Consensus Optimization Algorithm for Distributed Intelligent Medical Diagnostic Collaborative Systems Based on Verifiable Random Functions and Reputation Mechanisms
Abstract
1. Introduction
1.1. Related Work
1.2. Contribution
- (1)
- Technical Innovation: In this study, an improved consensus algorithm, VS-PBFT, which incorporates a verifiable random function and dynamic reputation mechanism, is proposed based on the PBFT consensus mechanism. In the leader node selection process, VRF provides cryptographic randomness, avoiding the predictability issues of traditional mechanisms. Meanwhile, the reputation mechanism dynamically adjusts the nodes’ priorities, optimizing efficiency and security in the consensus process. The combination of both effectively reduces the risk of single-point attacks, enhancing the system’s robustness and stability.
- (2)
- Application Scenario Design: Based on the proposed consensus algorithm, this study designs a distributed diagnosis collaboration system model for intelligent medical scenarios, which serves as a typical application case of the VS-PBFT algorithm, and is used to validate its application potential in medical data security and collaborative processing. The model embodies the applicability of the algorithm in privacy protection, data immutability, and multi-agency collaboration at the system architecture level, which helps to demonstrate the practical value of the proposed algorithm in real complex scenarios.
1.3. Organization
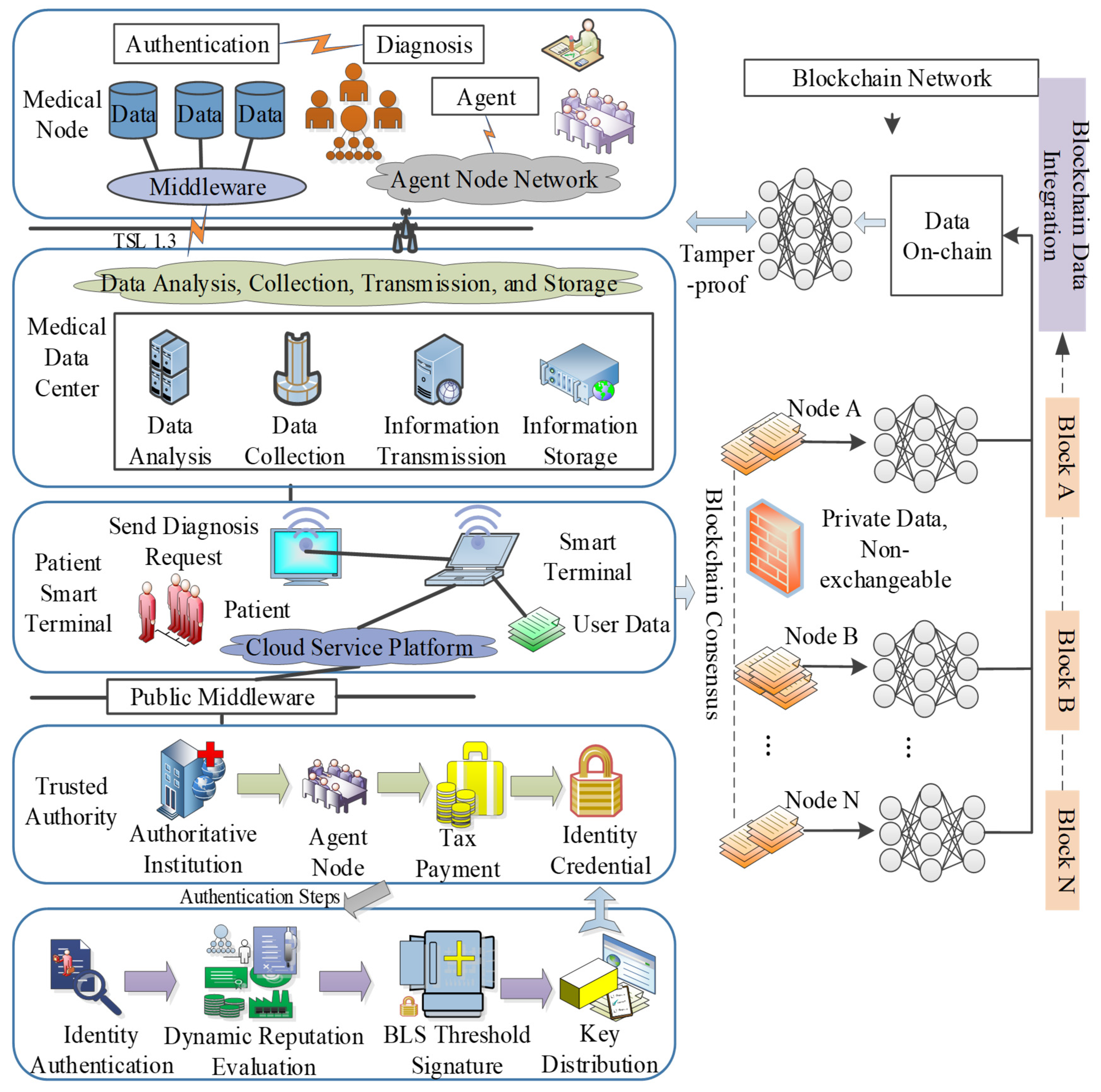
2. System Model Design and Scheme Setup
2.1. Model Design
2.2. System Objectives
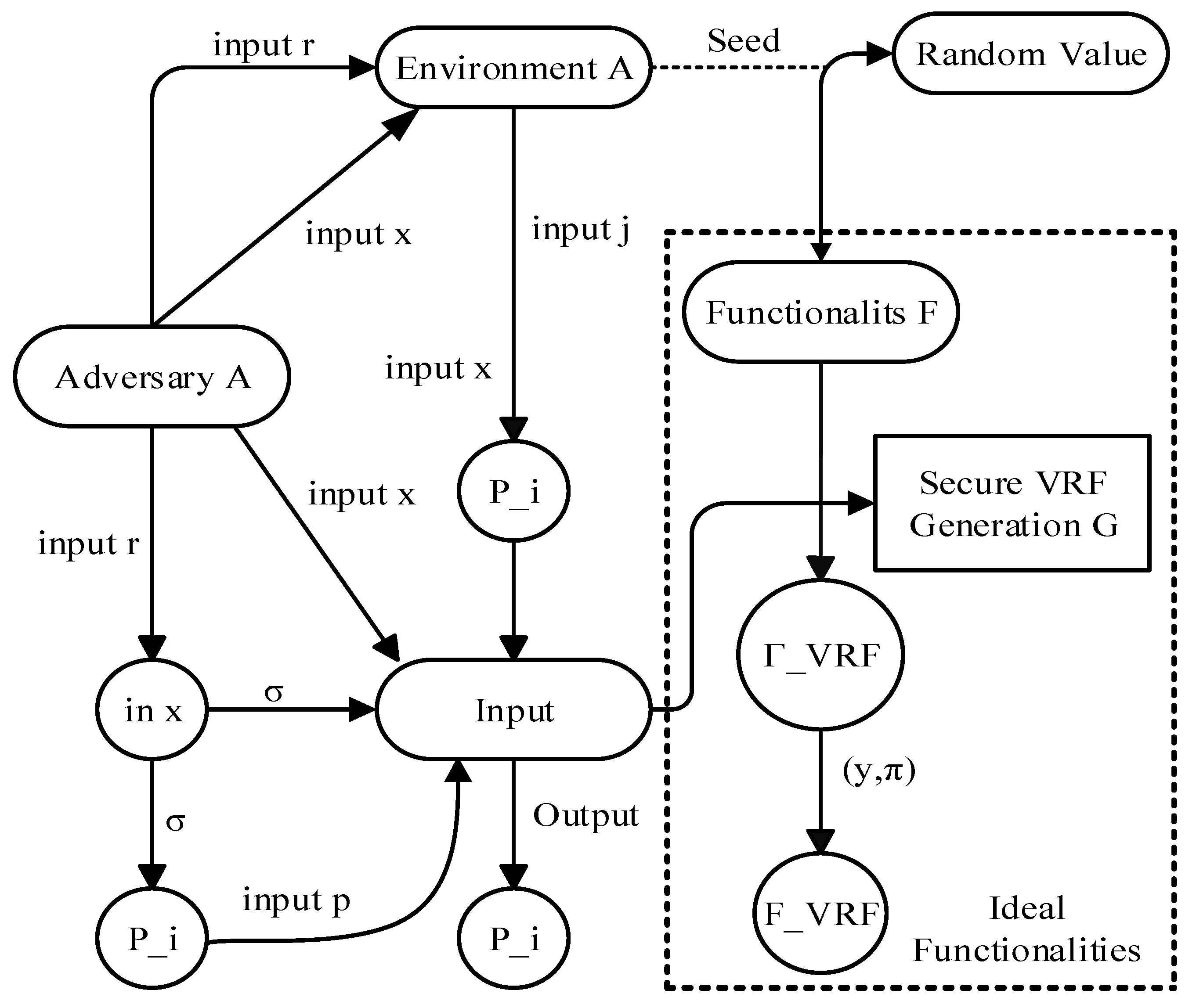
3. VS-PBFT Algorithm Based on the Combination of Reputation Mechanism and Verifiable Random Function (VRF)
3.1. Optimization of Master Node Selection Mechanism of Enhanced VS-PBFT Consensus Algorithm Based on VRF
- Verifiability: For all key pairs and strings , if , then there exists a negligible polynomial , such that:
- Uniqueness: For all key pairs and prime strings , there exists no such that and hold simultaneously, i.e.,:
- For all functions where obeys the PPT distribution, there exists a negligible polynomial , such that:
3.1.1. Key Generation for VRF
3.1.2. Generation and Output of Random Numbers
3.1.3. Proof Generation
| Algorithm 1 VRF Proof Generation Algorithm |
| Input: Secret key sk, Message m |
| Output: Proof π |
| 1: CP(sk, m): |
| 2: SD ← sk[0…31] |
| 3: HS ← Init_SHA512() |
| 4: HS ← Up(HS, SD) |
| 5: HS ← Up(HS, m) |
| 6: H ← R(HS) |
| 7: π ← S(h, sk) |
| 8: return −1 |
| 9: if VS(H, π, DP(sk)) = F then |
| 10: return CP(sk, m) |
| 11: else |
| 12: return π |
| 13: End if |
3.1.4. VRF Proof Verification
3.1.5. Master Node Election Process
| Algorithm 2 VRF-based View Change Algorithm |
| INPUT: Current view v, Number of nodes N, Current leader LC |
| OUTPUT: New leader LN, New view v’ |
| 1: CV(v, N, L): |
| 2: v’ ← v + 1 |
| 3: NI ← r[0] mod N |
| 4: SD ← “leader-election” || v’ |
| 5: (pk, sk) ← G(λ) |
| 6: π ← CP(sk, SD) |
| 7: r ← CO(π) |
| 8: CL ← r[0] mod N |
| 9: if CL = L then |
| 10: LN ← (CL + 1) mod N |
| 11: else |
| 12: LN ← CL |
| 13: End i |
| 14: BV(v’, LN, π, r) |
| 15: return (LN, v’) |
3.2. Research on Enhanced VS-PBFT Consensus Algorithm Based on Dynamic Reputation Mechanism
3.2.1. Credibility Constraints on the Consensus Process
3.2.2. Combination of Credibility Update and Consensus Process
| Algorithm 3 Reputation-Weighted Message Verification Algorithm |
| INPUT: Message m, Sender ID s, Recipient ID r, Current reputations {Rep_i}_{i = 1}^N |
| OUTPUT: Boolean result, Updated reputation R’ |
| 1: VM(m, s, r, {R}_{i = 1}^N): |
| 2: θ ← 30.0 |
| 3: if CanP(s, R, θ) = F then |
| 4: return (F, R) |
| 5: End if |
| 6: SV ← (m[6] = ‘1’) |
| 7: CM ← (CCT(m[3]) = CI) |
| 8: VIM ← (CCT(m[4]) = VIN) |
| 9: if SV ∧ CM ∧ VIM then |
| 10: R’ ← UR(s, R, T) |
| 11: return (T, R’) |
| 12: else |
| 13: R’ ← UR(s, R, F) |
| 14: return (F, R’) |
| 15: End if |
4. Experimental Results and Analysis
4.1. Experimental Environment Setup
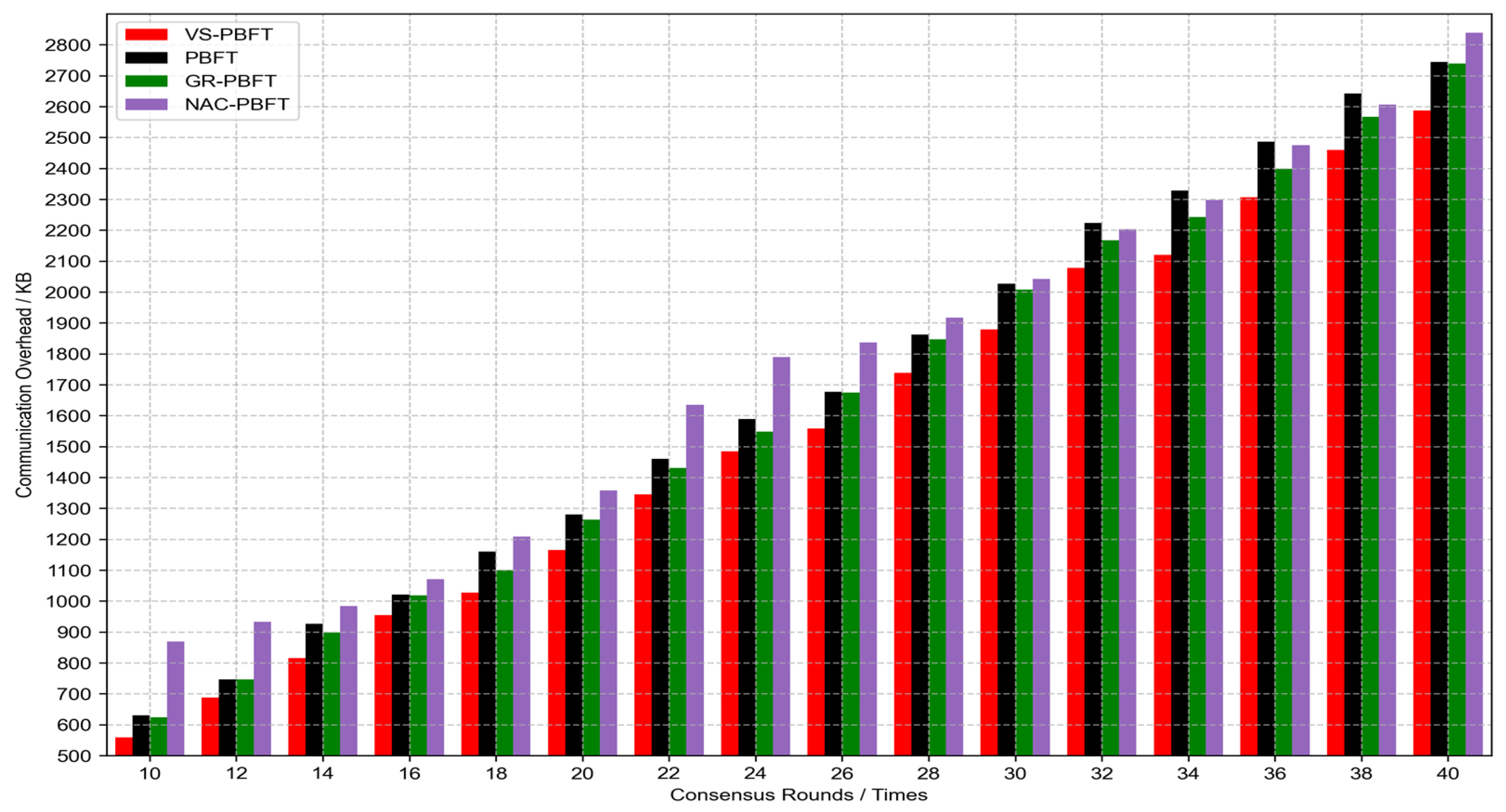
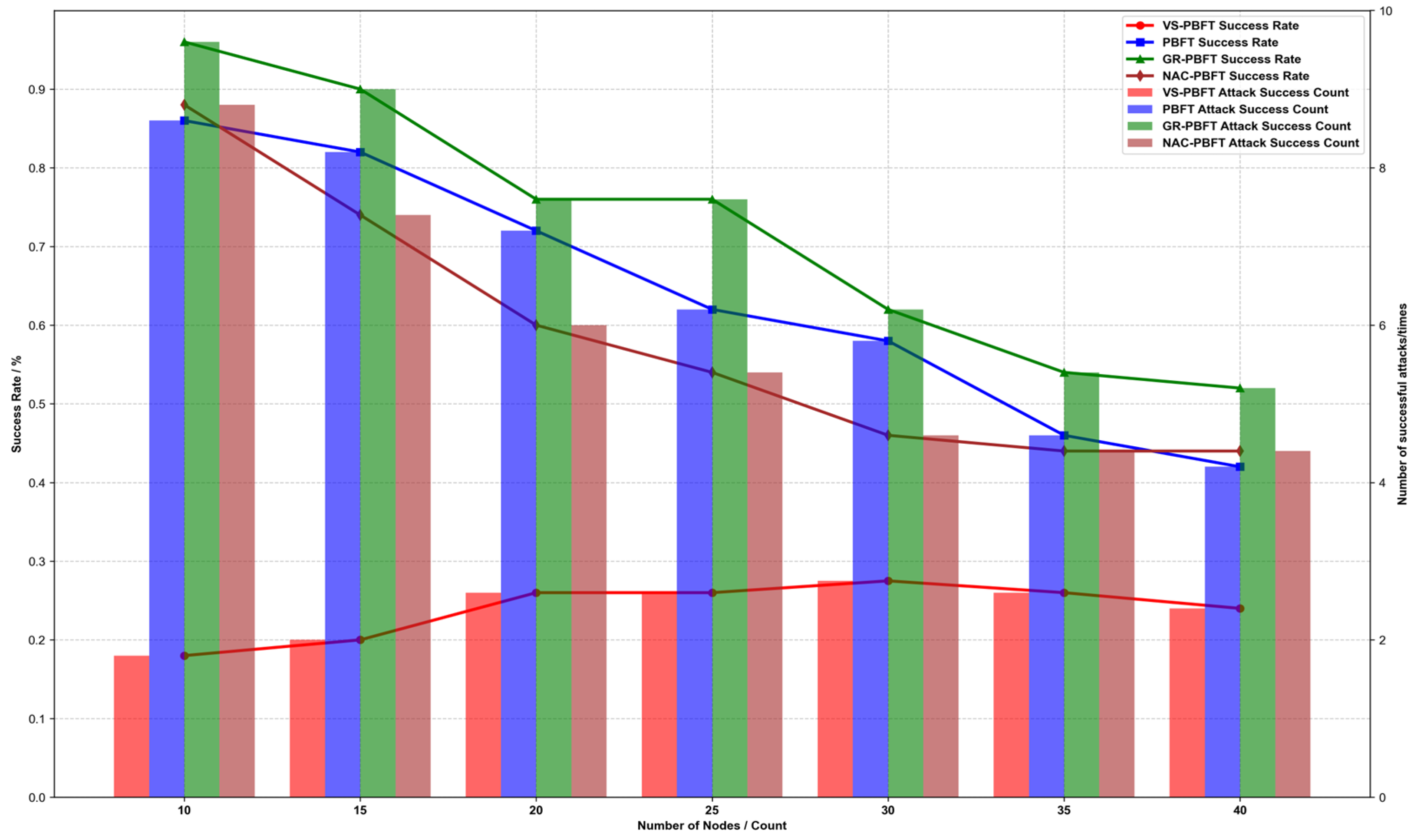
4.2. Experimental Results
5. Conclusions
5.1. Research Summary
5.2. Limitations and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 25 April 2025).
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the IEEE International Congress on Big Data, Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar]
- Castro, M.; Liskov, B. Practical Byzantine Fault Tolerance and Proactive Recovery. ACM Trans. Comput. Syst. 2002, 20, 398–461. [Google Scholar] [CrossRef]
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine Generals Problem. In Concurrency: The Works of Leslie Lamport; Association for Computing Machinery: New York, NY, USA, 2019; pp. 203–226. [Google Scholar]
- Sousa, J.; Bessani, A.; Vukolić, M. A Byzantine Fault-Tolerant Ordering Service for the Hyperledger Fabric Blockchain Platform. In Proceedings of the IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Naples, Italy, 23–26 June 2018; pp. 51–58. [Google Scholar]
- Chen, L.; Xu, L.; Shah, N.; Gao, Z.; Lu, Y.; Shi, W. On Security Analysis of Proof-of-Elapsed-Time (PoET). In Proceedings of the International Symposium on Stabilization, Safety, and Security of Distributed Systems, Boston, MA, USA, 5–8 November 2017; pp. 282–297. [Google Scholar]
- Ekparinya, P.; Gramoli, V.; Jourjon, G. The Attack of the Clones Against Proof-of-Authority. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 24–27 February 2019. [Google Scholar]
- Cai, S.; Han, T.; Wang, Y.; Zhang, H. Study of Blockchain’s Consensus Mechanism Based on Score: An Improved Consensus Mechanism. IET Blockchain 2021, 1, 41–55. [Google Scholar] [CrossRef]
- Micali, S.; Rabin, M.; Vadhan, S. Verifiable Random Functions. In Proceedings of the IEEE Annual Symposium on Foundations of Computer Science, New York, NY, USA, 17–19 October 1999; pp. 120–130. [Google Scholar]
- Gilad, Y.; Hemo, R.; Micali, S.; Vlachos, G.; Zeldovich, N. Algorand: Scaling Byzantine Agreements for Cryptocurrencies. In Proceedings of the ACM Symposium on Operating Systems Principles (SOSP), Shanghai, China, 29–31 October 2017; pp. 51–68. [Google Scholar]
- Hanke, T.; Movahedi, M.; Williams, D. DFINITY Technology Overview Series, Consensus System. arXiv 2018, arXiv:1805.04548. [Google Scholar]
- Hoffman, K.; Zage, D.; Nita-Rotaru, C. A Survey of Attack and Defense Techniques for Reputation Systems. ACM Comput. Surv. 2009, 42, 1–31. [Google Scholar] [CrossRef]
- Kamvar, S.D.; Schlosser, M.T.; Garcia-Molina, H. The Eigentrust Algorithm for Reputation Management in P2P Networks. In Proceedings of the International Conference on World Wide Web (WWW), Budapest, Hungary, 20–24 May 2003; pp. 640–651. [Google Scholar]
- Jøsang, A.; Ismail, R.; Boyd, C. A survey of trust and reputation systems for online service provision. Decis Support Syst. 2007, 43, 618–644. [Google Scholar] [CrossRef]
- Yang, Z.; Yang, K.; Lei, L.; Zheng, K.; Leung, V.C. Blockchain-Based Decentralized Trust Management in Vehicular Networks. IEEE Internet Things J. 2018, 6, 1495–1505. [Google Scholar] [CrossRef]
- U.S. Department of Health and Human Services. Summary of the HIPAA Privacy Rule. Available online: https://www.hhs.gov/hipaa/for-professionals/privacy/guidance/general-overview/index.html (accessed on 26 April 2025).
- European Data Protection Board. EDPB Adopts Guidelines on Processing Personal Data Through Blockchains, April 2025. Available online: https://edpb.europa.eu (accessed on 26 April 2025).
- Nunes, T.; Rupino da Cunha, P. Reflections about Blockchain in Health Data Sharing: Navigating a Disruptive Technology. Digital Health 2024, 10, 230. [Google Scholar] [PubMed Central]
- Croman, K.; Decker, C.; Eyal, I.; Gencer, A.E.; Juels, A.; Kosba, A.; Wattenhofer, R. On Scaling Decentralized Blockchains. In Proceedings of the 3rd Workshop on Bitcoin and Blockchain Research; Springer: Berlin/Heidelberg, Germany, 2016; pp. 106–125. [Google Scholar]
- Xie, M.; Liu, J.; Chen, S.; Lin, M. A Survey on Blockchain Consensus Mechanism: Research Overview, Current Advances and Future Directions. Int. J. Intell. Comput. Cybern. 2023, 16, 314–340. [Google Scholar] [CrossRef]
- Barreno, M.; Nelson, B.; Joseph, A.D.; Tygar, J.D. The security of machine learning. Mach. Learn. 2010, 81, 121–148. [Google Scholar] [CrossRef]
- Goodfellow, I.; Shlens, J.; Szegedy, C. Explaining and harnessing adversarial examples. arXiv 2014, arXiv:1412.6572. [Google Scholar]
- Lei, K.; Zhang, Q.; Xu, L.; Qi, Z. Reputation-Based Byzantine Fault-Tolerance for Consortium Blockchain. In Proceedings of the 24th IEEE International Conference on Parallel and Distributed Systems (ICPADS), Singapore, 11–13 December 2018; pp. 604–611. [Google Scholar]
- Chen, J.; Zhang, X.; Shangguan, P. Improved PBFT Algorithm Based on Reputation and Voting Mechanism. Proc. J. Phys. Conf. Ser. 2020, 1486, 032023. [Google Scholar] [CrossRef]
- Wang, T.; Guo, J.; Ai, S.; Cao, J. RBT: A Distributed Reputation System for Blockchain-Based Peer-to-Peer Energy Trading with Fairness Consideration. Appl. Energy 2021, 295, 117056. [Google Scholar] [CrossRef]
- Gu, R.; Chen, B.; Huang, D. Primary Node Selection Algorithm of PBFT Based on Anomaly Detection and Reputation Model. In Proceedings of the 11th International Conference on Computer Engineering and Networks, Beijing, China, 9–11 December 2022; Springer: Singapore, 2022; pp. 1613–1622. [Google Scholar]
- Biggio, B.; Corona, I.; Maiorca, D.; Nelson, B.; Šrndić, N.; Laskov, P.; Giacinto, G.; Roli, F. Evasion attacks against machine learning at test time. In Proceedings of the European Conference on Machine Learning and Principles and Practice of Knowledge Discovery in Databases (ECML PKDD), Prague, Czech Republic, 23–27 September 2013; pp. 387–402. [Google Scholar]
- Niu, K.; Yao, Z.; Si, X. Improved PBFT Consensus Algorithm Based on Reputation Value for IoT. In Proceedings of the 4th International Conference on Blockchain Technology and Information Security (ICBCTIS), Wuhan, China, 17–19 August 2024; IEEE: New York, NY, USA, 2024; pp. 185–190. [Google Scholar]
- Gura, N.; Patel, A.; Wander, A.; Eberle, H.; Shantz, S.C. Comparing elliptic curve cryptography and RSA on 8-bit CPUs. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems (CHES), Cambridge, MA, USA, 11–13 August 2004; pp. 119–132. [Google Scholar]
- Cascudo, I.; David, B. SCRAPE: Scalable Randomness Attested by Public Entities. In Proceedings of the International Conference on Theory and Applications of Cryptology and Information Security, Hong Kong, China, 3–7 December 2017; Springer: Cham, Switzerland, 2017; pp. 3–32. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Yellick, J. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the 13th EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Kietzmann, P.; Schmidt, T.C.; Wählisch, M. A guideline on pseudorandom number generation (PRNG) in the IoT. arXiv 2020, arXiv:2007.11839. [Google Scholar] [CrossRef]
- Seo, H.; Azarderakhsh, R. Efficient Curve448 on Cortex-M4. IACR Cryptology ePrint Archive. Report 2021/1355, 2021. Available online: https://eprint.iacr.org/2021/1355 (accessed on 25 April 2025).
- Zhang, Q.; Wang, S.; Zhang, D.; Wang, J.; Sun, J. FortunChain: EC-VRF-Based Scalable Blockchain System for Realizing State Sharding. IEEE Trans. Netw. Serv. Manag. 2023, 20, 4340–4353. [Google Scholar] [CrossRef]
- Jiang, C.; Guo, C.; Shan, C.; Zhang, Y. VPBFT: Improved PBFT Consensus Algorithm Based on VRF and PageRank Algorithm. In Proceedings of the International Conference on Blockchain and Trustworthy Systems, Haikou, China, 8–10 August 2023; Springer Nature: Singapore, 2023; pp. 237–251. [Google Scholar]
- Chen, P.; Chen, Y.; Tan, C.; Yang, Y.; Li, B.; Huang, J. Slicing PBFT Consensus Algorithm Based on VRF. In Proceedings of the IEEE International Conference on Blockchain, Copenhagen, Denmark, 19–22 August 2024; IEEE: New York, NY, USA, 2024; pp. 569–574. [Google Scholar]
- Benet, J. IPFS—Content Addressed, Versioned, P2P File System. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Pass, R.; Seeman, L.; Shelat, A. Analysis of the Blockchain Protocol in Asynchronous Networks. In Advances in Cryptology—EUROCRYPT 2017, Proceedings 36th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Paris, France, 30 April–4 May 2017; Springer: Cham, Switzerland, 2017; pp. 643–673. [Google Scholar]



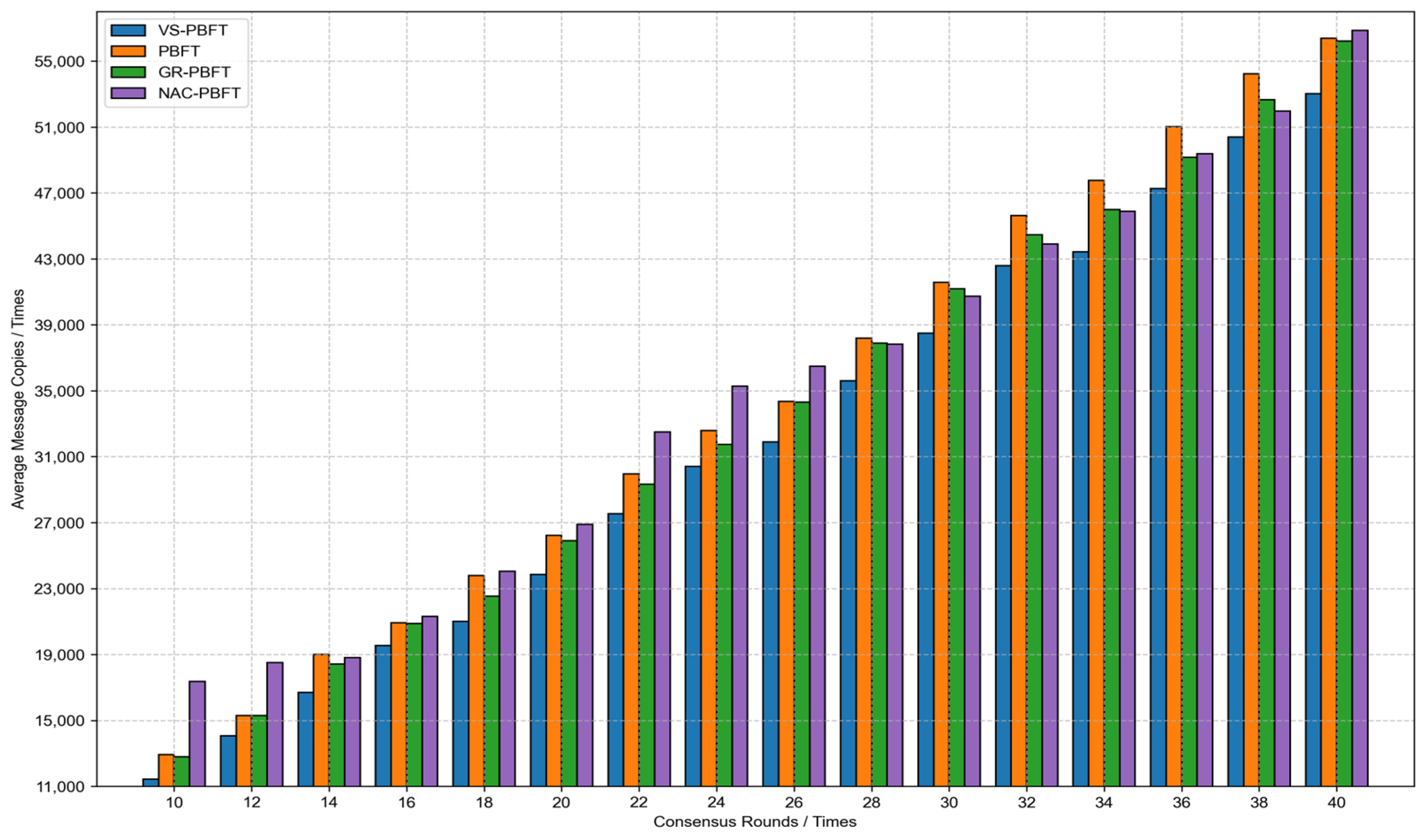

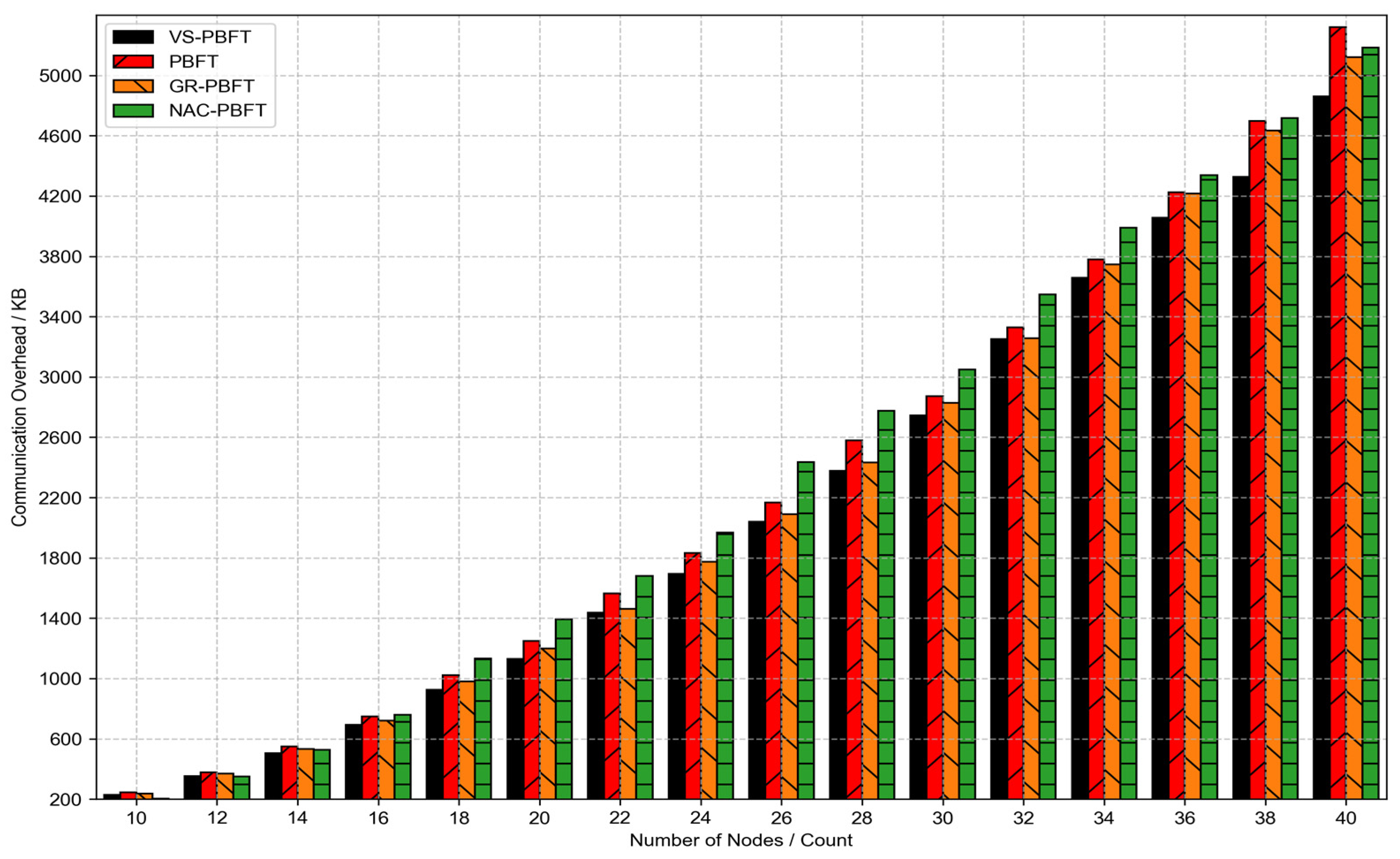



| Evaluation Metric | VS-PBFT | PBFT | GR-PBFT | NAC-PBFT | POW | POS |
|---|---|---|---|---|---|---|
| High Transaction Throughput | √ | √ | × | √ | √ | × |
| Low Transaction Latency | √ | × | √ | × | × | √ |
| Good Scalability | √ | × | × | × | √ | √ |
| Strong Security | √ | × | × | √ | × | √ |
| High Fault Tolerance | √ | √ | × | √ | × | × |
| Low Resource Consumption | √ | × | √ | √ | × | × |
| Low Communication Overhead | √ | × | √ | × | × | √ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, S.; Zhang, Y.; Zhao, Y. Consensus Optimization Algorithm for Distributed Intelligent Medical Diagnostic Collaborative Systems Based on Verifiable Random Functions and Reputation Mechanisms. Electronics 2025, 14, 2020. https://doi.org/10.3390/electronics14102020
Liu S, Zhang Y, Zhao Y. Consensus Optimization Algorithm for Distributed Intelligent Medical Diagnostic Collaborative Systems Based on Verifiable Random Functions and Reputation Mechanisms. Electronics. 2025; 14(10):2020. https://doi.org/10.3390/electronics14102020
Chicago/Turabian StyleLiu, Shizhuang, Yang Zhang, and Yating Zhao. 2025. "Consensus Optimization Algorithm for Distributed Intelligent Medical Diagnostic Collaborative Systems Based on Verifiable Random Functions and Reputation Mechanisms" Electronics 14, no. 10: 2020. https://doi.org/10.3390/electronics14102020
APA StyleLiu, S., Zhang, Y., & Zhao, Y. (2025). Consensus Optimization Algorithm for Distributed Intelligent Medical Diagnostic Collaborative Systems Based on Verifiable Random Functions and Reputation Mechanisms. Electronics, 14(10), 2020. https://doi.org/10.3390/electronics14102020




