Reconfigurable CAN Intrusion Detection and Response System
Abstract
1. Introduction
- Create a real scenario environment for an embedded system showcasing a bus-off assault on the CAN accompanied by a method for detecting such an attack.
- Devise a safeguarding mechanism for CAN communication with a response system designed to counteract potential intrusions.
- Explore different configurations of CAN communication protocol error states on reconfigurable platforms forming part of intrusion detection and intrusion response systems.
- Introduce a reconfigurable CAN protocol based on a field programmable gate array (FPGA).
2. Background
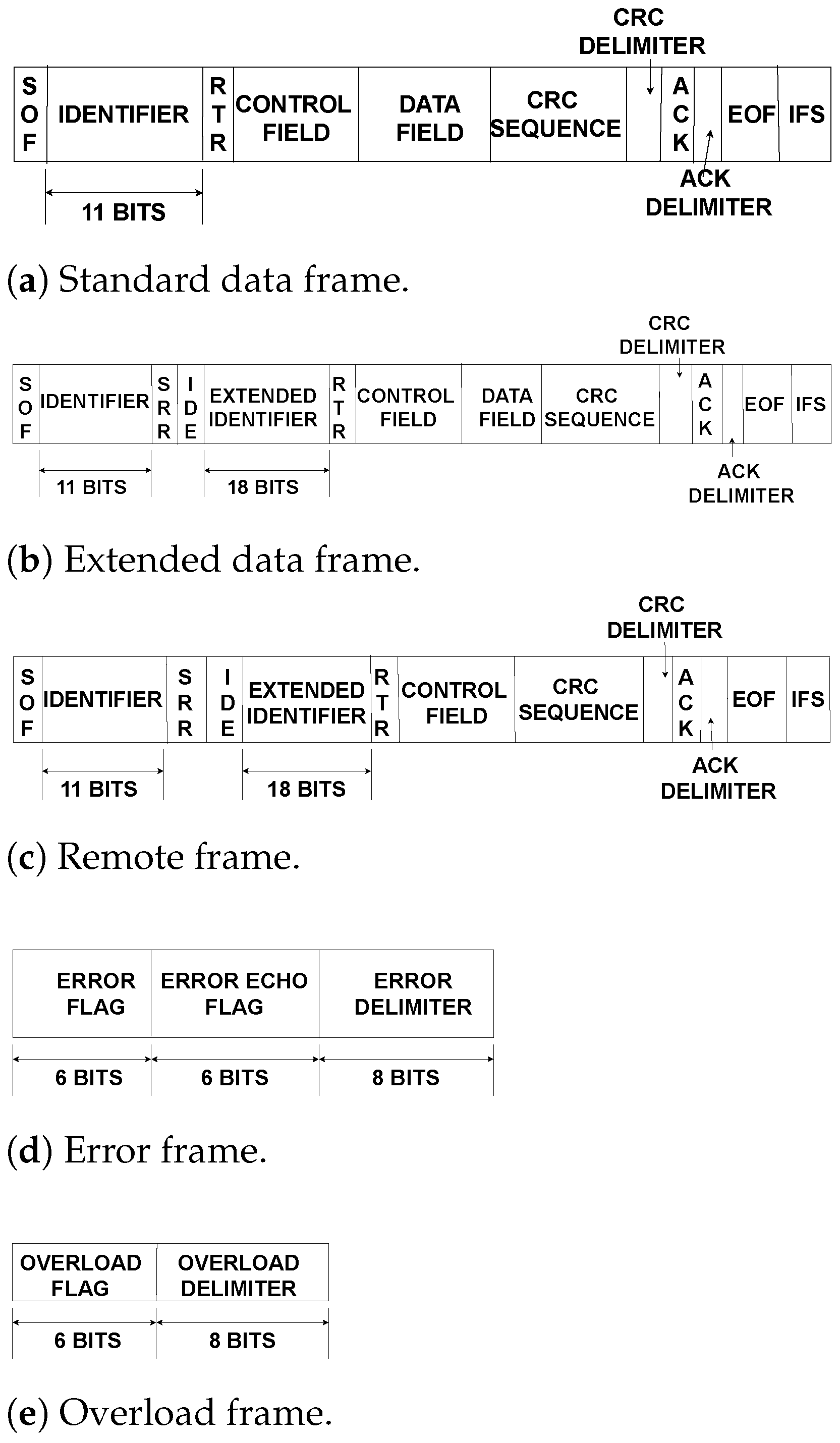
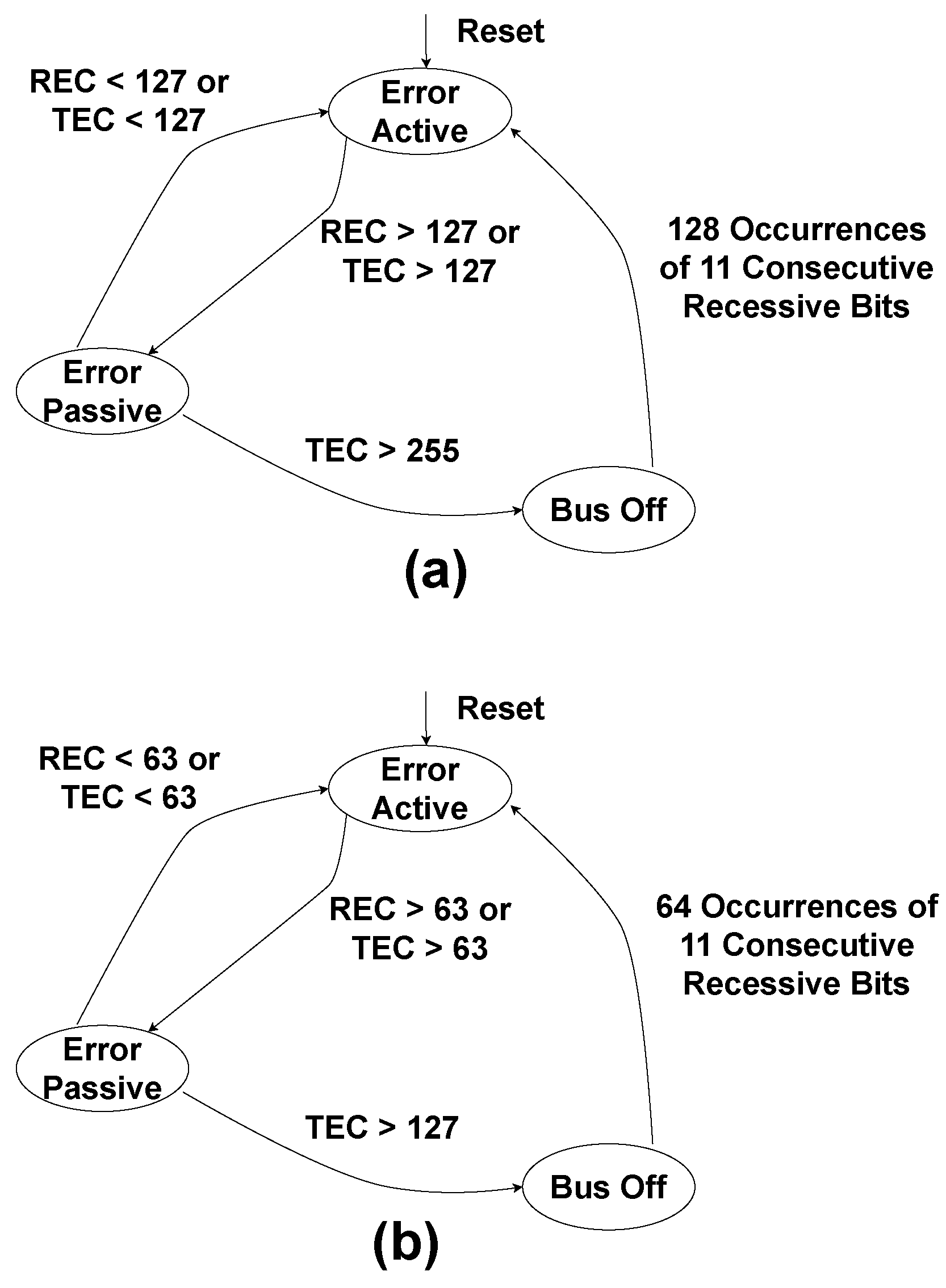
2.1. CAN Preliminaries
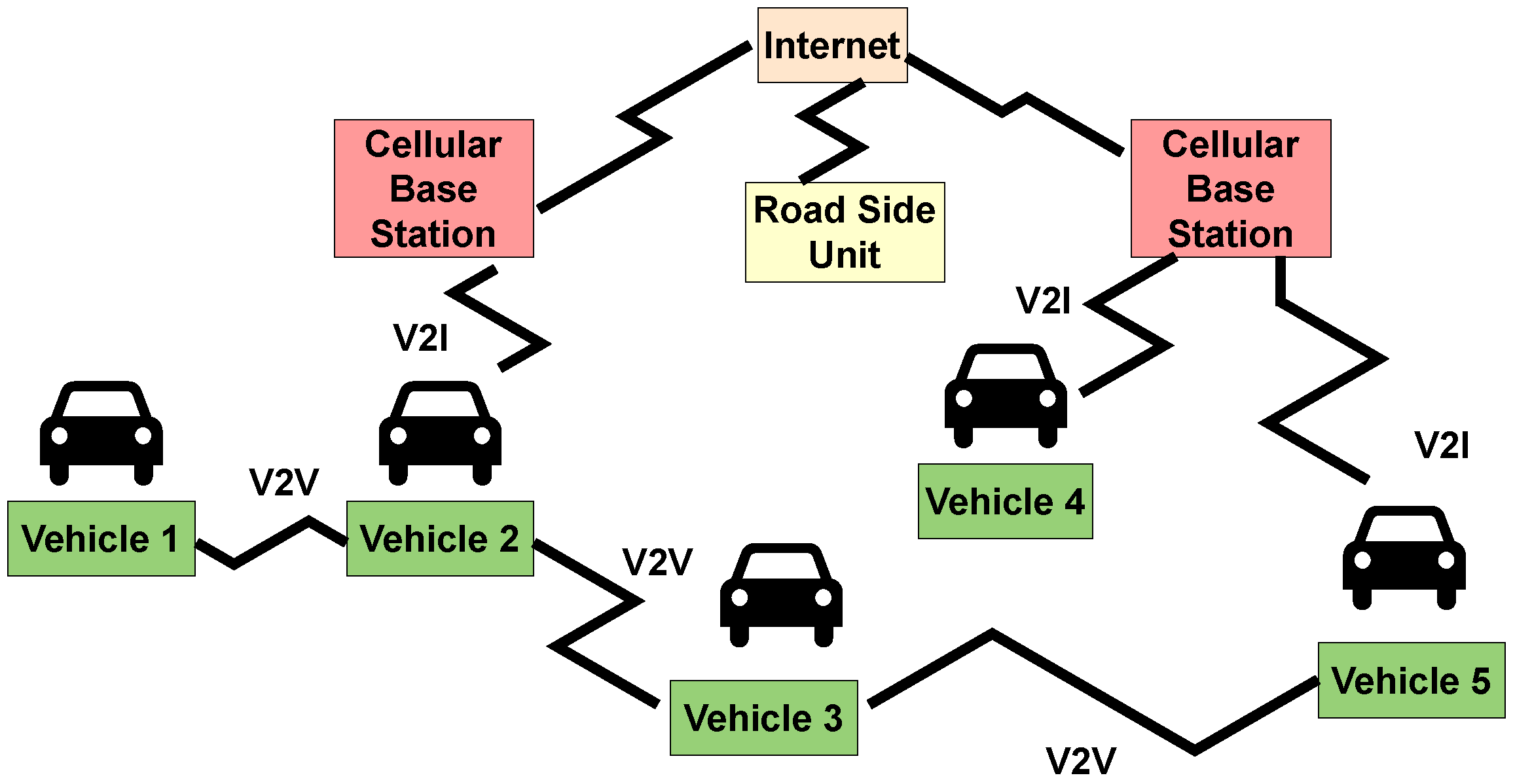
2.2. Characteristics and Vulnerabilities of CAN IVNs
2.2.1. IVN Characteristics
2.2.2. Vulnerabilities in CAN-Based IVNs
2.3. Types of CAN Attacks
2.4. Constraints of CAN IVN IDS
2.5. Categories of IVN IDSs
2.5.1. Statistical-Based IDS for IVN
2.5.2. Machine Learning-Based IDS for IVN
2.5.3. Neural Network-Based IDS for IVN
2.6. Advantages of Implementing CAN Protocol on Reconfigurable Computing Platform
3. Proposed Methodology
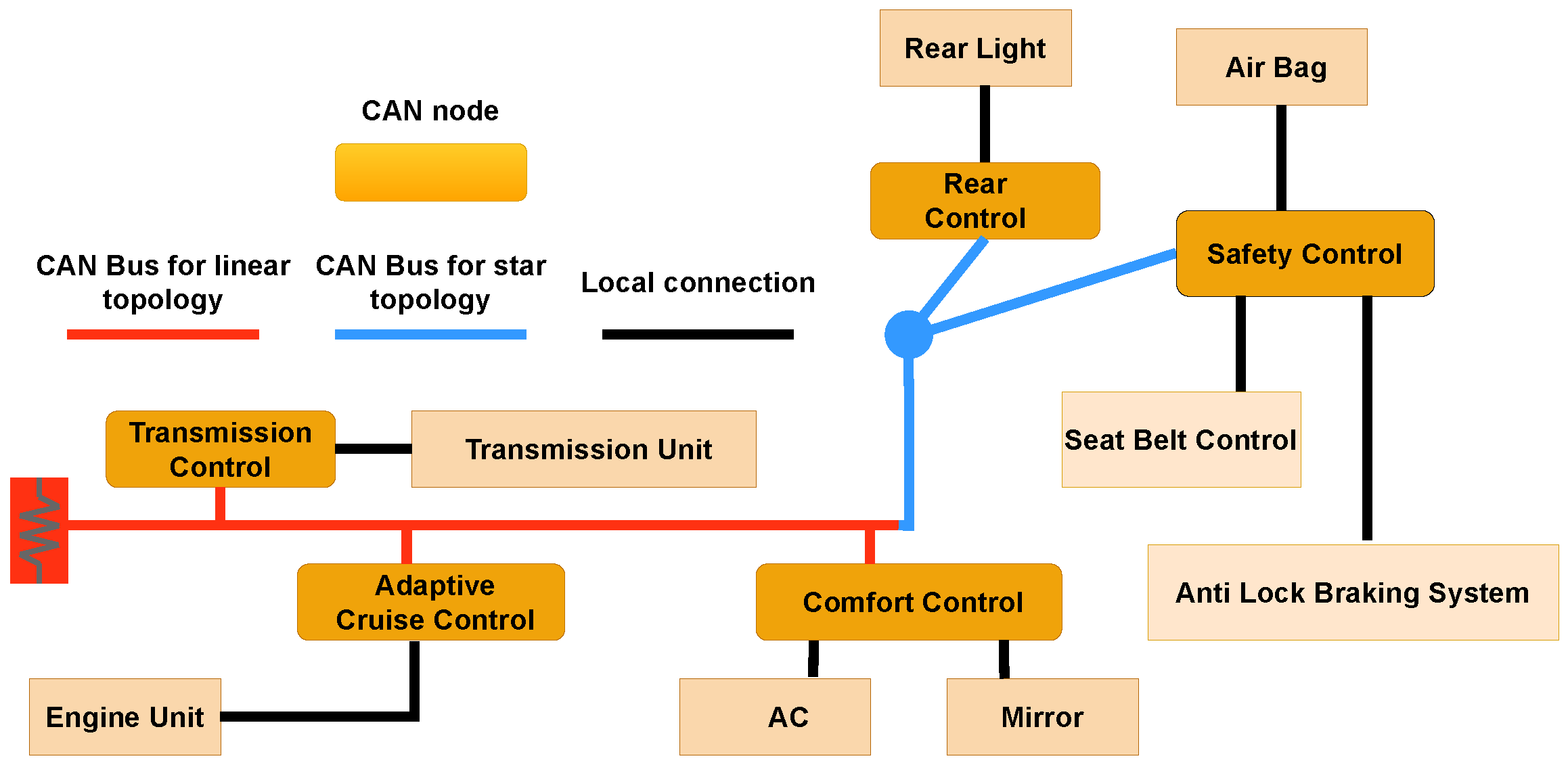
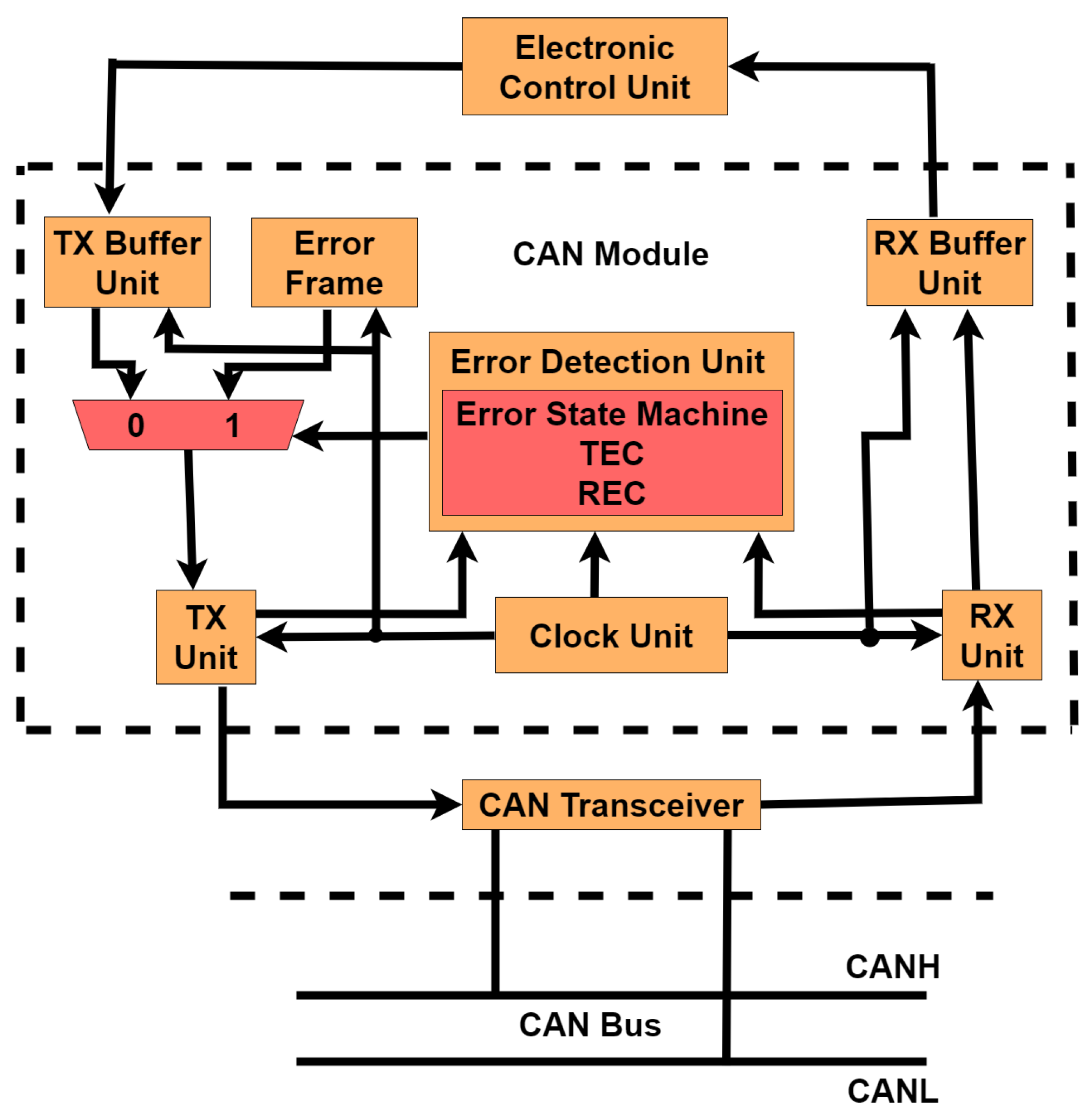
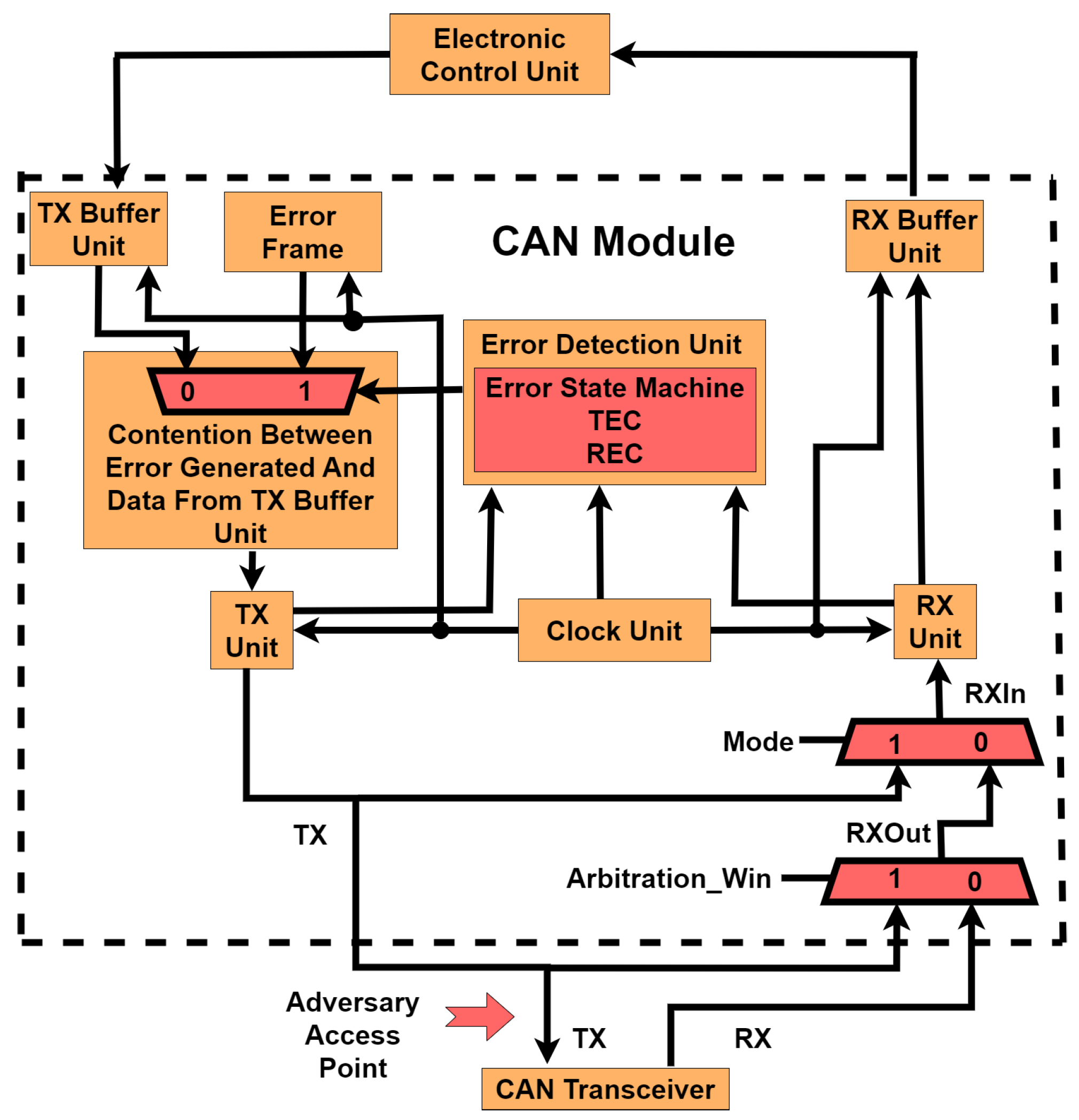
3.1. CAN Architecture
3.2. Communication among CAN Nodes over CAN Bus
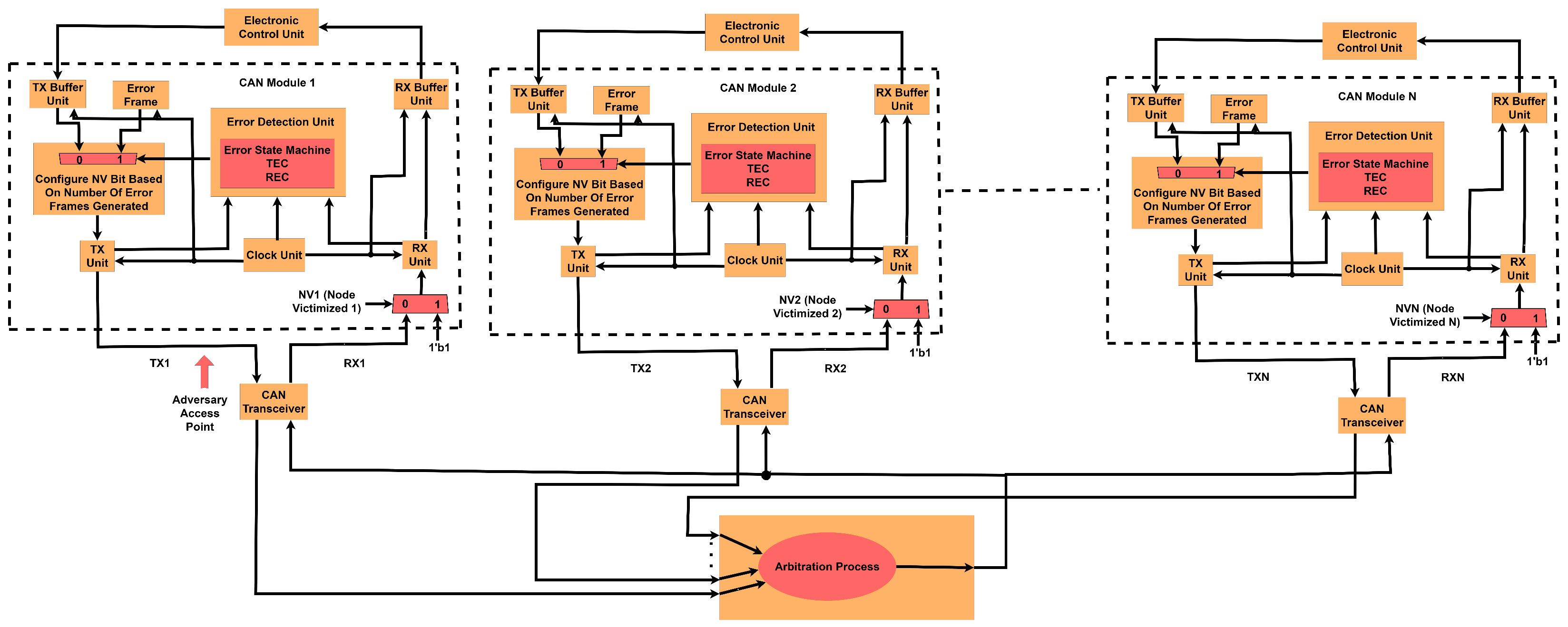
3.3. Proposed Intrusion Detection and Intrusion Response Systems
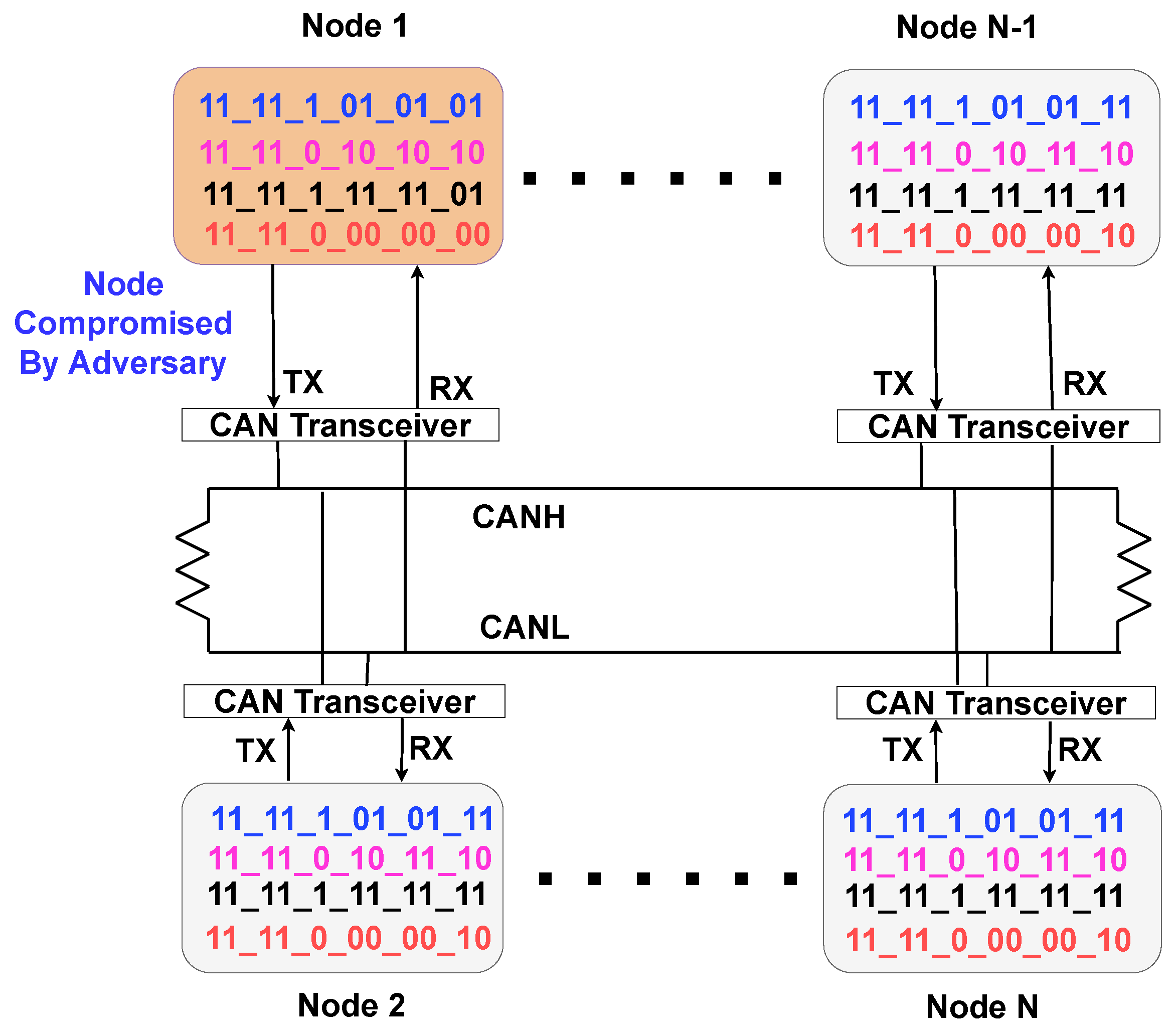
3.4. Threat Model for Individual CAN Nodes Interacting over CAN Bus
3.5. Threat Model for Interaction of Multiple CAN Nodes
| Algorithm 1 The bus-off attack detection and response algorithm. |
|
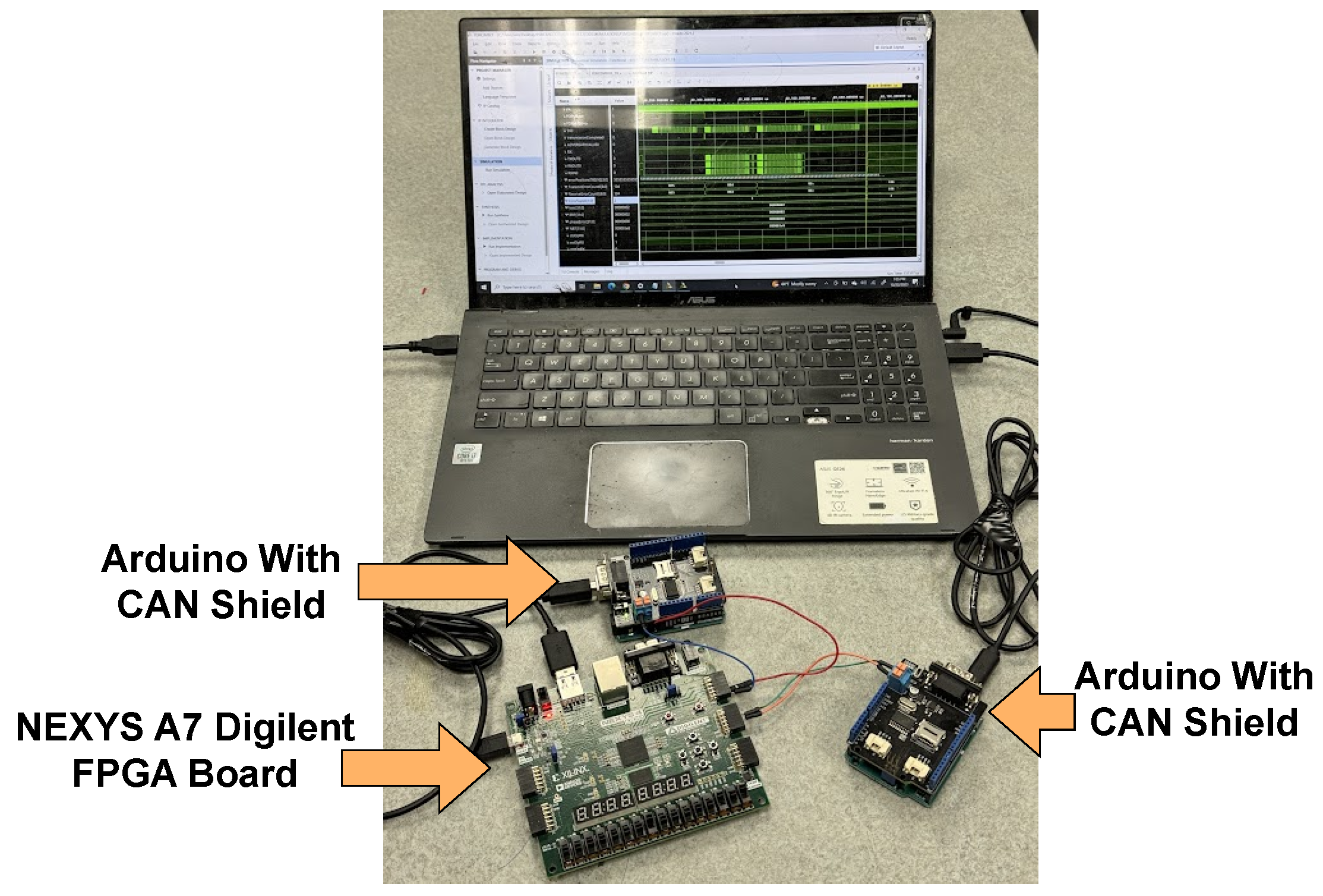
4. Experimental Results
4.1. Experimental Setup
4.2. Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wei, H.; Ai, Q.; Zhai, Y.; Zhang, Y. Automotive Security: Threat Forewarning and ECU Source Mapping Derived From Physical Features of Network Signals. IEEE Trans. Intell. Transp. Syst. 2023, 25, 2479–2491. [Google Scholar] [CrossRef]
- Tan, Z.; Dai, N.; Su, Y.; Zhang, R.; Li, Y.; Wu, D.; Li, S. Human—Machine interaction in intelligent and connected vehicles: A review of status quo, issues, and opportunities. IEEE Trans. Intell. Transp. Syst. 2021, 23, 13954–13975. [Google Scholar] [CrossRef]
- Siegel, J.E.; Erb, D.C.; Sarma, S.E. A survey of the connected vehicle landscape—Architectures, enabling technologies, applications, and development areas. IEEE Trans. Intell. Transp. Syst. 2017, 19, 2391–2406. [Google Scholar] [CrossRef]
- Su, Z.; Dai, M.; Xu, Q.; Li, R.; Zhang, H. UAV enabled content distribution for internet of connected vehicles in 5G heterogeneous networks. IEEE Trans. Intell. Transp. Syst. 2021, 22, 5091–5102. [Google Scholar] [CrossRef]
- Sunny, J.; Sankaran, S.; Saraswat, V. A Hybrid Approach for Fast Anomaly Detection in Controller Area Networks. In Proceedings of the 2020 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), New Delhi, India, 14–17 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Blanco, S. Car Hacking Danger Is Likely Closer than You Thinkt. Available online: https://www.caranddriver.com/news/a37453835/car-hacking-danger-is-likely-closer-than-you-think/ (accessed on 1 April 2024).
- Shin, C. A framework for fragmenting/reconstituting data frame in Controller Area Network (CAN). In Proceedings of the 16th International Conference on Advanced Communication Technology, Pyeongchang, Republic of Korea, 16–19 February 2014; pp. 1261–1264. [Google Scholar] [CrossRef]
- Ullah, K. On the Use of Opportunistic Vehicular Communication for Roadside Services Advertisement and Discovery. Ph.D. Thesis, Universidade de São Paulo, São Paulo, Brazil, 2016. [Google Scholar]
- Zhang, X.; Cui, X.; Cheng, K.; Zhang, L. A Convolutional Encoder Network for Intrusion Detection in Controller Area Networks. In Proceedings of the 2020 16th International Conference on Computational Intelligence and Security (CIS), Guangxi, China, 27–30 November 2020; pp. 366–369. [Google Scholar] [CrossRef]
- Choi, E.; Han, S.; Choi, J.W. Channel capacity analysis for high speed controller area network (CAN). In Proceedings of the 2015 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 28–30 October 2015; pp. 188–190. [Google Scholar] [CrossRef]
- Jeong, Y.; Kim, H.; Lee, S.; Choi, W.; Lee, D.H.; Jo, H.J. In-Vehicle Network Intrusion Detection System Using CAN Frame-Aware Features. IEEE Trans. Intell. Transp. Syst. 2023, 25, 3843–3853. [Google Scholar] [CrossRef]
- Cho, K.T.; Shin, K.G. Fingerprinting electronic control units for vehicle intrusion detection. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016; pp. 911–927. [Google Scholar]
- Jo, H.J.; Choi, W. A Survey of Attacks on Controller Area Networks and Corresponding Countermeasures. IEEE Trans. Intell. Transp. Syst. 2022, 23, 6123–6141. [Google Scholar] [CrossRef]
- Islam, R.; Devnath, M.K.; Samad, M.D.; Al Kadry, S.M.J. GGNB: Graph-based Gaussian naive Bayes intrusion detection system for CAN bus. Veh. Commun. 2022, 33, 100442. [Google Scholar] [CrossRef]
- Ansari, M.R.; Yu, S.; Yu, Q. IntelliCAN: Attack-resilient Controller Area Network (CAN) for secure automobiles. In Proceedings of the 2015 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFTS), Amherst, MA, USA, 12–14 October 2015; pp. 233–236. [Google Scholar] [CrossRef]
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A Survey of Intrusion Detection for In-Vehicle Networks. IEEE Trans. Intell. Transp. Syst. 2020, 21, 919–933. [Google Scholar] [CrossRef]
- Khandelwal, S.; Shreejith, S. A Lightweight FPGA-based IDS-ECU Architecture for Automotive CAN. In Proceedings of the 2022 International Conference on Field-Programmable Technology (ICFPT), Hong Kong, China, 5–9 December 2022; pp. 1–9. [Google Scholar]
- Islam, R.; Refat, R.U.D. Improving CAN bus security by assigning dynamic arbitration IDs. J. Transp. Secur. 2020, 13, 19–31. [Google Scholar] [CrossRef]
- Pollicino, F.; Stabili, D.; Marchetti, M. Performance comparison of timing-based anomaly detectors for Controller Area Network: A reproducible study. Acm Trans.-Cyber-Phys. Syst. 2023, 8, 1–24. [Google Scholar] [CrossRef]
- Tariq, S.; Lee, S.; Woo, S.S. CANTransfer: Transfer learning based intrusion detection on a controller area network using convolutional LSTM network. In Proceedings of the 35th annual ACM symposium on applied computing, Brno, Czech Republic, 30 March–3 April 2020; pp. 1048–1055. [Google Scholar]
- Microchip, C. Controller MCP2515 Datasheet. Available online: https://ww1.microchip.com/downloads/aemDocuments/documents/APID/ProductDocuments/DataSheets/MCP2515-Family-Data-Sheet-DS20001801K.pdf (accessed on 1 April 2023).
- Zhang, L. Intrusion Detection Systems to Secure In-Vehicle Networks. Ph.D. Thesis, University of Michigan-Dearborn, Dearborn, MI, USA, 2023. [Google Scholar]
- Han, K.; Mun, H.; Balakrishnan, M.; Yeun, C.Y. Enhancing security and robustness of Cyphal on Controller Area Network in unmanned aerial vehicle environments. Comput. Secur. 2023, 135, 103481. [Google Scholar] [CrossRef]
- Olufowobi, H.; Young, C.; Zambreno, J.; Bloom, G. Saiducant: Specification-based automotive intrusion detection using controller area network (can) timing. IEEE Trans. Veh. Technol. 2019, 69, 1484–1494. [Google Scholar] [CrossRef]
- Zhang, H.; Meng, X.; Zhang, X.; Liu, Z. CANsec: A practical in-vehicle controller area network security evaluation tool. Sensors 2020, 20, 4900. [Google Scholar] [CrossRef] [PubMed]
- Park, S.B.; Jo, H.J.; Lee, D.H. Flooding attack mitigator for in-vehicle CAN using fault confinement in CAN protocol. Comput. Secur. 2023, 126, 103091. [Google Scholar] [CrossRef]
- Humayed, A.; Li, F.; Lin, J.; Luo, B. Cansentry: Securing can-based cyber-physical systems against denial and spoofing attacks. In Proceedings of the Computer Security—ESORICS 2020: 25th European Symposium on Research in Computer Security, ESORICS 2020, Guildford, UK, 14–18 September 2020; Proceedings, Part I 25. Springer: Berlin/Heidelberg, Germany, 2020; pp. 153–173. [Google Scholar]
- Han, M.L.; Kwak, B.I.; Kim, H.K. Event-triggered interval-based anomaly detection and attack identification methods for an in-vehicle network. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2941–2956. [Google Scholar] [CrossRef]
- Ansari, M.R. Low-Cost Approaches to Detect Masquerade and Replay Attacks on Automotive Controller Area Network. Ph.D. Thesis, University of New Hampshire, Durham, NH, USA, 2016. [Google Scholar]
- Jedh, M.; Othmane, L.B.; Ahmed, N.; Bhargava, B. Detection of message injection attacks onto the can bus using similarities of successive messages-sequence graphs. IEEE Trans. Inf. Forensics Secur. 2021, 16, 4133–4146. [Google Scholar] [CrossRef]
- Islam, R.; Refat, R.U.D.; Yerram, S.M.; Malik, H. Graph-based intrusion detection system for controller area networks. IEEE Trans. Intell. Transp. Syst. 2020, 23, 1727–1736. [Google Scholar] [CrossRef]
- Zhang, H.; Zeng, K.; Lin, S. Federated graph neural network for fast anomaly detection in controller area networks. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1566–1579. [Google Scholar] [CrossRef]
- Müter, M.; Asaj, N. Entropy-based anomaly detection for in-vehicle networks. In Proceedings of the 2011 IEEE Intelligent Vehicles Symposium (IV), Baden-Baden, Germany, 5–9 June 2011; pp. 1110–1115. [Google Scholar]
- Marchetti, M.; Stabili, D.; Guido, A.; Colajanni, M. Evaluation of anomaly detection for in-vehicle networks through information-theoretic algorithms. In Proceedings of the 2016 IEEE 2nd International Forum on Research and Technologies for Society and Industry Leveraging a better tomorrow (RTSI), Bologna, Italy, 7–9 September 2016; pp. 1–6. [Google Scholar]
- Mithu, M.R.A.; Kholodilo, V.; Manicavasagam, R.; Ulybyshev, D.; Rogers, M. Secure industrial control system with intrusion detection. In Proceedings of the Thirty-Third International Flairs Conference, North Miami Beach, FL, USA, 17–20 May 2020. [Google Scholar]
- Moulahi, T.; Zidi, S.; Alabdulatif, A.; Atiquzzaman, M. Comparative performance evaluation of intrusion detection based on machine learning in in-vehicle controller area network bus. IEEE Access 2021, 9, 99595–99605. [Google Scholar] [CrossRef]
- Dong, Y.; Chen, K.; Peng, Y.; Ma, Z. Comparative study on supervised versus semi-supervised machine learning for anomaly detection of in-vehicle CAN network. In Proceedings of the 2022 IEEE 25th International Conference on Intelligent Transportation Systems (ITSC), Macau, China, 8–12 October 2022; pp. 2914–2919. [Google Scholar]
- Narasimhan, H.; Vinayakumar, R.; Mohammad, N. Unsupervised deep learning approach for in-vehicle intrusion detection system. IEEE Consum. Electron. Mag. 2021, 12, 103–108. [Google Scholar] [CrossRef]
- Islam, R. Early Stage DRC Prediction Using Ensemble Machine Learning Algorithms. IEEE Can. J. Electr. Comput. Eng. 2022, 45, 354–364. [Google Scholar] [CrossRef]
- Seo, E.; Song, H.M.; Kim, H.K. GIDS: GAN based intrusion detection system for in-vehicle network. In Proceedings of the 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, Ireland, 28–30 August 2018; pp. 1–6. [Google Scholar]
- Desta, A.K.; Ohira, S.; Arai, I.; Fujikawa, K. U-CAN: A Convolutional Neural Network Based Intrusion Detection for Controller Area Networks. In Proceedings of the 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC), Los Alamitos, CA, USA, 27 June–1 July 2022; pp. 1481–1488. [Google Scholar]
- Kheddar, H.; Himeur, Y.; Awad, A.I. Deep transfer learning for intrusion detection in industrial control networks: A comprehensive review. J. Netw. Comput. Appl. 2023, 220, 103760. [Google Scholar] [CrossRef]
- Kulisz, J.; Jokiel, F. A Hardware Implementation of the PID Algorithm Using Floating-Point Arithmetic. Electronics 2024, 13, 1598. [Google Scholar] [CrossRef]
- Islam, R.; Saha, B.; Bezzam, I. Resonant Energy Recycling SRAM Architecture. IEEE Trans. Circuits Syst. II Express Briefs 2021, 68, 1383–1387. [Google Scholar] [CrossRef]
- Islam, R. Feasibility Prediction for Rapid IC Design Space Exploration. Electronics 2022, 11, 1161. [Google Scholar] [CrossRef]
- Joost, R.; Salomon, R. Advantages of FPGA-based multiprocessor systems in industrial applications. In Proceedings of the 31st Annual Conference of IEEE Industrial Electronics Society, 2005. IECON 2005, Raleigh, NC, USA, 6–10 November 2005. [Google Scholar]
- Croteau, B.; Kiriakidis, K.; Severson, T.A.; Robucci, R.; Rahman, S.; Islam, R. State Estimation Adaptable to Cyberattack Using a Hardware Programmable Bank of Kalman Filters. IEEE Trans. Control Syst. Technol. 2024, 1–13. [Google Scholar] [CrossRef]
- Tang, L.; Li, Y.; Wang, H.; Sun, Y. Verification of CAN bus controller based on VIP. In Proceedings of the 2023 IEEE International Conference on Sensors, Electronics and Computer Engineering (ICSECE), Jinzhou, China, 18–20 August 2023; pp. 1383–1387. [Google Scholar]
- Lee, H.; Jeong, S.; Kim, H. CAN Dataset for Intrusion Detection; Hacking and Countermeasure Research Lab: Seoul, Republic of Korea, 2018; Available online: https://goo.gl/WiVeFj (accessed on 1 April 2024).




| Modules | Description |
|---|---|
| TX | Basic CAN transmission module. |
| RX | Basic CAN reception module. |
| GE | A module that introduces form error, CRC error, and bit error in a single frame within a single CAN node built on the combination of transmission and reception modules. |
| MGE | A module that presents form error, CRC error, and bit error in multiple frames within a single CAN node built on top of the GE module. |
| MGEESM | A module that introduces form error, CRC error, and bit error in multiple frames and introduces an error state machine within a single CAN node built based on the MGE module. |
| MCIWOERROR111 | A module that interacts with multiple nodes without error introduction for a frame size of 111 bits. |
| MCIWITHERROR111 | A module that interacts with multiple nodes and considers error introduction for a frame size of 111 bits. |
| BOAD111 | A module that interacts with multiple nodes and considers the introduction of errors and error state machine for a frame size of 111 bits. |
| Modules | Slice LUTs | Slice Registers | Slice | LUT as Logic | Bonded IOB | BUFGCTRL | F7 Muxes | F8 Muxes |
|---|---|---|---|---|---|---|---|---|
| MGEESM | 2299 | 595 | 794 | 2299 | 26 | 1 | 92 | 7 |
| BOAD111 | 2663 | 662 | 897 | 2663 | 21 | 1 | - | - |
| Modules | Sub-Cases | Latency | Power | Energy |
|---|---|---|---|---|
| Form Error in MGEESM | TEC value 255. Error introduced every frame. | 8.730 ms | 0.113 W | 0.986 mJ |
| TEC value 255. Error introduced every alternate frame. | 13.886 ms | 0.113 W | 1.569 mJ | |
| TEC value 127. Error introduced every frame. | 4.314 ms | 0.113 W | 0.487 mJ | |
| TEC value 127. Error introduced every alternate frame. | 7.008 ms | 0.113 W | 0.792 mJ | |
| CRC Error in MGEESM | TEC value 255. Error introduced every frame. | 8.606 ms | 0.113 W | 0.972 mJ |
| TEC value 255. Error introduced every alternate frame. | 13.742 ms | 0.113 W | 1.553 mJ | |
| TEC value 127. Error introduced every frame. | 4.254 ms | 0.113 W | 0.481 mJ | |
| TEC value 127. Error introduced every alternate frame. | 6.936 ms | 0.113 W | 0.784 mJ | |
| Bit Error in MGEESM | TEC value 255. Error introduced every frame. | 8.048 ms | 0.113 W | 0.909 mJ |
| TEC value 255. Error introduced every alternate frame | 13.094 ms | 0.113 W | 1.480 mJ | |
| TEC value 127. Error introduced every frame. | 3.984 ms | 0.113 W | 0.450 mJ | |
| TEC value 127. Error introduced every alternate frame. | 6.612 ms | 0.113 W | 0.747 mJ | |
| BOAD111 | TEC value 255. Error introduced every frame. | 7.711 ms | 0.115 W | 0.887 mJ |
| TEC value 255. Error introduced every alternate frame. | 12.582 ms | 0.115 W | 1.447 mJ | |
| TEC value 127. Error introduced every frame. | 3.951 ms | 0.115 W | 0.454 mJ | |
| TEC value 127. Error introduced every alternate frame. | 6.442 ms | 0.115 W | 0.741 mJ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saini, R.; Islam, R. Reconfigurable CAN Intrusion Detection and Response System. Electronics 2024, 13, 2672. https://doi.org/10.3390/electronics13132672
Saini R, Islam R. Reconfigurable CAN Intrusion Detection and Response System. Electronics. 2024; 13(13):2672. https://doi.org/10.3390/electronics13132672
Chicago/Turabian StyleSaini, Rachit, and Riadul Islam. 2024. "Reconfigurable CAN Intrusion Detection and Response System" Electronics 13, no. 13: 2672. https://doi.org/10.3390/electronics13132672
APA StyleSaini, R., & Islam, R. (2024). Reconfigurable CAN Intrusion Detection and Response System. Electronics, 13(13), 2672. https://doi.org/10.3390/electronics13132672






