1. Introduction
Recent breakthroughs in quantum computing underscore the escalating vulnerabilities of current cryptographic algorithms. The potential for quantum computers to break widely used 2048-bit RSA keys within hours [
1], exemplified by advancements such as the Willow processor from Google (Mountain View, CA, USA) [
2,
3], suggests cryptanalytic quantum capabilities may emerge within 5–10 years. This necessitates the accelerated deployment of post-quantum cryptographic (PQC) solutions.
Traditional public-key algorithms such as RSA and Elliptic Curve Cryptography (ECC) are vulnerable to Shor’s algorithm [
4,
5]. While symmetric algorithms such as AES-256 offer more resilience against Grover’s algorithm, their key distribution often relies on vulnerable public-key methods. The security of all cryptographic systems also critically depends on high-quality random number generation. Traditional pseudo-random number generators (PRNGs) can have vulnerabilities [
6], whereas true random number generators (TRNGs) harnessing physical entropy offer stronger security.
Research has intensified on PQC algorithms and secure TRNGs. Kyber, a Key Encapsulation Mechanism (KEM) based on the Module Learning With Errors (MLWE) problem, was selected by NIST for PQC standardization [
7], ensuring intellectual property accessibility [
8]. Concurrently, TRNG technology has advanced, with various hardware implementations demonstrating high throughput and resilience [
9,
10,
11,
12]. However, challenges remain in achieving optimal randomness, cost-effectiveness, and robust integration of TRNGs with PQC frameworks, especially on accessible hardware.
FPGA-based System-on-Chips (SoCs) like the Xilinx Zynq family (San Jose, CA, USA) offer a flexible platform for cryptographic systems, combining programmable logic (PL) for hardware acceleration with processing systems (PSs) for control [
13,
14,
15]. This paper leverages this architecture to propose a high-security hybrid cryptosystem on a Zynq UltraScale+ MPSoC platform. Our work introduces three key innovations:
A Multi-Level Hardware TRNG: A TRNG based on a multi-level Ring Oscillator (RO) architecture (5, 7, 9, and 11 inverter stages) with three-level pooling, delivering 49.6 Mbps of entropy and passing NIST SP 800-22 tests.
The FA-Kyber Framework: Flow-Adaptive Kyber, integrating Kyber768-KEM with hardware-assisted network traffic monitoring for adaptive, dual-trigger (time/volume-based) key updates and robust exception handling.
High-Performance Encrypted Data Transmission: An FPGA-accelerated AES-256-GCM module achieving over 550 Mbps secure data transmission.
Our integrated system (
Figure 1) balances performance, resource utilization, and post-quantum security. The remainder of this paper is organized as follows:
Section 2 details the methodology,
Section 3 presents the experimental results, and
Section 4 discusses these findings, their implications, and limitations. Finally,
Section 5 summarizes the key contributions and concludes the work.
2. Materials and Methods
This section details the theoretical foundations, system design, implementation specifics, and evaluation methodologies employed in this work.
2.1. Mathematical Notation and Kyber-KEM Overview
This subsection establishes the mathematical foundations for our quantum-resistant cryptographic system, covering notation conventions and the Kyber Key Encapsulation Mechanism implementation details.
Notation and Definitions
The ring of integers modulo a prime q is denoted by . The polynomial ring is defined with and . Polynomials in are denoted by bold lowercase letters (e.g., ). Vectors and matrices with entries from (i.e., elements of modules such as or ) are also denoted by bold letters; context usually distinguishes vectors (e.g., ) from matrices (e.g., ). The i-th coefficient of a polynomial is denoted by (using a non-bold symbol for the polynomial when referring to its coefficients, or if itself is a single polynomial).
The product of two polynomials is denoted by . Coefficient-wise multiplication is denoted by ∘. Kyber utilizes the Number Theoretic Transform (NTT) for efficient polynomial multiplication. The NTT of a polynomial is denoted by . Polynomial multiplication using the NTT is computed as , where and are the forward and inverse transforms, respectively. Byte arrays of a specific length, say , are denoted by . The i-th bit of an element is denoted by .
2.2. Kyber Key Encapsulation Mechanism (Kyber-KEM)
Kyber is an IND-CCA secure Key Encapsulation Mechanism based on the Module Learning With Errors (MLWE) problem [
7]. The MLWE problem involves finding a secret vector
and error vector
(small coefficients sampled via Centered Binomial Distribution, CBD) from samples
, where
has uniformly random coefficients in
. This work uses Kyber768 (NIST Security Level 3), with
, providing security comparable to AES-256.
Key Generation. Two random seeds, , are used. An extendable output function (XOF) expands to matrix (stored as in NTT domain). generates secret vector and error vector from CBD. The public key is . The private key is .
Encapsulation. To generate a shared secret and ciphertext, new random values
,
, and
(from CBD) are sampled. A random message
is also generated. The ciphertext components are
Message is encoded (e.g., to polynomial ) and combined with to form v (e.g., ). The shared key is , where is a hash function. The ciphertext comprises compressed versions of and v.
Decapsulation. The recipient uses to recover from , typically by recomputing parts of the encapsulation and verifying to ensure IND-CCA security.
Implementation Optimizations. The efficiency of Kyber operations critically depends on NTT and modular reduction algorithms. Our implementation employs Cooley–Tukey for forward NTT and Gentleman–Sande for inverse NTT, leveraging their complementary data flow to eliminate reordering overhead [
16]. For modular arithmetic with fixed
, Barrett reduction outperforms Montgomery reduction by avoiding domain conversion costs while enabling precomputed reciprocals [
17,
18].
2.3. System Hardware Architecture and Data Flow
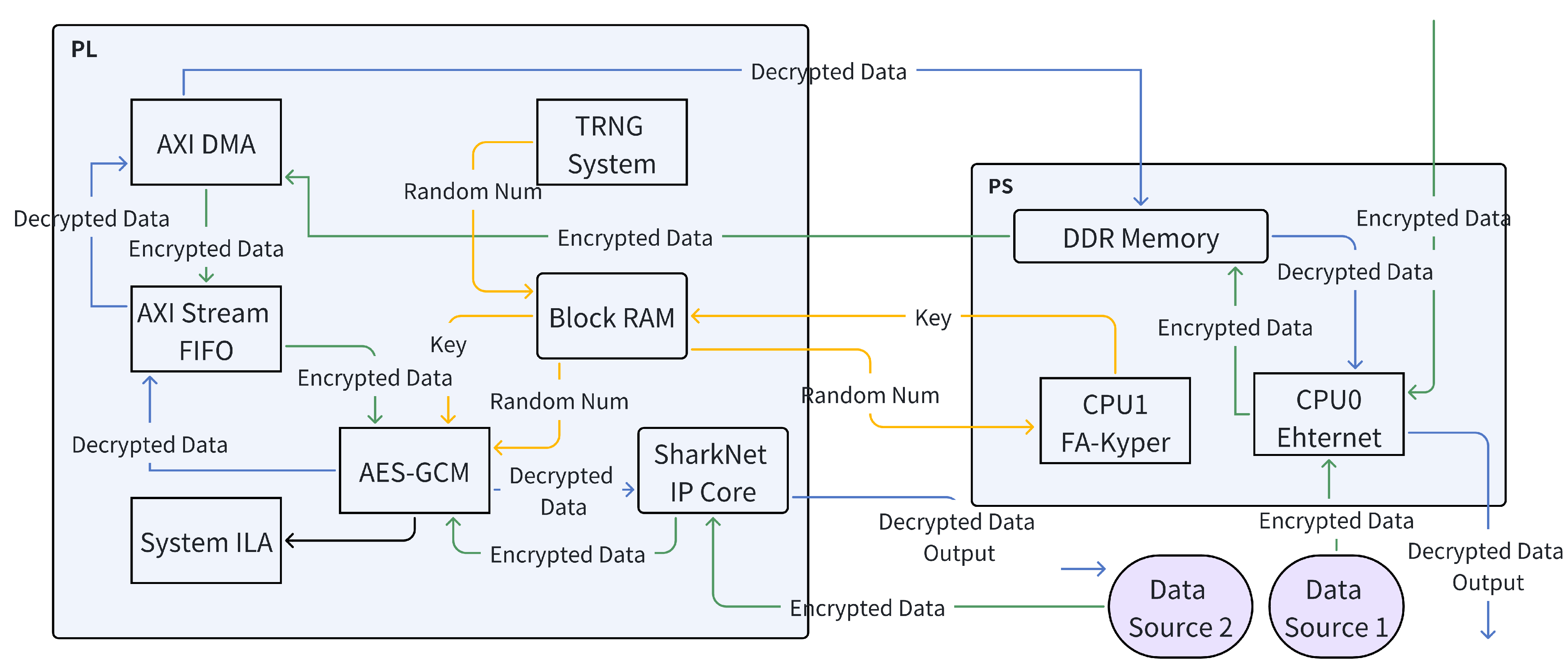
The hardware data flow for the cryptographic system’s transmitter and receiver operations is depicted in
Figure 2 and
Figure 3, respectively. These figures illustrate the integration of AES encryption, the TRNG, and network interfaces within the Zynq MPSoC’s processing system (PS) and programmable logic (PL).
As shown in
Figure 2 (transmitter), data originating in the PS (managed by CPU0 for Ethernet and CPU1 for FA-Kyber) is transferred via AXI DMA to the PL. Here, an AXI Stream FIFO buffers data before encryption by the AES-GCM core. The TRNG supplies random numbers for AES-GCM (e.g., IVs). Encrypted data is then prepared for network transmission, potentially through a specialized IP core (e.g., SharkNet, for specific protocols beyond standard Ethernet) or standard Ethernet, and can also be routed to PS DDR memory.
Figure 3 (receiver) shows incoming encrypted data being decrypted by the PL’s AES-GCM core. Decrypted data is then transferred via AXI DMA back to the PS for CPU processing or storage in DDR memory.
This architectural design strategically partitions tasks: High-speed cryptographic operations (AES acceleration, TRNG entropy generation) are implemented in the PL for parallelism and efficiency. Complex control logic, including Kyber-KEM key management (FA-Kyber framework) and higher-level network protocol handling, resides in the PS. This PS-PL separation is crucial for achieving both high performance and enhanced security, as further discussed regarding implementation security in
Section 4.3.3.
2.4. FA-KYBER Framework Design and Implementation
The Flow-Adaptive Kyber (FA-KYBER) framework integrates the Kyber-KEM with network-adaptive key management strategies. It utilizes the Zynq UltraScale+ MPSoC’s Generic Ethernet MAC (GEM) controller, incorporating a Traffic-Sensing Trigger (TST) mechanism to dynamically adjust key update thresholds based on network conditions.
2.4.1. Traffic-Sensing Threshold (TST) Mechanism
Unlike existing adaptive key management approaches that rely on CPU load monitoring [
19] or fixed-interval rotation [
20], FA-KYBER introduces network-traffic-aware adaptation. Previous systems ignore network-layer attack indicators or require expensive SDN controller overhead [
21]. Our hardware-register-based monitoring achieves <1% CPU utilization while providing multi-metric threat assessment, representing one of the first frameworks to couple network characteristics with post-quantum key rotation frequency.
The TST mechanism dynamically adjusts the key update threshold using Equation (
3):
Here,
is a baseline data volume, and coefficients
and
balance responsiveness to average bandwidth
(detailed in
Section 2.4.3) and the current transmission volume ratio
. The policy enforces volume-based, time-based (e.g., a maximum interval), and anomaly-based (via GEM error counters) triggers for key updates.
The mathematical formulation in Equation (
3) represents a constrained optimization problem that is well-suited for linear programming solutions. The model exhibits favorable computational properties: the logarithmic bandwidth term
can be linearized through piecewise approximation techniques [
22], while the traffic ratio
maintains inherent linearity. Given bounded parameters (
,
,
), the solution space remains convex and computationally tractable [
23,
24].
Parameter optimization for
and
can be achieved through regression analysis on historical traffic patterns, where the objective function minimizes prediction error while maintaining system responsiveness [
25]. This linear modeling approach aligns with established frameworks for adaptive threshold optimization in network security, demonstrating superior performance over static methods in balancing detection accuracy and computational overhead [
26,
27].
To enhance practical robustness, the TST mechanism incorporates dual-layer validation logic. To minimize false positives, it requires anomalous behavior to persist across multiple consecutive monitoring windows, distinguishing genuine threats from transient network fluctuations. To counter false negatives, especially from low-rate attacks, it cross-validates bandwidth-based metrics with hardware error counter monitoring (e.g., RXCRCERR), providing a more comprehensive detection capability based on established anomaly detection and adaptive threshold principles [
28,
29].
The TST interfaces directly with the GEM controller’s hardware performance registers. Accessing these memory-mapped counters allows precise traffic measurement with negligible performance impact, unlike software-based monitoring. A non-blocking polling mechanism samples RXCNT and TXCNT registers, handling overflows and ensuring reliable, concurrent monitoring without packet delays.
2.4.2. Decentralized Device Discovery and Key Exchange Coordination
A decentralized coordination mechanism using Address Resolution Protocol (ARP) tables enables peer discovery and key exchange coordination, enhancing resilience by avoiding central authorities. To prevent collisions and ensure a unique active exchange per pair, a deterministic initiator selection (based on lexicographically smaller MAC address) is used. The system extends ARP scanning with state management to track device transitions and maintain key state synchronization.
2.4.3. Adaptive TST Algorithm Implementation
The TST value (Equation (
3)) is calculated in two phases. First, current bandwidth (
) is measured using GEM hardware counters (RXCNT, TXCNT) over an interval
:
where
denotes the change from the previous interval. Second, average bandwidth (
) is updated via an Exponential Weighted Moving Average (EWMA):
with weighting factor
. Accumulated transmission volume is tracked precisely, handling counter overflows. Numerical stability is ensured via bounds checking and logarithm domain validation. Key updates are triggered if (1) the volume exceeds the TST threshold; (2) a maximum time (e.g., 4 h) elapses; or (3) GEM error counters detect abnormal network behavior (
Section 2.4.5).
2.4.4. Key Update Protocol Implementation
The key update protocol follows a three-phase approach for decentralized security and efficiency.
Initiation: Kyber-KEM processing starts when a time-based or TST-based threshold is met. The exchange initiator is determined by MAC address comparison (
Section 2.4.2), preventing collisions.
Exchange: Nodes communicate over an encrypted channel using messages with session identifiers, timestamps, and authentication codes. Staged buffers optimize message processing and reduce cryptographic memory operations.
Verification: A verification sequence confirms successful key establishment before transitioning to the new key. A dual-key buffer maintains current and pending keys within a transition window (e.g., 10 ms ± 5 ms tolerance) for continuous secure operation.
Exception Handling: A three-tiered recovery (immediate retry, then attempts at increasing intervals, e.g., 500 ms, 5000 ms) addresses failures. Consistent timing mitigates side-channel risks. Communication flags enable seamless fallback to pre-shared keys during sustained failures, maintaining security state awareness.
2.4.5. Network Performance Monitoring for Adaptive Security
The FA-KYBER framework employs multiple network metrics from GEM hardware registers for adaptive key management with minimal overhead. Beyond throughput (via RXCNT/TXCNT sampling), it monitors CRC errors (RXCRCERR) and length errors (RXLENERR) as indicators of potential network manipulation. If these error rates exceed adaptive thresholds, the system enters an elevated security state, accelerating key rotation.
Adaptive error thresholds are calculated dynamically based on historical data using a sliding window approach with efficient online statistics. A circular buffer maintains the last
W error observations for each monitored type (CRC errors, length errors), where
W is dynamically configurable (default: 1000 samples). When new observations arrive, we use Welford’s incremental algorithm [
30] to update the mean (
) and standard deviation (
) without recomputing from scratch.
For each new observation , the running statistics are updated as follows:
- -
(current window size);
- -
;
- -
;
- -
;
- -
;
- -
.
The window size
W adapts to network conditions: 500–2000 samples based on traffic stability [
31]. When the buffer reaches capacity, new observations replace the oldest entries using modular indexing [
32]. This ensures
update complexity per new observation while maintaining statistical relevance. The adaptive threshold is
where
k is a sensitivity factor (e.g., 3.5). This statistical approach distinguishes normal fluctuations from potential attacks. Automatic recalibration every 24 h during low-traffic periods prevents drift from long-term environmental changes [
33].
A hysteresis mechanism prevents oscillation. To return to normal operation from an elevated state, error rates must fall below a recovery threshold
and remain there for a configurable period (e.g., three 5-minute monitoring cycles). These calculations are performed on the PS, using a circular buffer for historical data, conserving PL resources and allowing flexible parameter tuning.
To guard against poisoning attacks aimed at suppressing key updates, the design incorporates two key defenses inspired by research into the robust detection of advanced threats [
34]. First, the mandatory time-based trigger (e.g., max 4 h) acts as a fail-safe, preventing indefinite suppression of key rotation. Second, the adaptive threshold mechanism is hardened by bounding the statistical impact of outliers on the historical traffic baseline. This prevents an adversary from artificially inflating the TST threshold through malicious traffic injection, thus preserving detection sensitivity.
2.5. Multi-Level Hardware TRNG Design and Implementation
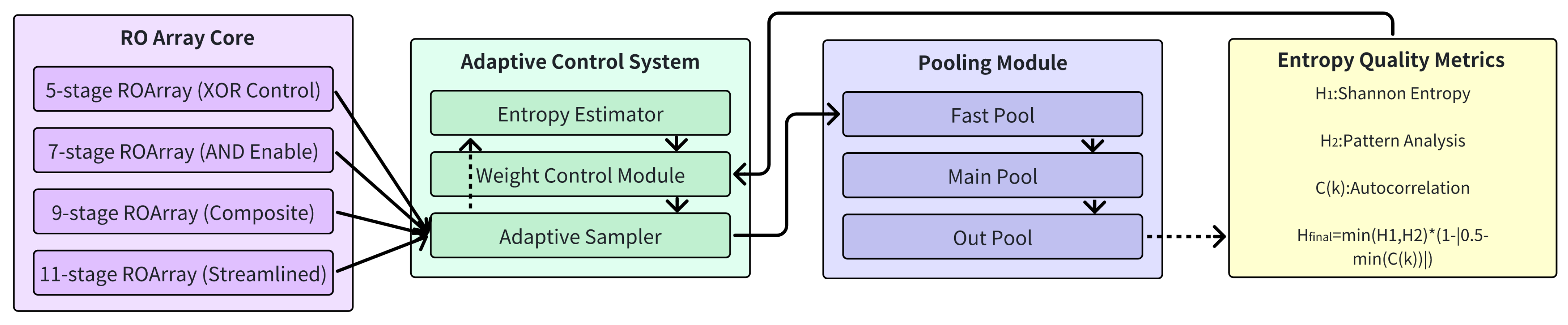
The True Random Number Generator (TRNG), a critical component for robust entropy, is based on a multi-level Ring Oscillator (RO) architecture within the FPGA, leveraging inherent physical noise. Key design principles include utilizing differentiated RO stages (5, 7, 9, and 11 inverters) as independent entropy sources and a multi-tier pooling architecture to refine raw entropy.
The TRNG’s structure, detailed in
Figure 4, comprises an RO Array Core, a Pooling Module, and an Adaptive Control System. This configuration aims to eliminate biases and produce a statistically sound random bitstream. The adaptive control system, with its entropy estimator and adaptive sampler, continuously monitors and adjusts TRNG parameters to maintain randomness quality under varying conditions.
Physical isolation of entropy sources is crucial. As depicted in
Figure 5, distinct RO configurations are spatially separated on the FPGA using Pblock constraints and careful placement. This “Physical Isolation Design” minimizes crosstalk and electromagnetic interference. The varied distributions (e.g., even, linear, staggered multi-row) for different RO types (5, 7, 9, and 11 stages) further enhance spatial diversity and the unpredictability of the TRNG output.
2.6. Security Analysis Methodology
The cryptosystem’s security was evaluated against classical and quantum-capable adversaries, based on established cryptographic principles and specific assessment methodologies tailored to its components and objectives.
2.6.1. Security Model and Assumptions
Our security model considers two attacker profiles: traditional attackers (classical resources, network attacks, limited by computational problem hardness) and quantum-capable attackers (access to large-scale quantum computers for Shor’s/Grover’s algorithms). This dual approach ensures comprehensive assessment towards goals of confidentiality, integrity, and availability. The analysis relies on four fundamental assumptions:
- (1)
The MLWE problem underlying Kyber remains intractable against quantum computers.
- (2)
AES-256, despite Grover’s algorithm, maintains sufficient security when combined with quantum-resistant key exchange.
- (3)
The TRNG (
Section 2.5) produces statistically random outputs verifiable by NIST SP 800-22 tests.
- (4)
PS-PL architectural separation on Zynq provides a degree of isolation against certain side-channel attacks.
The system aims for IND-CCA2 security for Kyber-KEM and AEAD security for AES-GCM, targeting at least 128-bit post-quantum security. Evaluation objectives include assessing these security levels, verifying TRNG quality, and analyzing the FA-KYBER’s adaptive key rotation for approximating forward secrecy by limiting key exposure.
2.6.2. Quantum Resistance Assessment
Quantum resistance was primarily assessed by
Confirming Kyber-768’s (NIST Level 3) 128-bit post-quantum security target and MLWE problem hardness against known quantum algorithms (e.g., Shor’s ineffectiveness).
Evaluating AES-256’s effective security (approx. 128-bit) under Grover’s algorithm.
Analyzing how FA-KYBER’s adaptive key rotation (limiting session key exposure time/volume) contributes to overall quantum resilience.
2.6.3. TRNG Security Evaluation
Statistical Randomness Verification: Subjecting output bitstreams to the NIST SP 800-22 test suite, using pass/fail and p-value distribution as metrics, with entropy estimation following NIST SP 800-90B [
35] for non-IID sources.
Adaptive Mechanism Review: Assessing the adaptive sampling mechanism’s role in maintaining entropy quality against environmental manipulation.
Physical Isolation Review: Examining layout strategies (Pblocks, spatial separation) for minimizing entropy source correlation and side-channel susceptibility.
2.6.4. Protocol-Level Security Assessment
FA-KYBER’s protocol-level security enhancements were assessed by examining the following:
The dual-trigger (time/volume-based) key update’s effectiveness in ensuring regular refreshes and limiting key exposure.
The TST mechanism’s potential as an integrated anomaly detector by reviewing its designed response to bandwidth anomalies, elevated CRC/length error rates. TST effectiveness was further evaluated by simulating network attacks (e.g., bandwidth exhaustion, probing) and observing system response against defined detection metrics.
The exception-handling protocol’s (graded retries, consistent timing) design for resisting timing analysis and ensuring continuity.
The pre-shared key fallback mechanism’s role in maintaining baseline security during sustained key exchange failures.
2.6.5. Implementation Security Design Considerations
Implementation security was addressed through the following design choices:
PS-PL separation for isolating Kyber-KEM (PS) from TRNG/AES (PL) to mitigate certain side-channel vectors.
RO TRNG physical design (Pblocks, clock domain separation,
Section 2.5) for entropy independence.
Standard software practices (secure clearing of sensitive data, consistent exception handling) to prevent information leakage.
FA-KYBER’s adaptive key rotation to limit single-key exposure windows, reducing side-channel attack viability.
While these architectural choices provide foundational security measures, a comprehensive quantitative assessment of side-channel attack resistance represents a critical limitation that must be acknowledged. Side-channel attacks, particularly power analysis attacks (Differential Power Analysis, DPA; Simple Power Analysis, SPA) and electromagnetic analysis, pose significant threats to cryptographic implementations [
36,
37]. Recent research has demonstrated successful attacks on both masked software [
38] and hardware implementations [
39] of Kyber-768, revealing vulnerabilities even in protected implementations using Boolean masking and other countermeasures.
Our current design incorporates several features that provide a foundation for side-channel resistance: the PS-PL architectural separation limits potential attack surfaces by isolating cryptographic operations across different domains; the multi-level RO TRNG’s physical design with spatial separation (
Section 2.5) reduces electromagnetic coupling between entropy sources; and the FA-KYBER framework’s adaptive key rotation inherently limits the temporal exposure window available for side-channel analysis. Nevertheless, dedicated countermeasures such as Boolean masking for polynomial operations [
40], constant-time implementations, and formal leakage assessment using standardized methodologies like the Test Vector Leakage Assessment (TVLA) [
41] would be essential for deployment in adversarial environments and represent important directions for future investigation.
2.7. Performance Evaluation Methodology
Comprehensive experiments evaluated the cryptosystem’s performance. This section details the hardware platform, network test environment, evaluation metrics, and specific test scenarios.
2.7.1. Hardware Platform and Test Environment
The system was implemented on AXU4EV-P development boards (ALINX, Shanghai, China) featuring a Xilinx Zynq UltraScale+ MPSoC (XCZU4EV-1SFVC784: quad-core ARM Cortex-A53 at 1.5 GHz, PL at 100 MHz, 8GB DDR4 SDRAM). A customized carrier board provided Gigabit Ethernet and other interfaces. Tests were controlled by a host PC (Intel Corporation, Santa Clara, CA, USA) running Ubuntu 22.04 and equipped with an Intel Core i9-12900K processor and 64GB RAM. The network environment comprised three AXU4EV-P boards in a star topology via a Gigabit Ethernet switch, with a baseline one-way delay of 0.8 ms (±0.3 ms jitter). Network congestion (20%, 50%, 80%) was simulated by running bandwidth-intensive applications on additional board pairs connected to the same switch, offering a realistic assessment of robustness without specialized simulation tools.
2.7.2. Evaluation Metrics
Key performance metrics included the following:
Encryption Throughput (Mbps): Rate of successfully processed data under various conditions.
Key Exchange Latency (ms): Time for Kyber-KEM operations during updates.
Service Interruption (ms or %): Impact of key updates on data flow.
End-to-End Encryption Latency (ms): Total packet processing time (encryption, transmission, decryption) for sizes of 64–8192 bytes.
Resource Utilization: PL (LUTs, BRAMs, DSPs) and PS (CPU load, memory) usage.
Power Consumption (W): Board power draw at idle and full load.
TRNG Quality: Output throughput (Mbps) and NIST SP 800-22 test suite results.
These metrics provide a holistic view of performance and operational characteristics.
2.7.3. Test Scenarios and Data Collection
System performance was evaluated under diverse conditions using the test scenarios summarized in
Table 1. Data collection involved PS-side cycle counters, a Vivado Design Suite (v2022.2) for PL resources, and combined hardware (GEM registers) and software statistics for network performance. Each test configuration was repeated 10 times for statistical validity. These scenarios were designed to ensure comprehensive and representative results.
3. Results
3.1. Overall System Performance
System performance was robust and consistent.
Table 2 shows encrypted data rates from a 2-h test series (10-minute key update intervals).
Across 10 independent 2-h tests, the system showed high stability (average throughput, 564.8 ± 7.2 Mbps; standard deviation (SD), 1.3% of the mean), confirming operational consistency. The consistently low latency (3.14 ± 0.10 ms) and high success rate (99.99 ± 0.01%) further affirm its reliability for real-world deployment.
3.1.1. Throughput Analysis Across Packet Sizes
Encryption throughput was evaluated for various packet sizes. For 64-byte packets (raw network throughput 86.1 Mbps), the encrypted throughput was 73.43 Mbps (85% efficiency). For larger packets (4096–8192 bytes, raw network throughput approaching 900 Mbps), consistent encryption throughput of 558–575 Mbps was maintained.
Figure 6 illustrates system throughput and encryption efficiency versus Ethernet packet size. Overall throughput increased with packet size due to reduced relative protocol overhead. Encryption efficiency (encrypted throughput/raw network throughput) peaked for smaller packets, and then decreased to 63% for 8192-byte packets as the system processing capacity became the bottleneck over the Gigabit Ethernet link.
3.1.2. Latency Characteristics
Table 3 details the system’s end-to-end latency components.
Baseline Ethernet latency averaged 0.683 ms (range: 0.465–0.810 ms). Encryption and key management added overhead, resulting in total end-to-end latencies from 1.8 ms (64-byte packets) to 5.7 ms (8192-byte packets). Average temporary service interruption during key updates was 78 ms. This minimal impact highlights the FA-KYBER protocol’s efficiency. Double buffering prevented packet loss during key transitions, maintaining a continuous data stream with only microsecond-level jitter.
3.1.3. System Stability and Resource Consumption
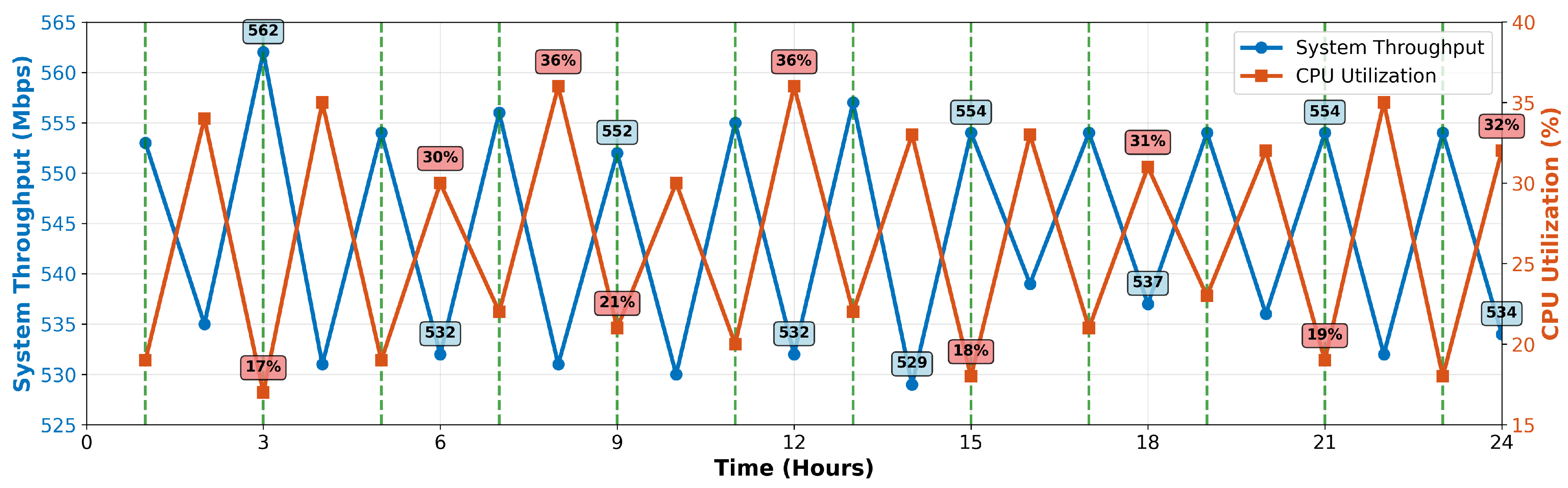
Figure 7 shows system throughput and PS CPU utilization during a 24-h stability test. Average throughput remained at 564 Mbps. CPU utilization peaked at 32–35% during key updates, remaining significantly lower otherwise, indicating efficient steady-state operation.
Power consumption varied minimally: 4.5 W idle (5V/0.90A) to 4.9 W full-load (5V/0.98A), showing good energy efficiency. MPSoC core temperatures stabilized between 50 °C and 62 °C under varying loads, well within specifications. Throughout the 24-h test, all 144 key updates were successful (100% rate), verifying operational reliability with frequent rotation. The TRNG maintained stable, high-quality entropy generation (verified by periodic NIST SP 800-22 tests). Zynq Performance Monitoring Unit (PMU) data corroborated efficient resource utilization.
3.2. Component-Level Performance Results
The performance of key individual hardware and software components was evaluated for a detailed understanding of their contributions.
3.2.1. TRNG Performance Results
The multi-level RO TRNG produced a stable 49.6 Mbps throughput. It successfully passed all NIST SP 800-22 statistical tests, with detailed
p-values in
Table 4.
Entropy contributions from distinct RO configurations were as follows: 5 stages (14.2 Mbps), 7 stages (12.8 Mbps), 9 stages (11.5 Mbps), and 11 stages (11.1 Mbps). This diversified output enhances overall randomness quality.
3.2.2. Encryption Engine and Kyber Operation Performance
The AES-256-GCM engine (extended from [
42]) achieved > 550 Mbps throughput using 7.2% FPGA logic resources on the Zynq UltraScale+ XCZU4EV. Engine latency included a 0.28 μs initialization and 0.15 μs per-block (32-byte) processing time. Software Kyber-768 on an ARM Cortex-A53 core showed efficient operation: key generation: 1.2
; encapsulation: 1.5
; and decapsulation: 1.7
(average). The peak PS memory footprint during key generation was 2.4 MB.
3.2.3. FA-KYBER Framework Adaptive Behavior
The FA-KYBER evaluation focused on key exchange efficiency and adaptive security response.
Key Exchange Efficiency. The average key exchange completion time (including Kyber-KEM and protocol overhead) was 74.3 , with 99.7% of it completed within 85 . Dual-key buffering prevented packet loss. Peak PS memory for an update cycle was 128 kB.
TST Mechanism Overhead. PS-based TST traffic monitoring consumed < 1% CPU utilization of its allocated core, due to direct GEM register access. Upon significant network changes (e.g., 20% to 80% congestion), TST recalculated and applied new key update thresholds (Equation (
3)) with an average response time of 1.8
post-detection.
Adaptive Security Response to Network Congestion. As shown in
Figure 8, increasing network congestion (0% to 90%) reduced throughput (from 565 Mbps to 39 Mbps). Concurrently, FA-KYBER increased key update frequency from time-based (e.g., 2/hour at low congestion) to a TST-driven maximum of 5/hour at ≥70% congestion, even as throughput further declined.
3.3. Security Analysis Findings
Key findings from the security evaluation (methodology in
Section 2.6) are presented.
3.3.1. Verification of Cryptographic Primitives and TRNG Quality
The Kyber-768 implementation was verified against test vectors and NIST specifications, confirming its Level 3 (128-bit post-quantum) security. AES-256-GCM was similarly verified for correct encryption, decryption, and authentication. As detailed (
Section 3.2.1,
Table 4), the TRNG passed all NIST SP 800-22 tests, providing high-quality randomness. Its adaptive sampling maintained stable entropy output under simulated environmental variations (voltage, ±15%; temperature, −40 °C to 85 °C during component stress tests).
3.3.2. Effectiveness of Protocol-Level Security Mechanisms
FA-KYBER’s TST mechanism demonstrated 93.7% detection accuracy across 150 simulated network attacks (bandwidth exhaustion: 96%; temporal analysis probes: 92%; replay attacks: 93%). Simulations used real network traffic baselines with superimposed attack traffic. The dual-trigger key update (time/TST-based) ensured regular refreshes, adapting to traffic conditions as observed in the 24-h test (
Section 3.1.3). The exception-handling protocol (<0.1% activation during tests) successfully recovered connections from transient issues.
During validation, the persistence-checking logic was observed to significantly reduce false positive triggers from transient network spikes. In simulated poisoning attack scenarios, the hardened baseline calculation successfully resisted manipulation attempts, and the mandatory time-based trigger provided a reliable backstop, confirming the effectiveness of the layered defensive mechanisms.
3.3.3. Assessment of Implementation Security Aspects
Architectural PS-PL separation was maintained, confining Kyber-KEM to PS and TRNG/AES to PL, verified through code review and testing against unauthorized data paths. RO TRNG physical design choices (Pblocks, etc.) were implemented per methodology (
Section 2.5). While direct side-channel leakage measurement was beyond the scope of this study, adaptive key rotation inherently limits exposure windows. Sensitive cryptographic materials were cleared from memory post-use (verified during debugging).
4. Discussion
The experimental results (
Section 3) validate the proposed quantum-resistant hybrid cryptographic system’s successful implementation and robust performance on the Zynq UltraScale+ MPSoC. This section interprets these findings, contextualizes them within existing research, outlines contributions and limitations, and suggests future research.
4.1. Interpretation of Overall System Performance
The system’s high throughput (>560 Mbps,
Table 2) and low standard deviation (1.3%) confirm its suitability and stability for bandwidth-intensive, post-quantum secure communications. The average end-to-end latency of 3.14 ms is acceptable for many interactive applications, with AES processing and system overheads identified (
Table 3) as primary contributors, suggesting avenues for further optimization. Critically, minimal service interruption (78 ms) during key updates, with no packet loss due to dual-key buffering, underscores the FA-KYBER framework’s effectiveness in maintaining both communication continuity and cryptographic agility. Throughput analysis across packet sizes (
Figure 6) revealed expected efficiency scaling, defining a practical performance envelope. Long-term stability tests (24-h,
Figure 7) demonstrated consistent throughput, successful key rotation, stable TRNG output, and manageable power/thermal characteristics (4.5 W idle, 4.9 W load), supporting its viability for mission-critical operations. Transient CPU spikes during key updates did not compromise stability, reflecting a balanced PS-PL task distribution.
4.2. Interpretation of Component-Level Performance and Design Choices
Individual component performance underpins the system’s overall efficacy and security.
4.2.1. Significance of TRNG Performance and Quality
The multi-level RO TRNG’s stable 49.6 Mbps throughput adequately meets the randomness demands for Kyber, AES-GCM IVs, and other cryptographic operations without becoming a performance bottleneck. Successfully passing all NIST SP 800-22 tests (
Table 4) provides strong evidence of high-quality, unpredictable random numbers, crucial for the cryptosystem’s security foundation. This robustness is likely enhanced by diversified noise sources from distinct RO configurations.
4.2.2. Implications of Encryption Engine and Kyber Operation Speeds
The AES-256-GCM engine’s >550 Mbps throughput with modest FPGA resource usage (7.2%) signifies efficient hardware acceleration, capable of handling high-bandwidth streams. Its low per-block latency (0.15 μs post-initialization) benefits delay-sensitive tasks. Kyber-768 software execution times on the ARM core (key generation: 1.2ms; encapsulation: 1.5ms; decapsulation: 1.7ms) are competitive for embedded PQC KEMs. While more intensive than traditional counterparts, these latencies are acceptable for secure session establishment given the enhanced quantum security, confirming Kyber’s feasibility on resource-constrained platforms.
4.2.3. Effectiveness and Novelty of the FA-KYBER Adaptive Framework
The FA-KYBER framework represents a significant advancement over static key management policies. Its dual-trigger (time and TST-based) mechanism provides a responsive approach. Key strengths include the TST’s low CPU overhead (<1%), leveraging hardware counters, and its adaptive threshold (Equation (
3)) with quick responsiveness (1.8s). The adaptive key update frequency under network congestion (
Figure 8), increasing up to five updates/hour, is particularly noteworthy as it actively reduces key lifetimes under stress, offering a practical enhancement to forward secrecy. This adaptive sophistication, surpassing fixed-interval/volume rotations, potentially offers superior security utility.
4.3. Interpretation of Security Analysis Findings and Implications
Security analysis (
Section 3.3) supports the system’s resilience against targeted classical and quantum threats, alongside its protocol and implementation robustness.
4.3.1. Confidence in Cryptographic Primitives and Randomness
Verified Kyber-768 and AES-256-GCM implementations ensure adherence to their designed security levels. Kyber-768 meeting the 128-bit post-quantum security target is central to the system’s quantum resistance. While Grover’s algorithm theoretically impacts AES-256 [
43], its remaining 128-bit effective security is widely considered adequate. The TRNG’s successful NIST SP 800-22 testing (
Table 4) is paramount, ensuring the entropy source is not an exploitable weak link. High-quality randomness is essential for all cryptographic secrets and nonces. The TRNG’s stability under simulated stress (
Section 3.3.1) suggests practical reliability, although comprehensive side-channel analysis would provide further assurance.
4.3.2. Effectiveness and Practicality of Protocol-Level Defenses
The FA-KYBER TST mechanism’s 93.7% detection accuracy against simulated network attacks (
Section 3.3.2) highlights its utility as an integrated, lightweight intrusion detection capability. This allows for proactive responses, such as more frequent key rotations, enhancing cryptographic agility. High detection rates for common disruptions like bandwidth exhaustion (96%) and replay attacks (93%) demonstrate good sensitivity. The appropriate triggering of key updates by both time- and TST-based mechanisms validates the dual-trigger design’s utility in ensuring both baseline key freshness and dynamic protection.
4.3.3. Implications of Implementation Security Measures
The verified PS/PL architectural separation (
Figure 2 and
Figure 3) provides a degree of defense-in-depth, making it more challenging for vulnerabilities in one domain to compromise the other. RO TRNG design choices (Pblocks, differentiated routing) represent practical efforts towards entropy source integrity. Standard practices like clearing sensitive cryptographic material from memory post-use reduce attack windows. Furthermore, FA-KYBER’s adaptive key rotation, by limiting key lifetimes, inherently reduces the value of a compromised key and the time available for attacks, complementing theoretical cryptographic strength.
4.4. Comparison with Existing Work
This research is contextualized by comparison with existing cryptographic solutions and TRNGs.
4.4.1. Comparison with Other Cryptographic Systems
The proposed system, with a >550 Mbps throughput and 256-bit post-quantum security (
Table 5), significantly advances practical PQC implementation on embedded platforms. While some traditional, non-quantum-resistant systems offer higher throughput (e.g., ZUC [
44]), and other embedded PQC efforts report lower performance or lack comprehensive integration [
14,
45,
46], our work distinguishes itself. The key differentiator is the holistic integration of high-throughput AES-256-GCM, robust Kyber-768, a hardware TRNG, and the adaptive FA-KYBER framework, addressing the full post-quantum secure communication lifecycle. This combination offers a practical, flexible solution with throughput surpassing that of many reported PQC systems for similar embedded platforms.
4.4.2. Comparison of TRNG Performance and Design
Our multi-level RO TRNG (49.6 Mbps, full NIST SP 800-22 compliance) compares favorably with recent designs (
Table 6). While some alternatives offer higher throughput (e.g., Meitei et al. [
12], but with partial NIST compliance) or use advanced fabrication (e.g., Park et al. [
9]), our TRNG strikes a practical balance of sufficient throughput, strong randomness, and implementability on standard FPGAs. The multi-level, adaptive sampling RO architecture is key to this balance.
4.4.3. Novelty in System Integration and Adaptive Key Management
A primary contribution is the synergistic integration of Kyber-KEM, AES-GCM, a quality TRNG, and the innovative FA-KYBER framework on an embedded SoC. To our knowledge, few existing works present such a comprehensive, end-to-end PQC system featuring both a validated hardware TRNG and dynamic, network-traffic-adaptive key rotation. While individual components are well-studied, their effective integration and the development of adaptive security mechanisms responsive to real-world network dynamics are critical for practical PQC deployment. FA-KYBER’s TST mechanism, in particular, offers intelligent, resource-efficient key lifecycle management, enhancing security by minimizing key exposure windows.
4.4.4. Brief Comparison with Related Approaches
Our approach differs from recent adaptive security frameworks [
47] that focus on malware detection without cryptographic integration. While SDN-based systems achieve good threat detection, they require continuous controller monitoring with higher overhead. FA-KYBER’s hardware-register approach achieves 93.7% anomaly detection with minimal resource consumption, specifically optimized for post-quantum environments where existing frameworks lack coverage.
4.5. Broader Implications and Significance
This work has several broader implications. It demonstrates the feasibility of deploying comprehensive, high-performance PQC systems on resource-constrained embedded platforms (FPGAs/SoCs), crucial for securing future IoT, industrial control, automotive, and edge computing applications. Achieving >550 Mbps encryption with robust key management and entropy generation on such devices indicates that PQC adoption need not be limited to high-end hardware. The FA-Kyber framework’s traffic-adaptive key management suggests a new approach to operational security, moving beyond static policies to dynamically respond to network conditions and potential threats. Its principles could inspire more intelligent, resilient security architectures, with the TST mechanism’s lightweight intrusion detection capabilities offering a path towards self-defending cryptosystems. Furthermore, demonstrating a reliable, high-throughput hardware TRNG using standard FPGA resources underscores the importance of building strong cryptographic foundations without resorting to exotic or expensive entropy sources, vital for cost-sensitive applications. Overall, this research provides a tangible blueprint for quantum-resistant, context-aware secure communication systems, bridging theoretical PQC development with practical, high-performance system-level implementation.
4.6. System Portability Considerations
While this work focuses on the Zynq UltraScale+ platform, the architectural design principles employed support potential cross-platform adaptability. This section discusses the theoretical portability considerations and migration challenges.
4.6.1. Architectural Design for Portability
Our PS-PL separation architecture (
Figure 2 and
Figure 3) follows established heterogeneous computing principles, enabling theoretical mapping to various platforms: ARM+FPGA SoCs (Intel Cyclone V/Arria 10), CPU+GPU systems, and CPU+dedicated accelerator configurations. The modular design separates hardware-intensive operations (AES encryption, TRNG) from software control logic (Kyber-KEM, FA-KYBER), facilitating independent platform optimization.
4.6.2. Component Portability Analysis
Cryptographic algorithms demonstrate inherent portability: Kyber-768 as an NIST standard with a C reference implementation exhibits natural cross-architecture compatibility, while our measured performance (1.2–1.7 ms operations) should scale predictably with processor capabilities. AES-256-GCM represents a widely supported standard with hardware acceleration available across most platforms. The TRNG design presents the greatest platform dependency, as our multi-level Ring Oscillator implementation (
Section 2.5) relies on FPGA-specific routing and placement, requiring significant adaptation for cross-vendor migration or alternative entropy sources for non-FPGA platforms.
4.6.3. Migration Challenges and Limitations
Cross-platform migration faces several challenges: toolchain adaptation (Vivado vs. Quartus), resource architecture differences (CLBs vs. ALMs), and platform-specific integration requirements. The FA-KYBER framework’s network monitoring, while conceptually portable through standard APIs, would require platform-specific driver adaptation.
Important limitation: This analysis represents theoretical considerations based on architectural principles rather than empirical validation. Actual migration would require substantial engineering effort including performance characterization, component optimization, security validation, and integration testing on target platforms. Future work should prioritize establishing baselines for strategically important alternative platforms.
4.7. Limitations of the Study
Despite promising results, this study has the following limitations:
Comprehensive Side-Channel Attack Analysis: While our architectural design incorporates several SCA-aware features (PS-PL separation, adaptive key rotation, TRNG spatial isolation), this work lacks formal side-channel resistance evaluation against power analysis attacks (DPA/SPA), electromagnetic analysis attacks, and timing-based attacks. Quantitative security assessment using standardized methodologies such as Test Vector Leakage Assessment (TVLA) [
41] was not performed due to the requirement for specialized equipment (oscilloscopes, electromagnetic probes) and evaluation frameworks that were beyond the scope of this initial implementation study. Recent research has demonstrated successful side-channel attacks on masked implementations of Kyber-768 [
37,
39], highlighting that even protected implementations can be vulnerable without comprehensive countermeasures such as higher-order masking, shuffling, and constant-time operations specifically tailored for lattice-based cryptographic operations.
Network Attack Simulation Scope: TST effectiveness was validated against specific simulated attacks (bandwidth exhaustion, replay attacks, and temporal analysis probes). However, this evaluation has important limitations regarding attack sophistication. Our assessment did not include advanced persistent threats (APTs), machine learning-based adaptive adversaries that learn from system responses, multi-vector coordinated attacks that combine network and cryptographic vectors, or sophisticated stealth attacks designed to operate below detection thresholds while gradually compromising system security. These advanced attack scenarios represent a critical gap in current evaluation, as real-world adversaries often employ such sophisticated techniques. Future work should prioritize evaluation against adaptive adversaries using reinforcement learning approaches, coordinated multi-stage attacks, and stealth techniques specifically designed to evade TST detection mechanisms. Adaptive thresholds could be susceptible to poisoning without robust recalibration mechanisms.
Platform Specificity: Results are specific to the Zynq UltraScale+ MPSoC. Performance on other platforms may vary.
Software Kyber-KEM: The software Kyber implementation, while performant, introduces timing-based vulnerabilities and performance limitations compared to dedicated hardware acceleration, which could provide enhanced side-channel resistance and ultra-low-latency capabilities.
Large Network Scalability: ARP-based peer discovery was tested on a small scale (three nodes). Scalability and security in larger, more dynamic networks were not evaluated. While our decentralized approach theoretically supports larger deployments, several factors require investigation: (1) ARP table management overhead grows linearly with network size, potentially impacting the <1% CPU utilization advantage; (2) key exchange collision avoidance through MAC address comparison may face timing challenges in networks with >50 nodes; (3) the TST mechanism’s bandwidth monitoring accuracy could degrade in highly dynamic topologies with frequent joins/leaves. Theoretical analysis suggests our approach should scale to 20–50 node networks without architectural modifications, but empirical validation across different network sizes (10, 25, 50+ nodes) and topologies (mesh, hierarchical) is essential for production deployment confidence. Additionally, our TST mechanism’s anomaly detection capabilities (achieving 93.7% accuracy against simulated single-point attacks) have not been validated against sophisticated distributed attack scenarios that could exploit larger network topologies, such as coordinated multi-node DDoS attacks, distributed traffic analysis, or synchronized timing attacks across multiple network segments.
TRNG Long-Term Degradation: Our 24-h evaluation, while sufficient for operational validation, cannot assess potential long-term entropy degradation under extended operational periods (>1 month) and complex environmental variations. FPGA aging studies indicate RO frequency changes of 0.3–1.8% over months, which could affect entropy quality and would require extended monitoring for comprehensive characterization. Additionally, the cumulative effects of temperature cycling, voltage fluctuations, and electromagnetic interference over extended periods on the multi-level RO architecture’s entropy generation characteristics remain uncharacterized.
Formal Verification: System-level security properties, particularly component interactions and FA-Kyber logic, were not formally verified.For the benefit of future work, a proposed roadmap for this task is detailed in
Appendix A.
These limitations offer avenues for future refinement and research.
4.8. Future Research Directions
Building on these findings and limitations, future research directions include the following:
Formal Side-Channel Analysis and Enhanced Countermeasures:Building upon the SCA-aware architectural features identified in this work, conducting comprehensive side-channel resistance evaluation using Test Vector Leakage Assessment (TVLA) methodology [
41] and implementing dedicated countermeasures. Priority research areas include the following: (a) power analysis testing of Kyber-768 operations using differential and correlation power analysis techniques; (b) electromagnetic leakage assessment of the multi-level RO TRNG under varying environmental conditions; (c) timing attack analysis of the FA-KYBER key exchange protocol; (d) implementation and evaluation of masking schemes for polynomial arithmetic operations [
40]; and (e) integration of established SCA countermeasures such as clock randomization, noise injection, and shuffling techniques, validated through standardized leakage assessment frameworks.
Machine Learning-Enhanced TST Anomaly Detection: Extending the current TST mechanism with machine learning techniques to detect more subtle and sophisticated network attacks. Priority research areas include the following: (a) developing lightweight neural network models suitable for embedded deployment that can identify complex attack patterns beyond simple threshold-based detection; (b) implementing federated learning approaches to enable collaborative threat intelligence sharing across multiple nodes without compromising privacy; (c) designing adaptive models that can evolve with emerging attack vectors while maintaining low computational overhead on the PS; and (d) validating ML-enhanced detection against advanced persistent threats (APTs) and zero-day attack scenarios that current rule-based systems might miss.
Advanced TST Anomaly Detection: Incorporating machine learning techniques into the TST mechanism for more sophisticated detection of subtle or novel network attacks and to reduce false positives/negatives.
Hardware Acceleration for PQC KEMs: Designing and integrating a dedicated PL-based Kyber accelerator to further reduce key exchange latency and offload PS resources. Crucially, this hardware implementation would serve as a foundation for robust side-channel countermeasures (e.g., constant-time logic, power randomization, and masking techniques), directly mitigating the timing-based vulnerabilities identified in software-based approaches.
Cross-Platform Validation and Optimization: Building upon the theoretical portability analysis (
Section 4.6), empirical validation on alternative platforms represents a critical next step. Priority should focus on Intel/Altera SoC FPGAs and CPU+GPU configurations, with particular emphasis on TRNG adaptation strategies and performance characterization across different hardware architectures.
Scalable and Secure Network Management: Investigating more robust and scalable peer discovery and key management protocols for larger, dynamic network deployments. Priority research should include the following: (1) empirical testing on networks of 10–100 nodes to establish performance baselines; (2) hybrid discovery mechanisms combining ARP with hierarchical or DHT-based approaches for >50 node deployments; (3) distributed TST coordination to maintain anomaly detection effectiveness in segmented networks; (4) load balancing strategies for concurrent key exchanges to prevent network congestion during mass key rotation events; (5) evaluation against distributed attack scenarios including coordinated multi-node attacks, distributed traffic injection to poison TST baselines, and synchronized timing analysis across network segments to validate the robustness of our adaptive security mechanisms in complex threat environments.
Extended TRNG Reliability Assessment and Health Monitoring: Conducting comprehensive long-term evaluations (>1 month) of the multi-level RO TRNG under complex environmental stress conditions to characterize entropy degradation patterns. This research should include the following: (a) extended operational testing across temperature ranges (−40 °C to +85 °C), voltage variations (±15%), and humidity cycling to assess cumulative effects on entropy quality; (b) development of predictive models for entropy degradation based on environmental exposure history; (c) implementation of adaptive recalibration algorithms that can compensate for aging-induced frequency drift while maintaining statistical randomness; (d) design of online health monitoring systems that can detect early signs of entropy degradation before NIST SP 800-22 test failures occur; and (e) establishment of maintenance protocols for long-term deployment scenarios in harsh industrial environments.
Formal Verification and Security Proofs: Applying formal verification techniques to the FA-Kyber logic and overall system architecture to provide stronger assurance of security properties.
Exploration of Hybrid PQC Schemes: Investigating hybrid PQC approaches (e.g., combining Kyber with a classical KEM for defense in depth) and enhancing cryptographic agility.
Application to Specific Use Cases: Tailoring and evaluating the system for specific demanding applications such as V2X communications, industrial IoT, or biomedical device security.
Addressing these areas would further enhance the security, performance, and applicability of quantum-resistant cryptosystems.
5. Conclusions
This paper presented the design and comprehensive evaluation of an optimized quantum-resistant cryptographic system, demonstrating the practical feasibility of deploying high-performance post-quantum security on embedded platforms. Our integrated solution on the Zynq UltraScale+ MPSoC successfully combines three key elements: NIST-standardized Kyber-KEM for secure key exchange, a novel multi-level hardware TRNG providing stable 49.6 Mbps of high-quality entropy, and the innovative FA-KYBER framework for adaptive key management. The system delivers an encrypted data throughput exceeding 550 Mbps at a low average latency of 3.14 ms, validating its suitability for demanding, real-world applications.
The success of this work illuminates several clear and critical paths for future research. While our software-based Kyber implementation is efficient, hardware acceleration is the next logical step to reduce key exchange latency below the current 1.2–1.7 ms, enabling ultra-low-latency secure communications. The demonstrated 93.7% anomaly detection rate of our FA-KYBER framework provides a strong baseline, which could be further enhanced by incorporating machine learning models for more sophisticated threat intelligence. To build upon our security-conscious design, a comprehensive side-channel analysis (SCA) of the PS-PL architecture is essential for hardening against physical attacks. Finally, investigating long-term TRNG stability and developing scalable key management protocols are crucial for ensuring robust, enterprise-grade deployment.
In conclusion, this research provides more than just a high-performance implementation; it offers a tangible blueprint for developing the next generation of secure systems. By synergistically integrating quantum-resistant algorithms, robust hardware entropy sources, and context-aware adaptive security, this work establishes a new benchmark and a clear research roadmap for building resilient communications infrastructure capable of withstanding the quantum threat.
Author Contributions
Conceptualization, K.Z. and W.L.; methodology, K.Z., Y.Z., and W.L.; software, K.Z.; validation, K.Z., M.Y., and Z.Y.; formal analysis, K.Z.; investigation, K.Z.; resources, W.L. and Y.Z.; data curation, K.Z., M.Y., and Z.Y.; writing—original draft preparation, K.Z.; writing—review and editing, K.Z., W.L., Y.Z., M.Y., and Z.Y.; visualization, K.Z.; supervision, W.L. and Y.Z.; project administration, W.L. and Y.Z.; funding acquisition, W.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Foundation of State Key Laboratory of Dynamic Measurement Technology, North University of China (a National Key Laboratory), under Grant 2023-SYSJJ-05; by the National Natural Science Foundation of China under Grant 62201523; by the Fundamental Research Program of Shanxi Province under Grant 20210302124329; and by the Innovative Research Group Project of the National Science Foundation of China under Grant 51821003.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A. A Proposed Roadmap for Formal Verification
As suggested by our analysis in
Section 4.7, formal verification was not within the scope of this work. However, for the benefit of interested readers and future research, this appendix outlines a practical roadmap for applying formal methods to a hybrid cryptographic system like ours, based on established practices in the formal verification of cryptographic systems [
48,
49]. The process involves progressively refining models from high-level protocol abstractions down to implementation-specific details.
A graphical overview of the proposed verification process is shown in
Figure A1.
Figure A1.
Proposed flowchart for the formal verification of the hybrid cryptosystem.
Figure A1.
Proposed flowchart for the formal verification of the hybrid cryptosystem.
The verification process can be broken down into four main phases:
Phase 1: Formal Specification. The initial step is to translate the system’s security goals and operational requirements into a precise, machine-readable format. For our system, this would involve the following:
Protocol Properties: Defining security goals for the FA-KYBER key exchange protocol. This includes properties like mutual authentication (i.e., the initiator and responder correctly identify each other), key secrecy (i.e., the exchanged session key remains unknown to an attacker), and forward secrecy (i.e., the compromise of long-term keys does not compromise past session keys).
System-Level Invariants: Specifying properties of the overall system. For instance, an invariant for the Traffic-Sensing Threshold (TST) mechanism would be “If the network error rate exceeds the adaptive threshold , a key update procedure must be initiated within a bounded time.” Another invariant would be that the dual-key buffer ensures no packet is dropped or processed with an incorrect key during the key transition window.
Attacker Model: Formally defining the attacker’s capabilities, typically using the Dolev-Yao model for network-level attacks, which grants the adversary full control over the network (can intercept, modify, and inject messages).
Phase 2: System Modeling. In this phase, different aspects of the system are abstracted into formal models suitable for analysis. This requires creating multiple models at different levels of abstraction:
Protocol Model: Modeling the FA-KYBER key update protocol as a state machine. This model would capture the roles (initiator, responder), messages exchanged, session identifiers, and the cryptographic primitives (e.g., Kyber.Encaps, Kyber.Decaps) as abstract functions.
Architectural Model: Creating a higher-level model of the Zynq PS-PL architecture. The PS and PL would be modeled as concurrent processes communicating over abstract channels (representing AXI buses). This is crucial for analyzing potential race conditions or unintended information flows between the Kyber logic in the PS and the AES/TRNG hardware in the PL.
Implementation Model: Creating a model that more closely reflects the C code running on the PS and the Verilog/VHDL code in the PL. This is essential for verifying implementation-specific properties.
Phase 3: Automated Verification and Analysis. With formal models in place, automated tools can be used to search for flaws or prove that certain properties hold:
Protocol Security: A symbolic model checker like ProVerif [
50] or Tamarin [
51] would be used on the protocol model. These tools are excellent at automatically finding attacks on cryptographic protocols, such as man-in-the-middle or replay attacks, for an unbounded number of sessions.
System-Level Properties: A model checker like TLA+ [
52] or SPIN would be applied to the architectural model. These tools can verify system-wide properties like liveness (“the system eventually completes a key exchange despite transient failures”) and safety (“the system never enters a state where two different keys are used for the same data stream simultaneously”).
Implementation Correctness: A bounded model checker like CBMC [
53] (C Bounded Model Checker) could be used to find bugs in the C implementation of the FA-KYBER framework, such as buffer overflows, integer overflows, or logical errors in the TST calculation.
Phase 4: Manual Proof and Composition. Not all properties can be proven automatically. This phase uses interactive theorem provers to tackle more complex properties and to tie the results from different models together.
Complex Properties: An interactive theorem prover like Coq [
54] or Isabelle/HOL would be used. For example, proving the mathematical correspondence between the high-level cryptographic specification of Kyber and its constant-time C implementation requires this level of rigor.
Linking Models: The most critical task here is to prove that the abstract models (e.g., the protocol model) are a correct representation of the more detailed implementation models. This ensures that the security properties proven on the abstract model actually hold for the real system.
Stating Cryptographic Assumptions: The hardness of the underlying mathematical problem (e.g., MLWE for Kyber) is not proven here but is stated as a formal assumption. The proofs are then conducted *under the assumption* that these cryptographic primitives are secure.
This structured approach, combining automated tools for broad analysis and manual proofs for deep, critical properties, represents a robust methodology for gaining high assurance in the security of complex quantum-resistant cryptosystems [
55,
56].
References
- Gidney, C.; Ekerå, M. How to factor 2048 bit RSA integers in 8 h using 20 million noisy qubits. Quantum 2021, 5, 433. [Google Scholar] [CrossRef]
- Google Research. Meet Willow, Our State-of-the-Art Quantum Chip. 2024. Available online: https://blog.google/technology/research/google-willow-quantum-chip/ (accessed on 17 April 2025).
- Acharya, R.; Abanin, D.A.; Aghababaie-Beni, L.; Aleiner, I.; Andersen, T.I.; Ansmann, M.; Arute, F.; Arya, K.; Asfaw, A.; Astrakhantsev, N.; et al. Quantum error correction below the surface code threshold with substantial suppression of logical errors. Nature 2025, 638, 920–926. [Google Scholar] [CrossRef]
- Bhatia, V.; Ramkumar, K.R. An Efficient Quantum Computing technique for cracking RSA using Shor’s Algorithm. In Proceedings of the 2020 IEEE 5th International Conference on Computing Communication and Automation (ICCCA), Greater Noida, India, 30–31 October 2020; pp. 89–94. [Google Scholar] [CrossRef]
- Gaithuru, J.N.; Bakhtiari, M. Insight into the operation of NTRU and a comparative study of NTRU, RSA and ECC public key cryptosystems. In Proceedings of the 2014 8th. Malaysian Software Engineering Conference (MySEC), Kota Kinabalu, Malaysia, 23–24 September 2014; pp. 273–278. [Google Scholar] [CrossRef]
- Kumar, A.; Mishra, A. Evaluation of Cryptographically Secure Pseudo Random Number Generators for Post Quantum Era. In Proceedings of the 2022 IEEE 7th International Conference for Convergence in Technology (I2CT), Pune, India, 7–9 April 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Abdulrahman, A.; Hwang, V.; Kannwischer, M.J.; Sprenkels, A. Faster Kyber and Dilithium on the Cortex-M4. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2022, 2022, 112–143. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology. NIST PQC License Summary and Excerpts. 2022. Available online: https://csrc.nist.gov/csrc/media/Projects/post-quantum-cryptography/documents/selected-algos-2022/nist-pqc-license-summary-and-excerpts.pdf (accessed on 17 April 2025).
- Park, J.; Lee, Y.K.; Bohdan, K.; Choi, Y.; Shin, J.; Rhew, H.G.; Shin, J. A PVT-Tolerant STR-Based TRNG in 4-nm Achieving 60 Mbp/s and Its Performance Analysis via Mathematical Modeling. IEEE Solid-State Circuits Lett. 2024, 7, 255–258. [Google Scholar] [CrossRef]
- Cheng, Z.; Qin, Y.; Wang, Z.; Zou, F.; Wang, C.; Cai, Y.; Huang, R. A High-Throughput and Configurable TRNG Based on Dual-Mode Memristor for Stochastic Computing. In Proceedings of the 2023 IEEE International Conference on Integrated Circuits, Technologies and Applications (ICTA), Nanjing, China, 25–27 October 2023; pp. 108–109. [Google Scholar] [CrossRef]
- Cabral, J.N.; Casaleiro, J.; Oliveira, L. Design of a 28nm CMOS Self-Biased Ring Oscillator for Intrinsically Robust PVT TRNG. In Proceedings of the 2023 18th Conference on Ph.D Research in Microelectronics and Electronics (PRIME), Lisbon, Portugal, 18–21 June 2023; pp. 225–228. [Google Scholar] [CrossRef]
- Meitei, H.B.; Kumar, M. Design and Implementation of Multiple Ring Oscillator-Based TRNG Architecture by Using ADPLL. IEEE Access 2025, 13, 9252–9264. [Google Scholar] [CrossRef]
- Singh, G.; Kaur, A. Simplified RSA Encryption Module for FPGA: A Comparative Analysis Between Kintex and Genesys Boards. In Proceedings of the 2024 Second International Conference on Intelligent Cyber Physical Systems and Internet of Things (ICoICI), Vijayawada, India, 20–30 August 2024; pp. 691–695. [Google Scholar] [CrossRef]
- Ram, R.V.R.; Kaveri, R.M.; Bhuvanesh, P.; Mariammal, K. FPGA Acceleration of Authenticated Encryption with PUF-Key. In Proceedings of the 2023 IEEE International Carnahan Conference on Security Technology (ICCST), Zurich, Switzerland, 11–15 October 2023; pp. 1–8. [Google Scholar] [CrossRef]
- Ashfaque, M.R.; Singh, V.P.; Kondeti, M.; Shingala, F.; H, P.; S, S.D.; Prabhakar, A. TRNG integration in FPGA-based QKD Control Electronics. In Proceedings of the 2024 IEEE Space, Aerospace and Defence Conference (SPACE), Bengaluru, India, 22–23 July 2024; pp. 552–556. [Google Scholar] [CrossRef]
- Zhang, C.; Liu, D.; Liu, X.; Zou, X.; Niu, G.; Liu, B.; Jiang, Q. Towards Efficient Hardware Implementation of NTT for Kyber on FPGAs. In Proceedings of the 2021 IEEE International Symposium on Circuits and Systems (ISCAS), 22–28 May 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Barrett, P. Implementing the Rivest Shamir and Adleman Public Key Encryption Algorithm on a Standard Digital Signal Processor. In Advances in Cryptology — CRYPTO’ 86; Odlyzko, A.M., Ed.; Springer: Berlin/Heidelberg, Germany, 1987; pp. 311–323. [Google Scholar]
- Nguyen, T.H.; Pham, C.K.; Hoang, T.T. A High-Efficiency Modular Multiplication Digital Signal Processing for Lattice-Based Post-Quantum Cryptography. Cryptography 2023, 7, 46. [Google Scholar] [CrossRef]
- Xiao, C.; Zhang, L.; Xie, Y.; Liu, W.; Liu, D. Hardware/Software Adaptive Cryptographic Acceleration for Big Data Processing. Secur. Commun. Netw. 2018, 2018, 7631342. [Google Scholar] [CrossRef]
- Rana, S.; Parast, F.K.; Kelly, B.; Wang, Y.; Kent, K.B. A comprehensive survey of cryptography key management systems. J. Inf. Secur. Appl. 2023, 78, 103607. [Google Scholar] [CrossRef]
- Hamarsheh, A. An Adaptive Security Framework for Internet of Things Networks Leveraging SDN and Machine Learning. Appl. Sci. 2024, 14, 4530. [Google Scholar] [CrossRef]
- Almohri, H.M.; Watson, L.T.; Yao, D.; Ou, X. Security Optimization of Dynamic Networks with Probabilistic Graph Modeling and Linear Programming. IEEE Trans. Dependable Secur. Comput. 2016, 13, 474–487. [Google Scholar] [CrossRef]
- Almohri, H.M.J.; Watson, L.T.; Alemzadeh, H.; Almutawa, M. On Parallel Real-Time Security Improvement Using Mixed-Integer Programming. IEEE Access 2021, 9, 58824–58837. [Google Scholar] [CrossRef]
- Thomas, M.; Sela, L. A Mixed-Integer Linear Programming Framework for Optimization of Water Network Operations Problems. Water Resour. Res. 2024, 60, e2023WR034526. [Google Scholar] [CrossRef]
- Lian, L. Network traffic prediction model based on linear and nonlinear model combination. ETRI J. 2024, 46, 461–472. [Google Scholar] [CrossRef]
- Al Tobi, A.M.; Duncan, I. Improving Intrusion Detection Model Prediction by Threshold Adaptation. Information 2019, 10, 159. [Google Scholar] [CrossRef]
- Kaushik, S.; Bhardwaj, A.; Almogren, A.; Bharany, S.; Altameem, A.; Rehman, A.U.; Hussen, S.; Hamam, H. Robust machine learning based Intrusion detection system using simple statistical techniques in feature selection. Sci. Rep. 2025, 15, 3970. [Google Scholar] [CrossRef]
- Almazmomi, N.K. Advanced Persistent Threat Detection Using Optimized and Hybrid Deep Learning Approach. Secur. Priv. 2025, 8, e70011. [Google Scholar] [CrossRef]
- Bhavsar, M.; Roy, K.; Kelly, J.; Olusola, O. Anomaly-based intrusion detection system for IoT application. Discov. Internet Things 2023, 3, 5. [Google Scholar] [CrossRef]
- Welford, B.P. Note on a Method for Calculating Corrected Sums of Squares and Products. Technometrics 1962, 4, 419–420. [Google Scholar] [CrossRef]
- Wang, Z.; Wang, Y.; Gao, C.; Wang, F.; Lin, T.; Chen, Y. An adaptive sliding window for anomaly detection of time series in wireless sensor networks. Wirel. Netw. 2022, 28, 393–411. [Google Scholar] [CrossRef]
- Jiang, D.; Liu, J.; Xu, Z.; Qin, W. Network traffic anomaly detection based on sliding window. In Proceedings of the 2011 International Conference on Electrical and Control Engineering, Yichang, China, 16–18 September 2011; pp. 4830–4833. [Google Scholar] [CrossRef]
- Chmielowiec, A. Algorithm for error-free determination of the variance of all contiguous subsequences and fixed-length contiguous subsequences for a sequence of industrial measurement data. Comput. Stat. 2021, 36, 2813–2840. [Google Scholar] [CrossRef]
- Wang, W.; Jian, S.; Tan, Y.; Wu, Q.; Huang, C. Robust unsupervised network intrusion detection with self-supervised masked context reconstruction. Comput. Secur. 2023, 128, 103131. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology. Recommendation for the Entropy Sources Used for Random Bit Generation; Special Publication NIST SP 800-90B; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018.
- Huang, Z.; Wang, H.; Cao, B.; He, D.; Wang, J. A comprehensive side-channel leakage assessment of CRYSTALS-Kyber in IIoT. Internet Things 2024, 27, 101331. [Google Scholar] [CrossRef]
- Wang, R.; Brisfors, M.; Dubrova, E. A Side-Channel Attack on a Higher-Order Masked CRYSTALS-Kyber Implementation. In Applied Cryptography and Network Security; Pöpper, C., Batina, L., Eds.; Springer: Cham, Switzerland, 2024; pp. 301–324. [Google Scholar]
- Wang, K.; Xu, D.; Tian, J. An Improved Two-Step Attack on CRYSTALS-Kyber. arXiv 2024, arXiv:2407.06942. [Google Scholar]
- Ji, Y.; Dubrova, E. A Side-Channel Attack on a Masked Hardware Implementation of CRYSTALS-Kyber. In Proceedings of the 2023 Workshop on Attacks and Solutions in Hardware Security, New York, NY, USA, 14–18 October 2023; pp. 27–37. [Google Scholar] [CrossRef]
- Özeren, S.; Yayla, O. Methods for Masking CRYSTALS-Kyber Against Side-Channel Attacks. Cryptology ePrint Archive, Report 2023/1340. 2023. Available online: https://eprint.iacr.org/2023/1340 (accessed on 24 June 2025).
- Wang, Y.; Tang, M. A Survey of Side-Channel Leakage Assessment. Electronics 2023, 12, 3461. [Google Scholar] [CrossRef]
- Hadipour, H. VHDL Implementation of AES Algorithm. 2017. Available online: https://github.com/hadipourh/AES-VHDL (accessed on 17 April 2025).
- Chamola, V.; Jolfaei, A.; Chanana, V.; Parashari, P.; Hassija, V. Information security in the post quantum era for 5G and beyond networks: Threats to existing cryptography, and post-quantum cryptography. Comput. Commun. 2021, 176, 99–118. [Google Scholar] [CrossRef]
- Madani, M.; Assad, S.E.; Tanougast, C.; Vella, M.J.; Bourennane, E.B.; Deforges, O. FPGA-Based Implementation of Enhanced ZUC Stream Cipher Based on Dynamic S-Box. In Proceedings of the 2023 International Conference on Engineering and Emerging Technologies (ICEET), Paris, France, 27–28 October 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Jaspin, K.; Selvan, S.; Sahana, S.; Thanmai, G. Efficient and Secure File Transfer in Cloud Through Double Encryption Using AES and RSA Algorithm. In Proceedings of the 2021 International Conference on Emerging Smart Computing and Informatics (ESCI), Pune, India, 5–7 March 2021; pp. 791–796. [Google Scholar] [CrossRef]
- Islam, M.M.; Hossain, M.S.; Hasan, M.K.; Shahjalal, M.; Jang, Y.M. Design and Implementation of High-Performance ECC Processor with Unified Point Addition on Twisted Edwards Curve. Sensors 2020, 20, 5148. [Google Scholar] [CrossRef]
- Alwhbi, I.A.; Zou, C.C.; Alharbi, R.N. Encrypted Network Traffic Analysis and Classification Utilizing Machine Learning. Sensors 2024, 24, 3509. [Google Scholar] [CrossRef]
- Wikipedia. Formal verification. 2025. Available online: https://en.wikipedia.org/wiki/Formal_verification (accessed on 23 June 2025).
- Chapman, R.; Petcher, A.; Hansen, T.; Peng, Y.; Lepoint, T.; Bytheway, C.; Kampanakis, P. Formal Verification of Cryptographic Software at AWS: Current Practices and Future Trends; Technical Report; Amazon Science: Seattle, WA, USA, 2024. [Google Scholar]
- Blanchet, B. An efficient cryptographic protocol verifier based on Prolog rules. In Proceedings of the 14th IEEE Computer Security Foundations Workshop, Cape Breton, NS, Canada, 11–13 June 2001; pp. 82–96. [Google Scholar] [CrossRef]
- The Tamarin Prover Team. Tamarin Prover. Available online: https://tamarin-prover.github.io/ (accessed on 23 June 2025).
- Lamport, L. Specifying Systems: The TLA+ Language and Tools for Hardware and Software Engineers; Addison-Wesley Professional: Boston, MA, USA, 2002. [Google Scholar]
- Clarke, E.; Kroening, D.; Lerda, F. A Tool for Checking ANSI-C Programs. In Tools and Algorithms for the Construction and Analysis of Systems; Springer: Berlin/Heidelberg, Germany, 2004; pp. 168–176. [Google Scholar] [CrossRef]
- The Coq Development Team. The Coq Proof Assistant. Available online: https://coq.inria.fr/ (accessed on 23 June 2025).
- Galois, Inc. Cryptol: The Language of Cryptography. Available online: https://tools.galois.com/cryptol (accessed on 23 June 2025).
- ICFEM 2024 Organising Committee. ICFEM 2024 Conference Program. Available online: https://icfem2024.info/ (accessed on 23 June 2025).
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).