Abstract
An Identity Management System (IDMS) is responsible for managing and organizing identities and credentials exchanged between users, Identity Providers (IDPs), and Service Providers (SPs). The primary goal of IDMS is to ensure the confidentiality and privacy of users’ personal data. Traditional IDMS relies on a third party to store user information and authenticate the user. However, this approach poses threats to user privacy and increases the risk of single point of failure (SPOF), user tracking, and data unavailability. In contrast, decentralized IDMSs that use blockchain technology offer potential solutions to these issues as they offer powerful features including immutability, transparency, anonymity, and decentralization. Despite its advantages, blockchain technology also suffers from limitations related to performance, third-party control, weak authentication, and data leakages. Furthermore, some blockchain-based IDMSs still exhibit centralization issues, which can compromise user privacy and create SPOF risks. This study proposes a decentralized IDMS that leverages blockchain and smart contract technologies to address the shortcomings of traditional IDMSs. The proposed system also utilizes the Interplanetary file system (IPFS) to enhance the scalability and performance by reducing the on-chain storage load. Additionally, the proposed IDMS employs the Elliptic Curve Integrated Encryption Scheme (ECIES) to provide an extra layer of security to protect users’ sensitive information while improving the performance of the systems’ transactions. Security analysis and experimental results demonstrated that the proposed IDMS offers significant security and performance advantages compared to its counterparts.
1. Introduction
In today’s world, having a digital identity is crucial to accessing online services. As a result, the digital IDMS has become essential. This system manages and organizes the data associated with digital identities and the parties that use them. Unfortunately, most current systems rely on centralization in data management. This means that a central digital IDMS stores and authenticates user data through a certificate authority, posing significant threats to user privacy. Centralized identity management comes with risks, including single point of failure, third-party control, data disclosure, and identity theft, all of which can compromise the security and privacy of users.
The concept of Blockchain was introduced by an anonymous individual named Satoshi Nakamoto in 2008 [1]. It is a technology that combines several other technologies, such as Blockchain data structure, public key infrastructure PKI, DLT, and consensus mechanisms [2]. The main reason for its widespread adoption is its decentralization feature, which helps to overcome the single point of failure problem SPOF commonly associated with centralized systems. Blockchain technology also offers great data protection capabilities, as any data that is stored on the Blockchain cannot be modified or deleted [3,4].
Blockchain technology can enhance a central IDMS by utilizing its distributed ledger features. This eliminates the issue of a single point of failure by distributing system copies to multiple peers. Even if one peer fails, the remaining peers can complete the task without any issues. Additionally, the system’s decentralization ensures that data management and storage are not reliant on a single party. The blockchain also offers smart contracts that automatically execute orders based on preset conditions, which enhances user privacy and anonymity. Incorporating blockchain technology into identity management brings numerous advantages, such as enhancing the overall quality of the system and protecting user privacy. This is made possible by the decentralized, transparent, and immutable nature of the blockchain. Nonetheless, some obstacles remain, such as the need to address scalability issues within the blockchain framework.
This study introduces a prototype of a blockchain-based IDMS that aims to improve user privacy. It achieves this by removing the third-party control, resolving the single point of failure issue, and minimizing data disclosure. Additionally, the proposed system enhances performance, security, and privacy by utilizing ECIES encryption algorithm. The main contributions of this research can be outlined as follows:
- (1)
- Enhance user privacy by avoiding the third-party control.
- (2)
- Improve confidentiality, integrity, and performance through utilizing ECIES encryption algorithm.
- (3)
- Solve issues related to centralized IDMS, such as SPOF.
- (4)
- Provide the user full control over their attributes data.
- (5)
- Introduce a prototype implementation for a secure blockchain-based IDMS.
2. Literature Review
This section provides a brief overview of the main approaches to IDMS and discusses significant research contributions associated with both centralized and decentralized (e.g., blockchain-based) IDMSs. Current research gaps are also highlighted in this section.
2.1. Overview of IDMSs Approaches
Identity management models (IDMMs) aim to process identity information securely and efficiently across several information systems and domains. These models are classified according to the use of identity information and the requirements for cross-domain access. Previous research has identified three primary approaches to IDMMs: the Isolated User Identity Model (SILO), the Federated Identity Model (FIM), and the User-Centric Model [5].
SILO is the most commonly used model for identity management due to its simplicity and convenience for users. The model basically involves two parties: the Identity Provider (IDP) and the user. Users in SILO are required to create multiple digital identities to access services across various domains. This poses significant challenges regarding the management of the user’s identity information. Moreover, users depend entirely on the IDP to manage their identities information, which raises significant privacy concerns, including potential user tracking and unauthorized exposure of sensitive information [6].
On the other hand, FIM consists of three parties: the Identity Provider (IDP), the Service Provider (SP), and the user. So, it involves one more party, the SP, in comparison with SILO. The IDP is responsible for establishing the user’s identity and issuing the necessary credentials. In this model, the user relies on the IDP to provide credentials related to their identity and to authenticate themselves to the SP. However, this complete dependence on the IDP gives this party comprehensive knowledge of user behaviors and relationships with the SPs. As a result, this may lead to privacy violations. Moreover, if the IDP services become unavailable for any reason, it causes the single point of failure problem [5].
The User-Centric Model, also referred to as the Open Trust Model, promotes a mutual trust among all parties involved in the IDMS. This model grants users the ability to select which attributes and credentials to share and can also choose the IDP. Nevertheless, this model has shortcomings related to privacy, as the IDP can control the information sharing with the SP and track the user’s behavior [5].
Overall, each IDM model has its advantages and disadvantages, and it is important to evaluate these factors when selecting an IDM approach. The following sections discuss the main approaches and research to related to IDMSs. These systems can be classified into centralized IDMSs and decentralized or blockchain-based IDMSs.
2.2. Centralized IDMSs
The study published in [7] explored several technologies that are used to implement IDMS. Researchers found that the assertion markup language (SAML) is an efficient and applicable choice as it received a high level of acceptance from users. The study concluded that SAML technology can considerably contribute to solving the problem of single sign-on. Another technology called WS-Federation has received increasing interest due to its ability to simplify the management of user’s identity across multiple IT systems. The study found that both approaches, SAML and WS-Federation, have common functionalities.
In [8], a claim-based IDMS was proposed by the Microsoft organization. The IDMS is called Microsoft CardSpace and is used to satisfy the seven laws of identity. This IDMS model is characterized by its ability to provide users with more control to their digital identities. In particular, this model allows users to choose the card, through an identity selector, after completing the service provider (SP) policy. The identity selector plays an intermediary role between the user, the IDP, and the SP. The identity selector is utilized to retrieve the security policy after the user picks the card and completes the user authentication mechanism with the IDP. Then the security token is forwarded to the SP to log the user in so he can obtain the required services. Another advantage of the proposed IDMS is that it preserves the integrity of security tokens through using an xml-signature. Moreover, it employs TLS/SSL communication protocols to provide confidentiality for transactional information issued by the IDP and the SP. However, the claim-based IDMS violates user privacy, as it requires presenting the user credentials to the identity selector. One more disadvantage of the IDMS is that it requires users to undergo the authentication procedures each time before a security token can be issued, leading to extra unwanted overhead for the user.
A research project published in [9] proposed several frameworks for IDM. Although the proposed approach provided advantages in terms of facilitating the management of user identity, it poses privacy concerns. Specifically, it allows the Identity Provider (IDP) to monitor users’ movements, as the IDP can track all the Service Providers (SPs) accessed by each user.
Shibboleth, a Federated IDMS, and its single sign-on framework were presented in [10]. The proposed IDMS seeks to enhance by the user privacy by maintaining anonymity through the use of short-term random IDs. However, this approach involves a great risk since it may connect the users to untrusted or fake IDPs, which increases the possibility of stealing the sensitive credentials information.
In [11], researchers released an open-source IDMS called OpenID system. The proposed IDMS allows the user to utilize the OpenID-enabled SPs. However, the proposed IDMS is susceptible to the risk of credential theft, and the man-in-the-middle (MITM) attack.
Another claim-based IDMS was proposed in [12]. Researchers implemented proof-of-authenticity and a challenge–response method to mitigate the problem of the malicious IDP, which may cause considerable damage to the SP and the user. The proposed IDMS demonstrated notable improvements compared to its counterparts in terms of protecting the users’ privacy.
The research studies reviewed in the literature included various features that enhanced the efficiency and security of IDMSs; however, they also presented several challenges related to user privacy. The challenges found in the previous literature included data disclosure [8], user monitoring, credential theft [9], the man-in-the-middle attacks, and the presence of fake parties [11]. Furthermore, a single point of failure (SPOF) remains a critical issue associated with the centralized Identity Management (IDM) approaches that were discussed in this section.
The next section presents state-of-the-art studies that adopted a decentralized approach for IDMS using blockchain technology.
2.3. Blockchain-Based IDMSs
In [13], the authors utilized a private permissioned blockchain to develop IDMS suitable for Internet of Things (IOT) applications. The Hyperledger Fabric blockchain was used for smart homes. The proposed IDMS uses smart contracts to perform identity registration, identity verification, and identity revocation efficiently. The proposed approach enhanced IOT entities communications by including an identity management protocol. The study demonstrated that the use of private blockchain to develop IDMS has advantages in terms of security and scalability. However, the use of private blockchain exposes the system to the risk of SPOF and central authority issues.
The Hyperledger Indy blockchain was utilized to develop a decentralized IDMS for public transportation based on self-sovereign identity principles [14]. The proposed system provides users with more control over their identities and allows us to create multiple decentralized identifiers for the user.
Another decentralized IDMS was proposed in [15] for the public sector in South Korea. The proposed system includes a mobile application to create electronic ID cards, which are issued and managed by a national central authority. The users’ identity information is stored on their devices and can be verified through the blockchain. Researchers used the Hyperledger Fabric V1.0 to increase the privacy level. Although the proposed system uses blockchain, it inhibits problems related to traditional or centralized IDMSs, as it requires a centralized authority to manage and control users’ data. This might not be appropriate for many applications like an e-commerce system. Moreover, relying on a centralized unit to manage and verify data exposes the system to the SPOF risks.
Authors in [16] used blockchain and smart contract technologies to design a cross-domain self-IDMS. They used three types of smart contacts to manage the different functions, including issuing the users’ identity information and recovering the login credentials. While the proposed IDMS demonstrates superior performance compared to many other previously proposed IDMSs, it does have limitations regarding user data availability when users are not connected to the system. This limitation arises because the system requires storing all users’ information on their local devices. Another research project referenced in [13] explored the use of blockchain technology to improve data management and security in the healthcare sector. The project employed a hybrid methodology that combines the blockchain and a centralized database to enhance the security of healthcare records and make them accessible to an authorized party through the decentralized blockchain technology. The use of blockchain allows enhanced user identity verification and to avoid the SPOF problem. However, the proposed approach introduces potential risks to data confidentiality, as it uses the user’s log in credentials to decrypt sensitive data. If these credentials are cracked or intercepted by an attacker, they could easily access confidential information. In [17], researchers proposed a framework based on blockchain and machine learning algorithms. The framework primarily aims to solve problems related to centralized IDMS, such as centralized access control (AC) and SPOF, and improve the users’ privacy. The proposed approach utilized machine learning algorithms to improve the access control mechanism and detect any AC rules which do not satisfy the security policy.
A permissioned blockchain-based IDMS was introduced in [18]. The proposed system contributes to solving the key distribution and authentication issues in e-health systems. Moreover, authors applied a mutual authentication equation and achieved anonymity by making the user’s identity hidden, which enhances the privacy level. Authors in [19] presented a blockchain-based IDMS to solve problems in traditional centralized e-banking systems. The proposed IDMS utilized the concept of self-sovereign identity in the open banking operations to provide efficient authentication mechanism and improve users’ privacy.
Researchers in [20] introduced a blockchain-based authentication scheme and asymmetric key encryption to secure data transferred through communication channels between connected vehicles. They applied elliptic curve cryptography (ECC) to improve the performance of cryptographic operations and increase transaction pseudonymity. Another study proposed a protocol based on the Ethereum blockchain to secure a communication network for vehicles. While the proposed protocol improved the privacy of vehicle information, the system’s scalability is affected due to the large volume of information stored in the blockchain. In [21], a blockchain-based anonymous reputation system (BARS) was introduced to enhance the privacy and trust between connected vehicles in the network. Authors in [17] proposed a proof-of-concept IDMS for the internet of things (IoT). The proposed IDMS used blockchain and smart contract technologies to ensure integrity of data transferred between connected devices. Another research that utilized the blockchain to address security challenges in IoT was introduced in [22]. The proposed approach uses the Hyperledger fabric blockchain to develop a decentralized IDMS that enhances the authentication, and authorization processes and eliminates the SPOF issues.
The research referenced in [23] explored enhancing certificate management in the food supply chain by developing a self-sovereign decentralized IDMS. The proposed system uses blockchain technology to manage certificates issuance and verification processes. Additionally, the Inter Planetary File System (IPFS) was used to store data off chain, which improves the performance and scalability of the system. Another research [24] implemented the Hyperledger Fabric blockchain to enhance transactions tracking and data security for the supply chain system.
To improve supply chain security, the authors in [25] also implemented a Hyperledger Fabric framework to ensure each registered device in the supply chain is tracked and to improve system security. One more research [26] explored the use of a permissioned blockchain and smart contracts to enhance the management of identity information over the supply chain system and provide users with more control over their identity information. Moreover, the proposed system increases identity protection by using cryptographic proof techniques.
A number of research works attempted to utilize blockchain features to improve privacy and trust in healthcare E-Systems. In [27], researchers used the Ethereum blockchain to identify and authenticate the users’ identity in healthcare electronic applications, while in [28], authors proposed a decentralized access management system using blockchain. Authors of [29] introduced a blockchain-based IDMS combined with the zero-knowledge proof (ZKP) algorithms to improve the privacy and identity management in healthcare E-Systems. There was also an attempt to solve problems related to centralized authentication and authorization processes in IoT by using a Hyperledger Fabric blockchain and smart contracts. Authors of [30] attempted to improve users’ privacy in healthcare systems by using a permissioned Hyperledger Fabric blockchain. In [31], researchers proposed a DNS-IDMS architecture that is implemented on Ethereum’s permissioned blockchain to address the threats to users’ privacy and provide them with more control over their identities.
Private blockchain prototype was proposed in [32] to address security challenges in large-scale IoT systems that use centralized database. The authors demonstrated that the use of distributed ledger technology addresses issues related to access control and improves the flexibility and adaptability of the system. An Ethereum-based IDMS cloud protocol was proposed by [33], which was an improved version of CIDM (Consolidated Identity Management). Researchers showed that the proposed protocol has the potential to solve the third-party reliance problem that is encountered by traditional IDMSs. Also, smart contracts were used in the proposed IDMS to ensure the privacy of data and enhance the system flexibility.
An improved method based on Ethereum for signing transactions was proposed by [34]. The method tries to solve the users’ movement tracking problems by allowing them to delete their data and discard their identity afterward. Another research in [35] proposed an Attribute Trust-enhancing Identity Broker (ATIB) architecture to enhance the trust in E-Systems. In [36], the authors proposed a method that uses the distributed identity provider technology with blockchain and smart contracts to improve the privacy of users in IDMSs. Researchers in [37] explored the use of a cryptographic authentication scheme along with blockchain to enhance the security of the authentication process. Researchers introduced an implementation of a permission blockchain with attribute-based access control (ABAC) and an identity-based signature (IBS) in order to improve the security of IoT by avoiding the threats of SPOF, information leaks, and Distributed Denial of Service (DDoS). Previous research studies investigated improving identity authentication in healthcare E-Systems by using permissioned blockchains [18]. Researchers demonstrated that the blockchain has potential to avoid MITM attacks and secure key distribution operations. The authors of [38] proposed a fine-grained access control scheme based on the blockchain to improve the security of Vehicular Ad Hoc Network (VANET) data sharing. Smart contract technology is also employed to increase the scalability of the proposed system. Another research attempt in [39] presented an application of a private blockchain based on Hyperledger Fabric in the agricultural sector. The research aimed to secure communication between the different entities and eliminate reliance on a third party.
The next section introduces the system prototype for the proposed blockchain-based IDMS for enhanced privacy and security.
3. Proposed Blockchain-Based IDMS Prototype
This study involved conducting a comprehensive review of both centralized and decentralized IDMS solutions to identify the current gaps and issues. The theoretical research showed potential for blockchain technologies and relevant features to address these gaps and enhance the privacy of IDMS. Various blockchain technologies were analyzed, leading to the selection of the public blockchain Ethereum due to its permissionless nature, smart contract functionality, and mining process accessibility. The proposed IDMS utilizes Ethereum blockchain features to mitigate centralized IDMS issues, such as reliance on a central authority [13,15,40], third-party involvement [30], or privacy concerns related to data disclosure [16,41].
The prototype implementation of the proposed IDMS was conducted using the Goerli blockchain as a test net, Solidity for smart contract development, and a React-Web3 project for wallet integration. The smart contract was deployed via Remix. Furthermore, several tools and algorithms were employed to ensure user privacy and data confidentiality, including hash functions to verify data integrity and Elliptic Curve Integrated Encryption Scheme (ECIES) for encrypting user data, ensuring only authorized access to sensitive information.
The following section elaborates on the role of the smart contract technology that was adopted in the proposed approach.
3.1. Smart Contracts
The smart contract plays a crucial role in the IDMS by facilitating core functions and enhancing privacy. It protects user privacy by enabling private communication between parties. Users interact with SPs via smart contracts, improving privacy, speed, and system performance by self-execution. Additionally, smart contracts reduce reliance on third parties, which enhances privacy and minimizes information disclosure. The system actors include User, SP, and Admin (IDP). Each actor’s role and relationship were clearly defined, with one global smart contract managing the system.
The proposed IDMS approach was evaluated based on its ability to improve privacy and address security challenges in traditional IDMSs. The next section outlines the system design and implementation details.
3.2. System Design and Implementation
This section presents the various design components and implementation environment for the enhanced IDMS. It highlights the role of the proposed design in improving privacy and security features.
3.2.1. System Objectives
This research developed a blockchain-integrated IDMS prototype to achieve decentralization and empower users with full control over data exposure. The objectives of the proposed IDMS include:
- ▪
- Addressing centralized IDM challenges: centralization, SPOF, third-party control, data disclosure, and user tracking.
- ▪
- Utilizing blockchain features: decentralization, distribution, and P2P communication to eliminate central control and user tracking.
- ▪
- Enhancing privacy using smart contracts to enable direct user-to-SP communication without third-party involvement.
- ▪
- Implementing ECIES encryption to protect user attributes from unauthorized access and improve the performance of cryptographic operations.
The next subsection details the integration solution for IDMS and blockchain, which is adopted in this study.
3.2.2. IDMS and Blockchain Integration Solution
Blockchain offers decentralization, transparency, integrity, anonymity, and data encryption. By integrating IDMS with blockchain, this study aims to achieve the following:
- ▪
- Ethereum public blockchain ensuring user control without hierarchical authority.
- ▪
- Distributed architecture eliminating SPOF risks.
- ▪
- Smart contracts facilitating private user-SP interactions, bypassing third parties.
- ▪
- Service tokens containing encrypted attributes signed by the admin, ensuring privacy.
- ▪
- Minimum data disclosure principle combined with ECIES encryption for user anonymity and protection.
The subsections below introduce implementation environment and system design for the proposed blockchain-based IDMS.
3.3. Implementation Environment
The decentralized IDMS prototype was developed using the Ethereum blockchain. Tools and technologies include Web3, React [42], and MetaMask [43], with Goerli test network for system testing. The prototype was built on a Dell laptop (Intel Core i5-11320H, 8 GB RAM (Intel, Santa Clara, CA, USA)).
3.4. System Design
This study introduces a prototype that employs blockchain technology for decentralized IDM implementation. Smart contracts are integral to system functions and privacy enhancement. ECIES encryption ensures heightened user privacy.
The decentralized IDMS features a smart contract owned by the IDP/Admin, without access to actual data. User attributes are signed before transmission, with only hashed attributes stored on-chain. The system relies on user-controlled tokens rather than individual contracts. These encrypted and signed tokens ensure security and efficiency, leveraging AES symmetric encryption for faster performance.
The system supports secure service exchanges between users and SPs using encryption and decryption mechanisms. Our proposed system includes three main actors: Admin, SP, and User. It should be mentioned that Admin has the same role as identity provider (IDP) in the proposed IDMS. In the following, we list a brief description of the functions assigned to each actor.
- ▪
- Admin (IDP) functions:
Token management: Verify and sign received tokens.
Add service providers: Register SPs by adding addresses to the system.
- ▪
- User functions:
Add attributes, create encrypted service tokens, and request signature verification.
Generate tokens containing general attributes (e.g., for gaming/shopping) without requiring an admin signature.
- ▪
- SP functions:
Receive, decrypt, and verify service tokens without third-party involvement.
The overall system design and functions are depicted in Figure 1.
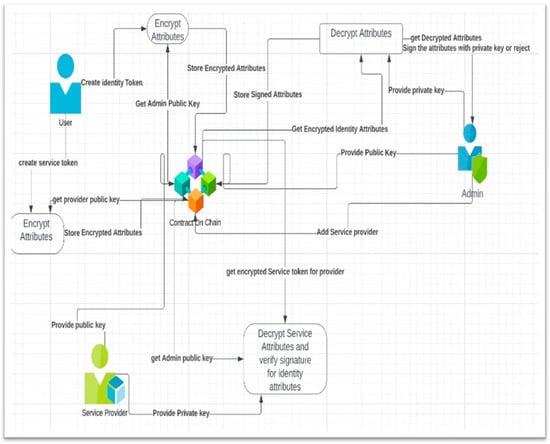
Figure 1.
Proposed IDMS design and functions.
The following section introduces cryptography algorithms and techniques adopted in this study to ensure privacy and minimum data disclosure.
- ▪
- The InterPlanetary File System (IPFS):
The IPFS technology was employed in the proposed IDMS to offer the capability for off-chain data storage. IPFS is preferable due to its content-addressable and decentralized architecture. Unlike traditional centralized cloud storage solutions, IPFS ensures data integrity by using cryptographic hashes as content identifiers, enabling verifiable and tamper-proof storage. This makes IPFS an ideal choice to be used with the IDMS in this research.
However, IPFS requires external pinning services or local electronic devices to maintain long-term data availability. This can incur additional costs and creates a tradeoff in terms of persistent access.
3.5. ECIES and Minimum Data Disclosure
The encryption and decryption of user attributes in the proposed system follow the following steps:
- The user encrypts attributes using ECIES, which employs the user’s private key and the IDP’s public key to generate a shared secret that is fed to the KDF. Then, the KDF derives the AES shared key for encryption.
- On the IDP side, the decryption key is generated using the IDP’s private key and the user’s public key in a similar method adopted in step 1. This allows the IDP to decrypt and verify the hash using the AES shared key. The IDP signs each attribute, re-encrypts them, and returns them to the user, storing only the hash on-chain.
- The user encrypts the service token (containing IDP-signed attributes) using ECIES, now utilizing the user’s private key and the SP’s public key. The SP decrypts the service token and verifies the IDP signature with the IDP’s public key, without direct involvement from the IDP.
- Attributes are encrypted individually to adhere to the minimum data disclosure principle. The user selects which information to include in the service token, allowing for a mix of signed and unsigned attributes (e.g., a username requiring a signature, but a nickname for gaming or shopping not requiring one).
The following section presents key processes performed by each actor in the proposed IDMS’s environment.
3.6. System Processes
The main actors in the proposed IDMS are the user, admin, and service provider (SP). Each actor interacts with the system according to processes described in the following subsections.
3.6.1. User Page
The user adds attributes to create an identity token by encrypting sensitive attributes and sending them to the admin for decryption, signing, and return. Encryption and signing occur per attribute rather than in bulk to ensure minimal data disclosure. The user communicates with SPs independently, preventing admin tracking. While the admin signs multiple user tokens and attributes, they cannot determine which SP the user contacts. The system process begins as follows:
- ▪
- The user adds attributes and encrypts them by clicking the Encrypt button.
- ▪
- The admin provides a public key to facilitate ECIES encryption by clicking Provide Public Key.
- ▪
- After encryption, the admin receives a token to sign the user attributes.
The user identity page in the proposed IDMS is shown in Figure 2.
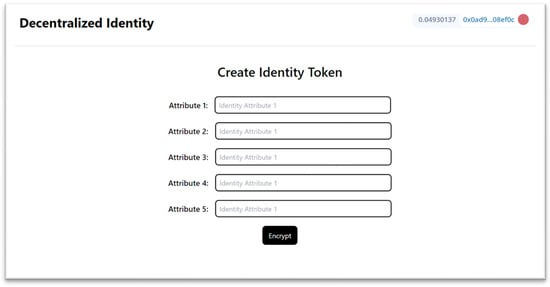
Figure 2.
User identity page in the proposed IDMS.
The following subsection presents admin processes in the proposed IDMS.
3.6.2. Admin Side
The key processes allowed for the system admin can be described as follows:
- ▪
- The admin retrieves a token by clicking Get Token, selecting the token ID, and decrypting attributes individually.
- ▪
- Decryption is performed per attribute, allowing the user to selectively send attributes.
- ▪
- Encrypted and decrypted attributes are displayed for signature completion.
- ▪
- Once all attributes are decrypted, the admin verifies and signs them using Verify and Sign.
- ▪
- After signing, the admin clicks Save Signatures to store attribute hashes on-chain while never storing the actual attributes.
- ▪
- The user then creates a service token by selecting a SP address, adding extra service attributes if necessary, and choosing which signed attributes to include.
- ▪
- The user can set a token expiration date and encrypt the service token with ECIES using the SP’s public key. The token is then automatically sent to the SP.
The admin page in the proposed system prototype is depicted in Figure 3.
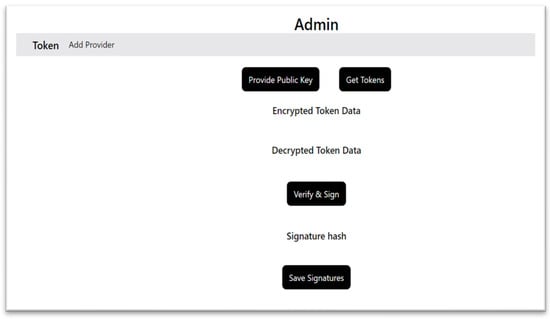
Figure 3.
Admin page in the proposed IDMS.
Figure 4 shows an example for creating the signature of the hashed user attributes. This function is allowed for the admin in the proposed IDMS.
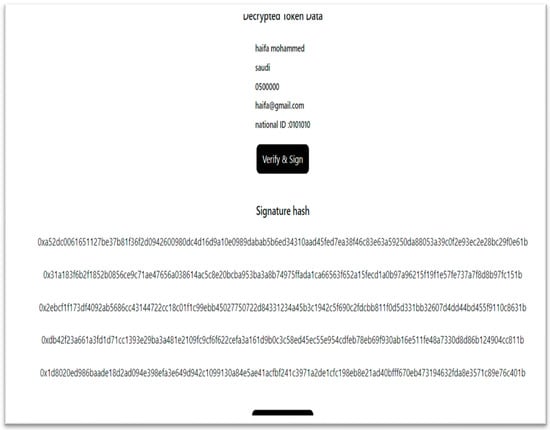
Figure 4.
Creating the signature hash in the proposed IDMS.
Figure 5 shows an example for encrypting and decrypting user attributes in the proposed IDMS.
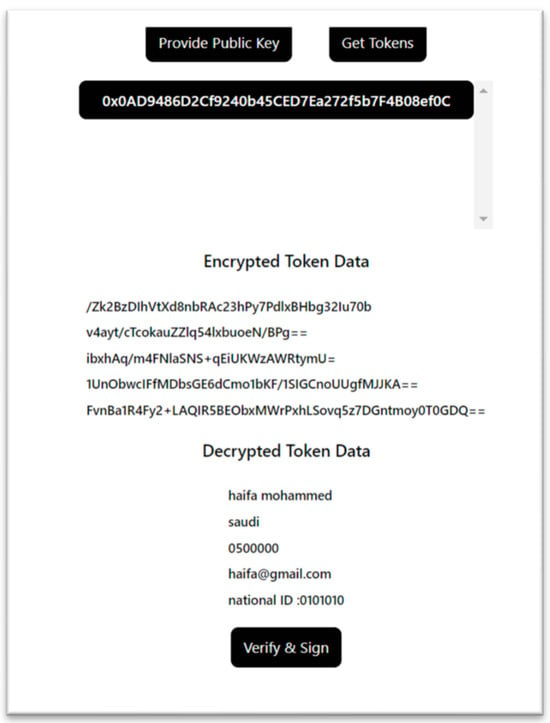
Figure 5.
Encrypting and decrypting user attributes in the proposed IDMS.
The following subsection presents the main processes permitted by the system for the SP.
3.6.3. SP Side
In the following, a description of the main processes available for SPs in the proposed IDMS:
- ▪
- The SP receives the service token, which appears on their page.
- ▪
- The SP decrypts the token by clicking its address, revealing user service attributes and verified signed attributes.
- ▪
- A message confirms verification.
The following subsection highlights the importance of verifying the identity token by the identity provider. This technique is adopted in the proposed IDMS.
3.7. Identity Token Verification
In the proposed IDMS, the identity token is, overall, verified by the identity provider. This ensures that all attributes in the token are IDP-signed. The SP verifies the admin signature by clicking Verify Hash. If any signed attributes are modified, verification fails; otherwise, it succeeds, confirming the token’s integrity and authenticity without third-party involvement or tracking.
3.8. IDMS Workflow
This subsection aims to clearly illustrate the operational logic and interaction among the primary components of the proposed IDMS. Figure 6 depicts the system workflow diagram, which shows the key actors, such as User, admin (IDP), and Service Provider (SP). Additionally, the diagram shows the main technologies used in the proposed system, including smart contracts, ECIES encryption, Hashing Module, Metamask Wallet, and the Ethereum blockchain.
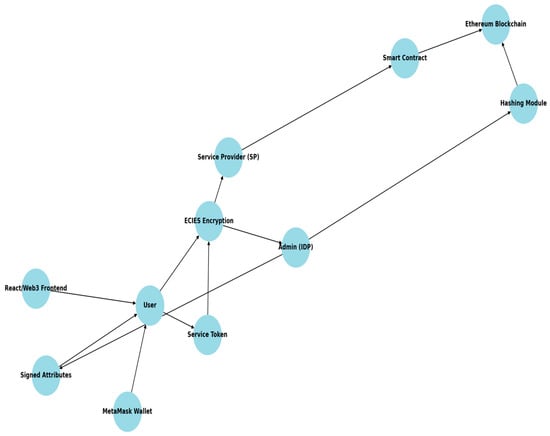
Figure 6.
Flowchart for the proposed blockchain-based IDMS.
The User is the primary actor in the proposed IDMS. The user has full control over their identity attributes. The user initiates the process by encrypting personal attributes and then sending them to the Admin. Upon receiving encrypted attributes from the user, the Admin decrypts these attributes, verifies them, and signs approved user’s attributes. Then, the admin encrypts and sends back the signed attributes to the user. It is worth mentioning that only hashes of the user’s data are stored on-chain for enhanced security and performance. The Admin uses the hashing function to produce the hash code of the user’s data, which ensures integrity. Moreover, all actors in the IDMS utilize ECIES encryption to secure attributes, thus ensuring confidentiality and privacy. The SP is the third actor in the proposed IDMS. The SP receives the service token from the user, decrypts it, and then verifies the Admin’s signature on the attributes.
The Ethereum blockchain is a crucial technology involved in the IDMS. The blockchain is used to store signed attribute hashes and smart contract data. This distributed ledger technology protects the IDMS from major threats such as SPOF and unauthorized modification. The proposed IDMS utilizes a service token, which is composed by the user from signed attributes and may include expiration rules. The token is encrypted by the user and sent to the SP. Another technology employed by the proposed IDMS to enable the user interaction with the system is the decentralized frontend built using React and Web3.js. Also, the proposed system utilizes the MetaMask wallet to enable the user to manage the key and interact with the Ethereum network.
4. Result and Discussion
The proposed system for utilizing blockchain technology for digital IDM demonstrated several positive results compared to previous studies in the same field. This section discusses all the solutions offered by the current study, as well as the improvements that have been achieved.
4.1. Proposed Solutions and Achieved Improvements
The following subsections outline the proposed solutions in this research and highlight the improvements achieved.
4.1.1. Decentralization and SPOF Mitigation
Traditional IDM systems suffer from centralization, leading to security risks such as a Single Point of Failure (SPOF). Our system addresses this issue using Distributed Ledger Technology (DLT), ensuring that even if one peer fails, others continue functioning and maintain a trusted copy.
4.1.2. Eliminating Third-Party Control
Centralized IDMSs often rely on Certificate Authorities (CAs) or third parties, leading to privacy risks such as user tracking. Some systems require users to obtain a token from a third party before accessing a service, allowing the third party to monitor interactions. Our system eliminates third-party control by leveraging smart contracts, enabling users to create and manage their tokens independently. Communication occurs through smart contracts, ensuring service providers remain undisclosed to the IDP, preserving privacy.
4.1.3. Enhanced Data Privacy and Minimal Disclosure
Our system implements the principle of minimal data disclosure, allowing users to specify which attributes appear in the service token. Instead of revealing all attributes, encryption and signing occur individually. Users can also define expiration dates for tokens, ensuring their data is protected post-service. All data is encrypted using ECIES, preventing plaintext exposure on the public blockchain.
4.1.4. Identity Theft Prevention
Users remain anonymous within the system, as each has a unique blockchain address for operations. Every transfer is signed with the sender’s ID address. If a token is stolen and reused, the system verifies the sender’s signature, rejecting unauthorized transactions. Additionally, encrypted service attributes ensure secure data exchange, allowing SPs to verify identity attributes via the IDP’s hashed data.
4.2. Security Analysis
This section provides detailed security analysis for the current approach, highlighting the main contributions of the proposed IDMS towards improving privacy and security.
4.2.1. Single Point of Failure (SPOF)
Suppose that our blockchain system consists of four peers (A, B, C, D). There was a glitch in the peer system (B), and this peer was no longer able to deal with the transactions, fetch data, or even add new blocks. The rest of the peers continued to work normally and added many blocks. After fixing the peer (B), there was a process of adding a new block when it arrived and was added. An error was detected in the hash chain of the blocks, so all the remaining peers (A, C, D) will compare their string with the chain of peer (B), and then the correct chain is copied to it to get back on the right track. Therefore, a single point of failure has no probability because the system is completely distributed to all peers.
4.2.2. 51% Attack
In the same example as above, for this attack to occur, three out of four peers in the system must be hacked to make modification or deletion of the block possible without the possibility of detection by the rest of the peers. Therefore, for this attack to occur, more than half of the peers in the system must be hacked, which is very rare because of the use of the public blockchain, which involves large number of participants, and it is very difficult to hack 51% of them [18,44].
4.2.3. Man-in-the-Middle Attack
In our system, we used ECIES encryption twice, once using the public key of the admin with ECIES to encrypt attributes and send it the admin, and the other time using the public key of the SP with ECIES when sending the service token. In this way, even if the conversation is hacked and the token is stolen, the hacker will not be able to decrypt it until he can obtain the private key of the receiver and the same random key from the KDF to generate the shared key of the decryption.
4.2.4. Anonymity
Each user in the system has their own blockchain address that they use as an identity within the system, and this allows them to maintain anonymity throughout the system and hide their real identity from others which is very important to the user so they will not be known to the other SPs. For example, the service provider and the user act in our system using the following identities:
0x0D700A6C62f93a83a48e627C1E352520aC7758f6
0x0AD9486D2CF9240B45CEDA272F5B7F4B08efOC
4.2.5. Integrity
Data within the block cannot be deleted or modified, which ensures data integrity and security, as any modification or deletion of one of the blocks in the chain will cause the hash for the rest of the chain to be destroyed as well, and that will be detected automatically from all the blockchain peers. In our system, the SP can verify the admin or IDP signature on user attributes by clicking on (verify hash) which will verify the hash by using the IDP public key, and any change in any character of the attributes will lead to verification failure, as shown in Figure 7.
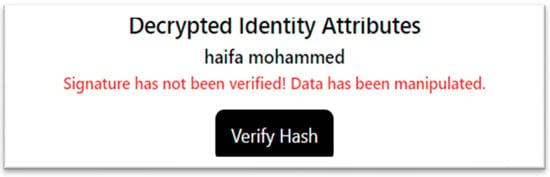
Figure 7.
Attribute verification failed.
4.2.6. Privacy
The user’s data is protected from redundant data disclosure in our system by applying the minimum data discloser principle, by allowing the user to select the specific attributes to be included in the service token in addition to setting an expiration date to the token to be invalid, so that the user can prevent their data from being disclosed multiple times. Also, using the ECIES encryption will protect the user data from being public to anyone. The proposed IDMS demonstrates enhanced privacy and provides more control for users over their attributes and personal data compared to other solutions presented in the literature such as in [45].
4.2.7. Security
Storing system data on the blockchain has many advantages, including achieving more decentralization, increasing the data integrity, because it cannot be deleted or modified. However, it poses a serious problem when it comes to storing private data due to the fact that it will be publicly accessible. In our system we use ECIES to encrypt the data and store the hash of it on the chain only to prevent data breaches.
The system has many advantages gained from integrating with blockchain technology, which improve system performance and increase user privacy by using ECIES encryption. But it is natural that there will be some limitations, such as scalability and transaction speed compared to the private blockchain, in addition to the user private key loss issue which we will try to come up with solutions for to improve in future.
The following section discusses the functionalities and enhanced security provided by cryptographic algorithms used in the proposed approach. A comparison of different algorithms is introduced to justify the selection of the cryptographic scheme adopted in this study.
4.3. The Use of ECIES
By using the ECIES encryption algorithm, system efficiency can be improved. The algorithm facilitates encryption and decryption with the same key without the need to share it between parties. To begin, the sender creates an encryption key using their private key, the receiver’s public key, and a random key. The sender then sends the encrypted message and random key to the receiver without sending the encryption key (which is also the decryption key). The receiver can then generate the decryption key using their private key, the sender’s public key, and the random key. This method ensures that even if the random key is compromised, an outside party cannot generate the decryption key without also obtaining the receiver’s private key. Figure 8 shows the ECIES keys generation test.
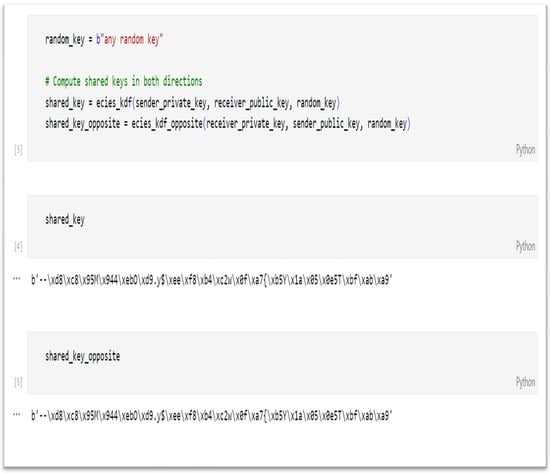
Figure 8.
ECIES keys generation test.
4.4. ECIES and ECDSA Algorithms Comparison
Initially, ECDSA with RSA was used for encryption, where user identity encryption was performed using the IDP’s public key and decrypted with the private key. Similarly, encryption for SPs was performed with the SP’s public key and decrypted using its private key. However, this method caused delays due to reliance on public key cryptography.
To improve performance, we adopted ECIES, which uses shared key encryption. The encryption process takes the receiver’s public key, the sender’s private key, and a shared secret, passing them through a key derivation function (KDF) to generate an AES encryption key. The decryption process uses the sender’s public key, receiver’s private key, and the shared secret to derive the AES decryption key.
The comparison below highlights the differences in processing speed and gas consumption between the two encryption methods. The results are further visualized in the following charts:
- ▪
- Pie Chart—Gas Consumption Comparison
This chart illustrates the proportion of gas consumed by ECIES and ECDSA with RSA. ECDSA with RSA consumes significantly more gas compared to ECIES (about 63.3% vs. 36.7%).
- ▪
- Line Chart—Time Comparison of Encryption Methods
This chart compares the execution time of both encryption methods across five different measurements. ECDSA with RSA takes longer on average, while ECIES exhibits more stable and slightly lower execution times.
Table 1 shows comparison between the different encryption algorithms in terms of time-consumption and gas cost.

Table 1.
Encryption algo-comparison.
Figure 9 Illustrates gas consumption results for both encryption methods. It is obvious that the use of ECIES and ECDSA with ECIES is more efficient since they consume less gas compared to the ECDSA with RSA method.
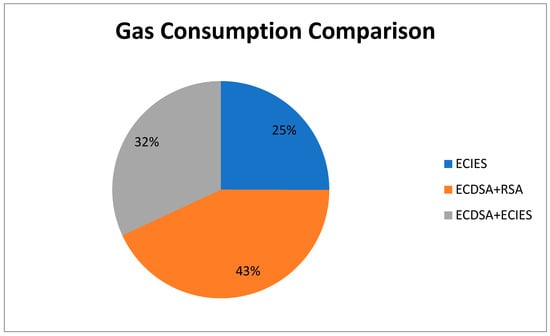
Figure 9.
Gas consumption comparison.
Figure 10 shows a comparison between the ECIES, ECDSA with ECIES, and ECDSA with RSA methods in terms of time consumption. It is obvious that the ECIES and ECDSA with ECIES methods achieve higher performance because they require less time to perform cryptographic operations compared to the ECDSA with RSA method.
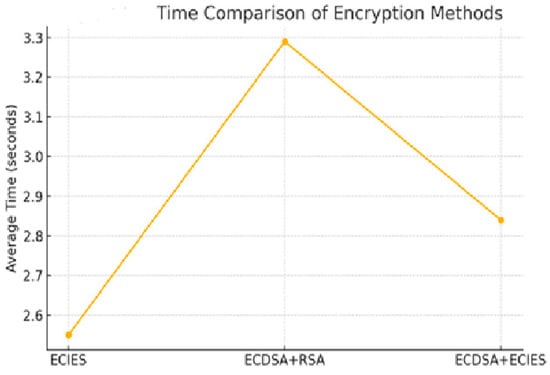
Figure 10.
Time comparison of encryption methods.
The next section illustrates the alignment of the proposed system with known threat models.
4.5. Alignment of the Proposed IDMS with the STRIDE Threat Model
To ensure a structured evaluation of the proposed IDMS’s security, this study applied the STRIDE threat modeling framework, developed by Microsoft. The STRIDE model categorizes cybersecurity threats into six major domains: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service (DoS), and Elevation of Privilege [46]. In the following, we provide a brief discussion illustrating how the proposed IDMS complies with essential security standards mentioned in the STRIDE model:
- (1)
- Spoofing: Spoofing was mitigated through Ethereum address-based identity binding and cryptographic signatures.
- (2)
- Tampering: The threat of tempering data was addressed by storing hashed attributes on-chain, where any unauthorized modification triggers verification failure.
- (3)
- Repudiation: This threat was handled by using digitally signed transactions and attributes that are recorded immutably on the blockchain, providing an auditable history. Thus, the use of cryptographic digital signature offers non-repudiation service effectively.
- (4)
- Information Disclosure: The threat of information disclosure was effectively minimized via ECIES encryption and the principle of minimum data disclosure adopted in the proposed IDMS. Only hashed or encrypted data is exposed to offer enhanced privacy and confidentiality.
- (5)
- Denial of Service: This threat was reduced by using a decentralized network (Ethereum public blockchain), ensuring redundancy.
- (6)
- Elevation of Privilege: This threat is prevented through strict role definitions enforced by smart contracts, which define access and verification capabilities for Admins, Users, and service providers.
This alignment with the STRIDE threat model provides a formal basis to validate that the proposed IDMS is resistant to common threat categories in blockchain environments.
4.6. Limitations of the Proposed IDMS
While the proposed IDMS achieved enhanced privacy, decentralization, and user control, there are limitations related to scalability and throughput. The proposed IDMS relies on the public Ethereum blockchain, which suffers from scalability issues. The transaction throughput for such type of blockchain is also limited, affecting the real-time usability of the blockchain-based IDMS. One more limitation is related to transaction fees. The use of smart contracts and data storage on the Ethereum blockchain incurs gas fees and additional costs. This may hinder widespread adoption of the proposed IDMS, especially for applications requiring frequent interactions and smart contract transactions.
The research conclusion and main future research directions relevant to this study are presented in the next section.
5. Conclusions
A digital identity is crucial for online interactions, particularly for delivering essential services. Authentication of users is essential for government agencies, businesses, and digital services for various purposes, such as service access, customer identification, and security monitoring. Therefore, protecting digital identities and user privacy becomes vital. Most Identity Management Systems (IDMSs) operate in a centralized manner, which limits user control over their data due to reliance on a Certificate Authority (CA) or third-party entities. Additionally, centralized IDMS face Single Point of Failure (SPOF) risks, increasing security vulnerabilities. Also, third-party reliance threatens user privacy by enabling tracking and behavioral monitoring. Previous decentralized solutions for IDMS have utilized private blockchains; however, these still introduce centralization risks as they restrict decision-making to a limited group rather than all users, affecting decentralization. Moreover, some decentralized IDMSs face challenges related to weak authentication, scalability, information exposure, and performance.
This research introduced a prototype implementation for a decentralized IDMS by leveraging the public blockchain and smart contract technologies. The proposed IDMS addresses key issues, including privacy, centralization, third-party control, tracking, and SPOF. Additionally, the ECIES encryption algorithm was incorporated with the implementation of the proposed IDMS to offer an extra layer of security, prevent data disclosure, and improve system performance.
Future research will explore different features to improve the system efficiency, including the methods to recover the user’s identity in cases where the private key is lost. Moreover, more experiments will be conducted to explore system-level performance and scalability under variety of load factors, as well as the potential integration with real-world identity frameworks.
Author Contributions
Conceptualization, H.M.A. and M.A.; methodology, H.M.A. and M.A.; software, H.M.A.; validation, M.A.; formal analysis, H.M.A. and M.A.; investigation, H.M.A. and M.A.; resources, H.M.A. and M.A.; data curation, H.M.A.; writing—original draft preparation, H.M.A. and M.A.; writing—review and editing, M.A.; visualization, H.M.A. and M.A.; supervision, M.A.; project administration, M.A.; funding acquisition, M.A. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported and funded by the Deanship of Scientific Research at Imam Mohammad Ibn Saud Islamic University (IMSIU) (grant number IMSIU-DDRSP2504).
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Acknowledgments
Authors gratefully acknowledges the support of the Deanship of Scientific Research at Imam Mohammad Ibn Saud Islamic University (IMSIU) for funding and facilitating this research.
Conflicts of Interest
The authors declare no conflicts of interest.
Correction Statement
This article has been republished with a minor correction to the existing affiliation information. This change does not affect the scientific content of the article.
Abbreviations
The following abbreviations are used in this manuscript:
| IDMS | Identity Management System |
| ECIES | Elliptic Curve Integrated Encryption Scheme |
| SP | Service Provider |
| IDP | Identity Provider |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| KDF | Key Derivation Function |
| DLT | Distributed Ledger Technology |
| SPOF | Single Point of Failure |
References
- Aitzhan, N.; Svetinovic, D. Security and Privacy in Decentralized Energy Trading through Multi-Signatures, Blockchain and Anonymous Messaging Streams. IEEE Trans. Dependable Secur. Comput. 2016, 15, 840–852. [Google Scholar] [CrossRef]
- Castiglione Maldonado, F. Introduction to Blockchain and Ethereum: Use Distributed Ledgers to Validate Digital Transactions in a Decentralized and Trustless Manner; Packt Publishing: Birmingham, UK, 2018. [Google Scholar]
- Joshi, J.; Nepal, S.; Zhang, Q.; Zhang, L.-J. Blockchain—ICBC 2019. In Proceedings of the Blockchain—ICBC 2019: Second International Conference, Held as Part of the Services Conference Federation, SCF 2019, San Diego, CA, USA, 25–30 June 2019; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Bao, Z.; Wang, Q.; Shi, W.; Wang, L.; Lei, H.; Chen, B. When Blockchain Meets SGX: An Overview, Challenges, and Open Issues. IEEE Access 2020, 8, 170404–170420. [Google Scholar] [CrossRef]
- L’Amrani, H.; Berroukech, B.; Ajhoun, R.; El Idrissi, Y. Identity Management Systems: Laws of Identity for Models′ Evaluation. In Proceedings of the 2016 4th IEEE International Colloquium on Information Science and Technology (CiSt), Tangier, Morocco, 24–26 October 2016. [Google Scholar]
- Jøsang, A.; AlZomai, M.; Suriadi, S. Usability and Privacy in Identity Management Architectures. In Proceedings of the Fifth Australasian Symposium on ACSW Frontiers, Ballarat, Australia, 30 January–2 February 2007. [Google Scholar]
- Agudo, I. Digital Identity and Identity Management Technologies. Serbian Publ. InfoReview Joins UPENET Netw. CEPIS Soc. J. Mag. 2010, XI, 6–12. [Google Scholar]
- Alrodhan, W.; Mitchell, C. Improving the Security of CardSpace. EURASIP J. Inf. Secur. 2009, 2009, 1–8. [Google Scholar] [CrossRef][Green Version]
- Alrodhan, W. Privacy and Practicality of Identity Management Systems: Academic Overview; Vdm Verlag Dr. Müller: Saarbrücken, Germany, 2011. [Google Scholar]
- Ferdous, M.S.; Poet, R. A Comparative Analysis of Identity Management Systems. In Proceedings of the 2012 International Conference on High Performance Computing & Simulation (HPCS), Madrid, Spain, 2–6 July 2012. [Google Scholar]
- Dai, Z.; Zhou, W.; Deakin University, School of Information Technology. The Federated Identity and Access Management Architectures: A Literature Survey; Deakin University, School of Information Technology: Geelong, VIC, Australia, 2005. [Google Scholar]
- Alrodhan, W.; Mitchell, C. Enhancing User Authentication in Claim-Based Identity Management. In Proceedings of the 2010 International Symposium on Collaborative Technologies and Systems, Chicago, IL, USA, 17–21 May 2010. [Google Scholar]
- Bouras, M.; Lu, Q.; Dhelim, S.; Ning, H. A Lightweight Blockchain-Based IoT Identity Management Approach. Future Internet 2021, 13, 24. [Google Scholar] [CrossRef]
- Stockburger, L.; Kokosioulis, G.; Mukkamala, A.; Mukkamala, R.; Avital, M. Blockchain-enabled Decentralized Identity Management: The Case of Self-sovereign Identity in Public Transportation. Blockchain Res. Appl. 2021, 2, 100014. [Google Scholar] [CrossRef]
- Sung, C.; Park, J. Understanding of blockchain-based identity management system adoption in the public sector. J. Enterp. Inf. Manag. 2021, 34, 1481–1505. [Google Scholar] [CrossRef]
- Niu, J.; Ren, Z. A self-sovereign identity management scheme using smart contracts. MATEC Web Conf. 2021, 336, 08005. [Google Scholar] [CrossRef]
- Outchakoucht, A.; Es-Samaali, H.; Philippe, J. Dynamic Access Control Policy based on Blockchain and Machine Learning for the Internet of Things. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 417–424. [Google Scholar] [CrossRef]
- Xiang, X.; Wang, M.; Fan, W. A Permissioned Blockchain-Based Identity Management and User Authentication Scheme for E-Health Systems. IEEE Access 2020, 8, 171771–171783. [Google Scholar] [CrossRef]
- Liao, C.-H.; Guan, X.-Q.; Cheng, J.-H.; Yuan, S.-M. Blockchain-Based Identity Management and Access Control Framework for Open Banking Ecosystem. Futur. Gener. Comput. Syst. 2022, 135, 450–466. [Google Scholar] [CrossRef]
- Feng, X.; Cui, K.; Jiang, H.; Li, Z. EBAS: An Efficient Blockchain-Based Authentication Scheme for Secure Communication in Vehicular Ad Hoc Network. Symmetry 2022, 14, 1230. [Google Scholar] [CrossRef]
- Akhter, A.F.M.S.; Ahmed, M.; Shah, A.F.M.S.; Anwar, A.; Kayes, A.S.M.; Zengin, A. A Blockchain-Based Authentication Protocol for Cooperative Vehicular Ad Hoc Network. Sensors 2021, 21, 1273. [Google Scholar] [CrossRef] [PubMed]
- Figueroa-Lorenzo, S.; Añorga Benito, J.; Arrizabalaga, S. Modbus Access Control System Based on SSI over Hyperledger Fabric Blockchain. Sensors 2021, 21, 5438. [Google Scholar] [CrossRef]
- Cocco, L.; Tonelli, R.; Marchesi, M. Blockchain and Self Sovereign Identity to Support Quality in the Food Supply Chain. Future Internet 2021, 13, 301. [Google Scholar] [CrossRef]
- Cui, P.; Dixon, J.; Guin, U.; Dimase, D. A Blockchain-Based Framework for Supply Chain Provenance. IEEE Access 2019, 7, 157113–157125. [Google Scholar] [CrossRef]
- Wang, S.; Li, D.; Zhang, Y.; Chen, J. Smart Contract-Based Product Traceability System in the Supply Chain Scenario. IEEE Access 2019, 7, 115122–115133. [Google Scholar] [CrossRef]
- Ferdousi, T.; Gruenbacher, D.; Scoglio, C.M. A Permissioned Distributed Ledger for the US Beef Cattle Supply Chain. IEEE Access 2020, 8, 154833–154847. [Google Scholar] [CrossRef]
- Javed, I.T.; Alharbi, F.; Bellaj, B.; Margaria, T.; Crespi, N.; Qureshi, K.N. Health-ID: A Blockchain-Based Decentralized Identity Management for Remote Healthcare. Healthcare 2021, 9, 712. [Google Scholar] [CrossRef]
- Zhu, Y.; Huang, C.; Hu, Z.; Al-Dhelaan, A.; Al-Dhelaan, M. Blockchain-Enabled Access Management System for Edge Computing. Electronics 2021, 10, 1000. [Google Scholar] [CrossRef]
- Ra, G.; Kim, T.; Lee, I. VAIM: Verifiable Anonymous Identity Management for Human-Centric Security and Privacy in the Internet of Things. IEEE Access 2021, 9, 75945–75960. [Google Scholar] [CrossRef]
- Stamatellis, C.; Papadopoulos, P.; Pitropakis, N.; Katsikas, S.; Buchanan, W.J. A Privacy-Preserving Healthcare Framework Using Hyperledger Fabric. Sensors 2020, 20, 6587. [Google Scholar] [CrossRef] [PubMed]
- Kassem, J.A.; Sayeed, S.; Marco-Gisbert, H.; Pervez, Z.; Dahal, K. DNS-IdM: A Blockchain Identity Management System to Secure Personal Data Sharing in a Network. Appl. Sci. 2019, 9, 2953. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. BlendCAC: A Smart Contract Enabled Decentralized Capability-Based Access Control Mechanism for the IoT. Computers 2018, 7, 39. [Google Scholar] [CrossRef]
- Wang, S.; Pei, R.; Zhang, Y. EIDM: A Ethereum-Based Cloud User Identity Management Protocol. IEEE Access 2019, 7, 115281–115291. [Google Scholar] [CrossRef]
- Gutierrez-Aguero, I.; Anguita, S.; Larrucea, X.; Gomez-Goiri, A.; Urquizu, B. Burnable Pseudo-Identity: A Non-Binding Anonymous Identity Method for Ethereum. IEEE Access 2021, 9, 108912–108923. [Google Scholar] [CrossRef]
- Gruner, A.; Muhle, A.; Meinel, C. ATIB: Design and Evaluation of an Architecture for Brokered Self-Sovereign Identity Integration and Trust-Enhancing Attribute Aggregation for Service Provider. IEEE Access 2021, 9, 138553–138570. [Google Scholar] [CrossRef]
- Moreno, R.T.; Garcia-Rodriguez, J.; Bernabe, J.B.; Skarmeta, A. A Trusted Approach for Decentralised and Privacy-Preserving Identity Management. IEEE Access 2021, 9, 105788–105804. [Google Scholar] [CrossRef]
- Sun, S.; Du, R.; Chen, S.; Li, W. Blockchain-Based IoT Access Control System: Towards Security, Lightweight, and Cross-Domain. IEEE Access 2021, 9, 36868–36878. [Google Scholar] [CrossRef]
- Li, H.; Pei, L.; Liao, D.; Chen, S.; Zhang, M.; Xu, D. FADB: A Fine-Grained Access Control Scheme for VANET Data Based on Blockchain. IEEE Access 2020, 8, 85190–85203. [Google Scholar] [CrossRef]
- Desabathina, N.V.M.; Merugu, S.; Gunjan, V.K.; Kumar, B.S. Agricultural Crowdfunding Through Blockchain. In ICDSMLA 2020; Kumar, A., Senatore, S., Gunjan, V.K., Eds.; Springer: Singapore, 2022; Volume 783. [Google Scholar]
- Verhelst, R. Implementing SSI: Comparing Uport, Sovrin and IRMA. Available online: https://info.vismaconnect.nl/blog/different-approaches-ssi (accessed on 12 February 2023).
- Bouras, M.A.; Lu, Q.; Zhang, F.; Wan, Y.; Zhang, T.; Ning, H. Distributed Ledger Technology for eHealth Identity Privacy: State of The Art and Future Perspective. Sensors 2020, 20, 483. [Google Scholar] [CrossRef] [PubMed]
- Banik, R. Tutorial: Building a web3 Frontend with React. 2021. Available online: https://medium.com/scrappy-squirrels/tutorial-building-a-web3-frontend-with-react-e0a87ea3bad (accessed on 12 February 2023).
- Docs, M. Introduction|MetaMask Docs. Available online: https://docs.metamask.io/guide/ (accessed on 12 February 2023).
- Frankenfield, J. 51% Attack. 2019. Available online: https://www.investopedia.com/terms/1/51-attack.asp (accessed on 16 February 2023).
- Das, D.; Dasgupta, K.; Biswas, U. A secure blockchain-enabled vehicle identity management framework for intelligent transportation systems. Comput. Electr. Eng. 2023, 105, 108535. [Google Scholar] [CrossRef]
- Shostack, A. Threat Modeling: Designing for Security; John Wiley & Sons: Hoboken, NJ, USA, 2014. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).