Hierarchical-Based Dynamic Scenario-Adaptive Risk Assessment for Power Data Lifecycle
Abstract
1. Introduction
- Thoroughly investigate the spectrum of security needs throughout the entire lifecycle of data within the power grid, especially focusing on scenario-specific disclosures and their inherent security challenges.
- Develop a comprehensive framework for data lifecycle security protection, meticulously analysing security requirements at each stage of data openness and usage.
- Introduce an innovative, holistic approach to data security risk assessment, blending hierarchical analysis with fuzzy comprehensive evaluation. This methodology is designed to dynamically adapt to different scenarios, thereby enhancing the precision and effectiveness of security level assessments.
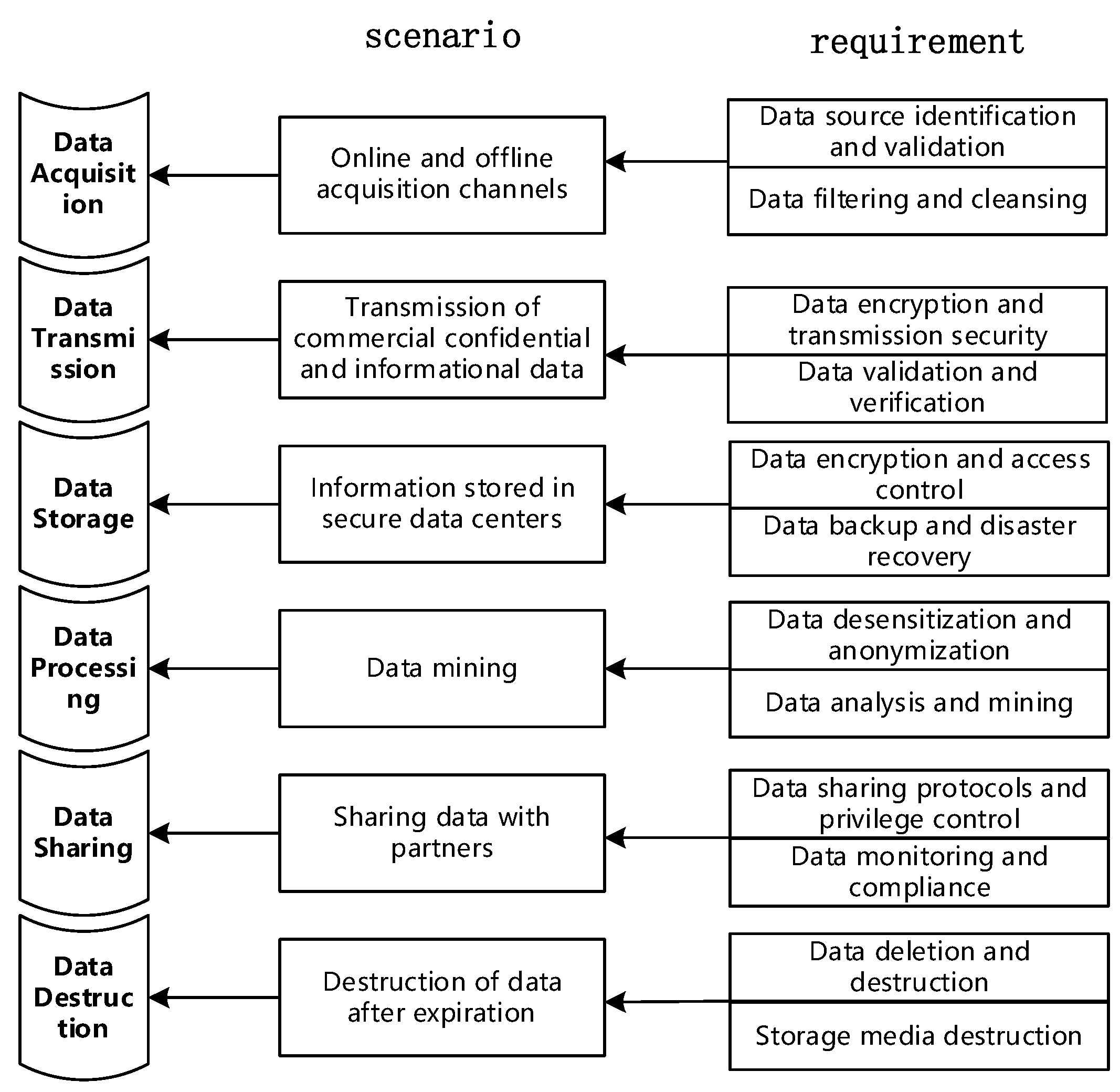
2. Data Lifecycle Protection Requirements
2.1. Data Acquisition Phase
2.2. Data Transmission Phase
2.3. Data Storage Phase
2.4. Data Processing Phase
2.5. Data Sharing Phase
2.6. Data Destruction Phase
3. Analysis of Data Lifecycle Protection Processes
3.1. Overall Process of Data Lifecycle Protection
3.2. Data Services Workflow
4. Risk Detection Programme for Full Lifecycle Protection of Data
4.1. Hierarchical Modelling Constructs for Full Lifecycle Data Security Risks
4.2. Weight-Based Fuzzy Comprehensive Evaluation Analysis
5. Simulation Experiment
- (1)
- Level I (85~100%);
- (2)
- Level II (70~84%);
- (3)
- Level III (60~69%);
- (4)
- Level IV (50~59%);
- (5)
- Level V (Less than 50%).
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Xie, F.; Lin, H.; Lin, Y.; Zhang, X.; Liu, F. A lifecycle security solution for sensitive data. Telecommun. Eng. Stand. 2020, 33, 61–67. [Google Scholar]
- Gartner. How to Use the Data Security goverznance Framework [EB/OL]. 15 August 2019. Available online: https://www.gartner.com/en/documents/3873369/how-to-use-the-data-security-governance-framework (accessed on 2 January 2024).
- Yang, N. Summary Version of Data Security Governance White Paper. Cyber Secur. Informatiz. 2018, 7, 22–26. [Google Scholar]
- Huawei Cloud, Huawei Cloud Data Security White Paper. Available online: https://www.huaweicloud.com/special/baipishu-sjaq.html (accessed on 30 October 2022).
- Zhang, G.; Qiu, X.; Gao, Y. Software defined security architecture with deep learning-based network anomaly detection module. In Proceedings of the 11th IEEE Int Conf on Communication Software and Networks (ICCSN), Chongqing, China, 12–15 June 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 784–788. [Google Scholar]
- Wu, Z.; Liang, C.; Li, Y. Intrusion detection method based on deep learning. In Proceedings of the IEEE Int Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking, Haikou, China, 5–7 July 2019; IEEE: Piscataway, NJ, USA, 2022; pp. 445–452. [Google Scholar]
- Indhumathi, R.; Devi, S.S. Healthcare Cramér generative adversarial network (HCGAN). Distrib. Parallel Databases 2022, 40, 657–673. [Google Scholar] [CrossRef]
- Peng, C.; Jin, L.; Li, Z.; Xing, S.; Zhang, H. Data security risk analysis for the whole data life cycle. Digit. Commun. World 2022, 2, 99–101. [Google Scholar]
- Yang, P.; Xiong, N.; Ren, J. Data security and privacy protection for cloud storage: A survey. IEEE Access 2020, 8, 131723–131740. [Google Scholar] [CrossRef]
- Knowen, C.; Ronoh, L. Prioritizing Personal Data Protection in Insurance Organizations: A Review. J. Inf. Secur. Cybercrimes Res. 2023, 6, 40–56. [Google Scholar] [CrossRef]
- Pan, J.; Wang, J.; Ma, Y. Smart Grid System Security Protection Authentication Encryption Technology. Inf. Syst. Eng. 2023, 1, 64–66. [Google Scholar]
- Peng, J.; Gao, J. Research on Computer Network Information Security and Protection Strategies. Comput. Digit. Eng. 2011, 39, 121–124+178. [Google Scholar]
- Ge, Y.; Xu, W.; Zhang, L. Integrative security protection system for full life cycle of big data based on SM crypto algorithm. In Proceedings of the International Conference on Algorithms, High Performance Computing, and Artificial Intelligence (AHPCAI 2021), Sanya, China, 19–20 November 2021; Volume 12156, pp. 396–402. [Google Scholar]
- Shah, S.I.H.; Peristeras, V.; Magnisalis, I. DaLiF: A data lifecycle framework for data-driven governments. J. Big Data 2021, 8, 1–44. [Google Scholar] [CrossRef]
- Hansen, E.R.; Lissandrini, M.; Ghose, A.; Løkke, S.; Thomsen, C. Transparent integration and sharing of life cycle sustainability data with provenance. In Proceedings of the International Semantic Web Conference, Athens, Greece, 2–6 November 2020; Springer International Publishing: Cham, Switzerland, 2020; pp. 378–394. [Google Scholar]
- Zhou, F.; Qing, C.; Pei, X.B. Data security protection of electricity marketing information system. Comput. Mod. 2019, 3, 111. [Google Scholar]
- Wang, C.; Song, L. Exploration of data security protection system for industrial internet. Inf. Commun. Technol. Policy 2020, 4, 7–11. [Google Scholar]
- Liu, Y.; Eckert, C.M.; Earl, C. A review of fuzzy AHP methods for decision-making with subjective judgements. Expert Syst. Appl. 2020, 161, 113738. [Google Scholar] [CrossRef]
- Malinin, A.; Gales, M. Reverse kl-divergence training of prior networks: Improved uncertainty and adversarial robustness. Adv. Neural Inf. Process. Syst. 2019, 2, 32. [Google Scholar]
- Lyu, H.M.; Sun, W.J.; Shen, S.L.; Zhou, A.N. Risk assessment using a new consulting process in fuzzy AHP. J. Constr. Eng. Manag. 2020, 146, 04019112. [Google Scholar] [CrossRef]
- Lin, X. Design of network security risk detection system based on N-gram algorithm. Inf. Comput. (Theor. Ed.) 2023, 35, 215–217. [Google Scholar]
- Li, N. A fuzzy evaluation model of college English teaching quality based on analytic hierarchy process. Int. J. Emerg. Technol. Learn. (Ijet) 2021, 16, 17–30. [Google Scholar] [CrossRef]
- Kong, D. Research on network security situation assessment technology based on fuzzy evaluation method. J. Phys. Conf. Ser. 2021, 1883, 012108. [Google Scholar] [CrossRef]
- Pamucar, D.; Ecer, F. Prioritizing the weights of the evaluation criteria under fuzziness: The fuzzy full consistency method–FUCOM-F. Facta Univ. Ser. Mech. Eng. 2020, 18, 419–437. [Google Scholar] [CrossRef]
- Zhou, B.; Chen, J.; Wu, Q.; Pamučar, D.; Wang, W.; Zhou, L. Risk priority evaluation of power transformer parts based on hybrid FMEA framework under hesitant fuzzy environment. Facta Univ. Ser. Mech. Eng. 2022, 20, 399–420. [Google Scholar]



| Number of Experiments/Session | Probability of Occurrence of Real Risk/% | True Risk Level | Assessing Risk Level |
|---|---|---|---|
| 1 | 77 | II | II |
| 2 | 67 | III | III |
| 3 | 90 | I | I |
| 4 | 55 | IV | IV |
| 5 | 78 | II | II |
| 6 | 89 | I | I |
| 7 | 64 | III | III |
| 8 | 51 | IV | IV |
| 9 | 95 | I | I |
| 10 | 75 | II | II |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, Y.; Jiang, S.; Shan, Q.; Yang, Y.; Yu, Y.; Shen, W.; Guo, Q. Hierarchical-Based Dynamic Scenario-Adaptive Risk Assessment for Power Data Lifecycle. Electronics 2024, 13, 631. https://doi.org/10.3390/electronics13030631
Song Y, Jiang S, Shan Q, Yang Y, Yu Y, Shen W, Guo Q. Hierarchical-Based Dynamic Scenario-Adaptive Risk Assessment for Power Data Lifecycle. Electronics. 2024; 13(3):631. https://doi.org/10.3390/electronics13030631
Chicago/Turabian StyleSong, Yubo, Shuai Jiang, Qiuhong Shan, Yixin Yang, Yue Yu, Wen Shen, and Qian Guo. 2024. "Hierarchical-Based Dynamic Scenario-Adaptive Risk Assessment for Power Data Lifecycle" Electronics 13, no. 3: 631. https://doi.org/10.3390/electronics13030631
APA StyleSong, Y., Jiang, S., Shan, Q., Yang, Y., Yu, Y., Shen, W., & Guo, Q. (2024). Hierarchical-Based Dynamic Scenario-Adaptive Risk Assessment for Power Data Lifecycle. Electronics, 13(3), 631. https://doi.org/10.3390/electronics13030631






