Abstract
In response to the Cybersecurity Law, organizations face numerous management and technical requirements. Detection techniques such as vulnerability scanning and penetration testing are employed to identify risks. Addressing these vulnerabilities demands substantial manpower, time, and financial resources. Security concerns also arise during digital file transmission and remediation efforts. This study proposes a security detection platform with step-by-step implementation guidelines, enabling resource-limited units to replicate the setup and address security gaps. It compares detection results between open-source and commercial tools, highlighting key differences and offering remediation strategies. Numerous digital files (e.g., test reports) are generated during testing. To ensure secure storage and sharing, the system integrates IOTA’s distributed ledger and IPFS, generating HASH values and uploading files on-chain to preserve integrity and authenticity. The objective is to deliver a scalable, cost-effective security detection framework that enhances system resilience while minimizing resource consumption.
1. Introduction
Under the Cybersecurity Law, all agencies categorized as Class C are mandated to undergo information security inspections every two years [1]. These inspections are conducted at a technical level to ensure that the organizations’ information and communication systems are not vulnerable to exploitation. Units involved in government-funded projects are required to prioritize the remediation of medium- and high-risk vulnerabilities [2]. Due to the large number of agencies subject to testing and the variation in technical and human resources across units, each round of inspection represents a significant operational undertaking.
Automated vulnerability scanning tools are commonly employed to identify known security flaws by matching them against a defined set of signatures or rule databases [3]. However, the effectiveness of detection varies depending on the tool brand, scanning ruleset, and system configuration [4]. While these tools efficiently handle large-scale scanning tasks, the post-detection remediation phase remains a challenge. Reports typically include vulnerability types and severity levels, but the recommendations are often minimal or generic. Conducting in-depth analysis and proposing tailored remediation strategies empowers internal teams to enhance their security posture, contributing to long-term operational resilience.
From a budgetary perspective, organizations typically allocate cybersecurity investments toward antivirus software, firewalls, and workforce training [5,6]. With increasing risks from third-party dependencies, vulnerability scanning of the software supply chain has become critical [7,8]. While functionality and performance were historically prioritized over security, regular technical scans are now essential for proactive risk management. Early identification and patching of vulnerabilities can reduce both exposure and remediation costs.
Security audit reports often require secure transmission and storage. Common practices such as password-encrypted files and access-controlled links via cloud platforms like Google Drive remain vulnerable to interception or access mismanagement. Audit procedures frequently require submission of original logs and artifacts, necessitating repeated confirmation, cross-verification, and documentation—processes that are time-consuming and resource-intensive.
In response, this study proposes integrating blockchain technology—specifically IOTA—and IPFS to enhance audit efficiency, integrity, and security [9,10,11]. The immutability, decentralization, and cryptographic protections provided by blockchain support secure file sharing and traceable vulnerability reports.
The literature emphasizes the operational challenges public agencies face in meeting inspection requirements, particularly for Class C organizations. The proposed IOTA–IPFS framework addresses these by improving the integrity, traceability, and security of reporting workflows. Unlike traditional centralized systems reliant on vulnerable cloud platforms and manual coordination, this decentralized model provides tamper-proof logs and cryptographically verifiable data transmission. By using cost-effective, open-source tools and decentralized storage, the framework supports operational resilience. Compared to Ethereum, which incurs gas fees and latency due to its reliance on smart contracts, IOTA’s feeless DAG architecture is better suited for high-frequency auditing. Hyperledger Fabric, while offering secure traceability in permissioned environments, demands complex deployment and governance, making it less ideal for resource-limited agencies. The IOTA–IPFS model, in contrast, remains lightweight and accessible, reducing risks of data manipulation and operational bottlenecks, and offering a secure, scalable solution for regulatory compliance.
This study draws from past testing experience and statistical records to offer practical insights and tool selection guidance. A key contribution lies in enabling resource-constrained units to select affordable tools, triage vulnerabilities, and implement remediation workflows. By developing a comprehensive detection framework, the study aims to improve compliance and technical capacity while reducing overhead.
Additionally, the research compares commercial and open-source security tools to evaluate the viability of self-managed solutions under budgetary constraints [12,13]. Timely detection and response are emphasized as crucial risk mitigation strategies.
Further, the study highlights the encryption and decentralized storage of reports via IPFS. Storing assets in tamper-resistant formats preserves critical data and enables secure sharing. This approach improves pre-test data collection, mid-test analysis, and post-test archiving, ensuring the continuity and integrity of vulnerability communication workflows [14,15].
The integration of decentralized technologies such as IOTA and IPFS into vulnerability tracking offers a novel yet practical solution that both coordinates with and diverges from platforms like Ethereum and Hyperledger, as well as conventional systems. Compared to Ethereum’s fee-based model and Hyperledger’s enterprise complexity, the IOTA–IPFS approach provides a lightweight, cost-effective framework accessible to public-sector institutions. Its cryptographic immutability and decentralized storage enhance audit integrity, reduce access risks, and ensure secure, scalable compliance with cybersecurity mandates.
Research Objectives
This study is structured around four primary objectives: (1) to compare the effectiveness of commercial and open-source vulnerability detection tools and analyze their output to support evaluation and adoption in resource-limited environments; (2) to conduct security testing, rank risks, and provide actionable remediation suggestions to accelerate patching and strengthen self-assessment; (3) to store testing reports in IPFS and integrate with IOTA for secure, traceable documentation; (4) to ensure data integrity by uploading detection and remediation outcomes to the blockchain, forming a verifiable audit trail.
2. Testing of Information Security
2.1. Testing
In 2019, the Cybersecurity Law stipulated that vulnerability scans and penetration tests must be conducted every two years in security testing projects. In order to maintain an organization’s information security, security checks and vulnerability scans must be performed regularly. These are the main reasons:
(1) Perform risk assessments: regular testing helps identify and respond immediately to new threats and vulnerabilities.
(2) Prevent potential threats: by scanning for vulnerabilities regularly, organizations can identify and fix potential security holes and prevent hackers from exploiting weaknesses.
(3) Compliance with regulations and standards: organizations are required to conduct regular vulnerability scans and tests to ensure compliance with information security management standards.
(4) Protect corporate image: avoiding potential attacks, reducing the risk of security incidents, and protecting the corporate brand can be achieved by proactively detecting and patching vulnerabilities.
(5) Reduce losses: detecting vulnerabilities early and repairing them can prevent data leakage, service interruptions, and business interruptions.
In order to maintain customer trust, it is important to protect customer information. Data security can be ensured through regular testing.
Security testing evaluates networks, applications, and computers for known vulnerabilities, which may come from programming errors or configuration errors in routers, firewalls, application servers, and web servers. It may be necessary to change network security policies, install patches, educate users about security, and reconfigure software to address vulnerabilities [16]. Black box, white box, and penetration testing are usually conducted based on the tester’s understanding of the system architecture and the needs of the tested unit. There are different requirements for different testing methods under the Cybersecurity Law.
In black box testing, the attacker’s position is simulated without internal information in order to identify system loopholes and weaknesses. Often, tools are used to perform a quick assessment and make recommendations for remediation. A white box test is a source code test. For the tester to use tools for testing, both parties must sign a confidentiality agreement and provide the complete program code. This provides developers with detailed reports upon detection of in-depth system vulnerabilities. A penetration test simulates real-world attacks, attempting to enter a system and gain unauthorized access to test whether vulnerabilities can be exploited. Testing and backups are essential for minimizing losses.
There are advantages and disadvantages to each of these security detection methods. In order to ensure the security of their systems, organizations can choose and combine them according to their own needs and resources. Security testing includes black box, white box, and penetration testing, with a brief introduction to common tools, practices, benefits, and costs (Table 1).

Table 1.
Security testing includes black box, white box, and penetration testing.
The next step is to explain the information security testing process (see Figure 1). It consists of five stages: demand investigation, vulnerability detection, result analysis, execution retesting, and completion of detection.
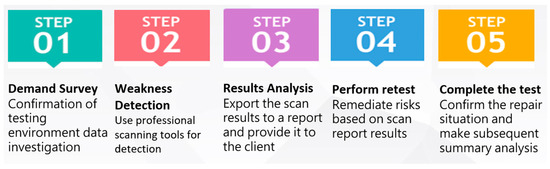
Figure 1.
Information security testing process.
Phase 1: Through effective communication, determine the scope, purpose, and special requirements of testing with stakeholders based on an understanding of organizational needs and goals. Establish a solid foundation for the next steps by ensuring that the test meets all organizational expectations.
Phase 2: Automated or manual methods are used to detect system vulnerabilities, such as network vulnerabilities, program vulnerabilities, program code loopholes, etc. Identifying potential risks is crucial to optimizing security.
Phase 3: Analyze the detection results carefully to assess vulnerabilities and risks. Identify the most dangerous vulnerabilities in the system and develop a strategy for resolving them.
Phase 4: Ensure that previous vulnerabilities are successfully patched, and that the overall security of the system is significantly enhanced by retesting.
Phase 5: To complete the testing process, confirm patch status. Create a final test report, including detailed results, vulnerability patch status, recommended security improvements, and future strategy recommendations.
Security vulnerabilities are frequently addressed during the development or upgrading of information systems. However, as information technology continues to evolve, IT professionals are increasingly challenged by the growing complexity and frequency of these issues. To enhance efficiency in managing such risks, it is essential to leverage appropriate information security detection tools. While these tools play a critical role in identifying potential threats, it is important to acknowledge that each tool has inherent limitations in terms of its detection scope and coverage [17]. Therefore, complex Web applications should be run. A security analysis should be automated as much as possible using static, dynamic, and interactive analysis tools, as well as manual inspection to reduce false positives and find more true positives.
Security threats continue to pose a significant challenge to organizations as new vulnerabilities and attacks emerge. Vulnerabilities are introduced during the development process and are often recurrences. A new security vulnerability will be published to the CVE vulnerability database in order to identify and describe these security vulnerabilities so that these security professionals can share information security vulnerabilities. To detect the basis and description of the vulnerability, the detection tools will also be linked to this source [18].
Detection and analysis tools can differ in their vulnerability definitions and classifications, vulnerability scanning technologies or source vulnerability libraries, vulnerability reporting policies, etc. For the same software code, these differences may result in different vulnerability reports [19]. Consequently, sometimes in addition to cross-using different tools for detection, manual testing by development engineers themselves or penetration testing by penetration testing professionals is also required to determine whether the vulnerability can be exploited and if patching or prevention are actually required.
In order to maintain an organization’s information security foundation, regular information security testing and vulnerability scanning are essential. As a result, they help organizations respond to changes in the threat environment, discover vulnerabilities in advance, comply with regulations, protect the corporate image, reduce losses, and ensure customer trust. Five steps are essential to implementation: demand investigation, weakness detection, result analysis, execution retesting, and confirmation report. This study examines how to reduce the cost of detection investment or shorten the time to patch vulnerabilities, regardless of the cost of detection or patching after the vulnerability is discovered.
2.2. Blockchain
Satoshi Nakamoto first proposed the concept of “blockchain” in 2008. Encrypted hashes are generated using cryptography as its main principle. Each block contains the HASH value of the previous block. As a result of this setting, the blockchain is difficult to manipulate. It requires more than 51% of the computing power of the block nodes to change its content. Data chains are established and stored using this consensus mechanism technology.
Based on their chain structure, blockchain systems can be classified into three categories: standard blockchains, hybrid blockchains, and directed acyclic graphs (DAGs). Blockchain systems, including Bitcoin and Ethereum, store all submitted transactions in a blockchain, adding new blocks to the chain as they are submitted. Nodes can participate in a standard blockchain network and maintain a complete copy of the chain. A hybrid blockchain architecture (such as Hyperledger Fabric) maintains multiple chains in order to protect privacy. Data can only be accessed by nodes in a specific chain, and different chains can exchange information and issue cross-chain transactions. IOTA is a DAG-based blockchain system that differs from standard blockchains and hybrid blockchains [20]. IOTA is a distributed ledger technology (DLT) specifically designed for the Internet of Things (IoT) ecosystem. Unlike traditional blockchains, IOTA does not use a chain of blocks. Instead, it is based on a structure known as the Directed Acyclic Graph (DAG), which IOTA refers to as the Tangle. In IOTA, each new transaction must validate two previous transactions, forming a web-like graph structure rather than a linear sequence.
Data storage and sharing are safer and more efficient when blockchain technology and IPFS are combined. IPFS is a decentralized file storage and sharing protocol that ensures the reliability and availability of files by distributing them across multiple nodes. The combination of blockchain and IPFS can enable secure storage and efficient sharing of sensitive medical information, while solving problems such as single point failures and data tampering [21]. Combining the above can also improve the efficiency of searching for electronic resources and provide better services to medical institutions and patients.
Therefore, blockchain technology can be used to improve digital file storage and sharing. A method of ensuring archives are secure, private, and not easily altered is by combining IPFS and blockchain. A smart contract can also automate processing on electronic resource sharing platforms and improve system efficiency. Overall, these studies demonstrate the potential benefits of blockchain technology for resource sharing, providing more secure, transparent, and efficient solutions.
2.3. IPFS Interstellar Archive System
In a hypermedia distribution network, IPFS enables content-addressable peer-to-peer storage, sharing, and persistence of files (Figure 2). Like Bitcoin, it allows you to store unchangeable data and eliminate redundant files. To facilitate file access, search the network for node addresses.

Figure 2.
Schematic diagram of the upload process of the IPFS Interstellar Archive System.
Data growth in the blockchain causes excessive storage pressure on the chain due to accelerated data growth. As part of the decentralized archive storage system, the IPFS interstellar archive can connect all nodes to a unified storage system, easing the storage pressure on the blockchain itself. Additionally, IPFS solves the problem of data redundancy on the Internet. To achieve efficient storage, the content owner stores the corresponding hash value on the blockchain in the private IPFS network [22].
IPFS saves data regardless of its size, generating a unique hash value. The parties can save this hash value and use it to retrieve the data in the future. The IPFS network divides data into many small blocks, each with its own unique hash value for identifying it. The blocks are then distributed to the peers closest to the peer’s ID on the network.
The digital file will be encrypted and uploaded to IPFS, and the recipient will need the decryption key to open the resource.
File storage using IPFS and blockchain solves the problems of huge data and blockchain storage while enhancing file sharing security. Our files can be stored and shared more easily and efficiently using IPFS’s decentralized storage and global node network. Taking advantage of this combination opens up new possibilities for managing and utilizing digital resources.
2.4. IOTA
In 2018, IOTA was launched as an open-source decentralized ledger technology. Based on a directed acyclic graph (DAG), each block contains multiple transactions [23].
A peer-to-peer network runs IOTA’s open-source decentralized ledger technology. A directed acyclic graph (DAG) approach is used to store each transaction, and the technology was officially launched in 2018. With IOTA, everyone’s devices can make small payments and exchange data for free without incurring any additional costs in the era of the Internet of Everything. Tangle is IOTA’s DAG structure. As shown in Figure 3, Tangle is a network ledger architecture. There is no requirement to specify which block the additional transactions should be included in, and multiple forks are allowed. The ledger is updated by randomly selecting two transactions for verification. Transactions can be generated synchronously, which is much faster and more scalable than traditional blockchains [24].
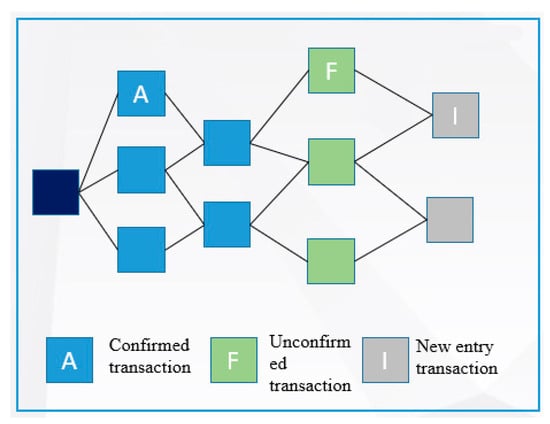
Figure 3.
IOTA Tangle architecture diagram.
IOTA technology has the following characteristics:
Highly scalable: as the number of transactions increases, more transactions will be available for approval, so the approval rate increases.
Zero-fee transactions: there are no miners in IOTA, so there are no transaction fees.
Secure data transmission: data stored and transmitted using IOTA are encoded or referenced, and are protected.
Low resource requirements: IOTA is designed primarily for IoT devices with limited resources
2.5. Proposed Architecture: Secure Vulnerability Reporting Framework with IOTA and IPFS
Architectural Innovation Overview
The proposed system introduces a lightweight, tamper-resistant, and decentralized digital reporting architecture by integrating: (1) IPFS (InterPlanetary File System): for decentralized and content-addressed storage of vulnerability reports and supporting evidence; and (2) IOTA Tangle (DAG-based blockchain): for immutable logging of digital file hash values, metadata (e.g., scan time, system ID, severity distribution), and access control records without incurring transaction fees.
Unlike traditional centralized security audit storage systems (e.g., Google Drive with password-protected.zip files), this design ensures: (1) immutable logging of scan results; (2) decentralized data redundancy; (3) cryptographic linkage between vulnerability data and remediation trails; and (4) zero-cost micro-recording with IOTA’s feeless model.
In this Table 2, we propose a novel architecture that combines IPFS for decentralized file storage and IOTA for immutable, feeless blockchain logging. This dual-layer approach addresses key limitations in traditional security report management systems.

Table 2.
Key design innovations.
Implementation Notes: (1) IPFS Integration: Python (version 3.13.3) script uploads files via ipfshttpclient, stores the resulting CID. (2) IOTA Integration: the CID, timestamp, hash (SHA-256), and severity summary are encoded into a JSON payload and anchored using the IOTA Python SDK; (3) verification protocol: a validator module checks hash integrity and confirms data timestamp alignment to prevent backdated tampering; and (4) web interface (optional extension): a React-based dashboard retrieves and verifies report history and integrity in real time, using the IOTA Explorer API and IPFS gateway.
To highlight the advantages of the proposed IPFS + IOTA framework, we compare it against traditional file sharing mechanisms commonly used in information security report management (Table 3).

Table 3.
Comparison with traditional workflow.
Security Evaluation: (1) tamper resistance: hash verification + immutable DAG ensure data has not been altered post-upload; (2) replay prevention: timestamp + hash make replay attacks infeasible; and (3) confidentiality (optional): files can be AES-encrypted before IPFS upload; encryption key is shared out-of-band or anchored via IOTA’s Masked Authenticated Messaging (MAM) protocol.
3. Research Methods and Procedures
This study adopts a design science research methodology (DSRM) to develop, implement, and evaluate a secure and efficient information security detection and reporting framework. The research is structured in four phases: (1) environment and requirement analysis, (2) tool selection and implementation, (3) vulnerability testing and blockchain integration, and (4) comparative evaluation and analysis. Both qualitative observations and quantitative metrics are employed to assess the outcomes.
3.1. Research Methods
There are four main stages in this study (Figure 4). The first step is to solve the problem of insufficient detection resources in various units, and to develop free and open-source software to detect weak scans. Different units are provided with the platform construction process teaching so that they can build accordingly. A second step entails analyzing and comparing the actual detection results of commercial and open-source weak scan software tools. The third step is to integrate and analyze the actual detection report results to determine how to further repair the risks and weaknesses. Each unit can also use the integrated recommended repair method to determine if the system has relevant risks, as well as speed up the process of patching vulnerabilities once the detection report is received by the tested unit. After detection, the files are encrypted and uploaded to IPFS to get a shared link and HASH value to solve the problem of retaining them. To ensure that the relevant digital files cannot be tampered with and their integrity can be verified, blockchain technology is used to upload the uploaded data and HASH value to the IOTA public chain. This series of steps is intended to achieve the security and reliability of digital files related to information security detection.
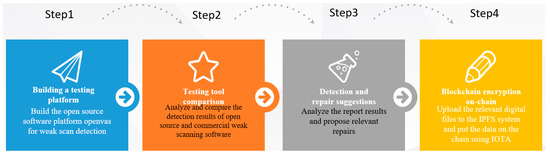
Figure 4.
Research framework.
3.2. Establish a Testing Platform
The purpose of this study is to develop an open-source host vulnerability scan detection tool called OpenVAS (Figure 5), which is mainly maintained by the Greenbone Organization. Weak scan detection tools are used to help host system administrators identify possible vulnerabilities and risks in their systems and provide relevant reports after the detection is complete. Furthermore, the report content will explain which vulnerabilities have been discovered, their sources, and recommendations for patching, so that administrators can patch the vulnerabilities according to the recommended methods to prevent attacks. This software will also regularly update vulnerability CVEs from common vulnerability database sources such as NVT, SCAP, CERT, etc., to ensure that it can detect newly discovered vulnerabilities.
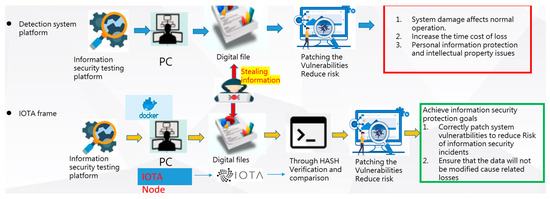
Figure 5.
Blockchain system functional architecture.
The OpenVAS open-source weak scanning tool is recommended to be installed on the Kali Linux system platform, since there have been no reported problems with installation on this platform. Kali Linux also includes about 600 penetration testing tools that can be used and built on a virtual machine environment for testing. Table 4 shows the environmental system specification requirements. Specifications can be further adjusted and configured based on the performance requirements and resources of the unit.

Table 4.
Host server specifications.
The following are the steps for installation:
- Create a virtual machine using VirtualBox (version 7.1.8) and install Kali Linux.
- As soon as Kali is installed, the first step is to update the system. To ensure that all OpenVAS packages have the latest version, the Kali system will release tool version updates from time to time:
- Once the system update is complete, install OpenVAS. Here are the instructions for installation:
The command is as follows: sudo apt install gvm-y
- 4.
- Set up OpenVAS. The admin account and password will appear after the execution is complete. It should be saved. When you log in later, it will be used as your username. Passwords are long strings.
- 5.
- Run the check command to confirm that there are no problems with the installation. The message “It seems like your GVM-XXX installation is OK.” means that the installation was successful.
- 6.
- Update the vulnerability database manually, the update will take some time to complete.
- 7.
- Enable GVM service.
3.3. Blockchain System Functional Architecture
By replacing the original operation mode with a functional architecture (Figure 5), we can add the concept of blockchain to the digital files created by the information security detection platform. Based on the results of weak scanning, relevant digital files are produced based on the information provided by the tested unit for the information security detection system platform. Essentially, they are used to fix system vulnerabilities on the tested unit, reducing the risk of system attacks and avoiding possible system damage that can affect normal operations or increase the cost of time loss, as well as the risk of leaking personal information or intellectual property confidentiality. In the event that the digital files produced by the test are stolen by hackers, serious risks will occur. The files should be uploaded to IPFS after joining the IOTA node. By generating a HASH, you can further verify the integrity of the digital files and the issue of tampering. Therefore, relative security and reliability can be achieved, so that the recommended patches for system vulnerabilities are not used by those with ulterior motives and that the data files are not tampered with, reducing unnecessary losses and ensuring the unit’s sustainability.
3.4. Blockchain and IPFS Integration
Following vulnerability analysis, security reports and system snapshots were stored using a hybrid decentralized architecture:
IPFS (InterPlanetary File System) was used to store raw vulnerability scan reports.
IOTA (Tangle-based DLT) was implemented to record the hash values of IPFS files and associated metadata (timestamp, source, and severity summary) on-chain.
This ensures immutability, traceability, and integrity of audit data. The integration was built using Python (version 3.13.3) (IPFS API) and the IOTA Python SDK.
4. Experimental Results and Discussion
4.1. Is Rapid7, a Paid Detection Tool, or OpenVAS, an Open-Source Free Detection Tool, More Accurate?
Rapid7, a paid detection tool, and OpenVAS, a free detection tool, each have their own advantages and limitations. If a vulnerability can be exploited, regardless of how serious it is, it has attack value from a hacker’s perspective. The accuracy of vulnerability scanning varies among the many detection tools available on the market. It remains to be seen whether the vulnerability can be exploited successfully. It is more important to focus on the importance of the vulnerability rather than how the detection results are handled. One of the keys to preventing potential attackers from exploiting the vulnerability is quick patching. Security consists of managing detected vulnerabilities effectively, reducing the risk of attacks, protecting confidential information, and maintaining system availability.
4.1.1. A Comparative Analysis of Rapid7 and OpenVAS, Two Paid Detection Tools
As shown in Table 5, we have sorted out and explained many important concerns, including safety research and costs:

Table 5.
Comparison of evaluation items: RAPID7 and OpenVAS.
- Security research: In addition to having better detection interfaces and customized reporting functions, paid tools are maintained by professional research teams; open-source tools are mainly promoted by their communities, and their interfaces and report outputs are relatively simple. In spite of this, both open-source and paid tools will be included in the public CVE vulnerability database, and their final detection results are quite good.
- Cost: The cost of paid tools varies depending on the software, the manufacturer, and the number of years of use. Open-source tools, on the other hand, provide the software for free and only require the configuration of the required resources (such as virtual machines or physical machines). In contrast, open-source tools require professional engineers to build, maintain, and update them.
- Benefits: Detection and patching reports can be provided by both tools, enabling host system maintenance vendors to more effectively improve and reduce vulnerability risks.
4.1.2. Test Comparison Results Between Open-Source and Paid Tools
A university’s system hosts were scanned for vulnerabilities using the paid tool Rapid7 and the open-source tool OpenVAS. As shown in Table 6, paid tools perform better at detecting issues with older versions, especially in detecting issues with older versions. In hosts 1, 4, 5, 6, 13, and 15, Rapid7 was able to detect the older version of the problem, while the results of the other hosts were similar.

Table 6.
Comparison of actual detection results of weak scanning software.
Based on the severity of the vulnerabilities and the key vulnerabilities, we found that four hosts had detection differences, and 100% of the vulnerabilities were related to the A-category version update. There were 46 vulnerabilities detected on nine hosts, with 32 vulnerabilities totaling 69% falling under category A version update issues, eight vulnerabilities totaling 17% falling under category B security protocols and certificates, and six vulnerabilities totaling 14% falling under category C network service communication protocol settings. Detection differences for medium-risk vulnerabilities were observed on six hosts, of which two vulnerabilities totaling 19% were related to version updates, seven vulnerabilities totaling 58% were related to security protocols and certificates, and three vulnerabilities totaling 25% were related to communication protocol settings for network services, as shown in Table 6.
Vulnerability scanning tools are primarily designed to assist us in identifying vulnerabilities that can be exploited by attackers during the development process. However, it should be noted that there is no scanner that can achieve 100% perfect results at the moment. Version updates reflect the basic security concepts that system administrators should possess. It is imperative to pay attention to the versions of operating systems, tools, and packages used to ensure that there are no known major vulnerabilities. Whenever a version update is needed, it is important to assess the potential impact on the system. Before applying the update to the formal environment, it is recommended to test it in a test environment.
4.2. Test Results-Based Repair Suggestions
Based on the results of past tests [3,13], we categorized 25 common risks into four categories (Figure 6). Category A deals with version update issues, which include vulnerabilities in programs, databases, servers, and openssl versions that need to be updated. Among the security protocols and certificates in Category B are HTTPS certificates, TLS/SSL protocols, and weak encryption suites. The C category contains network communication protocol settings, such as FTP plain text authentication prohibition and SSH weak encryption algorithm issues, as well as IIS initial settings and disabling SMB1 services. In Category D, unauthorized access to databases and files is mainly prevented by controlling access permissions well.
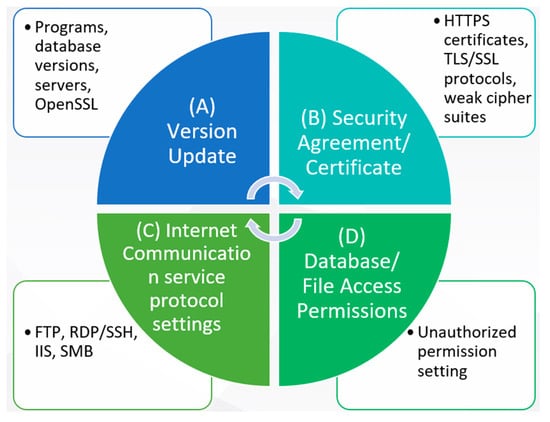
Figure 6.
Detection result and repair suggestions.
4.2.1. Version Update/Patch Enhancement: Program Version, Database Version, Server, and OpenSSL
It is important to update and enhance programs, databases, servers, OpenSSL, etc., regularly in order to maintain the system and ensure information security. Maintaining the latest and most secure version of the system is crucial, and version updates and enhancements should not be neglected due to cost or human resource concerns. To ensure privacy and security, version updates can effectively reduce potential risks and threats.
Let us take PHP5.6 as an example. As its maintenance stopped in 2018, newly discovered vulnerabilities cannot be patched, making it easier for hackers to exploit known security vulnerabilities. As reported by the CVE vulnerability database, there were 109 CVE vulnerabilities affecting versions 5.6.x~7.0.11 in 2016. By patching multiple vulnerabilities at once, administrators can significantly reduce the risk of information security breaches.
The official website offers regular security announcements, vulnerability information, and patch announcements for which official support has been discontinued. It is also recommended to pay attention to patch announcements for which official support has been discontinued. Apache’s official website provides instructions on how to update its security, and the National Information and Communications Security Research Institute official website or your local network center can keep you updated on the latest security warnings.
- (1)
- PHP, APACHE
Taking the PHP programming language as an example, new vulnerabilities are discovered every year, and old versions pose serious risks; therefore, it is necessary to regularly update and review the current version (server, programming language, etc.) to see if there is any newly discovered CVE vulnerability information. For version updates, it is also necessary to prepare a test area for update testing, and the program developers must confirm that the program functions are functioning normally before patching them in the official area.
- (2)
- Open SSL
Remote attackers can exploit most of the CVE vulnerabilities frequently discovered in OpenSSL, leading to denial of service or leakage of sensitive information and bypassing system control permissions. It is, therefore, important to frequently check whether the official website has released relevant version updates for the discovered vulnerabilities. As soon as a new version is released, it should be evaluated, tested, and updated.
- (3)
- Apache Tomcat
Update Apache Tomcat to the latest version, pay attention to relevant security announcements, and take appropriate security measures, such as setting strong passwords or limiting access rights. Security is ensured by preventing vulnerabilities from being exploited to execute arbitrary code.
- (4)
- WordPress
With a large number of plug-ins and a high degree of extensibility, WordPress is an open-source content management system (CMS). As a result of the diversity of plug-ins and the involvement of third-party developers, there are indeed some vulnerabilities. Updating WordPress regularly and installing the latest security patches will reduce the risk of your website being hacked.
4.2.2. Security Protocols/Certificates: HTTPS Certificates, TLS/SSL Protocols, and Weak Encryption Suites
Enabling insecure TLS/SSL protocols, canceling weak encryption suites, and ensuring the accuracy and validity period of certificate chains prevent information from being intercepted, stolen, or cracked. Communication integrity and confidentiality are ensured by these patches. It is necessary to disable insecure TLS/SSL protocols to prevent attackers from decrypting communications or conducting man-in-the-middle attacks. Enabling weak cipher suites prevents the use of easily cracked encryption algorithms and ensures data security.
An attacker could impersonate a trusted organization or website if the certificate chaining is not set up correctly or the certificate has expired, or if snooping, modifying, or tampering has occurred with the communications. Data security and privacy could be seriously compromised by such attacks. The purpose of these measures is to prevent data from being eavesdropped, forged, or modified by others while it is being transmitted.
- (1)
- Disable insecure TLS/SSL protocols or packages
Data transmission over the Internet is protected by TLS/SSL encryption. The National Security Agency (NSA) recommends disabling TLS 1.0, TLS 1.1, SSL 2.0, and SSL 3.0 protocols because hackers have already used the old versions of TLS protocols to launch attacks. A more secure encryption protocol, such as TLS 1.2 or TLS 1.3, should be used to reduce the risk of cyber-attacks. Among the algorithms supported by TLS 1.2 are NULL, RC2, RC4, DES, IDEA, and TDES/3DES. TLS/SSL protocols will continue to be monitored for security in the future.
- (2)
- A valid HTTPS certificate chain must be set up correctly and within the validity period
Data such as account numbers, passwords, and personal information cannot be intercepted or read during transmission with HTTPS certificates. Chrome (version 93) was updated in August 2011 and will support HTTPS-Only mode, which will display a warning message when a website does not support HTTPS. SSL certificates enhance website security, user trust, and search engine rankings while protecting sensitive information from attacks and theft.
4.2.3. Protocol Settings for Network Communication Services: FTP (Transfer Protocol), RDP/SSH (Remote Desktop Protocol), IIS (Internet Information Services), SMB (Server Message Block)
By disabling FTP’s plain text authentication method, authentication security is improved. By disabling unnecessary default features and services and strengthening authentication, IIS security settings help protect server resources. SSH’s weak encryption suite is also canceled, and only more secure encryption algorithms can be used, improving communication confidentiality and integrity. Additionally, by removing the SMB1 service, known security vulnerabilities such as ransomware attacks and remote code execution vulnerabilities are eliminated. It is also important to ensure the integrity and recoverability of data by implementing an effective backup mechanism. As a result of these comprehensive patches, network communications and services are strengthened, along with the overall system security.
- (1)
- Enable encryption for FTP or disable plain text authentication
Users can upload and download files through FTP by transferring files between different hosts. Data can therefore be stolen if the transmission process is not properly encrypted. To avoid being exposed to attacks and data theft on the Internet, it is recommended to use SSH or FTPS encryption methods for transmission.
- (2)
- The initial settings of IIS
IIS (Internet Information Services) is Microsoft’s web server software for Windows operating systems, including the following: web page configuration (Web), file transfer (FTP), email (SMTP), network news (NNTP), and other deployment and management functions. Using an outdated version of IIS, opening unused ports, or not paying attention to security settings may provide attackers with the opportunity to exploit.
- (3)
- Fix the problem of weak encryption suites (SSH, weak encryption, and weak algorithms).
SSH mainly protects the confidentiality and integrity of data by establishing a secure connection between the client and the server. As a result, data can be intercepted if a secure encryption algorithm is not used during transmission. To reduce the possibility of cyber-attacks and data theft on the Internet, it is recommended to disable insecure encryption suites and limit connection IPs.
- (4)
- Disable SMB1
SMB1 is a network protocol for sharing resources between machines, but it has security vulnerabilities and is vulnerable to man-in-the-middle attacks. SMB1 should be disabled to improve security. As a result of these vulnerabilities, SMB becomes a channel for viruses and hackers to spread, such as the WannaCry ransomware.
4.2.4. Access Permissions for Databases and Files
The management of database and archive access rights is crucial. If permissions are not configured properly, unauthorized users may gain access to sensitive data, resulting in data leakage or misuse. It is possible for data to be accidentally modified, deleted, or leaked if legitimate users are granted permissions that exceed their needs, or if permissions are too permissive or not properly restricted. It is therefore crucial to grant only the minimum permissions needed by legitimate users, and to review and update permissions configurations regularly. Fine-grained access control, role-based permission management, and enhanced authentication can help ensure the security and confidentiality of databases and files.
Access Restrictions to Databases
Open access databases often raise several issues, including security, privacy, data quality, regulatory compliance, and system performance. In order to ensure the integrity, privacy, and reliability of the database, appropriate security measures, data protection strategies, compliance mechanisms, and effective system management measures must be implemented. Therefore, it is recommended to restrict the database to the internal network and only accept connections from allowed systems, implement authentication and authorization mechanisms, use encrypted communications to protect data transmission, and regularly update and patch the database system, followed by firewalls and intrusion detection systems that protect database security.
Based on Table 7, this study summarizes the time efficiency required to upload a piece of data to IOTA and compares it with traditional blockchains (such as Bitcoin and Ethereum).

Table 7.
Comparison of on-chain efficiency between IOTA and traditional blockchains.
IOTA has zero transaction costs. With Tangle, IOTA uses a directed acyclic graph (DAG) technology that does not require miners to verify transactions, so there are no transaction fees. In particular, it can be used for Internet of Things (IoT) applications involving a large number of small transactions. Although the transaction cost is zero, the network’s security and decentralization may differ from other blockchain technologies. According to actual measured data, uploading a piece of information to the chain usually takes a few seconds to a few minutes.
Bitcoin: Transaction fees for Bitcoin are generally high, depending on network congestion and transaction size. Based on current network conditions. In terms of security and decentralization, Bitcoin is the first and most widely accepted cryptocurrency. Transaction fees are high, and transaction confirmation times are slow (often taking 10 min or more).
Ethereum: In Ethereum, the transaction fee is called GAS, and it is based on computational complexity, network congestion, and the GAS price set by the user. High flexibility and broad developer support are available for smart contracts and decentralized applications. It can take 1–2 min for a transaction to be confirmed, especially during times of network congestion. Transaction fees are moderate.
Several institutional cybersecurity audits and internal pilot projects have tested decentralized approaches incorporating blockchain and IPFS, offering precedent and validation for the proposed platform. For example, the Taiwan Ministry of Digital Affairs launched a pilot initiative in 2023 to explore blockchain-secured vulnerability reporting across select Class C government agencies. These pilot tests integrated IPFS for encrypted report storage and used IOTA to anchor timestamped audit trails, successfully demonstrating improved data integrity and coordination efficiency between agencies and third-party security contractors. Similarly, the European Union Agency for Cybersecurity (ENISA) supported an internal trial in which decentralized storage was applied to store penetration testing results from multiple critical infrastructure sectors, enhancing audit transparency and long-term archival reliability. In the private sector, Siemens AG piloted a blockchain-based vulnerability tracking module within its internal security operations center, using DAG-based structures (inspired by IOTA’s architecture) to document incident response timelines and verification events in a tamper-proof manner. Additionally, academic institutions such as the University of Tartu in Estonia conducted research-backed pilot deployments of decentralized file systems for cybersecurity log management, integrating IPFS nodes into their university-wide audit framework. These tested applications reveal the practical viability of integrating decentralized technologies in both public and private sectors to strengthen security assessments, promote verifiable compliance, and facilitate secure collaboration across organizational boundaries.
5. Conclusions and Recommendations
As part of the technical review process, information security testing has been mandated since the implementation of the Cybersecurity Law [1]. The frequency and complexity of cyber threats, such as malicious software, unauthorized intrusions, data breaches, and other information security incidents, have intensified alongside rapid advancements in digitalization and emerging technologies [5,6,25]. Consequently, enterprises are advised to conduct periodic security assessments to detect and remediate system vulnerabilities [8]. Security test reports typically identify system flaws, classify associated risks, and propose remediation strategies. These digital artifacts should be securely archived to support traceability, forensic investigation, and compliance with information governance standards [8].
To address integrity and availability concerns in report preservation, this study leverages both the immutability of blockchain technology and the decentralized storage capacity of the InterPlanetary File System (IPFS) [4,9,10]. This dual-layered approach not only fortifies data authenticity but also improves resilience against unauthorized access and malicious tampering [14]. By embedding cryptographic proofs such as hash values, the stored reports become verifiable and resistant to post facto alterations.
A comparative analysis of open-source and commercial vulnerability detection tools was conducted based on key performance indicators including feature set, usability, scanning efficiency, and cost-effectiveness. The results indicate that open-source solutions offer substantial advantages in terms of customization, transparency, and reduced operational costs—particularly for organizations with constrained budgets [4,12,26]. Accordingly, this research provides a framework for selecting appropriate tools, guiding the installation, configuration, and troubleshooting of open-source software to optimize security posture.
Moreover, this study emphasizes the importance of continuous software asset monitoring, urging development teams to periodically verify whether operating systems, programming languages, databases, and related toolsets remain under active maintenance or have been flagged for known vulnerabilities on official repositories [13]. Such practices are essential for ensuring long-term system stability and minimizing latent risk exposure.
The information security detection workflow classifies discovered vulnerabilities by severity level and provides actionable remediation guidance. This enables third-party or outsourced technical teams to apply security patches in a timely and targeted manner. By prioritizing high-risk vulnerabilities, organizations can substantially bolster the robustness of their cybersecurity infrastructure [5,27]. Furthermore, structured remediation instructions enhance internal capacity-building, promoting greater awareness of secure development practices and response preparedness.
In addition, this study’s integration of blockchain and IPFS for secure digital file handling demonstrates an effective model for tamper-proof storage, traceable dissemination, and trust-enhanced collaboration. Blockchain’s inherent resistance to data alteration, when paired with IPFS’s decentralized file distribution, offers a reliable mechanism for safeguarding the authenticity and confidentiality of critical testing documentation [11,15].
Future Directions for Research and Development
While automated security assessment tools offer broad coverage and repeatability, incorporating real-world attack simulations and case-based training can further enrich organizational resilience. The inclusion of practical exploit demonstrations enhances comprehension of threat vectors, fosters proactive defense strategies, and contributes to a more adaptive cybersecurity culture [28,29,30].
Author Contributions
Conceptualization, I.-C.L., C.-C.C. (Ching-Chun Chang), and C.-C.C. (Chin-Chen Chang); methodology, J.-Y.R.; software, J.-Y.R.; validation, C.-T.W., C.-C.C. (Ching-Chun Chang), and C.-C.C. (Chin-Chen Chang); formal analysis, C.-T.W.; investigation, C.-C.C. (Ching-Chun Chang) and C.-C.C. (Chin-Chen Chang); resources, C.-C.C. (Ching-Chun Chang) and C.-C.C. (Chin-Chen Chang); data curation, C.-C.C. (Ching-Chun Chang) and C.-C.C. (Chin-Chen Chang); writing—original draft preparation, C.-T.W.; writing—review and editing, C.-T.W.; supervision, C.-C.C. (Chin-Chen Chang); project administration, I.-C.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Chen, X.; Lin, Y.; Wu, Z. Cybersecurity Law Compliance in Taiwan: Challenges and Opportunities. J. Cybersecur. 2020, 1, 100–110. [Google Scholar]
- National Communications Commission (NCC). Guidelines on Information and Communication Security Management for Government Agencies; National Communications Commission: Taipei, Taiwan, 2022.
- National Institute of Standards and Technology (NIST). Security and Privacy Controls for Information Systems and Organizations (NIST Special Publication 800-53 Revision 5); NIST: Gaithersburg, MD, USA, 2020. [CrossRef]
- Amankwah, R.; Chen, J.; Kudjo, P.K.; Towey, D. An empirical comparison of commercial and open-source web vulnerability scanners. Softw. Pr. Exp. 2020, 50, 1842–1857. [Google Scholar] [CrossRef]
- European Union Agency for Cybersecurity (ENISA). ENISA Threat Landscape 2022; Publications Office of the European Union: Luxembourg, 2002; Available online: https://cymarop.ro/ENISA_Threat_Landscape.pdf (accessed on 5 May 2025).
- Symantec Corporation. Internet Security Threat Report. 2018, Volume 23. Available online: https://docs.broadcom.com/docs/istr-23-2018-en (accessed on 20 April 2025).
- National Institute of Standards and Technology. Secure Software Development Framework (SSDF) Version 1.1: Recommendations for Mitigating the Risk of Software Vulnerabilities (NIST Special Publication 800-218); U.S. Department of Commerce: Washington, WA, USA, 2022. [CrossRef]
- ISO/IEC 27036-3:2023; Cybersecurity—Supplier Relationships—Part 3: Guidelines for Hardware, Software, and Services Supply Chain Security. International Organization for Standardization/International Electrotechnical Commission: Geneva, Switzerland, 2023.
- Benet, J. IPFS—Content Addressed, Versioned, P2P File System. arXiv 2014, arXiv:1407.3561. [Google Scholar] [CrossRef]
- Chen, F. Enhancing Cloud Computing Security with Blockchain: A Hybrid Approach to Data Privacy and Integrity. J. Comput. Electron. Inf. Manag. 2024, 14, 75–79. [Google Scholar] [CrossRef]
- Zyskind, G.; Nathan, O.; Pentland, A. Decentralizing Privacy: Using Blockchain to Protect Personal Data. In Proceedings of the Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar] [CrossRef]
- Grance, T.; Jansen, W. Guidelines on Security and Privacy in Public Cloud Computing (NIST Special Publication 800-144); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2011. [Google Scholar] [CrossRef]
- OWASP Foundation. OWASP API Security Top 10—2023. 2023. Available online: https://owasp.org/API-Security/ (accessed on 5 May 2025).
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Haque, M.R.; Munna, S.I.; Ahmed, S.; Islam, M.T.; Onik, M.M.H.; Rahman, A.B.M.A. An Integrated Blockchain and IPFS Solution for Secure and Efficient Source Code Repository Hosting using Middleman Approach. arXiv 2024, arXiv:2409.14530. [Google Scholar] [CrossRef]
- Chhillar, K.; Shrivastava, S. Vulnerability Scanning and Management of University Computer Network. In Proceedings of the 2021 10th International Conference on Internet of Everything, Microwave Engineering, Communication and Networks (IEMECON), Jaipur, India, 1–2 December 2021; pp. 1–6. [Google Scholar]
- Tudela, F.M.; Higuera, J.-R.B.; Higuera, J.B.; Montalvo, J.-A.S.; Argyros, M.I. On Combining Static, Dynamic and Interactive Analysis Security Testing Tools to Improve OWASP Top Ten Security Vulnerability Detection in Web Applications. Appl. Sci. 2020, 10, 9119. [Google Scholar] [CrossRef]
- Cruz, D.B.; Almeida, J.R.; Oliveira, J.L. Open Source Solutions for Vulnerability Assessment: A Comparative Analysis. IEEE Access 2023, 11, 100234–100255. [Google Scholar] [CrossRef]
- Imtiaz, N.; Thorn, S.; Williams, L. A comparative study of vulnerability reporting by software composition analysis tools. In Proceedings of the 15th ACM/IEEE International Symposium on Empirical Software Engineering and Measurement (ESEM), New York, NY, USA, 11 October 2021; pp. 1–11. [Google Scholar]
- Wei, Q.; Li, B.; Chang, W.; Jia, Z.; Shen, Z.; Shao, Z. A Survey of Blockchain Data Management Systems. ACM Trans. Embed. Comput. Syst. 2022, 21, 25. [Google Scholar] [CrossRef]
- Sun, J.; Yao, X.; Wang, S.; Wu, Y. Blockchain-Based Secure Storage and Access Scheme for Electronic Medical Records in IPFS. IEEE Access 2022, 8, 59389–59401. [Google Scholar] [CrossRef]
- Kang, P.; Yang, W.; Zheng, J. Blockchain Private File Storage-Sharing Method Based on IPFS. Sensors 2022, 22, 5100. [Google Scholar] [CrossRef] [PubMed]
- Silvano, W.F.; Marcelino, R. Iota Tangle: A cryptocurrency to communicate Internet-of-Things data. Future Gener. Comput. Syst. 2020, 112, 307–319. [Google Scholar] [CrossRef]
- Lin, I.-C.; Chang, C.-C.; Chang, Y.-S. Data Security and Preservation Mechanisms for Industrial Control Network Using IOTA. Symmetry 2022, 14, 237. [Google Scholar] [CrossRef]
- Ritesh, V. Cybersecurity Challenges in the Era of Digital Transformation. ResearchGate. 2023. Available online: https://www.researchgate.net/publication/377625512_CYBERSECURITY_CHALLENGES_IN_THE_ERA_OF_DIGITAL_TRANSFORMATION (accessed on 5 May 2025).
- FS Community. What Are the Advantages of Open Source Software? FS Community. 2 November 2023. Available online: https://community.fs.com/blog/what-are-the-advantages-of-open-source-software.html (accessed on 5 May 2025).
- Householder, A.D.; Wassermann, G.; Manion, A.; King, C. The CERT® Guide to Coordinated Vulnerability Disclosure (CMU/SEI-2017-SR-022); Software Engineering Institute, Carnegie Mellon University: Pittsburgh, PA, USA, 2017. [Google Scholar] [CrossRef]
- Gundu, T. Learn, Unlearn and Relearn: Adaptive Cybersecurity Culture Model. Int. Conf. Cyber Warf. Secur. 2024, 19, 95–102. [Google Scholar] [CrossRef]
- MITRE Corporation. MITRE ATT&CK® Framework: Adversary Emulation and Red Teaming. 2023. Available online: https://attack.mitre.org/resources/get-started/adversary-emulation-and-red-teaming/ (accessed on 5 May 2025).
- Pescatore, J.; Hicks, T.A. SANS 2022 Top New Attacks and Threat Report; SANS Institute: Maryland, MD, USA, 2022; Available online: https://www.sans.org/white-papers/sans-2022-top-new-attacks-threat-report/ (accessed on 5 May 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).