Multi-Layer Cryptosystem Using Reversible Cellular Automata
Abstract
1. Introduction
- Development of an innovative multi-layer encryption algorithm entirely based on reversible cellular automata, leveraging a cascade of RCA modules to strengthen diffusion and security characteristics of the cipher;
- Full integration of cellular automata principles in both encryption logic and random state generation, ensuring structural consistency and alignment with CA-based design methodology validated in prior studies;
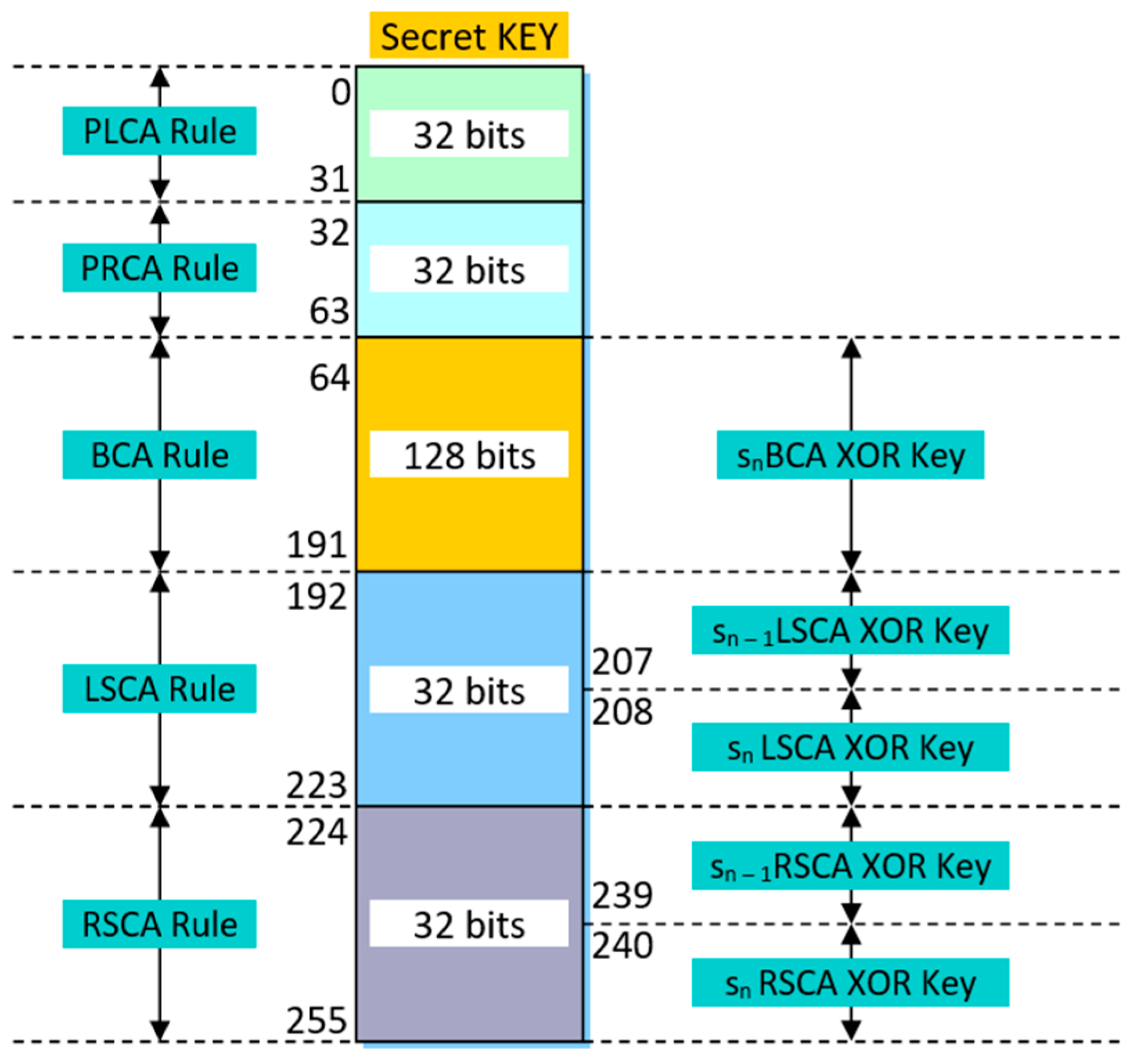
- Design of a robust key structure consisting of 256-bits, enabling dynamic rule configuration for each RCA and securing critical recovery data, thereby significantly expanding the cryptographic keyspace;
- FPGA-based hardware implementation optimized for parallelism and reversibility, utilizing modular RCA units along with the inclusion of a custom PC–FPGA communication interface allowing seamless encryption/decryption operations and secure key/data handling;
- Application of NIST statistical tests to assess ciphertext randomness along with visual evaluation techniques and performance analysis confirming high entropy and resistance to pattern-based attacks, further demonstrating the cryptosystem’s effectiveness.
2. Materials and Methods of the Cryptosystem
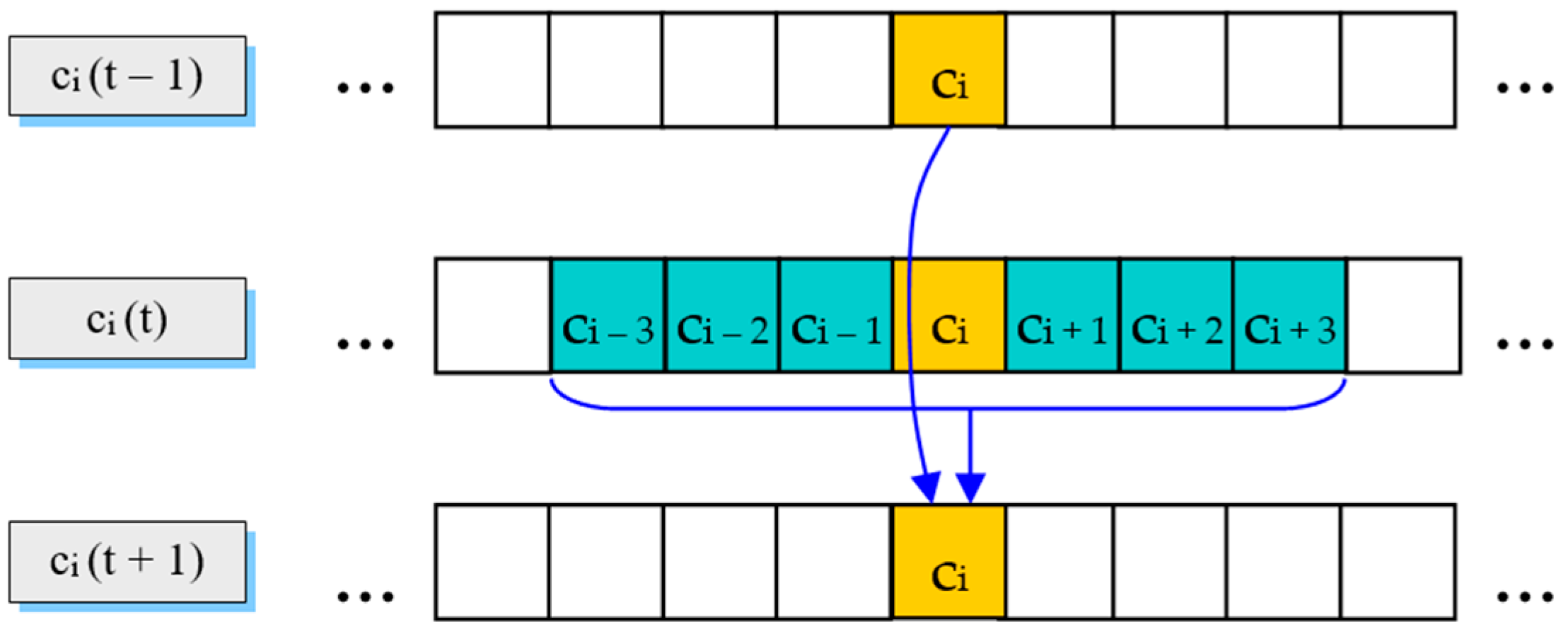
2.1. Cellular Automata Models
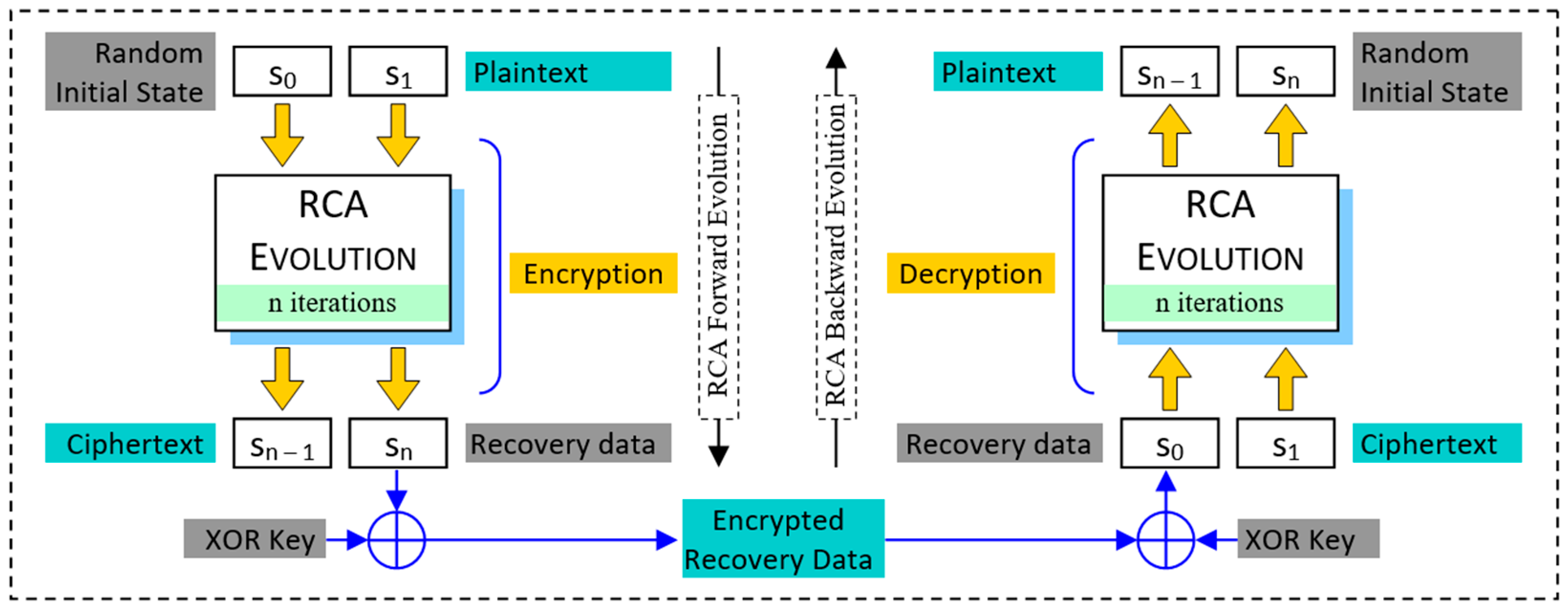
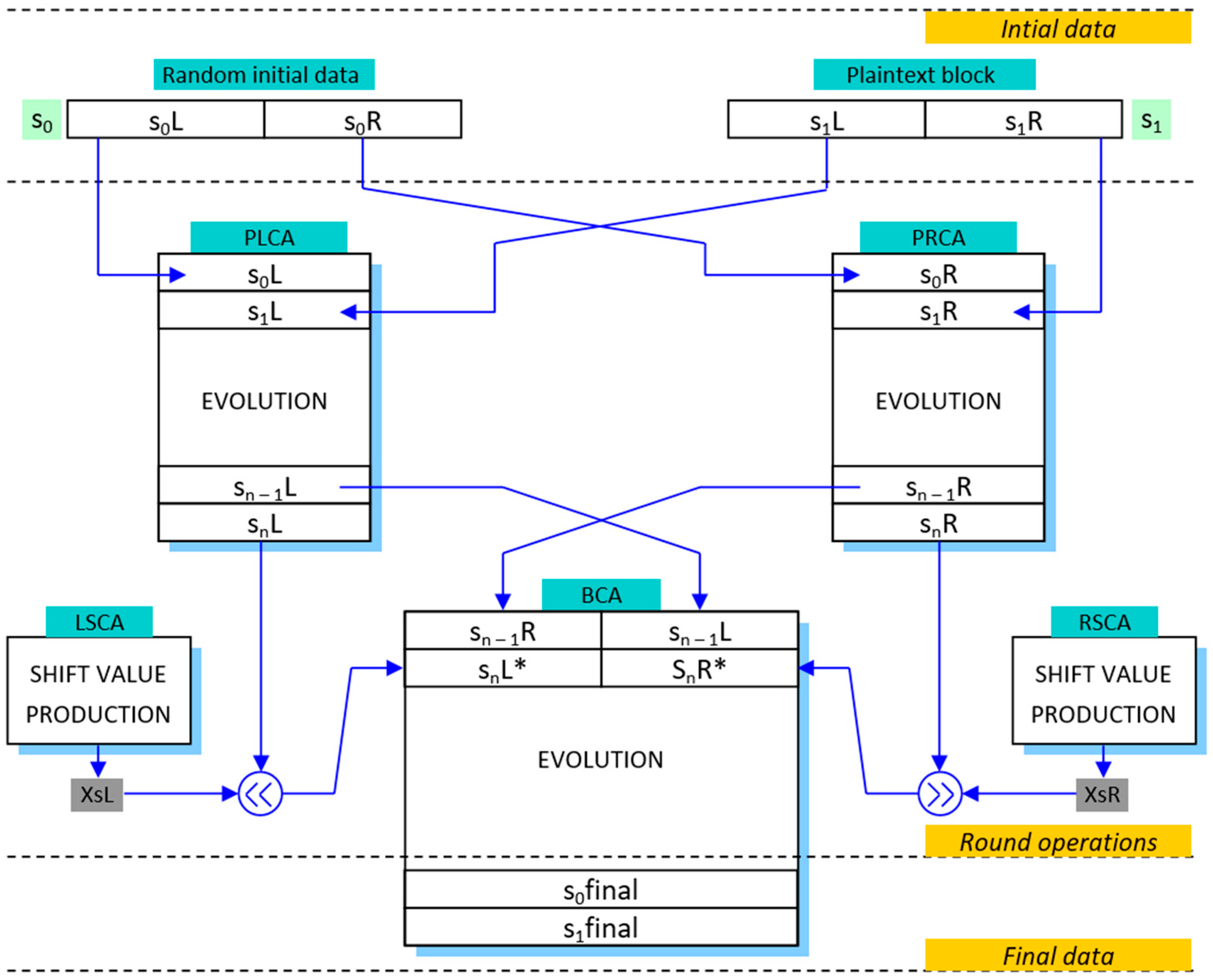
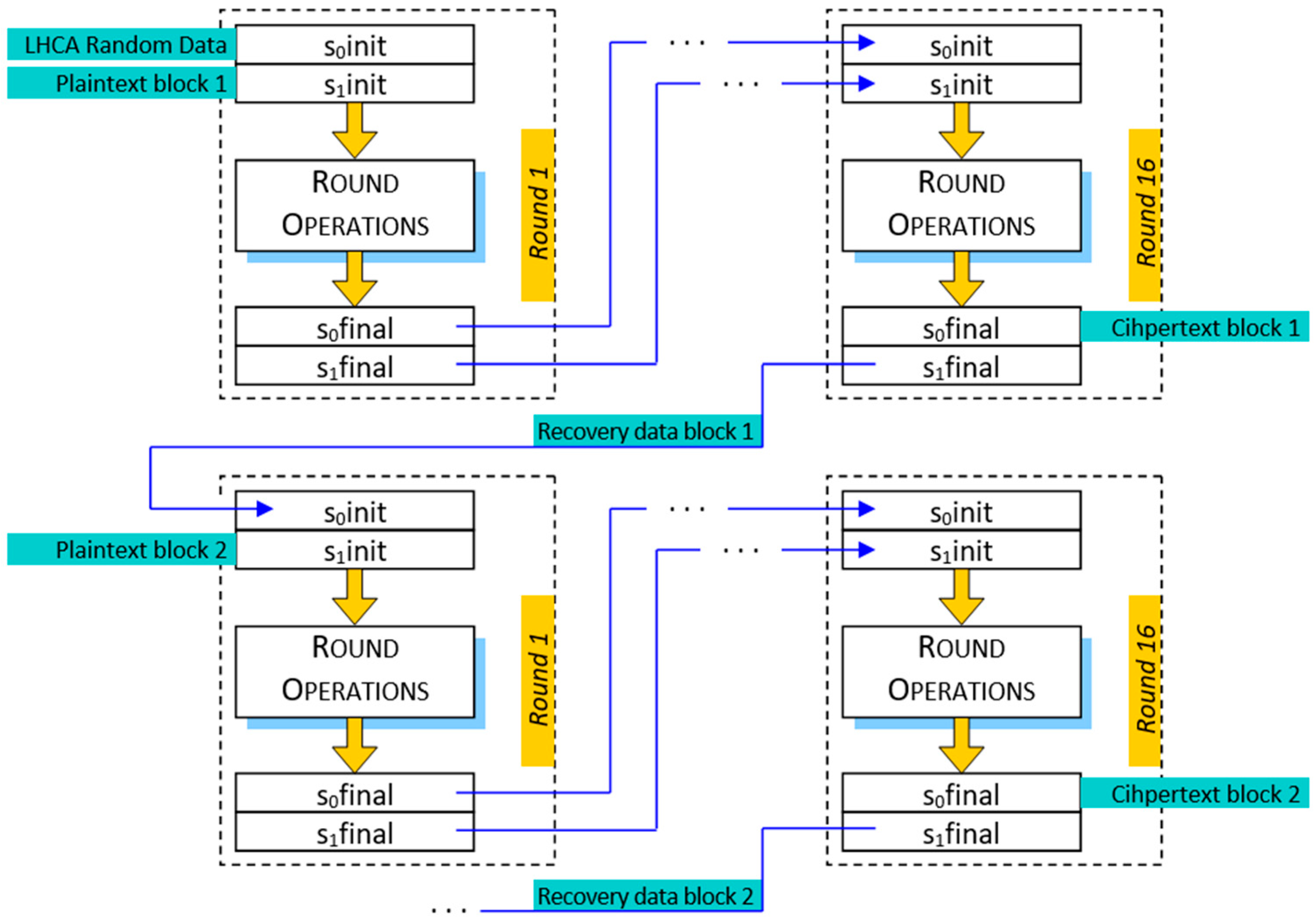
2.2. Multi-Layer RCA-Based Encryption Design
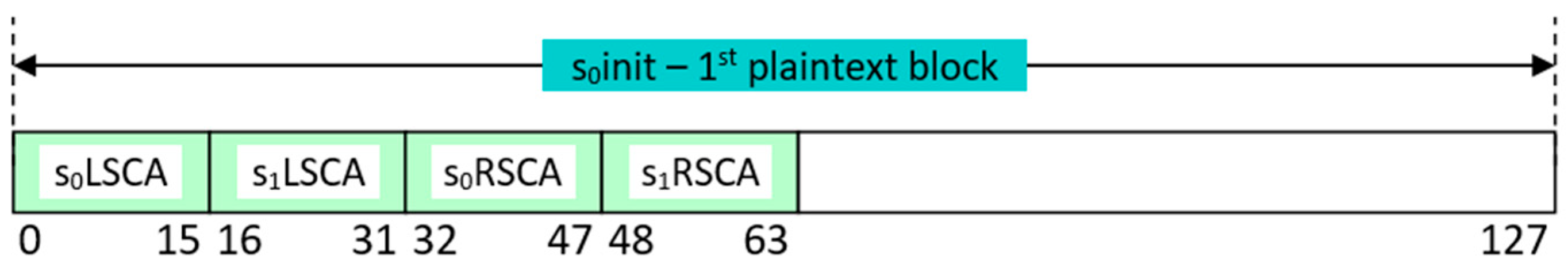
- Primary Transformation Layer: consists of two parallel RCA modules (denoted as PLCA and PRCA), each processing a separate half of the input data block;
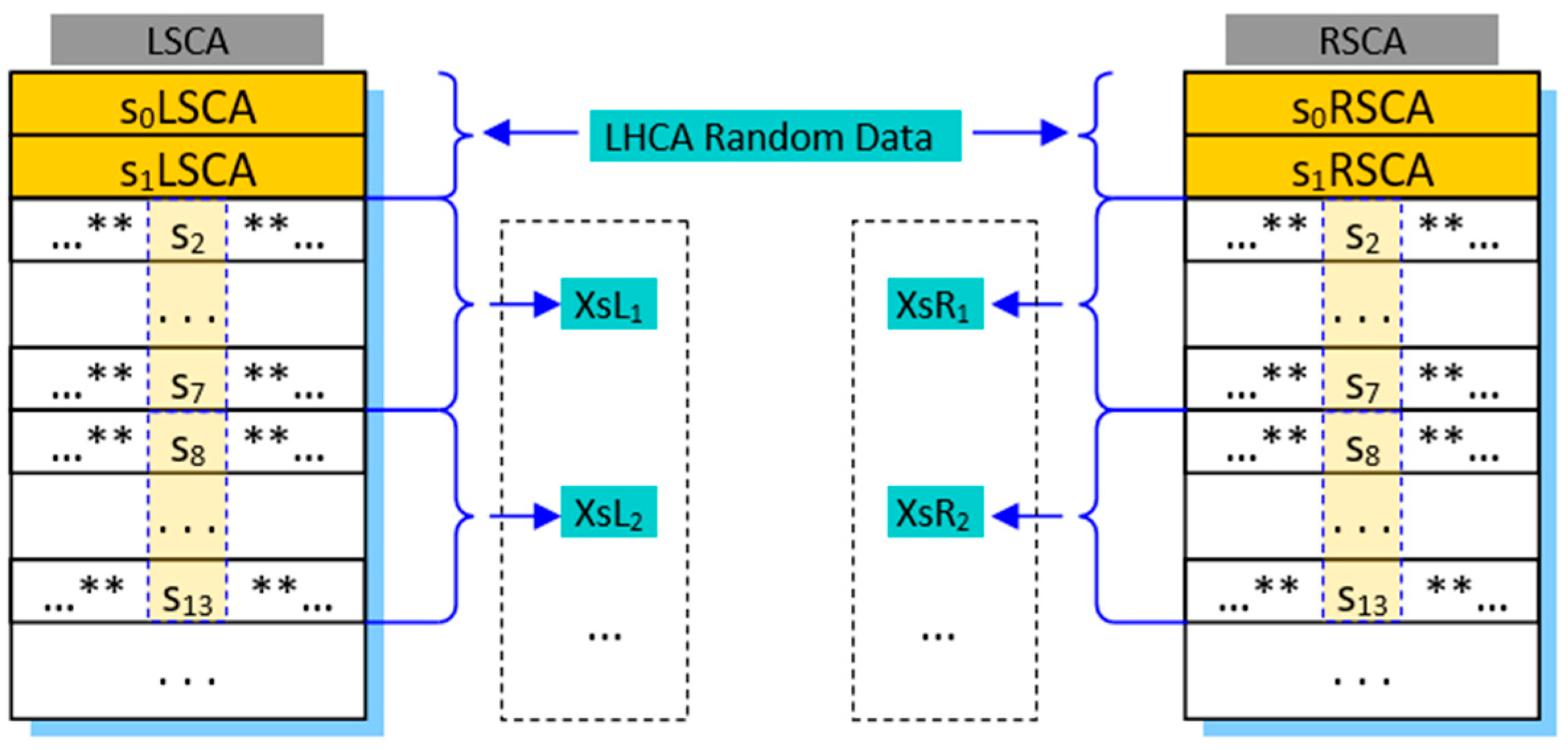
- Shift Computation Layer: introduces controlled variability in the data flow by employing additional RCA modules (LSCA and RSCA) to dynamically generate shift values in order to increase dispersion and eliminate symmetry in the data;
- Binding Layer: performs the recombination of the processed data using another RCA module (BCA) operating over the entire block length, resulting in a final encrypted output for the current round and an additional state used for the next block encryption.
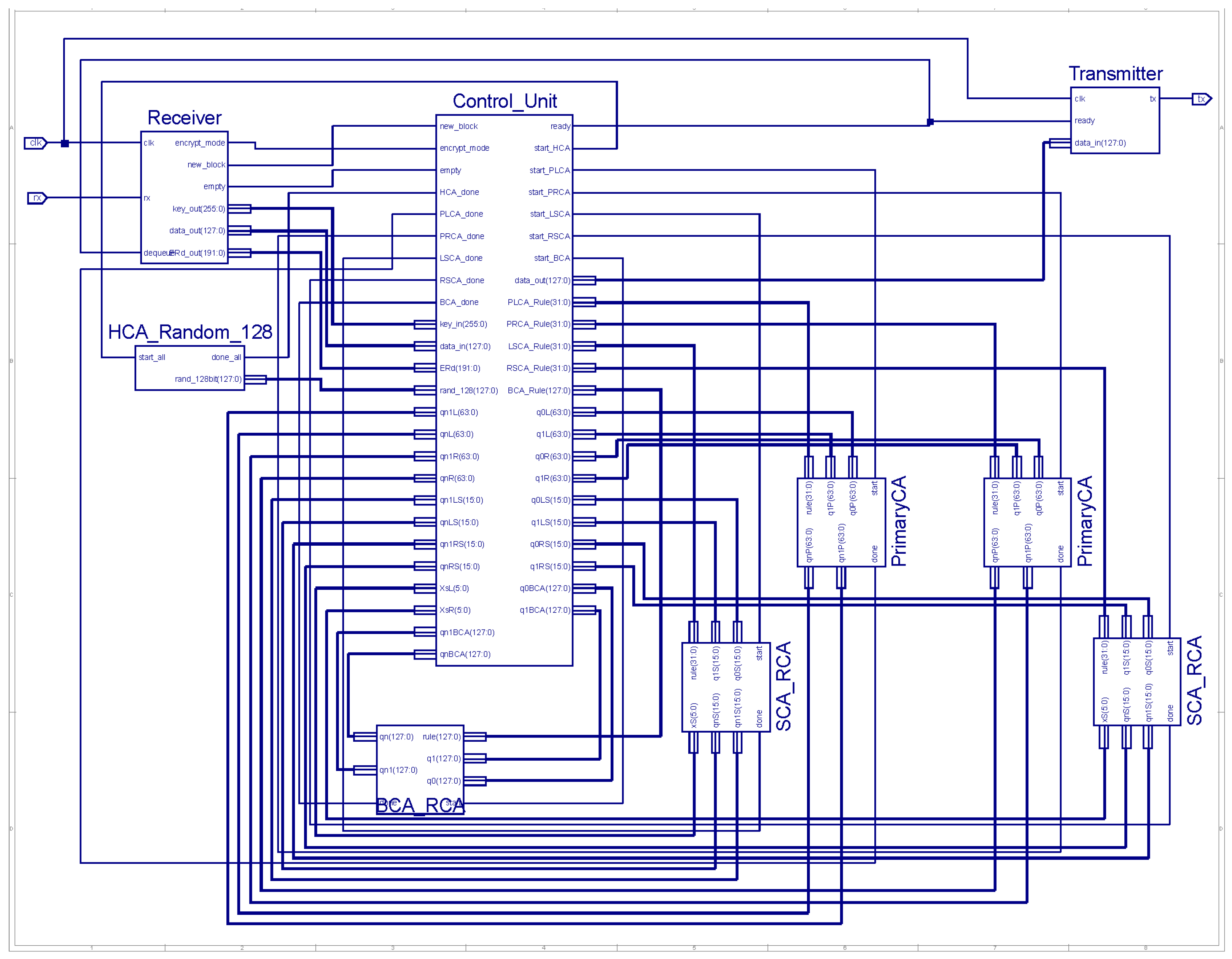
3. Hardware Architecture and Implementation
| Algorithm 1: FPGA-Based Multi-Layer RCA Overall Operation Logic Flow |
| Initialize UART Communication Initialize RCA Units with Key Rules Load Secret Key (256-bit) Generate Initial Random State (128-bit) while (Receiver detects new data block) if Received Data Identifier = ‘K’ Store Secret Key from Incoming Stream else if Received Data Identifier = ‘P’ OR ‘C’ Store Input Block into Buffer Set encrypt_mode Flag Accordingly end if while (Buffer Not Empty) Dequeue 128-bit Block from FIFO if encrypt_mode = ENCRYPT for Round = 1 to 16 Evolve PLCA and PRCA in Parallel Compute Shift Values using LSCA and RSCA Apply Circular Shifts to PLCA and PRCA Outputs Evolve BCA Using Shifted Outputs end for Store Final BCA State Generate Encrypted Recovery Data (ERd) Append ERd to Final Cipher Block Transmit Cipher Block via UART else if encrypt_mode = DECRYPT Extract ERd and Restore Last States for Round = 1 to 16 Reverse BCA Evolution Reverse Shifts and Primary RCAs Evolutions end for Transmit Decrypted Plaintext Block end if end while end while end |
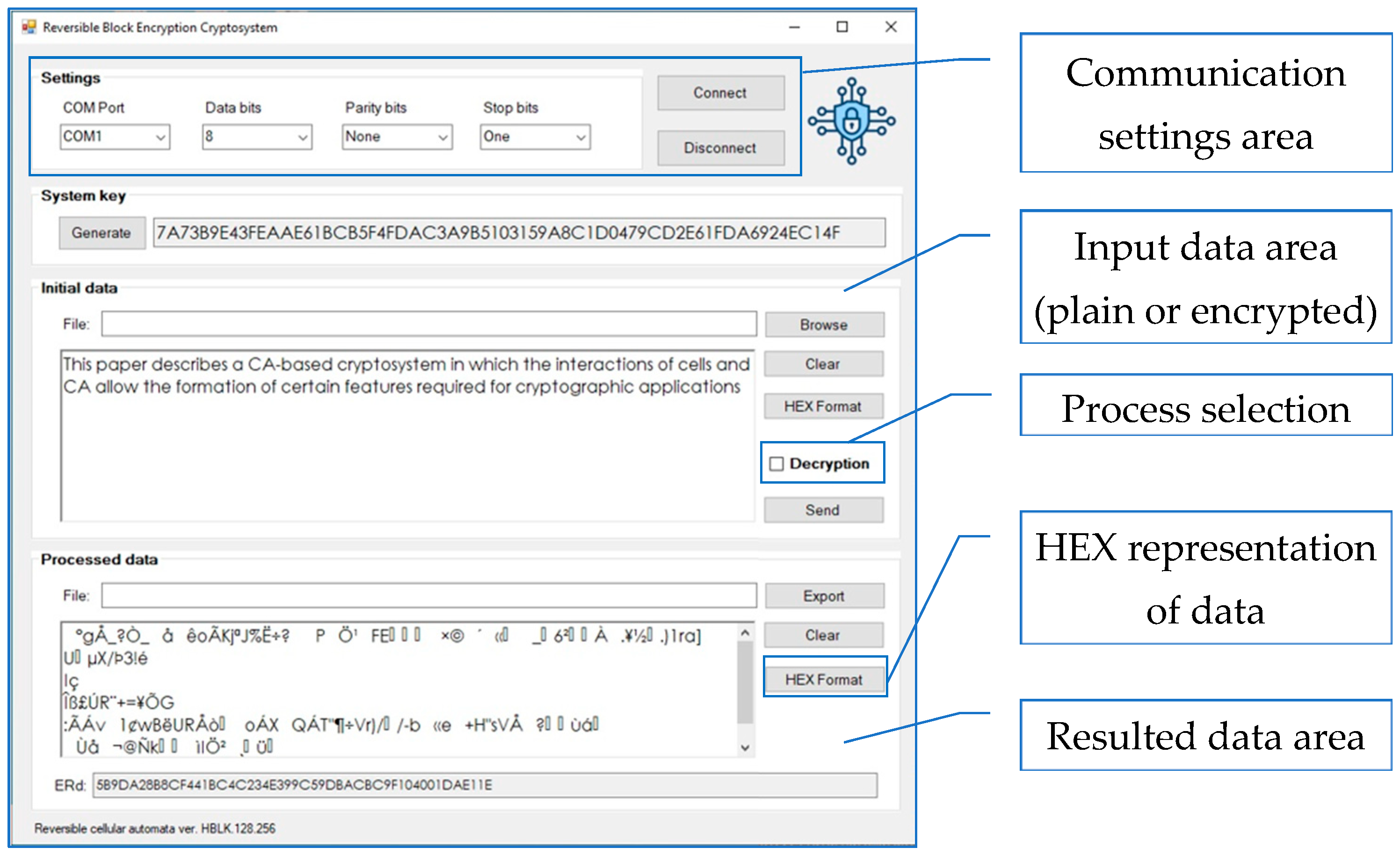
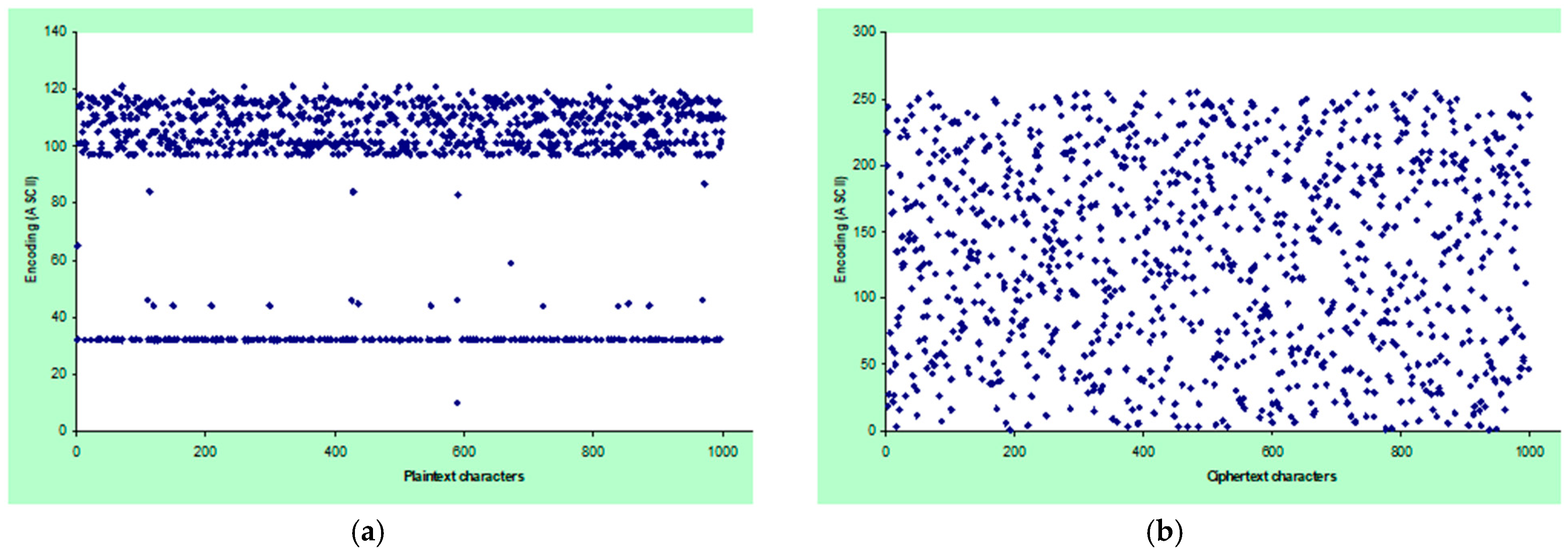
4. Results and Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| CA | Cellular Automata |
| HCA | Hybrid Cellular Automata |
| LCA | Linear Cellular Automata |
| RCA | Reversible Cellular Automata |
| PLCA | Primary Left Cellular Automata |
| PRCA | Primary Right Cellular Automata |
| LSCA | Left Shifting Cellular Automata |
| RSCA | Right Shifting Cellular Automata |
| BCA | Binding Cellular Automata |
| FPGA | Field Programmable Gate Array |
| ERd | Encrypted Recovery data |
| DES | Data Encryption Standard |
| AES | Advanced Encryption Standard |
| IoT | Internet of Things |
| NIST | National Institute of Standards and Technology |
References
- Scripcariu, L.; Diaconu, F.; Mătăsaru, P.D.; Gafencu, L. AES Vulnerabilities Study. In Proceedings of the 10th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Iasi, Romania, 28–30 June 2018. [Google Scholar] [CrossRef]
- Rahmani, M.; Nitaj, A.; Ziane, M. Partial Exposure Attacks on a New RSA Variant. Cryptography 2024, 8, 44. [Google Scholar] [CrossRef]
- American Scientist. Available online: https://www.americanscientist.org/article/is-quantum-computing-a-cybersecurity-threat (accessed on 7 May 2025).
- Alexan, W.; Youssef, M.; Hussein, H.H.; Ahmed, K.K.; Hosny, K.M.; Fathy, A.; Mansour, M.B.M. A new multiple image encryption algorithm using hyperchaotic systems, SVD, and modified RC5. Sci. Rep. 2025, 15, 9775. [Google Scholar] [CrossRef]
- Cantoro, R.; Deligiannis, N.I.; Reorda, M.S.; Traiola, M.; Valea, E. Evaluating Data Encryption Effects on the Resilience of an Artificial Neural Network. In Proceedings of the 2020 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFT), Frascati, Italy, 19–21 October 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Deng, Q.; Wang, C.; Sun, Y.; Deng, Z.; Yang, G. Memristive Tabu Learning Neuron Generated Multi-Wing Attractor with FPGA Implementation and Application in Encryption. IEEE Trans. Circuits Syst. I Regul. Pap. 2024, 72, 300–311. [Google Scholar] [CrossRef]
- Huang, Y.; Zhang, S.; Wang, B. An Improved Genetic Algorithm with Swarm Intelligence for Security-Aware Task Scheduling in Hybrid Clouds. Electronics 2023, 12, 2064. [Google Scholar] [CrossRef]
- Jiang, M.; Yang, H. Image Encryption Using a New Hybrid Chaotic Map and Spiral Transformation. Entropy 2023, 25, 1516. [Google Scholar] [CrossRef] [PubMed]
- Corona-Bermúdez, E.; Chimal-Eguía, J.C.; Téllez-Castillo, G. Cryptographic Services Based on Elementary and Chaotic Cellular Automata. Electronics 2022, 11, 613. [Google Scholar] [CrossRef]
- Levina, A.; Mukhamedjanov, D.; Bogaevskiy, D.; Lyakhov, P.; Valueva, M.; Kaplun, D. High Performance Parallel Pseudorandom Number Generator on Cellular Automata. Symmetry 2022, 14, 1869. [Google Scholar] [CrossRef]
- Stănică, G.C.; Anghelescu, P. Reversible cellular automata encryption algorithm implemented on FPGA. In Proceedings of the 2023 International Conference on Applied Electronics (AE), Pilsen, Czech Republic, 6–7 September 2023; pp. 1–4. [Google Scholar] [CrossRef]
- Stănică, G.C.; Anghelescu, P. Reversible Cellular Automata Based Cryptosystem. Electronics 2024, 13, 2515. [Google Scholar] [CrossRef]
- Wang, X.Y.; Li, L.; Sun, B. Chaotic Image Encryption Algorithm Based on Block Theory and Reversible Mixed Cellular Automata. Opt. Laser Technol. 2020, 121, 105756. [Google Scholar]
- Zhang, B.; Liu, L. Chaos-Based Image Encryption: Review, Application, and Challenges. Mathematics 2023, 11, 2585. [Google Scholar] [CrossRef]
- Chen, K.; Wang, X.; Fu, Y.; Li, L. Efficient Quantization and Data Access for Accelerating Homomorphic Encrypted CNNs. Electronics 2025, 14, 464. [Google Scholar] [CrossRef]
- Abbassi, N.; Gafsi, M.; Amdouni, R.; Hajjaji, M.A.; Mtibaa, A. Hardware implementation of a robust image cryptosystem using reversible cellular-automata rules and 3-D chaotic systems. Integration 2022, 87, 49–66. [Google Scholar] [CrossRef]
- Nanda, S.K.; Mohanty, S.; Pattnaik, P.K.; Sain, M. Throughput Optimized Reversible Cellular Automata Based Security Algorithm. Electronics 2022, 11, 3190. [Google Scholar] [CrossRef]
- Siddiqui, A.F.; Sekhar, C. FPGA Acceleration of AES Algorithm for High-Performance Cryptographic Applications. Int. J. Inf. Technol. Comput. Eng. 2024, 4, 1–11. [Google Scholar] [CrossRef]
- Yang, C.-H.; Lee, J.-D.; Tam, L.-M.; Li, S.-Y.; Cheng, S.-C. FPGA Implementation of Image Encryption by Adopting New Shimizu–Morioka System-Based Chaos Synchronization. Electronics 2025, 14, 740. [Google Scholar] [CrossRef]
- Guang, Y.; Yu, L.; Dong, W.; Wang, Y.; Zeng, J.; Zhao, J.; Ding, Q. Chaos-Based Lightweight Cryptographic Algorithm Design and FPGA Implementation. Entropy 2022, 24, 1610. [Google Scholar] [CrossRef]
- Stănică, G.C.; Anghelescu, P. Design of a Multi-Layer Symmetric Encryption System Using Reversible Cellular Automata. Mathematics 2025, 13, 304. [Google Scholar] [CrossRef]
- Wolfram, S. A New Kind of Science; Wolfram Media: Champaign, IL, USA, 2002. [Google Scholar]
- Anghelescu, P. Evolution of Hybrid Cellular Automata for Density Classification Problem. Symmetry 2024, 16, 599. [Google Scholar] [CrossRef]
- Stănică, G.C.; Anghelescu, P. Cryptographic Algorithm Based on Hybrid One-Dimensional Cellular Automata. Mathematics 2023, 11, 1481. [Google Scholar] [CrossRef]
- Wolfram, S. Random Sequence Generation by Cellular Automata. Adv. Appl. Math. 1986, 7, 123–169. [Google Scholar] [CrossRef]
- Hatkar, S.S.; Pawar, B.K. Symmetric key algorithm using Vernam cipher: VSA. In Proceedings of the International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 26–27 August 2016. [Google Scholar]
- Hortensius, P.; McLeod, R.; Card, H. Parallel random number generation for VLSI systems using cellular automata. IEEE Trans. Comput. 1989, 38, 1466–1473. [Google Scholar] [CrossRef]
- Bassham, L.; Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Leigh, S.; Levenson, M.; Vangel, M.; Heckert, N.; Banks, D. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2010; pp. 800–822. [Google Scholar]
- Anghelescu, P. Parallel Optimization of Program Instructions Using Genetic Algorithms. Comput. Mater. Contin. 2021, 67, 3293–3310. [Google Scholar] [CrossRef]
- Li, H.; Li, T.; Feng, W.; Zhang, J.; Zhang, J.; Gan, L.; Li, C. A novel image encryption scheme based on non-adjacent parallelable permutation and dynamic DNA-level two-way diffusion. J. Inf. Secur. Appl. 2021, 61, 102844. [Google Scholar] [CrossRef]
- Hua, Z.; Zhu, Z.; Yi, S.; Zhang, Z.; Huang, H. Cross-plane colour image encryption using a two-dimensional logistic tent modular map. Inf. Sci. 2021, 546, 1063–1083. [Google Scholar] [CrossRef]
- Li, H.; Yu, S.; Feng, W.; Chen, Y.; Zhang, J.; Qin, Z.; Zhu, Z.; Wozniak, M. Exploiting Dynamic Vector-Level Operations and a 2D-Enhanced Logistic Modular Map for Efficient Chaotic Image Encryption. Entropy 2023, 25, 1147. [Google Scholar] [CrossRef]
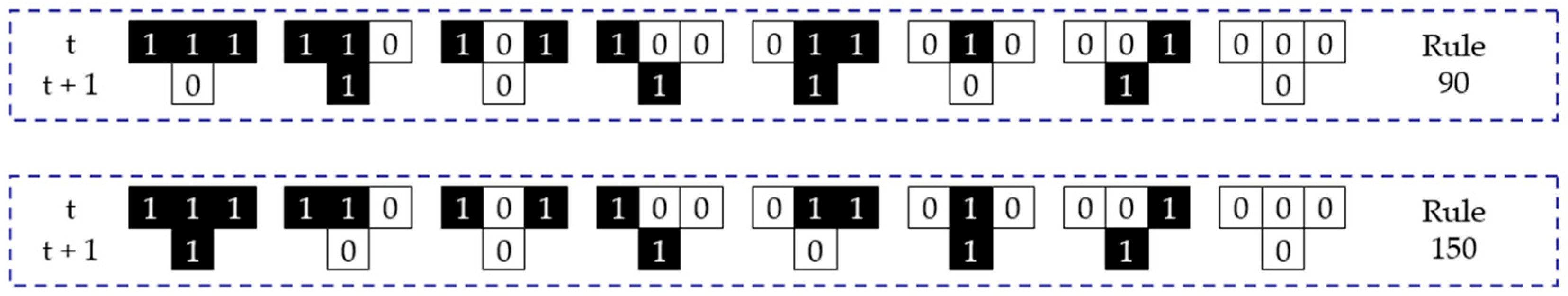

| Rule 1 | 111 | 110 | 101 | 100 | 011 | 010 | 001 | 000 |
|---|---|---|---|---|---|---|---|---|
| 90 | 0 | 1 | 0 | 1 | 1 | 0 | 1 | 0 |
| 150 | 1 | 0 | 0 | 1 | 0 | 1 | 1 | 0 |
| Number of Cells | Maximum Cycle Length | Rule |
|---|---|---|
| 32 | 232 | 01000110000010011011101111010101 |
| NIST Statistical Test | p-Value | Test Result—Proportion |
|---|---|---|
| Frequency (monobits) | 0.122325 | SUCCESS—10/10 |
| Block frequency | 0.534146 | SUCCESS—10/10 |
| Runs | 0.350485 | SUCCESS—10/10 |
| Longest run of one in a block | 0.350485 | SUCCESS—9/10 |
| Cumulative sums (forward) | 0.035174 | SUCCESS—10/10 |
| Cumulative sums (reverse) | 0.739918 | SUCCESS—10/10 |
| Rank | 0.213309 | SUCCESS—10/10 |
| FFT | 0.739918 | SUCCESS—9/10 |
| Non-overlapping template | 0.066882 | SUCCESS—10/10 |
| Overlapping template | 0.911413 | SUCCESS—10/10 |
| Approximate entropy | 0.739918 | SUCCESS—10/10 |
| Serial 1 | 0.122325 | SUCCESS—10/10 |
| Serial 2 | 0.350485 | SUCCESS—10/10 |
| Linear complexity | 0.534146 | SUCCESS—9/10 |
| BS 1 | BS 2 | BS 3 | BS 4 | BS 5 | BS 6 | BS 7 | BS 8 | BS 9 | BS 10 | |
|---|---|---|---|---|---|---|---|---|---|---|
| No. of 0s | 50,030 | 50,270 | 49,970 | 50,327 | 49,793 | 50,002 | 50,008 | 50,120 | 50,028 | 50,386 |
| No. of 1s | 49,970 | 49,730 | 50,030 | 49,673 | 50,207 | 49,998 | 49,992 | 49,880 | 49,972 | 49,614 |
| Resource | Used/Total | Area (%) |
|---|---|---|
| No. of slices | 3771/4656 | 81 |
| No. of slice flip-flops | 5587/9312 | 60 |
| No. of 4 input LUTs | 7449/9312 | 80 |
| No. of bonded IOBs | 62/232 | 27 |
| No. of GCLKs | 1/8 | 12 |
| Timing | Value | |
| Minimum period | 13,28 ns | |
| Maximum frequency | 75,301 MHz | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Stănică, G.C.; Anghelescu, P. Multi-Layer Cryptosystem Using Reversible Cellular Automata. Electronics 2025, 14, 2627. https://doi.org/10.3390/electronics14132627
Stănică GC, Anghelescu P. Multi-Layer Cryptosystem Using Reversible Cellular Automata. Electronics. 2025; 14(13):2627. https://doi.org/10.3390/electronics14132627
Chicago/Turabian StyleStănică, George Cosmin, and Petre Anghelescu. 2025. "Multi-Layer Cryptosystem Using Reversible Cellular Automata" Electronics 14, no. 13: 2627. https://doi.org/10.3390/electronics14132627
APA StyleStănică, G. C., & Anghelescu, P. (2025). Multi-Layer Cryptosystem Using Reversible Cellular Automata. Electronics, 14(13), 2627. https://doi.org/10.3390/electronics14132627






