Efficient Post-Quantum Cryptography Algorithms for Auto-Enrollment in Public Key Infrastructure
Abstract
1. Introduction
Key Contributions
- Post-quantum integration in the SCEP: It presents the first known integration of post-quantum cryptographic (PQC) signature schemes—CRYSTALS–Dilithium, Falcon, and SPHINCS+—into the widely used Simple Certificate Enrollment Protocol (SCEP), enhancing its resilience against quantum-era threats.
- Performance and resource evaluation: This study benchmarks multiple PQC variants across the performance, throughput, and resource consumption metrics, identifying Dilithium2 and Falcon512 as the most efficient candidates for secure certificate enrollment.
- Resource-constrained device analysis: It evaluates the algorithms’ suitability for constrained environments such as IoT and embedded systems, providing practical guidance for real-world PQC deployment on low-power platforms.
- Scalability and deployment insights: This work examines the protocol’s behavior in large-scale deployment scenarios and discusses compatibility considerations, migration strategies from the RSA/ECC, and implementation security challenges.
2. Research Motivation
2.1. Improve Security Enrollment Protocols Against Quantum Attacks
2.2. Comparative Analysis of Certificate Enrollment Protocols
3. Literature Review
3.1. Research Works That Implemented the Traditional Public Key for Auto-Enrollment
3.2. Research Works Using PQ Crypto Algorithms
3.3. Research Gaps
- -
- Lack of integration: Post-quantum cryptographic algorithms and their successful integration into current PKI systems, particularly regarding device registration procedures, are not well studied.
- -
- Performance and resource impact: Not much research has been performed on how applying PQ algorithms in device enrollment scenarios may affect performance and resource needs. It is essential to comprehend how these algorithms affect the effectiveness and speed of enrollment procedures [25].
- -
- Practical implementation: The PKI infrastructure, including device enrollment systems, lacks case studies and practical instructions on how to switch from classical to post-quantum cryptography techniques [26].
4. Research Methods
4.1. Implementation of Research Work
4.1.1. Establishment of Independent PQ CAs
- -
- Dilithium2: A variant of the Dilithium post-quantum signature scheme, designed for efficiency and strong security.
- -
- Dilithium3: An advanced variant providing enhanced security and performance improvements over Dilithium2.
- -
- Dilithium5: The base version of the Dilithium scheme.
- -
- Falcon512: A variant providing strong security with a focus on compact signatures.
- -
- Falcon1024: A variant offering higher security levels with larger signature sizes.
- -
- SPHINCS+-SHA256-128f-robust: A variant using the SHA256 hash function, designed for robustness and security.
- -
- SPHINCS+-Haraka-128f-robust: A variant using the Haraka hash function, focusing on performance and robustness.
- -
- SPHINCS+-SHAKE256-128f-robust: A variant using the SHAKE256 hash function, combining high security with efficiency.
- -
- OpenXPKI: Open-source public key infrastructure (PKI) software solution designed for managing digital certificates, cryptographic keys, and customizable certificate workflows. Issuance of the certificate is done via OpenXPKI.
- -
- LibOQS: Open-source C library developed by the Open Quantum Safe (OQS) project, providing implementations of post-quantum cryptographic algorithms for key encapsulation and digital signatures, along with a common API and testing tools to facilitate integration and evaluation within various applications and protocols.
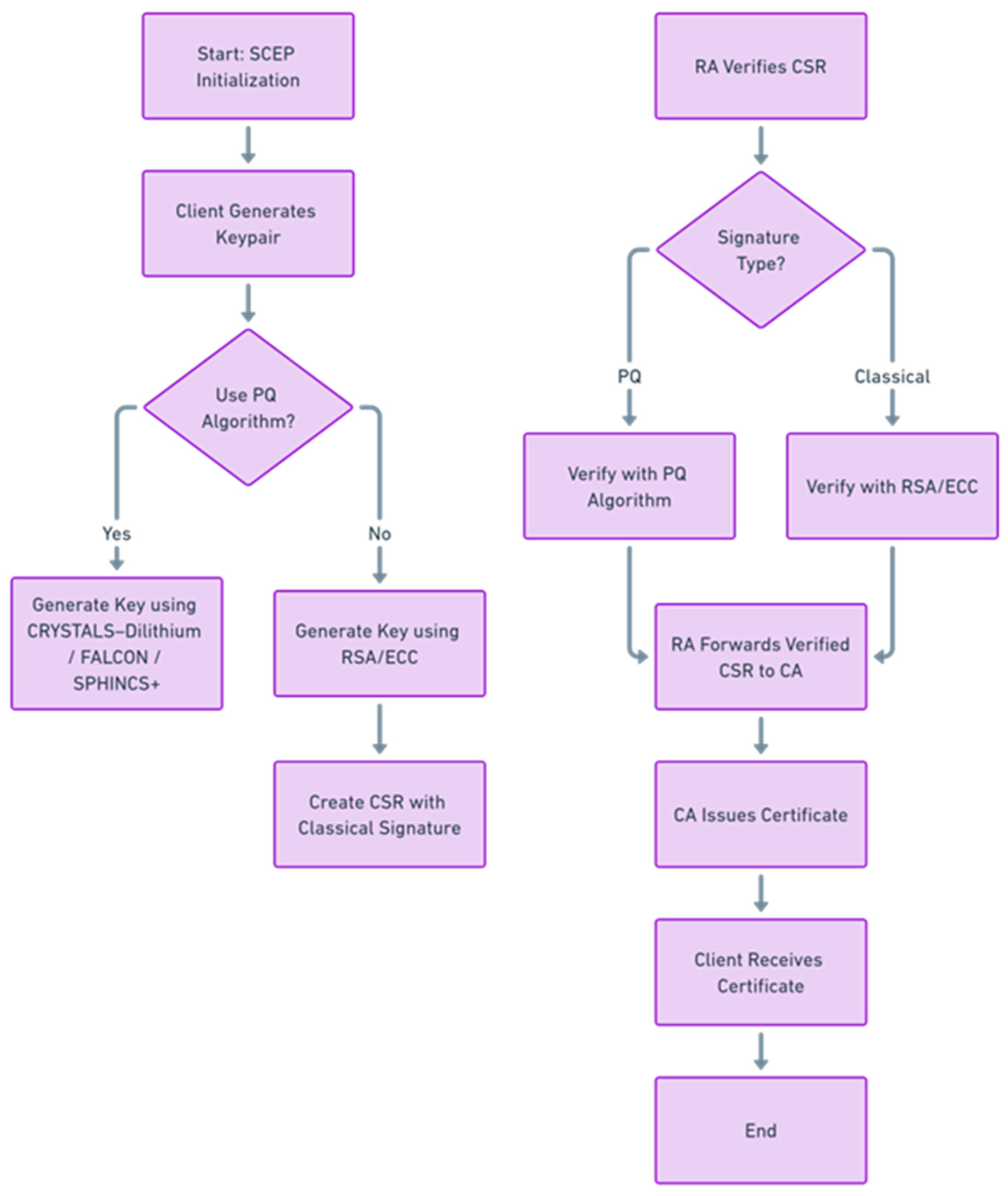
4.1.2. Incorporation of PQC Algorithms in SCEP Enrollment
- The SCEP process starts with the client generating a keypair, choosing between classical (RSA/ECC) or post-quantum (e.g., Dilithium, Falcon, SPHINCS+).
- A certificate signing request (CSR) is created using the selected algorithm and sent to the registration authority (RA).
- The RA verifies the CSR, using either classical or post-quantum signature verification based on the algorithm used.
- Once verified, the CSR is forwarded to the certificate authority (CA), which issues the certificate and returns it to the client.
4.1.3. Compatibility Considerations and Challenges
- Increased Key and Signature Sizes
- 2.
- Legacy System Interoperability
- 3.
- X.509 Certificate Format Limitations
4.2. Evaluation Criteria
- (a)
- Performance and throughput: Performance and throughput are critical aspects of evaluating how post-quantum (PQ) cryptographic algorithms perform in the context of the SCEP (Simple Certificate Enrollment Protocol). Specifically, the focus is on measuring the time required to issue various PQ certificates and understanding how different post-quantum algorithms impact the efficiency of the certificate issuance process.
- (b)
- Resource consumption: Resource consumption is a critical factor in evaluating the efficiency of the PQ-SCEP protocol, particularly in terms of the data transmission and storage requirements. This aspect focuses on quantifying the amount of data exchanged and managed during the issuance of post-quantum (PQ) certificates, including the impact on the network bandwidth and storage capacity.
4.3. Implementation Workflow
5. Experimental Results and Discussion
5.1. Performance and Throughput
5.1.1. Evaluation Results of Dilithium Algorithm Variants
5.1.2. Evaluation Results of Falcon Algorithm Variants
5.1.3. Evaluation Results of SPHINCS+ Algorithm Variants
5.2. Resource Consumption
5.2.1. Evaluation in Low-Resource and Constrained Environments
Benchmarking Setup
- ARM Cortex-M4 (e.g., STM32F4 @ 168 MHz, 256 KB RAM)
- b.
- RISC-V embedded boards
- c.
- Raspberry Pi Zero (Broadcom BCM2835 ARM11, 512 MB RAM)
Algorithm Comparison on Constrained Devices
Observations and Suitability by Device Type
- ○
- Dilithium2 performs well on 32-bit microcontrollers with moderate RAM (>64 KB) and is the most balanced in terms of size vs. speed.
- ○
- Falcon512 provides the smallest signatures but requires floating-point hardware and tight implementation controls to prevent side-channel leaks—challenging on bare-metal embedded systems.
- ○
- SPHINCS+ is highly secure and side-channel resistant but incurs high computation times and large signatures, making it less practical for ultra-low-power devices
Trade-Offs and Deployment Recommendations
Mitigation and Optimization Strategies
- ○
- Dilithium and Falcon can be compiled using lightweight variants of PQClean with reduced memory footprints.
- ○
- Hardware acceleration or external crypto co-processors may enable SPHINCS+ in otherwise unsuitable environments.
- ○
- Devices with limited flash can store private keys externally (e.g., HSM modules) and offload signings to more capable edge systems.
5.3. Expanded Performance Evaluation
5.3.1. Scalability Considerations
- -
- Transmission overhead
- -
- Certificate processing time
- -
- Storage requirements on the certification authority (CA) and client side
- -
- Throughput (certificates processed per second)
- -
- Latency in automated enrollment
- -
- Bandwidth consumption
5.3.2. Theoretical Estimates Based on the Literature
- -
- Dilithium2 can issue ~12,000 certificates per second on a modern multi-core CA server.
- -
- Falcon512 achieves higher throughput (~20,000 certs/s) but requires precise floating-point arithmetic.
- -
- SPHINCS+ is significantly slower (sub-1000 certs/s), making it less ideal for high-volume issuance.
- -
- Dilithium2 would require ≈ 84 s of continuous processing.
- -
- SPHINCS+ would require distributed CA infrastructure or long queues.
5.3.3. Network and System Load Implications
- -
- Certificate sizes (e.g., 1.7 KB for Dilithium vs. 300 B for RSA) may lead to increased traffic during bootstrapping or renewal cycles.
- -
- Memory and CPU constraints in edge devices (e.g., routers, IoT hubs) must be considered when parsing PQC certificates or verifying signatures.
- -
- Load-balancing, caching, and batch issuance techniques may help mitigate these bottlenecks in production systems.
5.3.4. Mitigation Strategies for Large-Scale Use
- -
- Parallelized CA implementations can issue thousands of certificates per second with appropriate queuing and thread pools.
- -
- Hybrid rollout models can reduce the load by issuing PQC certificates only to critical or PQC-ready systems first.
- -
- Use of compression and differential encoding may reduce the transmission size, especially for repetitive certificate metadata.
5.3.5. Future Performance Optimization Opportunities
- -
- -
- Using lightweight variants of the PQC algorithms where the NIST Level 1 suffices.
- -
- Profiling and tuning the PQC libraries on embedded and cloud-native platforms.
5.4. Security Analysis
5.4.1. Security in the Context of the SCEP
5.4.2. Resilience to Quantum Attacks
5.4.3. Side-Channel and Implementation Security
- -
- Dilithium: Resistant to side-channel attacks due to deterministic signature generation and lack of floating-point operations [28].
- -
- Falcon: Efficient but uses FFT and floating-point math, which can introduce side-channel leakage if not hardened [29].
- -
- SPHINCS+: Conservative and stateless, but incurs high signature size and slower verification [30].
5.4.4. Standardization Status and Trustworthiness
- -
- FIPS 203: CRYSTALS–Dilithium
- -
- FIPS 204 (draft): Falcon
- -
- FIPS 205 (draft): SPHINCS+
5.5. Recommendations Based on Research Findings
5.5.1. Dilithium Algorithms
- (a)
- Dilithium2
- (b)
- Dilithium3
- (c)
- Dilithium5
5.5.2. Falcon Algorithms
- (a)
- Falcon512
- (b)
- Falcon1024
5.5.3. SPHINCS+ Algorithms
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Correction Statement
Abbreviations
| PKI | Public Key Infrastructure |
| SCEP | Simple Certificate Enrollment Protocol |
| ECC | Elliptic Curve Cryptography |
| PQCA | Post-Quantum Crypto Algorithm |
References
- Rexha, B. Increasing user privacy in online transactions with, X. 509 v3 certificate private extensions and smartcards. In Proceedings of the Seventh IEEE International Conference on E-Commerce Technology (CEC’05), Munich, Germany, 19 July 2005; IEEE: Piscataway, NJ, USA, 2005; pp. 293–300. [Google Scholar]
- Diffie, W.; Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Adams, C.; Farrell, S.; Kause, T.; Monk, T. Internet X.509 Public Key Infrastructure Certificate Management Protocols. RFC 2510. Available online: https://www.rfc-editor.org/rfc/rfc2510 (accessed on 2 December 2024).
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; IEEE: Piscataway, NJ, USA, 1994; pp. 124–134. [Google Scholar]
- Bernstein, D.J.; Buchmann, J.; Dahmen, E. (Eds.) Post-Quantum Cryptography; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Mosca, M. Cybersecurity in an era with quantum computers: Will we be ready? IEEE Secur. Priv. 2015, 13, 58–62. [Google Scholar] [CrossRef]
- Chen, L.; Jordan, S.; Liu, Y.K.; Moody, D.; Peralta, R.; Perlner, R.; Smith-Tone, D. Report on Post-Quantum Cryptography. NISTIR 8105; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2016. [Google Scholar]
- Höglund, J.; Samuel, L.; Martin, F.; Shahid, R. PKI4IoT: Towards public key infrastructure for the Internet of Things. Comput. Secur. 2020, 89, 101658. [Google Scholar] [CrossRef]
- He, Z.; Martin, F.; Shahid, R. Indraj: Digital certificate enrollment for battery-powered wireless devices. In Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks, Miami, FL, USA, 15–17 May 2019; pp. 117–127. [Google Scholar]
- Rossberg, M.; Markus, T. Secure enrollment of certificates using short PINs. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August–1 September 2017; pp. 1–9. [Google Scholar]
- Woods, C. Secure interoperability with commercial open standards. In Proceedings of the 2015 IEEE International Conference on Smart Grid Communications (SmartGridComm), Miami, FL, USA, 2–5 November 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 509–514. [Google Scholar]
- Dongale, D.T.; Kamath, S.R. Reviewing Trends and Technology Shaping the Future of Public Key. Int. J. Curr. Res. 2016, 8, 28411–28420. [Google Scholar]
- Schaad, J.; Nyström. Specify Protocols for Certificate Enrollment and Management Using Cryptographic Message Syntax (CMS) in RFC 5272, 2010.
- Bos, J.W.; Costello, C.; Naehrig, M.; Stebila, D. Post-Quantum Key Exchange for the TLS Protocol from the Ring Learning with Errors Problem. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 17–21 May 2015; pp. 553–570. [Google Scholar]
- Fan, J.; Fabian, W.; Jafar, Z.; John, G.; Serge, M.; Mike, O.; Carlisle, A. Impact of post-quantum hybrid certificates on PKI, common libraries, and protocols. Int. J. Secur. Netw. 2021, 16, 200–211. [Google Scholar] [CrossRef]
- Mini, T.T. Secure Device Identifiers and Device Enrollment in Industrial Control System. In Proceedings of the 2019 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Goa, India, 16–19 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Stebila, D.; Fluhrer, S. Post-Quantum TLS. Internet-Draft Draft-Stebila-TLS-Hybrid-Design-01, 2019; This draft explores the design of TLS extensions to support post-quantum cryptographic algorithms within the PKI framework. [Google Scholar]
- Campagna, M.; Chuengsatiansup, C. Hybrid Post-Quantum Signatures for TLS Certificate Authentication. In Proceedings of the NIST 2nd PQC Standardization Conference, Santa Barbara, CA, USA, 22–25 August 2019. [Google Scholar]
- Kuhlmann, D.; Meyer, C.; Krämer, J.; Buchmann, J. Post-Quantum Certificate Enrollment in EST: Performance Analysis and Feasibility for Constrained Devices. In Proceedings of the 17th International Conference on Availability, Reliability and Security (ARES 2022), Vienna, Austria, 23–26 August 2022. [Google Scholar] [CrossRef]
- Meijer, J.; Kampanakis, P.; Dang, Q. Post-Quantum Certificate Management using ACME and Hybrid Certificates. In Proceedings of the 2022 IEEE Symposium on Security and Privacy Workshops (SPW), San Francisco, CA, USA, 23–25 May 2022; pp. 226–231. [Google Scholar]
- Peng, L.; Xie, X.; Chen, H.; Zhang, Q. A Lightweight and Adaptable PKI Framework Supporting Post-Quantum Signatures for IoT Devices. Future Gener. Comput. Syst. 2023, 143, 33–45. [Google Scholar] [CrossRef]
- Rosulek, M.; McGrew, D.; Huelsing, A. Efficient Post-Quantum Certificate-Based Authentication for Device Provisioning. ACM Trans. Embed. Comput. Syst. 2022, 21, 1–20. [Google Scholar] [CrossRef]
- Hülsing, A.; Oder, T.; Rijneveld, J.; Schwabe, P. Benchmarking Suite for Post-Quantum PKI Integration. In Cryptology Eprint Archive, Report 2021/768; European Conference: Ghent, Belgium, 2021; Available online: https://eprint.iacr.org/2021/768 (accessed on 5 January 2025).
- Alagic, G.; Alperin-Sheriff, J.; Apon, D.; Cooper, D.; Dang, Q.; Kelsey, J.; Liu, Y.-K.; Miller, C.; Moody, D.; Peralta, R. Status report on the second round of the NIST post-quantum cryptography standardization process. NIST IR 2020, 8309, 39. [Google Scholar]
- Bindel, N.; Brendel, J.; Fischlin, M.; Goncalves, B.; Stebila, D. Hybrid Key Encapsulation Mechanisms and Authenticated Key Exchange. In Proceedings of the Post-Quantum Cryptography: 10th International Conference, PQCrypto 2019, Chongqing, China, 8–10 May 2019. [Google Scholar]
- PQClean Project. Available online: https://github.com/PQClean/PQClean (accessed on 25 January 2025).
- Bürstinghaus-Steinbach, K.; Krauß, C.; Niederhagen, R.; Schneider, M. Post-Quantum TLS on Embedded Systems: Integrating and Evaluating Kyber and SPHINCS+ with mbed TLS. In Proceedings of the 15th ACM Asia Conference on Computer and Communications Security (ASIA CCS’ 20), Taipei, Taiwan, 5–9 October 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 841–852. [Google Scholar] [CrossRef]
- Hülsing, A.; Hvass, B.S.; Hansen, L.L.; Winterhalter, T.; Hritcu, C.; Spitters, B. NIST PQC Finalist Algorithms: Performance Benchmarks and Scaling Scenarios. IACR Cryptology ePrint Archive. 2023. Available online: https://eprint.iacr.org/2023/185 (accessed on 4 January 2025).
- Oder, T. Efficient Implementation of Dilithium on RISC-V and ARM Cortex-M. PQCrypto 2020. [Google Scholar]
- Open Quantum Safe liboqs. Available online: https://github.com/open-quantum-safe/liboqs (accessed on 10 March 2025).
- Beullens, W.; D’Anvers, J.P.; Hülsing, A.T.; Lange, T.; Panny, L.; de Saint Guilhem, C.; Smart, N.P. Post-Quantum Cryptography: Current State and Quantum Mitigation; ENISA: Athens, Greece, 2021. [Google Scholar]
- Fouque, P.A.; Hoffstein, J.; Kirchner, P.; Lyubashevsky, V.; Pornin, T.; Prest, T.; Ricosset, T.; Seiler, G.; Whyte, W.; Zhang, Z. Falcon: Fast-Fourier Lattice-Based Compact Signatures over NTRU. PQCrypto 2018, 36, 1–75. [Google Scholar]
- Hülsing, A. SPHINCS+—Submission to the NIST PQC Project, Version 3.1. NIST PQC Round 3. 2023.
- NIST. FIPS203—Module Lattice-Based Signature Scheme, CRYSTALS-Dilithium; Department of Commerce: Washington, DC, USA, 2024. [Google Scholar] [CrossRef]
- NIST PQC Finalists. Available online: https://csrc.nist.gov/Projects/post-quantum-cryptography (accessed on 1 March 2025).
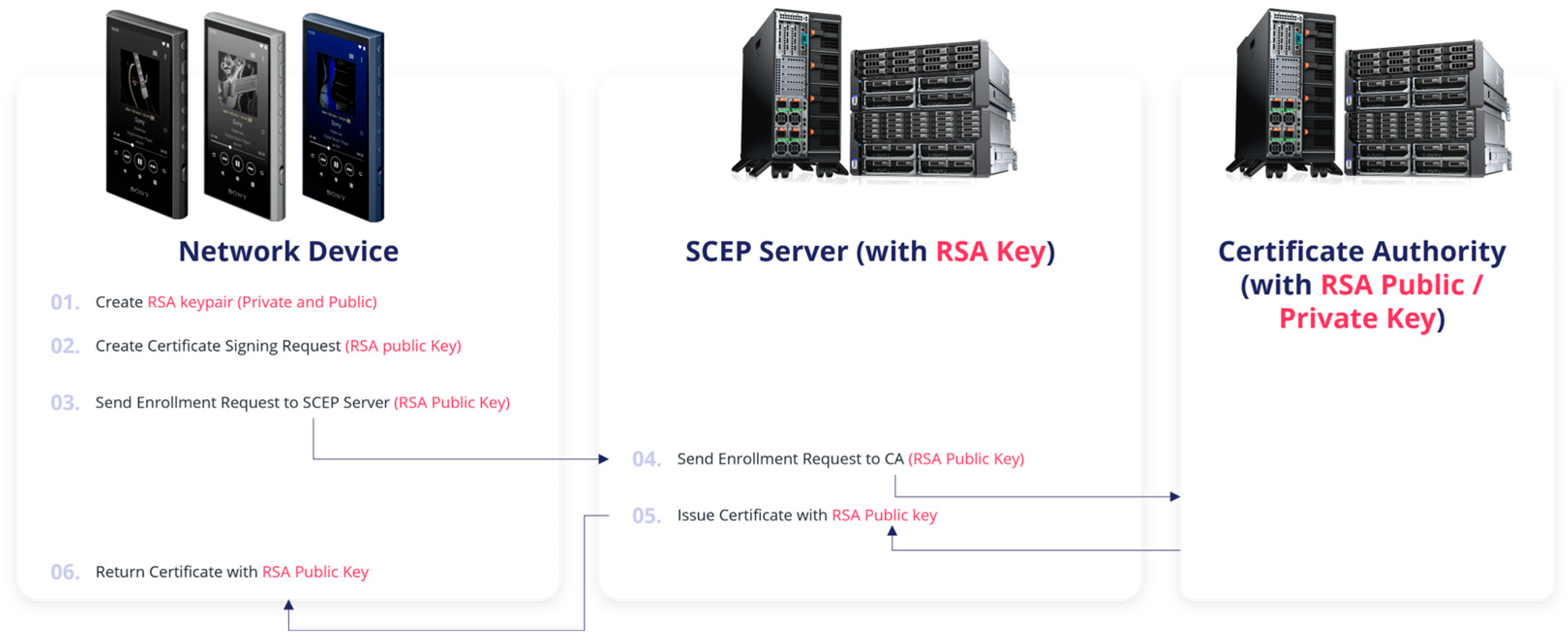
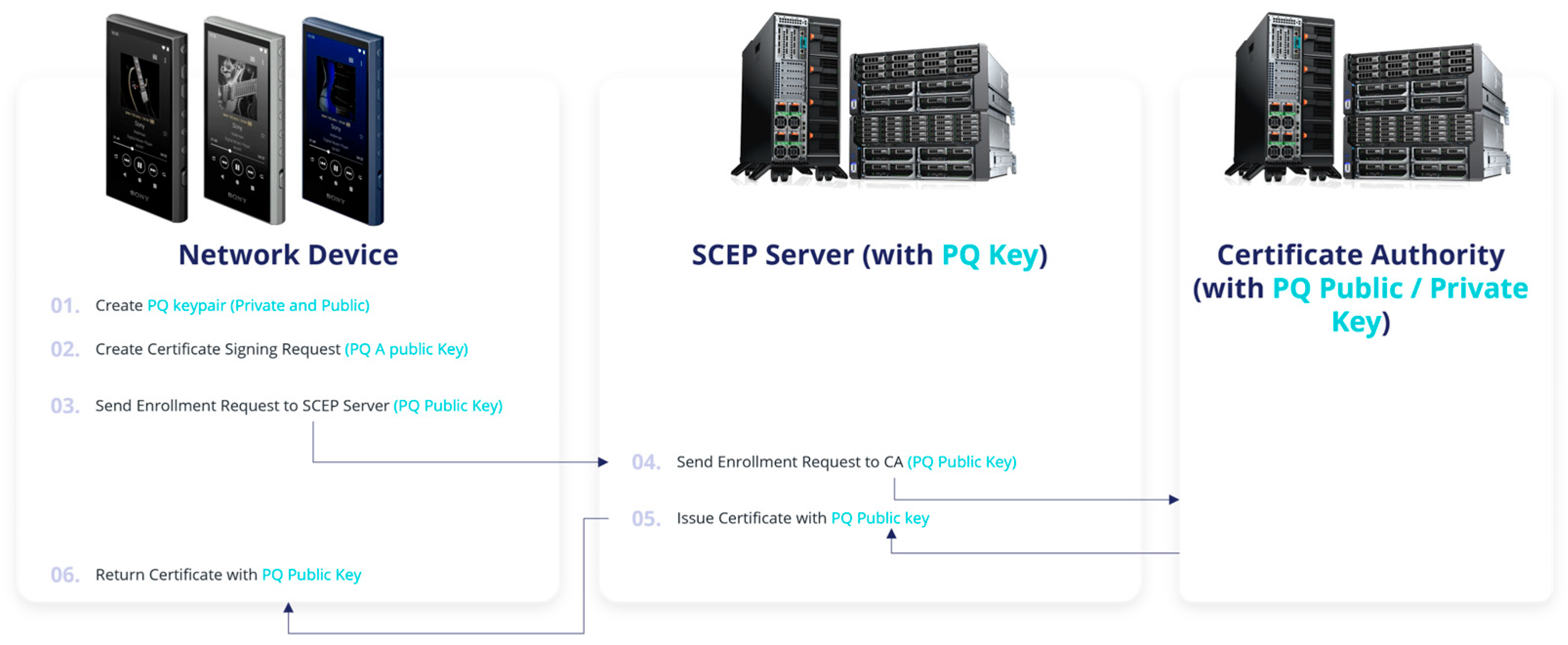


| Feature/Protocol | SCEP | EST | ACME |
|---|---|---|---|
| Protocol Architecture | HTTP-based PKI enrollment using PKCS#7/PKCS#10 | HTTPS-based enrollment with RESTful API | HTTP-based client–server architecture with DNS/HTTP-01 challenges |
| Primary Use Cases | Network devices (routers, firewalls, switches) | Enterprise and IoT device provisioning | Web servers, automated TLS certificate issuance |
| Security Features | Basic (challenge password, manual revocation) | Strong (TLS mutual auth, certificate revocation via CRLs/OCSP) | Automated domain validation, certificate transparency |
| PQC Adaptability | Requires extension for PQC support (this work) | More flexible; can be extended for PQ-hybrid or PQ-only certificates | Currently classical, some research into PQ extension underway |
| Backward Compatibility | High—suitable for legacy systems | Moderate—designed for modern environments | Low—mainly for cloud-native and web infrastructure |
| Resource Requirements | Low | Moderate | High (requires external DNS/HTTP infrastructure) |
| Dilithium Variant | Time to Sign 1000x Certificates (Seconds) | |||
|---|---|---|---|---|
| Iteration 1 | Iteration 2 | Iteration 3 | Average | |
| 1.79 | 1.85 | 2.21 | 1.95 |
| 1.85 | 2.11 | 2.27 | 2.08 |
| 1.94 | 2.29 | 2.34 | 2.19 |
| Falcon Variant | Time to Sign 1000x Certificates (Seconds) | |||
|---|---|---|---|---|
| Iteration 1 | Iteration 2 | Iteration 3 | Average | |
| 1.83 | 2.11 | 2.22 | 2.05 |
| 2.08 | 2.37 | 2.49 | 2.31 |
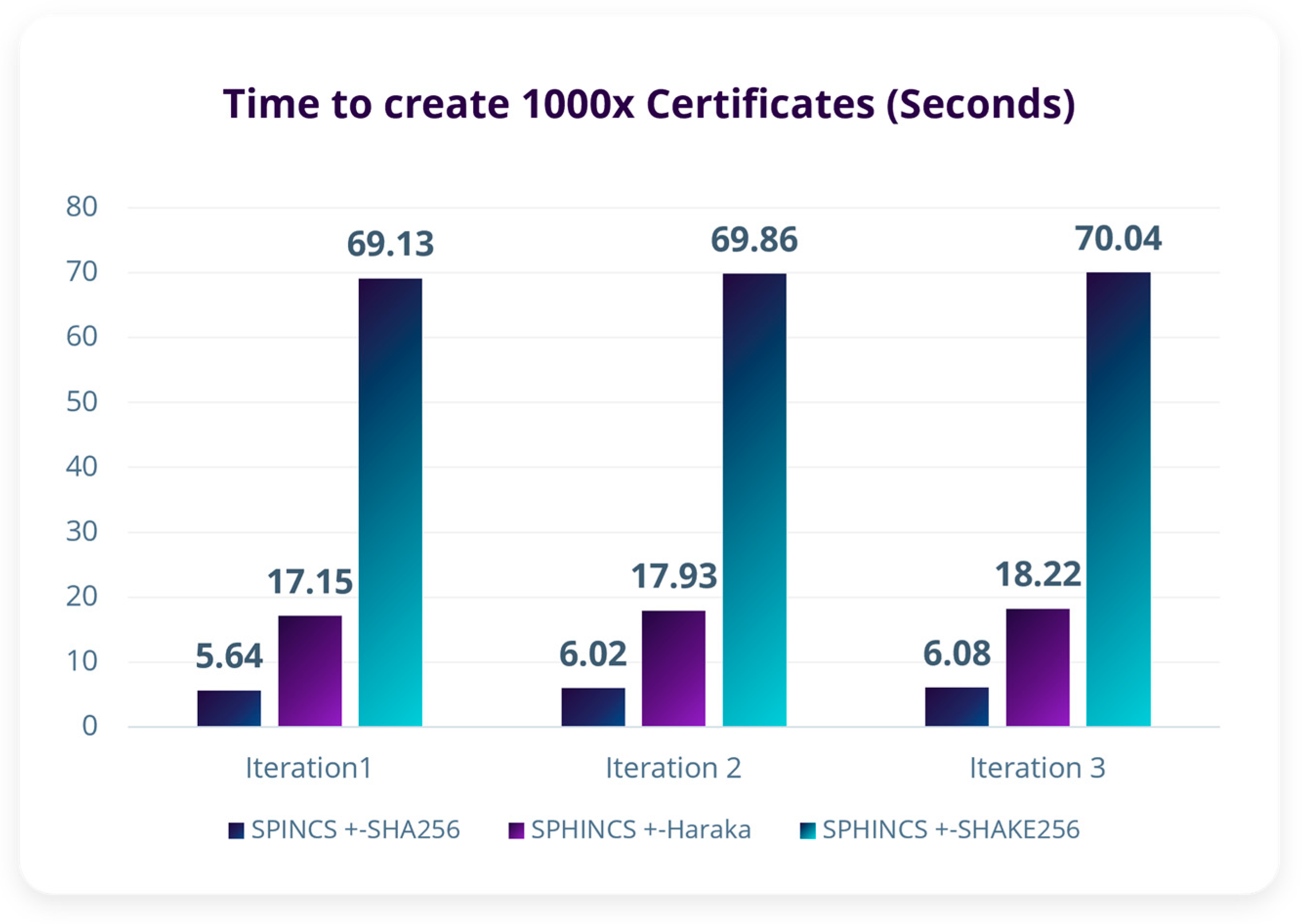
| SPHINCS+ Variant | Time to Sign 1000x Certificates (Seconds) | |||
|---|---|---|---|---|
| Iteration 1 | Iteration 2 | Iteration 3 | Average | |
| 5.64 | 6.02 | 6.08 | 5.91 |
| 17.15 | 17.93 | 18.22 | 17.77 |
| 69.13 | 69.86 | 70.04 | 69.68 |
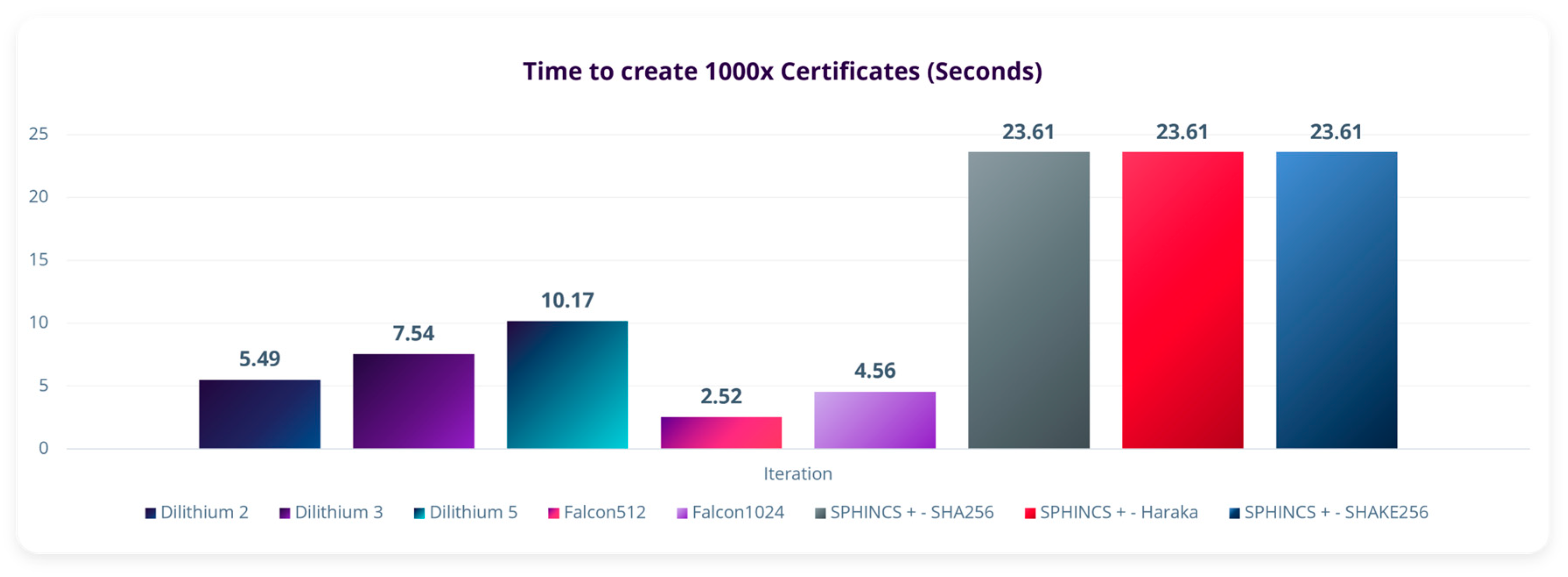
| Sr. | Algorithm | Size of Certificate (KBytes) |
|---|---|---|
| 1. | Dilithium2 | 5.49 |
| 2. | Dilithium3 | 7.54 |
| 3. | Dilithium5 | 10.17 |
| 4. | Falcon512 | 2.52 |
| 5. | Falcon1024 | 4.56 |
| 6. | SPHINCS+-SHA256-128f-robust | 23.61 |
| 7. | SPHINCS+-Haraka-128f-robust | 23.61 |
| 8. | SPHINCS+-SHAKE256-128f-robust | 23.61 |
| Algorithm | Code Size (KB) | Signature Size (Bytes) | Sign Time (ms) | Verify Time (ms) | Notes |
|---|---|---|---|---|---|
| Dilithium2 | ~20–30 KB | ~2420 | ~10–12 ms | ~3–5 ms | Efficient, suitable for constrained 32-bit systems |
| Falcon-512 | ~25–40 KB | ~666 | ~20–40 ms | ~5–10 ms | Very compact sigs, but uses FFTs and floats (harder to implement securely) |
| SPHINCS+-128s | ~40–70 KB | ~8080 | ~100–300 ms | ~4–8 ms | Conservative and robust, but slower and storage-heavy |
| Device Type | Recommended Algorithm | Reasoning |
|---|---|---|
| IoT Sensor (Cortex-M4) | Dilithium2 | Good balance of RAM, speed, and signature size |
| Router (ARMv7/ARM64) | Falcon512 or Dilithium2 | Falcon if FPU available; otherwise Dilithium |
| Edge Gateway (Raspberry Pi) | Any, including SPHINCS+ | Sufficient resources for even heavyweight schemes |
| Algorithm | Type | NIST Security Level | Notable Features |
|---|---|---|---|
| CRYSTALS-Dilithium | Lattice-based | Level 2, 3, 5 | Strong side-channel resistance, efficient [28] |
| Falcon | Lattice-based | Level 1, 5 | Compact signatures, vulnerable to side-channel unless carefully implemented [29] |
| SPHINCS+ | Hash-based | Level 1, 3, 5 | Stateless, robust, conservative design [34] |
| Threat | Classical SCEP | PQC-Enhanced SCEP |
|---|---|---|
| Quantum key compromise | Vulnerable | Resistant |
| Forged CSRs | Feasible with quantum computers | Infeasible with current knowledge |
| Side-channel risks | Moderate (RSA/ECC) | Mitigated via PQ-safe libraries |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Dabbagh, R.; Alkhatib, M.; Albalawi, T. Efficient Post-Quantum Cryptography Algorithms for Auto-Enrollment in Public Key Infrastructure. Electronics 2025, 14, 1980. https://doi.org/10.3390/electronics14101980
Al-Dabbagh R, Alkhatib M, Albalawi T. Efficient Post-Quantum Cryptography Algorithms for Auto-Enrollment in Public Key Infrastructure. Electronics. 2025; 14(10):1980. https://doi.org/10.3390/electronics14101980
Chicago/Turabian StyleAl-Dabbagh, Rehab, Mohammad Alkhatib, and Tahani Albalawi. 2025. "Efficient Post-Quantum Cryptography Algorithms for Auto-Enrollment in Public Key Infrastructure" Electronics 14, no. 10: 1980. https://doi.org/10.3390/electronics14101980
APA StyleAl-Dabbagh, R., Alkhatib, M., & Albalawi, T. (2025). Efficient Post-Quantum Cryptography Algorithms for Auto-Enrollment in Public Key Infrastructure. Electronics, 14(10), 1980. https://doi.org/10.3390/electronics14101980







