Cybersecurity in MAS-Based Adaptive Protection for Microgrids—A Review
Abstract
1. Introduction
- (i)
- A synthesis and critical evaluation of existing cybersecurity approaches for MAS-based adaptive protection in microgrids.
- (ii)
- An identification of the research gaps and a proposal for future research directions.
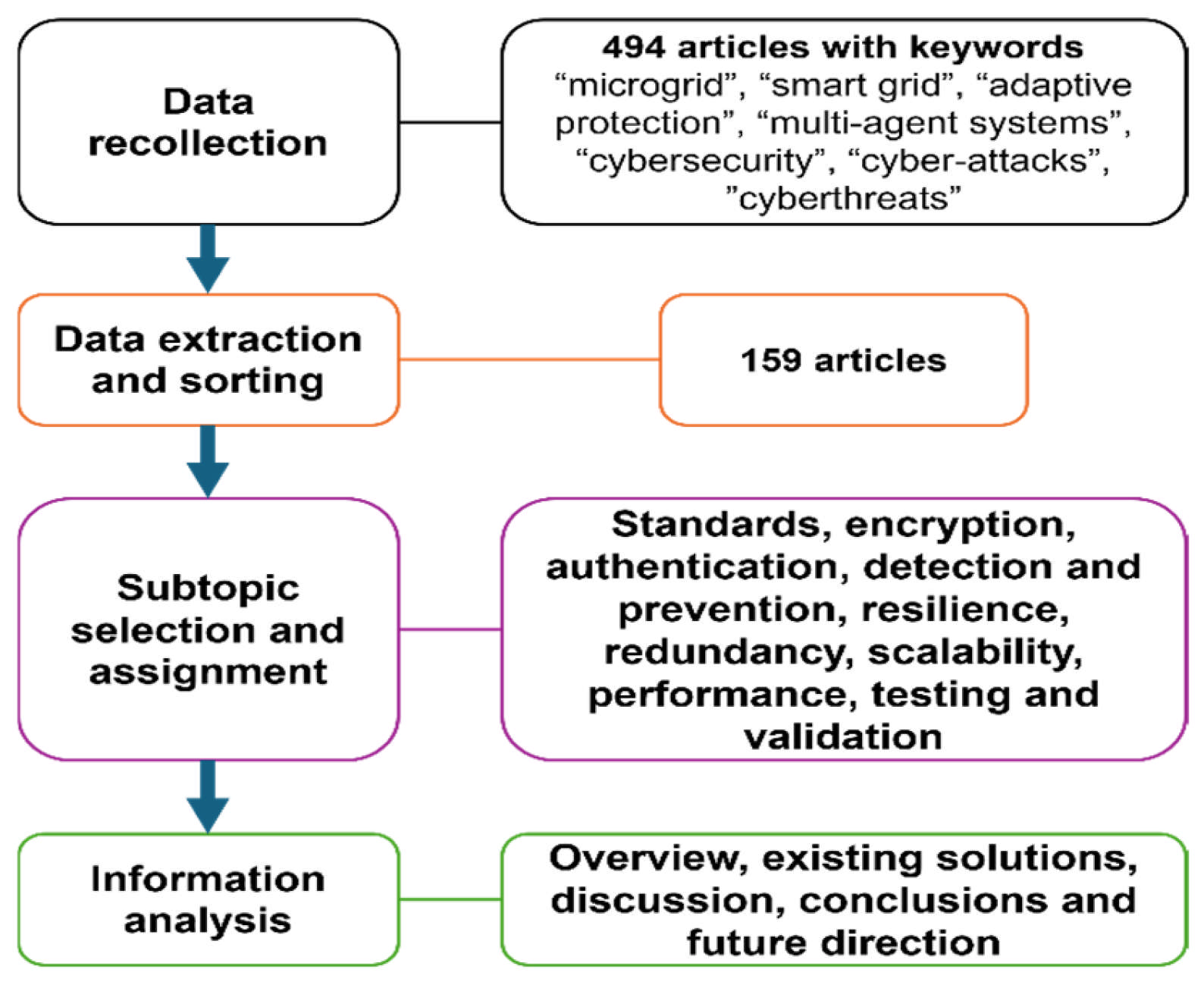
2. Methodology
3. Overview of AC Microgrids and MAS-Based Adaptive Protection
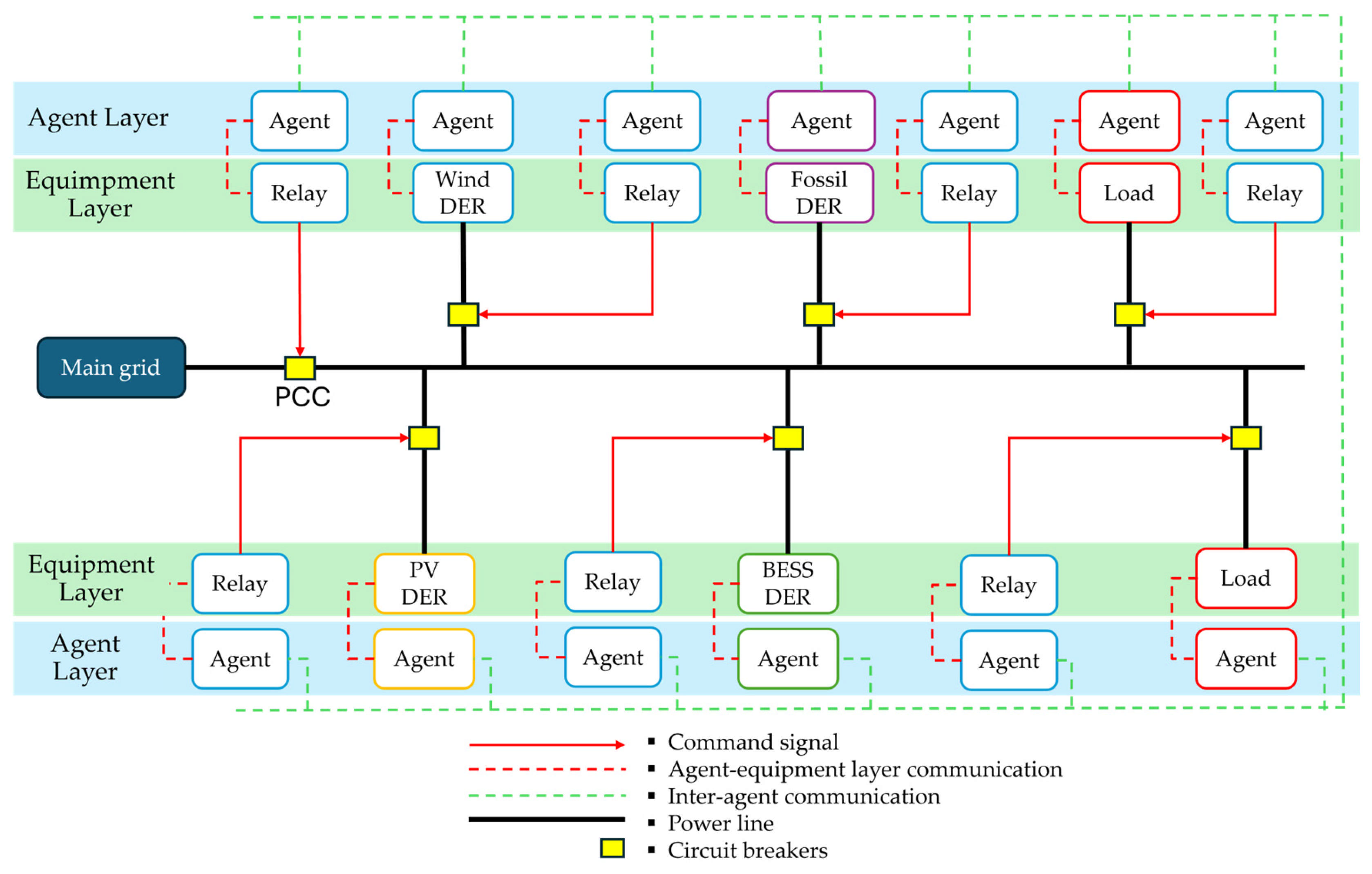
3.1. Structure and Components of AC Microgrids
3.2. MAS in MG Protection and Cybersecurity
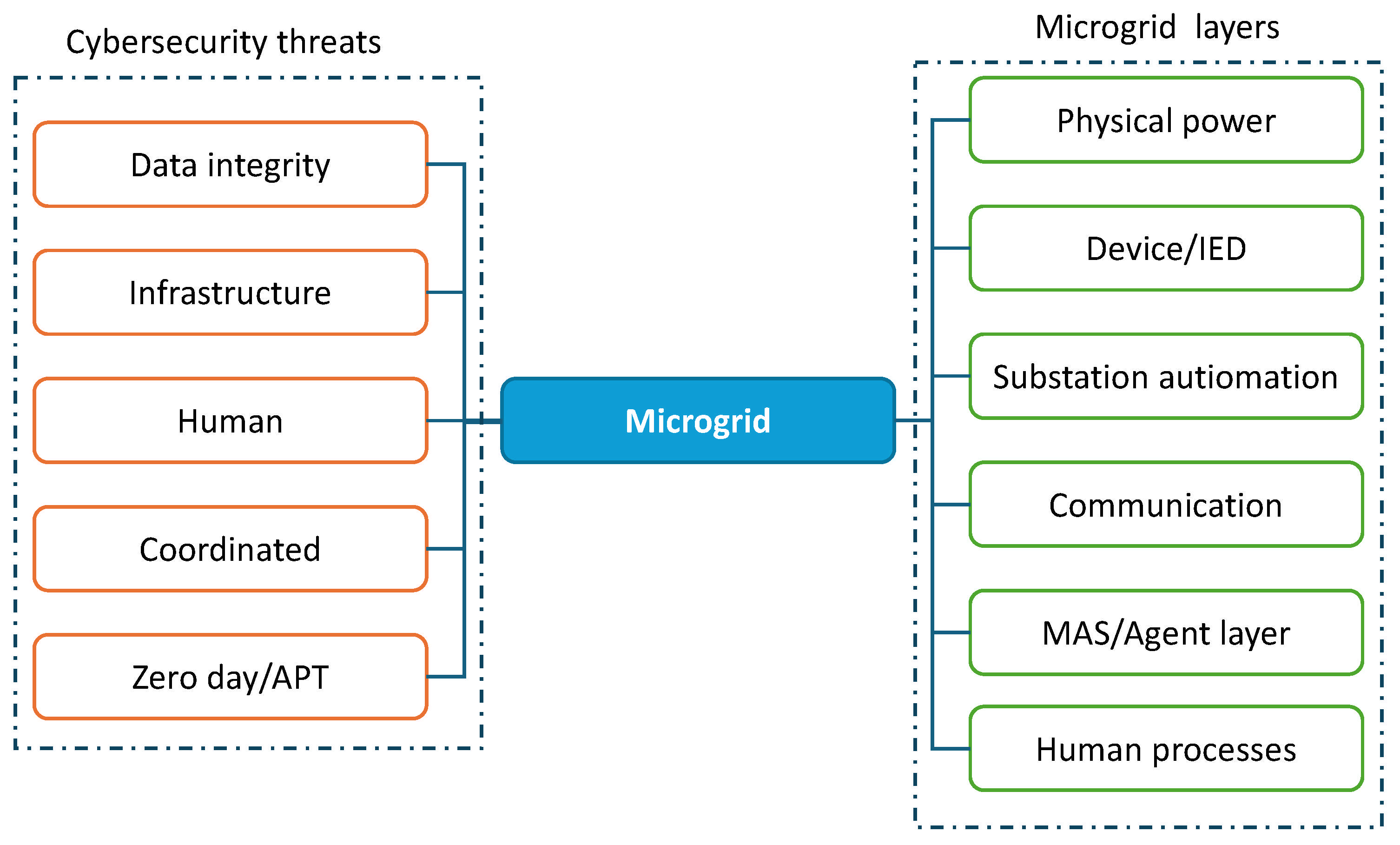
4. Cybersecurity Threats in AC Microgrids
4.1. Cyber Threats in Power Systems
4.1.1. Data Integrity Attacks
4.1.2. Infrastructure and Communication Attacks
4.1.3. Human-Focused Threats
4.1.4. Coordinated and Multi-Stage Attacks
4.1.5. Zero-Day and Advanced Persistent Threats (APTs)
4.2. Impact of Cyberattacks on MAS-Based Adaptive Protection in Microgrids
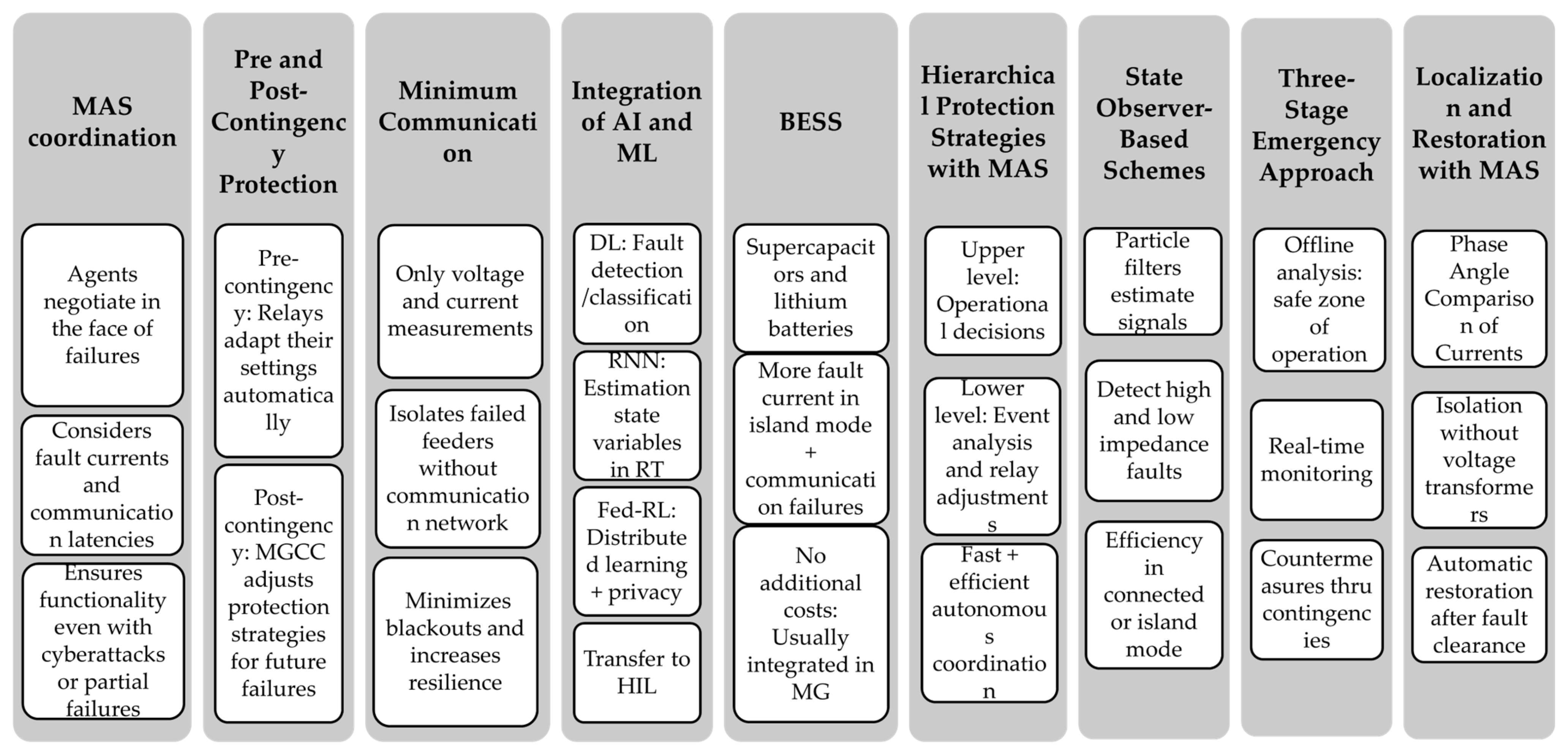
5. Existing Solutions
5.1. Cybersecurity Standards in Power Systems
5.2. Encryption in MAS-Based Microgrids
5.3. Authentication
5.4. Distributed Detection, Mitigation, and Prevention
5.5. Resilience Strategies
5.6. Scalability and Performance
6. Discussion
7. Potential Future Directions
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AC | Alternating Current |
| ACL | Agent Communication Language |
| AES | Advanced Encryption Standard |
| AGC | Automatic Generation Control |
| AI | Artificial Intelligence |
| APT | Advanced Persistent Threat |
| AsyE | Asymmetric Encryption |
| BESS | Battery Energy Storage System |
| BIC | Bidirectional Interlinking Converter |
| BLK | Blockchain |
| CB | Circuit Breaker |
| CHIL | Controller Hardware-in-the-Loop |
| CIP | Critical Infrastructure Protection |
| CKKS | Cheon–Kim–Kim–Song |
| DAS | Distribution Automation System |
| DC | Direct Current |
| DCDM | Decentralized Consensus Decision-Making |
| DER | Distributed Energy Resource |
| DES | Data Encryption Standard |
| DG | Distributed Generation |
| DL | Deep Learning |
| DM | Detection And Mitigation |
| DNP3 | Distributed Network Protocol 3 |
| DoS | Denial-of-Service |
| DT | Detection |
| ECC | Elliptic Curve Cryptography |
| EIoT | Electrical Internet of Things |
| ELK | Elasticsearch, Logstash, and Kibana |
| EMS | Energy Management System |
| ESS | Energy Storage System |
| FDI | False Data Injection |
| Fed-RL | Federated Reinforcement Learning |
| FIPA | Foundation for Intelligent Physical Agent |
| FNR | False Negative Rate |
| FPR | False Positive Rate |
| GOOSE | Generic Object-Oriented Substation Event |
| HIL | Hardware-in-the-Loop |
| HMI | Human–Machine Interface |
| HVDC | High-Voltage Direct Current |
| I-ANN | Informatics Artificial Neural Network |
| ICT | Information and Communication Technology |
| IDPS | Intrusion Detection Protection System |
| IDS | Intrusion Detection System |
| IED | Intelligent Electronic Device |
| IoT | Internet of Things |
| IP | Internet Protocol |
| IPS | Interface Protection System |
| ISE | Integral Squared Error |
| ISMS | Information Security Management System |
| JADE | Java Agent Development Framework |
| JWT | Json Web Token |
| LAN | Local Area Network |
| LC | Inductance Capacitance |
| LCS | Large Change Sensitivity |
| M2M | Machine-to-Machine |
| MA | Master Agent |
| MAC | Media Access Control |
| MARL | Multi-Agent Reinforcement Learning |
| MAS | Multi-Agent System |
| MG | Microgrid |
| MGCC | Microgrid Central Controller |
| MHDM | MAS-Based Detection and Mitigation |
| MitM | Man-in-the-Middle |
| ML | Machine Learning |
| MMG | Multi-Microgrid |
| MT | Mitigation |
| NERC | North American Electric Reliability Corporation |
| NSM | Network and System Management |
| OCC | One-Class Classifier |
| OPF | Optimal Power Flow |
| OT | Operational Technology |
| PCC | Point of Common Coupling |
| PCS | Paillier Cryptosystem |
| PF | Performance Function |
| PI | Proportional-Integral |
| PKI | Public Key Infrastructure |
| RI | Resilience Index |
| RL | Reinforcement Learning |
| RNN | Recurrent Neural Network |
| RSA | Rivest–Shamir–Adleman |
| RT | Real-Time |
| RTAC | Real-Time Automation Controller |
| SA | Slave Agent |
| SCADA | Supervisory Control and Data Acquisition |
| SG | Smart Grid |
| SMV | Sampled Measured Value |
| SNTP | Simple Network Time Protocol |
| SPoF | Single Point of Failure |
| SVR | Support Vector Regression |
| SyE | Symmetric Encryption |
| TADR | True Attack Detection Rate |
| TCP/IP | Transport Control Protocol/Internet Protocol |
| TNR | True-Negative Rate |
| TPR | True-Positive Rate |
| UDP | User Datagram Protocol |
| U.S. | United States |
| VLAN | Virtual Local Area Network |
| W-MSR | Weighted Mean Subsequence Reduced |
| WMSR | Weighted Mean Subsequence Reduced |
| WSN | Wireless Sensor Network |
References
- Taher, M.A.; Tariq, M.; Sarwat, A.I. Enhancing Security in Islanded AC Microgrid: Detecting and Mitigating FDI Attacks in Secondary Consensus Control through AI-Based Method. In Proceedings of the 2023 IEEE International Conference on Energy Technologies for Future Grids, ETFG 2023, Wollongong, Australia, 3–6 December 2023. [Google Scholar] [CrossRef]
- Rahmoune, F.; Ait Aali, N.; El Bouzekri El Idrissi, Y. Enhancing Green Energy Security: Exploring Multi-Agent Systems Perspectives for a Secure Smart Grid Information System. Procedia Comput. Sci. 2024, 236, 485–492. [Google Scholar] [CrossRef]
- Patarroyo-Montenegro, J.F.; Andrade, F.; Guerrero, J.M.; Vasquez, J.C. A Linear Quadratic Regulator with Optimal Reference Tracking for Three-Phase Inverter-Based Islanded Microgrids. IEEE Trans. Power Electron. 2021, 36, 7112–7122. [Google Scholar] [CrossRef]
- Patarroyo-Montenegro, J.F.; Vasquez-Plaza, J.D.; Andrade, F. A State-Space Model of an Inverter-Based Microgrid for Multivariable Feedback Control Analysis and Design. Energies 2020, 13, 3279. [Google Scholar] [CrossRef]
- Satpathy, P.R.; Ramachandaramurthy, V.K.; Padmanaban, S. Advanced Protection Technologies for Microgrids: Evolution, Challenges, and Future Trends. Energy Strategy Rev. 2025, 58, 101670. [Google Scholar] [CrossRef]
- Do Nascimento, L.L.; Rolim, J.G. Multi-Agent System for Adaptive Protection in Microgrids. In Proceedings of the 2013 IEEE PES Conference on Innovative Smart Grid Technologies, ISGT LA 2013, Washington, DC, USA, 24–27 February 2013. [Google Scholar]
- Khazaei, A.A.; Mahmoudi, A. Decentralized Adaptive Protection Structure for Microgrids Based on Multi–Agent Systems. In Proceedings of the 2019 Iranian Conference on Renewable Energy & Distributed Generation (ICREDG), Tehran, Iran, 11–12 June 2019; pp. 1–8. [Google Scholar]
- Senarathna, T.S.S.; Udayanga Hemapala, K.T.M. Review of Adaptive Protection Methods for Microgrids. AIMS Energy 2019, 7, 557–578. [Google Scholar] [CrossRef]
- IEC 61850-8-1:2011+AMD1:2020 CSV; Communication Networks and Systems for Power Utility Automation—Part 8-1: Specific Communication Service Mapping (SCSM). International Electrotechnical Commission: Geneva, Switzerland, 2020.
- Abbaspour, E.; Fani, B.; Sadeghkhani, I.; Alhelou, H.H. Multi-Agent System-Based Hierarchical Protection Scheme for Distribution Networks with High Penetration of Electronically-Coupled DGs. IEEE Access 2021, 9, 102998–103018. [Google Scholar] [CrossRef]
- Gutierrez-Rojas, D.; Nardelli, P.H.J.; Mendes, G.; Popovski, P. Review of the State of the Art on Adaptive Protection for Microgrids Based on Communications. IEEE Trans. Industr Inform. 2021, 17, 1539–1552. [Google Scholar] [CrossRef]
- Alvarez-Alvarado, M.S.; Apolo-Tinoco, C.; Ramirez-Prado, M.J.; Alban-Chacón, F.E.; Pico, N.; Aviles-Cedeno, J.; Recalde, A.A.; Moncayo-Rea, F.; Velasquez, W.; Rengifo, J. Cyber-Physical Power Systems: A Comprehensive Review about Technologies Drivers, Standards, and Future Perspectives. Comput. Electr. Eng. 2024, 116, 109149. [Google Scholar] [CrossRef]
- Shobole, A.A.; Abafogi, M. Adaptive Protection in Smart Distribution Networks: Coordination Demonstration of Multi-Agent Systems. In Proceedings of the 2023 5th Global Power, Energy and Communication Conference (GPECOM), Cappadocia, Turkiye, 14–16 June 2023; pp. 483–488. [Google Scholar]
- North American Electric Reliability Corporation. 2025 ERO Reliability Risk Priorities Report; North American Electric Reliability Corporation (NERC): Atlanta, GA, USA; Washington, DC, USA, 2025; Available online: https://www.nerc.com/comm/RISC/Related%20Files%20DL/2025_RISC_ERO_Priorities_Report.pdf (accessed on 25 August 2025).
- Gurina, L.; Zoryna, T. Distributed Energy: Benefits of Use and Threats to Cybersecurity. In Proceedings of the 2023 International Conference on Industrial Engineering, Applications and Manufacturing, ICIEAM 2023, Sochi, Russia, 15–19 May 2023; pp. 87–92. [Google Scholar] [CrossRef]
- Bidram, A.; Poudel, B.; Damodaran, L.; Fierro, R.; Guerrero, J.M. Resilient and Cybersecure Distributed Control of Inverter-Based Islanded Microgrids. IEEE Trans. Industr Inform. 2020, 16, 3881–3894. [Google Scholar] [CrossRef]
- Zhou, Q.; Shahidehpour, M.; Alabdulwahab, A.; Abusorrah, A.; Che, L.; Liu, X. Cross-Layer Distributed Control Strategy for Cyber Resilient Microgrids. IEEE Trans. Smart Grid 2021, 12, 3705–3717. [Google Scholar] [CrossRef]
- Gehbauer, C.; Black, D.R. Secured Microgrid Operation for Military Facilities—Findings from a Crowd Hacking Event. In Proceedings of the 2024 IEEE Power and Energy Society Innovative Smart Grid Technologies Conference, ISGT 2024, Washington, DC, USA, 19–22 February 2024. [Google Scholar] [CrossRef]
- Anand, A.; Nagu, B.; Gudur, K. Transition Control and Operation of Hybrid Energy System. In Proceedings of the 2024 IEEE International Conference on Smart Power Control and Renewable Energy, ICSPCRE 2024, Rourkela, India, 19–21 July 2024. [Google Scholar]
- Rouhani, A.; Abasi, M.; Joorabian, M.; Davatgaran, V. Designing a Novel Optimal Energy Management to Determine the Contribution and Effect of Primary Sources on the Structure and Components Size of Smart Microgrids and Smart Buildings. In Proceedings of the 2024 9th International Conference on Technology and Energy Management, ICTEM 2024, Behshar, Iran, 14–15 February 2024. [Google Scholar]
- Guarnieri, M.; Bovo, A.; Giovannelli, A.; Mattavelli, P. A Real Multitechnology Microgrid in Venice: A Design Review. IEEE Ind. Electron. Mag. 2018, 12, 19–31. [Google Scholar] [CrossRef]
- Chae, W.-K.; Won, J.-N.; Lee, H.-J.; Kim, J.-E.; Kim, J. Comparative Analysis of Voltage Control in Battery Power Converters for Inverter-Based AC Microgrids. Energies 2016, 9, 596. [Google Scholar] [CrossRef]
- Eyimaya, S.E.; Altin, N. Microgrids: Definitions, Architecture, and Control Strategies; Academic Press: Cambridge, MA, USA, 2023. [Google Scholar]
- Sinha, R.R.; Kanwar, N. Hybrid Microgrids: Architecture, Modeling, Limitations, and Solutions; Academic Press: Cambridge, MA, USA, 2023. [Google Scholar]
- Weber, L.; Nasiri, A.; Hyypio, D.; Dittman, W. Modeling and Control of a Synchronous Generator in an AC Microgrid Environment. In Proceedings of the ECCE 2016—IEEE Energy Conversion Congress and Exposition, Milwaukee, WI, USA, 18–22 September 2016. [Google Scholar]
- Udoha, E.; Das, S.; Abusara, M. A Power Management System for Interconnected Ac Islanded Microgrids Using Back-To-Back Converter. IET Conf. Proc. 2023, 2023, 177–183. [Google Scholar] [CrossRef]
- De la Cruz, J.; Wu, Y.; Candelo-Becerra, J.E.; Vásquez, J.C.; Guerrero, J.M. Review of Networked Microgrid Protection: Architectures, Challenges, Solutions, and Future Trends. CSEE J. Power Energy Syst. 2024, 10, 448–467. [Google Scholar] [CrossRef]
- Rouhani, S.H.; Su, C.L.; Mobayen, S.; Razmjooy, N.; Elsisi, M. Cyber Resilience in Renewable Microgrids: A Review of Standards, Challenges, and Solutions. Energy 2024, 309, 133081. [Google Scholar] [CrossRef]
- Hussain, N.; Nasir, M.; Vasquez, J.C.; Guerrero, J.M. Recent Developments and Challenges on AC Microgrids Fault Detection and Protection Systems–A Review. Energies 2020, 13, 2149. [Google Scholar] [CrossRef]
- Vegunta, S.C.; Higginson, M.J.; Kenarangui, Y.E.; Li, G.T.; Zabel, D.W.; Tasdighi, M.; Shadman, A. AC Microgrid Protection System Design Challenges—A Practical Experience. Energies 2021, 14, 2016. [Google Scholar] [CrossRef]
- Gaggero, G.B.; Rossi, M.; Girdinio, P.; Marchese, M. Cybersecurity Issues in Communication-Based Electrical Protections. In Proceedings of the International Conference on Electrical, Computer, and Energy Technologies, ICECET 2022, Prague, Czech Republic, 20–22 July 2022. [Google Scholar] [CrossRef]
- Uzair, M.; Li, L.; Eskandari, M.; Hossain, J.; Zhu, J.G. Challenges, Advances and Future Trends in AC Microgrid Protection: With a Focus on Intelligent Learning Methods. Renew. Sustain. Energy Rev. 2023, 178, 113228. [Google Scholar] [CrossRef]
- Kaur, G.; Prakash, A.; Rao, K.U. A Critical Review of Microgrid Adaptive Protection Techniques with Distributed Generation. Renew. Energy Focus 2021, 39, 99–109. [Google Scholar] [CrossRef]
- Shobole, A.A.; Wadi, M. Multiagent Systems Application for the Smart Grid Protection. Renew. Sustain. Energy Rev. 2021, 149, 111352. [Google Scholar] [CrossRef]
- Patnaik, B.; Mishra, M.; Bansal, R.C.; Jena, R.K. AC Microgrid Protection—A Review: Current and Future Prospective. Appl. Energy 2020, 271, 115210. [Google Scholar] [CrossRef]
- dos Reis, F.B.; Pinto, J.O.C.P.; dos Reis, F.S.; Issicaba, D.; Rolim, J.G. Multi-Agent Dual Strategy Based Adaptive Protection for Microgrids. Sustain. Energy Grids Netw. 2021, 27, 100501. [Google Scholar] [CrossRef]
- Khalid, H.; Shobole, A. Existing Developments in Adaptive Smart Grid Protection: A Review. Electr. Power Syst. Res. 2021, 191, 106901. [Google Scholar] [CrossRef]
- Fawzy, N.; Habib, H.F.; Mohammed, O.; Brahma, S. Protection of Microgrids with Distributed Generation Based on Multiagent System. In Proceedings of the 2020 IEEE International Conference on Environment and Electrical Engineering and 2020 IEEE Industrial and Commercial Power Systems Europe (EEEIC/I&CPS Europe), Madrid, Spain, 9–12 June 2020; pp. 1–5. [Google Scholar]
- Albarakati, J.A.; Azeroual, M.; Boujoudar, Y.; EL Iysaouy, L.; Aljarbouh, A.; Tassaddiq, A.; EL Markhi, H. Multi-Agent-Based Fault Location and Cyber-Attack Detection in Distribution System. Energies 2023, 16, 224. [Google Scholar] [CrossRef]
- Aazami, R.; Esmaeilbeigi, S.; Valizadeh, M.; Javadi, M.S. Novel Intelligent Multi-Agents System for Hybrid Adaptive Protection of Micro-Grid. Sustain. Energy Grids Netw. 2022, 30, 100682. [Google Scholar] [CrossRef]
- De La Cruz, J.; Vasquez, J.C.; Guerrero, J.M.; Luna, E.G.; Candelo-Becerra, J.E. Adaptive Multi-Agent-Zonal Protection Scheme for AC Microgrids. In Proceedings of the 2023 25th European Conference on Power Electronics and Applications (EPE’23 ECCE Europe), Aalborg, Denmark, 4–8 September 2023; pp. 1–9. [Google Scholar]
- Ataei, M.A.; Gitizadeh, M. A Distributed Adaptive Protection Scheme Based on Multi-agent System for Distribution Networks in the Presence of Distributed Generations. IET Gener. Transm. Distrib. 2022, 16, 1521–1540. [Google Scholar] [CrossRef]
- Memon, A.A.; Kauhaniemi, K. Real-Time Hardware-in-the-Loop Testing of IEC 61850 GOOSE-Based Logically Selective Adaptive Protection of AC Microgrid. IEEE Access 2021, 9, 154612–154639. [Google Scholar] [CrossRef]
- Satuyeva, B.; Sultankulov, B.; Nunna, H.S.V.S.K.; Kalakova, A.; Doolla, S. Q-Learning Based Protection Scheme for Microgrid Using Multi-Agent System. In Proceedings of the 2019 International Conference on Smart Energy Systems and Technologies (SEST), Porto, Portugal, 9–11 September 2019; pp. 1–6. [Google Scholar]
- Rahman, M.S.; Isherwood, N.; Oo, A.M.T. Multi-Agent Based Coordinated Protection Systems for Distribution Feeder Fault Diagnosis and Reconfiguration. Int. J. Electr. Power Energy Syst. 2018, 97, 106–119. [Google Scholar] [CrossRef]
- Tripathi, J.M.; Yadav, N.; Mallik, S.K.; Chandel, A. A Multi-Agent Approach for Protection Coordination in a Microgrid Using JADE Platform. In Proceedings of the 2025 IEEE 1st International Conference on Smart and Sustainable Developments in Electrical Engineering, SSDEE 2025, Dhanbad, India, 28 February–2 March 2025; pp. 1–6. [Google Scholar] [CrossRef]
- Alzahrani, S.; Sinjari, K.; Mitra, J. Multi-Agent and State Observer-Based Technique for Microgrid Protection. IEEE Trans. Ind. Appl. 2024, 60, 2697–2705. [Google Scholar] [CrossRef]
- Najar, A.; Kazemi Karegar, H.; Esmaeilbeigi, S. Multi-agent Protection Scheme for Microgrid Using Deep Learning. IET Renew. Power Gener. 2024, 18, 663–678. [Google Scholar] [CrossRef]
- Dizioli, F.A.S.; Barra, P.H.A.; Menezes, T.S.; Lacerda, V.A.; Coury, D.V.; Fernandes, R.A.S. Multi-Agent System-Based Microgrid Protection Using Angular Variation: An Embedded Approach. Electr. Power Syst. Res. 2023, 220, 109324. [Google Scholar] [CrossRef]
- IEC 60870-5-104:2006/AMD1:2016/COR1:2023; Telecontrol Equipment and Systems—Part 5-104: Transmission Protocols—Network Access for IEC 60870-5-101 Using Standard Transport Profiles (Corrigendum 1 to Amendment 1). International Electrotechnical Commission: Geneva, Switzerland, 2023.
- Abbaspour, E.; Fani, B.; Karami-Horestani, A. Adaptive Scheme Protecting Renewable-Dominated Micro-Grids against Usual Topology-Change Events. IET Renew. Power Gener. 2021, 15, 2686–2698. [Google Scholar] [CrossRef]
- Uzair, M.; Li, L.; Zhu, J.G.; Eskandari, M. A Protection Scheme for AC Microgrids Based on Multi-Agent System Combined with Machine Learning. In Proceedings of the 2019 29th Australasian Universities Power Engineering Conference (AUPEC), Nadi, Fiji, 26–29 November 2019; pp. 1–6. [Google Scholar]
- Abbaspour, E.; Fani, B.; Heydarian-Forushani, E. A Bi-Level Multi Agent Based Protection Scheme for Distribution Networks with Distributed Generation. Int. J. Electr. Power Energy Syst. 2019, 112, 209–220. [Google Scholar] [CrossRef]
- Faria, I.M.; Furlan, R.H.; Martins, P.E.T.; Menezes, T.S.; Oleskovicz, M.; Coury, D.V. The Proposition of a Multiagent System for Adaptive Protection of a Distribution System. In Proceedings of the 2018 Simposio Brasileiro de Sistemas Eletricos (SBSE), Niteroi, Brazil, 12–16 May 2018; pp. 1–6. [Google Scholar]
- Daryani, M.J.; Karkevandi, A.E. Decentralized Cooperative Protection Strategy for Smart Distribution Grid Using Multi-Agent System. In Proceedings of the 2018 6th International Istanbul Smart Grids and Cities Congress and Fair (ICSG), Istanbul, Turkey, 25–26 April 2018; pp. 134–138. [Google Scholar]
- Daryani, M.J.; Karkevandi, A.E.; Usta, O. Multi-Agent Approach to Wide-Area Integrated Adaptive Protection System of Microgrid for Pre- and Post-Contingency Conditions. In Proceedings of the 2018 IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), Sarajevo, Bosnia and Herzegovina, 21–25 October 2018; pp. 1–6. [Google Scholar]
- Pullaguram, D.; Sahoo, S. Cyber Security Threats in Multi-Agent Microgrids. In Cyber Security for Microgrids; Institution of Engineering and Technology: Stevenage, UK, 2022; pp. 105–125. [Google Scholar]
- Owoputi, R.; Ray, S. Security of Multi-Agent Cyber-Physical Systems: A Survey. IEEE Access 2022, 10, 121465–121479. [Google Scholar] [CrossRef]
- Khatana, V.; Chakraborty, S.; Saraswat, G.; Patel, S.; Salapaka, M.V. A Distributed Malicious Agent Detection Scheme for Resilient Power Apportioning in Microgrids. In Proceedings of the IECON 2024—50th Annual Conference of the IEEE Industrial Electronics Society, Chicago, IL, USA, 3–6 November 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Karanfil, M.; Rebbah, D.E.; Debbabi, M.; Kassouf, M.; Ghafouri, M.; Youssef, E.N.S.; Hanna, A. Detection of Microgrid Cyberattacks Using Network and System Management. IEEE Trans. Smart Grid 2023, 14, 2390–2405. [Google Scholar] [CrossRef]
- IEC 62351-7:2017; Power Systems Management and Associated Information Exchange—Data and Communications Security—Part 7: Network and System Management (NSM) Data Object Models. International Electrotechnical Commission: Geneva, Switzerland, 2017.
- Roy, S.D.; Debbarma, S.; Guerrero, J.M. Machine Learning Based Multi-Agent System for Detecting and Neutralizing Unseen Cyber-Attacks in AGC and HVDC Systems. IEEE J. Emerg. Sel. Top. Circuits Syst. 2022, 12, 182–193. [Google Scholar] [CrossRef]
- Al-dulaimi, F.N.S.; Kurnaz, S. Enhancing Cybersecurity and Frequency Control Efficiency in AC Islanded Microgrids: A Distributed Approach with a Stochastic Models. In Proceedings of the 2024 8th International Conference on Green Energy and Applications (ICGEA), Singapore, 14–16 March 2024. [Google Scholar] [CrossRef]
- Hu, B.; Zhou, C.; Tian, Y.-C.; Hu, X.; Junping, X. Decentralized Consensus Decision-Making for Cybersecurity Protection in Multimicrogrid Systems. IEEE Trans. Syst. Man. Cybern. Syst. 2021, 51, 2187–2198. [Google Scholar] [CrossRef]
- Zhou, T.L.; Xiahou, K.S.; Zhang, L.L.; Wu, Q.H. Multi-Agent-Based Hierarchical Detection and Mitigation of Cyber Attacks in Power Systems. Int. J. Electr. Power Energy Syst. 2021, 125, 106516. [Google Scholar] [CrossRef]
- Choi, I.-S.; Hong, J.; Kim, T.-W. Multi-Agent Based Cyber Attack Detection and Mitigation for Distribution Automation System. IEEE Access 2020, 8, 183495–183504. [Google Scholar] [CrossRef]
- Boakye-Boateng, K.; Ghorbani, A.A.; Lashkari, A.H. Securing Substations with Trust, Risk Posture, and Multi-Agent Systems: A Comprehensive Approach. In Proceedings of the 2023 20th Annual International Conference on Privacy, Security and Trust, PST 2023, Copenhagen, Denmark, 21–23 August 2023. [Google Scholar] [CrossRef]
- Wang, Y.; Mondal, S.; Deng, C.; Satpathi, K.; Xu, Y.; Dasgupta, S. Cyber-Resilient Cooperative Control of Bidirectional Interlinking Converters in Networked AC/DC Microgrids. IEEE Trans. Ind. Electron. 2021, 68, 9707–9718. [Google Scholar] [CrossRef]
- Abianeh, A.J.; Wan, Y.; Ferdowsi, F.; Mijatovic, N.; Dragicevic, T. Vulnerability Identification and Remediation of FDI Attacks in Islanded DC Microgrids Using Multiagent Reinforcement Learning. IEEE Trans. Power Electron. 2022, 37, 6359–6370. [Google Scholar] [CrossRef]
- Stout, W.M.S. Toward a Multi-Agent System Architecture for Insight & Cybersecurity in Cyber-Physical Networks. In Proceedings of the 2018 International Carnahan Conference on Security Technology (ICCST), Montreal, QC, Canada, 22–25 October 2018; pp. 1–5. [Google Scholar]
- Ogbogu, C.E.; Thornburg, J.; Okozi, S.O. Smart Grid Fault Mitigation and Cybersecurity with Wide-Area Measurement Systems: A Review. Energies 2025, 18, 994. [Google Scholar] [CrossRef]
- Liu, M.; Teng, F.; Zhang, Z.; Ge, P.; Sun, M.; Deng, R.; Cheng, P.; Chen, J. Enhancing Cyber-Resiliency of DER-Based Smart Grid: A Survey. IEEE Trans. Smart Grid 2024, 15, 4998–5030. [Google Scholar] [CrossRef]
- Jimada-Ojuolape, B.; Teh, J.; Lai, C.M. Securing the Grid: A Comprehensive Analysis of Cybersecurity Challenges in PMU-Based Cyber-Physical Power Networks. Electr. Power Syst. Res. 2024, 233, 110509. [Google Scholar] [CrossRef]
- Rath, S.; Nguyen, L.D.; Sahoo, S.; Popovski, P. Self-Healing Secure Blockchain Framework in Microgrids. IEEE Trans. Smart Grid 2023, 14, 4729–4740. [Google Scholar] [CrossRef]
- Rath, S.; Pal, D.; Sharma, P.S.; Panigrahi, B.K. A Cyber-Secure Distributed Control Architecture for Autonomous AC Microgrid. IEEE Syst. J. 2020, 15, 3324–3335. [Google Scholar] [CrossRef]
- Abdelkader, S.; Amissah, J.; Kinga, S.; Mugerwa, G.; Emmanuel, E.; Mansour, D.E.A.; Bajaj, M.; Blazek, V.; Prokop, L. Securing Modern Power Systems: Implementing Comprehensive Strategies to Enhance Resilience and Reliability against Cyber-Attacks. Results Eng. 2024, 23, 102647. [Google Scholar] [CrossRef]
- Yaacoub, J.P.; Noura, H.; Azar, J.; Salman, O.; Chahine, K. Cybersecurity in Smart Renewable Energy Systems. In Proceedings of the 2024 International Wireless Communications and Mobile Computing (IWCMC), Ayia Napa, Cyprus, 27–31 May 2024; pp. 1534–1540. [Google Scholar]
- Nair, P.S.; Mandal, S.K.; Sharma, N. Securing Smart Microgrids: A Cybersecurity Survey. In Proceedings of the 2023 International Conference on Power Energy, Environment & Intelligent Control (PEEIC), Greater Noida, India, 19–23 December 2023; pp. 1318–1322. [Google Scholar]
- Rath, S.; Das, T.; Sengupta, S. Improvise, Adapt, Overcome: Dynamic Resiliency Against Unknown Attack Vectors in Microgrid Cybersecurity Games. IEEE Trans. Smart Grid 2024, 15, 4245–4258. [Google Scholar] [CrossRef]
- Tripathy, M.; Niyogi, R.; Kumar, P.S.; Kumbhar, G.B.; Singh, R.; Thakur, V. A Novel Approach for Detection of Cyber Attacks in Microgrid SCADA System. In Proceedings of the 2023 IEEE 3rd International Conference on Sustainable Energy and Future Electric Transportation (SEFET), Bhubaneswar, India, 9–12 August 2023; pp. 1–6. [Google Scholar]
- Abraham, D.; Toftegaard, Ø.; Retnam, B.B.J.D.; Gebremedhin, A.; Yayilgan, S.Y. Consequence Simulation of Cyber Attacks on Key Smart Grid Business Cases. Front. Energy Res. 2024, 12, 1395954. [Google Scholar] [CrossRef]
- Khalaf, M.; Ayad, A.; Tushar, M.H.K.; Kassouf, M.; Kundur, D. A Survey on Cyber-Physical Security of Active Distribution Networks in Smart Grids. IEEE Access 2024, 12, 29414–29444. [Google Scholar] [CrossRef]
- Anderson, J.; Bougie, J.; Dood, M.; Falk, H.; Formea, J.; Haveron, S.; Holstein, D.; Lacroix, M.; Laughner, T.; Mix, S.; et al. Task Force on Utility & Municipality Challenges on Analyzing and Implementing Cybersecurity Standards and Best Practices. Available online: https://resourcecenter.ieee-pes.org/publications/technical-reports/pes_tr_tr116_psccc_100824 (accessed on 9 September 2025).
- Hasan, M.K.; Abdulkadir, R.A.; Islam, S.; Gadekallu, T.R.; Safie, N. A Review on Machine Learning Techniques for Secured Cyber-Physical Systems in Smart Grid Networks. Energy Rep. 2024, 11, 1268–1290. [Google Scholar] [CrossRef]
- IEC 62443-2-4:2015; Security for Industrial Automation and Control Systems—Part 2-4: Security Program Requirements for IACS Service Providers. International Electrotechnical Commission: Geneva, Switzerland, 2015.
- Téglásy, B.Z.; Gran, B.A.; Katsikas, S.; Gkioulos, V.; Lundteigen, M.A. Clarification of the Cybersecurity and Functional Safety Interrelationship in Industrial Control Systems: Barrier Concepts and Essential Functions. In Proceedings of the 30th European Safety and Reliability Conference and the 15th Probabilistic Safety Assessment and Management Conference, Venice, Italy, 1–5 November 2020; pp. 1980–1987. [Google Scholar]
- ISO/IEC 27000:2018; Information Technology—Security Techniques—Information Security Management Systems—Overview and Vocabulary. International Organization for Standardization/International Electrotechnical Commission: Geneva, Switzerland, 2018.
- Culot, G.; Nassimbeni, G.; Podrecca, M.; Sartor, M. The ISO/IEC 27001 Information Security Management Standard: Literature Review and Theory-Based Research Agenda. TQM J. 2021, 33, 76–105. [Google Scholar] [CrossRef]
- IEEE 2030-2011; IEEE Guide for Smart Grid Interoperability of Energy Technology and Information Technology Operation with the Electric Power System (EPS), and End-Use Applications, and Loads. Institute of Electrical and Electronics Engineers (IEEE): New York, NY, USA, 2011.
- Hasan, M.K.; Habib, A.A.; Shukur, Z.; Ibrahim, F.; Islam, S.; Razzaque, M.A. Review on Cyber-Physical and Cyber-Security System in Smart Grid: Standards, Protocols, Constraints, and Recommendations. J. Netw. Comput. Appl. 2023, 209, 103540. [Google Scholar] [CrossRef]
- IEEE 1686-2022; Standard for Intelligent Electronic Devices Cybersecurity Capabilities. IEEE (Institute of Electrical and Electronics Engineers): New York, NY, USA, 2022.
- IEEE 1547.3-2007; Guide for Monitoring, Information Exchange, and Control of Distributed Resources Interconnected with Electric Power Systems. IEEE: New York, NY, USA, 2007.
- IEEE 1402-2021; Guide for Physical Security of Electric Power Substations. IEEE: New York, NY, USA, 2021.
- IEEE C37.240-2014; Standard Cybersecurity Requirements for Substation Automation, Protection, and Control Systems. IEEE: New York, NY, USA, 2014.
- Alsafran, A.S. A Feasibility Study of Implementing IEEE 1547 and IEEE 2030 Standards for Microgrid in the Kingdom of Saudi Arabia. Energies 2023, 16, 1777. [Google Scholar] [CrossRef]
- Kim, Y.-S.; Lee, G.; Kang, J. Lightweight IEC 61850 Secure Communication Module for Microgrids. In Lecture Notes on Data Engineering and Communications Technologies; Springer: Cham, Switzerland, 2017; Volume 2, pp. 443–451. [Google Scholar] [CrossRef]
- Cusimano, J. Overview of ISA 62443 and Its Relationship to the NIST Framework. In Proceedings of the ISA Process Control and Safety Symposium 2014, PCS 2014, Houston, TX, USA, 7–9 October 2014; pp. 859–872. [Google Scholar]
- Goodwin, S. The Need for a Financial Sector Legal Standard to Support the NIST Cybersecurity Framework. In Proceedings of the IEEE Southeast Con, Mobile, AL, USA, 26 March–3 April 2022; pp. 89–95. [Google Scholar]
- Wang, L.; Zhang, P.; Tang, Z. Programmable Crypto-Control for Networked Microgrids. In Microgrids; Wiley: Hoboken, NJ, USA, 2024; pp. 335–357. [Google Scholar]
- Cheng, Z.; Ye, F.; Cao, X.; Chow, M.-Y. A Homomorphic Encryption-Based Private Collaborative Distributed Energy Management System. IEEE Trans. Smart Grid 2021, 12, 5233–5243. [Google Scholar] [CrossRef]
- Zhuo, Q.; Zhang, H.; Hu, X. A Homomorphic Cryptography Based Privacy-Preserving Consensus Algorithm with Event-Triggering in Distributed Energy Management. In Proceedings of the 2021 40th Chinese Control Conference (CCC), Shanghai, China, 26–28 July 2021; pp. 6772–6777. [Google Scholar]
- Liu, B.; Wu, J.; Chai, L. Distributed Privacy-Preserving Algorithm for Economic Dispatch and Demand Response of Smart Grid with Homomorphic Encryption. IEEE Trans. Smart Grid 2025, 16, 173–182. [Google Scholar] [CrossRef]
- Joshi, S.; Li, R.; Bhattacharjee, S.; Das, S.K.; Yamana, H. Privacy-Preserving Data Falsification Detection in Smart Grids Using Elliptic Curve Cryptography and Homomorphic Encryption. In Proceedings of the 2022 IEEE International Conference on Smart Computing (SMARTCOMP), Helsinki, Finland, 20–24 June 2022; pp. 229–234. [Google Scholar]
- Raso, E.; Bracciale, L.; Gallo, P.; Bernardinetti, G.; Bianchi, G.; Sanseverino, E.R.; Loreti, P. Performance Evaluation of Cryptographic Schemes for Blockchain Security of Smart Grids. In Proceedings of the 2022 Workshop on Blockchain for Renewables Integration (BLORIN), Palermo, Italy, 2–3 September 2022; pp. 113–117. [Google Scholar]
- Mohamed, M.O.; Abdelaziz, A.Y.; Abo-Elyousr, F.K. Blockchain-Based Approach for Load Frequency Control of Smart Grids under Denial-of-Service Attacks. Comput. Electr. Eng. 2024, 116, 109150. [Google Scholar] [CrossRef]
- Awais, M.; Abbas, Q.; Tariq, S.; Warraich, S.H. Blockchain Based Secure Energy Marketplace Scheme to Motivate P2P Microgrids. Int. J. Inform. Commun. Technol. (IJ-ICT) 2022, 11, 177. [Google Scholar] [CrossRef]
- Sharma, D.D.; Lin, J.; Sarojwal, A.; Sharma, A.; Sharma, A. Blockchain Based Adaptive Non-Cooperative Game Strategy for Smart Power Contracts. In Proceedings of the 2023 IEEE 8th International Conference for Convergence in Technology (I2CT), Lonavla, India, 7–9 April 2023; pp. 1–6. [Google Scholar]
- Sabir, B.E.; Youssfi, M.; Bouattane, O.; Allali, H. Authentication Model Based on JWT and Local PKI for Communication Security in Multi-Agent Systems. In Learning and Analytics in Intelligent Systems; Springer: Cham, Switzerland, 2020; Volume 7, pp. 469–479. [Google Scholar] [CrossRef]
- Feng, L.; Mei, H. Research and Design of Security in Multi-Agent System. In Proceedings of the IET International Conference on Wireless Mobile and Multimedia Networks Proceedings (ICWMMN 2006), Online, 6–9 November 2006; p. 417. [Google Scholar] [CrossRef]
- Jiang, Y.; Du, S.; Xu, W.; Dong, Y. V2G Charging and Discharging Information Authentication Based on Blockchain Technology. In Proceedings of the 2024 IEEE 4th International Conference on Digital Twins and Parallel Intelligence, DTPI 2024, Wuhan, China, 18–20 October 2024; pp. 732–736. [Google Scholar] [CrossRef]
- Mahmood, S.; Gohar, M.; Choi, J.G.; Koh, S.J.; Alquhayz, H.; Khan, M. Digital Certificate Verification Scheme for Smart Grid Using Fog Computing (Fonica). Sustainability 2021, 13, 2549. [Google Scholar] [CrossRef]
- Ogunnusi, O.S.; Razak, S.A.; Abdullah, A.H. A Lightweight One-Pass Authentication Mechanism for Agent Communication in Multi-Agent System Based Applications. J. Teknol. 2015, 77, 1–9. [Google Scholar] [CrossRef][Green Version]
- Mehta, P.J.; Parne, B.L.; Patel, S.J. SE-LAKAF: Security Enhanced Lightweight Authentication and Key Agreement Framework for Smart Grid Network. Peer Peer Netw. Appl. 2023, 16, 1513–1535. [Google Scholar] [CrossRef]
- Zhu, L.; Cao, Y.; Liao, L.; Tan, Y.; Durad, M.H.; Wang, D. Secure Group Communication in Multi-Agent Systems. WSEAS Trans. Commun. 2006, 5, 781–787. [Google Scholar]
- Bolgouras, V.; Ntantogian, C.; Panaousis, E.; Xenakis, C. Distributed Key Management in Microgrids. IEEE Trans. Industr. Inform. 2020, 16, 2125–2133. [Google Scholar] [CrossRef]
- Samuel, O.; Javaid, N.; Khalid, A.; Imrarn, M.; Nasser, N. A Trust Management System for Multi-Agent System in Smart Grids Using Blockchain Technology. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar]
- Xu, M.; Qin, Y.; Mei, W.; Lin, C.; Shen, L. Lightweight Access Authentication Management Method for Complex Power End-Side Devices. In Proceedings of the Sixth International Conference on Information Science, Electrical, and Automation Engineering (ISEAE 2024), Wuhan, China, 19–21 April 2024; Volume 13275, p. 57. [Google Scholar]
- Boi, B.; Esposito, C. Decentralized Authentication in Microservice Architectures with SSI and DID in Blockchain. In Proceedings of the International Conference on Cloud Computing Technology and Science, CloudCom, Naples, Italy, 4–6 December 2023; pp. 216–223. [Google Scholar]
- Pathak, A.; Al-Anbagi, I.; Hamilton, H.J. Privacy-Preserving Authentication Mechanism for P2P Energy Trading in Smart Grid Networks. In Proceedings of the IEEE International Conference on Communications, Denver, CO, USA, 9–13 June 2024; pp. 3085–3090. [Google Scholar]
- Daubry, W.; Dricot, J.-M.; Henneaux, P. Decentralized Group Authentication with Membership Verification in Islanded Smart Grids. In Proceedings of the 2023 12th Mediterranean Conference on Embedded Computing (MECO), Budva, Montenegro, 6–10 June 2023; pp. 1–6. [Google Scholar]
- Alshowkan, M.; Evans, P.; Starke, M.; Earl, D.; Peters, N. Authentication of Smart Grid Communications Using Quantum Key Distribution. Sci. Rep. 2022, 12, 12731. [Google Scholar] [CrossRef]
- Mezquita, Y.; Gazafroudi, A.S.; Corchado, J.M.; Shafie-Khah, M.; Laaksonen, H.; Kamišalić, A. Multi-Agent Architecture for Peer-to-Peer Electricity Trading Based on Blockchain Technology. In Proceedings of the 2019 XXVII International Conference on Information, Communication and Automation Technologies (ICAT), Sarajevo, Bosnia and Herzegovina, 20–23 October 2019; pp. 1–6. [Google Scholar]
- Cheng, Z.; Chow, M.-Y. An Augmented Bayesian Reputation Metric for Trustworthiness Evaluation in Consensus-Based Distributed Microgrid Energy Management Systems with Energy Storage. In Proceedings of the 2020 2nd IEEE International Conference on Industrial Electronics for Sustainable Energy Systems (IESES), Cagliari, Italy, 1–3 September 2020; pp. 215–220. [Google Scholar]
- Bougueroua, N.; Mazouzi, S.; Belaoued, M.; Seddari, N.; Derhab, A.; Bouras, A. A Survey on Multi-Agent Based Collaborative Intrusion Detection Systems. J. Artif. Intell. Soft Comput. Res. 2021, 11, 111–142. [Google Scholar] [CrossRef]
- Isaza, G.A.; Castillo, A.G.; Duque, N.D. An Intrusion Detection and Prevention Model Based on Intelligent Multi-Agent Systems, Signatures and Reaction Rules Ontologies. In Advances in Intelligent and Soft Computing; Springer: Berlin/Heidelberg, Germany, 2009; Volume 55, pp. 237–245. [Google Scholar] [CrossRef]
- Ouiazzane, S.; Addou, M.; Barramou, F. A Multi-Agent Model for Network Intrusion Detection. In Proceedings of the ICSSD 2019—International Conference on Smart Systems and Data Science, Rabat, Morocco, 3–4 October 2019. [Google Scholar]
- Mudzingwa, D.; Agrawal, R. A Study of Methodologies Used in Intrusion Detection and Prevention Systems (IDPS). In Proceedings of the IEEE Southeastcon, Orlando, FL, USA, 15–18 March 2012. [Google Scholar]
- Devi, V.A.; Bhuvaneswari, E.; Tummala, R.K. Decentralized Hybrid Intrusion Detection System for Cyber Attack Identification Using Machine Learning. In Proceedings of the 2023 International Conference on Data Science, Agents and Artificial Intelligence, ICDSAAI 2023, Chennai, India, 21–23 December 2023. [Google Scholar]
- Mezghani, S.; Ktata, F.B. A Distributed Intelligent Agent Based Intrusion Detection System Using Deep Learning Algorithms. In Proceedings of the DTUC ‘20: Proceedings of the 2nd International Conference on Digital Tools & Uses Congress, Virtual, 7–15 October 2020. [Google Scholar]
- Ali, A.; Zia, A.; Razzaque, A.; Shahid, H.; Sheikh, H.T.; Saleem, M.; Yousaf, F.; Muneer, S. Enhancing Cybersecurity with Artificial Neural Networks: A Study on Threat Detection and Mitigation Strategies. In Proceedings of the 2nd International Conference on Cyber Resilience, ICCR 2024, Dubai, United Arab Emirates, 26–28 February 2024. [Google Scholar]
- Louati, F.; Barika Ktata, F.; Amous, I. An Intelligent Security System Using Enhanced Anomaly-Based Detection Scheme. Comput. J. 2024, 67, 2317–2330. [Google Scholar] [CrossRef]
- Louati, F.; Ktata, F.B.; Amous, I. Big-IDS: A Decentralized Multi Agent Reinforcement Learning Approach for Distributed Intrusion Detection in Big Data Networks. Cluster Comput. 2024, 27, 6823–6841. [Google Scholar] [CrossRef]
- Tesnim, Y.; Farah, J. A Multi-Agent-Based System for Intrusion Detection. In Smart Innovation, Systems and Technologies; Springer: Singapore, 2021; Volume 241, pp. 177–191. [Google Scholar] [CrossRef]
- Achbarou, O.; El Kiram, M.A.; Bourkoukou, O.; Elbouanani, S. A Multi-Agent System-Based Distributed Intrusion Detection System for a Cloud Computing. In Communications in Computer and Information Science; Springer: Cham, Switzerland, 2018; Volume 929, pp. 98–107. [Google Scholar] [CrossRef]
- Zhang, X.; Zhang, Z.; Zhang, R.; Liu, W.; Li, H.; Peng, J. Event-Triggered Resilient Recovery Learning Control Protocol for Interconnected DC Microgrids with Distributed Attack Detection. Sustain. Energy Grids Netw. 2024, 38, 101364. [Google Scholar] [CrossRef]
- Zhang, H.; Meng, W.; Qi, J.; Wang, X.; Zheng, W.X. Distributed Load Sharing Under False Data Injection Attack in an Inverter-Based Microgrid. IEEE Trans. Ind. Electron. 2019, 66, 1543–1551. [Google Scholar] [CrossRef]
- Hosseini, S.A.; Sadeghi, S.H.H.; Nasiri, A. Decentralized Adaptive Protection Coordination Based on Agents Social Activities for Microgrids with Topological and Operational Uncertainties. IEEE Trans. Ind. Appl. 2021, 57, 702–713. [Google Scholar] [CrossRef]
- Samkari, H.S.; Johnson, B.K. Multi-Agent Protection Scheme for Resilient Microgrid Systems with Aggregated Electronically Coupled Distributed Energy Resources. In Proceedings of the IECON 2018—44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 752–757. [Google Scholar]
- Mumtaz, F.; Khan, H.H.; Zafar, A.; Ali, M.U.; Imran, K. A State-Observer-Based Protection Scheme for AC Microgrids with Recurrent Neural Network Assistance. Energies 2022, 15, 8512. [Google Scholar] [CrossRef]
- Mukherjee, S.; Hossain, R.R.; Mohiuddin, S.M.; Liu, Y.; Du, W.; Adetola, V.; Jinsiwale, R.A.; Huang, Q.; Yin, T.; Singhal, A. Resilient Control of Networked Microgrids Using Vertical Federated Reinforcement Learning: Designs and Real-Time Test-Bed Validations. arXiv 2023, arXiv:2311.12264. [Google Scholar] [CrossRef]
- Habib, H.F.; Esfahani, M.M.; Mohammed, O. Improvement of Protection Scheme for Microgrids Using Lithium- Ion Battery during Islanding. In Proceedings of the 2018 IEEE Industry Applications Society Annual Meeting (IAS), Portland, OR, USA, 23–27 September 2018; pp. 1–8. [Google Scholar]
- Habib, H.F.; Esfahani, M.M.; Mohammed, O.A. Investigation of Protection Strategy for Microgrid System Using Lithium-Ion Battery During Islanding. IEEE Trans. Ind. Appl. 2019, 55, 3411–3420. [Google Scholar] [CrossRef]
- Diaz Caicedo, A.M.; Gómez-Luna, E.; Franco Mejia, E. Revolutionizing Protection Dynamics in Microgrids: Local Validation Environment and a Novel Global Management Control Through Multi-Agent Systems. Comput. Electr. Eng. 2024, 120, 109748. [Google Scholar] [CrossRef]
- Shaker, A.; Bozorg, M.; Safari, A.; Najafi-Ravadanegh, S. An Adaptive Emergency Approach for Hybrid Networked Microgrids Resilience. IEEE Access 2022, 10, 103164–103175. [Google Scholar] [CrossRef]
- Habib, H.F.; Mohammed, O. Decentralized Multi-Agent System for Protection and the Power Restoration Process in Microgrids. In Proceedings of the 2017 Ninth Annual IEEE Green Technologies Conference (GreenTech), Denver, CO, USA, 29–31 March 2017; pp. 358–364. [Google Scholar]
- Ahmad, S.; Ahn, B.; Kim, T.; Choi, J.; Chae, M.; Han, D.; Won, D. Blockchain-Integrated Resilient Distributed Energy Resources Management System. In Proceedings of the 2022 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Singapore, 25–28 October 2022; pp. 59–64. [Google Scholar]
- Babahajiani, P.; Zhang, P. Cyber-Resilient Distributed Microgrid Control. In Microgrids; Wiley: Hoboken, NJ, USA, 2024; pp. 307–334. [Google Scholar]
- Chhor, J.; Sourkounis, C. Networked Control Approach for Voltage Regulation with Optimal Reactive Power-Sharing. In Proceedings of the IECON 2018—44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 225–230. [Google Scholar]
- Yan, C.; Han, Y.; Yang, P.; Wang, C. Microgrid Cybersecurity: Addressing Challenges and Ensuring Resilience. In Proceedings of the 2023 IEEE 4th China International Youth Conference on Electrical Engineering, CIYCEE 2023, Chengdu, China, 8–10 December 2023. [Google Scholar] [CrossRef]
- Jahromi, M.Z.; Yaghoubi, E.; Yaghoubi, E.; Maghami, M.R.; Chamorro, H.R. An Innovative Real-Time Recursive Framework for Techno-Economical Self-Healing in Large Power Microgrids Against Cyber–Physical Attacks Using Large Change Sensitivity Analysis. Energies 2025, 18, 190. [Google Scholar] [CrossRef]
- Surinkaew, T.; Kerdphol, T. Informatics-Centric Neural Network for Distributed Energy Resources Against Diverse Cyber Threats. IEEE Trans. Industr Inform. 2024, 20, 14029–14041. [Google Scholar] [CrossRef]
- Nguyen, T.L.; Wang, Y.; Nguyen, H.T.; Hoang, T.T. Interconnected Microgrid Systems: Architecture, Hierarchical Control, and Implementation. In Smart Cyber-Physical Power Systems: Fundamental Concepts, Challenges, and Solutions; Wiley: Hoboken, NJ, USA, 2025. [Google Scholar]
- Luu, N.A.; Nguyen, T.L. Secondary Control for Cyber-Physical Interconnected Microgrid Systems. Eng. Technol. Appl. Sci. Res. 2025, 15, 21944–21950. [Google Scholar] [CrossRef]
- Mohamed, N. Renewable Energy in the Age of AI: Cybersecurity Challenges and Opportunities. In Proceedings of the 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT), Kamand, India, 24–28 June 2024; pp. 1–6. [Google Scholar]
| Ref. | VLD | CMP | CSCAD |
|---|---|---|---|
| [46] | JADE | ACL | • |
| [47] | MATLAB/Simulink | • | • |
| [48] | DIgSILENT MATLAB | • | Eliminates communication dependency between agents for fault isolation |
| [49] | PSCAD/EMTD | • | • |
| [41] | ETAP OPAL-RT | IEC 60870 [50] /Modbus | • |
| [39] | MATLAB/Simulink JADE | TCP/IP | Protection against physical faults and cyberattack detection |
| [40] | MATLAB/Simulink | IEC 61850 | Reducing telecommunication risk and minimizing time delay for single-event faults by using offline calculations |
| [42] | MATLAB JADE | Binary data exchange between agents | Enhances robustness against cyberattacks and one-point failures by operating in a fully distributed manner |
| [36] | PSCAD/EMTDC JADE | FIPA | Reduces the risk of communication failures and delays by having a backup offline protection strategy |
| [10] | ETAP | IEC 61850 | • |
| [51] | ETAP MATLAB | IEC 61850 | Self-healing scheme that adapts based on virtual local area network (VLAN) segmentation and communication mapping |
| [38] | Not detailed | • | • |
| [44] | JADE MATLAB | Blockchain for information exchange | • |
| [52] | Simulink AnyLogic | • | • |
| [53] | ETAP | IEC 61850 | • |
| [7] | MATLAB | • | • |
| [54] | RSCAD JADE | • | • |
| [55] | MATLAB | • | • |
| [56] | MATLAB | IEC 61850 | • |
| Ref. | Contribution | CStd | FC | ATT | EU | Key Tools | CSCAD |
|---|---|---|---|---|---|---|---|
| [59] | Distributed detection for malicious DER | • | DT | FDI | • | OPAL-RT, UDP |
|
| [63] | Integrates distributed stochastic control and intelligent secondary frequency control | • | MT | FDI, DoS | • | MATLAB |
|
| [67] | MAS-based trust management system for substation risk | • | DT | DoS | • | Docker, Python, JADE, Modbus TCP/IP |
|
| [60] | Hybrid rule-based and ML anomaly detection | IEC 62351 | DT | MitM | ✓ | OPAL-RT, IEC 61850 IEC-104 [9,50] |
|
| [69] | Multi-agent deep RL for vulnerability ID and detection of FDI attacks | • | ID | FDI | • | MATLAB/Simulink, dSPACE |
|
| [62] | ML-based MAS for unseen data integrity and availability attacks | • | DT | FDI | • | Unspecified |
|
| [39] | MAS for fault location, isolation, reconfiguration, and cyberattack detection | • | DT | FDI | • | MATLAB/Simulink, TCP/IP, JADE |
|
| [64] | Decentralized consensus decision-making (DCDM) with blockchain for cybersecurity | • | DM | • | BLK | Blockchain |
|
| [68] | Distributed resilient control for BICs in AC/DC microgrids | • | CO | FDI | • | MATLAB/Simulink OPC-UA |
|
| [65] | Three-level hierarchical MAS for detecting and mitigating cyberattacks/physical faults | • | DM | LAN MitMDoS | • | MATLAB/Simulink, TCP/IP, JADE |
|
| [16] | Secure intrusion mitigation for microgrid distributed control systems | • | MT | FDI | • | MATLAB/Simulink |
|
| [66] | MAS for cybersecurity-enhanced DAS with anomaly detection/mitigation | IEC 62351 | DM | MitM DoS | ✓ | MATLAB, IEC 61850 |
|
| Ref. | Attack Type | Target Layer | Example | Impact on MAS |
|---|---|---|---|---|
| [60,74,78] | Data Integrity (FDI) | MAS/Agent, Comm. | False measurement injection | False fault detection, mis-tripping |
| [60,75,79] | DoS | Comm. Network, MAS | Flooding IEC 61850 GOOSE | Delayed/failed adaptive response |
| [76,80] | MitM | Comm. Network | Altered relay settings | Hidden miscoordination |
| [75,80] | Insider Threat | MAS Software, Ops. | Config. sabotage | Loss of coordination |
| [58,76,77] | APT/Zero-Day | All layers | Persistent infiltration | Long-term disruption of MAS |
| Ref. | Standard | Focus/Use | Key Limitations |
|---|---|---|---|
| [12] | NERC CIP | Widely used in power utilities to identify cyber vulnerabilities and recommend protections | Manual, costly compliance; not tailored for microgrids or modern communication tech like Wireless Sensor Networks (WSNs) |
| [96] | IEC 62351 | Enhances IEC 61850 with security for communication/data transfer | Optional use; introduces latency; lacks key management; vulnerable to replay, DoS, Simple Network Time Protocol (SNTP) attacks |
| [88] | ISO/IEC 27000-series | ISMS framework, widely used in information security governance | Limited technical controls; less adaptable to resource-constrained devices; variable implementation |
| [81,97,98] | NIST Cybersecurity Framework | Flexible framework for critical infrastructure protection | IT centric; voluntary adoption; incomplete mapping to other standards; limited smart grid specificity |
| [12] | IEEE Standards | Technical protocols and cybersecurity for DER, IEDs, and substation systems | Fragmented coverage; multiple standards with varying relevance to microgrid-scale protection |
| Challenge | Description |
|---|---|
| Complexity of Standards |
|
| Interoperability Issues |
|
| Domain-Specific Gaps |
|
| Resource Constraints |
|
| Compliance vs. Effectiveness |
|
| Evolving Threat Landscape |
|
| Testing and Validation |
|
| Legacy System Integration |
|
| Ref. | Encryption Type | Performance | MAS Use Cases | Notes and Mitigations |
|---|---|---|---|---|
| [104] | Symmetric authenticated encryption | Low latency, suitable for fast control | Frequent control and telemetry | Use for time-critical channels; combine with mutual authentication and rolling keys |
| [100,101,102] | Homomorphic encryption (partial/fully) | High CPU utilization and latency on-device | Privacy-preserving aggregation, distributed optimal power flow (OPF) | Useful for sums/optimization; mitigate by offloading, event-triggering, or encrypting only aggregates |
| Ref. | Technique | Authentication | Description/Use | Drawbacks |
|---|---|---|---|---|
| [108,109] | Public Key Infrastructure (PKI) | Digital Certificates | Authenticates agents and ensures message integrity and non-repudiation | Poor scalability and high management and maintenance costs |
| [110,111] | JSON Web Token (JWT) | Used with PKI for stateless, secure communication, and frequent remote calls | Highly centralized is limiting for MG | |
| [112,113] | One-Pass Authentication | Lightweight Mechanisms | Reduces communication and computational overhead, especially in large agent systems | Challenges in maintaining user anonymity and session key secrecy Limitations in balancing efficiency, performance, and security |
| [114,115] | Group Key Management | Group Re-key Protocols | Ensures that all agents share the same encryption key for secure group communication | Most are insecure and susceptible to MitM and impersonation attacks, or are not suitable for autonomous MG |
| [104,116] | Blockchain + ZKP | - | Audit, settlements, reputation, market transactions; off-chain techniques and permissioned ledgers reduce overhead | High storage and computation, throughput limits; best for non-real-time market functions |
| Ref. | Challenge Area | Key Issues | Proposed Approaches | Limitations/Trade-Offs |
|---|---|---|---|---|
| [148,149,150] | System Complexity | DER integration and advanced communication technologies increase uncertainties and complicated management. | Innovative frameworks to manage disturbances without recalculating full power flow equations. | Added complexity in microgrid operations. |
| [151] | Control vs. Cybersecurity | Difficult to ensure optimal control performance while addressing cyber threats. | I-ANN enhances robustness and damping, mitigating rapid voltage/frequency fluctuations. | Replacement of PI controllers with I-ANN introduces new optimization complexities. |
| [59,150] | Real-Time Adaptability and Efficiency | Balancing immediate updates with computational efficiency. | Frameworks optimizing generation/reconfiguration under technical, economic, and reliability constraints; low-footprint attack detection. | High trade-offs between updating speed and computational load. |
| [69,152,153] | Multi-Agent Coordination | Agents must coordinate within and across microgrids during cyberattacks. | Distributed malicious DER detection and isolation, modular and less delay-sensitive than centralized methods. | Requires extensive data and high-performance computing. |
| [63,150,153] | Scalability and Resilience | Large-scale adaptability and resilience remain challenging. | Large change sensitivity (LCS) method, hierarchical distributed control, bandwidth-efficient solutions. | Increased complexity in communication and coordination with scale. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Taveras Cruz, A.J.; Aybar-Mejía, M.; Colon-González, C.G.; Mariano-Hernández, D.; Hernandez, J.C.; Andrade-Rengifo, F.; Hernández-Callejo, L. Cybersecurity in MAS-Based Adaptive Protection for Microgrids—A Review. Electronics 2025, 14, 3663. https://doi.org/10.3390/electronics14183663
Taveras Cruz AJ, Aybar-Mejía M, Colon-González CG, Mariano-Hernández D, Hernandez JC, Andrade-Rengifo F, Hernández-Callejo L. Cybersecurity in MAS-Based Adaptive Protection for Microgrids—A Review. Electronics. 2025; 14(18):3663. https://doi.org/10.3390/electronics14183663
Chicago/Turabian StyleTaveras Cruz, Armando J., Miguel Aybar-Mejía, Carlos G. Colon-González, Deyslen Mariano-Hernández, Jesús C. Hernandez, Fabio Andrade-Rengifo, and Luis Hernández-Callejo. 2025. "Cybersecurity in MAS-Based Adaptive Protection for Microgrids—A Review" Electronics 14, no. 18: 3663. https://doi.org/10.3390/electronics14183663
APA StyleTaveras Cruz, A. J., Aybar-Mejía, M., Colon-González, C. G., Mariano-Hernández, D., Hernandez, J. C., Andrade-Rengifo, F., & Hernández-Callejo, L. (2025). Cybersecurity in MAS-Based Adaptive Protection for Microgrids—A Review. Electronics, 14(18), 3663. https://doi.org/10.3390/electronics14183663












