1. Introduction
The rapid digitalisation of healthcare has significantly transformed service delivery and data management, presenting substantial opportunities for efficiency and innovation. However, these innovations have also introduced complex risks related to data protection, privacy, and cybersecurity [
1,
2,
3,
4]. The extensive generation of sensitive health data, along with its potential exposure to cyber threats, has rendered data security an indispensable priority for healthcare organisations across the globe [
5,
6,
7,
8]. As sensitive health data is increasingly stored and transmitted electronically, healthcare organisations face mounting threats from cybercrime, regulatory non-compliance, and governance deficiencies that have led to financial losses, reputational damage, and disruptions to clinical services [
1,
9,
10,
11,
12,
13].
Despite the proliferation of legal frameworks and technological safeguards, the healthcare sector continues to experience frequent data breaches. These persistent failures often result from fragmented, reactive approaches that fail to address the systemic nature of data governance [
5,
12,
14,
15,
16,
17]. Regulatory frameworks such as the EU’s General Data Protection Regulation (GDPR), the U.S. HIPAA, and WHO’s data protection principles emphasise fairness, transparency, and accountability [
3,
4]. Yet, research shows that compliance across healthcare systems remains inconsistent, particularly in Africa, Asia, and even among G7 nations due to varying levels of awareness, institutional maturity, and workforce experience [
12,
18,
19,
20].
The global significance of data protection was underscored during the G20 Leaders’ Summit in Japan in June 2019, where leaders recognised data as a fundamental enabler of economic growth and societal well-being [
1,
18,
19,
21,
22]. Although digitalisation fosters innovation and inclusivity, it also introduces complex challenges related to privacy, security, and compliance [
2,
17,
18,
23]. However, sustainable implementation of data protection remains elusive. Practical experience, tenure, and organisational culture often have greater influence on compliance behaviour than academic knowledge or technical regulation alone [
2,
17,
18,
23]. Many existing frameworks overlook these contextual dynamics, treating cybersecurity, governance, and compliance in isolation rather than as interdependent components of a cohesive system [
1,
18,
19,
21,
22].
This study identifies recurring challenges related to data protection, privacy, and cybersecurity within digital health systems [
1,
9,
10,
11,
12]. It further explores effective strategies for safeguarding patient data without compromising accessibility for authorised users, aiming to achieve a balance between data security and operational efficiency [
24,
25,
26]. While some frameworks attempt to address these dynamics, they rarely consider organisational and contextual factors comprehensively. This paper aims to improve the understanding of compliance within digital health ecosystems [
12,
18,
19,
20].
In response, this study proposes a novel, integrated framework for digital health data protection, structured around six critical pillars: technology, policy, cybersecurity, legal compliance, governance, and risk assessment [
14,
15,
23,
27,
28,
29]. Although frameworks like the GDPR, HIPAA, and NHS DSP Toolkit exist, most lack the flexibility, contextual adaptability, and integrated validation needed for real-world implementation. The proposed framework responds to these limitations by offering a harmonised model rooted in engineering design principles and empirical analysis. This study presents actionable strategies for safeguarding sensitive health information and aligning organisational practices with global standards to create resilient healthcare systems by examining the intersection of governance, cybersecurity, and data protection compliance. It emphasises the importance of maintaining data accessibility for authorised stakeholders while navigating the complexities of managing digital health data effectively [
14,
15,
23,
27,
28,
29].
The core objective of this paper is to quantitatively clarify the causal relationships between components of the proposed framework—such as how organisational governance and cybersecurity practices impact data protection compliance—and to verify its structural validity using empirical engineering methods. These include exploratory factor analysis (EFA) and Partial Least Squares Structural Equation Modelling (PLS-SEM), applied to data collected through a structured survey of healthcare professionals [
28,
29,
30,
31].
The key findings and contributions of this work are as follows:
It offers a robust, interdisciplinary framework that unifies fragmented dimensions of digital data protection into a measurable, scalable model.
It provides actionable strategies for policymakers to align regulations, organisations to prioritise governance and cybersecurity, and researchers to advance secure, compliant digital health systems through practical applications.
It presents a robust digital health data protection framework built on six pillars: technology, cybersecurity, governance, policy, legislation, and risk assessment.
It extends discourse on digital health data governance by integrating socio-technical theory with engineering-based empirical validation, thereby contributing to the fields of information systems, industrial engineering, electronic governance, and health informatics.
The novelty of this research lies in the fact that, unlike existing piecemeal or compliance-centric models, it designs and proposes a systematic and measurable data protection framework that integrates six critical pillars and is empirically validated using engineering-based methods. This unified socio-technical approach addresses the persistent fragmentation seen in current practices, especially within resource-constrained or highly heterogeneous healthcare settings [
14,
15,
23,
27,
28,
29].
Ultimately, this study contributes to the broader disciplines of electronics, information systems, and industrial engineering by combining systems thinking, statistical modelling, and socio-technical integration to address a high-stakes, real-world problem. It reinforces the need for data protection frameworks that are not only theoretically sound but also practically actionable, especially in increasingly digitised and regulation-heavy environments [
15,
23,
28,
29].
2. Related Work
The digital revolution has fundamentally transformed global industries, ushering in unprecedented opportunities for economic growth, healthcare innovation, and cultural advancement. However, it has also brought about significant challenges, particularly in the management of sensitive health data within increasingly complex healthcare systems [
22,
32,
33]. According to Coughlin et al., the healthcare data sector is expected to experience a remarkable 36% compound annual growth rate (CAGR) by 2025, far exceeding growth in other industries. This exponential data growth underscores the urgency for robust data protection strategies [
22,
34,
35]. In recognition of these challenges, various regulatory and operational frameworks have emerged. The UK’s National Health Service (NHS) has instituted the Good Practice Guidelines Framework for General Practitioner (GP) Electronic Patient Records. These guidelines prioritise ethical and secure patient information management, ensuring that sensitive data is handled with the utmost care and integrity [
15].
In July 2023, the United States and the European Union launched the Data Privacy Framework (DPF), a comprehensive initiative designed to facilitate secure and trustworthy cross-border data transfers while adhering to the stringent requirements of the General Data Protection Regulation (GDPR). This framework mandates that organisations demonstrate their commitment to key data protection principles, fostering transparency and accountability for patients, who deserve to understand how their data is being used and shared [
5]. Innovative technical frameworks like PERSONA are redefining privacy by employing advanced automated access control rules, which significantly enhance the enforcement of privacy policies and reduce potential risks [
6]. Additionally, the Enterprise Data Management Framework (EDM) plays a crucial role in promoting data usability and compliance, focusing on the essential “4 Ps” of data privacy: places, people, platforms, and purposes. This holistic approach ensures that data privacy is woven into every aspect of data handling [
7].
Despite these advancements, the growing complexity of digital health ecosystems has exposed significant limitations in current frameworks. Models such as the NHS Data Security and Protection Toolkit, GDPR, and HIPAA offer important legal and ethical benchmarks, yet many lack mechanisms for empirical validation or adaptability across varied healthcare contexts. Others, like the DPF, PERSONA, and EDM, while conceptually strong, often remain fragmented or limited in practical implementation, especially in resource-constrained settings. Furthermore, socio-technical theories such as the Diffusion of Innovation (DoI) and socio-technical systems theory emphasise the importance of human-technical interaction in the adoption of digital health solutions. While insightful, these theories rarely translate into integrated, engineering-validated frameworks capable of guiding real-world operations [
10,
11,
19,
22].
Given the critical nature of healthcare data security amidst rising threats of exploitation and cybersecurity breaches, this investigation emphasises the urgent need for robust protective measures. This study identifies a persistent gap in global health data governance: the absence of empirically tested, context-sensitive, and operationally integrated frameworks. Addressing this gap, this research proposes a novel, six-pillar data protection framework encompassing technology, cybersecurity, governance, policy, legislation, and risk assessment. This integrated model aims to unify technical and regulatory perspectives while incorporating organisational dynamics such as compliance culture and contextual awareness [
18,
19,
20,
26]. Particularly relevant in both developing regions and advanced economies, including G7 nations, is the continued low awareness of data protection requirements, compounded by inconsistent enforcement and fragmented practices. This research seeks to advance our understanding of how institutional governance interacts with cybersecurity practices to drive compliance. The findings offer actionable strategies for stakeholders, from policymakers and IT leaders to healthcare administrators, enabling the creation of secure, ethical, and resilient digital health systems [
10,
11,
19,
22].
2.1. Case Study Failures and Framework Gaps
The rising incidence of data breaches within the healthcare sector represents a critical and escalating challenge, threatening not only the confidentiality of sensitive patient information but also the foundational trust between patients and healthcare providers. The expanding reliance on digital health technologies such as electronic health records (EHRs), telemedicine platforms, mobile health applications, and wearable devices has led to an exponential increase in the volume of personal health data that is generated, stored, and transmitted electronically. This data is particularly attractive to cybercriminals and consequently, healthcare organisations have become prime targets for cyberattacks, with data breaches resulting in identity theft, financial fraud, and disruptions to patient care. Therefore, understanding the underlying causes and implications associated with such breaches is essential to protecting patient data and maintaining the operational resilience of health systems [
11,
18,
19,
26].
Several high-profile incidents illustrate the severity and systemic nature of this threat. The 2015 breach at Anthem Inc. exposed the data of 79 million individuals due to phishing and weak security controls, while the 2017 NHS WannaCry ransomware attack triggered by unpatched software and fragmented governance disrupted over 80 hospital trusts. Similarly, Singapore’s 2018 SingHealth breach and the 2019 AMCA breach in the U.S. revealed vulnerabilities linked to weak authentication and third-party vendor risks, respectively. Beyond financial and operational impacts, such breaches erode patient trust and raise ethical concerns. For instance, the 2020 ransomware attack on the NHS delayed critical care and surgeries, directly affecting outcomes and weakening patient–provider relationships. A lack of trust may lead individuals to withhold important health information, ultimately impairing care quality and institutional credibility [
18,
19,
26,
36].
According to the U.S. Department of Health & Human Services (HHS), health data breaches tracked in 2023 affected about 184,000 records on average, with eight healthcare data breaches affecting more than 4 million records each. The tracked data also indicates that in the same year, the largest healthcare data breach impacted more than 11 million records. For 11 consecutive years, the healthcare industry has consistently faced the most expensive data exploitation compared to other sectors. In the United States, health data exploitations cost an average of USD 9.23 million in 2021 alone. Furthermore, patient information violations have seen an average surge in cost of about 30% from 2020 to 2021 [
36].
While countries like Estonia have achieved success through robust digital identity and e-governance systems, these models are resource-intensive and often unsuitable for less-resourced settings. These contrasts reveal a persistent gap in the global data protection strategy—a lack of empirically and unified frameworks that can guide healthcare institutions in implementing measurable and sustainable data protection strategies which can be adapted across diverse healthcare environments. This study responds to that gap by proposing an integrated framework, developed through engineering methodologies, to support secure, scalable, and compliant digital health systems. As digitisation accelerates, proactive strategies for preventing and managing data breaches will be essential to protecting personal health data and upholding the integrity of healthcare delivery [
18,
19,
20,
26].
2.2. Key Theories and Models for Digital Health Data Protection
The proposed framework seeks to clarify the interplay among organisational governance, cybersecurity practices, and data protection compliance to establish effective digital health data management requirements. The theory of change for digital health data protection provides a model that outlines the essential resources, activities, outputs, outcomes, and long-term impacts necessary for creating a secure and compliant digital health data environment [
13,
37].
This framework is particularly relevant for health organisations navigating regulatory requirements such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). By mapping these components, organisations can identify, monitor, and optimise resources and processes to enhance compliance, strengthen data security, and build stakeholder trust [
33,
35].
In light of the complexity of health systems, several additional theories offer insights into digital health data protection:
Diffusion of Innovations theory: Explored by Rogers (2003) [
27], this theory examines how innovations spread within communities and inform the implementation of digital health systems [
7].
Socio-technical systems (STSs) theory highlights the interactions between healthcare technologies and organisational structures, offering a framework for understanding how technological and human factors influence data protection [
38].
Privacy by Design (PbD): This principle emphasises the integration of privacy measures into technological and organisational processes, fostering regulatory compliance and user trust while addressing ethical implications [
16].
Compliance Theory: This theory emphasises the relationship between legal obligations and organisational culture, providing insights into how health organisations implement data protection regulations [
39].
Data Governance Frameworks: These frameworks are vital for responsible health data management, promoting accuracy, accessibility, security, and compliance with legal standards [
40].
By integrating these theoretical perspectives, health organisations can develop a more effective digital health data protection approach, ensuring compliance and safeguarding sensitive health information.
3. Materials and Methods
This research explores the interrelationships among governance, cybersecurity practices, and compliance, providing actionable insights for healthcare stakeholders. More specifically, this study is carried out with regard to the following research questions:
What are the primary factors influencing digital health data protection compliance?
How do organisational governance and cybersecurity practices impact compliance with data protection regulations?
How can these insights inform a framework to enhance data protection in healthcare?
3.1. Survey Research Design and Data Collection Approach
This study employed a quantitative research design methodology to collect data from various healthcare professionals and provide insights into data protection in the healthcare industry from this data. It utilised a structured electronic questionnaire administered through Microsoft Forms to collect essential data across several key dimensions [
18,
29]:
Technology and Cybersecurity Practices: This dimension assessed the infrastructure and protocols established to ensure data security.
Data Protection Legislation and Policies: This section evaluated participants’ awareness and adherence to legal frameworks and internal policies.
Digital Health Data Governance and Risk Assessment explored governance structures, risk assessment strategies, and overall organisational readiness for managing potential data breaches.
The questionnaire also captured demographic information and assessed participants’ attitudes toward digital health data security, privacy, and compliance [
17,
18,
41]. This study employed a stratified random sampling method to ensure diverse representation, taking into consideration variations in education level, profession, and geographic location. The research drew upon extensive advisory networks established to enhance health systems in sub-national governments across Nigeria and various global regions, engaging coordinators of professional healthcare practitioners’ platforms to facilitate the effective distribution of questionnaires [
18].
The healthcare professionals selected for this study were deliberately chosen due to their crucial roles in advancing digital health data protection within the healthcare sector. Participants were required to be practising healthcare professionals currently employed in a healthcare facility or organisation, ensuring their relevance to the study [
18].
The survey utilised a 5-point Likert scale to evaluate perceptions of digital health data protection, administered across seven countries—Nigeria, Liberia, Ghana, Algeria, the United Kingdom, the United States, and Canada. However, responses were only collected from Nigeria, Algeria, the United Kingdom, the United States, and Canada, with no feedback received from Ghana or Liberia—resulting in a response rate of 67.3% (101 out of 150). Participants were not compensated for their involvement, ensuring an unbiased representation of insights. This approach provided valuable perspectives on digital health data protection, organisational governance, and cybersecurity management practices across diverse healthcare settings.
3.2. Data Preparation
The dataset underwent a meticulous preprocessing stage to eliminate irrelevant metadata and non-Likert-scale responses, thereby improving the quality of the analysis. Subsequently, exploratory factor analysis (EFA) was performed, revealing three primary latent constructs of organisation governance, cybersecurity practices and data protection compliance inherent in the data [
13,
22,
32,
34,
42].
Table 1 below provides a structured overview of various constructs across key domains as contained in the survey form, including technology, cybersecurity, policy, data protection legislation, digital health data governance, and risk assessment. It highlights second-order constructs such as Cybersecurity Practices (CPs), Data Protection Compliance (DPC), and Organisational Governance (OG) and demonstrates their interrelationships [
3,
7,
43]. Furthermore, the table outlines the number of items or questions relevant to each construct, reflecting a thorough approach to evaluating these critical areas.
Organisational Governance in Health and Risk Management: This construct examines the frameworks and policies that inform decision-making processes within health organisations, particularly regarding effective risk management strategies.
Cybersecurity Practices and Protocols: This construct addresses the systematic approaches and measures organisations implement to protect their digital assets and information from cybersecurity threats.
Data Protection Compliance: This construct focuses on organisations’ adherence to applicable laws and regulations governing data protection and privacy, ensuring the appropriate handling of sensitive information.
The collected data was securely stored and handled in strict accordance with privacy regulations and ethical guidelines throughout the research process. This study, through the utilisation of an electronic questionnaire, aims to provide valuable insights into the public discourse surrounding digital health and compliance issues [
18,
32,
34,
44]. By understanding the factors that shape individual attitudes, policymakers and stakeholders can formulate targeted strategies to promote best practices in digital health data protection and address barriers to widespread acceptance. The findings of this study are expected to play a pivotal role in shaping future initiatives aimed at effectively managing digital health and associated compliance challenges [
18,
44].
3.3. Analytical Methodology
Numerous studies utilising survey data and related datasets have employed advanced analytical methods to derive meaningful insights. This study integrates various analytical techniques to explore the relationships among six key constructs: technology, cybersecurity, data protection legislation, digital health data governance, and risk assessment.
The methodological approach began with exploratory factor analysis (EFA) to identify latent structures within the dataset. We used Principal Axis Factoring (PAF) as the extraction method to prioritise shared variance among the items and applied an orthogonal (Varimax) rotation to enhance interpretability and clarity.
Following the EFA, Partial Least Squares Structural Equation Modelling (PLS-SEM) was employed as the primary analytical tool to investigate the interconnections among the constructs. PLS-SEM is particularly suitable for survey-based research, especially in contexts with developing theoretical frameworks. This robust method facilitates modelling complex relationships, including direct, indirect, and moderating effects, while maximising the explained variance in dependent variables. Furthermore, PLS-SEM effectively accommodates both reflective and formative measurement models, accurately representing constructs such as organisational governance, cybersecurity practices, and data protection compliance [
22,
23,
40].
Integrating EFA and PLS-SEM underscores the study’s multidisciplinary approach, facilitating a comprehensive analysis of the interplay between organisational governance, cybersecurity, and compliance. This combined approach provides a powerful mechanism for generating actionable insights and empirically validating the structural relationships within the digital health and data protection domain. These techniques’ methodological rigour and adaptability contribute to a deeper understanding of the complex dynamics in this field, thereby advancing theoretical and practical knowledge [
22,
23,
38,
40].
Factors were retained based on two principal criteria:
This thorough methodology ensured the accurate mapping of survey items to the identified constructs, reinforcing the findings’ validity and reliability.
3.4. Model Representation
Factor analysis assumes that the observed variables (X) are linear combinations of underlying latent factors F and unique error terms E:
where
X: Matrix of observed variables (dimension: p × n).
A: Factor loadings matrix (dimension: p × k, where k is the number of factors).
F: Matrix of latent factors (dimension: k × n).
E: Error or uniqueness matrix (dimension: p × n).
The equation X = AF + E serves as a model for analysing critical factors such as technology, cybersecurity, policy, data protection legislation, digital health data governance, and risk assessment. In this model, X represents the matrix of observed variables (p × n), which are expressed as linear combinations of latent factors F (k × n) and unique error terms E (p × n ). The factor loadings matrix A (p × k, where k is the number of latent factors) captures the relationships between the observed variables and the latent factors. This analytical approach facilitates an evaluation of how key factors interact and are influenced by external conditions, providing valuable insights into the system’s overall performance, compliance, and risk dynamics.
3.5. Measurement Model Analysis
The measurement model was evaluated through the examination of factor loadings and reliability. The factor analysis indicated a distinct structure comprising three factors: organisational governance, cybersecurity practices, and data protection compliance. This structure was supported by reliability analysis based on Cronbach’s alpha, which confirmed these factors as consistent measures of their respective constructs.
In PLS-SEM, the measurement model relates observed variables (X) to their latent variables (ξ)
3.6. Structural Model Analysis
The structural model was designed to evaluate the influence of Organisational Governance and Cybersecurity Practices on Data Protection Compliance. Path coefficients were estimated through linear regression, while bootstrapping techniques were used to compute 95% confidence intervals for each path, ensuring robust results [
18,
32,
34,
44].
Complemented by descriptive statistics, the quantitative analysis provided insights into the participants’ demographics and general trends following the data collection phase. This comprehensive approach captures a broad range of opinions, thus facilitating a more in-depth analysis of public perceptions. Inferential statistical analysis was employed to identify significant factors influencing digital health data protection compliance [
18,
32,
34,
44].
3.7. Model Validation and Structural Dynamics
Partial Least Squares Structural Equation Modelling (PLS-SEM) was employed to rigorously validate the measurement model and assess the hypothesised relationships between constructs within the structural model. This advanced methodology allowed for a detailed examination of the interconnectedness among constructs, offering valuable insights into their predictive relationships and the overall dynamics of the structural model [
18,
32,
34,
44].
This methodological rigour ensures that the findings contribute significantly to understanding factors influencing digital health data protection compliance, laying a foundation for future research and policy development [
18,
32,
34,
44].
4. Results
Digital health involves the integration of health-related data, including patient-generated information, with the use of advanced technological tools to unlock medical potential [
44,
45,
46]. A central premise of this field is that the capacity to collect, store, and analyse large volumes of health data serves as the main catalyst for advancements in digital health [
17,
41,
47]. Therefore, it is essential to evaluate digital health solutions based on their safety, functionality, quality, data protection, data security, and their overall positive impact on individuals [
45,
48,
49].
This rapidly expanding domain is fundamentally data-driven, with the increasing availability of health data being its defining characteristic rather than the technology itself [
50,
51,
52]. The research focuses on addressing the challenges associated with digital health data protection compliance by leveraging an integrated framework for a comprehensive understanding [
39,
42,
53,
54].
The initial analysis of survey data aligns with the research objectives, which investigate compliance challenges within digital health data protection. These insights are pivotal for developing targeted solutions that ensure the safe, secure, and efficient application of digital health technologies, promoting better healthcare outcomes [
39,
42,
53,
54].
4.1. Demographics
Table 2 illustrates that the respondents have diverse educational backgrounds, professional roles, workplace locations, and years of work experience. This comprehensive analysis provides valuable insights into the profile of the surveyed population [
29,
54,
55].
In terms of educational attainment, the respondents exhibit varied qualifications. A small proportion of respondents, 5%, hold PhD degrees, showcasing the presence of highly specialised individuals within the group. Meanwhile, the largest segment, accounting for 39%, has obtained Master’s degrees, indicating a significant focus on advanced education. Additionally, 45% of respondents possess Bachelor’s degrees or diplomas, demonstrating a solid foundational level of higher education. A minority, representing 1%, have completed secondary school as their highest level of education. These findings underscore the overall high level of educational achievement among the respondents [
29,
54,
55].
The professional distribution further highlights the diversity within the group surveyed. Medicine is the predominant profession, with 32% of respondents engaged in this field. Allied health professions account for the next largest segment, representing 36% of the group, followed by nursing at 24%. Pharmacy professionals constitute 7% of the respondents, while radiography accounts for 1%. This distribution indicates that the majority of respondents work in core healthcare fields, reflecting a strong representation of the healthcare workforce in the study [
29,
54,
55].
When examining workplace locations, the majority of respondents (74) are based in Nigeria, reflecting a strong regional focus. The United Kingdom follows with 21 respondents, while smaller numbers of respondents (4 and 1) are based in the United States and Canada, respectively, with one respondent located in Algeria. This geographic distribution highlights the global nature of the respondent group, with a significant concentration in Africa and representation from Western nations [
29,
54,
55].
Finally, the respondents’ years of work experience demonstrate a wide range of professional expertise. A considerable number, 23 respondents, have 20 or more years of experience, indicating a wealth of expertise within the group. Additionally, 16 respondents have between 15 and 19 years of experience, while 25 have 10 to 14 years. Respondents with 5 to 9 years and less than 5 years of experience constitute 16 and 21 individuals, respectively. This distribution reveals a balanced mix of seasoned professionals and those in the earlier stages of their careers [
29,
37,
54,
55].
Overall, the respondents reflect a diverse and highly qualified group of individuals. Their varied educational achievements, professional roles, workplace locations, and experience levels provide a rich foundation for analysing perspectives within the study. The data emphasises the group’s strong representation in healthcare and highlights their global and professional diversity [
29,
54,
55].
4.2. Demographic Moderation Analysis
To explore the moderating role of professional experience on compliance behaviour, a Multi-Group Analysis (MGA) was conducted within the Partial Least Squares Structural Equation Modelling (PLS-SEM) framework. We evaluated how work experience (categorised by tenure: <5 years, 5–10 years, >10 years) moderated the impact of governance on compliance.
The results revealed that governance exerted a significantly stronger positive influence on compliance among less experienced professionals (path coefficient = 0.61,
p < 0.01) compared to their more experienced counterparts with over 10 years of service (path coefficient = 0.35,
p < 0.05). This suggests that robust institutional governance structures can effectively mitigate knowledge and experience gaps among newer staff members, reinforcing compliance behaviours through clear policies and oversight [
27,
30,
31].
In contrast, the implementation of cybersecurity practices showed a stronger correlation with tenure than with formal academic qualifications. Long-tenured staff demonstrated higher adherence to cybersecurity protocols, likely due to accumulated institutional knowledge, familiarity with internal systems, and repeated exposure to security policies [
27,
31,
56].
Findings indicate that governance has a significantly stronger positive effect on compliance among less experienced staff, suggesting that institutional structures compensate for individual knowledge gaps, while also recognising the role of practical experience in fostering consistent cybersecurity practices. These insights offer critical implications for designing targeted compliance strategies that account for workforce heterogeneity in healthcare environments [
27,
44,
56].
4.3. Factor Analysis
Digital transformation has significantly reshaped society in recent years in ways that were previously unimaginable in the 20th century. This transformation holds the potential to disrupt the healthcare sector by addressing longstanding challenges related to quality, increasing costs, and the provision of value-added services [
41,
46,
49,
57]. The healthcare industry has witnessed considerable advancements, particularly in the digitisation of health data. As the global healthcare sector progresses into the digital age, a primary concern remains the capacity to foster successful innovation within the industry [
17,
32,
34,
43].
In this study, the analysis was performed utilising the factor analysis method. The survey columns were systematically categorised into specific groups for a more structured evaluation according to the following categories [
18]:
Group Mapping of Columns
Technology and Cybersecurity:
Survey columns that relate to infrastructure, security protocols, and cybersecurity practices: Technology_Q1, Technology_Q2, Technology_Q3, Technology_Q4, Technology_Q5 and Cybersecurity_Q1, Cybersecurity_Q2, Cybersecurity_Q3, Cybersecurity_Q4, and Cybersecurity_Q5.
Data Protection Legislation and Policy:
Columns with sentiments around organisational adherence to data protection regulations and internal policy standards were grouped as Data_Protection_Q1, Data_Protection_Q2, Data_Protection_Q3, Data_Protection_Q4, Data_Protection_Q5 and Policy_Q1, Policy_Q2, Policy_Q3, Policy_Q4, and Policy_Q5.
Digital Health Data Governance:
Columns associated with managing and safeguarding health data, including governance structures, processes, risk identification, assessment, and organisational readiness for data-related risks, were grouped as Digital_Health_Governance_Q1, Digital_Health_Governance_Q2,Digital_Health_Governance_Q3,Digital_Health_Governance_Q4,Digital_Health_Governance_Q5,Risk_Assessment_Q1,Risk_Assessment_Q2,Risk_Assessment_Q3,Risk_Assessment_Q4, Risk_Assessment_Q5, Risk_Assessment_Q6, and Risk_Assessment_Q7.
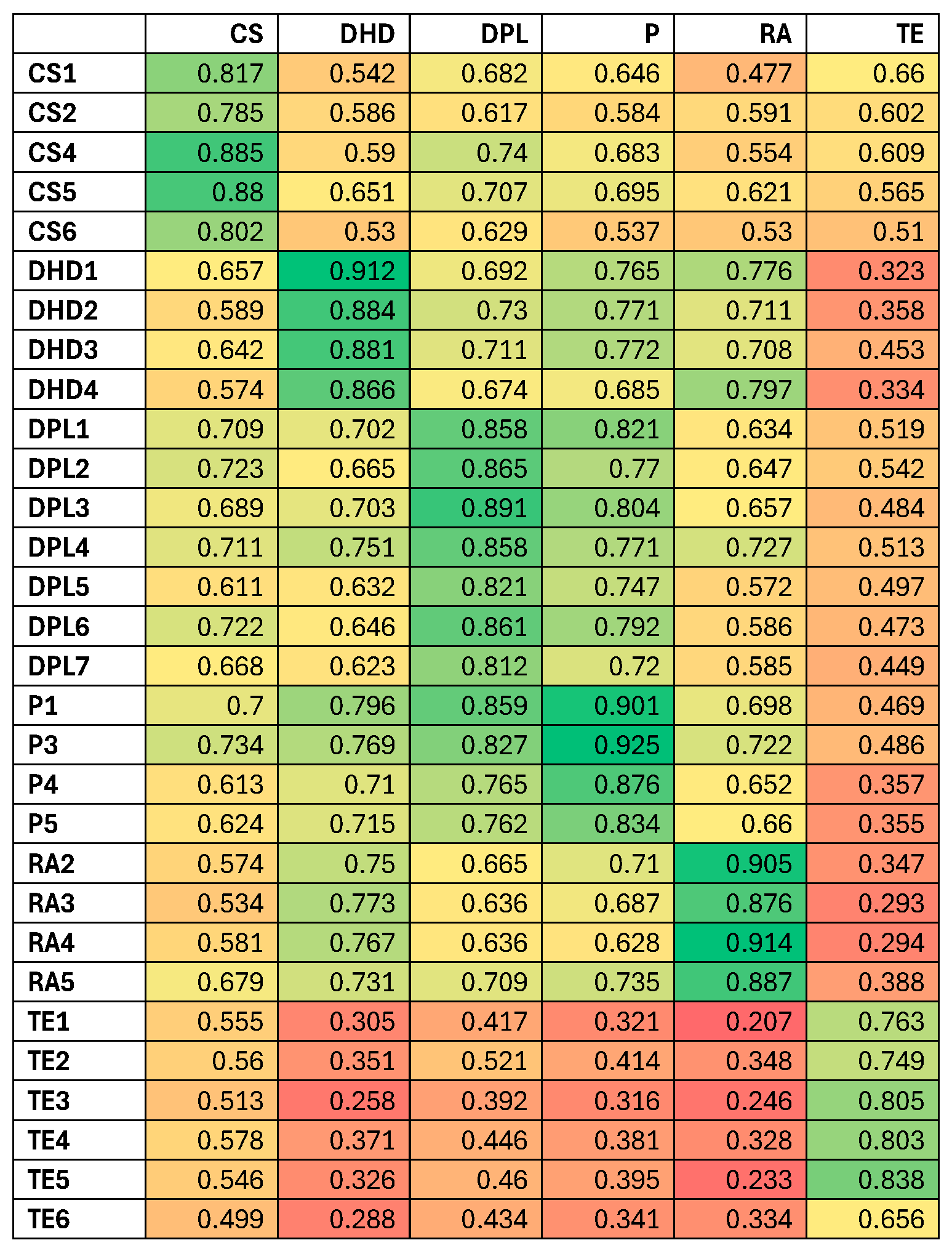
The heatmap diagram in
Figure 1 shows the mapping of all questionnaire items through factor analysis.
This research further employed structural equation modelling (SEM) to identify the factors most significantly influencing Data Protection Compliance. The analysis specifically examined the correlation coefficients (
Table 3 and
Table 4) between compliance and key determinants, namely Organisational Governance and Cybersecurity Practices. The findings from the correlation analysis (
Table 4) revealed the following relationships: Cybersecurity Practices exhibited a correlation of 0.711 with Data Protection Compliance, while Organisational Governance demonstrated a slightly stronger correlation of 0.845 with Data Protection Compliance [
17,
32,
34,
41].
The factor correlation matrix in
Table 3 provides compelling evidence that digital platforms and technologies have positively impacted health data management. This finding reflects a widespread recognition of the advantages associated with digital transformation within the healthcare sector [
17,
18,
41,
43,
47].
4.4. Structural Model Analysis
Data protection is a dynamic field that is continuously shaped by advancements in digital technologies and evolving business practices. Globally recognised as a fundamental human right, privacy is intrinsically linked to the obligation to safeguard individuals’ personal lives. Implementing effective data protection measures is crucial for ensuring the confidentiality of personal information throughout its entire lifecycle, thereby upholding both the right to privacy and the right to data protection [
12,
32,
34,
58].
In today’s digital age, the concept of privacy has expanded to encompass “e-privacy,” which refers to privacy concerns within the digital environment as articulated by the General Data Protection Regulation (GDPR) [
27,
40,
56,
59,
60].
To evaluate the factors influencing compliance with data protection standards, a structural model was developed to assess the impact of Organisational Governance and Cybersecurity Practices. Path coefficients were estimated utilising linear regression analysis, and bootstrapping techniques were employed to calculate 95% confidence intervals for each path [
18,
27,
56,
59,
60]. The resulting path coefficients, along with their corresponding confidence intervals, are presented as follows:
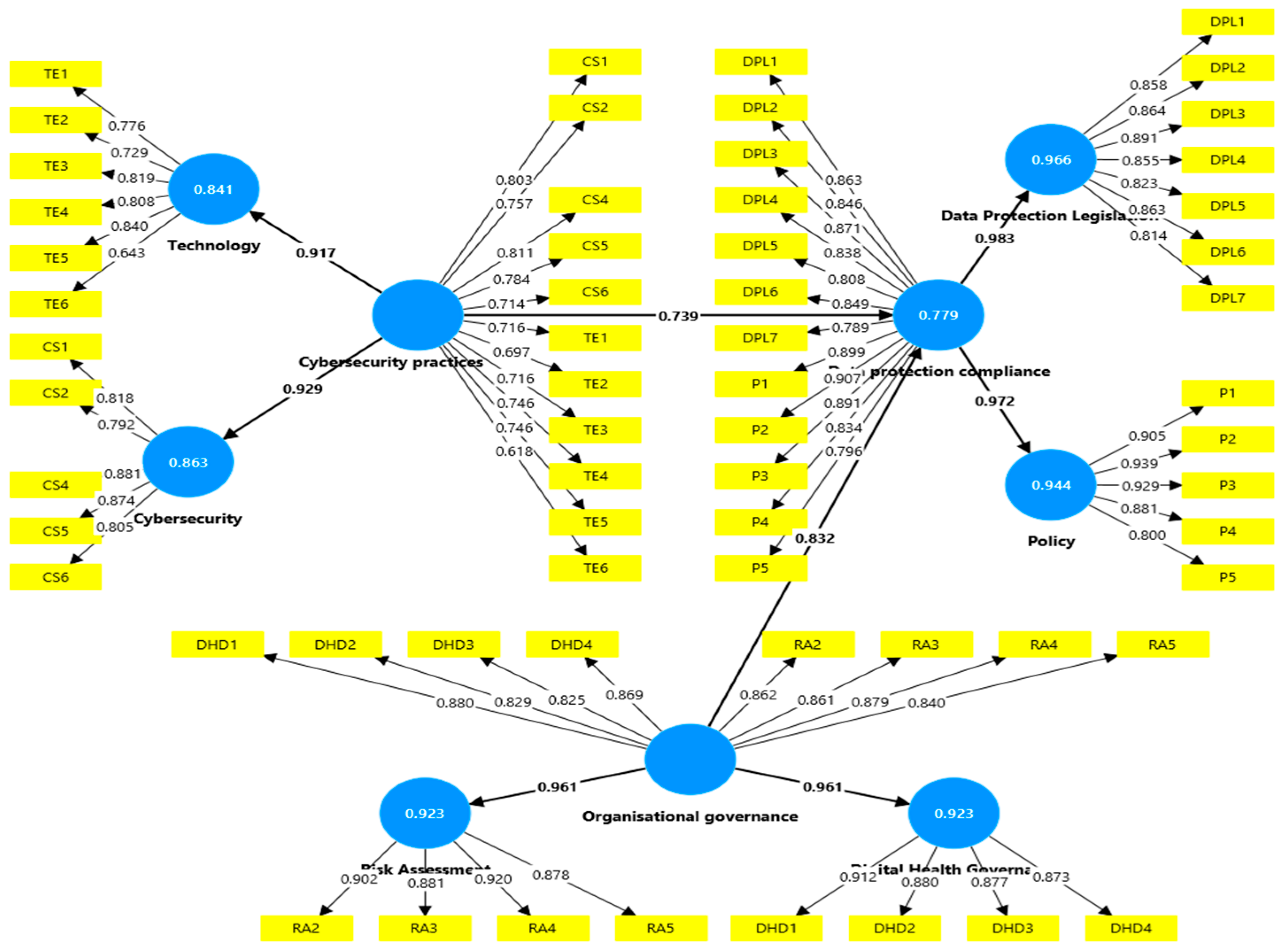
Organisational governance → Data Protection Compliance (Coefficient: 0.832,95% Confidence).
Cybersecurity Practices → Data Protection Compliance (Coefficient: 0.739,95% Confidence).
Figure 2 above presents a path diagram illustrating the hypothesised relationships among the Organisational Governance, Cybersecurity Practices, and Data Protection Compliance constructs. The arrows within the diagram indicate the direction of influence among these constructs, while the accompanying labels represent the strength of each relationship, quantified as path coefficients derived from the structural equation modelling (SEM) conducted for this analysis [
18].
Furthermore,
Figure 2 emphasises responses indicating that organisations acknowledge and comprehend the significance of data protection legislation. These responses suggest that achieving compliance is regarded as a top priority and serves as a critical foundation for the establishment of a robust framework for the protection of digital health data [
34,
42,
45,
61].
4.5. Organisational Governance to Data Protection Compliance
In today’s fast-paced business environment, one of the most critical lessons is the inevitability of the unexpected. Organisations must incorporate this unpredictability into their strategic planning. Decision-makers face a multitude of challenges, ranging from market fluctuations and technological advancements to evolving regulatory frameworks. This raises a critical question: how can organisations prepare for unforeseen or unknown challenges? In the complex and ever-changing healthcare landscape, risk awareness and risk-based thinking have emerged as indispensable leadership skills [
17,
22,
32,
55,
62,
63].
A 2022 study by the Project Management Institute found that organisations with a well-established risk management culture are significantly more likely to achieve project success [
13,
32,
53,
61]. Similarly, a
Harvard Business Review article emphasised that companies that embrace a risk-based decision-making approach are better positioned to adapt to change [
13,
22,
42,
53]. One practical approach is integrating risk analysis into the decision-making process, a critical step in light of the ongoing digital transformation in the healthcare sector [
22,
42,
53,
61].
This perspective aligns with the concept that robust organisational governance positively impacts data protection compliance. Governance involves creating and implementing policies, accountability frameworks, and risk assessment practices essential for adhering to data protection regulations and standards. Within digital healthcare, governance structures prioritising data privacy and security play a pivotal role in ensuring compliance with data protection legislation. A path coefficient of 0.832, as depicted in
Figure 2, reflects a moderate-to-strong influence, indicating that strengthening governance practices can significantly enhance compliance outcomes [
32,
42,
53,
61,
64,
65].
4.6. Cybersecurity Practices to Data Protection Compliance
Data security has emerged as a critical priority for organisations, relying not only on an organisation’s internal defences but also on the shared responsibility of all stakeholders involved in the digital health data protection ecosystem. This is especially important, given the varying access levels that different stakeholders possess regarding sensitive patient information [
13,
19,
21,
42]. A significant challenge is presented by Bring Your Own Device (BYOD) policies, which permit employees to utilise personal devices for professional purposes. While these policies offer convenience, they also introduce significant data security risks, including data leakage, exposure to malicious applications, and challenges in managing device security [
13,
18,
21,
22,
61,
66]. The scope of BYOD encompasses personal devices such as tablets, smartphones, USB drives, and personal computers that employees utilise to access organisational systems and sensitive data.
Research indicates that over 50% of organisations and more than 70% of employees currently use personal devices for work-related tasks, a rapidly increasing trend [
57]. Consequently, the security of BYOD environments has become a foremost concern for IT and security leaders [
13,
15,
18,
19,
28,
42].
This context underscores the essential role of cybersecurity in achieving compliance with data protection standards. Key cybersecurity practices, including robust data encryption, stringent access controls, and proactive threat monitoring, establish the fundamental framework for protecting sensitive health data from unauthorised access and breaches. The path coefficient of 0.739 demonstrates the substantial impact of strong cybersecurity measures on an organisation’s capacity to adhere to data protection requirements. In practical terms, enhancing cybersecurity protocols can significantly and directly improve an organisation’s compliance posture [
13,
15,
47,
51,
57].
4.7. Organisational Governance to Cybersecurity Practices
This intermediary relationship underscores the critical importance of effective governance frameworks in strengthening an organisation’s cybersecurity practices. Governance is a foundational element, establishing comprehensive policies, ensuring appropriate oversight, and allocating the resources necessary to consistently implement and maintain robust security measures. It prioritises data security and fosters a culture where cybersecurity practices are seamlessly integrated into the organisation’s daily operations [
13,
49,
51,
57].
The path coefficient indicates a moderate influence, suggesting that effective governance can indirectly bolster compliance by fostering robust and proactive cybersecurity initiatives. This dynamic illustrates how strategic governance not only shapes the direction of security initiatives but also creates an environment where cybersecurity becomes an intrinsic aspect of the organisation’s ethos [
13,
49,
51,
57].
4.8. Evaluating R2 and Q2 Values and Their Implications for Cybersecurity and Compliance
The analysis examines the R
2 and Q
2 values depicted in
Figure 3 and
Figure 4, providing insights into the variance of endogenous constructs as influenced by exogenous variables, with specific emphasis on Cybersecurity Practices and Data Protection Compliance. The R
2 value for Cybersecurity Practices signifies moderate explanatory power, indicating that a percentage of the variance can be attributed to Organisational Governance. This finding suggests that while governance is vital, it is essential to consider additional elements such as technology, employee training, and organisational culture to comprehensively understand the factors that impact cybersecurity.
Conversely, Data Protection Compliance presents a higher R
2 value of 0.785, indicating strong predictive relevance. This indicates that the combined effects of Organisational Governance and Cybersecurity Practices can explain 78.5% of the variance in compliance outcomes. These results underscore the pivotal roles that these two constructs play in achieving adherence to legal and regulatory requirements, consistent with established theoretical expectations [
13,
22,
23,
32,
42,
65].
The structural model further highlights the causal pathways between these constructs. Organisational Governance directly affects Cybersecurity Practices, suggesting that enhancements in governance yield improved cybersecurity measures. Subsequently, improved cybersecurity significantly impacts Data Protection Compliance, emphasising the interconnected nature of governance, cybersecurity, and compliance in strengthening an organisation’s regulatory posture [
13,
32,
49,
67].
The accompanying bar chart visually represents these constructs’ Predictive Relevance (Q
2 values). Organisational Governance exhibits excellent predictive relevance, while Cybersecurity Practices and Data Protection Compliance reveal moderate and strong (Q
2 = 0.746) predictive relevance, respectively. Collectively, these findings illustrate the varying degrees of influence exerted by these constructs, with governance and compliance demonstrating greater predictive strength than cybersecurity alone [
13,
32,
49,
67].
5. Discussion
The survey findings emphasise the urgent need for a strong compliance framework to protect digital health data. Such a framework would offer practical guidance for implementing compliance models across various healthcare settings. It would be designed to accommodate diverse organisational sizes, levels of technological maturity, and regulatory contexts. The objective is not merely for organisations to manage data security but to guide them in adopting best practices in health data protection, ensuring compliance with all applicable data protection regulations, including national laws, international standards, and GDPR [
18,
34,
40,
55,
59,
68].
These insights emphasise the inherent interconnectedness of governance, cybersecurity, and compliance in managing digital health. Effective governance plays a critical role in influencing compliance and strengthening cybersecurity practices, which, in turn, reinforces compliance outcomes. The findings suggest that organisations should embrace a holistic approach, wherein governance frameworks actively support cybersecurity initiatives, thereby collectively contributing to the achievement and sustainability of data protection standards [
34,
40,
55,
59].
5.1. Strengthening Governance to Foster Effective Compliance
Integrating digital technologies entails embedding digital solutions throughout an organisation’s operations and strategies. This integration seeks to streamline processes, enhance efficiency, and create new opportunities [
17,
45,
46]. Recognising the positive impact of digital technologies on health data management, the proposed framework will investigate how these tools can be leveraged to improve operational efficiency and strengthen data protection. This includes recommendations for healthcare organisations to adopt or develop technologies that incorporate built-in privacy and security features, which can lead to cost reductions, increased operational efficiency, enhanced competitiveness, and improved productivity [
43,
47,
48].
The integration of digital technologies has greatly transformed the healthcare sector, significantly enhancing data management capabilities and leading to improved patient outcomes. As we embrace this rapid digitisation of health data, developing and implementing strong governance and risk management frameworks is vital.
These measures will help mitigate cybersecurity risks and ensure adherence to regulatory requirements, such as the General Data Protection Regulation (GDPR), ultimately fostering a safer and more efficient healthcare environment. In healthcare, digital transformation requires governance structures equipped to address the complexities associated with data security and privacy [
43,
47,
48].
Such governance frameworks are a critical foundation for implementing effective cybersecurity protocols and ensuring adherence to regulatory standards. Structures that prioritise risk assessment, accountability, and compliance are essential for fostering effective data protection practices. Organisational governance is pivotal in shaping cybersecurity initiatives and achieving compliance outcomes. Consequently, it is essential to establish comprehensive policies, clear accountability mechanisms, and robust risk assessment frameworks to cultivate a secure and resilient digital health ecosystem [
17,
45,
46].
5.2. Cybersecurity Challenges and BYOD Policies in Digital Health
To enhance Bring Your Own Device (BYOD) and risk management policies, organisations must implement targeted measures to strengthen security and mitigate potential threats. BYOD practices present unique challenges; however, these challenges can be effectively addressed by integrating specific guidelines and best practices into a comprehensive framework. Such a framework ensures clarity in expectations, consistency in implementation, and a cohesive approach to minimising risks while maximising operational efficiency. By adopting deliberate strategies, organisations can safeguard their systems and sensitive data, particularly within sectors such as healthcare, where confidentiality is critical [
13,
28,
53,
61].
A robust BYOD policy should explicitly outline acceptable use, security protocols, and employee responsibilities regarding the use of personal devices in the workplace. This policy establishes clear boundaries and expectations, ensuring all stakeholders comprehend their roles in maintaining security. Regular updates to all devices, including personal devices, are essential to mitigate vulnerabilities and protect against emerging cyber threats. Keeping devices up to date with the latest security patches ensures that known vulnerabilities are promptly addressed, thereby reducing the likelihood of successful cyberattacks [
13,
28,
43,
46,
61,
69].
In addition to technical measures, educating employees through regular training and awareness programs is crucial. Such initiatives help employees understand the risks associated with BYOD practices, enabling them to effectively identify and report security threats. This training fosters a culture of vigilance and shared responsibility, which is essential in environments where personal devices interface with organisational systems. Regular training sessions also provide opportunities to update employees on new threats and evolving best practices, ensuring preparedness [
13,
28,
43,
46,
61].
Developing a thorough incident response plan is another critical component of a BYOD framework. This plan should detail specific actions for addressing security incidents involving personal devices, ensuring prompt and coordinated responses. A well-defined incident response strategy minimises the impact of breaches and enables organisations to recover quickly. Furthermore, conducting regular audits and compliance checks is necessary to evaluate the effectiveness of BYOD policies and ensure alignment with regulatory standards and industry norms [
13,
28,
53,
61,
70].
In the context of digital health systems, implementing and maintaining rigorous BYOD policies is especially important due to the sensitive nature of patient information. The risks associated with data breaches underscore the need for comprehensive guidelines that clearly define acceptable practices for personal device usage in healthcare environments. Organisations can foster a secure digital health ecosystem by conducting regular security audits and providing thorough employee training. These measures not only enhance system security but also protect sensitive health data from potential threats, ensuring trust and compliance in an increasingly complex digital landscape [
13,
28,
53,
61].
5.3. Cybersecurity’s Critical Role in Compliance and Regulatory Adherence
Leveraging compliance with data protection legislation involves utilising regulations and laws that govern personal data protection to further organisational objectives. This approach transcends mere adherence to legal requirements; it fosters a culture of best practices that enhances trust and security in the management of digital health data [
13,
27,
38,
40,
52,
54,
59]. By building a solid foundation of awareness and compliance, organisations can advance toward a proactive framework that encourages strategies that exceed basic compliance, thereby ensuring robust protection of sensitive information while setting higher standards for the industry [
13,
27,
38,
40,
52].
Healthcare organisations, in particular, must prioritise implementing robust data protection strategies to meet their legal obligations and ethical responsibilities. Compliance with data protection legislation guarantees adherence to the law, helps with risk mitigation, enhances the organisation’s reputation, and fosters trust among patients and stakeholders. In an increasingly data-driven environment, such proactive measures are essential for maintaining credibility and ensuring long-term success in the management of digital health information [
27,
38,
40,
52].
Adhering to data protection laws is critical for sustaining trust and safeguarding the confidentiality of patient information. Research indicates that organisations with strong governance structures and extensive cybersecurity measures are significantly more likely to achieve full compliance with these legal requirements. By adopting international standards and aligning with legislative frameworks, healthcare organisations can significantly enhance the credibility and resilience of their digital health systems, thus instilling confidence among users and partners [
27,
38,
40,
52].
Implementing effective cybersecurity practices is fundamental to complying with data protection laws. Strategies including advanced encryption techniques, stringent access control policies, and proactive threat detection mechanisms are essential for protecting sensitive health data from unauthorised access. These strategies not only address immediate security concerns but also contribute to fortifying the organisation’s overall security posture, ensuring preparedness against evolving cyber threats [
27,
38,
40,
52].
By continuously refining and strengthening these practices, healthcare organisations can significantly improve their ability to safeguard sensitive patient information while keeping pace with changing regulatory landscapes. Such ongoing efforts are integral to meeting compliance standards, fostering stakeholder trust, and preserving the integrity of digital health systems in an era in which data security is paramount [
27,
38,
40,
52].
5.4. The Human Side of Data Security
Research indicates that organisations encounter significant internal threats, often from employees who may neglect cybersecurity requirements due to carelessness, lack of awareness, or malicious intent. Such behaviours can have severe consequences, as employees frequently act as attack vectors in various capacities [
13,
21,
23,
26,
52,
57]. The findings derived from data analysis emphasise that human factors play a pivotal role in data protection. This study explores strategies to mitigate these risks by addressing human behaviour through targeted training, awareness programs, and policies promoting responsible handling of digital health data. The ultimate objective is to cultivate a robust culture of data protection within organisations [
13,
21,
23,
26,
52,
57].
Addressing human factors involves thoroughly understanding and managing the psychological and behavioural dimensions of employees’ interactions with data systems. Healthcare organisations can fortify their security protocols by implementing comprehensive training programs that educate employees about the significance of data security and equip them with practical skills to identify and address potential threats. Furthermore, clear and enforceable policies establish expectations for security practices, fostering a culture of accountability and vigilance [
13,
34,
49,
59].
By proactively addressing the human elements contributing to security vulnerabilities, healthcare organisations can significantly reduce insider threats and enhance compliance with data protection standards. Empowering employees to actively participate in safeguarding sensitive health data is imperative for creating a resilient security framework [
13,
21,
26].
The path diagram visually represents the hypothesised relationships between organisational governance, cybersecurity practices, and data protection compliance. It emphasises the critical role of human factors in data security, highlighting the interconnected nature of governance structures and cybersecurity measures and their influence on compliance outcomes [
13,
34,
49,
59]. This underscores the necessity of addressing human behaviour, awareness, and accountability to fortify the organisation’s security framework. The directional influences and path coefficients further reflect the significant impact of well-aligned governance and security practices on fostering a culture of compliance and mitigating risks associated with human vulnerabilities [
13,
34,
49,
59].
5.5. Validating the Socio-Technical Protection Model
The findings of this study empirically validate the proposed integrated data protection framework, emphasising the significance of a socio-technical approach in the safeguarding of digital health systems. The research reveals strong causal relationships between governance and cybersecurity policy dimensions and compliance behaviour, confirming that organisational structures, leadership, and accountability significantly influence data protection outcomes [
13,
36,
59].
An additional analysis of work experience yields novel insights. The findings indicate that employee tenure significantly affects both the governance–compliance relationship and cybersecurity behaviour. This supports the premise that compliance is not solely a function of academic training; rather, it is deeply connected to accumulated institutional knowledge and experiential learning. Therefore, digital health institutions should consider aligning compliance protocols and training initiatives not only with policy mandates but also with the demographic and experiential characteristics of their workforce [
26,
36,
49].
Furthermore, the findings indicate that relying on fragmented or top–down compliance frameworks may be inadequate. Instead, empirically grounded and system-integrated models, as demonstrated in our study, offer more resilient and adaptable strategies. Such models, especially when implemented with careful attention to human factors, can enhance the long-term effectiveness and scalability of data protection initiatives [
21,
36].
5.6. Integrated Digital Health Data Compliance Framework
This study addresses a critical challenge in digital health, designing a robust data protection framework that balances the transformative benefits of digital health systems with compliance with stringent data protection regulations [
17,
43,
46,
57].
The existing research underscores the growing complexity of managing digital health systems and the need for institutions to embrace continuous, well-governed, and accountable approaches to data protection. Recognising that data protection requires legal and technical expertise, this study proposes actionable measures to demystify compliance and empower stakeholders within the digital health ecosystem [
13,
22,
46,
49,
57].
This study presents a digital health data protection framework that integrates six key pillars: technology, cybersecurity, governance, policy, legislation, and risk assessment [
17,
43,
47,
57,
59]. The proposed framework is comprehensive and designed to enhance data protection in healthcare through the following components [
17,
43,
46,
57]:
Technology: utilising advanced digital tools for effective data protection.
Cybersecurity: implementing strong measures to prevent data breaches.
Governance: establishing accountability and oversight mechanisms to ensure compliance.
Policy: defining clear guidelines for data handling and management.
Legislation: ensuring adherence to legal standards, such as the General Data Protection Regulation (GDPR).
Risk Assessment: proactively identifying and mitigating potential threats to data security.
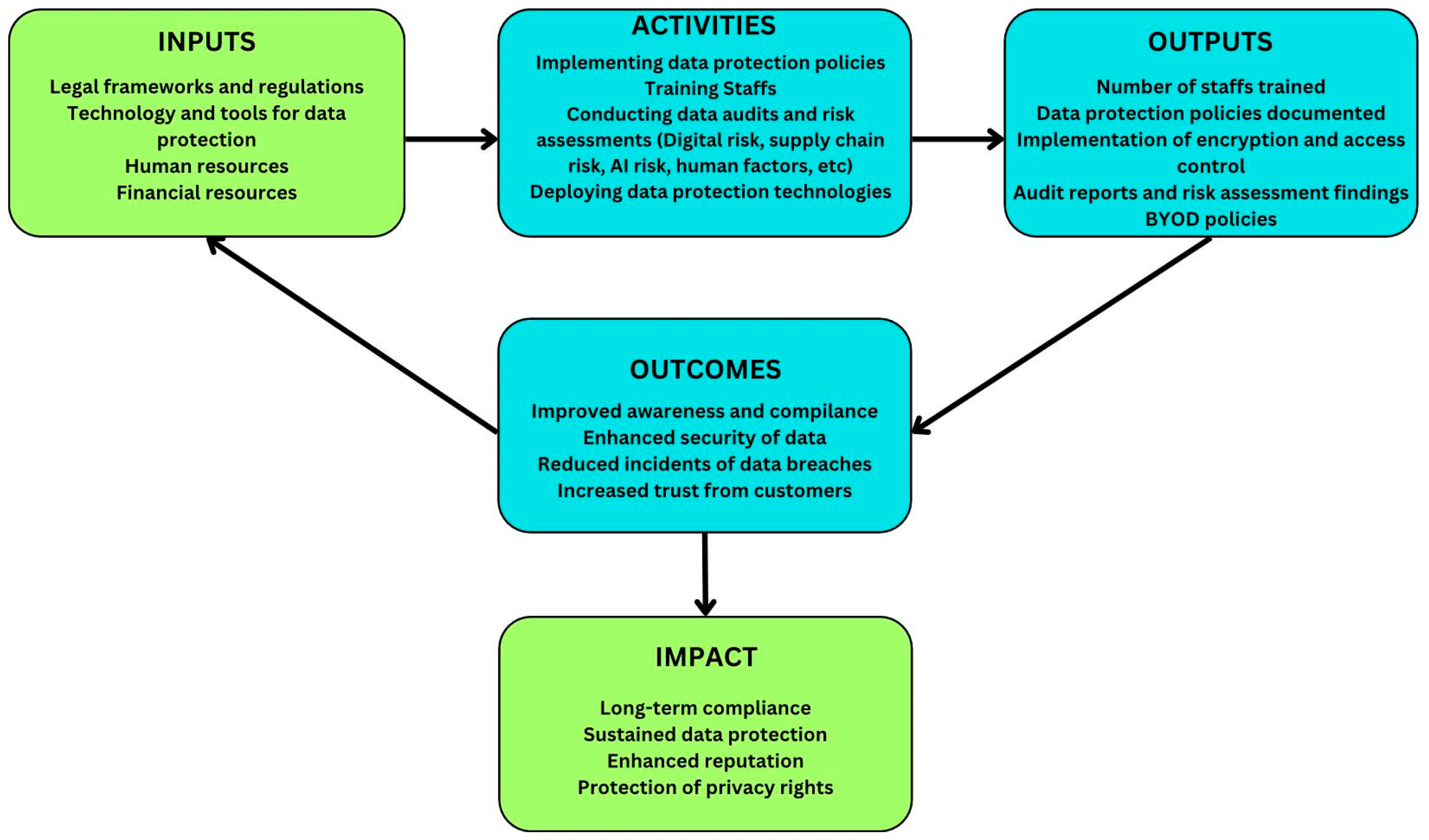
Figure 5 illustrates that the proposed framework integrates six foundational pillars: technology, cybersecurity, governance, policy, legislation, and risk assessment. Each pillar is critical—utilising advanced digital tools, implementing strong cybersecurity practices, establishing accountability mechanisms, defining clear policies, adhering to legal standards like GDPR, and proactively mitigating risks. The framework provides a comprehensive roadmap (Inputs → Activities → Outputs → Outcomes → Impact, as shown in
Figure 6) for healthcare organisations to enhance data security [
17,
43,
46,
57].
Figure 6 illustrates the framework roadmap, which employs a layered approach. This model highlights governance as the foundational component, integrates cybersecurity as a fundamental practice, and establishes compliance as the ultimate goal. Digital health systems are effectively governed, resilient, and aligned with regulatory standards across strategic, tactical, and operational dimensions using this structured methodology. This comprehensive roadmap facilitates the safeguarding of sensitive health data within an increasingly digitised landscape [
13,
22,
46,
49,
71].
The research’s key recommendations target stakeholders across sectors. Policymakers are urged to develop harmonised regulations that balance innovation with stringent data protection requirements. Organisations are encouraged to invest in governance and cybersecurity capacity-building to achieve sustained compliance. At the same time, researchers are invited to explore the dynamic interplay between governance, security, and compliance in diverse healthcare contexts. These actionable insights are designed to resonate across the healthcare ecosystem, promoting a unified approach to digital health data protection [
13,
22,
46,
49].
5.7. An Integrated Theory of Change Approach to a Digital Health Data Protection Framework
The framework utilises a theory of change methodology to develop a comprehensive approach to protecting digital health data. It emphasises the integration of governance, compliance, and cybersecurity practices to safeguard sensitive health information, thereby enhancing the security posture of digital health systems while meeting regulatory requirements and best practices [
17,
43,
46]. The theory of change model for digital health data protection, illustrated in
Figure 6, demonstrates how healthcare organisations can systematically improve cybersecurity practices and regulatory compliance. It outlines essential components such as inputs, activities, outputs, outcomes, and long-term impacts. This framework is especially relevant for health organisations navigating legal obligations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), as it assists in optimising resources to strengthen data security and build stakeholder trust [
43,
47,
57].
The process begins with key inputs, including legal frameworks, security technologies, human resources, and financial investments, enabling critical activities such as policy development, training, risk assessments, and cybersecurity technology deployment. The Diffusion of Innovations Theory explains the dissemination of security measures within healthcare organisations, while the socio-technical systems theory addresses the interaction between technology and organisational governance structures [
17,
43,
46,
57].
These activities result in measurable outputs that enhance compliance, improve data security, reduce breach incidents, and increase patient trust. The principles of Privacy by Design ensure security measures are embedded from the outset, while Compliance Theory emphasises the role of organisational governance culture in legal adherence. Ultimately, these initiatives foster sustained data security, enhance institutional reputation, and protect patients’ privacy rights. Data Governance Frameworks are crucial for maintaining data accuracy, accessibility, and security, promoting ongoing compliance with best practices. By integrating these theoretical perspectives, healthcare organisations can create a comprehensive strategy for digital health data protection, fostering trust and mitigating cybersecurity risks in a digitised healthcare ecosystem [
17,
43,
46,
57].
5.8. Comparative Analysis and Structured Framework for Sustainable Digital Health Data Protection
The proposed framework offers a structured and systematic approach to digital health data protection, addressing key limitations of existing models such as the NHS Good Practice Guidelines and the Data Privacy Framework (DPF) [
6,
7,
15,
22,
47]. Unlike these compliance-focused models, this framework integrates legal mandates, financial resources, technology adoption, audits, encryption, and workforce training into a cohesive methodology that ensures measurable security improvements. The framework effectively bridges the gap between policy and implementation by linking regulatory policies to practical data protection measures through logical progression. It also addresses shortcomings in traditional governance models by introducing explicit enforcement mechanisms across diverse healthcare environments, making it a more robust and actionable approach to digital health security [
6,
7,
15,
22,
47].
A key strength of this framework lies in its emphasis on clear cause-and-effect relationships, ensuring that regulatory requirements translate into tangible security enhancements. Unlike existing models that prioritise compliance without detailing implementation mechanisms, this approach integrates financial investments, staff training, encryption enforcement, and risk assessments into a dynamic and iterative security strategy. The framework also improves models like PERSONA and the Enterprise Data Management Framework (EDM) by incorporating continuous security verification through audit reports and risk assessment findings [
6,
7,
22]. Beyond regulatory compliance, it promotes long-term sustainability by fostering stakeholder engagement, security awareness, and proactive data protection measures. By linking compliance with sustained security outcomes such as protecting patient privacy and institutional reputation, the framework establishes a comprehensive and adaptive model that enables healthcare organisations to navigate digital health data protection and security challenges efficiently and effectively [
6,
7,
15,
22].
5.9. A Constructivist Grounded Theory Model for Safeguarding Digital Health Data
Constructivist Grounded Theory (CGT) (Charmaz, 2006) [
72] is employed as the primary methodological approach to validate the proposed framework. This highlights the dynamic, interpretive, and socially constructed aspects of digital health data protection and cybersecurity adoption in healthcare. CGT acknowledges that social interactions, institutional cultures, and evolving regulatory landscapes significantly shape digital health data security in contrast to positivist models. Policies and compliance mechanisms are continuously negotiated and redefined through stakeholder engagement and organisational adaptation [
35,
73,
74]. Within this constructivist paradigm, the adoption of cybersecurity technologies, governance policies, and data protection compliance in healthcare is conceptualised as an iterative process influenced by the perceptions, attitudes, and lived experiences of healthcare professionals, compliance officers, and policymakers [
35,
73,
74].
The framework leverages CGT’s iterative data collection and analysis to identify key barriers and facilitators to adopting digital health data protection and cybersecurity measures. It is worth noting that regulatory mandates are often subject to varying interpretations across organisations, affecting the implementation and effectiveness of security policies [
35,
73]. The co-development of digital health data protection and cybersecurity frameworks, while incorporating insights from end-users and subject-matter experts, enhances their relevance and facilitates seamless integration into daily healthcare practices.
Additionally, the framework adopts a theory of change (ToC) methodology to establish a structured and comprehensive approach to digital health data protection. By integrating governance, compliance, and cybersecurity measures, the framework safeguards sensitive health information while aligning with regulatory requirements and industry best practices. As illustrated in
Figure 6, the ToC model provides a systematic pathway for healthcare organisations to strengthen cybersecurity, enhance regulatory compliance, and foster a culture of data security awareness [
17,
43,
46,
47].
Furthermore, CGT allows for the integration of complementary theoretical perspectives, such as the Diffusion of Innovations Theory and socio-technical systems theory, enriching the understanding of digital health data protection adoption. These perspectives reveal that compliance transcends regulatory enforcement, fostering a culture of ethical responsibility, risk awareness, and proactive cybersecurity engagement [
35,
73].
The outcomes of this approach include measurable improvements in regulatory compliance, enhanced data security, reduced security breaches, and increased trust between patients and healthcare providers. Effective data protection governance requires robust technical measures, sustained commitment to ethical responsibility, stakeholder collaboration, and continuous adaptation. This methodological flexibility ensures that digital health data protection strategies remain dynamic, participatory, and responsive to emerging threats. By fostering a culture of trust, compliance, and innovation, healthcare organisations can mitigate cybersecurity risks while reinforcing resilience in the increasingly digitised field of healthcare [
17,
43,
46,
47].
7. Conclusions
This study underscores the critical necessity for a robust empirically grounded data protection framework within the realm of digital health, which aligns technological innovation with strict regulatory compliance requirements. Furthermore, it highlights the importance of continuous, accountable governance and integration of legal and technical expertise to empower stakeholders and facilitate compliance efforts [
13,
34,
49,
59]. The proposed framework is structured around six foundational pillars: technology, cybersecurity, governance, policy, legislation, and risk assessment. This integrated approach offers healthcare organisations a structured pathway to mitigate risks, enhance resilience, and ensure adherence to standards such as the General Data Protection Regulation (GDPR). By fostering proactive risk management and strategic governance, the framework enhances resilience and alignment with compliance standards while mitigating potential threats [
13,
34,
49,
75].
Unlike conventional models that address legal or technical dimensions in isolation, this framework adopts a socio-technical systems perspective to unify these domains and empirically validate their interdependencies. Using advanced engineering methodologies, including exploratory factor analysis (EFA) and Partial Least Squares Structural Equation Modelling (PLS-SEM), the study provides robust evidence of causal relationships between governance practices, cybersecurity practices, and data protection compliance [
13,
34,
59]. The contributions of this research are as follows: First, it delivers practical guidance for policymakers, calling for harmonised regulatory frameworks that can adapt to evolving digital health landscapes. Second, it equips healthcare institutions with a measurable model for implementing strategic investments in cybersecurity and governance infrastructure. Third, it advances theoretical discourse by demonstrating how governance serves as a foundational mechanism for ensuring compliance, security, and trust in digital systems [
13,
34,
49,
59].
While the empirical application focuses on healthcare, the framework’s design and methodological approach are broadly applicable to electronic governance, smart infrastructure, and digital risk management across sectors. Accordingly, this work contributes to both digital health informatics and the broader field of socio-technical systems engineering, offering conceptual novelty and empirical rigour for academics and practitioners alike [
13,
34,
49,
59].