An Effective Ensemble Learning-Based Real-Time Intrusion Detection Scheme for an In-Vehicle Network
Abstract
1. Introduction
- We design IDS with high accuracy for detecting and classifying attacks on the CAN bus. The scheme uses ensemble methods and Kappa Architecture’s efficient real-time data processing technique. We enhance IDS accuracy and efficiency by integrating ensemble methods and leveraging Kappa Architecture for real-time data analysis in the CAN bus attack detection scheme.
- We develop and test three supervised models that include hyperparameters tuning, balancing of data, and feature selection. The models are random forest (RF), eXtreme Gradient Boosting (XGBoost), and decision tree (DT).
- With three different ensemble methods, we combine the three supervised models to enhance our scheme’s ability to detect and classify DoS, fuzzing, replay, and spoofing attacks. These ensemble methods are stacking, voting, and bagging.
- In the evaluation of our scheme, we use well-known evaluation metrics, including accuracy, recall, F1 score, precision, and area under the curve receiver operating characteristic (ROC-AUC). The four attacks are accurately detected with an error rate of 1.5%.
2. Related Work
3. Background
3.1. CAN Bus
3.2. CAN Bus Attacks
3.3. Ensemble Methods
3.4. Kappa Architecture
3.5. Apache Spark
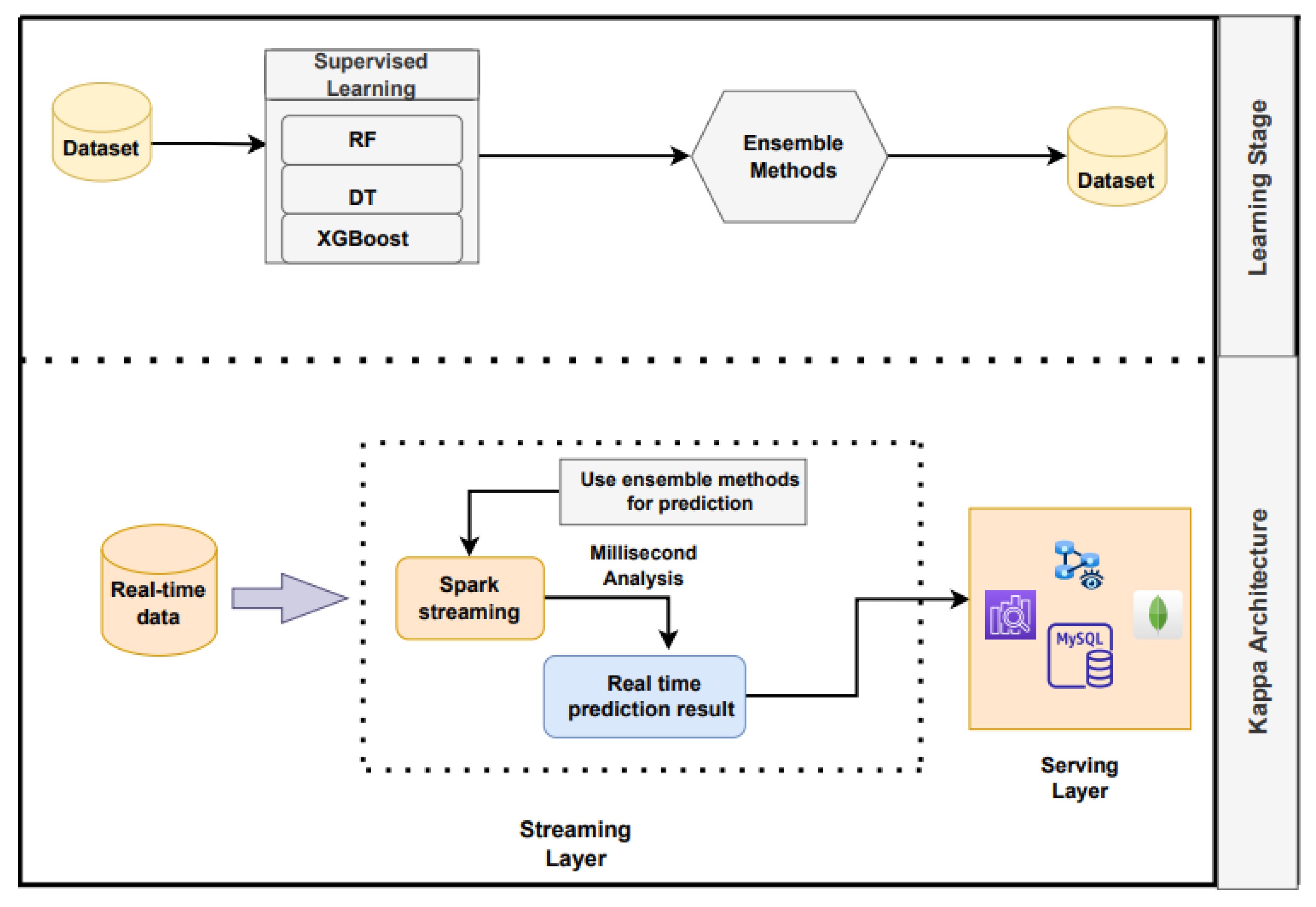
4. Proposed Method
4.1. Dataset
4.2. Learning Stage
4.3. Kappa Architecture
5. Results and Discussions
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Kleberger, P.; Olovsson, T.; Jonsson, E. Security aspects of the in-vehicle network in the connected car. In Proceedings of the 2011 IEEE Intelligent Vehicles Symposium (IV), Baden-Baden, Germany, 5–9 June 2011; pp. 528–533. [Google Scholar]
- Liu, J.; Zhang, S.; Sun, W.; Shi, Y. In-vehicle network attacks and countermeasures: Challenges and future directions. IEEE Netw. 2017, 31, 50–58. [Google Scholar] [CrossRef]
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A survey of intrusion detection for in-vehicle networks. IEEE Trans. Intell. Transp. Syst. 2019, 21, 919–933. [Google Scholar] [CrossRef]
- Petit, J.; Shladover, S.E. Potential cyberattacks on automated vehicles. IEEE Trans. Intell. Transp. Syst. 2014, 16, 546–556. [Google Scholar] [CrossRef]
- Lokman, S.F.; Othman, A.T.; Abu-Bakar, M.H. Intrusion detection system for automotive Controller Area Network (CAN) bus system: A review. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 184. [Google Scholar] [CrossRef]
- Young, C.; Zambreno, J.; Olufowobi, H.; Bloom, G. Survey of automotive controller area network intrusion detection systems. IEEE Des. Test 2019, 36, 48–55. [Google Scholar] [CrossRef]
- Bozdal, M.; Samie, M.; Aslam, S.; Jennions, I. Evaluation of can bus security challenges. Sensors 2020, 20, 2364. [Google Scholar] [CrossRef]
- Wang, Q.; Qian, Y.; Lu, Z.; Shoukry, Y.; Qu, G. A delay based plug-in-monitor for intrusion detection in controller area network. In Proceedings of the 2018 Asian Hardware Oriented Security and Trust Symposium (AsianHOST), Hong Kong, China, 17–18 December 2018; pp. 86–91. [Google Scholar]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental security analysis of a modern automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 447–462. [Google Scholar]
- Miller, C.; Valasek, C. Remote exploitation of an unaltered passenger vehicle. Black Hat USA 2015, 2015, 1–91. [Google Scholar]
- Karopoulos, G.; Kambourakis, G.; Chatzoglou, E.; Hernández-Ramos, J.L.; Kouliaridis, V. Demystifying in-vehicle intrusion detection systems: A survey of surveys and a meta-taxonomy. Electronics 2022, 11, 1072. [Google Scholar] [CrossRef]
- Khraisat, A.; Alazab, A. A critical review of intrusion detection systems in the internet of things: Techniques, deployment strategy, validation strategy, attacks, public datasets and challenges. Cybersecurity 2021, 4, 1–27. [Google Scholar] [CrossRef]
- Shichun, Y.; Zheng, Z.; Bin, M.; Yifan, Z.; Sida, Z.; Mingyan, L.; Yu, L.; Qiangwei, L.; Xinan, Z.; Mengyue, Z.; et al. Essential Technics of Cybersecurity for Intelligent Connected Vehicles: Comprehensive Review and Perspective. IEEE Internet Things J. 2023, 10, 21787–21810. [Google Scholar] [CrossRef]
- Kheddar, H.; Himeur, Y.; Awad, A.I. Deep transfer learning for intrusion detection in industrial control networks: A comprehensive review. J. Netw. Comput. Appl. 2023, 220, 103760. [Google Scholar] [CrossRef]
- Alalwany, E.; Mahgoub, I. Classification of Normal and Malicious Traffic Based on an Ensemble of Machine Learning for a Vehicle CAN-Network. Sensors 2022, 22, 9195. [Google Scholar] [CrossRef]
- Aliwa, E.; Rana, O.; Perera, C.; Burnap, P. Cyberattacks and countermeasures for in-vehicle networks. ACM Comput. Surv. (CSUR) 2021, 54, 21. [Google Scholar] [CrossRef]
- Alhowaide, A.; Alsmadi, I.; Tang, J. Ensemble detection model for IoT IDS. Internet Things 2021, 16, 100435. [Google Scholar] [CrossRef]
- Pham, N.T.; Foo, E.; Suriadi, S.; Jeffrey, H.; Lahza, H.F.M. Improving performance of intrusion detection system using ensemble methods and feature selection. In Proceedings of the Australasian Computer Science Week Multiconference, Brisbane, QLD, Australia, 29 January–2 February 2018; pp. 1–6. [Google Scholar]
- Ed-Daoudy, A.; Maalmi, K. Real-time machine learning for early detection of heart disease using big data approach. In Proceedings of the 2019 International Conference on Wireless Technologies, Embedded and Intelligent Systems (WITS), Fez, Morocco, 3–4 April 2019; pp. 1–5. [Google Scholar]
- Ameer, S.; Shah, M.A.; Khan, A.; Song, H.; Maple, C.; Islam, S.U.; Asghar, M.N. Comparative analysis of machine learning techniques for predicting air quality in smart cities. IEEE Access 2019, 7, 128325–128338. [Google Scholar] [CrossRef]
- Saraswathi, A.; Mummoorthy, A.; GR, A.R.; Porkodi, K. Real-time traffic monitoring system using spark. In Proceedings of the 2019 International Conference on Emerging Trends in Science and Engineering (ICESE), Hyderabad, India, 18–19 September 2019; Volume 1, pp. 1–6. [Google Scholar]
- Moulahi, T.; Zidi, S.; Alabdulatif, A.; Atiquzzaman, M. Comparative performance evaluation of intrusion detection based on machine learning in in-vehicle controller area network bus. IEEE Access 2021, 9, 99595–99605. [Google Scholar] [CrossRef]
- Song, H.M.; Woo, J.; Kim, H.K. In-vehicle network intrusion detection using deep convolutional neural network. Veh. Commun. 2020, 21, 100198. [Google Scholar] [CrossRef]
- Javed, A.R.; Ur Rehman, S.; Khan, M.U.; Alazab, M.; Reddy, T. CANintelliIDS: Detecting in-vehicle intrusion attacks on a controller area network using CNN and attention-based GRU. IEEE Trans. Netw. Sci. Eng. 2021, 8, 1456–1466. [Google Scholar] [CrossRef]
- Rathore, R.S.; Hewage, C.; Kaiwartya, O.; Lloret, J. In-vehicle communication cyber security: Challenges and solutions. Sensors 2022, 22, 6679. [Google Scholar] [CrossRef] [PubMed]
- Khan, M.A.; Karim, M.R.; Kim, Y. A two-stage big data analytics framework with real world applications using spark machine learning and long short-term memory network. Symmetry 2018, 10, 485. [Google Scholar] [CrossRef]
- Patil, N.V.; Rama Krishna, C.; Kumar, K. S-DDoS: Apache spark based real-time DDoS detection system. J. Intell. Fuzzy Syst. 2020, 38, 6527–6535. [Google Scholar] [CrossRef]
- Othman, D.M.S.; Hicham, R.; Zoulikha, M.M. An efficient spark-based network anomaly detection. Int. J. Comput. Digit. Syst. 2020, 9, 1175–1185. [Google Scholar] [CrossRef]
- Bosch, C. Specification Version 2.0; Robert Bosch GmbH: Gerlingen, Germany, 1991; Volume 1. [Google Scholar]
- Johansson, K.H.; Törngren, M.; Nielsen, L. Vehicle applications of controller area network. In Handbook of Networked and Embedded Control Systems; CRC Press: Boca Raton, FL, USA, 2005; pp. 741–765. [Google Scholar]
- Takefuji, Y. Connected vehicle security vulnerabilities [commentary]. IEEE Technol. Soc. Mag. 2018, 37, 15–18. [Google Scholar] [CrossRef]
- Bozdal, M.; Samie, M.; Jennions, I. A survey on can bus protocol: Attacks, challenges, and potential solutions. In Proceedings of the 2018 International Conference on Computing, Electronics & Communications Engineering (iCCECE), Southend, UK, 16–17 August 2018; pp. 201–205. [Google Scholar]
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the 2016 International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016; pp. 63–68. [Google Scholar]
- Lee, H.; Jeong, S.H.; Kim, H.K. OTIDS: A novel intrusion detection system for in-vehicle network by using remote frame. In Proceedings of the 2017 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, AB, Canada, 28–30 August 2017. [Google Scholar]
- Groza, B.; Murvay, P.S. Efficient intrusion detection with bloom filtering in controller area networks. IEEE Trans. Inf. Forensics Secur. 2018, 14, 1037–1051. [Google Scholar] [CrossRef]
- Avatefipour, O.; Malik, H. State-of-the-art survey on in-vehicle network communication (CAN-Bus) security and vulnerabilities. arXiv 2018, arXiv:1802.01725. [Google Scholar]
- Pan, L.; Zheng, X.; Chen, H.; Luan, T.; Bootwala, H.; Batten, L. Cyber security attacks to modern vehicular systems. J. Inf. Secur. Appl. 2017, 36, 90–100. [Google Scholar] [CrossRef]
- Nowdehi, N.; Lautenbach, A.; Olovsson, T. In-vehicle CAN message authentication: An evaluation based on industrial criteria. In Proceedings of the 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall), Toronto, ON, Canada, 24–27 September 2017; pp. 1–7. [Google Scholar]
- Zhang, H.; Meng, X.; Zhang, X.; Liu, Z. CANsec: A practical in-vehicle controller area network security evaluation tool. Sensors 2020, 20, 4900. [Google Scholar] [CrossRef]
- Alalwany, E.; Mahgoub, I. Security and Trust Management in the Internet of Vehicles (IoV): Challenges and Machine Learning Solutions. Sensors 2024, 24, 368. [Google Scholar] [CrossRef]
- Seo, E.; Song, H.M.; Kim, H.K. GIDS: GAN based intrusion detection system for in-vehicle network. In Proceedings of the 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, UK, 28–30 August 2018; pp. 1–6. [Google Scholar]
- Wolpert, D.H. Stacked generalization. Neural Netw. 1992, 5, 241–259. [Google Scholar] [CrossRef]
- Dietterich, T.G. Ensemble learning. In The Handbook of Brain Theory and Neural Networks; MIT Press: Cambridge, MA, USA, 2002; Volume 2, pp. 110–125. [Google Scholar]
- Quinlan, J.R. Bagging, boosting, and C4.5. In Proceedings of the Thirteenth National Conference on Artificial Intelligence (AAAI-96), Portland, OR, USA, 4–8 August 1996; Volume 1, pp. 725–730. [Google Scholar]
- Lin, J. The lambda and the kappa. IEEE Internet Comput. 2017, 21, 60–66. [Google Scholar] [CrossRef]
- Choudhary, P.; Garg, K. Comparative analysis of spark and hadoop through imputation of data on big datasets. In Proceedings of the 2021 IEEE Bombay Section Signature Conference (IBSSC), Gwalior, India, 18–20 November 2021; pp. 1–6. [Google Scholar]
- Kumar, K.; Sharma, N.A.; Ali, A.S. Machine Learning Solutions for Investigating Streams Data using Distributed Frameworks: Literature Review. In Proceedings of the 2021 IEEE Asia-Pacific Conference on Computer Science and Data Engineering (CSDE), Brisbane, Australia, 8–10 December 2021; pp. 1–6. [Google Scholar]
- Tun, M.T.; Nyaung, D.E.; Phyu, M.P. Performance evaluation of intrusion detection streaming transactions using apache kafka and spark streaming. In Proceedings of the 2019 International Conference on Advanced Information Technologies (ICAIT), Dehradun, India, 5–7 June 2019; pp. 25–30. [Google Scholar]
- Karau, H.; Konwinski, A.; Wendell, P.; Zaharia, M. Learning Spark: Lightning-Fast Big Data Analysis; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2015. [Google Scholar]
- Meng, X.; Bradley, J.; Yavuz, B.; Sparks, E.; Venkataraman, S.; Liu, D.; Freeman, J.; Tsai, D.; Amde, M.; Owen, S.; et al. Mllib: Machine learning in apache spark. J. Mach. Learn. Res. 2016, 17, 1235–1241. [Google Scholar]
- Apvrille, L.; El Khayari, R.; Henniger, O.; Roudier, Y.; Schweppe, H.; Seudié, H.; Weyl, B.; Wolf, M. Secure automotive on-board electronics network architecture. In Proceedings of the FISITA 2010 World Automotive Congress, Budapest, Hungary, 30 May–4 June 2010; Volume 8. [Google Scholar]
- Studnia, I.; Alata, E.; Nicomette, V.; Kaâniche, M.; Laarouchi, Y. A language-based intrusion detection approach for automotive embedded networks. Int. J. Embed. Syst. 2018, 10, 1–12. [Google Scholar] [CrossRef]
- Kang, H.; Kwak, B.; Lee, Y.H.; Lee, H.; Lee, H.; Kim, H.K. Car hacking: Attack and defense challenge 2020 dataset. IEEE Dataport 2021. [Google Scholar] [CrossRef]
- Breiman, L. Random forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Song, Y.Y.; Ying, L. Decision tree methods: Applications for classification and prediction. Shanghai Arch. Psychiatry 2015, 27, 130. [Google Scholar] [PubMed]
- Chen, T.; He, T.; Benesty, M.; Khotilovich, V.; Tang, Y.; Cho, H.; Chen, K.; Mitchell, R.; Cano, I.; Zhou, T.; et al. Xgboost: Extreme Gradient Boosting. R Package Version 0.4-2. 2015, Volume 1, pp. 1–4. Available online: https://cran.r-project.org/web/packages/xgboost/vignettes/xgboost.pdf (accessed on 25 February 2024).
- Sokolova, M.; Japkowicz, N.; Szpakowicz, S. Beyond accuracy, F-score and ROC: A family of discriminant measures for performance evaluation. In Proceedings of the 19th Australasian Joint Conference on Artificial Intelligence, Hobart, Australia, 4–8 December 2006; pp. 1015–1021. [Google Scholar]
- Refat, R.U.D.; Elkhail, A.A.; Hafeez, A.; Malik, H. Detecting can bus intrusion by applying machine learning method to graph based features. In Proceedings of the Intelligent Systems and Applications: Proceedings of the 2021 Intelligent Systems Conference (IntelliSys), Amsterdam, The Netherlands, 1–2 September 2022; Volume 3, pp. 730–748. [Google Scholar]






| Message Type | Count |
|---|---|
| Normal | 3,372,743 |
| Flooding | 154,180 |
| Fuzzing | 89,879 |
| Replay | 47,593 |
| Spoofing | 7756 |
| Total | 3,672,151 |
| Models | Accuracy | Recall | Precision | F1 |
|---|---|---|---|---|
| RF | 0.973 | 0.973 | 0.977 | 0.973 |
| DT | 0.981 | 0.981 | 0.984 | 0.981 |
| XGBoost | 0.982 | 0.982 | 0.985 | 0.982 |
| Models | Accuracy | Recall | Precision | F1 |
|---|---|---|---|---|
| Stacking | 0.985 | 0.985 | 0.987 | 0.985 |
| Bagging | 0.983 | 0.983 | 0.985 | 0.983 |
| Voting | 0.979 | 0.979 | 0.981 | 0.978 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alalwany, E.; Mahgoub, I. An Effective Ensemble Learning-Based Real-Time Intrusion Detection Scheme for an In-Vehicle Network. Electronics 2024, 13, 919. https://doi.org/10.3390/electronics13050919
Alalwany E, Mahgoub I. An Effective Ensemble Learning-Based Real-Time Intrusion Detection Scheme for an In-Vehicle Network. Electronics. 2024; 13(5):919. https://doi.org/10.3390/electronics13050919
Chicago/Turabian StyleAlalwany, Easa, and Imad Mahgoub. 2024. "An Effective Ensemble Learning-Based Real-Time Intrusion Detection Scheme for an In-Vehicle Network" Electronics 13, no. 5: 919. https://doi.org/10.3390/electronics13050919
APA StyleAlalwany, E., & Mahgoub, I. (2024). An Effective Ensemble Learning-Based Real-Time Intrusion Detection Scheme for an In-Vehicle Network. Electronics, 13(5), 919. https://doi.org/10.3390/electronics13050919








