STALE: A Scalable and Secure Trans-Border Authentication Scheme Leveraging Email and ECDH Key Exchange
Abstract
1. Introduction
- To overcome the limitations of trust mechanisms in trans-border authentication, this paper proposes a trans-border distributed authentication method (STALE) based on a Certificateless Public Key Cryptosystem. The framework utilizes email addresses as unique user identifiers and CL-PKC-based key distribution, thus eliminating the single point of failure in traditional PKI architectures and the key escrow vulnerabilities in identity-based cryptosystems. Formal security analysis confirms that the scheme enables real-time dynamic authentication for cross-border digital identity verification.
- In the design of authentication protocols, this study presents key enhancements to the conventional ECDH key-exchange protocol. The improved scheme integrates forward secrecy and mutual authentication, significantly strengthening communication security in trans-border network environments while simultaneously improving authentication efficiency.
- To manage identity information securely, this work implements a distributed identity ledger architecture utilizing the FISCO BCOS consortium blockchain. The system employs rigorously designed smart contracts and an optimized consensus protocol to facilitate Decentralized Identity storage and verification. This approach guarantees tamper-proof data integrity, full auditability, and adherence to General Data Protection Regulation (GDPR) compliance standards.
2. Related Works
2.1. Public Key Infrastructure
2.2. Identity-Based Encryption
2.3. Certificateless Public Key Cryptography
2.4. Blockchain-Based Identity Authentication Technology
3. Preliminaries
3.1. CL-PKC Formulation
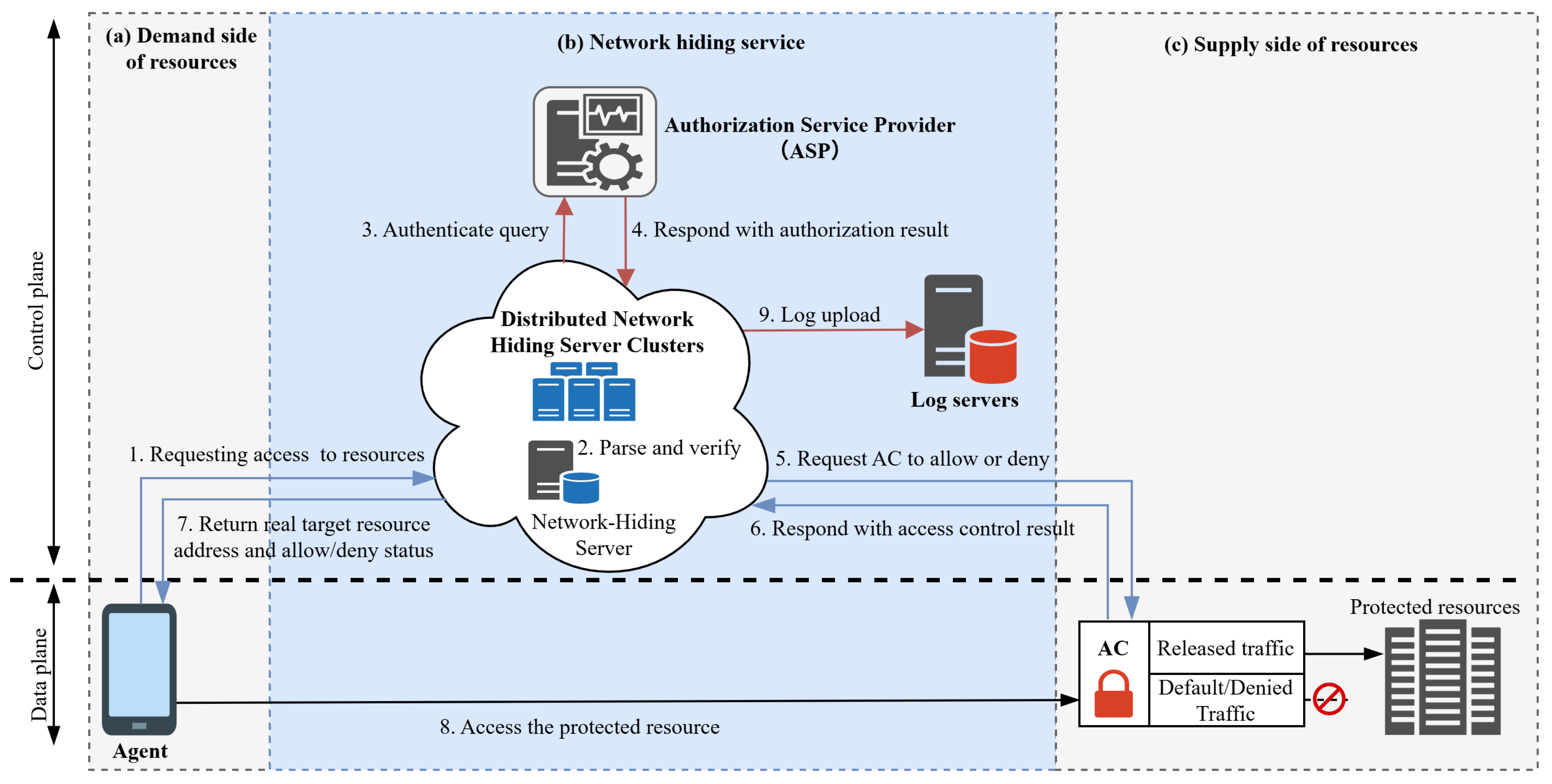
3.2. AHAC Framework
3.3. Blockchian
4. Methodology
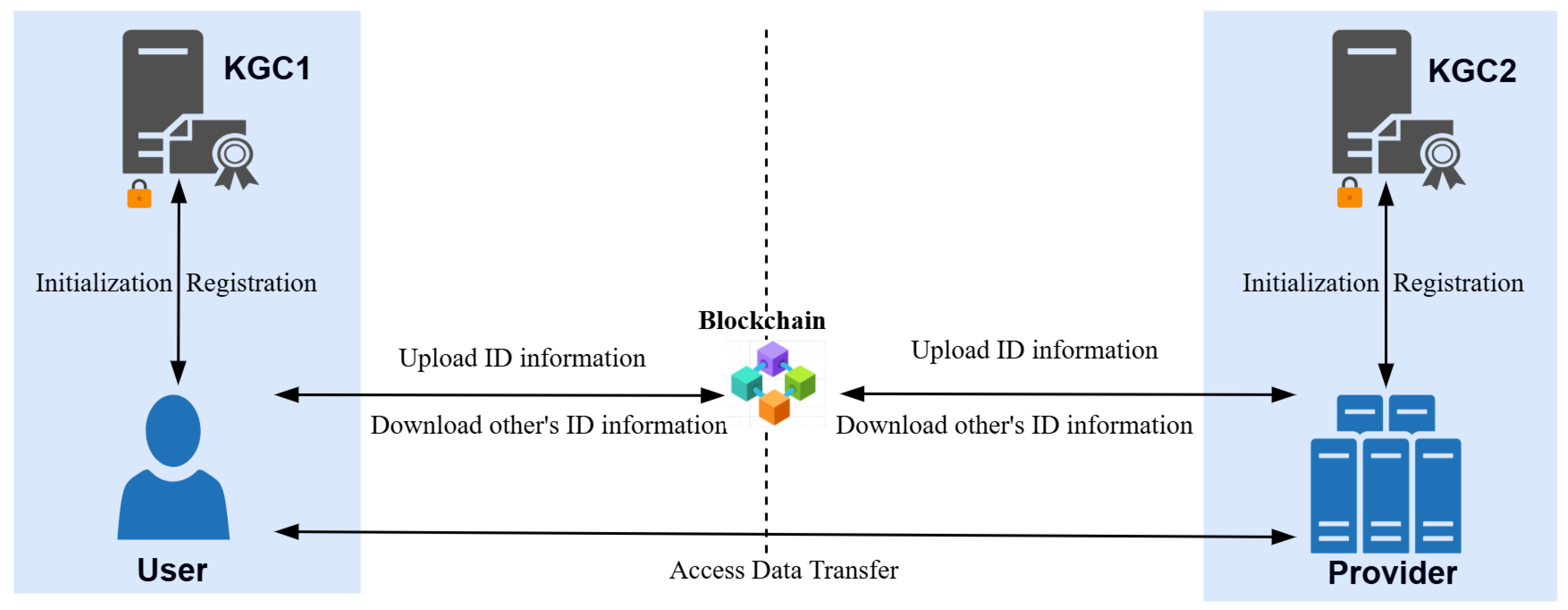
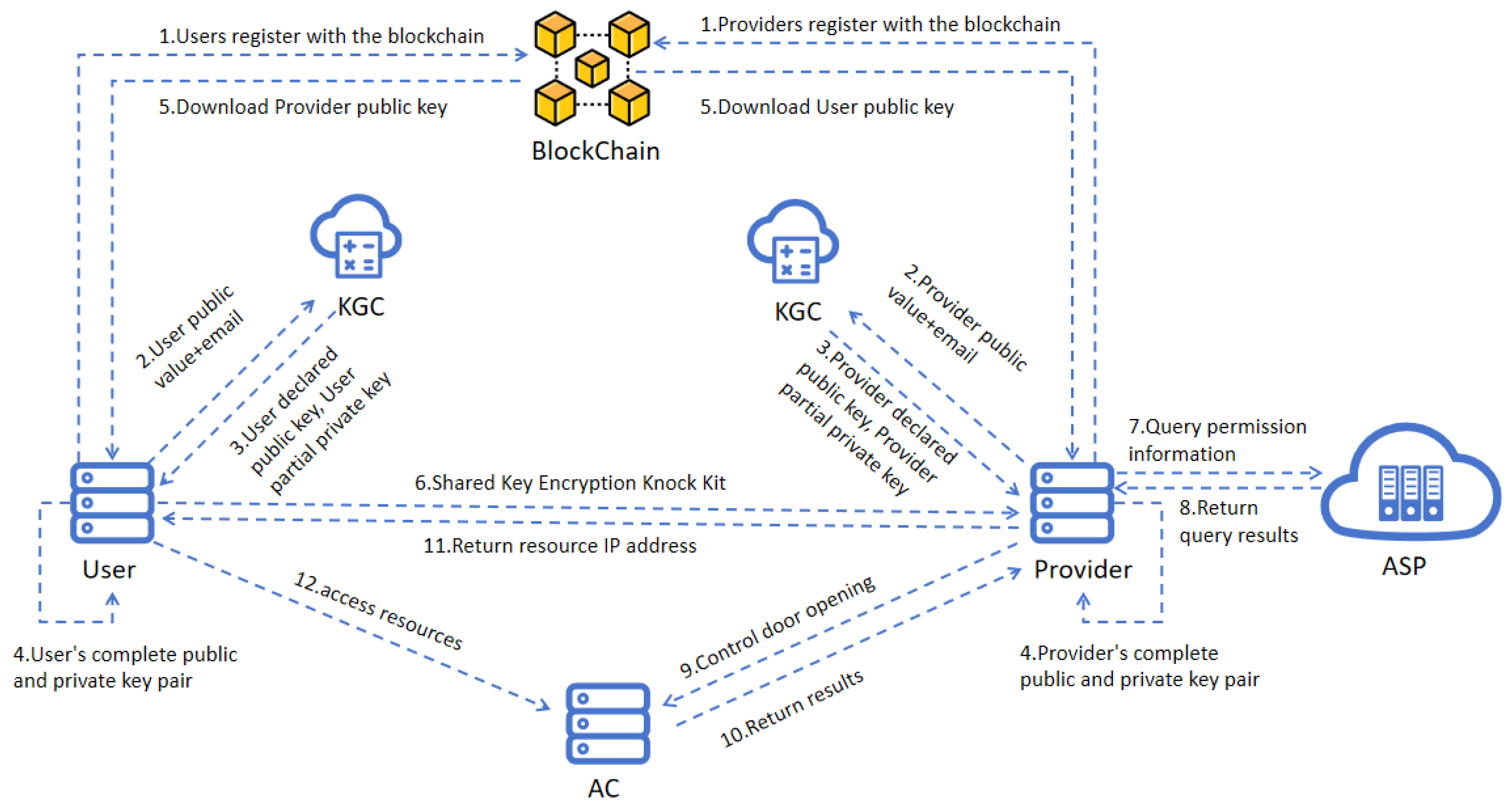
4.1. System Architecture
- KGC: The KGC is responsible for generating the system’s master public key and master private key for the relevant participants and completing user identity registration. The KGC can be deployed in a distributed manner, with one KGC able to register identities for multiple entities.
- User: In trans-border data scenarios, the User acts as the data access requester. The User downloads the Provider’s identity information from the blockchain and calculates its public key. Using the ECC algorithm, the User encrypts the session data packet and sends it to the Provider, requesting access to resources.
- Provider: The Provider functions as the data provider in trans-border scenarios, responsible for decrypting data packets and completing identity verification. The Provider downloads the User’s identity information from the blockchain, calculates its public key, decrypts the encrypted data packet, and performs the authentication process to ensure the security and legitimacy of the request.
- Blockchain: The blockchain records each user’s identity information (email and public key) on-chain, supporting tamper-resistant identity information, which helps maintain the reliability of identity management. Even in scenarios that span multiple jurisdictions, the blockchain ensures the integrity and consistency of the data.
4.2. Workflow
4.2.1. System Initialization
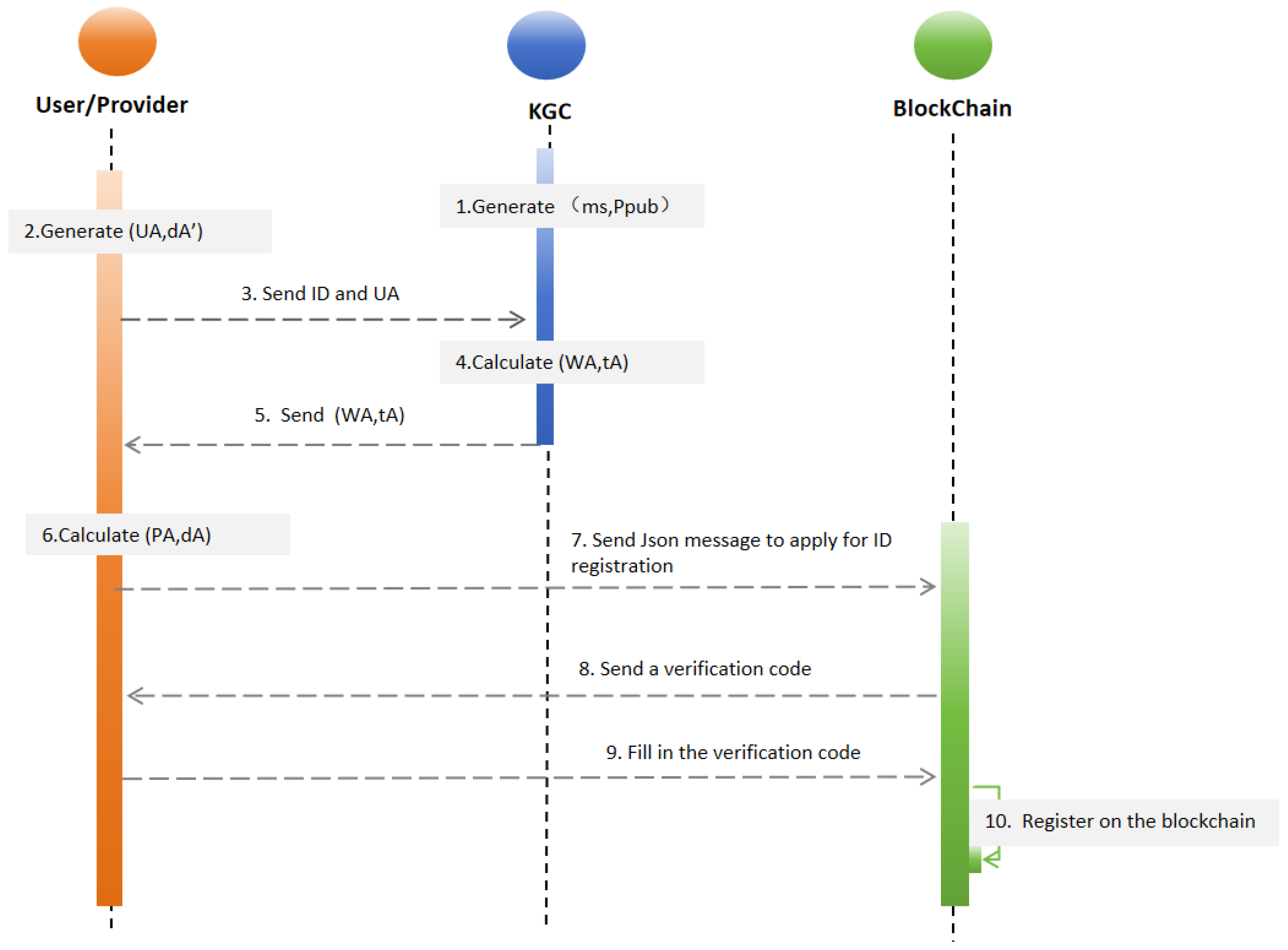
4.2.2. Identity Registration Stage
- Step 1: KGC generates the system parameters and the master public and private key pair, represented as .
- Step 2: Both the User and Provider send their respective identity IDs to the KGC. In this scheme, the identity ID is represented by an email address. Each entity (User and Provider) also generates its own public value and secret value, denoted as .
- Step 3: Upon receiving the identity information (ID) and public value from the User and Provider, the KGC combines these with the system parameters and the master key pair to compute the User’s declared public key and partial private key .
- Step 4: The KGC returns the User’s declared public key and partial private key to each respective entity (User and Provider).
- Step 5: Upon receiving the declared public key and partial private key from the KGC, both the User and Provider calculate their true private key , using their secret value and partial private key . They also calculate their true public key , using .
- Step 6: The User and Provider each verify their computed public key by comparing it with . If matches then the verification is successful, confirming the authenticity of the true public key ; otherwise, the public key is deemed invalid.
- Step 7: After successful verification, a JSON message is created to apply for identity registration on the blockchain. This JSON message contains the identity information (e.g., email and public key ).
- Step 8: The blockchain sends a verification code to the User and Provider to confirm the registration process.
- Step 9: The User and Provider fill in the verification code they received to authenticate their registration request.
- Step 10: Upon successful verification, the blockchain registers the identity information, making it immutable and accessible for trans-border authentication.
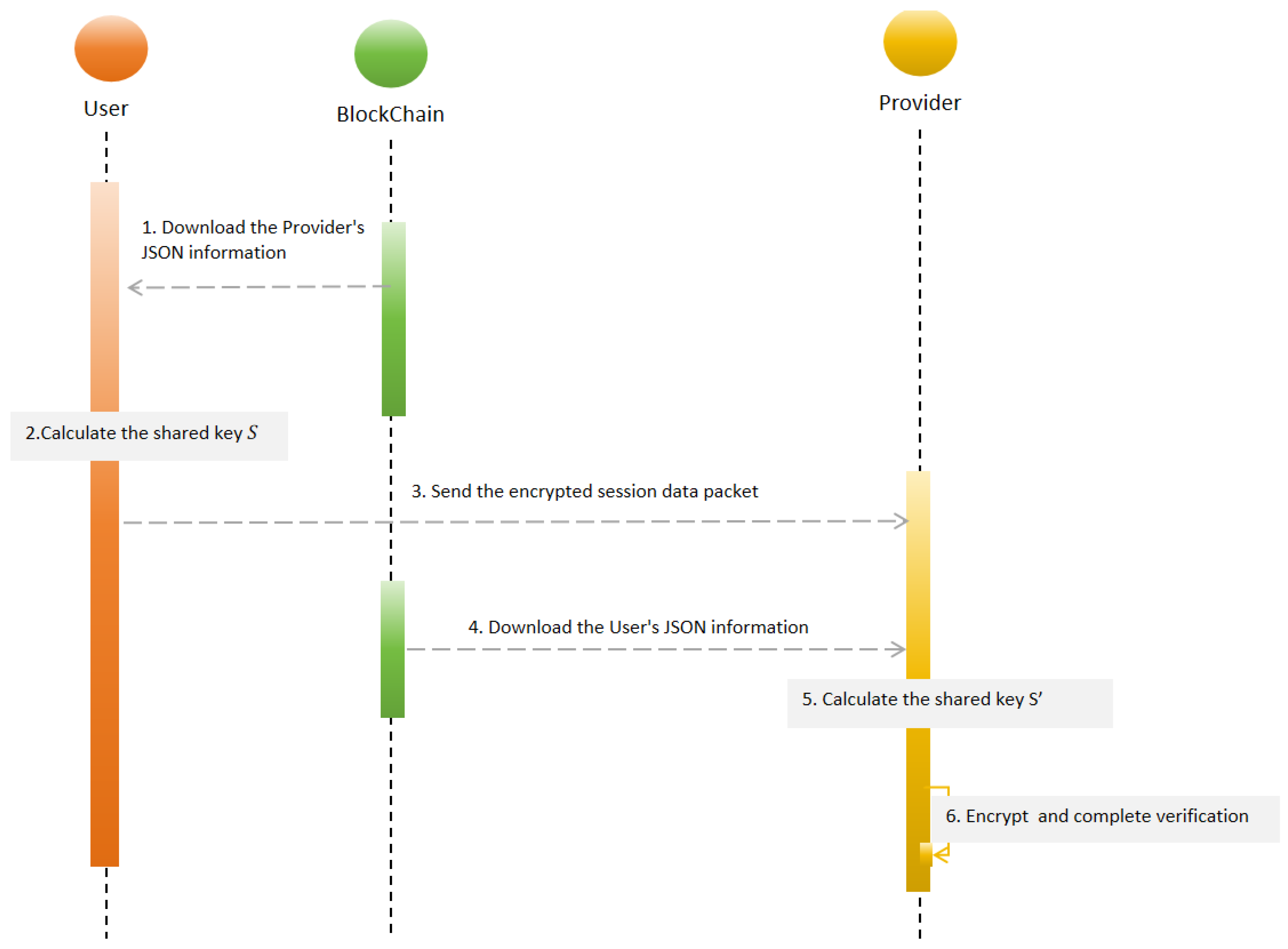
4.2.3. Authentication Stage
- Step 1: The User downloads the Provider’s JSON identity information from the blockchain, which includes the Provider’s email and public key.
- Step 2: Using the downloaded public key of the Provider, the User calculates a shared key S by performing elliptic curve point multiplication with their own private key. This shared key will be used to encrypt the session data.
- Step 3: The User encrypts the session data packet, using the shared key S, and sends this encrypted packet to the Provider.
- Step 4: The Provider downloads the User’s JSON identity information from the blockchain, including the User’s public key, to prepare for identity verification.
- Step 5: Using the User’s public key, the Provider calculates a shared key by performing elliptic curve point multiplication with their own private key. This shared key should match the User’s shared key S if the calculations are correct.
- Step 6: The Provider decrypts the received session data packet, using the shared key , and verifies the integrity and validity of the information, completing the identity verification process.
5. Experiments
5.1. Experimental Setup
5.1.1. Experiment Design
5.1.2. Experimental Topology
- Step 1: The User/Provider registered the Provider’s public key information on the blockchain.
- Step 2: The User/Provider calculated their public value and sent it along with their email to the KGC.
- Step 3: Upon receiving the User’s/Provider’s public value and email, the KGC computed the User’s/Provider’s declared public key and partial private key, then sent these back to the User/Provider.
- Step 4: The User/Provider received the declared public key and partial private key from the KGC and used this data to calculate their complete public and private key pair.
- Step 5: The User/Provider downloaded the other party’s public key information from the blockchain.
- Step 6: The User performed an elliptic curve point multiplication operation, using their private key and the Provider’s public key to generate a shared key. The User encrypted the “knock” packet with this shared key and sent it to the Provider.
- Step 7: Upon receiving the knock packet, the Provider calculated the shared key in the same way, decrypted the packet, and then queried the ASP (Authorization Service Provider) to check whether the User had access rights.
- Step 8: The ASP returned the access authorization result to the Provider.
- Step 9: Based on the authorization result, the Provider responded accordingly. If access was granted, the Provider notified the AHAC AC to allow access; if not, no response was given.
- Step 10: The AHAC AC returned the execution result to the Provider.
- Step 11: The Provider returned the resource IP address to the User.
- Step 12: The User received the IP address and successfully accessed the resource based on the IP.
5.2. Performance Test
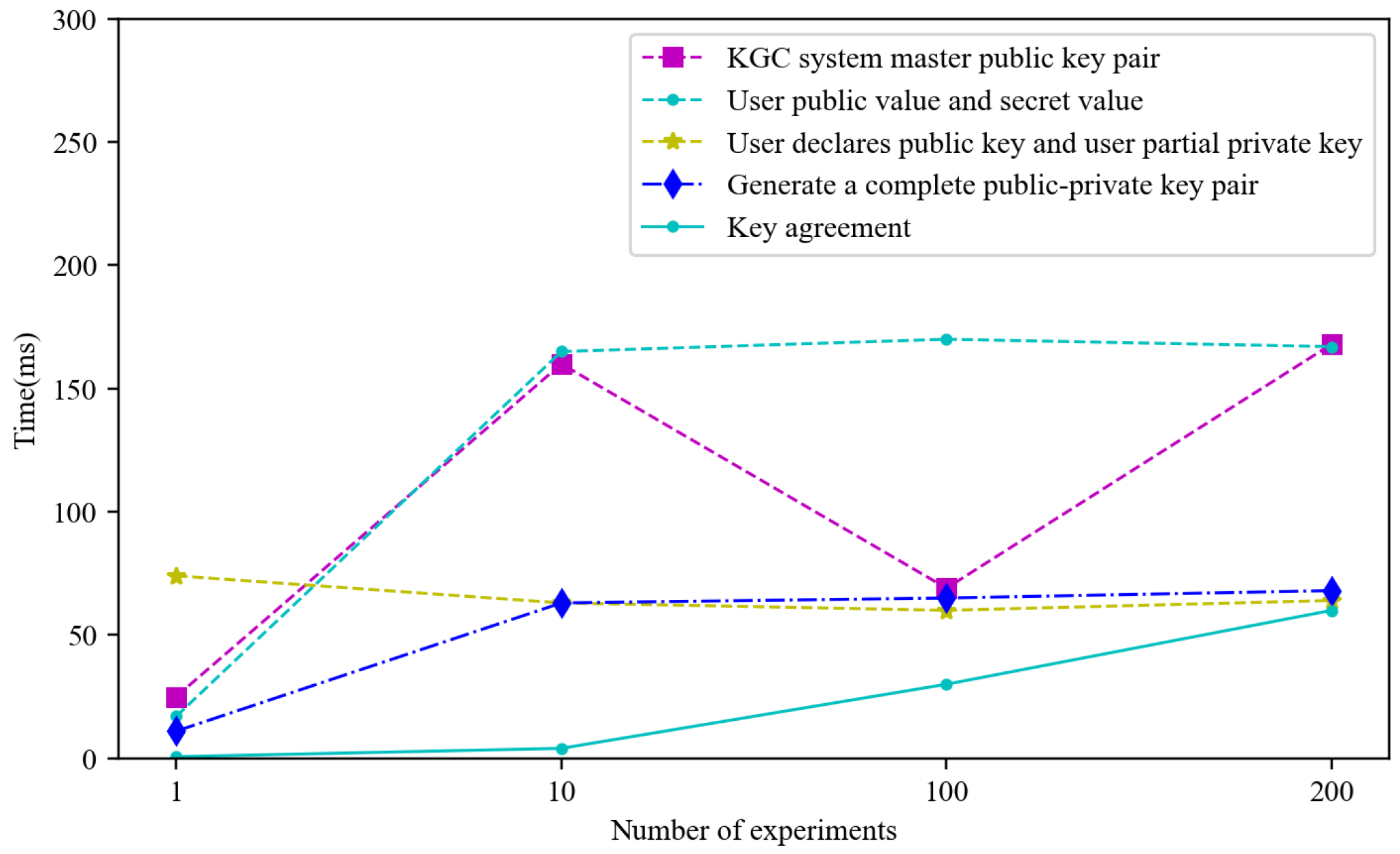
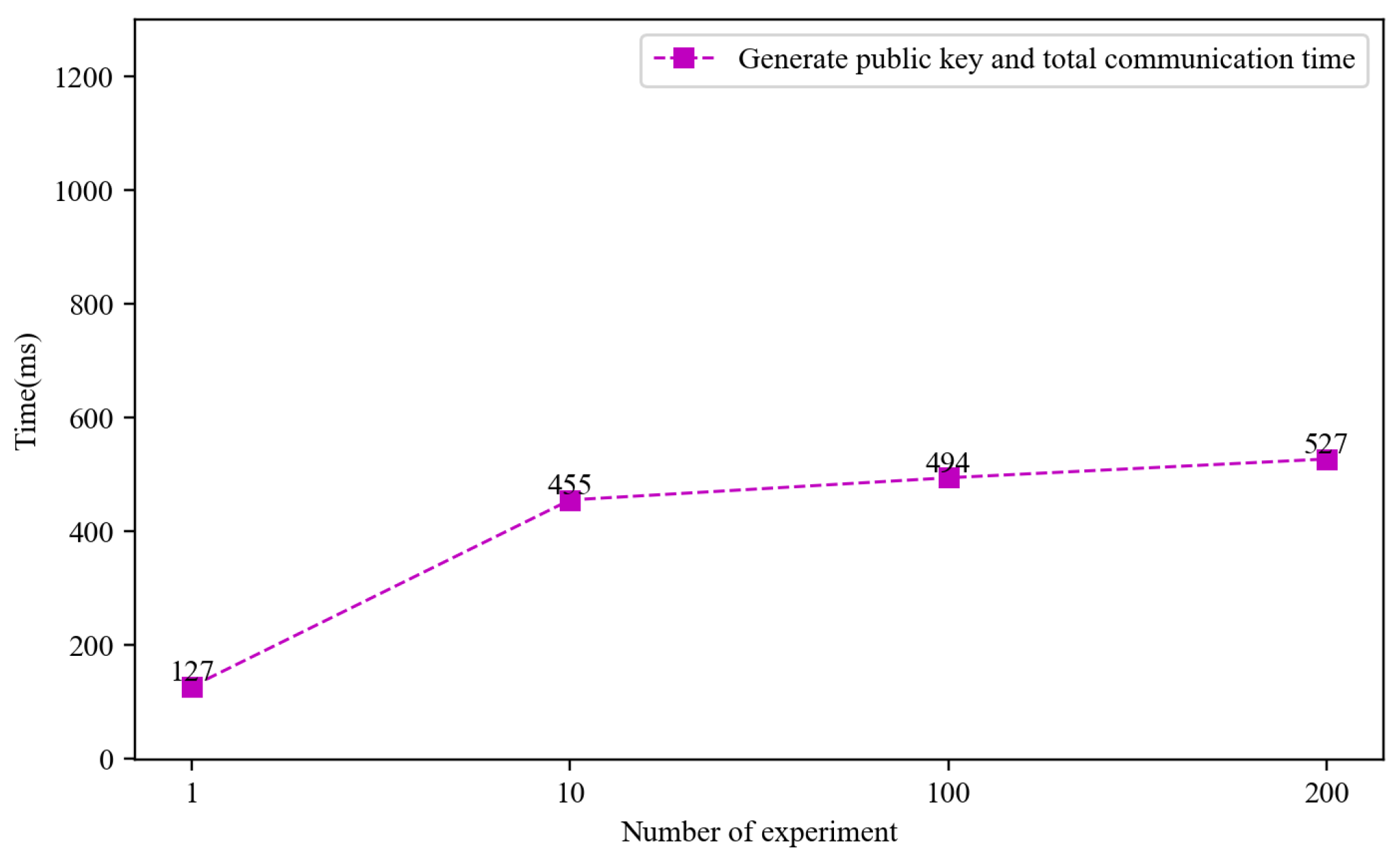
5.2.1. RQ1: What Is the Time Required for Key Generation and Key Agreement?
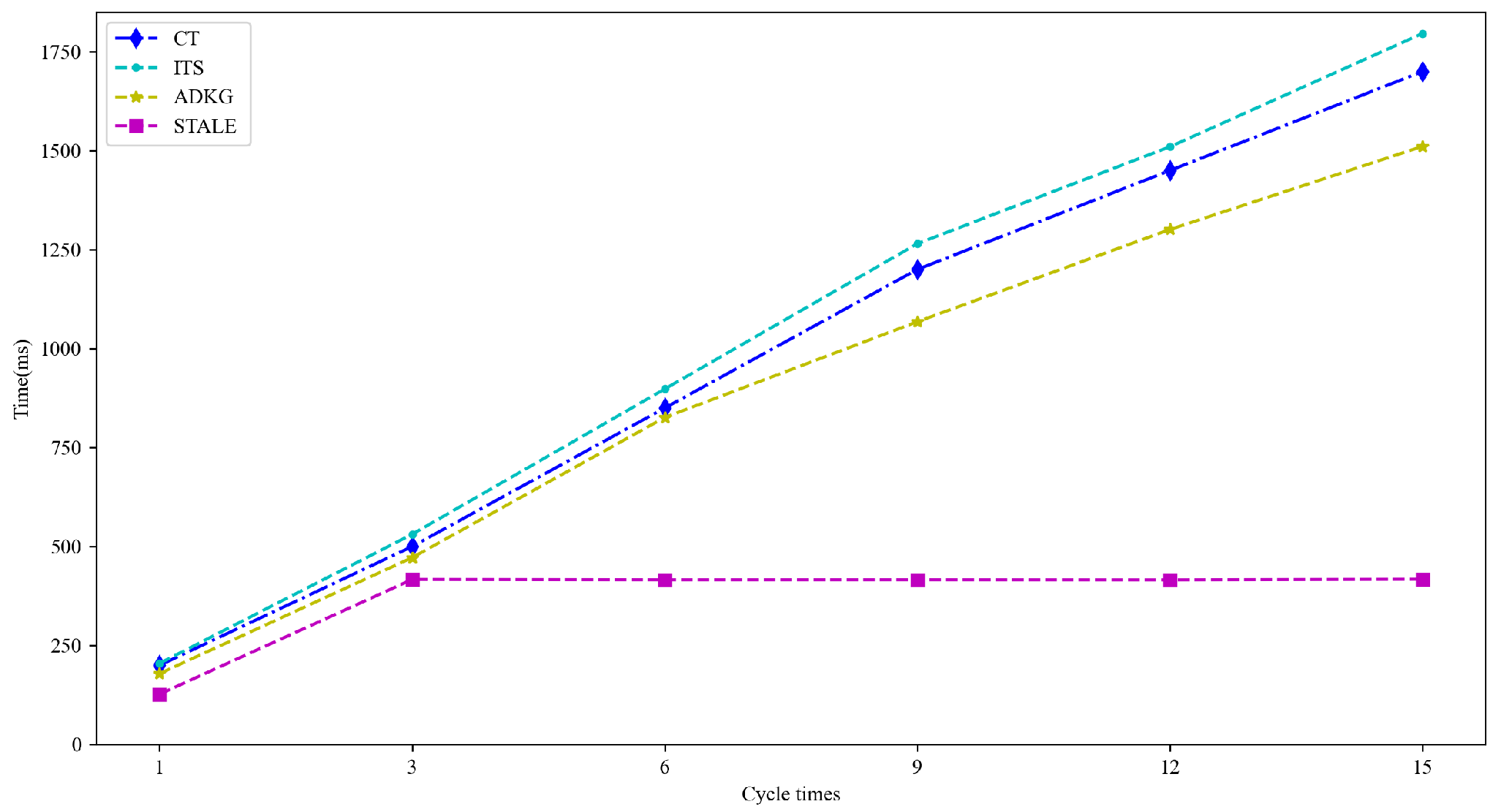
5.2.2. RQ2: What Is the Communication Overhead?
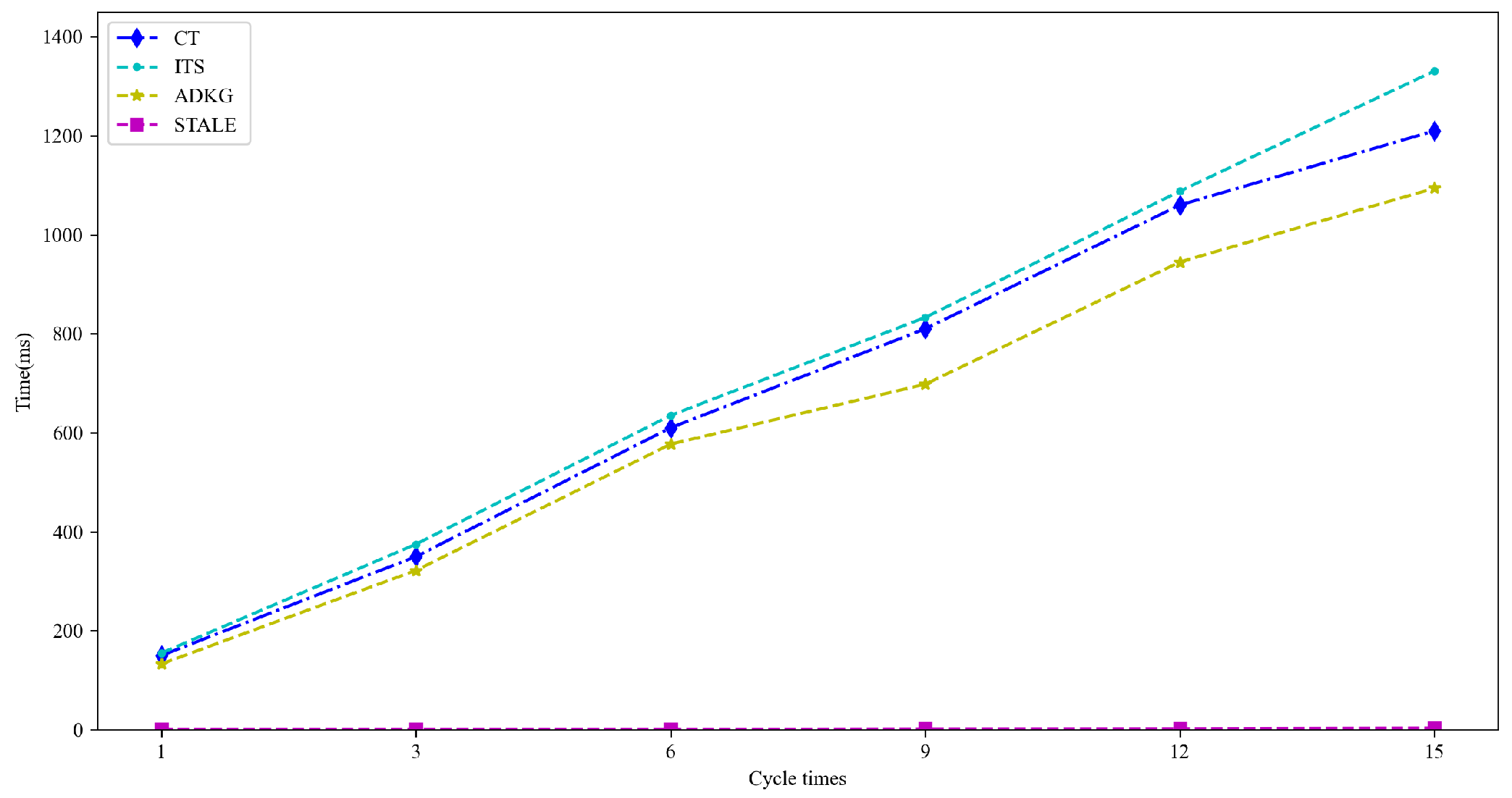
5.2.3. RQ3: What Is the Delay for Identity Registration on the Blockchain?
5.3. Security Analysis
5.3.1. Authenticity and Integrity
5.3.2. Global Applicability and Security of Email Addresses
5.3.3. Anonymity
5.3.4. Data Breach Protection
5.3.5. Resistance to Man-in-the-Middle Attacks
5.3.6. Performance and Scalability
5.4. Economic Cost Analysis
6. Conclusions and Future Work
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| ASP | Authorized Service Provider |
| CL-PKC | Certificateless Public Key Cryptography |
| ECDH | Elliptic Curve Diffie–Hellman |
| ECDHE | Elliptic Curve Diffie–Hellman Ephemeral |
| CA | Certificate Authority |
| PKI | Public Key Infrastructure |
| KGC | Key-Generation Center |
| RSA | Rivest–Shamir–Adleman |
| DID | Decentralized Identity |
| ECC | Elliptic Curve Cryptography |
| CLC | Certificateless Cryptosystems |
| IBE | Identity-Based Encryption |
| PKG | Private Key Generator |
| UCAP | Universal Certificate Authority Pool |
| DLT | Distributed Ledger Technology |
| GDPR | General Data Protection Regulation |
| D2D | Device-to-Device |
References
- Zheng, Y.; Bai, Q.; Zhao, L.; Chun, H.; Chen, J. Design and implementation of PKI-based certification authority. Sixth Int. Conf. Electron. Inf. Eng. 2015, 9794, 629–633. [Google Scholar]
- De Domenico, M.; Baronchelli, A. The fragility of decentralised trustless socio-technical systems. EPJ Data Sci. 2019, 8, 1–6. [Google Scholar] [CrossRef]
- Zhang, R.; Liu, J.; Han, Z.; Zheng, L. An IBE scheme using ECC combined public key. Comput. Electr. Eng. 2010, 36, 1046–1054. [Google Scholar] [CrossRef]
- Park, J.H.; Lee, D.H. An efficient IBE scheme with tight security reduction in the random oracle model. Des. Codes Cryptogr. 2016, 79, 63–85. [Google Scholar] [CrossRef]
- Chen, Y.; Zhang, F. A new certificateless public key encryption scheme. Wuhan Univ. J. Nat. Sci. 2008, 13, 721–726. [Google Scholar] [CrossRef]
- Raghav, R.; Chaudhary, E.A. Authentication System and Authorization System Using Blockchain Technology. In Proceedings of the 2023 IEEE North Karnataka Subsection Flagship International Conference (NKCon), Belagavi, India, 19–20 November 2023; pp. 1–6. [Google Scholar]
- Liu, H.; Ge, S.; Tan, G.; Tang, S. Research on Application of Identity Authentication Encryption Technology in Blockchain Scene. In Proceedings of the 8th International Conference on Cyber Security and Information Engineering, Putrajaya, Malaysia, 22–24 September 2023; pp. 126–129. [Google Scholar]
- Lan, F.; Jiang, Y. Optimization Exploration of Digital Identity Authentication Algorithm Based on Blockchain. Appl. Math. Nonlinear Sci. 2024, 9, 1–16. [Google Scholar] [CrossRef]
- Goodell, G.; Aste, T. A decentralized digital identity architecture. Front. Blockchain 2019, 2, 491305. [Google Scholar] [CrossRef]
- Huang, J.; Nicol, D.M. An anatomy of trust in public key infrastructure. Int. J. Crit. Infrastruct. 2017, 13, 238–258. [Google Scholar] [CrossRef]
- Yang, X.; Chen, C.; Ma, T.; Wang, J.; Wang, C. Revocable identity-based proxy re-signature against signing key exposure. PLoS ONE 2018, 13, e0194783. [Google Scholar] [CrossRef]
- Yakubov, A.; Shbair, W.; Wallbom, A.; Sanda, D.; State, R. A blockchain-based PKI management framework. In Proceedings of the The First IEEE/IFIP International Workshop on Managing and Managed by Blockchain (Man2Block) Colocated with IEEE/IFIP NOMS 2018, Tapei, Tawain, 23–27 April 2018. [Google Scholar]
- Lin, L.; Tian, Y.; Liu, Y. A blockchain-based privacy-preserving recommendation mechanism. In Proceedings of the 2021 IEEE 5th International Conference on Cryptography, Security and Privacy (CSP), Zhuhai, China, 8–10 January 2021; pp. 74–78. [Google Scholar]
- Liu, Q.; Gong, B.; Ning, Z. Research on CLPKC-IDPKC cross-domain identity authentication for IoT environment. Comput. Commun. 2020, 157, 410–416. [Google Scholar] [CrossRef]
- Chatterjee, S.; Sarkar, P. Identity-Based Encryption; Springer Science & Business Medial: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Zhang, Y.K.; Tian, J.Y.; Yang, C.; Zhang, Y.C.; Hou, F.T. A Novel IBE Based Authentication Scheme for Network Storage. Adv. Mater. Res. 2012, 452, 791–795. [Google Scholar] [CrossRef]
- Shao, S.; Chen, F.; Xiao, X.; Gu, W.; Lu, Y.; Wang, S.; Tang, W.; Liu, S.; Wu, F.; He, J.; et al. IBE-BCIOT: An IBE based cross-chain communication mechanism of blockchain in IoT. World Wide Web 2021, 24, 1665–1690. [Google Scholar] [CrossRef]
- Chen, J.; Lu, F.; Liu, Y.; Peng, S.; Cai, Z.; Mo, F. Cross trust: A decentralized MA-ABE mechanism for trans-border identity authentication. Int. J. Crit. Infrastruct. Prot. 2024, 44, 100661. [Google Scholar] [CrossRef]
- Adams, C. Security Analysis of a Privacy-Preserving Identity-Based Encryption Architecture. J. Inf. Secur. 2022, 13, 323–336. [Google Scholar] [CrossRef]
- Alimabi, S.; Babu, K.S. Implementing Secure Data Sharing with IBE Using Cloud Based Revocable Storage Systems. 2018. Available online: https://www.ijatir.org/uploads/264351IJATIR17084-164.pdf (accessed on 15 April 2025).
- Afroaz, K.; Rao, Y.V.S.; Rukma, R.N. A key escrow free anonymous identity based encryption scheme using ring signatures. In Proceedings of the 2022 IEEE 11th International Conference on Communication Systems and Network Technologies (CSNT), Indore, India, 23–24 April 2022; pp. 596–600. [Google Scholar]
- Zhang, F.T.; Sun, Y.X.; Zhang, L.; Geng, M.M.; Li, S.J. A study on certificateless public key cryptography. J. Softw. 2011, 22, 1316–1332. [Google Scholar] [CrossRef]
- Hamoud, O.N.; Kenaza, T.; Challal, Y. Towards using multiple KGC for CL-PKC to secure D2D communications. In Proceedings of the 2018 International Conference on Smart Communications in Network Technologies (SaCoNeT), El Oued, Algeria, 27–31 October 2018; pp. 283–287. [Google Scholar]
- Liu, Y.; Zhang, A.; Li, J.; Wu, J. An anonymous distributed key management system based on CL-PKC for space information network. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–7. [Google Scholar]
- Vasala, U.; Sakthidharan, D.G. Effective key management in dynamic wireless sensor networks. Int. J. Comput. Eng. Res. Trends 2017, 4, 308–312. [Google Scholar]
- Malik, M.; Kamaldeep; Dutta, M. On the Applicability of Certificateless Public Key Cryptography (CL-PKC) for Securing the Internet of Things (IoT). In Proceedings of the International Conference on IoT Inclusive Life (ICIIL 2019), NITTTR Chandigarh, India; Springer: Singapore, 2020; pp. 43–50. [Google Scholar]
- Wang, X.; Gu, C.; Wei, F.; Lu, S.; Li, Z. A Certificateless-Based Authentication and Key Agreement Scheme for IIoT Cross-Domain. Secur. Commun. Netw. 2022, 2022, 3693748. [Google Scholar] [CrossRef]
- Feng, L.; Qiu, F.; Hu, K.; Yu, B.; Lin, J.; Yao, S. CABC: A Cross-Domain Authentication Method Combining Blockchain with Certificateless Signature for IIoT. Future Gener. Comput. Syst. 2024, 158, 516–529. [Google Scholar] [CrossRef]
- Cao, L.; Liang, M.; Zhang, Z.; Cao, S. Certificateless Cross-Domain Group Authentication Key Agreement Scheme Based on ECC. Wirel. Commun. Mob. Comput. 2022, 2022, 7519688. [Google Scholar] [CrossRef]
- Kurbatov, O.; Shapoval, O.; Poluyanenko, N.; Kuznetsova, T.; Kravchenko, P. Decentralized Identification and Certification System. In Proceedings of the 2019 IEEE International Scientific-Practical Conference Problems of Infocommunications, Science and Technology (PIC S&T), Kyiv, Ukraine, 8–11 October 2019; pp. 507–510. [Google Scholar]
- Bai, Y.; Liu, Z.; Liu, X.; Lu, X.; Lei, H. A cross-chain identity authentication scheme based on DID. In Proceedings of the 2023 IEEE International Conference on Blockchain (Blockchain), Hainan, China, 17–21 December 2023; pp. 172–179. [Google Scholar]
- Zhong, T.; Shi, P.; Chang, J. Joint cloud cross-chain verification model of decentralized identifiers. In Proceedings of the 2021 IEEE International Performance, Computing, and Communications Conference (IPCCC), Austin, TX, USA, 29–31 October 2021; pp. 1–8. [Google Scholar]
- Huh, S.; Shim, M.; Lee, J.; Woo, S.S.; Kim, H.; Lee, H. Did we miss anything?: Towards privacy-preserving decentralized id architecture. IEEE Trans. Dependable Secur. Comput. 2023, 20, 4881–4898. [Google Scholar] [CrossRef]
- Park, C.S.; Nam, H.M. A new approach to constructing decentralized identifier for secure and flexible key rotation. IEEE Internet Things J. 2021, 9, 10610–10624. [Google Scholar] [CrossRef]
- Irwanto, F.; Jodis, J.; Indrakusuma, E.; Gui, A. Decentralized Identity (DID) for Know Your Customer (KYC) Process in the Banking Industry. In Proceedings of the 2023 IEEE 9th International Conference on Computing, Engineering and Design (ICCED), Kuala Lumpur, Malaysia, 7–8 November 2023; pp. 1–6. [Google Scholar]
- Alzahrani, B. An information-centric networking based registry for decentralized identifiers and verifiable credentials. IEEE Access 2020, 8, 137198–137208. [Google Scholar] [CrossRef]
- Li, Z.; Xu, Z.; Liang, C. Distributed Key Management Scheme Based on CL-PKC in P2P Networks. In Threats, Countermeasures, and Advances in Applied Information Security; IGI Global: Hershey, PA, USA, 2012; pp. 234–247. [Google Scholar]
- Xu, D.; Wang, W.; Zhu, L.; Zhao, J.; Wu, F.; Gao, J. CL-BC: A Secure Data Storage Model for Social Networks. Secur. Commun. Netw. 2022, 2022, 5428539. [Google Scholar] [CrossRef]
- Cheng, Z.; Chen, L. Certificateless public key signature schemes from standard algorithms. In Information Security Practice and Experience: 14th International Conference, ISPEC 2018, Tokyo, Japan, 25–27 September 2018; Proceedings 14; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; pp. 179–197. [Google Scholar]
- Xu, M.; Chen, B.; Tan, Z.; Chen, S.; Wang, L.; Liu, Y.; San, T.I.; Fong, S.W.; Wang, W.; Feng, J. AHAC: Advanced Network-Hiding Access Control Framework. Appl. Sci. 2024, 14, 5593. [Google Scholar] [CrossRef]
- Bagga, P.; Das, A.K.; Wazid, M.; Rodrigues, J.J.P.C.; Choo, K.-K.R.; Park, Y. On the design of mutual authentication and key agreement protocol in internet of vehicles-enabled intelligent transportation system. IEEE Trans. Veh. Technol. 2021, 70, 1736–1751. [Google Scholar] [CrossRef]
- Das, S.; Yurek, T.; Xiang, Z.; Miller, A.; Kokoris-Kogias, L.; Ren, L. Practical asynchronous distributed key generation. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 22–26 May 2022; pp. 2518–2534. [Google Scholar]
- Wang, Z.; Han, Z.; Liu, J.; Zhang, D. An authentication scheme based on PTPM and certificateless public key in cloud environment. J. Softw. 2016, 27, 1523–1537. [Google Scholar]
- Yang, X.; An, F.; Yang, P.; Liu, T.; Wang, C. A cross-domain authentication scheme based on certificateless signature in the cloud. Comput. Eng. 2017, 43, 128–133. [Google Scholar]
- Wang, X.; Chen, Z. An authentication scheme based on educational blockchain with certificateless signature. Comput. Syst. Appl. 2022, 31, 178–187. [Google Scholar]

| Function | Description |
|---|---|
| KGC-RandomNumber() | Generates KGC random numbers |
| MasterKeyPair() | Generates the KGC system main public and private key. |
| User-PartialKey() | Generates the secret value and user public value |
| () | Calculate user hash value |
| () | Calculate KGC parameters |
| User-UserPartialKey() | Generates the user’s declared public key and the user’s partial private key |
| User-PrivateKey() | Generates the user’s private key |
| User-RealPublicKey() | Generates the user’s public key |
| User-PublicKey() | Verifies whether the public and private keys are paired |
| Notation | Description |
|---|---|
| User identification | |
| Base point x-coordinate | |
| Base point y-coordinate | |
| n | Base point order |
| A finite field containing q elements | |
| Elements in that define an elliptic curve over | |
| Two bytes converted from | |
| Cryptographic hash algorithm with message digest length v bits | |
| User partial private key (secret value) | |
| User partial public key (public value) | |
| KGC master private key | |
| KGC master public key | |
| W | KGC random number |
| KGC generates User statement public key for User | |
| KGC generates User partial private key for User | |
| User full private key | |
| Actual public key of the User | |
| Verify User public key | |
| S | Party A calculates the shared key |
| Party B calculates the shared key |
| Programmes | Registration Phase Overhead | Communication/Authentication Phase Overhead | Total Overhead (bits) |
|---|---|---|---|
| Literature [43] | 1120 | ||
| Literature [44] | 1392 | ||
| Literature [45] | 1168 | ||
| Our method | 352 |
| Experiment Number | 1 | 5 | 10 | 20 | 50 |
|---|---|---|---|---|---|
| Time(s) | 10.27 | 9.34 | 9.58 | 11.27 | 8.66 |
| Company Name | Country | Total Operating Cost | Certificate Management Cost | Market Share | Main Business |
|---|---|---|---|---|---|
| DigiCert | USA | 350 | 120 | 30% | SSL Certificates, PKI |
| Entrust | USA | 280 | 100 | 25% | PKI, Digital Signatures |
| Sectigo | USA | 210 | 90 | 18% | SSL, Digital Certificates |
| TrustSign CA | China | 208 | 83 | 25% | Electronic Authentication, Digital Signatures |
| Shenzhen CA | China | 194 | 69 | 22% | Electronic Authentication, Enterprise Services |
| GlobalSign Europe | UK | 170 | 65 | 18% | SSL, PKI, IoT Security |
| D-Trust (Bundesdruckerei) | Germany | 135 | 55 | 12% | Digital Signatures, Enterprise Security, SSL |
| SECOM Trust Systems | Japan | 190 | 80 | 20% | SSL, Digital Signatures, PKI |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zheng, J.; Xu, M.; Li, J.; Chen, B.; Tan, Z.; Wang, A.; Zhang, S.; Liu, Y.; Zhang, K.Q.; Zheng, L.; et al. STALE: A Scalable and Secure Trans-Border Authentication Scheme Leveraging Email and ECDH Key Exchange. Electronics 2025, 14, 2399. https://doi.org/10.3390/electronics14122399
Zheng J, Xu M, Li J, Chen B, Tan Z, Wang A, Zhang S, Liu Y, Zhang KQ, Zheng L, et al. STALE: A Scalable and Secure Trans-Border Authentication Scheme Leveraging Email and ECDH Key Exchange. Electronics. 2025; 14(12):2399. https://doi.org/10.3390/electronics14122399
Chicago/Turabian StyleZheng, Jiexin, Mudi Xu, Jianqing Li, Benfeng Chen, Zhizhong Tan, Anyu Wang, Shuo Zhang, Yan Liu, Kevin Qi Zhang, Lirong Zheng, and et al. 2025. "STALE: A Scalable and Secure Trans-Border Authentication Scheme Leveraging Email and ECDH Key Exchange" Electronics 14, no. 12: 2399. https://doi.org/10.3390/electronics14122399
APA StyleZheng, J., Xu, M., Li, J., Chen, B., Tan, Z., Wang, A., Zhang, S., Liu, Y., Zhang, K. Q., Zheng, L., & Wang, W. (2025). STALE: A Scalable and Secure Trans-Border Authentication Scheme Leveraging Email and ECDH Key Exchange. Electronics, 14(12), 2399. https://doi.org/10.3390/electronics14122399







