Enhancing Account Information Anonymity in Blockchain-Based IoT Access Control Using Zero-Knowledge Proofs
Abstract
1. Introduction
1.1. Background
1.2. Motivation
- Object’s Privacy: From the viewpoint of an IoT device, challenges associated with private data analysis persist within these systems. In BIAC systems, not only subjects and resource owners but also IoT devices are required to connect to the on-chain environment. Due to the limitations in computational power, a commonly employed approach involves utilizing an intermediary object as the gateway for blockchain connection. In this structural setup, the object assumes control over IoT devices and represents them on the blockchain. However, a potential vulnerability arises in this configuration. In existing studies where the object is employed, privacy preservation for the object often gains less recognition compared to the subject’s privacy or is even overlooked. In this context, malicious attackers within the system could easily distinguish IoT devices if the object’s ID is directly used to represent the corresponding controlled IoT device. Once IoT devices are identified, attackers can exploit this information to steal both behavior and identity details from the IoT devices by analyzing public on-chain data.
- Proof Verification: In the pursuit of a high-efficiency and low storage cost, most systems presented in existing works perform zero-knowledge proof verification in the off-chain environment. Nevertheless, this introduces additional trust assumptions and eventually requires the blockchain’s intervention to resolve disputes [21]. Additionally, off-chain verification functions may be susceptible to proof falsification and tampering, which can compromise the accuracy and robustness of the access control mechanism within the system. Therefore, it is necessary to implement on-chain zero-knowledge proof verification in BIAC systems.
- Record Accessibility: In the majority of access control systems, access records are indispensable for auditability and traceability in case of accidents and mistakes. In BIAC, smart contracts often play the important role of maintaining these records due to their immutable feature, which safeguards access records against tampering and falsification. However, the use of smart contracts presents a double-edged sword. Conversely, concerns regarding the privacy of user access rights and actions are on the rise in smart contracts. For instance, in [12], the authors designed a lookup table using smart contracts to display registration information, which poses a high risk of unauthorized access to records. This is attributed to the accessibility of data stored in the smart contract by anyone who knows the contract’s address.
1.3. Our Contribution
- 1.
- To address object privacy, we propose a unified strategy that emphasizes protecting all entities, particularly the object. By combining hash functions with zero-knowledge proofs, we securely process subject and object identities, enhancing account anonymity. Our method offers stronger resistance to object-side linkage attacks than most existing approaches.
- 2.
- Our system uniquely applies zero-knowledge proofs to establish ownership of access rights, seamlessly integrating them with Capability-based Access Control and embedding them in access tokens. Unlike prior work, it supports on-chain verification of zero-knowledge proofs, reducing the risk of falsification and tampering while enhancing access control accuracy and robustness. To facilitate evaluation and comparison, we have made the full source code publicly available, including the on-chain verification function, in Section 5.3.
- 3.
- We also present a robust method for secure and auditable record access. Specifically, a privacy-preserving, tamper-resistant access log is implemented via smart contract, enabling authorized queries while blocking unauthorized ones. Compared to [12], our approach ensures higher confidentiality in access and auditing, addressing concerns related to smart contract transparency.
2. Related Work
3. Attack Model
3.1. Reidentification Attack
3.2. Replay Attack
3.3. Identity Forgery
4. Proposed System Architecture
4.1. System Framework
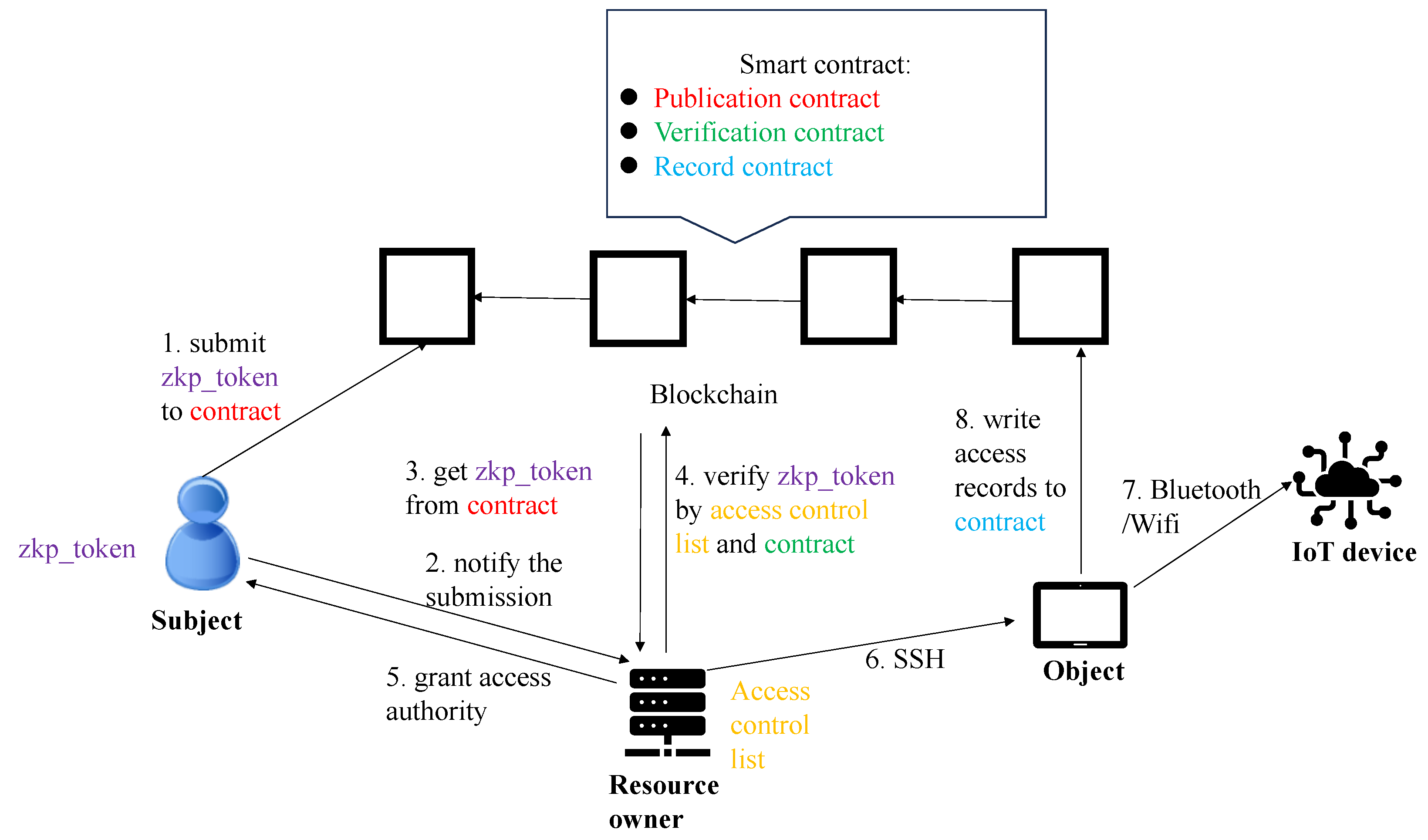
- Subject: The subject in our system functions as the requester of IoT resources, representing the user being served in these systems. In our approach, the subject initiates the process by registering their information with the resource owner, becoming eligible to obtain their original token. Building upon the original token, the subject generates a token with zero-knowledge proof to represent the ownership of access rights. Following verification by both the resource owner and the blockchain, the subject is granted access authority, enabling them to access the IoT device through the object.
- Object: The object serves as the gateway that links IoT devices to the blockchain and controls the IoT device based on instructions from the resource owner. Due to computational limitations, IoT devices are connected to the blockchain through objects rather than establishing a direct connection. As a result, the primary role of the object is to relay commands from the resource owner to the IoT devices and transmit the responses from the IoT device back to the owner. Additionally, the object is tasked with promptly recording access details to the smart contract whenever the corresponding IoT device is accessed.
- IoT device: The IoT device functions as the resource provider in the system, offering a range of functionalities for the subject to utilize. Typically, IoT devices rely on microprocessors, limiting their computational capabilities, especially for tremendous computations. Consequently, the primary focus of the IoT device is on providing services, such as measuring temperature and activating devices, rather than performing complex computations.
- Resource owner: The resource owner holds the ownership of various entities, including IoT devices and their corresponding objects, which are collectively referred to as the ’resource’. In the system, the resource owner plays the role of an administrator when someone seeks access to resources under his/her ownership. The resource owner holds the authority to assess the submitted token and issue a response, indicating acceptance or rejection. Briefly, the resource owner is responsible for creating the blockchain and smart contract, validating the zero-knowledge proof, managing the server, issuing access commands, and granting access authority. Moreover, it is notable that our system allows for the existence of multiple resource owners.
- Step 1: When the subject intends to utilize the IoT device, the zkp_token is first submitted to the corresponding contract for publication.
- Step 2: The subject issues a notification to the resource owner, informing the submission and requesting the retrieval of results via an off-chain channel.
- Step 3: Upon receiving the submitted zkp_token, as notified by the subject, the resource owner proceeds to trace the token’s owner. The process involves checking the consistency of the subject’s ID included in the notification with the ID in the zkp_token, as well as verifying the zkp_token through a hybrid multi-factor verification mechanism.
- Step 4: The verification outcome, whether acceptance or rejection, is then returned along with the details of conducting token verification within the same off-chain channel mentioned earlier to the subject.
- Step 5: In the context of acceptance, access authority is granted to the corresponding subject, allowing the subject to use the IoT device.
- Step 6: The resource owner, upon receiving an access request from the above-mentioned subject, directs the object’s control through SSH to establish connectivity with the IoT device
- Step 7: The IoT device is operated utilizing wireless technologies like Bluetooth and Wi-Fi following the subject’s request.
- Step 8: In the meantime, the object records the access details into the contract, capturing information such as the subject’s ID, the object’s ID, access behavior, and the timestamp.
4.2. Identity Abstraction
4.3. Access Control Mechanism
4.4. Main Functions
4.4.1. On-Chain Functions
4.4.2. Off-Chain Functions
4.4.3. Zero-Knowledge Proof Function
| Algorithm 1 Generate proof. |
|
| Algorithm 2 Verify proof. |
|
5. Implementation
5.1. Application Scenario
5.2. System Configuration
5.3. Experiment
| Algorithm 3 Hybrid multi-factor verification. |
|
6. Evaluation
6.1. Security Analysis
- Countermeasure against reidentification attack: To mitigate reidentification attacks, we introduced a dual privacy-preserving ID mechanism in our BIAC system, ensuring a complete decoupling of user identifiers from real-world identities. As outlined above, the ID structure in our system is defined as . In this design, the outer hash function initially differentiates the anonymized user ID from traceable account information, while the inner component, which utilizes the blockchain address to uniquely identify participants, significantly increases the difficulty of linking account information to real-world identities. Notably, blockchain accounts are neither unique nor establish a one-to-one mapping with users. Furthermore, even in scenarios where either the subject or object faces potential privacy leakage, the ability to change accounts and reregister offers a straightforward solution to mitigate such risks.
- Countermeasure against replay attack: Our BIAC system effectively mitigates replay attacks in both the authentication and resource-provisioning phases. During authentication, a 3-byte random value r is incorporated as the public signal of . This challenge–response authentication mechanism mandates a unique nonce for each authentication round, with the nonce serving as a crucial component in zero-knowledge proof generation, thereby fundamentally preventing replay attacks. Furthermore, to counter replay attacks in the resource-provisioning phase, our system leverages the blockchain to verify the consistency between authentication and resource access. If a replay attack is detected, the access request is immediately denied. In essence, the replay resistance in the resource-provisioning phase is inherently dependent on the authentication phase and is collectively ensured by the challenge–response authentication mechanism implemented in our system.
- Countermeasure against identity forgery: As previously discussed, identity forgery typically occurs on the object side, where privacy and authentication are often neglected in existing studies. However, our system explicitly addresses these concerns by integrating a privacy strategy that combines hash functions with zero-knowledge proofs to securely process both subject and object identities. Specifically, under these protection mechanisms, each legitimate IoT device and object remains anonymous and cannot be impersonated, except in cases involving the theft of a blockchain account.
6.2. Formal Security Proof
6.2.1. Adversary Assumption
6.2.2. Valid Verification
6.2.3. Soundness Analysis
6.2.4. Zero-Knowledge Analysis
6.3. Computation Overhead
6.4. Time Performance
6.5. Space Performance
6.6. Gas Fee Performance
7. Discussion
7.1. Selection of Zero-Knowledge Proof
7.2. Decentralization
7.3. Scalability
8. Conclusions
- 1.
- Currently, our primary focus is on demonstrating the feasibility of utilizing the token to access IoT devices within our system. However, for a capability-based access control system, enabling token delegation is crucial. The absence of token delegation may subject our system to heavy criticism regarding scalability and flexibility.
- 2.
- One of the primary objectives of this work is to leverage the blockchain and smart contracts to enhance decentralization. However, the inclusion of a resource owner as an entity could introduce a significant challenge by centralizing power and authority, thereby conflicting with this goal. While we have demonstrated that the centralized functionalities remain transparently supervised within the decentralized framework, a more effective approach would be to further reduce the involvement of the resource owner.
- 3.
- For an access control system, validating its practicality across various application scenarios is essential. However, our current use case and performance evaluation are limited to the smart building scenario.
- 1.
- We aim to integrate a flexible token delegation and revocation system into our framework while still ensuring the anonymity of accounts and preventing behavior, habits, and record privacy from leakage in the future.
- 2.
- To address the issue related to decentralization, we aim to distribute the resource owner’s authority across the blockchain network, and if feasible, to eliminate this entity entirely in future developments.
- 3.
- We consider that a comprehensive evaluation of scalability is crucial to demonstrate the system’s applicability to large-scale deployment. Therefore, we plan to extend our testing to diverse scenarios of varying scales, such as smart cities or industrial IoT (IIoT), and conduct a corresponding comprehensive performance evaluation in the future.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
Appendix A.1. Symbol Table
| Parameter | Symbol |
|---|---|
| Current Time | |
| Expiry Time | |
| Mapping Number | |
| Random Value | r |
| Proof | |
| Public Signal | |
| ori_token (owner side) | |
| ori_token (subject side) | |
| zkp_token |
Appendix A.2. Experiment Details




References
- Qiu, J.; Tian, Z.; Du, C.; Zuo, Q.; Su, S.; Fang, B. A Survey on Access Control in the Age of Internet of Things. IEEE Internet Things J. 2020, 7, 4682–4696. [Google Scholar] [CrossRef]
- Schiller, E.; Aidoo, A.; Fuhrer, J.; Stahl, J.; Ziörjen, M.; Stiller, B. Landscape of IoT security. Comput. Sci. Rev. 2022, 44, 100467. [Google Scholar] [CrossRef]
- Yue, K.; Zhang, Y.; Chen, Y.; Li, Y.; Zhao, L.; Rong, C.; Chen, L. A Survey of Decentralizing Applications via Blockchain: The 5G and Beyond Perspective. IEEE Commun. Surv. Tutorials 2021, 23, 2191–2217. [Google Scholar] [CrossRef]
- He, W.; Golla, M.; Padhi, R.; Ofek, J.; Dürmuth, M.; Fernandes, E.; Ur, B. Rethinking Access Control and Authentication for the Home Internet of Things (IoT). In Proceedings of the 27th USENIX Security Symposium (USENIX Security 18), Baltimore, MD, USA, 15–17 August 2018; pp. 255–272. [Google Scholar]
- Novo, O. Blockchain Meets IoT: An Architecture for Scalable Access Management in IoT. IEEE Internet Things J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Sandhu, R.; Coyne, E.; Feinstein, H.; Youman, C. Role-based access control models. Computer 1996, 29, 38–47. [Google Scholar] [CrossRef]
- Hu, V.C.; Kuhn, D.R.; Ferraiolo, D.F.; Voas, J. Attribute-Based Access Control. Computer 2015, 48, 85–88. [Google Scholar] [CrossRef]
- Sandhu, R.; Samarati, P. Access control: Principle and practice. IEEE Commun. Mag. 1994, 32, 40–48. [Google Scholar] [CrossRef]
- Barkley, J. Comparing Simple Role Based Access Control Models and Access Control Lists. In Proceedings of the Second ACM Workshop on Role-Based Access Control, Fairfax, VA, USA, 6–7 November 1997; RBAC ’97. pp. 127–132. [Google Scholar] [CrossRef]
- Rasifard, H.; Gopinath, R.; Backes, M.; Nemati, H. SEAL: Capability-Based Access Control for Data-Analytic Scenarios. In Proceedings of the 28th ACM Symposium on Access Control Models and Technologies, New York, NY, USA, 7–9 June 2023; SACMAT’23. pp. 67–78. [Google Scholar] [CrossRef]
- Li, A.S.; Safavi-Naini, R.; Fong, P.W.L. A Capability-based Distributed Authorization System to Enforce Context-aware Permission Sequences. In Proceedings of the 27th ACM on Symposium on Access Control Models and Technologies, New York, NY, USA, 8–10 June 2022; SACMAT’22. pp. 195–206. [Google Scholar] [CrossRef]
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart Contract-Based Access Control for the Internet of Things. IEEE Internet Things J. 2019, 6, 1594–1605. [Google Scholar] [CrossRef]
- Hu, Q.; Dai, Y.; Li, S.; Jiang, T. Enhancing Account Privacy in Blockchain-based IoT Access Control via Zero Knowledge Proof. IEEE Netw. 2022, 37, 117–1123. [Google Scholar] [CrossRef]
- Deogirikar, J.; Vidhate, A. Security attacks in IoT: A survey. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 10–11 February 2017; pp. 32–37. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Miers, I.; Garman, C.; Green, M.; Rubin, A.D. Zerocoin: Anonymous Distributed E-Cash from Bitcoin. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 19–22 May 2013; pp. 397–411. [Google Scholar] [CrossRef]
- Goldwasser, S.; Micali, S.; Rackoff, C. The knowledge complexity of interactive proof-systems. In Proceedings of the Seventeenth Annual ACM Symposium on Theory of Computing, Providence, RI, USA, 6–8 May 1985; STOC ’85. pp. 291–304. [Google Scholar] [CrossRef]
- Groth, J. On the Size of Pairing-Based Non-interactive Arguments. In Proceedings of the Advances in Cryptology—EUROCRYPT 2016, Vienna, Austria, 8–12 May 2016; Fischlin, M., Coron, J.S., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 305–326. [Google Scholar]
- Li, Q.; Xue, Z. A Privacy-Protecting Authorization System Based on Blockchain and Zk-SNARK. In Proceedings of the 2020 International Conference on Cyberspace Innovation of Advanced Technologies, New York, NY, USA, 21–23 October 2020; pp. 439–444. [Google Scholar] [CrossRef]
- Di Francesco Maesa, D.; Lisi, A.; Mori, P.; Ricci, L.; Boschi, G. Self Sovereign and Blockchain Based Access Control: Supporting Attributes Privacy with Zero Knowledge. J. Netw. Comput. Appl. 2023, 212, 103577. [Google Scholar] [CrossRef]
- Du, Y.; Duan, H.; Zhou, A.; Wang, C.; Au, M.H.; Wang, Q. Towards Privacy-assured and Lightweight On-chain Auditing of Decentralized Storage. In Proceedings of the 2020 IEEE 40th International Conference on Distributed Computing Systems (ICDCS), Singapore, 29 November–1 December 2020; pp. 201–211. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. BlendCAC: A BLockchain-Enabled Decentralized Capability-Based Access Control for IoTs. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, USA, 30 July–3 August 2018; pp. 1027–1034. [Google Scholar] [CrossRef]
- Nakamura, Y.; Zhang, Y.; Sasabe, M.; Kasahara, S. Exploiting Smart Contracts for Capability-Based Access Control in the Internet of Things. Sensors 2020, 20, 1793. [Google Scholar] [CrossRef] [PubMed]
- Wang, W.; Huang, H.; Yin, Z.; Gadekallu, T.R.; Alazab, M.; Su, C. Smart contract token-based privacy-preserving access control system for industrial Internet of Things. Digit. Commun. Netw. 2023, 9, 337–346. [Google Scholar] [CrossRef]
- Saini, A.; Zhu, Q.; Singh, N.; Xiang, Y.; Gao, L.; Zhang, Y. A Smart-Contract-Based Access Control Framework for Cloud Smart Healthcare System. IEEE Internet Things J. 2021, 8, 5914–5925. [Google Scholar] [CrossRef]
- Ma, S.; Deng, Y.; He, D.; Zhang, J.; Xie, X. An Efficient NIZK Scheme for Privacy-Preserving Transactions Over Account-Model Blockchain. IEEE Trans. Dependable Secur. Comput. 2021, 18, 641–651. [Google Scholar] [CrossRef]
- Lin, X.; Zhang, Y.; Huang, C.; Xing, B.; Chen, L.; Hu, D.; Chen, Y. An Access Control System Based on Blockchain with Zero-Knowledge Rollups in High-Traffic IoT Environments. Sensors 2023, 23, 3443. [Google Scholar] [CrossRef]
- Khanpara, P.; Lavingia, K.; Trivedi, R.; Tanwar, S.; Verma, A.; Sharma, R. A context-aware internet of things-driven security scheme for smart homes. Secur. Priv. 2023, 6, e269. [Google Scholar]
- Dinur, I.; Dunkelman, O.; Shamir, A. New Attacks on Keccak-224 and Keccak-256. In Fast Software Encryption; Canteaut, A., Ed.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 442–461. [Google Scholar]
- Buckman, A.H.; Mayfield, M.; BM Beck, S. What is a smart building? Smart Sustain. Built Environ. 2014, 3, 92–109. [Google Scholar]
- ethereum foundation. Official Go Implementation of the Ethereum Protocol. Available online: https://geth.ethereum.org (accessed on 29 November 2023).
- ethereum. A Python Interface for Interacting with the Ethereum Blockchain and Ecosystem. Available online: https://github.com/ethereum/web3.py (accessed on 29 November 2023).
- iden3. zkSnark Circuit Compiler. Available online: https://github.com/iden3/circom (accessed on 29 November 2023).
- iden3. zkSNARK Implementation in JavaScript & WASM. Available online: https://github.com/iden3/snarkjs (accessed on 29 November 2023).
- Wu, Y. Implementation of a BIAC System. Available online: https://github.com/wyx19981124/BIAC-system (accessed on 29 November 2023).
- Sun, X.; Yu, F.R.; Zhang, P.; Sun, Z.; Xie, W.; Peng, X. A Survey on Zero-Knowledge Proof in Blockchain. IEEE Netw. 2021, 35, 198–205. [Google Scholar] [CrossRef]
- Zahed Benisi, N.; Aminian, M.; Javadi, B. Blockchain-based decentralized storage networks: A survey. J. Netw. Comput. Appl. 2020, 162, 102656. [Google Scholar] [CrossRef]
- Nikolaenko, V.; Ragsdale, S.; Bonneau, J.; Boneh, D. Powers-of-Tau to the People: Decentralizing Setup Ceremonies. In Cryptology ePrint Archive, Paper 2022/1592; Springer Nature: Cham, Switzerland, 2022; Available online: https://eprint.iacr.org/2022/1592 (accessed on 29 November 2023).
- Gabizon, A.; Williamson, Z.J.; Ciobotaru, O. PLONK: Permutations over Lagrange-bases for Oecumenical Noninteractive arguments of Knowledge. In Cryptology ePrint Archive, Paper 2019/953; Springer Nature: Cham, Switzerland, 2019. [Google Scholar]
- Bünz, B.; Bootle, J.; Boneh, D.; Poelstra, A.; Wuille, P.; Maxwell, G. Bulletproofs: Short Proofs for Confidential Transactions and More. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 315–334. [Google Scholar] [CrossRef]












| Hu et al. [13] | Nakamura et al. [23] | Wang et al. [24] | Lin et al. [27] | Proposed System | |
|---|---|---|---|---|---|
| Access model | CapBAC | CapBAC | CapBAC | ABAC | CapBAC and ACL |
| Privacy preservation strategy | ZKP and Hash function | – | NTRU and NFT | ZK-rollups | ZKP and Hash function |
| Object’s privacy | ✕ | ✕ | ✕ | ✕ | ✓ |
| On-chain records | ✕ | ✕ | ✓ | ✕ | ✓ |
| Prevention of reidentification attack | ✓ | ✕ | ✓ | ✕ | ✓ |
| Prevention of replay attack | ✓ | ✕ | ✓ | ✓ | ✓ |
| Prevention of identity forgery | ✓ | ✕ | ✕ | ✓ | ✓ |
| Capability verification (cost) | Off-chain (low) | Off-chain (low) | On-chain (medium) | On-chain (high) | On-chain (low) |
| Implementation | IoT with different administrators | Token delegation in IoT | IIoT | High-traffic IoT | IoT in smart building |
| Token Type | Field | Description | Remark |
|---|---|---|---|
| ori_token | ID | Identity. | Keccak256 (Address) |
| Access rights | A set of authorized operations. | e.g., read operation | |
| Expiry time | The moment when the token becomes invalid. | Unix time | |
| zkp_token (additional) | Proof | Indicating the knowledge of the mapping number. | |
| Public signals | Public input and output signals from circuits. | 256 bytes | |
| Random value | A 3-byte number. |
| Entity | Device | CPU | GPU | OS | Memory |
|---|---|---|---|---|---|
| Subject A | MacBook Air | Intel i5-1030NG7 | Iris Plus G7 | MacOS 12.4 | 8 GB |
| Subject B | MacBook Pro | Intel i7-9750H | Iris Plus 655 | MacOS 11.5.2 | 8 GB |
| Miner/Resource owner/ Maintainer | Desktop PC | Intel i7-13700F | Nvidia GeForce RTX 4070 | Windows 11 | 32 GB |
| Object A | Raspberry Pi 4 | Cortex-A72 | Integrated GPU | Raspbian 10 | 1 GB |
| Object B | Raspberry Pi 3 | Cortex-A53 | Integrated GPU | Raspbian 8 | 1 GB |
| IoT device A | Switchbot IoT bot | ||||
| IoT device B | Switchbot IoT humidifier | ||||
| Complexity | Cost | |
|---|---|---|
| Hu et al. [13] | 11.3 ms | |
| Lin et al. [27] | 14.7 ms | |
| Our scheme | 4.9 ms |
| Complexity | Cost | |
|---|---|---|
| Hu et al. [13] | 21.4 ms | |
| Lin et al. [27] | 11 ms | |
| Our scheme | 9.1 ms |
| Process | Operation | Time [s] | Operater | Overall Time [s] |
|---|---|---|---|---|
| Setup | Circuit compilation | 39.63 | Resource owner | 982.58 |
| Trusted setup | 41.24 | |||
| Verification key generation | 901.71 | |||
| Execution | zkp_token generation | 6.98 | Subject | 16.04 |
| zkp_token submission | 0.74 | Subject | ||
| zkp_token verification | 0.15 | Resource owner | ||
| IoT operation | 2.44 | Resource owner/ Object/IoT device | ||
| Record creation | 5.73 | Object | ||
| Deployment | Publication contract | 1.89 | Resource owner | 7.42 |
| Verification contract | 3.72 | |||
| Recording contract | 1.81 |
| Function | Gas Used (gas) |
|---|---|
| Deploying Publication.sol | 965,225 |
| Deploying Verifier.sol | 6,446,120 |
| Deploying Recording.sol | 1,471,791 |
| Invoking publish_token() | 3,575,874 |
| Invoking verify_proof() | 0 |
| Invoking submit_record() | 244,263 |
| Property Scheme | Groth16 [18] | PLONK [39] | Bulletproofs [40] |
|---|---|---|---|
| Proof Size (256-bit) | ~800 bytes | 1–1.5 KB | 1–2 KB |
| Proof Generation Time | Fast (preprocessing required) | Slightly slower than Groth16 | Slower than both Groth16 and PLONK |
| Proof Verification Time | Extremely fast (constant time) | Fast (slightly slower than Groth16) | Slow (linear in witness size) |
| Trusted Setup | Required (circuit-specific) | Required (universal) | No trusted setup |
| Use Cases | Blockchain-based authentication | Blockchain rollups | Confidential transactions (e.g., Monero) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Y.; Matsubara, Y.; Kasahara, S. Enhancing Account Information Anonymity in Blockchain-Based IoT Access Control Using Zero-Knowledge Proofs. Electronics 2025, 14, 2772. https://doi.org/10.3390/electronics14142772
Wu Y, Matsubara Y, Kasahara S. Enhancing Account Information Anonymity in Blockchain-Based IoT Access Control Using Zero-Knowledge Proofs. Electronics. 2025; 14(14):2772. https://doi.org/10.3390/electronics14142772
Chicago/Turabian StyleWu, Yuxiao, Yutaka Matsubara, and Shoji Kasahara. 2025. "Enhancing Account Information Anonymity in Blockchain-Based IoT Access Control Using Zero-Knowledge Proofs" Electronics 14, no. 14: 2772. https://doi.org/10.3390/electronics14142772
APA StyleWu, Y., Matsubara, Y., & Kasahara, S. (2025). Enhancing Account Information Anonymity in Blockchain-Based IoT Access Control Using Zero-Knowledge Proofs. Electronics, 14(14), 2772. https://doi.org/10.3390/electronics14142772







