic curve point multiplication with their own private key. This shared key will be used to encrypt the session data.
- Step 3: The User encrypts the session data packet, using the shared key S, and sends this encrypted packet to the Provider.
- Step 4: The Provider downloads the User’s JSON identity information from the blockchain, including the User’s public key, to prepare for identity verification.
- Step 5: Using the User’s public key, the Provider calculates a shared key by performing elliptic curve point multiplication with their own private key. This shared key should match the User’s shared key S if the calculations are correct.
- Step 6: The Provider decrypts the received session data packet, using the shared key , and verifies the integrity and validity of the information, completing the identity verification process.
5. Experiments
5.1. Experimental Setup
5.1.1. Experiment Design
This study systematically evaluated the performance of CL-PKC-based key-management mechanisms and ECC in trans-border data transmission scenarios through experimental implementation within the proposed STALE model architecture. A simulated tripartite interaction environment was constructed, consisting of User terminals (User), trans-border service providers (Provider), and distributed KGC nodes. Using a controlled variable methodology, we focused on three critical performance dimensions: temporal complexity characteristics across key lifecycle phases (generation, distribution, negotiation, and updating); the quantitative effects of encrypted packet storage overhead on end-to-end transmission efficiency under constrained bandwidth; and identity authentication latency in the FISCO BCOS consortium blockchain framework and its impact on system real-time performance. This experimental design specifically targets three fundamental research questions:
RQ1: Key Generation and Agreement Time: Under the distributed CL-PKC architecture, what are the latency characteristics and influencing factors during both the key-generation phase (including master key pair generation and User partial private key computation) and the key-agreement phase (based on the ECDHE protocol)? Furthermore, how does its performance compare with traditional PKI systems and IBE schemes?
RQ2: Communication Overhead: A comparative analysis of the communication costs when employing the optimized ECDHE protocol for session key exchange versus different baseline approaches.
RQ3: Blockchain Registration Delay: Investigating the temporal characteristics of identity registration based on the FISCO BCOS consortium blockchain, including the impact of consensus mechanisms, smart contract execution efficiency, and trans-border network constraints on authentication real-time performance.
5.1.2. Experimental Topology
To address the above experimental design objectives, this paper designed a network topology based on the AHAC framework, as shown in Figure 6, in which this experiment was carried out on a desktop computer running Ubuntu 20.04, with the following equipment configuration: processor: Intel Core i7-9700K at 3.6 GHz; (Intel, Santa Clara, CA, USA); RAM: 16 GB DDR4; graphic processor: NVIDIA GeForce RTX 2060 (NVIDIA, Santa Clara, CA, USA); hard drive: 512 GB SSD. The software environment was Go programming language (version: 1.21.0), and the required dependency libraries included the relevant libraries for blockchain and cryptographic operations. Meanwhile, the experiment also used some blockchain simulation tools and communication protocol testing tools for testing the performance in trans-border data transmission scenarios.
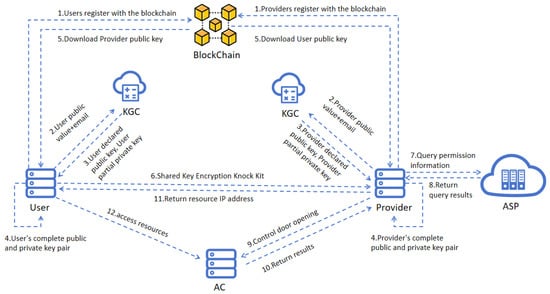
Figure 6.
Trans-border distributed authentication topology in STALE (integrated with AHAC framework).
Based on the network topology diagram above, the specific operational steps of this experiment were as follows:
- Step 1: The User/Provider registered the Provider’s public key information on the blockchain.
- Step 2: The User/Provider calculated their public value and sent it along with their email to the KGC.
- Step 3: Upon receiving the User’s/Provider’s public value and email, the KGC computed the User’s/Provider’s declared public key and partial private key, then sent these back to the User/Provider.
- Step 4: The User/Provider received the declared public key and partial private key from the KGC and used this data to calculate their complete public and private key pair.
- Step 5: The User/Provider downloaded the other party’s public key information from the blockchain.
- Step 6: The User performed an elliptic curve point multiplication operation, using their private key and the Provider’s public key to generate a shared key. The User encrypted the “knock” packet with this shared key and sent it to the Provider.
- Step 7: Upon receiving the knock packet, the Provider calculated the shared key in the same way, decrypted the packet, and then queried the ASP (Authorization Service Provider) to check whether the User had access rights.
- Step 8: The ASP returned the access authorization result to the Provider.
- Step 9: Based on the authorization result, the Provider responded accordingly. If access was granted, the Provider notified the AHAC AC to allow access; if not, no response was given.
- Step 10: The AHAC AC returned the execution result to the Provider.
- Step 11: The Provider returned the resource IP address to the User.
- Step 12: The User received the IP address and successfully accessed the resource based on the IP.
5.2. Performance Test
5.2.1. RQ1: What Is the Time Required for Key Generation and Key Agreement?
To evaluate the performance of the key-management and encryption operations, this experiment involved performance testing across the following stages. The metrics recorded included (1) the time required by the KGC to generate the system’s master public–private key pair, (2) the time taken by the User to generate their public and secret values, (3) the time required for the User to declare a public key and for the KGC to generate the User’s partial private key, (4) the time for the User to compute their complete private key and actual public key, (5) the time consumed in the authentication process, and (6) the total time for public key generation and the entire communication sequence. Each metric was measured multiple times to comprehensively assess performance in trans-border authentication scenarios. Each stage was tested 200 times, and the average time consumption for each stage, as well as the total time consumption for the entire process, was calculated. The results are shown in Figure 7:
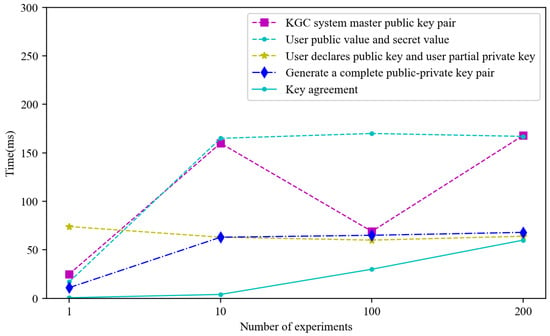
Figure 7.
Key generation time.
The experimental results indicate that the time for KGC system master public key pair generation remained relatively stable as the number of experiments increased. Although there was a slight rise after the initial experiment, it stabilized after 10 trials, suggesting that the KGC’s key pair generation is efficient and does not significantly impact performance as the experiment scale grows. The time required for user public and secret value generation started low and increased slightly with additional experiments, demonstrating good scalability. The time for user public key declaration and partial private key generation by the KGC was also stable, similar to the KGC master key generation, with a minor peak at 10 experiments before stabilizing, indicating that this step has low overhead. The time for the user to complete private and actual public key calculations remained consistently low across all the experiments, showing minimal variation and confirming that this calculation step maintains high efficiency even as the scale expands.
In contrast, the ECDH encryption and verification time started very low but gradually increased as the number of experiments grew, showing the largest rise among all the steps. This suggests that communication overhead could become a minor bottleneck for scalability, especially with frequent encryption and decryption operations. Overall, most stages in the key-management and encryption processes (such as key generation and public–private key calculations) demonstrated efficient and stable time consumption, exhibiting strong scalability.
Since CT [35], ITS [41], and ADKG [42] address trans-border identity verification through MA-ABE—a widely adopted approach—and share STALE’s compliance objectives while relying on centralized UCAP, they provide measurable overhead metrics (e.g., key-generation time) to contrast with STALE’s decentralized advantages. Therefore, we selected these three baselines for comparison with our proposed scheme (STALE). Specifically, we compared the runtime performance of key generation and key agreement between the two approaches. The results for key-generation time are shown in Figure 8, while key-agreement time is presented in Figure 9:
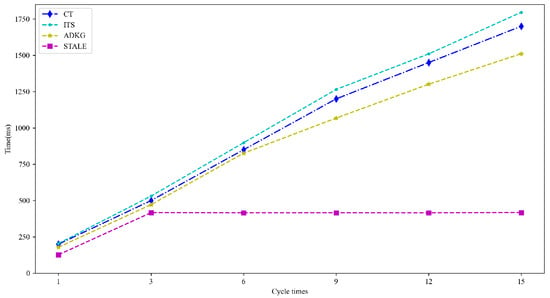
Figure 8.
Comparison of key pair generation time between STALE and baseline algorithms.
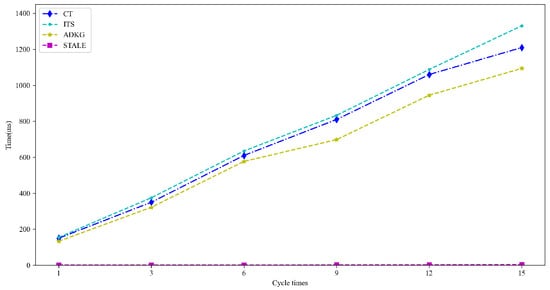
Figure 9.
Comparison of key-agreement time between STALE and baseline algorithms.
The experimental comparison of key-generation time between the baseline and STALE demonstrated distinct performance characteristics. The baseline exhibited a steady increase in processing time from 200 ms to 1700 ms across trials, revealing scalability challenges and potential inefficiencies for high-frequency applications. In contrast, STALE maintained consistent performance, starting at 127 ms and demonstrating minimal variation between 415 ms and 417.5 ms throughout all the trials. This comparative analysis highlights STALE’s superior scalability and stable performance, making it particularly suitable for frequent or large-scale key-generation tasks. The baseline’s progressively increasing time consumption indicates inherent limitations in handling substantial workloads effectively.
In the key-agreement time test, the experimental results demonstrate that STALE consistently maintained significantly lower key-agreement latency compared to the baseline. Starting at 0.60 ms, STALE’s processing time increased marginally to only 3.721 ms by the 15th attempt, highlighting its robust scalability and efficiency. In contrast, the baseline began at 150 ms and exhibited substantial growth to 1210 ms with increasing attempts, indicating considerable time consumption and potential scalability limitations. These findings suggest that STALE’s performance characteristics make it particularly suitable for applications requiring frequent and efficient key-agreement operations, whereas the baseline’s progressive time accumulation may restrict its viability in high-frequency scenarios.
In addition, this study integrated with AHAC to test the time required to complete an access communication. AHAC utilized the identity information proposed in this paper to perform authentication and successfully achieve access communication. The test results for the time taken are shown in Figure 10:
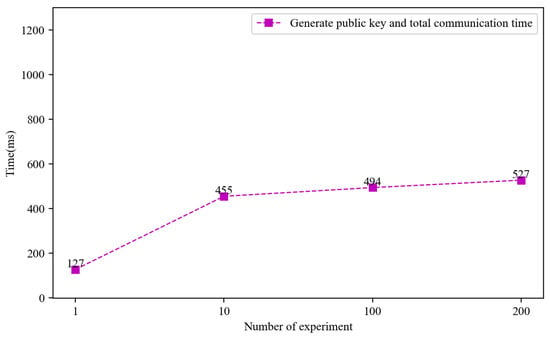
Figure 10.
Public key generation and authentication communication time.
The experiment measured the time required to generate a public key and complete authentication communication across different numbers of trials. The results demonstrate that the system maintained stable and manageable performance as the workload increased. The gradual rise from 127 ms for a single trial to 527 ms over 200 trials suggests strong scalability, with the system effectively handling higher loads without significant drops in efficiency. This consistent performance indicates that the system is capable of supporting frequent key-generation and communication processes in practical, high-demand environments.
5.2.2. RQ2: What Is the Communication Overhead?
This section provides statistics and comparisons for the communication overhead in the authentication process, comparing other cross-domain authentication schemes [43,44,45] and the proposed scheme, as summarized in Table 3:

Table 3.
Communication overhead.
We let represent the information length of the group variable, represent the information length on the elliptic curve, represent the information length of the timestamp, represent the length of user and anonymous identities, and represent the information length of HMAC. It was assumed that the length of was 80 bits; the timestamp was 16 bits; the group variable was 160 bits; the certificate ciphertext was 160 bits; the identity was 80 bits, and was 160 bits. The total overhead constituted the sum of the registration phase overhead and the communication/authentication phase overhead.
In the comparison of overhead among the four schemes, the proposed scheme demonstrated significant advantages, particularly in terms of total overhead. Specifically, the total overhead of the proposed scheme was only 352 bits, which was much lower than the 1120 bits in Scheme [43], the 1392 bits in Scheme [44], and the 1168 bits in Scheme [45]. These results indicate that the proposed scheme is more efficient in resource utilization, significantly reducing communication and storage costs while ensuring security. Additionally, the overhead in both the registration phase and the communication/authentication phase highlighted the competitiveness of the proposed scheme. The use of the algorithm in the registration phase substantially reduced overhead, and the communication/authentication phase incurred only , further optimizing performance. This optimization makes the proposed scheme more feasible for large-scale applications, enhancing overall system efficiency while reducing network load and providing strong support for practical implementation.
5.2.3. RQ3: What Is the Delay for Identity Registration on the Blockchain?
This study employed blockchain technology to achieve identity storage and sharing. To ensure identity authenticity, a dynamic email verification method was adopted during the blockchain registration phase. To evaluate the performance of on-chain identity registration, experiments were conducted on the FISCO BCOS consortium blockchain platform, measuring the identity registration process. Table 4 presents the average response time, confirming the feasibility of the proposed scheme:

Table 4.
Average time for identity registration on the blockchain.
Compared to the time required for key generation and key agreement, the on-chain registration time was significantly longer. The main reason for this was that the users had to manually input a verification code after receiving the dynamic password via email. This process was highly influenced by individual differences, with input speed varying from person to person, leading to variability in overall registration time. Additionally, the complexity of the verification process can further extend this phase. Although these times were notably longer than those for key generation and communication verification, they are negligible when considering the online operations required to obtain a trusted identity in PKI and DID systems.
5.3. Security Analysis
In the security analysis of the trans-border distributed certificateless authentication scheme proposed in this paper, we conducted an in-depth evaluation from multiple perspectives.
5.3.1. Authenticity and Integrity
This scheme combines CL-PKC with blockchain technology to ensure the authenticity of identity information and the integrity of data transmission. The decentralized nature of blockchain guarantees that identity data, once recorded, cannot be tampered with, effectively preventing unauthorized modifications. The combination of user-generated keys and partial keys from a trusted KGC ensures the legitimacy of user identities and prevents identity forgery. Additionally, all data transmissions employ ECC to maintain data integrity during transmission [22,26].
5.3.2. Global Applicability and Security of Email Addresses
The scheme uses email addresses as identity identifiers, which are globally applicable and unique, making them particularly suitable for trans-border identity authentication. Email addresses are easy to verify and widely used; integrating them with secondary verification methods (e.g., email verification codes or multi-factor authentication) enhances real-time authentication and security. Moreover, email addresses do not involve sensitive personal information, reducing the risk of privacy compliance issues, especially in trans-border legal contexts [18,43,44].
5.3.3. Anonymity
The system ensures user privacy during trans-border authentication through session keys generated using the ECDH algorithm. This scheme does not rely on traditional certificate mechanisms and bases identity verification on non-directly identifiable information like email addresses, enhancing user anonymity and minimizing the exposure of personal sensitive information during trans-border transmission [33].
5.3.4. Data Breach Protection
The scheme uses email addresses as identity IDs and avoids involving sensitive personal data. Additionally, the generated identity proofs are encrypted and stored in a decentralized manner on the blockchain, reducing the risk of data breaches. The immutability of blockchain ensures that identity information cannot be maliciously altered after storage, thus enhancing data security. The decentralized storage model eliminates single points of failure, further reducing the risk of large-scale data breaches associated with centralized storage [7].
5.3.5. Resistance to Man-in-the-Middle Attacks
Man-in-the-middle attacks attempt to intercept or alter data without the knowledge of the communicating parties. This scheme uses the ECDH algorithm to generate dynamic session keys and employs mutual authentication to ensure that both parties can verify each other’s identity. During each session, Users and service Providers use their complete private keys and the other party’s public key to generate a unique session key. Even if an attacker intercepts the communication, they cannot decrypt or modify the data. Since each communication uses a different session key, attackers cannot gain useful information by intercepting or replaying previous communications. Additionally, the immutability and transparency of blockchain further ensure that communication data cannot be tampered with by third parties during transmission [41].
5.3.6. Performance and Scalability
The scheme’s modular design through the AHAC framework ensures system scalability and adaptability to trans-border scenarios of various scale and complexities [40].
Based on the above six aspects of analysis, it is evident that the proposed decentralized certificateless identity authentication scheme integrates CL-PKC with blockchain technology. By employing the AHAC framework to achieve mutual authentication and a network concealment mechanism, the scheme significantly enhances identity authentication security and system resilience against attacks in trans-border data transmission. The solution aligns with the zero-trust security architecture, demonstrating strong potential for broader practical applications.
5.4. Economic Cost Analysis
The application of trans-border distributed certificateless authentication methods in trans-border scenarios offers significant economic advantages. Traditional certificate-based PKI systems rely on centralized CAs to manage the issuance and revocation of certificates, which incurs substantial financial, human, and time costs. According to financial reports from multiple publicly listed CA companies, millions of organizations worldwide depend on CA services for identity authentication. These operational costs typically include infrastructure development, certificate issuance and revocation, audits, and compliance expenses. Table 5 presents the cost distribution of certificate management among major global CA companies.

Table 5.
Operating cost data of CA public companies in the US, China, Europe, and Japan (Unit: million USD).
In traditional CA systems, particularly in trans-border business scenarios, maintaining and coordinating trust chains between different jurisdictions requires additional resources and time. The proposed scheme eliminates the need for CA trust management and offline authentication processes, significantly reducing these costs. Specifically, the complexity of certificate issuance, revocation, and renewal processes is greatly simplified, reducing the operational burden and minimizing potential economic losses due to improper key management. According to the data shown in Table 5, major CA companies invest substantial operational costs in certificate management. For example, DigiCert incurs an annual expense of USD 120 million on certificate management, which constitutes a significant part of its overall operational costs. Other companies, such as Entrust and Sectigo, face similar cost structures.
The proposed scheme eliminates the need for CA trust management and simplifies the key-management process, effectively lowering operational costs and avoiding the potential economic risks associated with certificate issuance errors or revocation delays. Overall, the STALE scheme provides a more efficient and cost-effective solution for trans-border data transmission and identity authentication, enhancing system security and scalability while offering a more economically viable option for modern digital ecosystems.
6. Conclusions and Future Work
Trans-border data flow has emerged as a critical research area in global digital transformation, encompassing pivotal challenges such as identity trust verification, data security governance, and privacy compliance assurance. The current studies exhibit notable gaps in designing trans-border identity authentication mechanisms, particularly in establishing inter-jurisdictional collaborative verification frameworks. This paper proposes STALE, a distributed certificate-free authentication method for trans-border scenarios, enabling real-time verification of trusted identities during transnational access. The scheme adopts email-based user identification integrated with a Certificate-free Public Key Cryptosystem, eliminating certificate management overhead and key escrow risks while streamlining authentication procedures and enhancing data privacy protection. Leveraging blockchain’s decentralized storage and verification, the system ensures tamper-proof identity records and transparent auditing. By employing ECDH for key exchange, the method achieves efficient and secure authentication, particularly suited for multi-jurisdictional environments. Furthermore, it removes reliance on CAs or third-party trust, significantly reducing operational costs through simplified management. Our experimental results demonstrate the scheme’s superior authentication efficiency, with marked advantages in communication and computational overhead. This work presents an innovative, cost-effective, and practical solution to trans-border identity authentication, offering critical insights for addressing globalization-driven challenges in transnational data transfer and identity management.
Future research will focus on addressing the following key challenges. Firstly, regarding system scalability, we will investigate optimization strategies for blockchain consensus mechanisms, with particular emphasis on sharding techniques. Secondly, in terms of standards compliance and regulatory alignment, subsequent work will prioritize interoperability with mainstream identity authentication frameworks. Finally, formal security verification will be explored. Advancements in these directions will enhance the applicability and security of the proposed scheme in real-world commercial environments, laying a theoretical foundation for constructing secure and reliable trans-border digital identity infrastructure.
Author Contributions
Conceptualization, M.X., J.Z. and Z.T.; methodology, M.X., J.Z. and Z.T.; software, B.C. and A.W.; validation, J.Z., Y.L. and S.Z.; formal analysis, S.Z. and B.C; investigation, M.X., J.Z. and Z.T.; resources, M.X. and Y.L; data curation, S.Z. and B.C; writing—original draft preparation, M.X. and Z.T.; writing—review and editing, M.X. and Z.T.; visualization, Y.L. and B.C.; supervision, J.L., L.Z. and W.W.; project administration, A.W. and K.Q.Z.; funding acquisition, J.L., L.Z. and W.W. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the research fund of MUST-YONGHENG Cross-border Data Flows Innovation Laboratory.
Informed Consent Statement
Informed consent was obtained from all subjects involved in the study.
Data Availability Statement
Data are available upon request.
Conflicts of Interest
Author Anyu Wang was employed by the company Tanka Inc. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| ASP | Authorized Service Provider |
| CL-PKC | Certificateless Public Key Cryptography |
| ECDH | Elliptic Curve Diffie–Hellman |
| ECDHE | Elliptic Curve Diffie–Hellman Ephemeral |
| CA | Certificate Authority |
| PKI | Public Key Infrastructure |
| KGC | Key-Generation Center |
| RSA | Rivest–Shamir–Adleman |
| DID | Decentralized Identity |
| ECC | Elliptic Curve Cryptography |
| CLC | Certificateless Cryptosystems |
| IBE | Identity-Based Encryption |
| PKG | Private Key Generator |
| UCAP | Universal Certificate Authority Pool |
| DLT | Distributed Ledger Technology |
| GDPR | General Data Protection Regulation |
| D2D | Device-to-Device |
References
- Zheng, Y.; Bai, Q.; Zhao, L.; Chun, H.; Chen, J. Design and implementation of PKI-based certification authority. Sixth Int. Conf. Electron. Inf. Eng. 2015, 9794, 629–633. [Google Scholar]
- De Domenico, M.; Baronchelli, A. The fragility of decentralised trustless socio-technical systems. EPJ Data Sci. 2019, 8, 1–6. [Google Scholar] [CrossRef]
- Zhang, R.; Liu, J.; Han, Z.; Zheng, L. An IBE scheme using ECC combined public key. Comput. Electr. Eng. 2010, 36, 1046–1054. [Google Scholar] [CrossRef]
- Park, J.H.; Lee, D.H. An efficient IBE scheme with tight security reduction in the random oracle model. Des. Codes Cryptogr. 2016, 79, 63–85. [Google Scholar] [CrossRef]
- Chen, Y.; Zhang, F. A new certificateless public key encryption scheme. Wuhan Univ. J. Nat. Sci. 2008, 13, 721–726. [Google Scholar] [CrossRef]
- Raghav, R.; Chaudhary, E.A. Authentication System and Authorization System Using Blockchain Technology. In Proceedings of the 2023 IEEE North Karnataka Subsection Flagship International Conference (NKCon), Belagavi, India, 19–20 November 2023; pp. 1–6. [Google Scholar]
- Liu, H.; Ge, S.; Tan, G.; Tang, S. Research on Application of Identity Authentication Encryption Technology in Blockchain Scene. In Proceedings of the 8th International Conference on Cyber Security and Information Engineering, Putrajaya, Malaysia, 22–24 September 2023; pp. 126–129. [Google Scholar]
- Lan, F.; Jiang, Y. Optimization Exploration of Digital Identity Authentication Algorithm Based on Blockchain. Appl. Math. Nonlinear Sci. 2024, 9, 1–16. [Google Scholar] [CrossRef]
- Goodell, G.; Aste, T. A decentralized digital identity architecture. Front. Blockchain 2019, 2, 491305. [Google Scholar] [CrossRef]
- Huang, J.; Nicol, D.M. An anatomy of trust in public key infrastructure. Int. J. Crit. Infrastruct. 2017, 13, 238–258. [Google Scholar] [CrossRef]
- Yang, X.; Chen, C.; Ma, T.; Wang, J.; Wang, C. Revocable identity-based proxy re-signature against signing key exposure. PLoS ONE 2018, 13, e0194783. [Google Scholar] [CrossRef]
- Yakubov, A.; Shbair, W.; Wallbom, A.; Sanda, D.; State, R. A blockchain-based PKI management framework. In Proceedings of the The First IEEE/IFIP International Workshop on Managing and Managed by Blockchain (Man2Block) Colocated with IEEE/IFIP NOMS 2018, Tapei, Tawain, 23–27 April 2018. [Google Scholar]
- Lin, L.; Tian, Y.; Liu, Y. A blockchain-based privacy-preserving recommendation mechanism. In Proceedings of the 2021 IEEE 5th International Conference on Cryptography, Security and Privacy (CSP), Zhuhai, China, 8–10 January 2021; pp. 74–78. [Google Scholar]
- Liu, Q.; Gong, B.; Ning, Z. Research on CLPKC-IDPKC cross-domain identity authentication for IoT environment. Comput. Commun. 2020, 157, 410–416. [Google Scholar] [CrossRef]
- Chatterjee, S.; Sarkar, P. Identity-Based Encryption; Springer Science & Business Medial: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Zhang, Y.K.; Tian, J.Y.; Yang, C.; Zhang, Y.C.; Hou, F.T. A Novel IBE Based Authentication Scheme for Network Storage. Adv. Mater. Res. 2012, 452, 791–795. [Google Scholar] [CrossRef]
- Shao, S.; Chen, F.; Xiao, X.; Gu, W.; Lu, Y.; Wang, S.; Tang, W.; Liu, S.; Wu, F.; He, J.; et al. IBE-BCIOT: An IBE based cross-chain communication mechanism of blockchain in IoT. World Wide Web 2021, 24, 1665–1690. [Google Scholar] [CrossRef]
- Chen, J.; Lu, F.; Liu, Y.; Peng, S.; Cai, Z.; Mo, F. Cross trust: A decentralized MA-ABE mechanism for trans-border identity authentication. Int. J. Crit. Infrastruct. Prot. 2024, 44, 100661. [Google Scholar] [CrossRef]
- Adams, C. Security Analysis of a Privacy-Preserving Identity-Based Encryption Architecture. J. Inf. Secur. 2022, 13, 323–336. [Google Scholar] [CrossRef]
- Alimabi, S.; Babu, K.S. Implementing Secure Data Sharing with IBE Using Cloud Based Revocable Storage Systems. 2018. Available online: https://www.ijatir.org/uploads/264351IJATIR17084-164.pdf (accessed on 15 April 2025).
- Afroaz, K.; Rao, Y.V.S.; Rukma, R.N. A key escrow free anonymous identity based encryption scheme using ring signatures. In Proceedings of the 2022 IEEE 11th International Conference on Communication Systems and Network Technologies (CSNT), Indore, India, 23–24 April 2022; pp. 596–600. [Google Scholar]
- Zhang, F.T.; Sun, Y.X.; Zhang, L.; Geng, M.M.; Li, S.J. A study on certificateless public key cryptography. J. Softw. 2011, 22, 1316–1332. [Google Scholar] [CrossRef]
- Hamoud, O.N.; Kenaza, T.; Challal, Y. Towards using multiple KGC for CL-PKC to secure D2D communications. In Proceedings of the 2018 International Conference on Smart Communications in Network Technologies (SaCoNeT), El Oued, Algeria, 27–31 October 2018; pp. 283–287. [Google Scholar]
- Liu, Y.; Zhang, A.; Li, J.; Wu, J. An anonymous distributed key management system based on CL-PKC for space information network. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–7. [Google Scholar]
- Vasala, U.; Sakthidharan, D.G. Effective key management in dynamic wireless sensor networks. Int. J. Comput. Eng. Res. Trends 2017, 4, 308–312. [Google Scholar]
- Malik, M.; Kamaldeep; Dutta, M. On the Applicability of Certificateless Public Key Cryptography (CL-PKC) for Securing the Internet of Things (IoT). In Proceedings of the International Conference on IoT Inclusive Life (ICIIL 2019), NITTTR Chandigarh, India; Springer: Singapore, 2020; pp. 43–50. [Google Scholar]
- Wang, X.; Gu, C.; Wei, F.; Lu, S.; Li, Z. A Certificateless-Based Authentication and Key Agreement Scheme for IIoT Cross-Domain. Secur. Commun. Netw. 2022, 2022, 3693748. [Google Scholar] [CrossRef]
- Feng, L.; Qiu, F.; Hu, K.; Yu, B.; Lin, J.; Yao, S. CABC: A Cross-Domain Authentication Method Combining Blockchain with Certificateless Signature for IIoT. Future Gener. Comput. Syst. 2024, 158, 516–529. [Google Scholar] [CrossRef]
- Cao, L.; Liang, M.; Zhang, Z.; Cao, S. Certificateless Cross-Domain Group Authentication Key Agreement Scheme Based on ECC. Wirel. Commun. Mob. Comput. 2022, 2022, 7519688. [Google Scholar] [CrossRef]
- Kurbatov, O.; Shapoval, O.; Poluyanenko, N.; Kuznetsova, T.; Kravchenko, P. Decentralized Identification and Certification System. In Proceedings of the 2019 IEEE International Scientific-Practical Conference Problems of Infocommunications, Science and Technology (PIC S&T), Kyiv, Ukraine, 8–11 October 2019; pp. 507–510. [Google Scholar]
- Bai, Y.; Liu, Z.; Liu, X.; Lu, X.; Lei, H. A cross-chain identity authentication scheme based on DID. In Proceedings of the 2023 IEEE International Conference on Blockchain (Blockchain), Hainan, China, 17–21 December 2023; pp. 172–179. [Google Scholar]
- Zhong, T.; Shi, P.; Chang, J. Joint cloud cross-chain verification model of decentralized identifiers. In Proceedings of the 2021 IEEE International Performance, Computing, and Communications Conference (IPCCC), Austin, TX, USA, 29–31 October 2021; pp. 1–8. [Google Scholar]
- Huh, S.; Shim, M.; Lee, J.; Woo, S.S.; Kim, H.; Lee, H. Did we miss anything?: Towards privacy-preserving decentralized id architecture. IEEE Trans. Dependable Secur. Comput. 2023, 20, 4881–4898. [Google Scholar] [CrossRef]
- Park, C.S.; Nam, H.M. A new approach to constructing decentralized identifier for secure and flexible key rotation. IEEE Internet Things J. 2021, 9, 10610–10624. [Google Scholar] [CrossRef]
- Irwanto, F.; Jodis, J.; Indrakusuma, E.; Gui, A. Decentralized Identity (DID) for Know Your Customer (KYC) Process in the Banking Industry. In Proceedings of the 2023 IEEE 9th International Conference on Computing, Engineering and Design (ICCED), Kuala Lumpur, Malaysia, 7–8 November 2023; pp. 1–6. [Google Scholar]
- Alzahrani, B. An information-centric networking based registry for decentralized identifiers and verifiable credentials. IEEE Access 2020, 8, 137198–137208. [Google Scholar] [CrossRef]
- Li, Z.; Xu, Z.; Liang, C. Distributed Key Management Scheme Based on CL-PKC in P2P Networks. In Threats, Countermeasures, and Advances in Applied Information Security; IGI Global: Hershey, PA, USA, 2012; pp. 234–247. [Google Scholar]
- Xu, D.; Wang, W.; Zhu, L.; Zhao, J.; Wu, F.; Gao, J. CL-BC: A Secure Data Storage Model for Social Networks. Secur. Commun. Netw. 2022, 2022, 5428539. [Google Scholar] [CrossRef]
- Cheng, Z.; Chen, L. Certificateless public key signature schemes from standard algorithms. In Information Security Practice and Experience: 14th International Conference, ISPEC 2018, Tokyo, Japan, 25–27 September 2018; Proceedings 14; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; pp. 179–197. [Google Scholar]
- Xu, M.; Chen, B.; Tan, Z.; Chen, S.; Wang, L.; Liu, Y.; San, T.I.; Fong, S.W.; Wang, W.; Feng, J. AHAC: Advanced Network-Hiding Access Control Framework. Appl. Sci. 2024, 14, 5593. [Google Scholar] [CrossRef]
- Bagga, P.; Das, A.K.; Wazid, M.; Rodrigues, J.J.P.C.; Choo, K.-K.R.; Park, Y. On the design of mutual authentication and key agreement protocol in internet of vehicles-enabled intelligent transportation system. IEEE Trans. Veh. Technol. 2021, 70, 1736–1751. [Google Scholar] [CrossRef]
- Das, S.; Yurek, T.; Xiang, Z.; Miller, A.; Kokoris-Kogias, L.; Ren, L. Practical asynchronous distributed key generation. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 22–26 May 2022; pp. 2518–2534. [Google Scholar]
- Wang, Z.; Han, Z.; Liu, J.; Zhang, D. An authentication scheme based on PTPM and certificateless public key in cloud environment. J. Softw. 2016, 27, 1523–1537. [Google Scholar]
- Yang, X.; An, F.; Yang, P.; Liu, T.; Wang, C. A cross-domain authentication scheme based on certificateless signature in the cloud. Comput. Eng. 2017, 43, 128–133. [Google Scholar]
- Wang, X.; Chen, Z. An authentication scheme based on educational blockchain with certificateless signature. Comput. Syst. Appl. 2022, 31, 178–187. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).