Enhancing Privacy in the Internet of Vehicles via Hyperelliptic Curve Cryptography
Abstract
1. Introduction
2. Related State of the Art
2.1. Authentication Schemes
2.2. Secure Message Dissemination
2.3. Secure Schemes That Distribute the Computational Load on the Network
2.4. Blockchain Schemes to IoV Privacy Preservation
3. Background on the Cryptographic Protocols Employed
3.1. AES Cryptographic Protocol
- The AES scheme is a block cipher that makes use of the same key either for the encryption or decryption period.
- The unencrypted text block size is 16 bytes (128 bits).
- The size of the key can be 128 bits, 192 bits or 256 bits.
- AES contains iterations, best known as rounds, related to the key sizes. These are the following: (i) 10 rounds for a 128-bit key size, (ii) 12 rounds for a 192-bit key size and (iii) 14 rounds for a 256-bit key size.
- AES contains four levels: (1) SubByte, (2) ShiftRow, (3) MixColumn and (4) AddRoundKey. These stages take place with a continuous logic and are realized as rounds on a 4 × 4 byte state array. The plaintext (the text to be encrypted) is fed in those rounds.
- The SubByte level is represents byte substitution in a non-linear rationale, which is realized on every byte of the state array through an independent logic.
- The ShiftRow stage consists of four rows. The initial row is unshifted, while the rest of the three rows are moved in a circular logic over 1 to 3 bytes.
- The MixColumns stage makes use of the column-by-column strategy for working the state. Every column is used as a polynomial consisting of four terms in a GF(28). Then, it undergoes multiplication with a fixed a(x) modulo x4 + 1 polynomial.
- The AddRoundKey part operates the states via the use of one of the sub-keys by realizing XOR computation. The latter is implemented between every byte of the sub-key and every byte of the state.
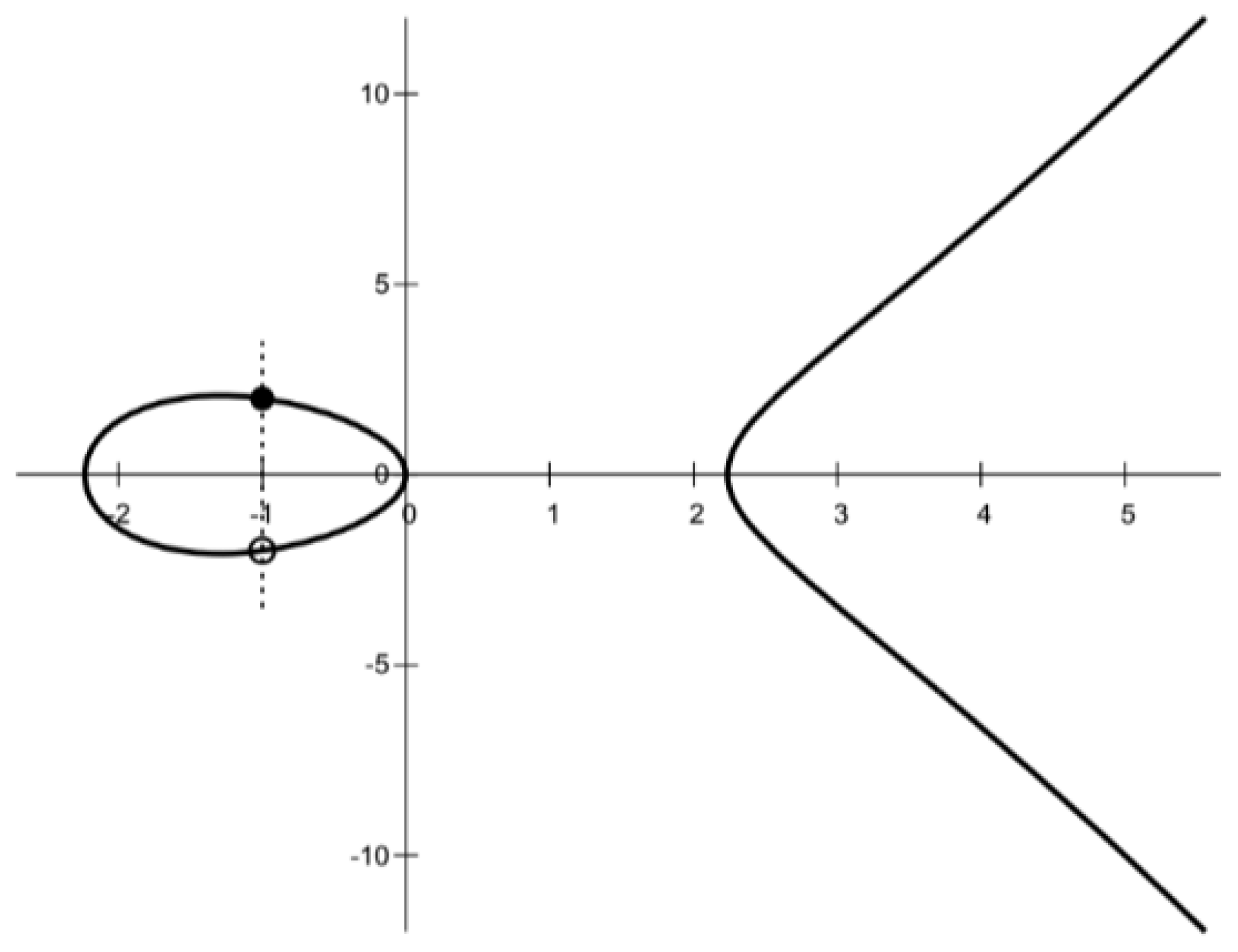
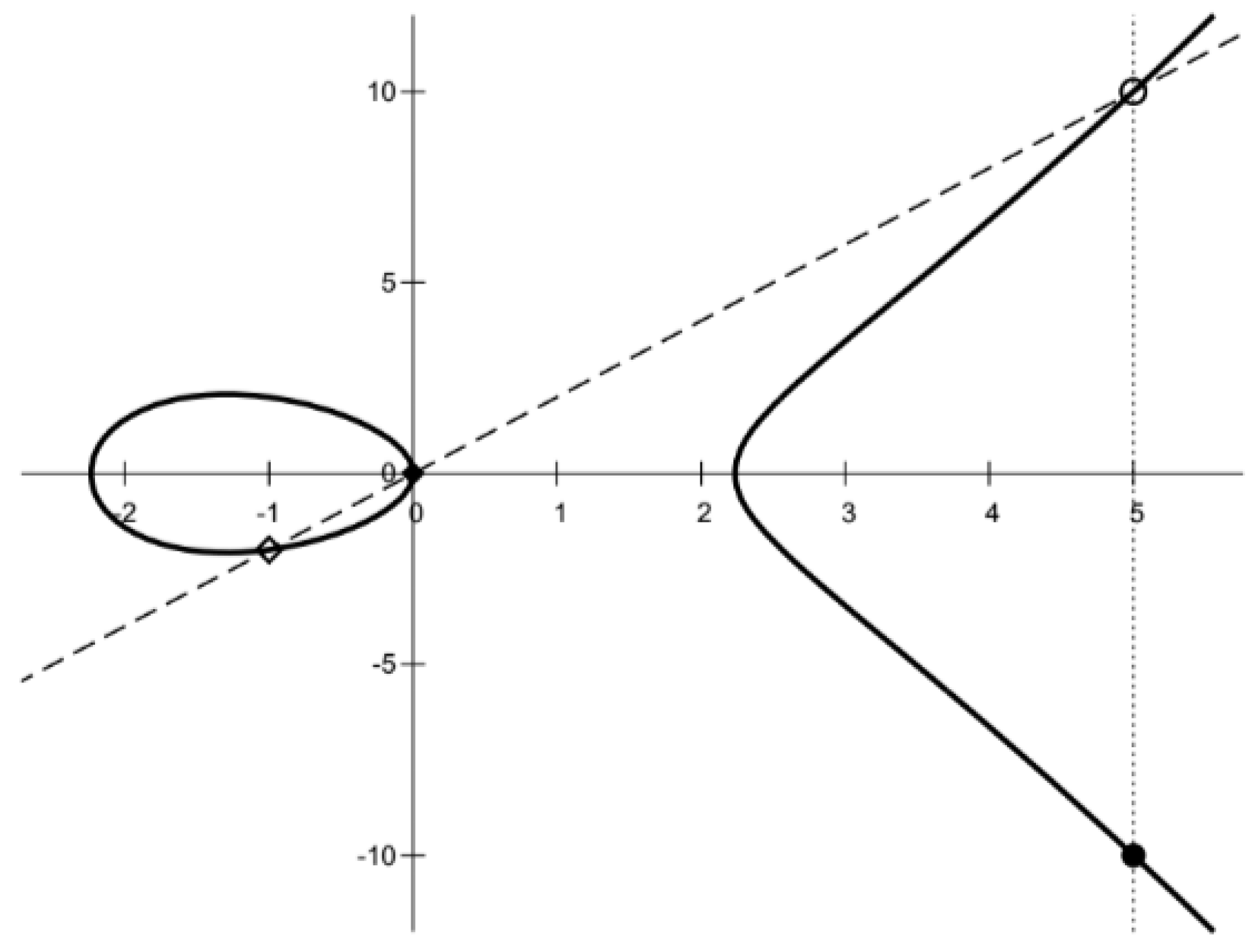
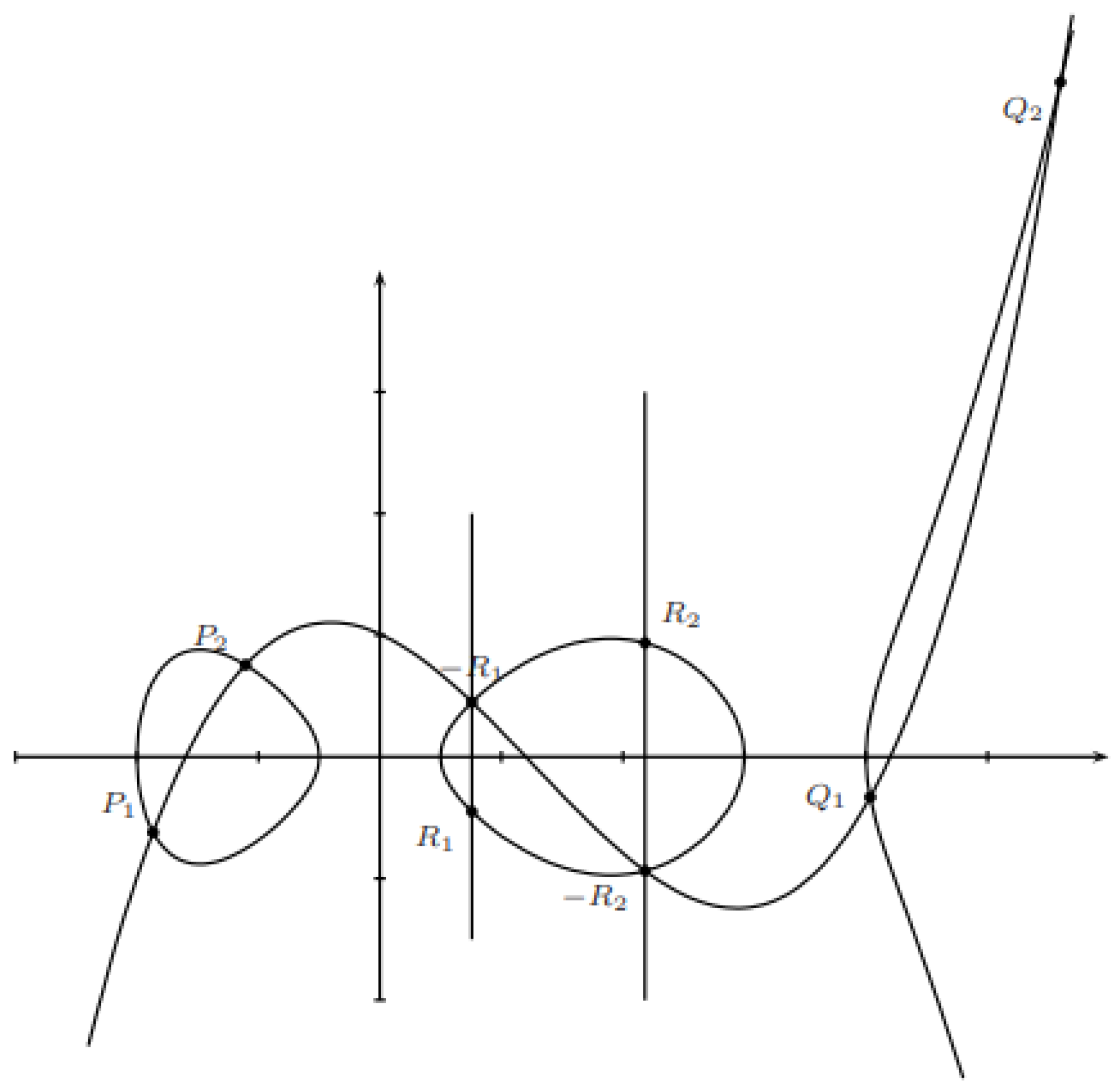
3.2. Elliptic Curve Cryptography
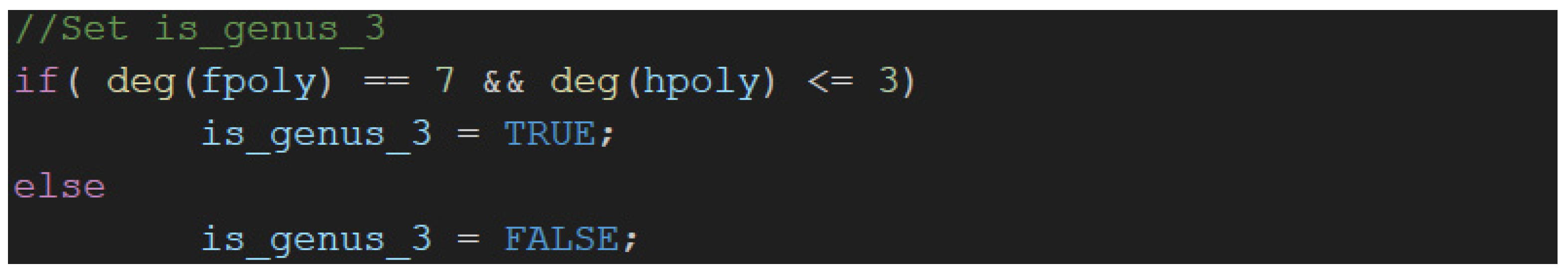
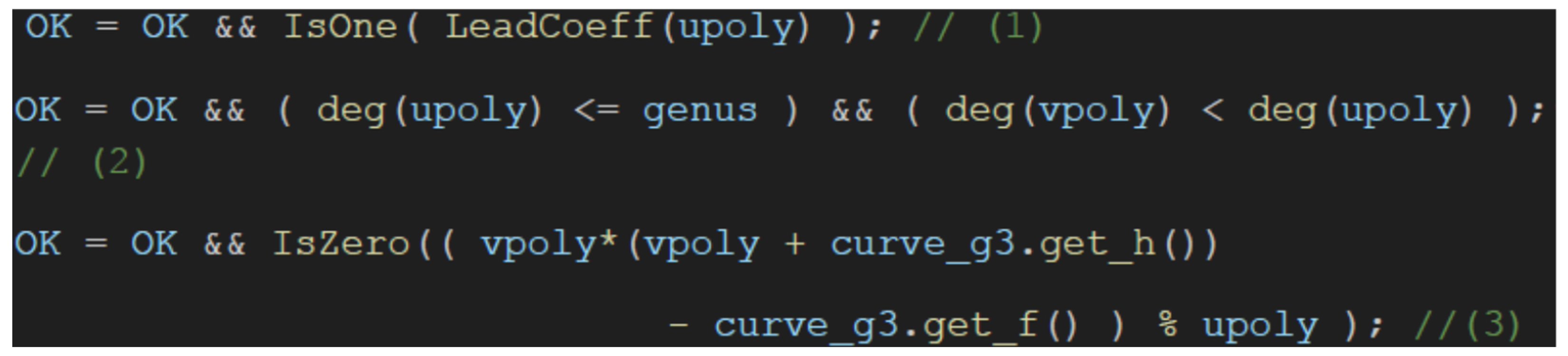
3.3. Hyperelliptic Curve Cryptography for Genus ≥2
- is singular;
- ;
- precisely divides the polynomial .
4. Proposed Approach
4.1. Design of the Proposed Approach
4.2. Implementation of the Proposed Approach
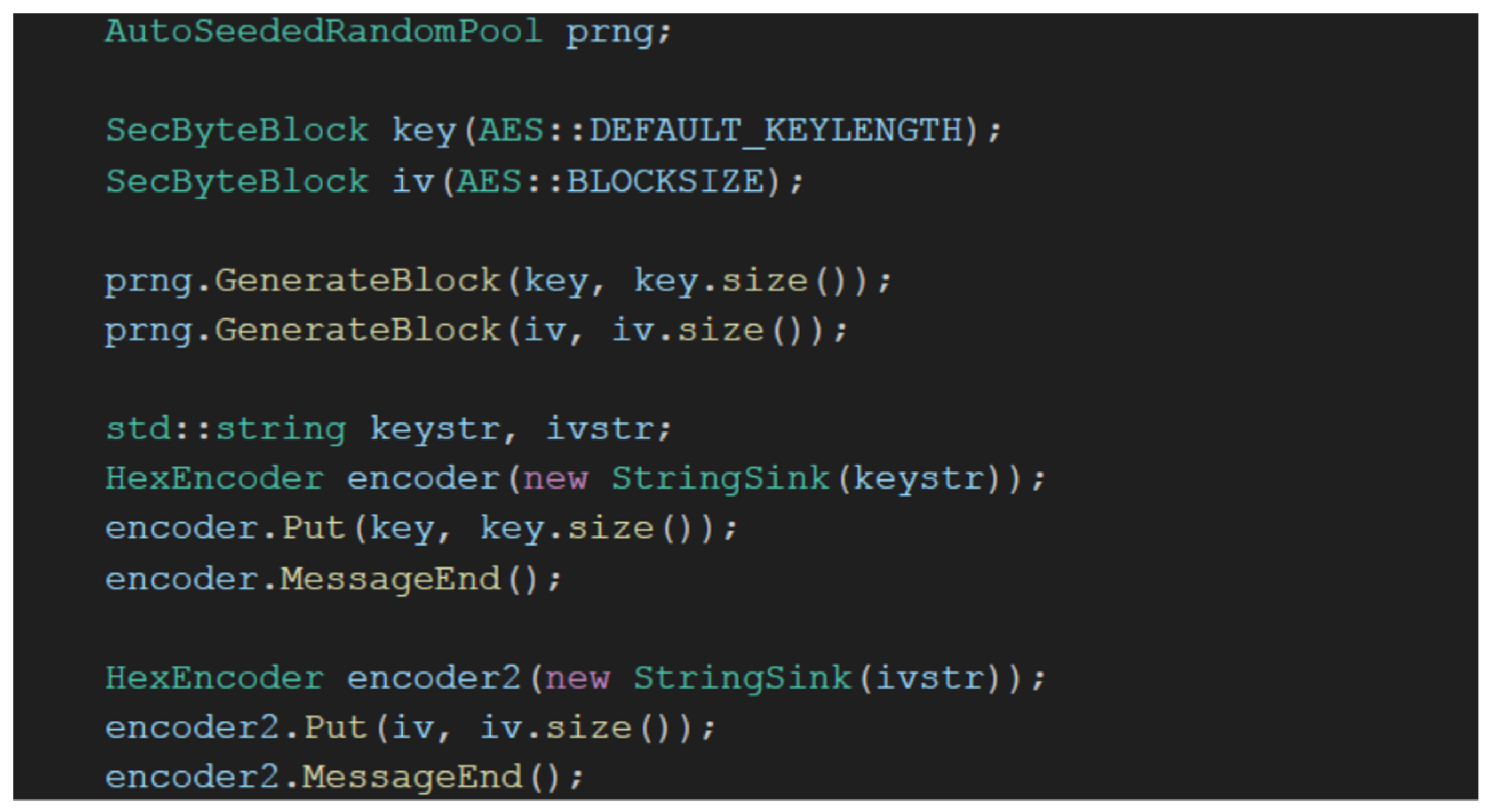
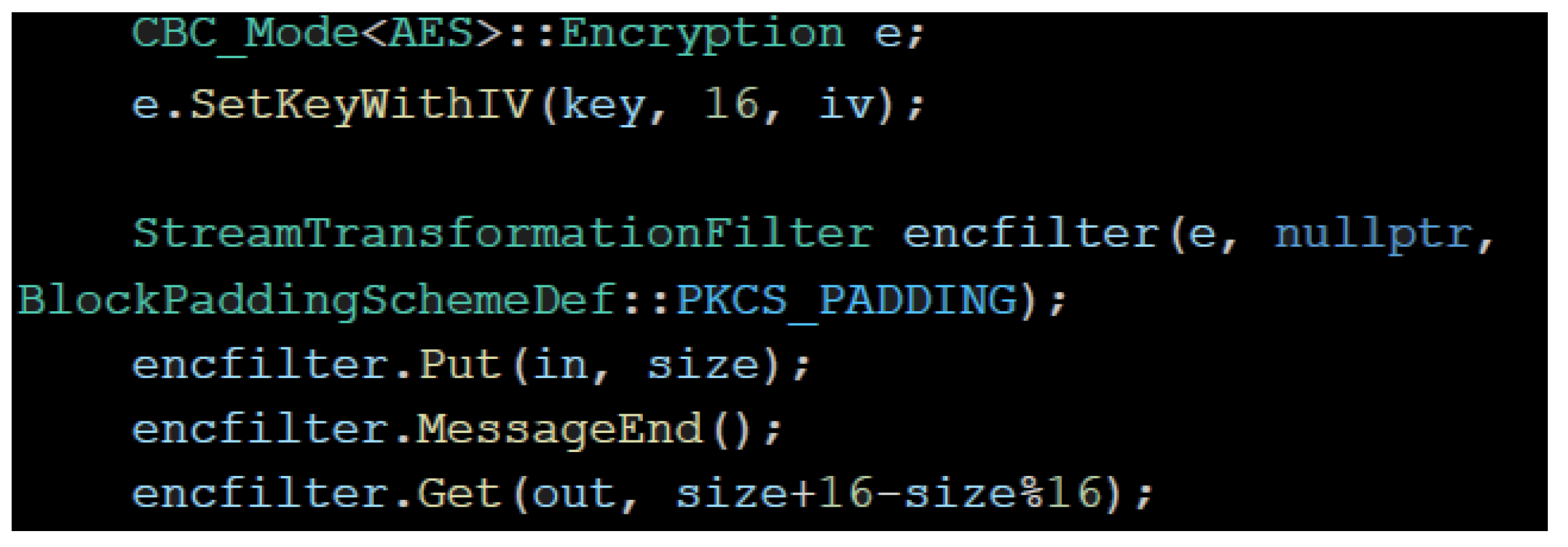
4.2.1. Cryptographic Techniques
- Operation method: cipher block chaining (CBC), since it is assumed that this provides significant security;
- Key size: 16 bytes (128 bits) for achieving speed;
- Block size: 128 bits.
4.2.2. Simulation of Road Traffic
4.2.3. VANET Communication
4.2.4. Energy Consumption Model
5. Experimental Evaluation
5.1. Evaluation Framework
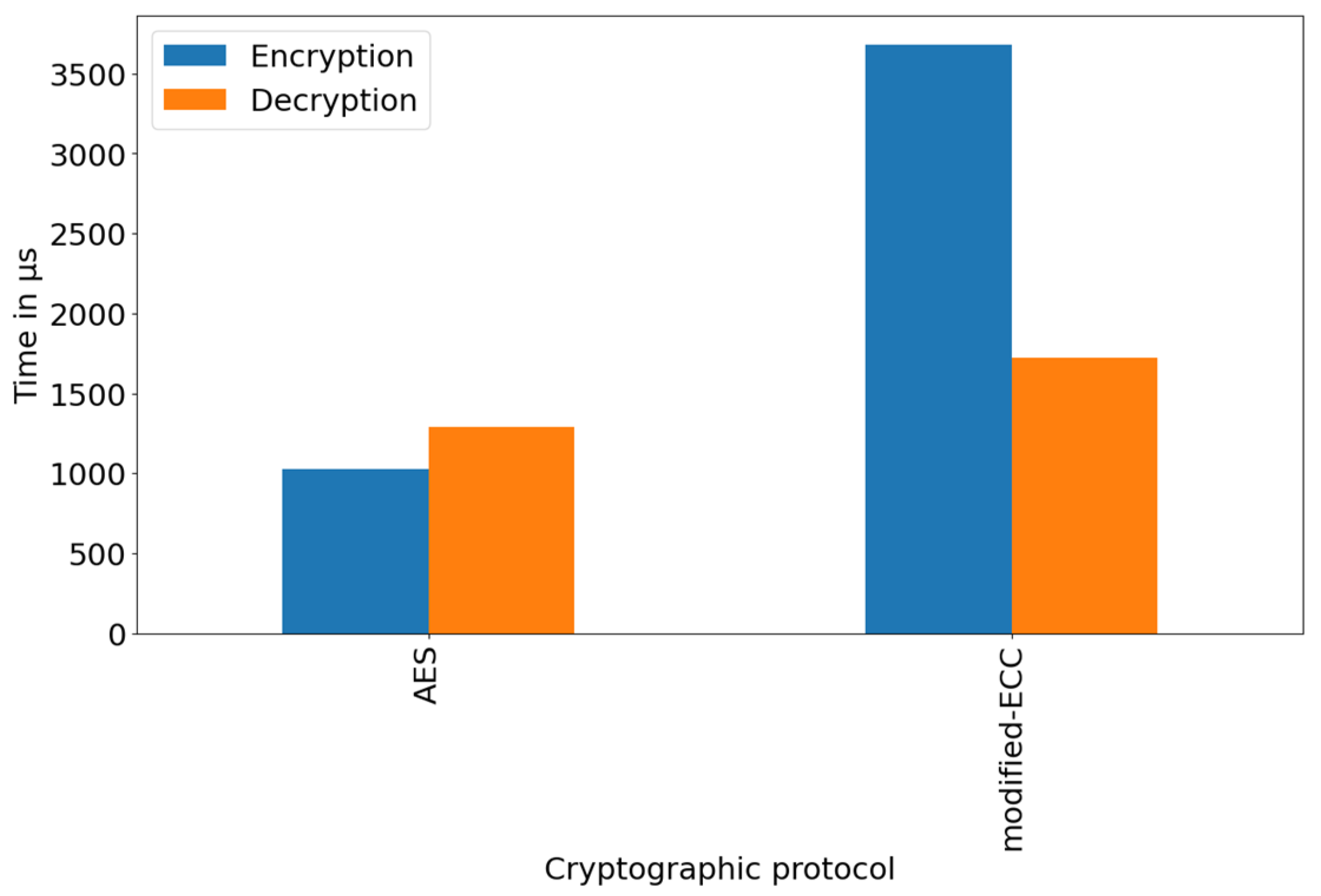
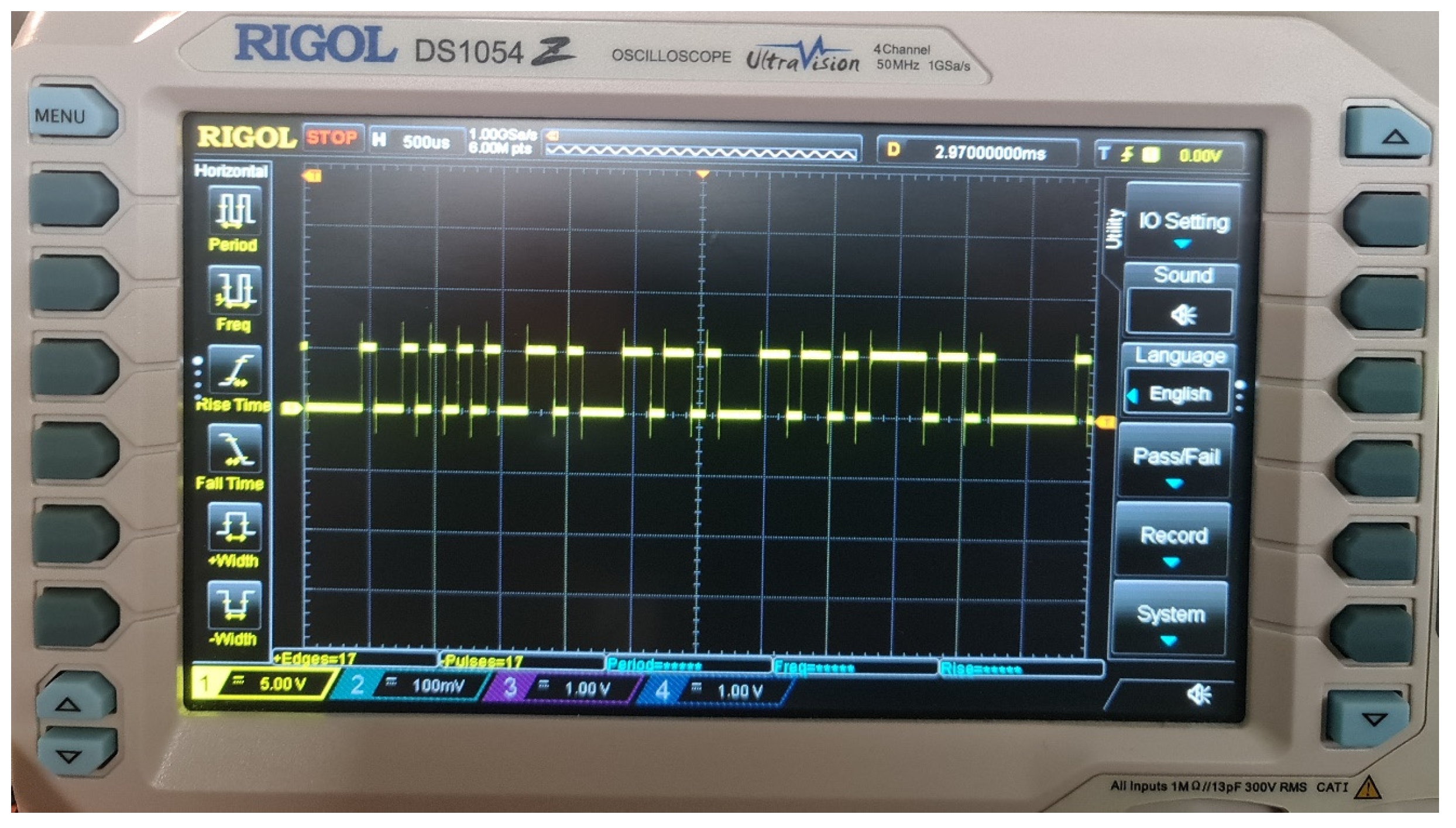
5.2. Duration of Cryptographic Operations
- Key pair generation;
- Certificate public key extraction;
- Message decryption;
- Message encryption;
- Signature generation;
- Signature verification;
- Decoding;
- Certificate private key reception;
- Certificate generation;
- Encoding.
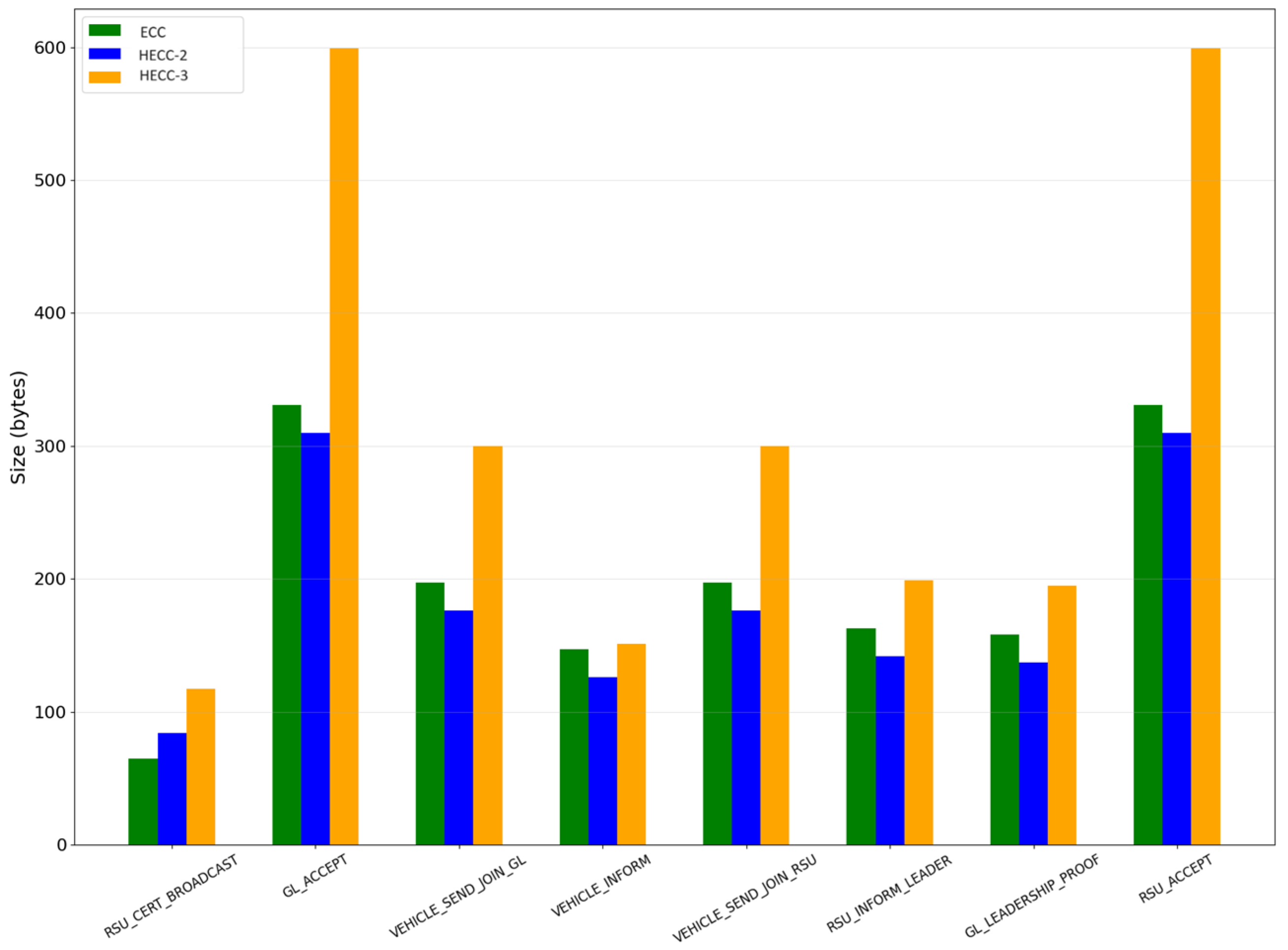
5.3. Size of Exchanged Messages
- RSU_CERT_BROADCAST: The certificate that RSU transmits periodically.
- VEHICLE_SEND_JOIN_RSU: The message “Join” that the vehicle sends to the RSU, when it needs to subscribe to the RSU’s area.
- RSU_ACCEPT: The RSU’s response to the vehicle’s message, “join”. It also contains the cryptographic symmetric key.
- RSU_INFORM_LEADER: The message that the RSU sends, in order to update a vehicle of the fact that a group leader has been chosen. This provides the proof of leadership.
- GL_LEADERSHIP_PROOF: The message that the GL (group leader) broadcasts periodically, in order to prove that it is valid and invite the vehicles to “join” him.
- VEHICLE_SEND_JOIN_GL: The message, “Join”, that the vehicle sends to the GL, when it needs to subscribe to the GL.
- GL_ACCEPT: The GL’s response to the vehicle’s message, “join”, also carrying the cryptographic symmetric key.
- VEHICLE_INFORM: The message that a vehicle sends in order to update for its position. It was chosen typically as an updating message for system evaluation.
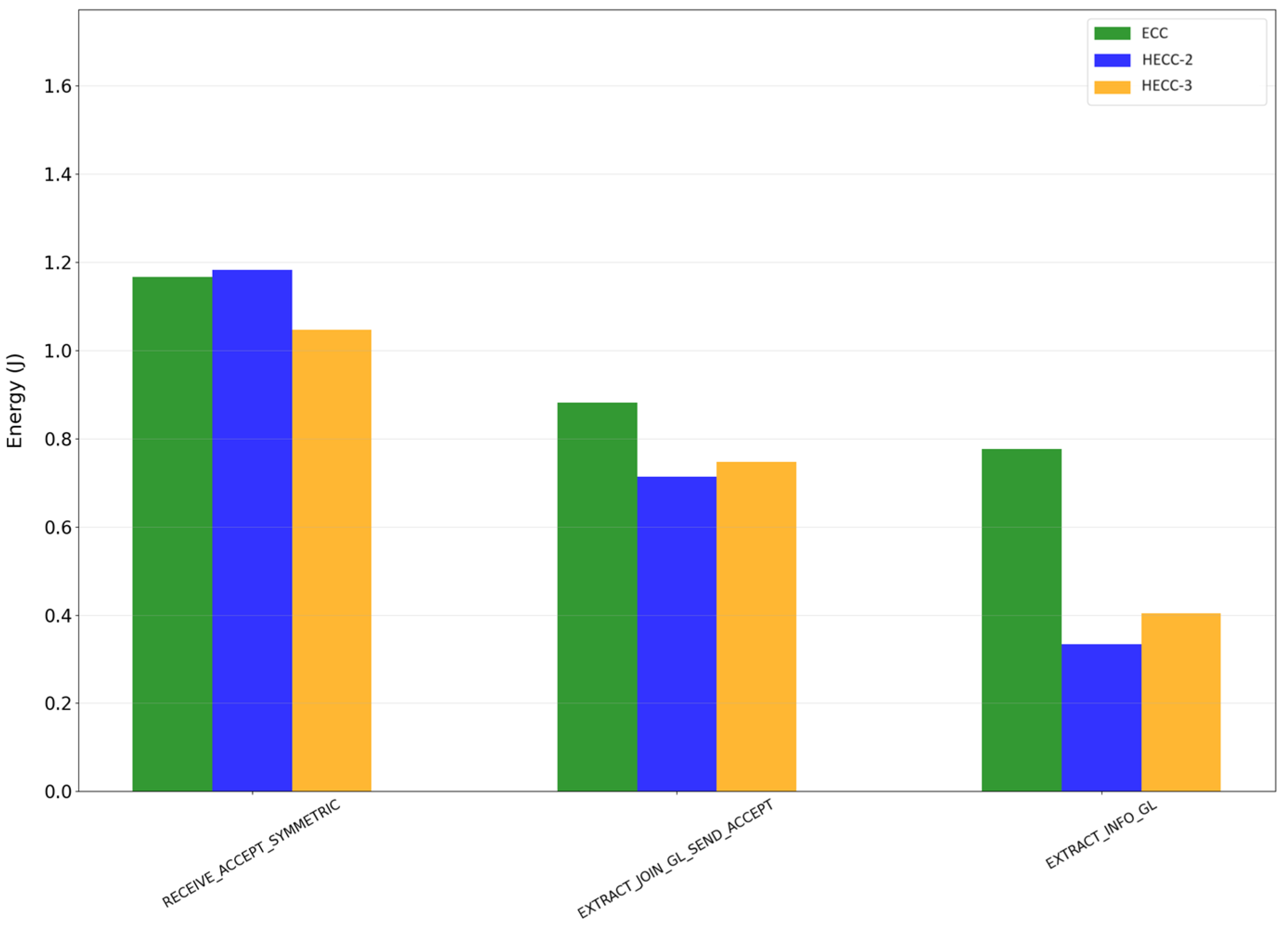
5.4. Energy Consumption
- RECEIVE_CERT: This just describes the procedure of receiving and processing the certificate of the RSU (a process of a very short duration).
- EXTRACT_GL_PROOF: This describes the procedure of receiving and processing the GL leader’s proof (a process of a very short duration).
- RECEIVE_ACCEPT_SYMMETRIC: This describes the procedure of sending the message “Join” and receiving and processing the “Accept” response from the RSU.
- EXTRACT_JOIN_SEND_ACCEPT: This describes the procedure of the “Join” message that the GL receives from a vehicle and the transmission of the “Accept” response.
- EXTRACT_INFO_GL: This describes the procedure of extracting a message, “Inform”, that the GL receives from a vehicle.
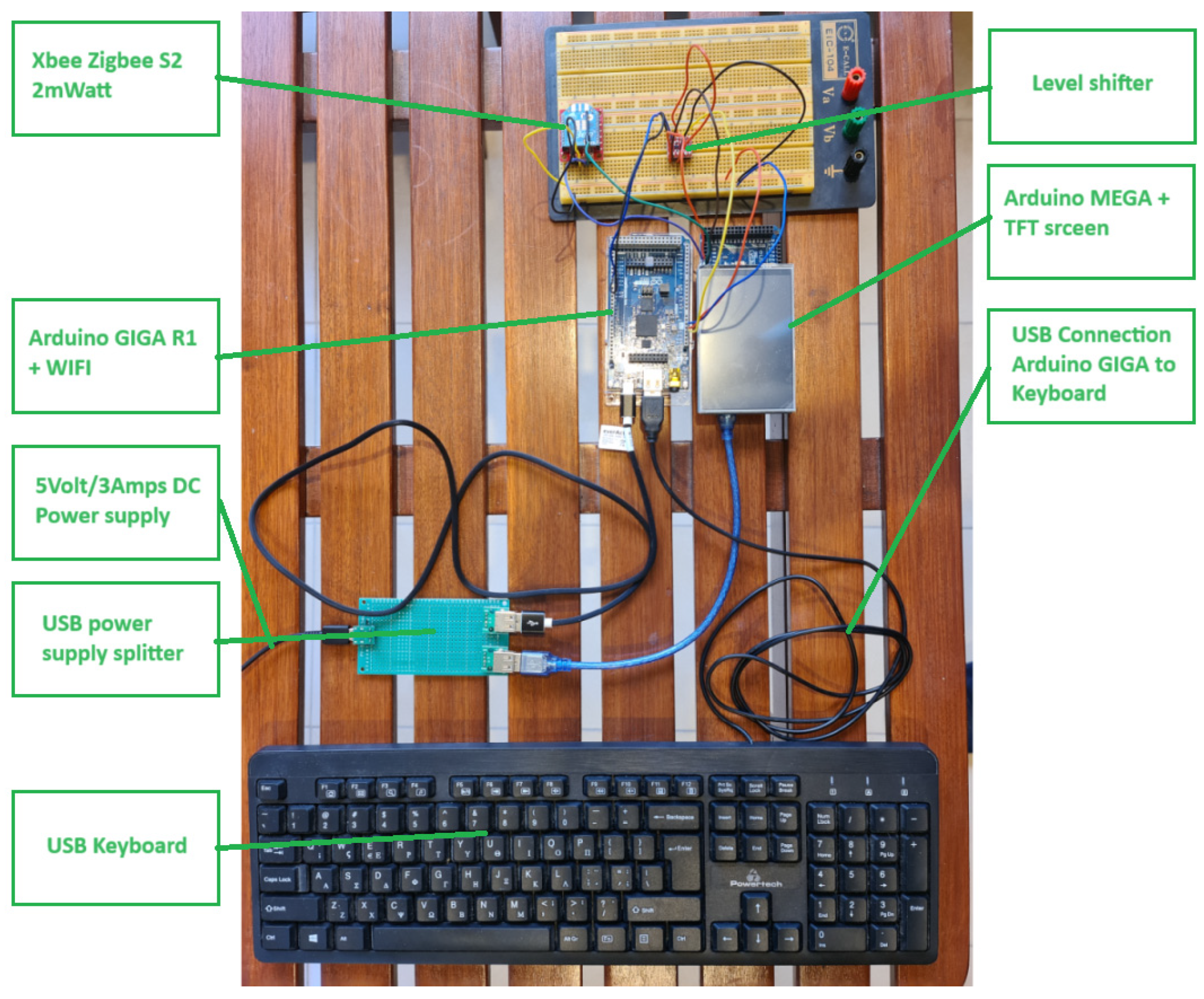
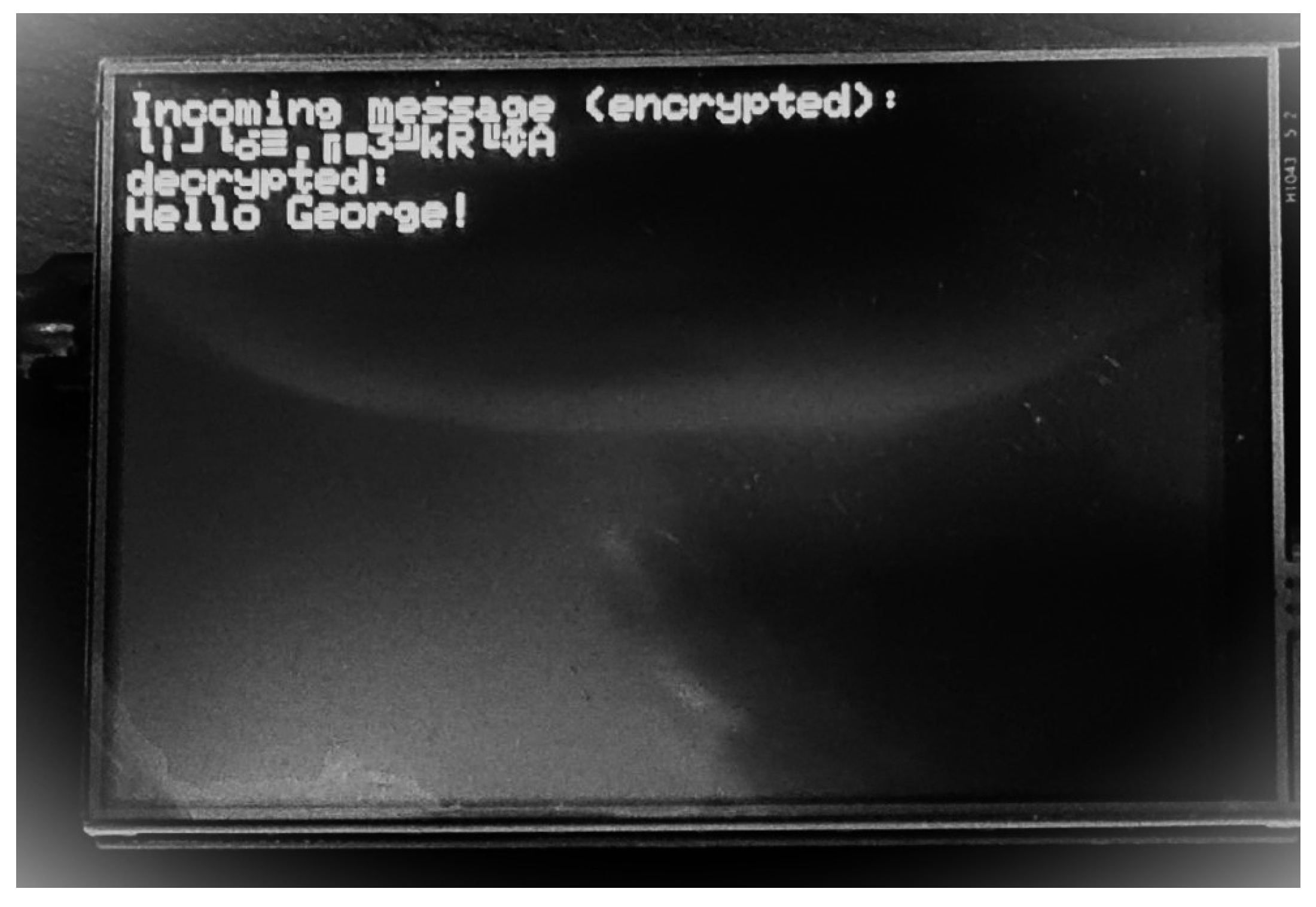
6. A System for Message Encryption via Zigbee Network, Using AES or ECC
- LCD Type: TFT;
- LCD Interface: SPI;
- LCD Controller: ILI9486;
- Touch Screen Type: Resistive;
- Touch Screen Controller: XPT2046;
- Colors: RGB, 65K colors;
- Resolution: 480 × 320 (Pixel);
- Aspect Ratio: 8:5;
- I/O Voltage: 3.3–5 V.
7. Conclusions and Plans for the Future
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Chen, W.; Wu, H.; Chen, X.; Chen, J. A Review of Research on Privacy Protection of Internet of Vehicles Based on Blockchain. J. Sens. Actuator Netw. 2022, 11, 86. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Abdullah, A.M.; Mohsan, S.A.H.; Noor, F. An Efficient and Conditional Privacy-Preserving Heterogeneous Signcryption Scheme for the Internet of Drones. Sensors 2023, 23, 1063. [Google Scholar] [CrossRef]
- Shayea, G.G.; Mohammed, D.A.; Abbas, A.H.; Abdulsattar, N.F. Privacy-Aware Secure Routing through Elliptical Curve Cryptography with Optimal RSU Distribution in VANETs. Designs 2022, 6, 121. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. A Secure Pseudonym-Based Conditional Privacy-Preservation Authentication Scheme in Vehicular Ad Hoc Networks. Sensors 2022, 22, 1696. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Deboarh, L.J. EAAP: Efficient Anonymous Authentication With Conditional Privacy-Preserving Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transport. Syst. 2017, 18, 2467–2476. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Y.; Chang, G. Efficient Privacy-Preserving Dual Authentication and Key Agreement Scheme for Secure V2V Communications in an IoV Paradigm. IEEE Trans. Intell. Transport. Syst. 2017, 18, 2740–2749. [Google Scholar] [CrossRef]
- Jo, H.J.; Kim, I.S.; Lee, D.H. Reliable Cooperative Authentication for Vehicular Networks. IEEE Trans. Intell. Transport. Syst. 2018, 19, 1065–1079. [Google Scholar] [CrossRef]
- Shen, Z.; Wang, Y.; Wang, H.; Liu, P.; Liu, K.; Zhang, J. Trust Mechanism Privacy Protection Scheme Combining Blockchain and Multi-Party Evaluation. IEEE Trans. Intell. Veh. 2024, 1–10. [Google Scholar] [CrossRef]
- Su, H.; Dong, S.; Wang, N.; Zhang, T. An Efficient Privacy-Preserving Authentication Scheme That Mitigates TA Dependency in VANETs. Veh. Commun. 2024, 45, 100727. [Google Scholar] [CrossRef]
- Mistareehi, H.; Islam, T.; Manivannan, D. A Secure and Distributed Architecture for Vehicular Cloud. Internet Things 2021, 13, 100355. [Google Scholar] [CrossRef]
- Rezazadeh Baee, M.A.; Simpson, L.; Boyen, X.; Foo, E.; Pieprzyk, J. ALI: Anonymous Lightweight Inter-Vehicle Broadcast Authentication with Encryption. IEEE Trans. Dependable Secur. Comput. 2022, 20, 1799–1817. [Google Scholar] [CrossRef]
- Dua, A.; Kumar, N.; Das, A.K.; Susilo, W. Secure Message Communication Protocol Among Vehicles in Smart City. IEEE Trans. Veh. Technol. 2018, 67, 4359–4373. [Google Scholar] [CrossRef]
- Mistareehi, H.; Manivannan, D. A Low-Overhead Message Authentication and Secure Message Dissemination Scheme for VANETs. Network 2022, 2, 139–152. [Google Scholar] [CrossRef]
- Batool, H.; Anjum, A.; Khan, A.; Izzo, S.; Mazzocca, C.; Jeon, G. A Secure and Privacy Preserved Infrastructure for VANETs Based on Federated Learning with Local Differential Privacy. Inf. Sci. 2024, 652, 119717. [Google Scholar] [CrossRef]
- Yadav, V.K. Anonymous and Linkable Ring Signcryption Scheme for Location-Based Services in VANETs. Veh. Commun. 2024, 45, 100717. [Google Scholar] [CrossRef]
- Shen, Z.; Ren, F.; Wang, H.; Liu, P.; Liu, K.; Zhang, J. Combining Blockchain and Crowd-Sensing for Location Privacy Protection in Internet of Vehicles. Veh. Commun. 2024, 45, 100724. [Google Scholar] [CrossRef]
- Huang, J.; Kong, L.; Wang, J.; Chen, G.; Gao, J.; Huang, G.; Khan, M.K. Secure Data Sharing over Vehicular Networks Based on Multi-Sharding Blockchain. ACM Trans. Sens. Netw. 2024, 20, 1–23. [Google Scholar] [CrossRef]
- Tandon, R.; Verma, A.; Gupta, P.K. D-BLAC: A Dual Blockchain-Based Decentralized Architecture for Authentication and Communication in VANET. Expert Syst. Appl. 2024, 237, 121461. [Google Scholar] [CrossRef]
- Hammod, D.N. Modified Lightweight AES Based on Replacement Table and Chaotic System. In Proceedings of the 2022 International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), Ankara, Turkey, 9 June 2022; pp. 1–5. [Google Scholar]
- Scheidler, R. An Introduction to Hyperelliptic Curve Arithmetic; World Scientific: Singapore, 2015. [Google Scholar]
- Alimoradi, R. A Study of Hyperelliptic Curves in Cryptography. Int. J. Comput. Netw. Inf. Secur. 2016, 8, 67–72. [Google Scholar] [CrossRef]
- Bh, P.; Chandravathi, D.; Roja, P.P. Encoding and Decoding of a Message in the Implementation of Elliptic Curve Cryptography Using Koblitz’s Method. Int. J. Comput. Sci. Eng. 2010, 2, 1904–1907. [Google Scholar]
- Campagna, M. SEC 4: Elliptic Curve Qu-Vanstone Implicit Certificate Scheme (ECQV). In Standards for Efficient Cryptography, Version 1; Certicom Research: Mississauga, ON, Canada, 2013. [Google Scholar]
- Cohen, H.; Frey, G.; Avanzi, R.; Doche, C.; Lange, T.; Nguyen, K.; Vercauteren, F. Handbook of Elliptic and Hyperelliptic Curve Cryptography; CRC Press: Boca Raton, FL, USA, 2005. [Google Scholar]
- Gaudry, P.; Schost, É. Construction of Secure Random Curves of Genus 2 over Prime Fields. In Advances in Cryptology—EUROCRYPT 2004; Cachin, C., Camenisch, J.L., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3027, pp. 239–256. ISBN 978-3-540-21935-4. [Google Scholar]
- Seck, M.; Diarra, N. Unified Formulas for Some Deterministic Almost-Injective Encodings into Hyperelliptic Curves. In Progress in Cryptology—AFRICACRYPT 2018; Joux, A., Nitaj, A., Rachidi, T., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2018; Volume 10831, pp. 183–202. ISBN 978-3-319-89338-9. [Google Scholar]
- Weng, A. A Class of Hyperelliptic CM-Curves of Genus Three. J.-Ramanujan Math. Soc. 2001, 16, 339–372. [Google Scholar]
- Pelzl, J.; Wollinger, T.; Paar, C. Special Hyperelliptic Curve Cryptosystems of Genus Two: Efficient Arithmetic and Fast Implementation. In Embedded Cryptographic Hardware: Design and Security; Nova Science Publishers: New York, NY, USA, 2004. [Google Scholar]
- Pelzl, J.; Wollinger, T.; Guajardo, J.; Paar, C. Hyperelliptic Curve Cryptosystems: Closing the Performance Gap to Elliptic Curves. In Cryptographic Hardware and Embedded Systems—CHES 2003; Walter, C.D., Koç, Ç.K., Paar, C., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2779, pp. 351–365. ISBN 978-3-540-40833-8. [Google Scholar]







Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Routis, G.; Dagas, P.; Roussaki, I. Enhancing Privacy in the Internet of Vehicles via Hyperelliptic Curve Cryptography. Electronics 2024, 13, 730. https://doi.org/10.3390/electronics13040730
Routis G, Dagas P, Roussaki I. Enhancing Privacy in the Internet of Vehicles via Hyperelliptic Curve Cryptography. Electronics. 2024; 13(4):730. https://doi.org/10.3390/electronics13040730
Chicago/Turabian StyleRoutis, George, Panagiotis Dagas, and Ioanna Roussaki. 2024. "Enhancing Privacy in the Internet of Vehicles via Hyperelliptic Curve Cryptography" Electronics 13, no. 4: 730. https://doi.org/10.3390/electronics13040730
APA StyleRoutis, G., Dagas, P., & Roussaki, I. (2024). Enhancing Privacy in the Internet of Vehicles via Hyperelliptic Curve Cryptography. Electronics, 13(4), 730. https://doi.org/10.3390/electronics13040730






